Computationally Efficient Robust Color Image Watermarking Using Fast Walsh Hadamard Transform
Abstract
:1. Introduction
2. Walsh Hadamard Transform and Related Works
3. Proposed Algorithm
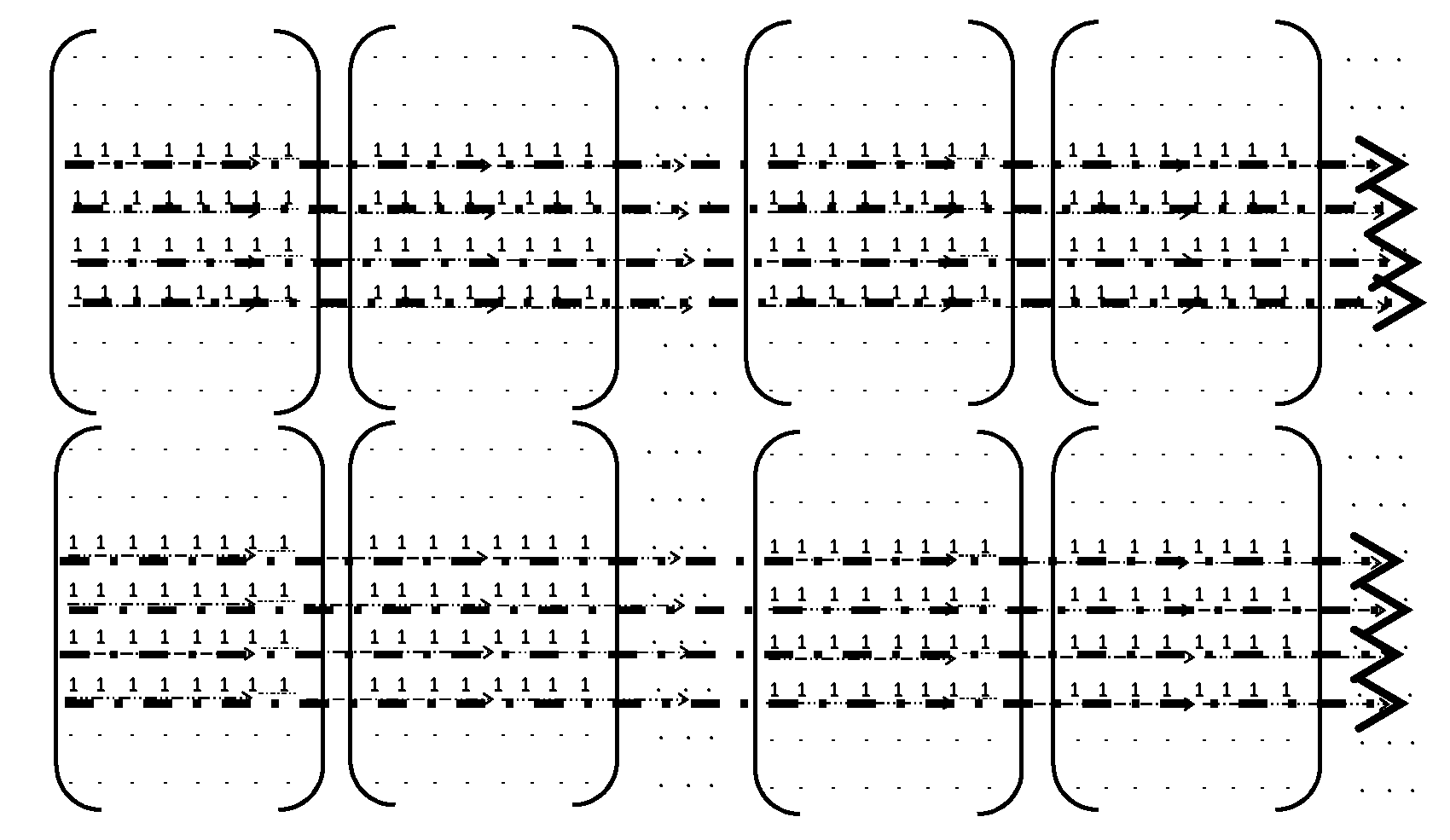
3.1. Computational Efficient Calculation
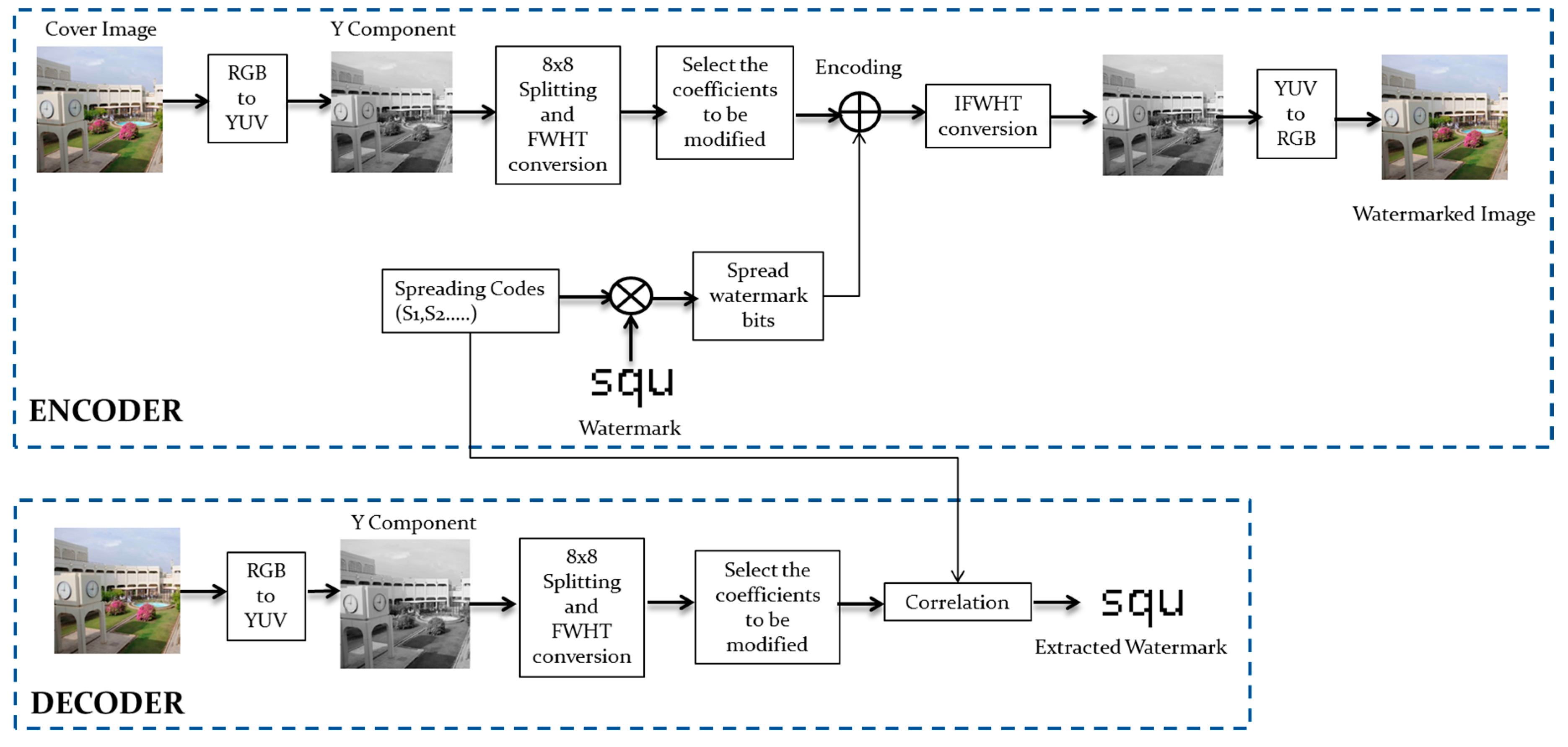
3.2. Embedding Algorithm
3.3. Decoding Algorithm
4. Performance Evaluation and Simulation Results
4.1. Performance Measures
4.2. Computational Complexity and Execution Time
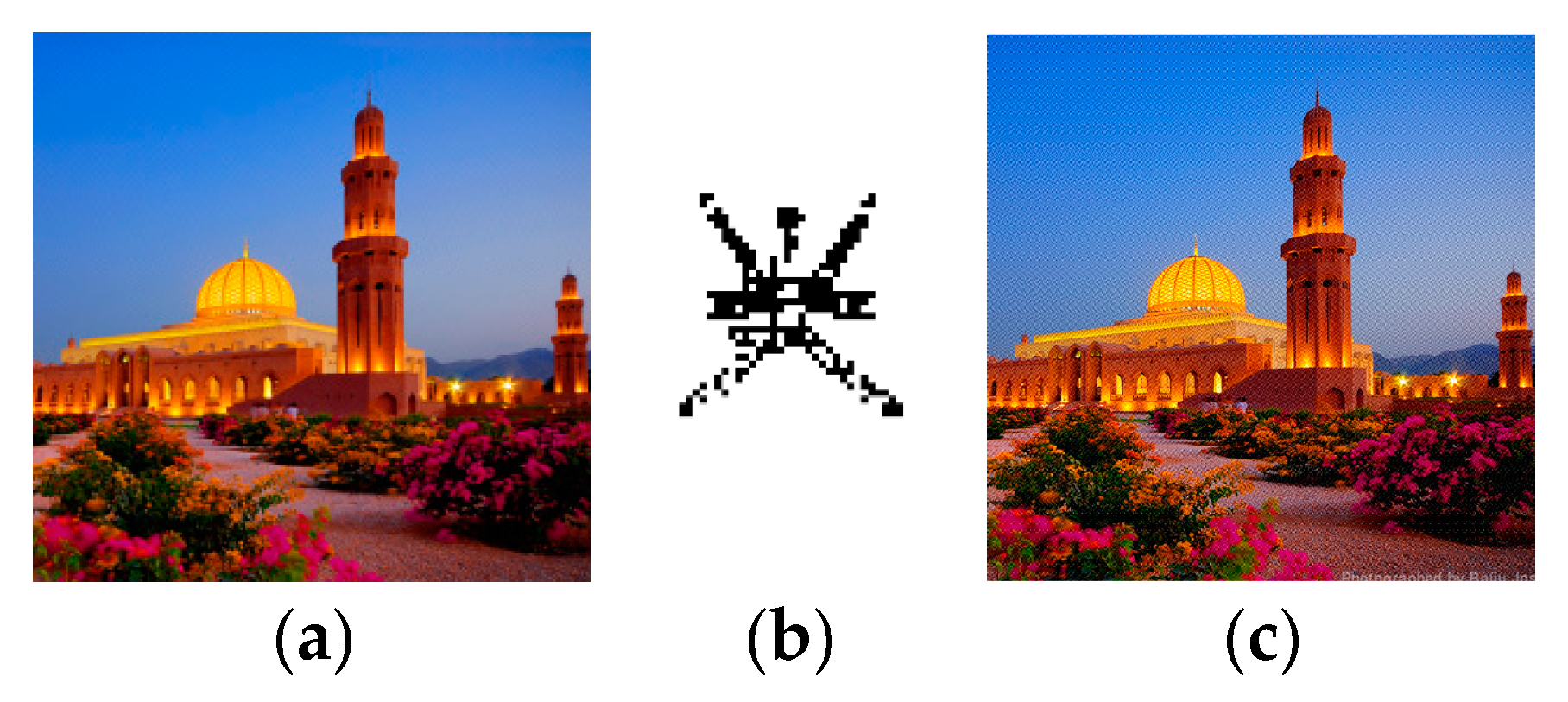
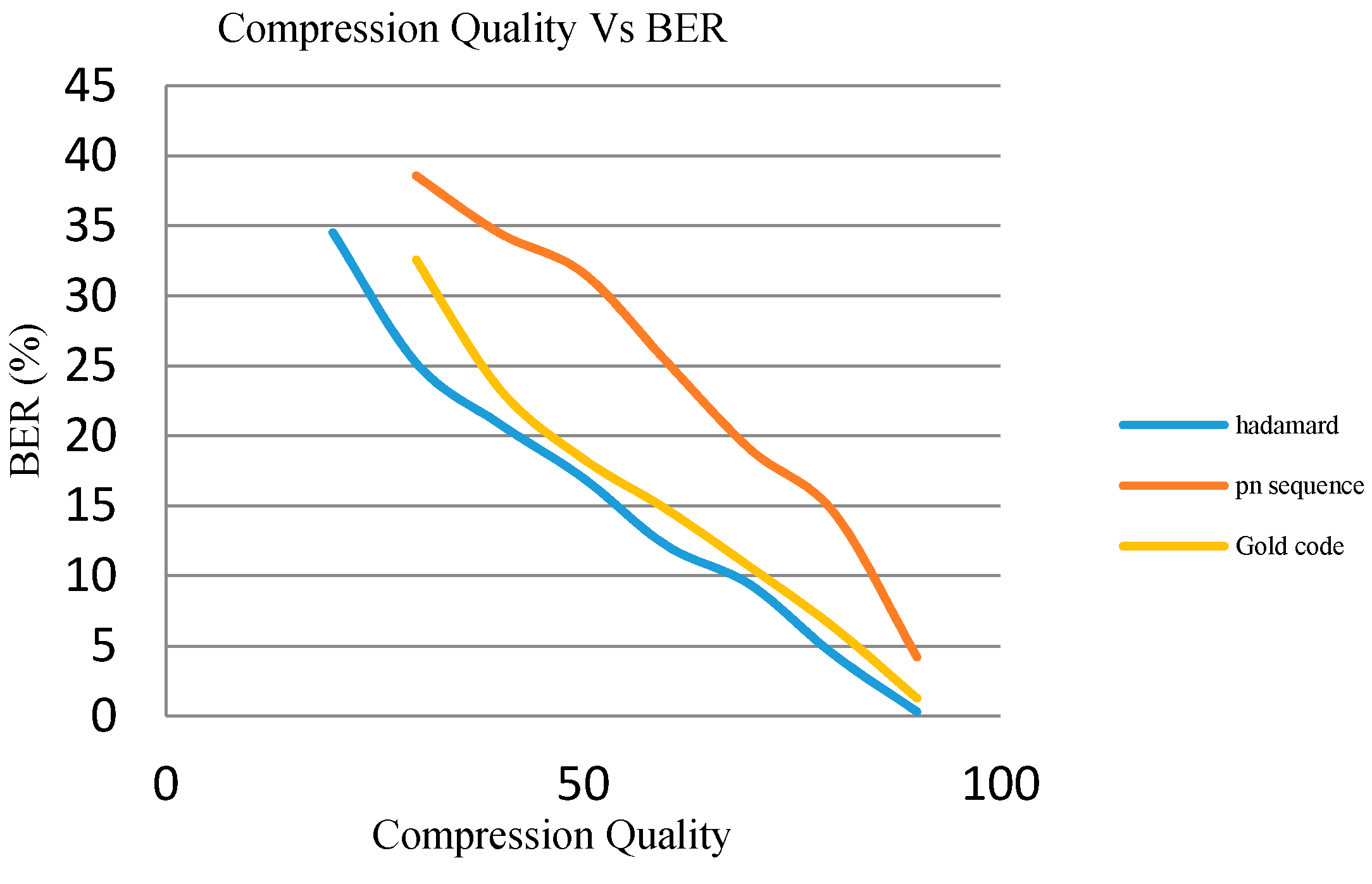
4.3. Perceptual Quality
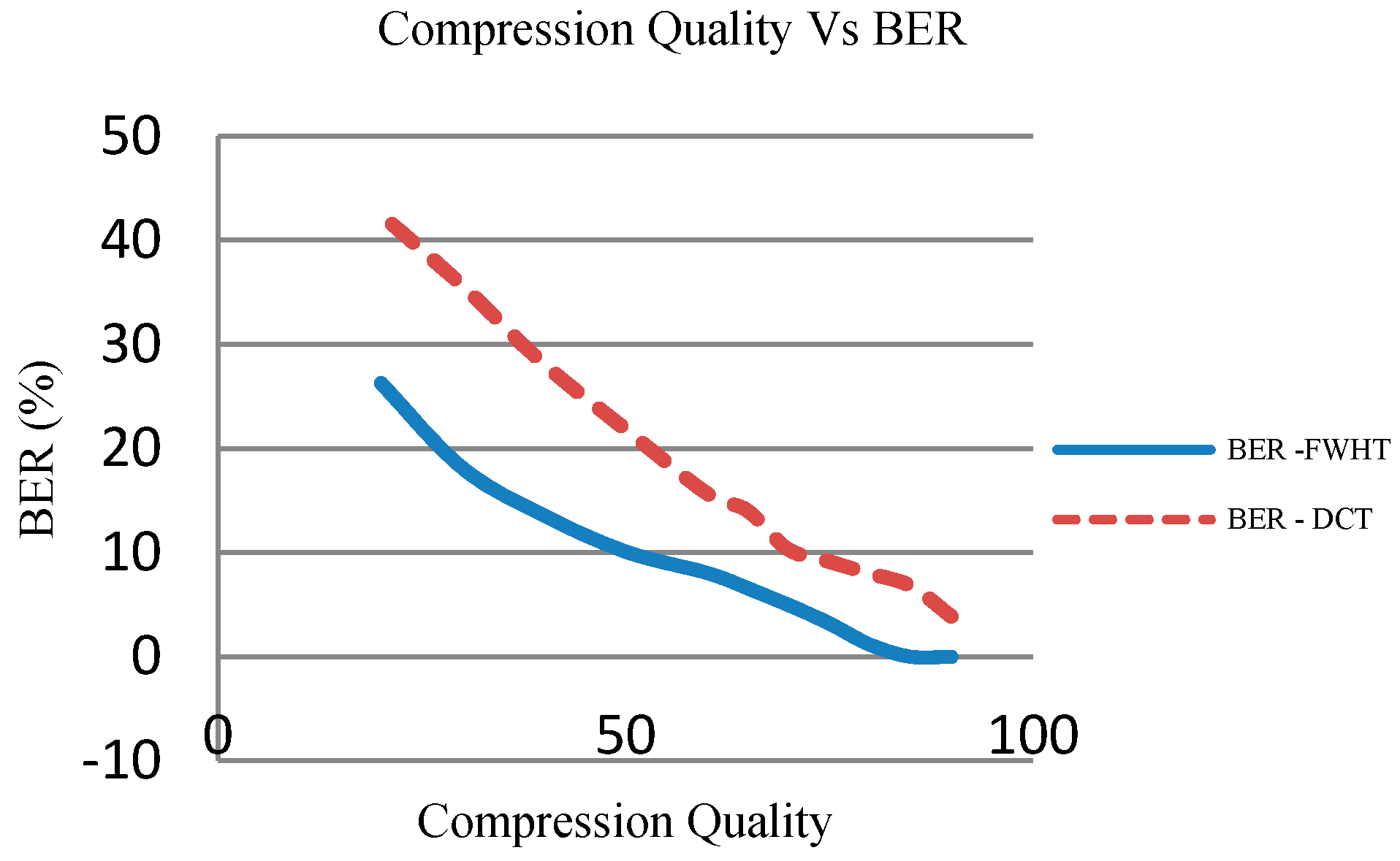
4.4. Robustness Analysis
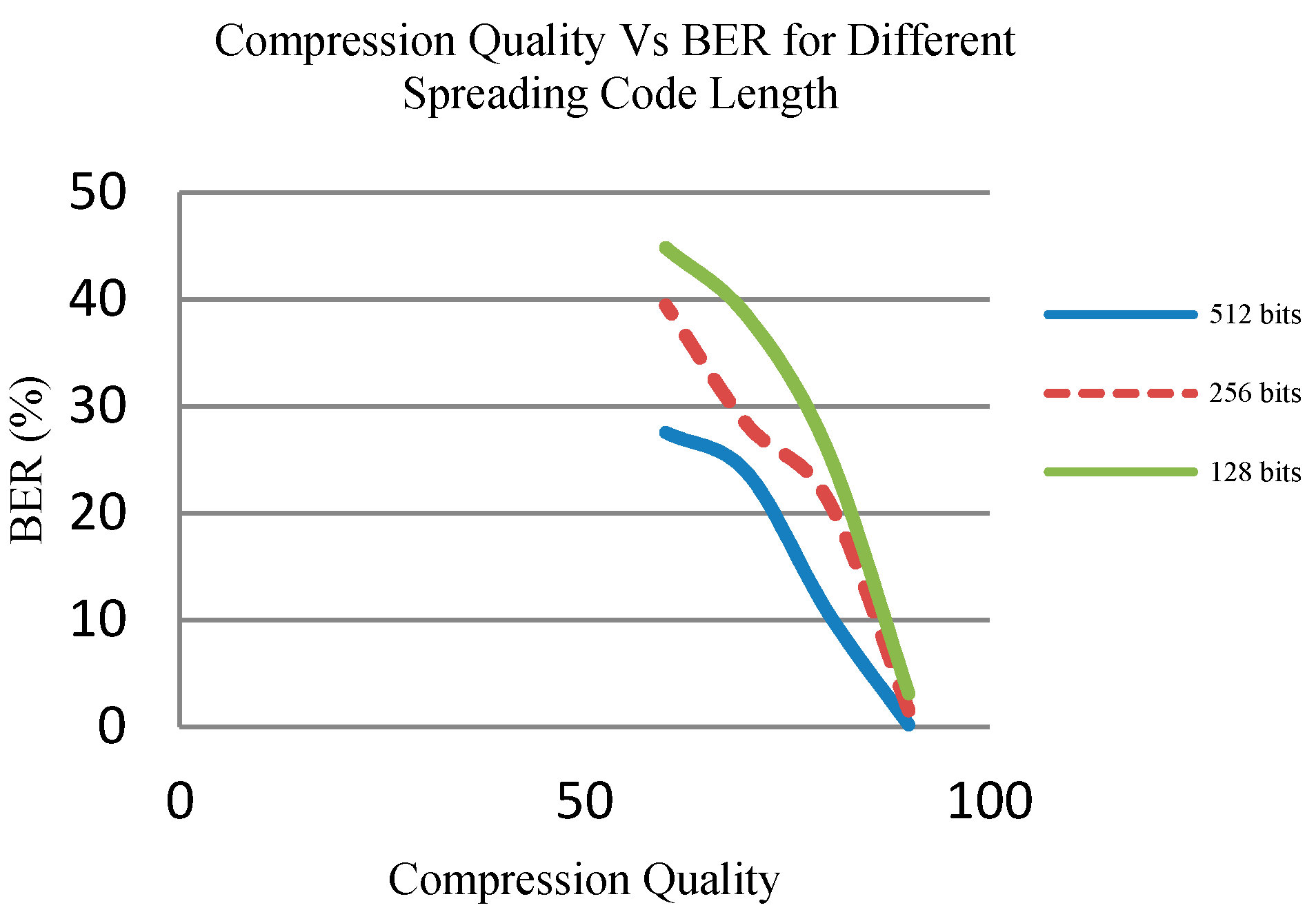
4.5. Effect of Spreading Code Length on Robustness
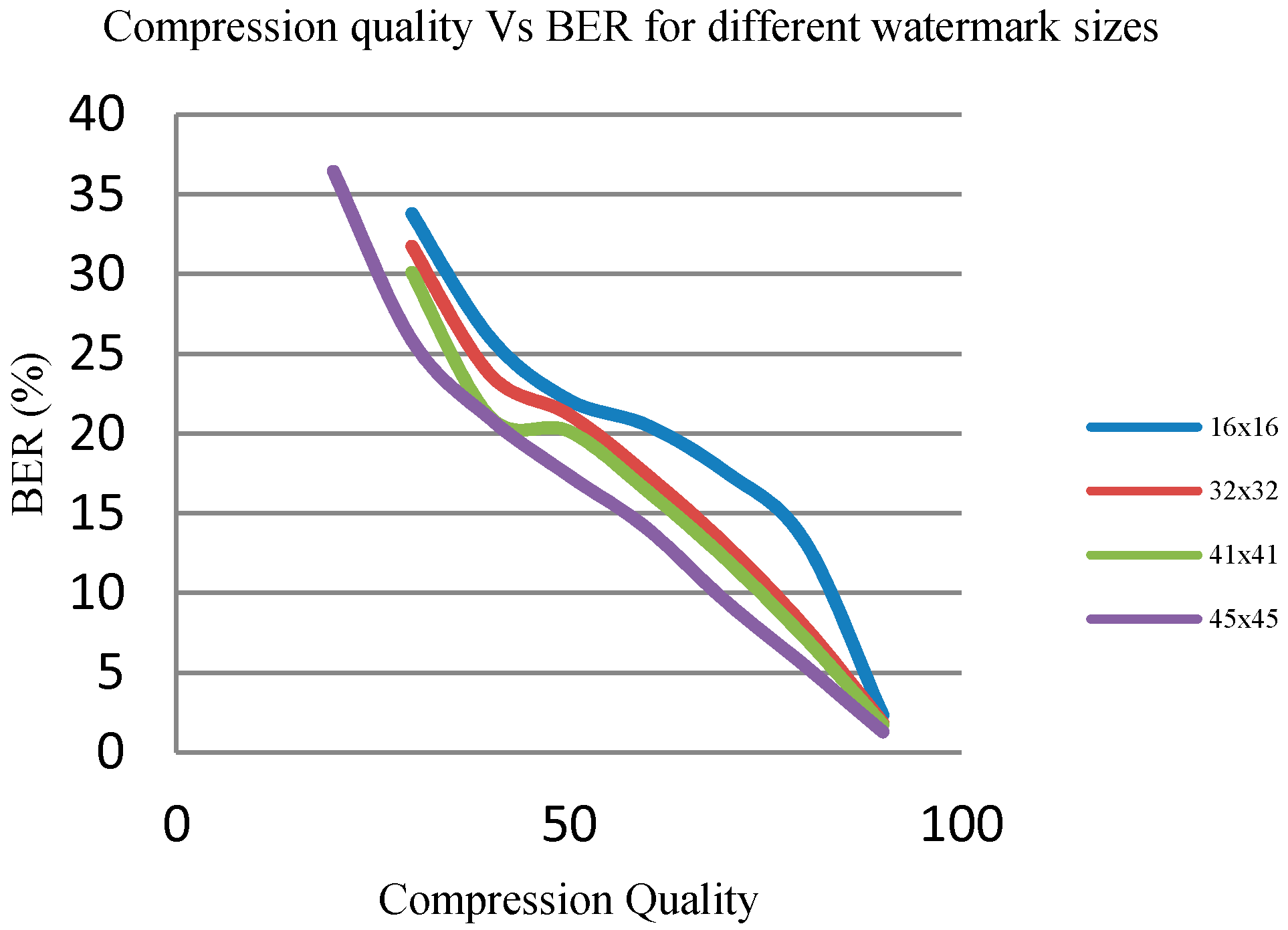
4.6. Effect of Number of Watermark Bits on Robustness
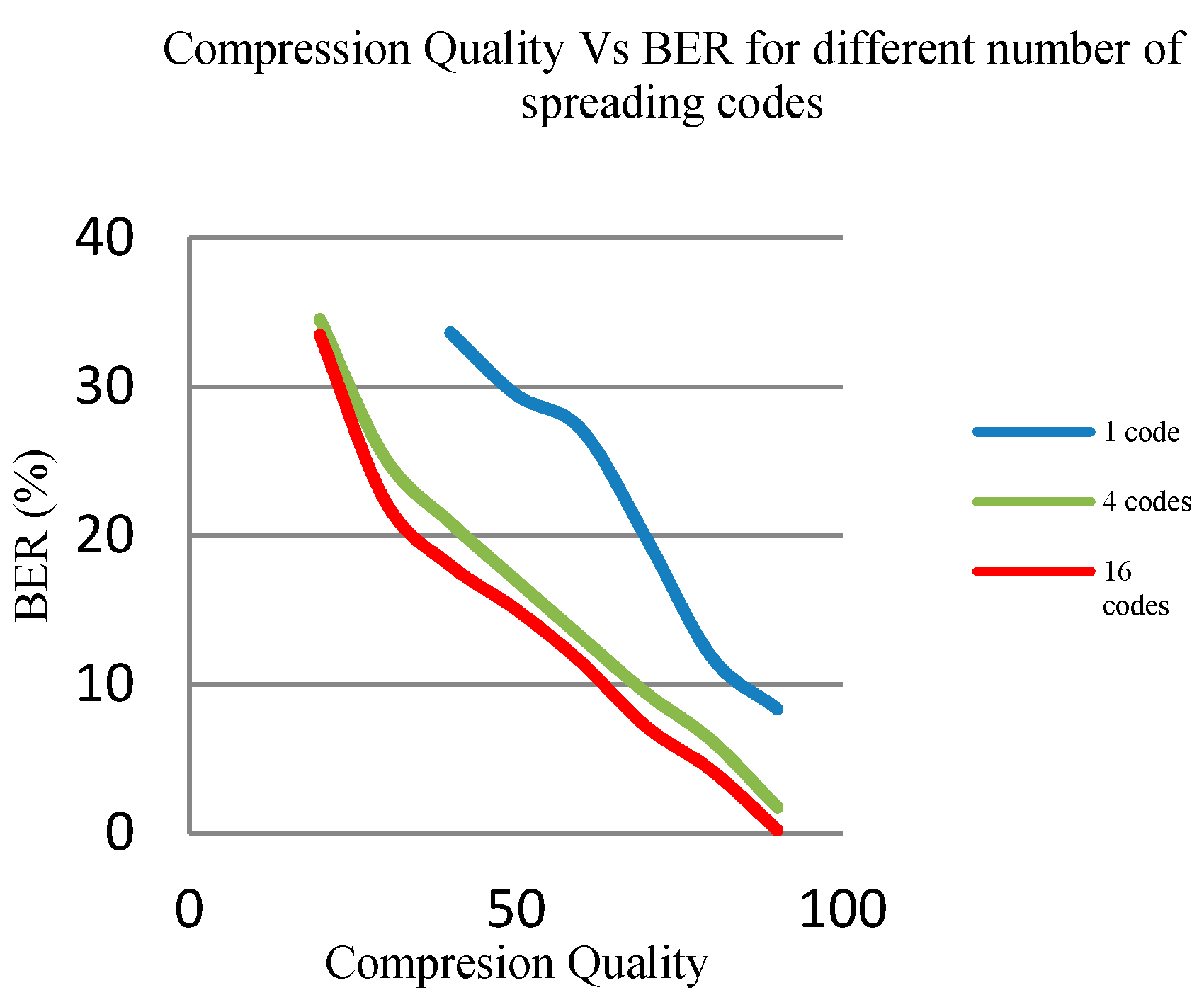
4.7. Effect of Number of Spreading Codes on Robustness
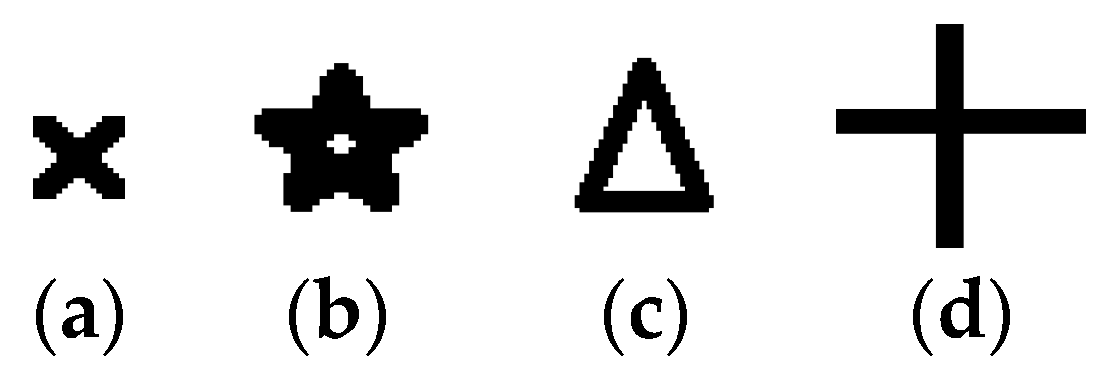
