Design of a CANFD to SOME/IP Gateway Considering Security for In-Vehicle Networks
Abstract
:1. Introduction
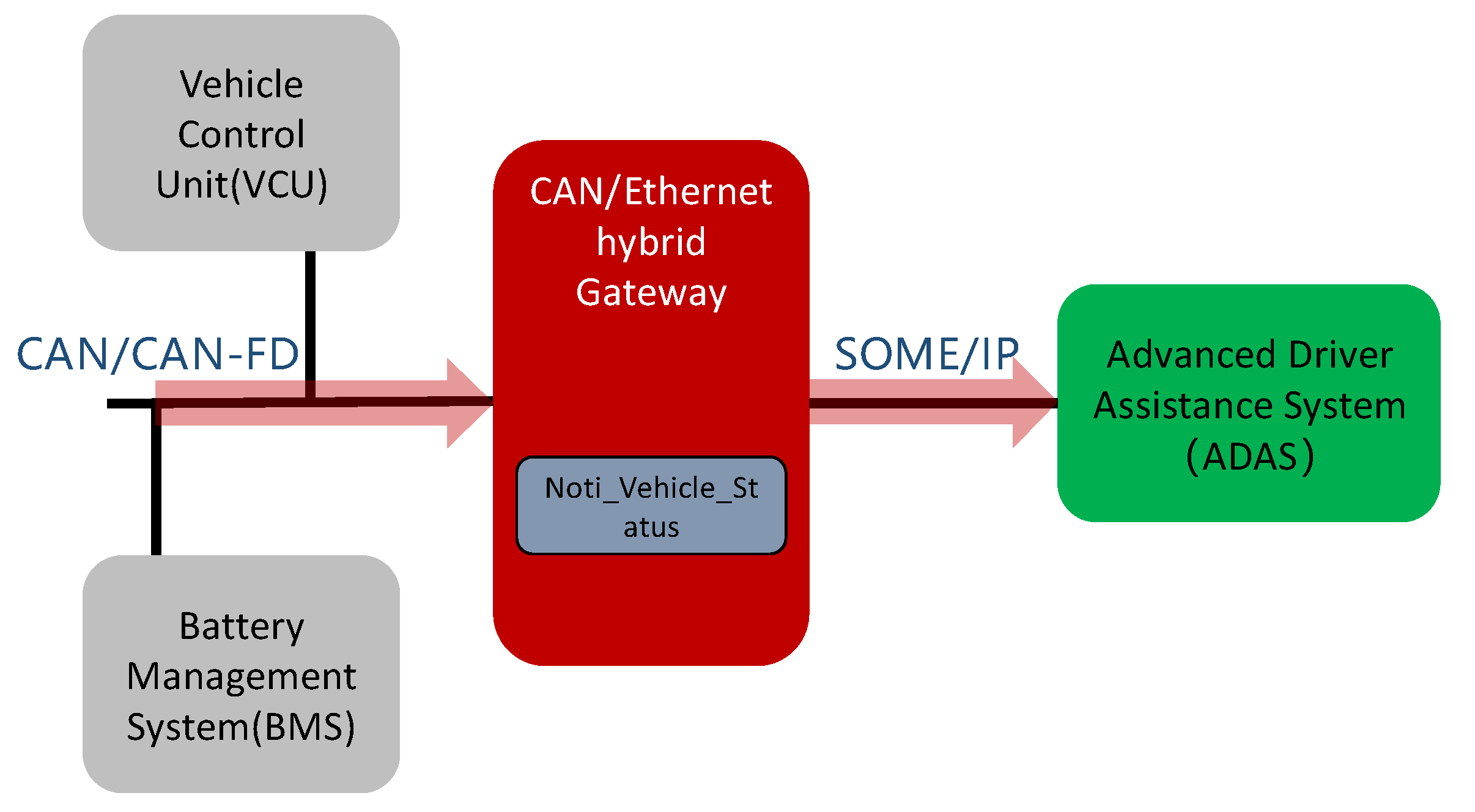
- The proposal of an in-vehicle gateway system for CAN/CANFD to SOME/IP protocol conversion. This system is composed of five modules, including a SOME/IP receive module, a CAN receive module, a protocol transform module, a security module, and a SOME/IP send module. The execution logic flow is as follows: first, the service request (request message) from the domain controller (e.g., ADAS) is received through the SOME/IP protocol. Then, the information required by the domain controller is obtained from the CAN bus through the CAN/CANFD protocol and converted into the SOME/IP message format. Finally, the SOME/IP protocol is used to return data (response message) to the domain controller;
- Providing three strengths of cyber security protection mechanisms in the process of the gateway system protocol conversion. The application developers can tune them according to security protection strength requirements to achieve the best compromise between security and performance. Among them, Scheme 1 is implemented based on the MAC algorithm to provide integrity protection for the routing process. It can resist frame forgery