Integrated Model of Image Protection Techniques
Abstract
:1. Introduction
2. Preliminaries
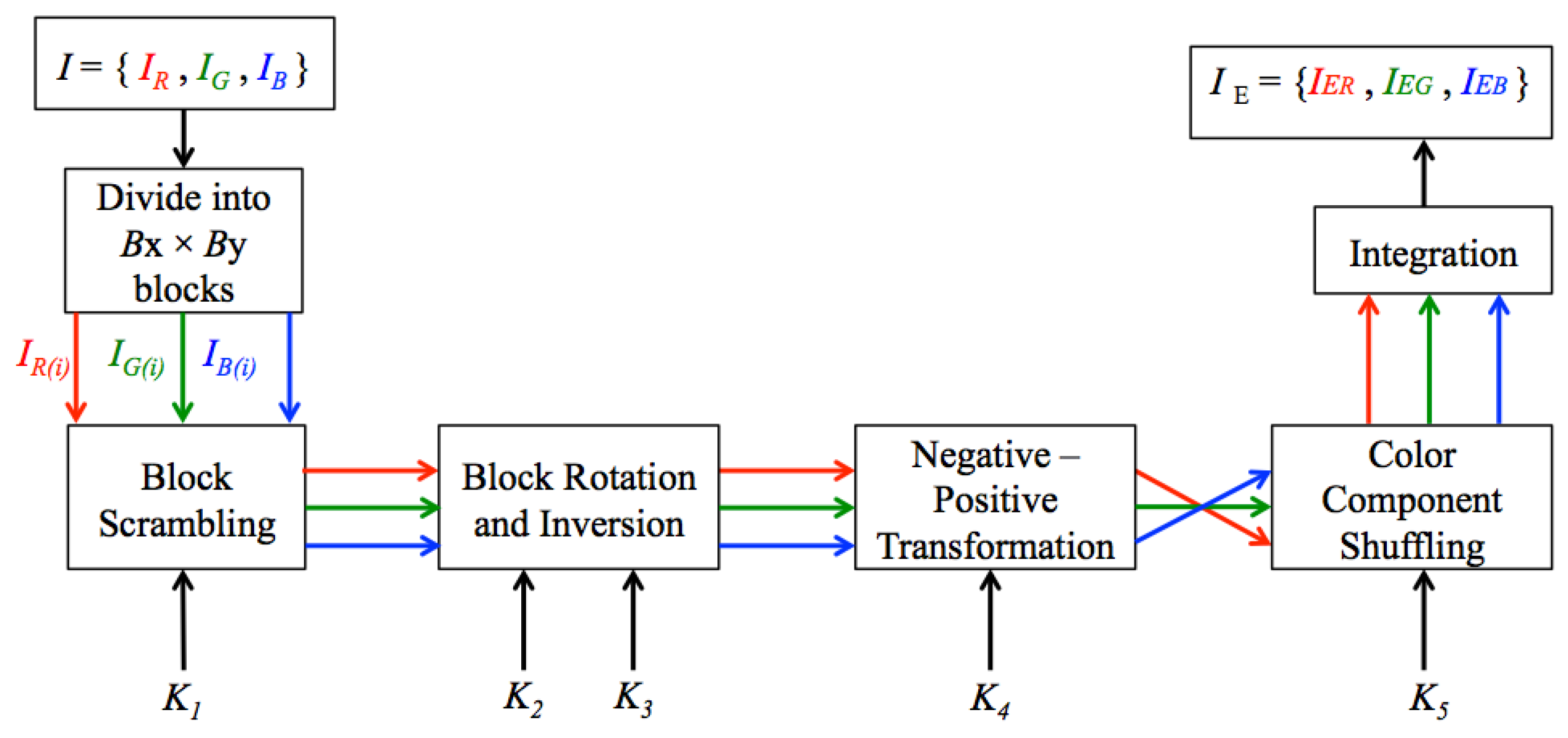
2.1. BPBE Scheme
- Step 1
- Divide each color component of a color image into multiple blocks with size.
- Step 2
- Permute the positions of the divided blocks randomly using a key .
- Step 3
- Rotate and invert each of the divided blocks using keys and .
- Step 4
- Apply a negative-positive transformation to the blocks using a key .
- Step 5
- Shuffle each color components in each block using a key .