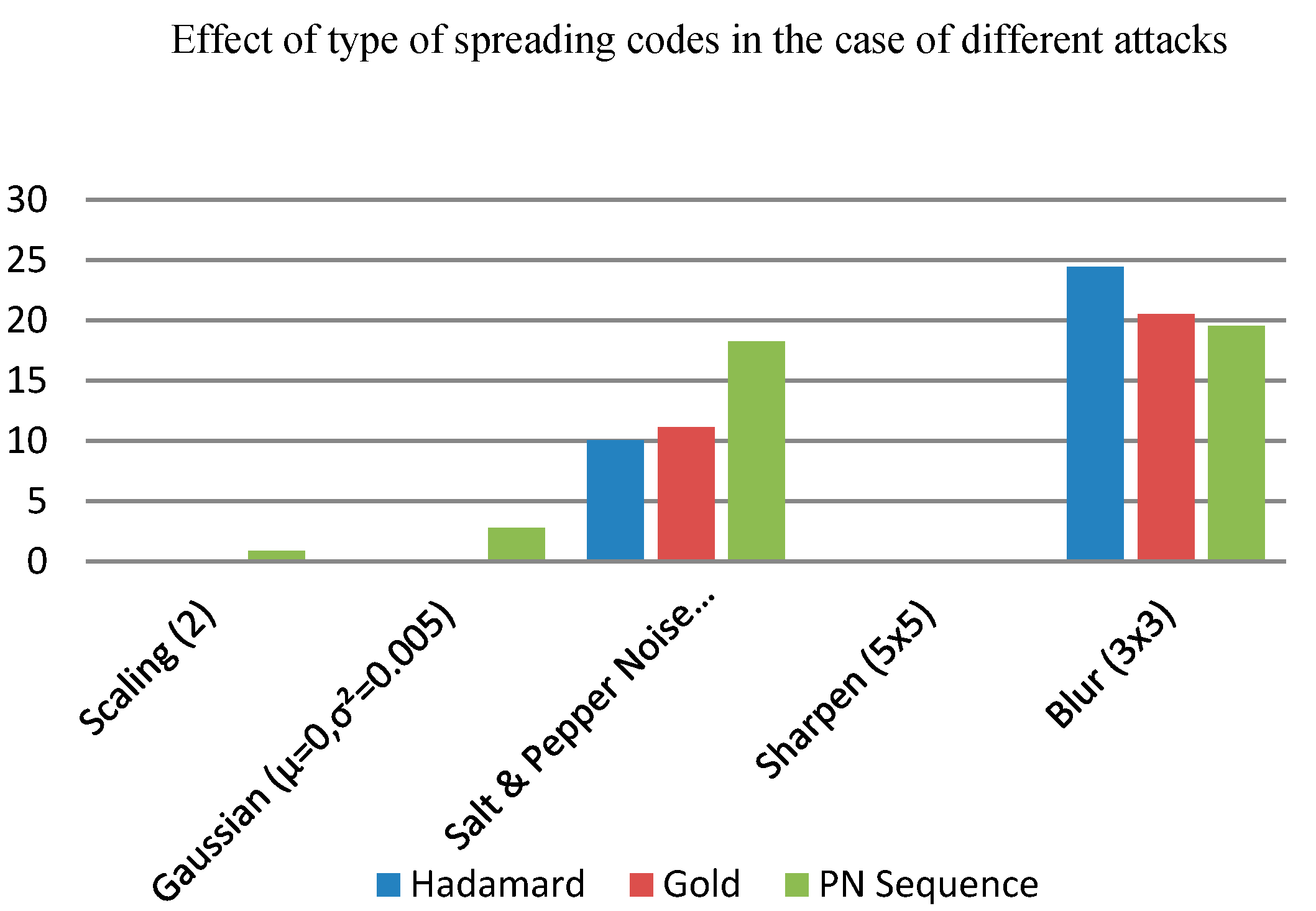
4.8. Effect of Type of Spreading Codes on Robustness
5. Conclusions
Author Contributions
Conflicts of Interest
References
- Vassaux, B.; Bas, P.; Chassery, J.M. A New CDMA Technique for Digital Image Watermarking. In Proceedings of the 2001 International Conference on Image Processing, Thessaloniki, Greece, 7–10 October 2001; Volume 3, pp. 983–986. [Google Scholar]
- Al-Haj, A.M. Advanced Techniques in Multimedia Watermarking: Image, Video and Audio Applications; Information Science Reference: Hershey, PA, USA, 2010. [Google Scholar]
- Cox, J.; Kilian, J.; Leighton, F.T.; Shamoon, T. Secure Spread Spectrum Watermarking for Multimedia. IEEE Trans. Image Process. 1997, 6, 1673–1687. [Google Scholar] [CrossRef] [PubMed]
- Samee, M.K.; Gotze, J. CDMA Based Reversible and Blind Watermarking Scheme for Images. Int. J. Future Comput. Commun. 2013, 2, 138. [Google Scholar] [CrossRef]