and frame tampering attacks. Scheme 2 is implemented based on the AEAD algorithm to provide integrity and confidentiality protection for the routing process. It can resist frame forgery, frame tampering, and frame sniffing attacks. However, Scheme 3 is not provided with cyber security protection in order to obtain a higher routing performance;
- Building the experimental platform, including the gateway, ADAS, and CAN/CANFD network and evaluating the protocol conversion and cyber security protection performance of the designed gateway. The experiment is carried out with the CAN/CANFD protocol type, CAN/CANFD payload length, and safety mechanism type as variables. At the same time, the experiment conducts a detailed evaluation of the gateway performance based on four indicators: CPU usage, memory usage, latency, and the percentage of the effective load of the SOME/IP message sent by the gateway program.
2. Related Work
2.1. Vehicle Routing
2.2. Authentication Techniques for In-Vehicle Networks
3. Preliminary Background
3.1. CANFD
3.2. Automotive Ethernet
3.3. SOME/IP
3.4. MAC and AE/AEAD
4. Design of a CAN/CANFD to SOME/IP Gateway
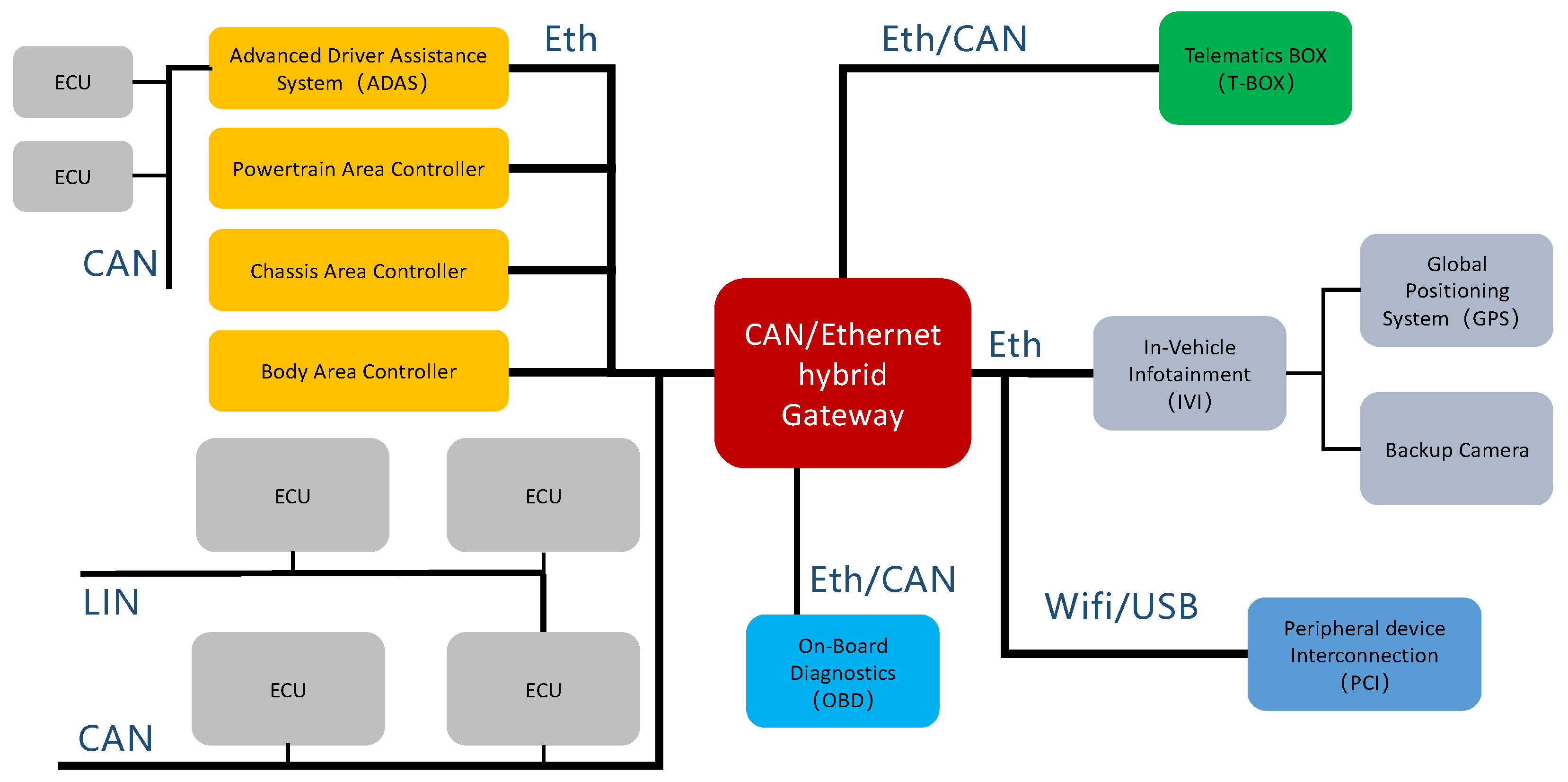
4.1. Application Scenarios
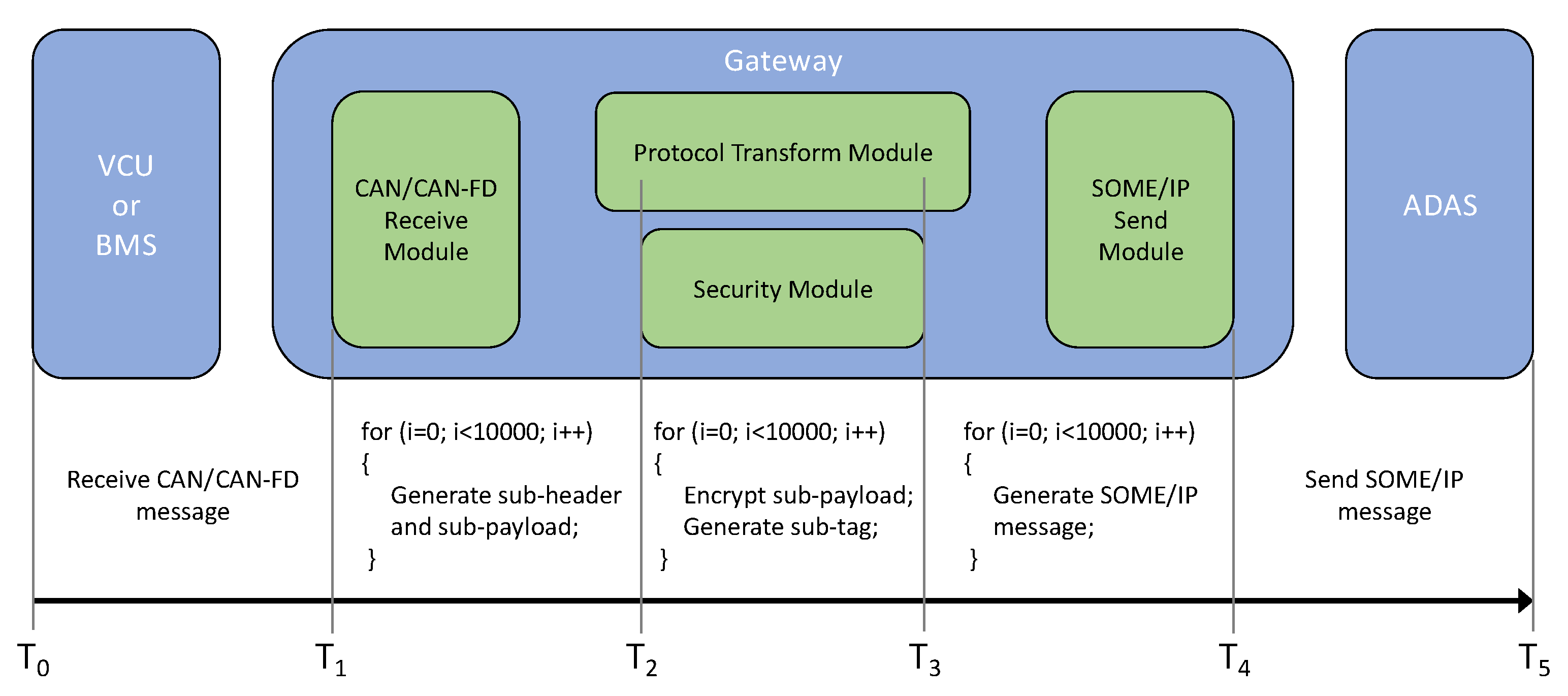