2.2. RDH
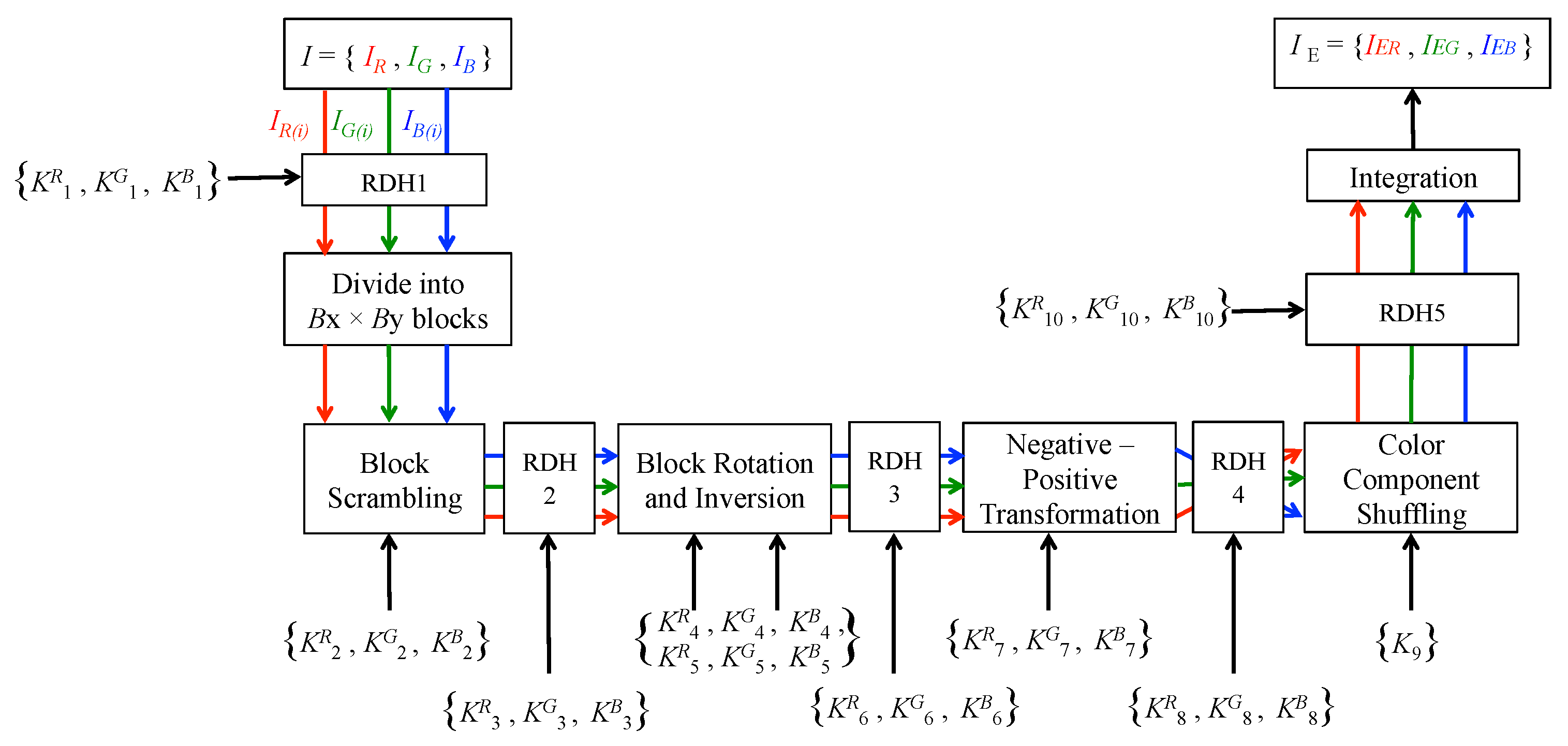
3. Proposed Scheme
3.1. Encryption and Embedding Process
- Step 1
- Apply RDH to an original image of pixels using keys , and .
- Step 2
- Divide each color component of an original image into multiple blocks with pixels.
- Step 3
- Permute the positions of the divided blocks randomly using keys , and .
- Step 4
- Apply RDH using keys , and .
- Step 5
- Rotate and invert each block randomly using keys , , , , and .
- Step 6
- Apply RDH using keys , and .
- Step 7
- Apply the negative-positive transformation for each block using keys , and .
- Step 8
- Apply RDH using keys , and .
- Step 9
- Shuffle the three color components, i.e., R, G, and B in each block by using a key .
