Abstract
The seamless integration of low-power, miniaturised, invasive/non-invasive lightweight sensor nodes have contributed to the development of a proactive and unobtrusive Wireless Body Area Network (WBAN). A WBAN provides long-term health monitoring of a patient without any constraint on his/her normal dailylife activities. This monitoring requires the low-power operation of invasive/non-invasive sensor nodes. In other words, a power-efficient Medium Access Control (MAC) protocol is required to satisfy the stringent WBAN requirements, including low-power consumption. In this paper, we first outline the WBAN requirements that are important for the design of a low-power MAC protocol. Then we study low-power MAC protocols proposed/investigated for a WBAN with emphasis on their strengths and weaknesses. We also review different power-efficient mechanisms for a WBAN. In addition, useful suggestions are given to help the MAC designers to develop a low-power MAC protocol that will satisfy the stringent requirements.
1. Introduction
A Wireless Body Area Network (WBAN) allows the integration of intelligent, miniaturized, low-power, invasive/non-invasive sensor nodes that monitor body functions and the surrounding environment. Each intelligent node has enough capability to process and forward information to a base station for diagnosis and prescription. A WBAN provides long term health monitoring of patients under natural physiological states without constraining their normal activities. It is used to develop a smart and affordable health care system and can be a part of diagnostic procedure, maintenance of a chronic condition, supervised recovery from a surgical procedure, and can handle emergency events.
Some of the common objectives in a WBAN are to achieve maximum throughput, minimum delay, and to maximize the network lifetime by controlling the main sources of energy waste, i.e., collision, idle listening, overhearing, and control packet overhead. A collision occurs when more than one packet transmits data at the same time. The collided packets have to be retransmitted, which consumes extra energy. The second source of energy waste is idle listening, meaning that a node listens to an idle channel to receive data. The third source is overhearing, i.e., to receive packets that are destined to other nodes. The last source is control packet overhead, meaning that control information are added to the payload. A minimal number of control packets should be used for data transmission. Medium Access Control (MAC) protocols play an important role in solving the aforementioned problems. Generally they are grouped into contention-based and schedule-based MAC protocols. In contention-based MAC protocols such as Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA) protocols, nodes contend for the channel to transmit data. If the channel is busy, the node defers its transmission until it becomes idle. These protocols are scalable with no strict time synchronization constraint. However, they incur significant protocol overhead. In schedule-based protocols such as Time Division Multiple Access (TDMA) protocols, the channel is divided into time slots of fixed or variable duration. These slots are assigned to nodes and each node transmits during its slot period. These protocols are energy conserving protocols. Since the duty cycle of radio is reduced, there is no contention, idle listening and overhearing problems. But these protocols require frequent synchronization. Table 1 compares CSMA/CA and TDMA protocols.

Table 1.
CSMA vs. TDMA Protocols.
The development of a low-power MAC protocol for a WBAN has been a hot research topic for the last few years. Considerable research efforts have been dedicated to propose/investigate new MAC protocols that could satisfy the crucial WBAN requirements. A number of researchers have considered IEEE 802.15.4 [1] for a WBAN since it supports low data rate applications, but it is not enough to support high data rate applications (data rate > 250 Kbps). Other protocols such as Heartbeat Driven MAC (H-MAC) [2], Reservation-based Dynamic TDMA (DTDMA) [3], Preamble-based TDMA (PB-TDMA) [4], and BodyMAC [5] protocols have been proposed/investigated in the existing literature. In this paper, an overview of the aforesaid protocols with focus on their strengths and weakness is presented. Useful suggestions are given to overcome the weaknesses of these protocols. Then, a comparative analysis of many power-efficient mechanisms such as Low-power Listening (LPL), scheduled-contention, and TDMA mechanisms is presented in the context of a WBAN. Examples are given to validate the discussion.
The rest of the paper is categorized into four sections. Section 2 presents the WBAN requirements. A study of different low-power MAC protocols proposed/investigated for a WBAN is given in Section 3. Section 4 reviews various power-efficient mechanisms for a WBAN with useful guidelines. The final section concludes our work.