- Shrivastava, V.; Saini, L.K. A Survey of Digital Watermarking Techniques and its Applications. Int. J. Comput. Sci. Trends Technol. IJCST 2014, 2, 303–313. [Google Scholar]
- Bamatraf, A.; Ibrahim, R.; Najib, M. A New Digital Watermarking Algorithm Using Combination of Least Significant Bit (LSB) and Inverse Bit. J. Comput. 2011, 3, 1–8. [Google Scholar]
- Masoumi, M.; Rezaei, M.; Hamza, A.B. A blind spatio-temporal data hiding for video ownership verification in frequency domain. AEU-Int. J. Electron. Commun. 2015, 69, 1868–1879. [Google Scholar] [CrossRef]
- Patil, P.; Bormane, D.S. DWT Based Invisible Watermarking Technique for Digital Images. Int. J. Eng. Adv. Technol. IJEAT 2013, 2, 603–605. [Google Scholar]
- Vishwanatham, V.M.; Reddy, G.S.; Jagadeesh, P. A Hybrid Digital Watermarking Algorithm for Colour Images Based on DWT and DCT; Annals Computer Science Series: Mirton, Romania, 2012. [Google Scholar]
- Khan, M.I.; Sarkar, M.I.H. An Efficient Image Watermarking Scheme Using BFS Technique Based on Hadamard Transform. Smart Comput. Rev. 2013, 3, 298–308. [Google Scholar]