4.2. Gateway Algorithm and System Architecture
- Message 1:
- Message 2:
- Message 3:
4.3. Security Mechanism
- Scheme 1 uses the MAC algorithm to calculate the message authentication code of the sub-header and sub-payload as the sub-tags to provide integrity protection for the routing process and resist frame forgery and frame tampering attacks;
- Scheme 2 uses the AEAD algorithm to calculate the message authentication code of the sub-header and sub-payload as the sub-tag and encrypts the sub-payload, which provides integrity and confidentiality protection for the routing process and resists frame forgery and frame tampering, and frame sniffing attacks;
- Scheme 3 does not use security protection.
5. Implementation and Evaluation of the Designed Gateway
5.1. Hardware Environment
- Gateway
- ADAS
- CAN/CANFD Bus
5.2. Experiment Settings
5.3. Performance Evaluation
5.4. Consideration
6. Conclusions
- The consumption of system resources in the designed gateway system can be afforded conveniently by devices running the Linux operating system. In the experimental groups, the CPU usage of the gateway is less than 5% in most working conditions, and the RAM usage is less than 20 MB;
- The gateway system designed just increases a few latencies to the data transmission process while completing protocol conversion and data transmission security protection. In the experimental groups, the latency of the process in the gateway system protocol conversion is less than 100 us under most conditions;
- The proportion of latency is less than 25% for the security schemes of the gateway system designed. Such an overhead is worthwhile since these security schemes provide integrity protection and confidentiality protection for the routing process;
- We recommend the use of the AES128-CMAC algorithm in scenarios that only need integrity protection. The performance obtained using this algorithm is significantly better than that obtained when using the SHA256-HMAC algorithm based on the AES acceleration encryption instruction set. We recommend the use of the Chacha20-poly1305 algorithm in scenarios that require both integrity and confidentiality protection.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Mundhenk, P. Security for Automotive Electrical/Electronic (E/E) Architectures. Ph.D. Thesis, Nanyang Technological University, Singapore, 2017. [Google Scholar]
- Andreas, L. Trends of Future E/E-Architectures. Available online: https://www.gsaglobal.org/wp-content/uploads/2019/05/Trends-of-Future-EE-Architectures.pdf (accessed on 6 October 2021).