2. WBAN MAC Requirements
The most important attribute of a good MAC protocol for a WBAN is energy efficiency. In some applications, the device should support a battery life of months or years without intervention, while others may require a battery life of only tens of hours due to the nature of the applications. For example, cardiac defibrillators and pacemakers should have a lifetime of more than 5 years, while swallowable camera pills have a lifetime of 12 hours [6]. Power-efficient and flexible duty cycling techniques are required to minimize the idle listening, overhearing, packet collisions and control packet overhead problems. Furthermore, low duty cycle nodes should not receive frequent synchronization and control information (beacon frames) if they have no data to send or receive.
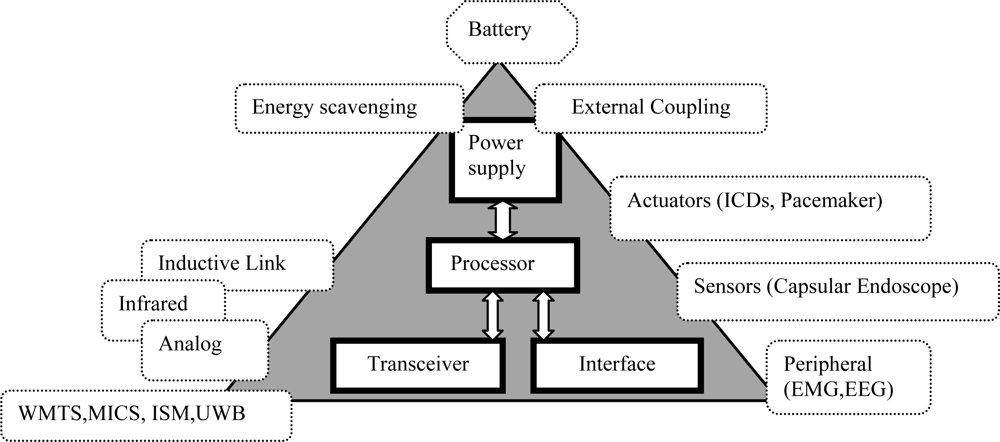
The WBAN MAC should support simultaneous operation on in-body (Medical Implant Communications Service, also called MICS) and on-body frequency bands/channels [Industrial, Scientific and Medical (ISM) or Ultra Wide Band (UWB)] at the same time. In other words, it should support Multiple Physical layers (Multi-PHYs) communication. Other important factors are scalability and adaptability to changes in the network, delay, throughput, and bandwidth utilization. Changes in the network topology, the position of the human body, and the node density should be handled rapidly and successfully. The MAC protocol for a WBAN should consider the electrical properties of the human body and the diverse traffic nature of in-body and on-body nodes. For example, the data rate of in-body nodes varies, ranging from few kbps in pacemaker to several Mbps in capsular endoscope. Figure 1 shows some of the potential issues of a MAC protocol for WBANs.
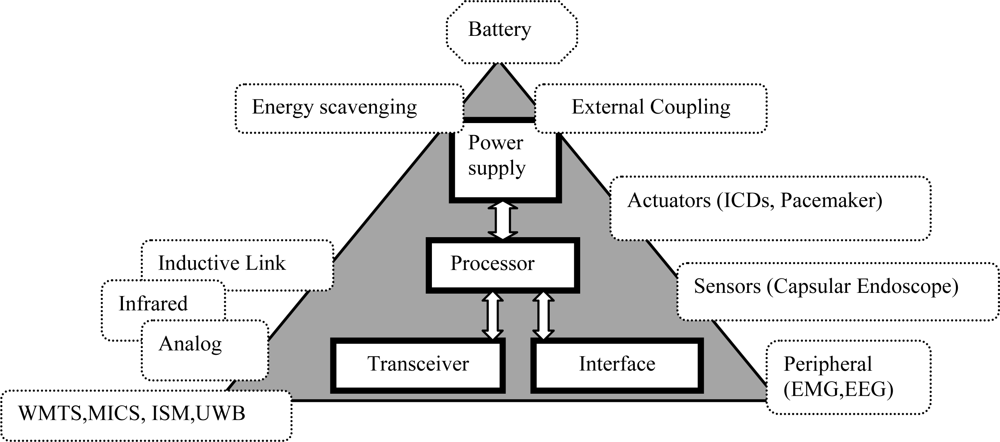
Figure 1.