- Step 10
- Apply RDH using keys , and .
- Step 11
- Generate the encrypted image by integrating all the transformed blocks.
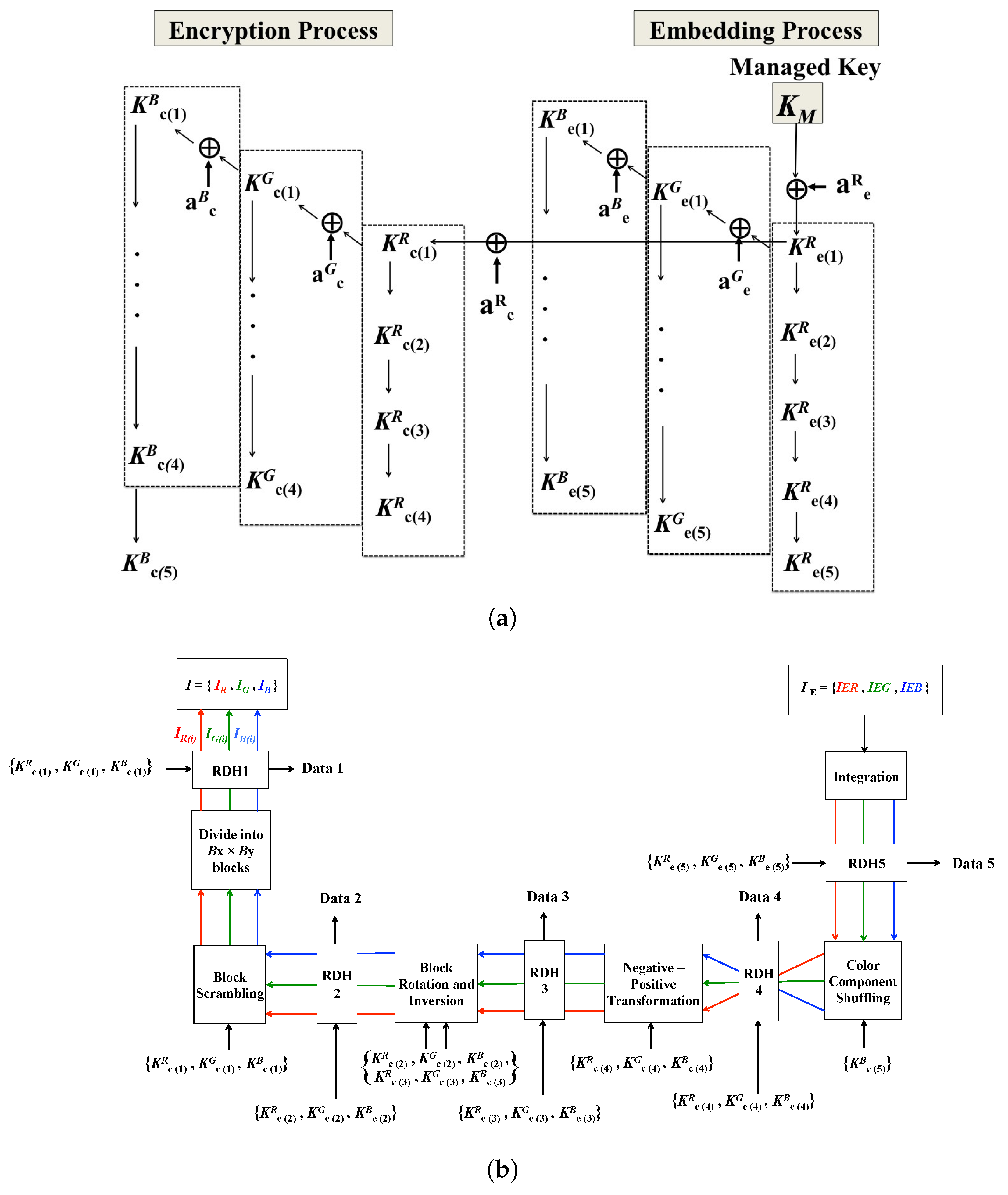
3.2. Key Derivation
3.3. Decryption and Extraction Process
3.3.1. Full Permission
3.3.2. Partial Permission
3.3.3. Decryption-Only Permission
4. Experimental Results and Analysis
4.1. Key Space
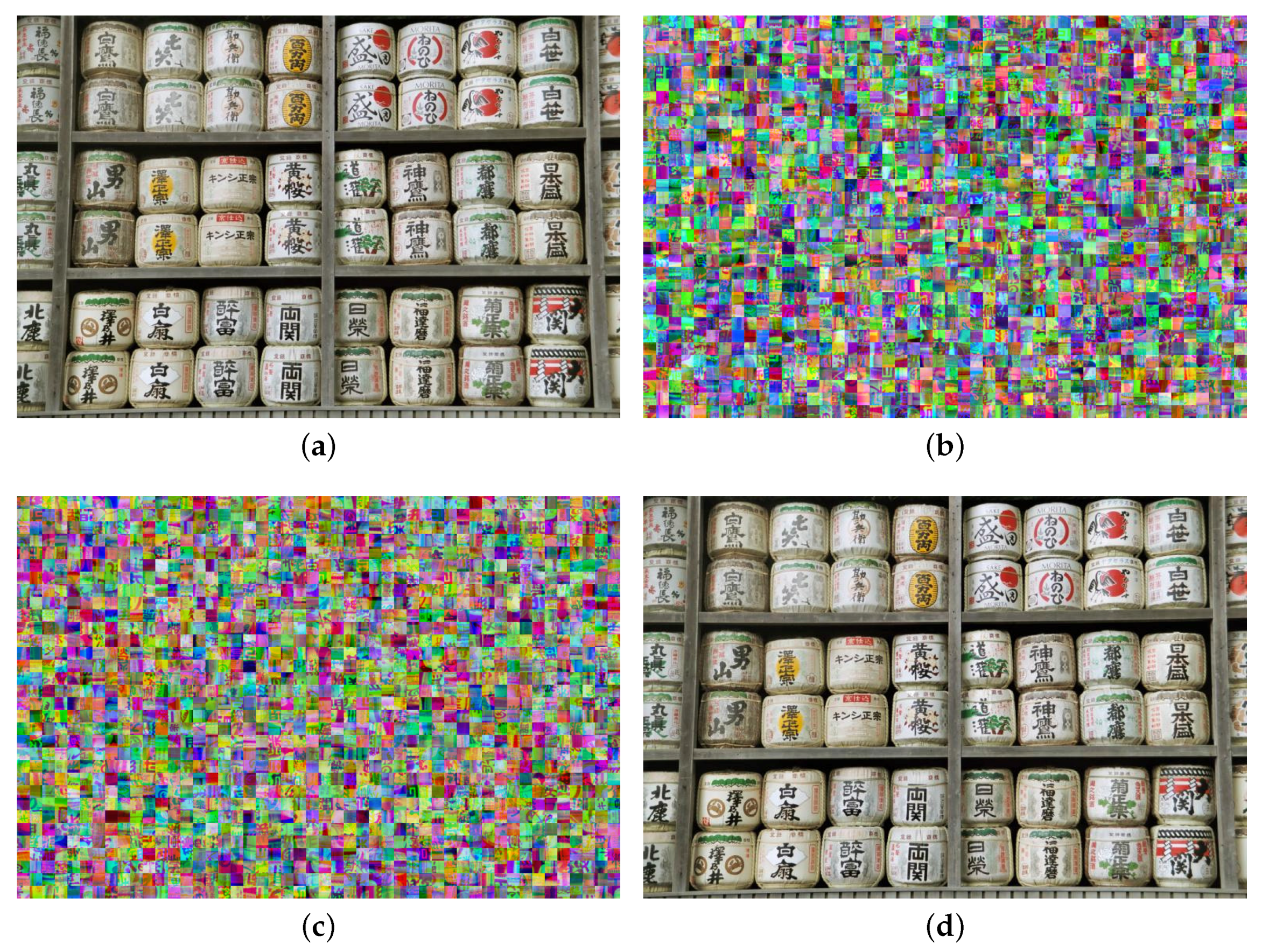
4.2. Resilience Against Jigsaw Puzzle Solvers
4.3. Compression Efficiency
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Cox, I.J.; Kilian, J.; Leighton, F.T.; Shamoon, T. Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 1997, 6, 1673–1687. [Google Scholar] [CrossRef] [PubMed]
- Tirkel, A.Z.; Osborne, C.F.; Schyndel, R.G. Image watermarking-a spread spectrum application. In Proceedings of the IEEE 4th International Symposium on Spread Spectrum Techniques and Applications, Mainz, Germany, 25 September 1996; Volume 2, pp. 785–789. [Google Scholar]
- Yeung, M.M.; Mintzer, F.C. Invisible watermarking for image verification. Electron. Imaging 1998, 7, 578–591. [Google Scholar] [CrossRef]
- Golijan, M.; Fridrich, J.J.; Du, R. Distortion-free data embedding. In Proceedings of the International Workshop on Information Hiding, Pittsburgh, PA, USA, 25–27 April 2001; pp. 27–41. [Google Scholar]
- Xuan, G.; Zhu, J.; Chen, J.; Shi, Y.Q.; Ni, Z.; Su, W. Distortionless data hiding based on integer wavelet transform. IEEE Electron. Lett. 2002, 38, 1646–1684. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Thodi, D.M.; Rodriguez, J.J. Expansion embedding techniques for reversible watermarking. IEEE Trans. Image Process. 2007, 16, 721–730. [Google Scholar] [CrossRef] [PubMed]