- Zhu, H.; Zhou, W.; Li, Z.; Li, L.; Huang, T. Requirements-Driven Automotive Electrical/Electronic Architecture: A Survey and Prospective Trends. IEEE Access 2021, 9, 100096–100112. [Google Scholar] [CrossRef]
- Lee, T.-Y.; Lin, I.-A.; Liao, R.-H. Design of a Flexray/Ethernet Gateway and Security Mechanism for in-Vehicle Networks. Sensors 2020, 20, 641. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lee, T.; Liao, R.; Lin, I.; Tsai, J. A Novel Flexray/Ethernet Gateway for in-Vehicle Networks. In Proceedings of the 2019 8th International Conference on Innovation, Communication and Engineering (ICICE), Zhengzhou, China, 25–30 October 2019. [Google Scholar]
- Park, J.S.; Kim, D.H.; Suh, I.H. Design and Implementation of Security Function According to Routing Method in Automotive Gateway. Int. J. Automot. Technol. 2021, 22, 19–25. [Google Scholar] [CrossRef]
- Park, J.S.; Heurtefeux, K.; Eom, S.; Kim, D. Routing Methods Considering Security and Real-Time of Vehicle Gateway System. SAE Tech. Pap. 2020, 1, 1294. [Google Scholar]
- Kim, J.H.; Seo, S.; Hai, N.; Cheon, B.M.; Lee, Y.S.; Jeon, J.W. Gateway Framework for in-Vehicle Networks Based on Can, Flexray, and Ethernet. IEEE Trans. Veh. Technol. 2015, 64, 4472–4486. [Google Scholar] [CrossRef]
- Shreejith, S.; Mundhenk, P.; Ettner, A.; Fahmy, S.A.; Steinhorst, S.; Lukasiewycz, M.; Chakraborty, S. Vega: A High Performance Vehicular Ethernet Gateway on Hybrid Fpga. IEEE Trans. Comput. 2017, 66, 1790–1803. [Google Scholar] [CrossRef] [Green Version]
- Lee, Y.S.; Kim, J.H.; Jeon, J.W. Flexray and Ethernet Avb Synchronization for High Qos Automotive Gateway. IEEE Trans. Veh. Technol. 2017, 66, 5737–5751. [Google Scholar] [CrossRef]
- Yadav, K.; Mittal, V.; Bhat, V. Novel Implementation of a Configurable Gateway between Can and Ethernet Protocol for in-Vehicle Networks. In Proceedings of the 2020 First IEEE International Conference on Measurement, Instrumentation, Control and Automation (ICMICA), Kurukshetra, India, 24–26 June 2020. [Google Scholar]
- Jo, C.; Park, J.; Jeon, J. Multi-Core Gateway Architecture and Scheduling Algorithm for High-Performance Gateway Implementation. In Proceedings of the 2020 IEEE International Conference on Consumer Electronics—Asia (ICCE-Asia), Seoul, Korea, 1–3 November 2020. [Google Scholar]
- Aliwa, E.; Rana, O.; Perera, C.; Burnap, P. Cyberattacks and Countermeasures for in-Vehicle Networks. ACM Comput. Surv. 2021, 54, 21. [Google Scholar] [CrossRef]
- Alnasser, A.; Sun, H.; Jiang, J. Cyber Security Challenges and Solutions for V2x Communications: A Survey. Comput. Netw. 2019, 151, 52–67. [Google Scholar] [CrossRef] [Green Version]
- Loukas, G.; Karapistoli, E.; Panaousis, E.; Sarigiannidis, P.; Bezemskij, A.; Vuong, T. A Taxonomy and Survey of Cyber-Physical Intrusion Detection Approaches for Vehicles. Ad Hoc Netw. 2019, 84, 124–147. [Google Scholar] [CrossRef]
- Puhm, A.; Roessler, P.; Wimmer, M.; Swierczek, R.; Balog, P. Development of a Flexible Gateway Platform for Automotive Networks. In Proceedings of the 2008 IEEE International Conference on Emerging Technologies and Factory Automation, Seoul, Korea, 15–18 September 2008. [Google Scholar]
- Bella, G.; Biondi, P.; Costantino, G.; Matteucci, I. Toucan: A Protocol to Secure Controller Area Network. In Proceedings of the ACM Workshop on Automotive Cybersecurity, Richardson, TX, USA, 27 March 2019; pp. 3–8. [Google Scholar]
- Agrawal, M.; Huang, T.; Zhou, J.; Chang, D. Can-Fd-Sec: Improving Security of Can-Fd Protocol. In Security and Safety Interplay of Intelligent Software Systems; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Carel, G.; Isshiki, R.; Kusaka, T.; Nogami, Y.; Araki, S. Design of a Message Authentication Protocol for Can Fd Based on Chaskey Lightweight Mac. In Proceedings of the 2018 Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan, 27–30 November 2018. [Google Scholar]
- Groza, B.; Murvay, S.; van Herrewege, A.; Verbauwhede, I. Libra-Can: Lightweight Broadcast Authentication for Controller Area Networks. ACM Trans. Embed. Comput. Syst. 2017, 16, 90. [Google Scholar] [CrossRef] [Green Version]