- Lee, L.T.; Pai, Y.T. DS-CDMA based Watermarking: A low power, high security algorithm for embedded systems. Int. J. Innov. Comput. Inf. Control 2010, 7, 5893–5908. [Google Scholar]
- Anju, R. Modified Algorithm for Digital Image Watermarking Using Combined DCT and DWT. Int. J. Inf. Comput. Technol. 2013, 3, 691–700. [Google Scholar]
- Garimella, A.; Satyanarayana, M.V.V.; Murugesh, P.S.; Niranjan, U.C. ASIC for Digital Color Image Watermarking. In Proceedings of the IEEE 11th Digital Signal Processing Workshop and IEEE Signal Processing Education Workshop, Taos Ski Valley, NM, USA, 1–4 August 2004; pp. 292–296. [Google Scholar]
- Chaturvedi, N. Comparison of Digital Image watermarking Methods DWT & DWT-DCT on the Basis of PSNR. Int. J. Innov. Res. Sci. Eng. Technol. 2012, 1, 147–153. [Google Scholar]
- Franklin, R.V.; GRS, M.; Santhi, V. Entropy based Robust Watermarking Scheme using Hadamard Transformation Technique. Int. J. Comput. Appl. 2011, 12, 14–21. [Google Scholar]
- Shen, J.; Tan, S.H.; Anthony, T.S.H. A Robust Digital Image-in-Image Watermarking Algorithm Using the Fast Hadamard Transform. In Proceedings of the 2003 International Symposium on Circuits and Systems, Bangkok, Thailand, 25–28 May 2003. [Google Scholar]
- Marjuni, A.; Logeswaran, R.; Ahmad Fauzi, M. F. An image watermarking scheme based on fast Walsh Hadamard transformation and discrete Cosine transformation. In Proceedings of the International Conference on Networking and Information Technology, Manila, Philippines, 11–12 June 2010; pp. 289–293. [Google Scholar]
- Shanthakumari, R.; Parvathavarthini, S. An Adapative Watermarking Process in Hadamard Transform. Int. J. Adv. Inf. Technol. 2014, 4, 1. [Google Scholar]
- Ishikawa, Y.; Uehira, K.; Yanaka, K. Practical evaluation of illumination watermarking technique using orthogonal transforms. J. Display Technol. 2010, 6, 351–358. [Google Scholar] [CrossRef]