- Wu, H.T.; Dugelay, J.L.; Shi, Y.Q. Reversible image data hiding with contrast enhancement. IEEE Signal Process. Lett. 2015, 22, 81–85. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Imaizumi, S.; Ogasawara, T.; Kiya, H. Block-Permutation-Based-Encryption Scheme with Enhanced Color Scrambling. In Proceedings of the 20th Scandinavian Conference on Image Analysis, Tromsø, Norway, 12–14 June 2017; Volume 10269, pp. 562–573. [Google Scholar]
- Kurihara, K.; Imaizumi, S.; Shiota, S.; Kiya, H. An Encryption-then-Compression System for Lossless Image Compression Standards. IEICE Trans. Inf. Syst. 2017, E100-D, 52–56. [Google Scholar] [CrossRef]
- Watanabe, O.; Uchida, A.; Fukuhara, T.; Kiya, H. An Encryption-then-Compression System for JPEG 2000 Standard. In Proceedings of the 2015 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brisbane, Australia, 19–24 April 2015. [Google Scholar]
- Kurihara, K.; Kikuchi, M.; Imaizumi, S.; Shiota, S.; Kiya, H. An Encryption-then-Compression System for JPEG/Motion JPEG Standard. IEICE Trans. Fundam. 2015, E98-A, 2238–2245. [Google Scholar] [CrossRef]
- Zhou, J.; Liu, X.; Au, O.C.; Tang, Y.Y. Designing an efficient image encryption-then-compression system via prediction error clustering and random permutation. IEEE Trans. Inf. Forensics Secur. 2014, 9, 39–50. [Google Scholar] [CrossRef]
- Erkin, Z.; Piva, A.; Katzenbeisser, S.; Lagendijk, R.L.; Shokrollahi, J.; Neven, G.; Barni, M. Protection and retrieval of encrypted multimedia content: When cryptography meets signal processing. EURASIP J. Inf. Secur. 2007, 2007. [Google Scholar] [CrossRef]