- Kang, K.; Baek, Y.; Lee, S.; Son, S.H. An Attack-Resilient Source Authentication Protocol in Controller Area Network. In Proceedings of the 2017 ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS), Beijing, China, 18–19 May 2017. [Google Scholar]
- Fassak, S.; El Idrissi, Y.; Zahid, N.; Jedra, M. A Secure Protocol for Session Keys Establishment between Ecus in the Can Bus. In Proceedings of the 2017 International Conference on Wireless Networks and Mobile Communications (WINCOM), Rabat, Morocco, 1–4 November 2017. [Google Scholar]
- Radu, A.-I.; Garcia, F.D. Leia: A Lightweight Authentication Protocol for Can. In 21st European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2016. [Google Scholar]
- Iorio, M.; Reineri, M.; Risso, F.; Sisto, R.; Valenza, F. Securing Some/IP for in-Vehicle Service Protection. IEEE Trans. Veh. Technol. 2020, 69, 13450–13466. [Google Scholar] [CrossRef]
- Iorio, M.; Buttiglieri, A.; Reineri, M.; Risso, F.; Sisto, R.; Valenza, F. Protecting in-Vehicle Services: Security-Enabled Some/IP Middleware. IEEE Veh. Technol. Mag. 2020, 15, 77–85. [Google Scholar] [CrossRef]
- ISO. Road Vehicles-Controller Area Network (Can)—Part 1: Data Link Layer and Physical Signalling; ISO 11898-1:2015; ISO: Vernier, Geneva, Switzerland, 2015. [Google Scholar]
- ISO; IEC; IEEE. ISO/EC/IEEE International Standard—Part 3: Standard for Ethernet—Amendment 1: Physical Layer Specifications and Management Parameters for 100 Mb/S Operation over a Single Balanced Twisted Pair Cable (100base-T1); ISO/IEC/IEEE 8802-3:2017/Amd 1:2017(E); ISO: Vernier, Geneva, Switzerland, 2018. [Google Scholar]
- Lim, H.; Herrscher, D.; Völker, L.; Waltl, M.J. IEEE 802.1 as Time Synchronization in a Switched Ethernet Based in-Car Network. In Proceedings of the 2011 IEEE Vehicular Networking Conference (VNC), Amsterdam, The Netherlands, 14–16 November 2011. [Google Scholar]
- IEEE. IEEE Standard for Local and Metropolitan Area Networks—Virtual Bridged Local Area Networks Amendment 12: Forwarding and Queuing Enhancements for Time-Sensitive Streams; IEEE Std 802.1Qav-2009 (Amendment to IEEE Std 802.1Q-2005); IEEE: Piscataway Township, NJ, USA, 2010. [Google Scholar]
- IEEE. IEEE Standard for Local and Metropolitan Area Networks—Virtual Bridged Local Area Networks Amendment 14: Stream Reservation Protocol (Srp); IEEE Std 802.1Qat-2010 (Revision of IEEE Std 802.1Q-2005); IEEE: Piscataway Township, NJ, USA, 2010. [Google Scholar]
- IEEE. IEEE Standard for Local and Metropolitan Area Networks—Audio Video Bridging (Avb) Systems—Corrigendum 1: Technical and Editorial Corrections; IEEE Std 802.1BA-2011/Cor 1-2016 (Corrigendum to IEEE Std 802.1BA-2011); IEEE: Piscataway Township, NJ, USA, 2016. [Google Scholar]
- IEEE. IEEE Standard for Layer 3 Transport Protocol for Time-Sensitive Applications in Local Area Networks; IEEE Std 1733-2011; IEEE: Piscataway Township, NJ, USA, 2011. [Google Scholar]
- IEEE. IEEE Standard for Layer 2 Transport Protocol for Time Sensitive Applications in a Bridged Local Area Network; IEEE Std 1722-2011; IEEE: Piscataway Township, NJ, USA, 2011. [Google Scholar]
- AUTOSAR. Some/IP Protocol Specification; Autosar Foundation Release R19-11, 696; AUTOSAR: Munich, Germany, 2019. [Google Scholar]
- ISO. Road Vehicles—Diagnostic Communication over Internet Protocol (Doip)—Part 1: General Information and Use Case Definition; ISO 13400-1:2011; ISO: Vernier, Geneva, Switerland, 2011. [Google Scholar]
- ISO. Road Vehicles—Diagnostic Communication over Internet Protocol (Doip)—Part 2: Transport Protocol and Network Layer Services; ISO 13400-2:2012; ISO: Vernier, Geneva, Switerland, 2012. [Google Scholar]
- Patzer, A.; Zaiser, R. Xcp–the Standard Protocol for Ecu Development; Vector Informatik Gmbh: Stuttgart, Germany, 2016. [Google Scholar]
- Völker, L. Scalable Service-Oriented Middleware over Ip (Some/IP). Available online: https://some-ip.com/ (accessed on 5 October 2021).