- Maity, S.P.; Kundu, M.K. A Blind CDMA Image Watermarking Scheme in Wavelet Domain. In Proceedings of the IEEE International Conference on Image Processing-ICIP 2004, Singapore, 24–27 October 2004; Volume 4, pp. 2633–2636. [Google Scholar]
- Wah, W.H. Image Watermarking and Data Hiding Techniques. Ph.D. Thesis, Hong Kong University of Science and Technology, Hong Kong, China, August 2003. [Google Scholar]
- Abdallah, E.E.; Hamza, A.B.; Bhattacharya, P. Robust block based image watermarking scheme using fast Hadamard transformation and single value decomposition. In Proceedings of the 18th International Conference on Pattern Recognition, Hong Kong, China, 20–24 August 2006; Volume 3, pp. 673–676. [Google Scholar]
- Mwangi, E. A wavelet based image watermarking scheme with a CDMA/Hadamard embedding technique. In Proceedings of the 9th International Symposium on Signal Processing and Its Applications, Sharjah, UAE, 12–15 February 2007; pp. 1–4. [Google Scholar]


| Existing FWHT Algorithms and Similar DCT Algorithm | Time for Embedding and Decoding (Seconds) |
|---|---|
| Samee (2013) | 1.9 |
| S. Maity et al. (2012) | 3 |
| M.K. Kundu et al. (2011) | 7.5 |
| Anthony et al. (2003) | 3 |
| Proposed Algorithm | 0.665 |
| Attacks/Distortions (Level) | DCT Technique (Samee) | FWHT Technique |
|---|---|---|
| Original |  |  |
| Scaling (6 times) |  |  |
| Gaussian Noise (μ = 0, σ² = 0.005) |  |  |
| Gaussian Noise (μ = 0.01, σ² = 0.005) |  |  |
| Gaussian Noise (μ = 0, σ² = 0.05) |  |  |
| Salt & Pepper Noise (Density—0.01) |  |  |
| Salt & Pepper Noise (Density—0.1) |  |  |
| Sharpen (3 × 3) |  |  |
| Blur (2 × 2) |  |  |
| Median filtering (3 × 3) |  |  |
| Gaussian filtering (5 × 5) |  |  |
| Crop (50%) |  |  |
| Attacks (Level) | Length—512 | Length—256 | Length—128 |
|---|---|---|---|
| Original |  |  |  |
| Scaling (6) |  |  |  |
| Gaussian noise (μ = 0, σ2 = 0.05) |  |  |  |
| Gaussian noise (μ = 0, σ2 = 0.05) |  |  |  |