- Liu, W.; Zeng, W.; Dong, L.; Yao, Q. Efficient compression of encrypted grayscale images. IEEE Trans. Image Process. 2010, 19, 1097–1102. [Google Scholar] [CrossRef] [PubMed]
- Johnson, M.; Ishwar, P.; Prabhakaran, V.; Schnoberg, D.; Ramchandran, K. On compressing encrypted data. IEEE Trans. Signal Process. 2004, 52, 2992–3006. [Google Scholar] [CrossRef]
- Hu, R.; Li, X.; Yang, B. A new lossy compression scheme for encrypted gray-scale images. In Proceedings of the 2014 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Florence, Italy, 4–9 May 2014; pp. 7387–7390. [Google Scholar]
- Yi, S.; Zhou, Y. Adaptive code embedding for reversible data hiding in encrypted images. In Proceedings of the 2017 IEEE International Conference on Image Processing (ICIP), Beijing, China, 17–20 September 2017; pp. 4322–4326. [Google Scholar]
- Chuman, T.; Kurihara, K.; Kiya, H. Security evaluation for block scrambling-based ETC systems against extended jigsaw puzzle solver attacks. In Proceedings of the 2017 IEEE International Conference on Multimedia and Expo (ICME), Hong Kong, China, 10–14 July 2017. [Google Scholar]
- International Organization for Standardization. ISO/ICE 14495-1:1999 Information Technology—Lossless and Nearlossless Compression of Continuous-Tone Still Images Baseline; International Organization for Standardization: Geneva, Switzerland, 1999. [Google Scholar]
- Content-Based Image Retrieval Database. Available online: http://imagedatabase.cs.washington.edu/groundtruth (accessed on 6 September 2017).