- AUTOSAR. Some/IP Service Discovery Protocol Specification; Autosar Foundation Release R19-11, 802; AUTOSAR: Munich, Germany, 2019. [Google Scholar]
- Sklavos, N. Book Review: Stallings, W. Cryptography and Network Security: Principles and Practice. Inf. Secur. J. A Glob. Perspect. 2014, 23, 49–50. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P.; Wagner, D. A Conventional Authenticated-Encryption Mode. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.480.743&rep=rep1&type=pdf (accessed on 16 October 2021).
- Eldewahi, A.E.W.; Sharfi, T.M.H.; Mansor, A.A.; Mohamed, N.A.F.; Alwahbani, S.M.H. Ssl/Tls Attacks: Analysis and Evaluation. In Proceedings of the 2015 International Conference on Computing, Control, Networking, Electronics and Embedded Systems Engineering (ICCNEEE), Khartoum, Sudan, 7–9 September 2015. [Google Scholar]
- GENIVI, GENIVI vSOMEIP. Vsomeip in 10 Minutes. Available online: https://github.com/COVESA/vsomeip/wiki/vsomeip-in-10-minutes (accessed on 16 October 2021).
- Liu, J.; Zhang, S.; Sun, W.; Shi, Y. In-Vehicle Network Attacks and Countermeasures: Challenges and Future Directions. IEEE Netw. 2017, 31, 50–58. [Google Scholar] [CrossRef]
- Dang, Q. Recommendation for Applications Using Approved Hash Algorithms; Special Publication (NIST SP): Gaithersburg, MD, USA. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=911479 (accessed on 9 October 2021).
- Dworkin, M. Recommendation for Block Cipher Modes of Operation: The Cmac Mode for Authentication. NIST 2016. [Google Scholar] [CrossRef]
- Dworkin, M.J. Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (Gcm) for Confidentiality and Authentication. NIST 2007. [Google Scholar] [CrossRef]
- Langley, A.; Chang, W.; Mavrogiannopoulos, N.; Strombergson, J.; Josefsson, S. Chacha20-Poly1305 Cipher Suites for Transport Layer Security (Tls). Internet Engineering Task Force (IETF). Available online: https://www.hjp.at/doc/rfc/rfc7905.html (accessed on 6 October 2021).