| Gaussian noise (μ = 0.01, σ2 = 0.005) |  |  |  |
| Salt and Pepper noise (Density = 0.001) |  |  |  |
| Salt and Pepper noise (Density = 0.1) |  |  |  |
| Sharpen (5 × 5) |  |  |  |
| Blur (3 × 3) |  |  |  |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kalarikkal Pullayikodi, S.; Tarhuni, N.; Ahmed, A.; Shiginah, F.B. Computationally Efficient Robust Color Image Watermarking Using Fast Walsh Hadamard Transform. J. Imaging 2017, 3, 46. https://doi.org/10.3390/jimaging3040046
Kalarikkal Pullayikodi S, Tarhuni N, Ahmed A, Shiginah FB. Computationally Efficient Robust Color Image Watermarking Using Fast Walsh Hadamard Transform. Journal of Imaging. 2017; 3(4):46. https://doi.org/10.3390/jimaging3040046
Chicago/Turabian StyleKalarikkal Pullayikodi, Suja, Naser Tarhuni, Afaq Ahmed, and Fahad Bait Shiginah. 2017. "Computationally Efficient Robust Color Image Watermarking Using Fast Walsh Hadamard Transform" Journal of Imaging 3, no. 4: 46. https://doi.org/10.3390/jimaging3040046