- Imaizumi, S.; Fujiyoshi, M.; Kiya, H. An efficient access control method for composite multimedia content. IEICE Electron. Express 2010, 7, 1534–1538. [Google Scholar] [CrossRef]
- Gallagher, A. Jigsaw puzzles with pieces of unknown orientation. In Proceedings of the 2012 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Providence, RI, USA, 16–21 June 2012; pp. 382–389. [Google Scholar]
- Cho, T.; Avidan, S.; Freeman, W. A probabilistic image jigsaw puzzle solvers. In Proceedings of the 2010 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), San Francisco, CA, USA, 13–18 June 2010; pp. 183–190. [Google Scholar]
- SIPI Database. Available online: http://sipi.usc.edu/database (accessed on 6 September 2017).

| Level | Embedding Capacity (bits) | |
|---|---|---|
| Single Embedding | Double Embedding | |
| Data 1 | 18,709 | 37,233 |
| Data 2 | 18,524 | 36,866 |
| Data 3 | 18,476 | 36,090 |
| Data 4 | 16,827 | 31,934 |
| Data 5 | 15,297 | 27,396 |
| Total | 87,833 | 169,519 |
| Image | Single Embedding | |
|---|---|---|
| (768 × 512 pixels) | Total Embedding Capacity (bits) | PSNR |
| Japan Image22 | 41,576 | 38.34 |
| Japan Image27 | 78,682 | 43.93 (max) |
| Japan Image32 | 87,833 | 40.41 |
| Australia Image01 | 75,360 | 43.80 |
| Australia Image03 | 86,720 | 41.69 |
| Australia Image05 | 41,965 | 38.75 |
| Indonesia Image01 | 285,821 | 37.91 |
| Indonesia Image35 | 240,071 | 37.42 (min) |
| Iran Image13 | 525,427 (max) | 38.29 |
| Iran Image49 | 132,792 | 38.41 |
| (512 × 768 pixels) | Total Embedding Capacity (bits) | PSNR |
| Japan Image26 | 38,418 (min) | 38.81 |
| Japan Image31 | 55,594 | 39.61 |
| Australia Image02 | 41,212 | 42.77 |
| Australia Image06 | 65,859 | 40.55 |
| Indonesia Image20 | 89,424 | 40.98 |
| Indonesia Image26 | 112,831 | 39.69 |
| Iran Image10 | 218,532 | 42.29 |
| Iran Image15 | 62,670 | 41.94 |
| Image (768 × 512 pixels) | Double Embedding | |
|---|---|---|
| Total Embedding Capacity (bits) | PSNR | |
| Japan Image01 | 131,529 | 37.44 |
| Japan Image13 | 85,156 | 34.64 |
| Japan Image32 | 169,519 | 34.65 |
| Japan Image17 | 165,832 | 35.55 |
| Japan Image15 | 88,180 | 32.93 |
| Japan Image22 | 79,477 | 32.43 |
| Japan Image27 | 142,136 | 39.68 |
| Japan Image08 | 90,016 | 34.53 |
| Japan Image20 | 101,275 | 35.66 |
| Japan Image02 | 111,144 | 37.65 |
| Component | BPBE Scheme | |
|---|---|---|
| Identical | Independent | |
| (Avg) | 0.102 | 0.002 |
| (Avg) | 0.152 | 0.006 |
| (Avg) | 0.197 | 0.008 |
| Image | Bitrate (bpp) |
|---|---|
| Original | 13.10 |
| Proposed scheme (independent) | 13.73 |
| Proposed scheme (identical) | 13.70 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aryal, A.; Imaizumi, S.; Horiuchi, T.; Kiya, H. Integrated Model of Image Protection Techniques. J. Imaging 2018, 4, 1. https://doi.org/10.3390/jimaging4010001
Aryal A, Imaizumi S, Horiuchi T, Kiya H. Integrated Model of Image Protection Techniques. Journal of Imaging. 2018; 4(1):1. https://doi.org/10.3390/jimaging4010001
Chicago/Turabian StyleAryal, Anu, Shoko Imaizumi, Takahiko Horiuchi, and Hitoshi Kiya. 2018. "Integrated Model of Image Protection Techniques" Journal of Imaging 4, no. 1: 1. https://doi.org/10.3390/jimaging4010001