| Author | Verification Platform | Support Protocols | Security Mechanism |
|---|---|---|---|
| Trong [4,5] | XC7Z020, 100 MHz, Xilinx | FlexRay, Ethernet (custom) | Integrity |
| Jin [6,7] | TC397, 300 MHz, AURIX | CAN/CANFD, Ethernet (IEEE 1722) | Integrity |
| Kim [8] | MPC5668, 116 MHz, NXP | CAN, FlexRay, Ethernet (custom) | None |
| Shreejith [9] | ZC70x, 200 MHz, Xilinx | FlexRay, Ethernet (custom) | None |
| Lee [10] | TC275, 200 MHz, Infineon | FlexRay, Ethernet (custom) | None |
| Yadav [11] | Unspecified | CAN, Ethernet (custom) | None |
| Jo [12] | CANoe | CAN, CANFD, Ethernet (custom) | None |
| This paper | S32G, 1000 MHz, NXP | CAN/CANFD, Ethernet (SOME/IP) | Integrity, confidentiality |
| Security Scheme | Algorithm Type | Security Mechanism | Algorithm | Security Strength |
|---|---|---|---|---|
| Scheme 1 | MAC | Integrity | AES128-CMAC | 128 bit |
| SHA256-HMAC | 128 bit | |||
| Scheme 2 | AEAD | Integrity, confidentiality | AES256-GCM | 256 bit |
| Chacha20-Poly1305 | 256 bit |
| Security Scheme | Protocol Type ID | Security Level ID | Crypto Algorithms ID | MAC Length |
|---|---|---|---|---|
| Scheme 1, AES128-CMAC | 0 for CAN2.0, 1 for CANFD | 0 | 0 | 0 for 128 bit, 1 for 256 bit |
| Scheme 1, SHA256-HMAC | 0 | 1 | ||
| Scheme 2, AES256-GCM | 1 | 0 | ||
| Scheme 2, Chacha20-Poly1305 | 1 | 1 | ||
| Scheme 3 | 2 | 0 |
| Proposed Architectures | Implementation Platform | Frequency | Baud Rate |
|---|---|---|---|
| Gateway | NXP-S32G-274evb | A53, 1000 MHz M7, 400 MHz | CAN, 500 Kbps CANFD, 500 Kbps + 2 Mbps Ethernet, 1000 Mbps |
| ADAS | NXP-IMX6ULL-alpha | A7, 800 MHz | Ethernet, 100 Mbps |
| VCU | VN1610 + CANoe12.0 | - | CAN, 500 Kbps CANFD, 500 Kbps + 2 Mbps |
| Experimental Variables | Evaluation Metrics | |||
|---|---|---|---|---|
| CAN or CANFD | Payload size | Security algorithm | For protocol conversion | For security scheme |
| CAN | 1 byte | AES128-CMAC | Effective load radio CPU usage RAM usage Latency | Latency |
| SHA256-HMAC | ||||
| AES256-GCM | ||||
| Chacha20-poly1305 | ||||
| None | ||||
| CAN | 8 bytes | AES128-CMAC | ||
| SHA256-HMAC | ||||
| AES256-GCM | ||||
| Chacha20-poly1305 | ||||
| None | ||||
| CANFD | 64 bytes | AES128-CMAC | ||
| SHA256-HMAC | ||||
| AES256-GCM | ||||
| Chacha20-poly1305 | ||||
| None | ||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zuo, Z.; Yang, S.; Ma, B.; Zou, B.; Cao, Y.; Li, Q.; Zhou, S.; Li, J. Design of a CANFD to SOME/IP Gateway Considering Security for In-Vehicle Networks. Sensors 2021, 21, 7917. https://doi.org/10.3390/s21237917
Zuo Z, Yang S, Ma B, Zou B, Cao Y, Li Q, Zhou S, Li J. Design of a CANFD to SOME/IP Gateway Considering Security for In-Vehicle Networks. Sensors. 2021; 21(23):7917. https://doi.org/10.3390/s21237917
Chicago/Turabian StyleZuo, Zheng, Shichun Yang, Bin Ma, Bosong Zou, Yaoguang Cao, Qiangwei Li, Sida Zhou, and Jichong Li. 2021. "Design of a CANFD to SOME/IP Gateway Considering Security for In-Vehicle Networks" Sensors 21, no. 23: 7917. https://doi.org/10.3390/s21237917
APA StyleZuo, Z., Yang, S., Ma, B., Zou, B., Cao, Y., Li, Q., Zhou, S., & Li, J. (2021). Design of a CANFD to SOME/IP Gateway Considering Security for In-Vehicle Networks. Sensors, 21(23), 7917. https://doi.org/10.3390/s21237917