Potential issues of a MAC protocol for a WBAN.
The Quality of Service (QoS) is also an important factor of a good MAC protocol for a WBAN. This includes point-to-point delay and delay variation. In some cases, real-time communication is required for many applications such as fitness and medical surgery monitoring applications. For multimedia applications, the latency should be less than 250 ms and the jitter should be less than 50 ms [6]. However, the reliability, latency, and jitter requirements depend on the nature of the applications. For emergency applications, the MAC protocol should allow in-body or on-body nodes to get quick access to the channel (in less than one second) and to send the emergency data to the coordinator. One such example is the detection of irregular heartbeat, high or low blood pressure or temperature, and excessively low or high blood glucose level in a diabetic patient. Another example is when the node is dying. Reporting medical emergency events should have higher priority than non-medical emergency (battery dying) events.
In a WBAN, most of the traffic is correlated, i.e., a patient suffering from a fever triggers temperature, blood pressure, and respiration sensors at the same time [7]. These changes may also affect the oxygen saturation level (SpO2) in the blood. These kinds of physiological parameters increase the traffic correlation. A single physiological fluctuation triggers many sensors at the same time. In this case, a CSMA/CA protocol encounters heavy collisions and extra energy consumption. Also, in CSMA/CA protocol, the nodes are required to perform Clear Channel Assessment (CCA) before transmission. However, the CCA is not always guaranteed in the MICS band since the path loss inside the human body due to tissue heating is much higher than in free space. Bin et al. studied the unreliability of a CCA in a WBAN and concluded that for a given −85 dBm CCA threshold, the on-body nodes cannot see the activity of the in-body nodes when they are at 3 meters distance away from the surface of the body [8]. Sana et al. have studied the behavior of the CSMA/CA protocol for a WBAN and concluded that the CSMA/CA protocol encounters heavy collision problems for high traffic nodes [9].
TDMA-based protocols provide good solutions to the traffic correlation, heavy collision, and CCA problems. These protocols are energy conserving protocols because the duty cycle is reduced and there are no contention, idle listening, and overhearing problems. However, common TDMA needs extra energy for periodic time synchronization. All the sensors (with and without data) are required to receive the periodic packets in order to synchronize their clocks. Therefore, the design and implementation of a new TDMA protocol is required that can accommodate the heterogeneous WBAN traffic in a power-efficient manner.
3. Existing/Proposed MAC Protocols for WBANs
3.1. IEEE 802.15.4
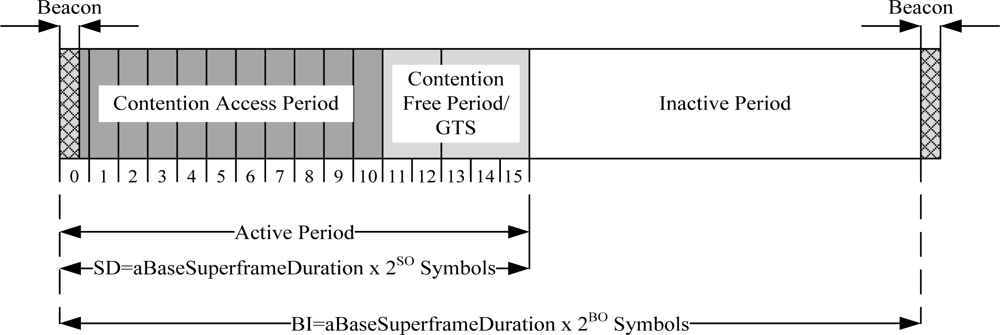
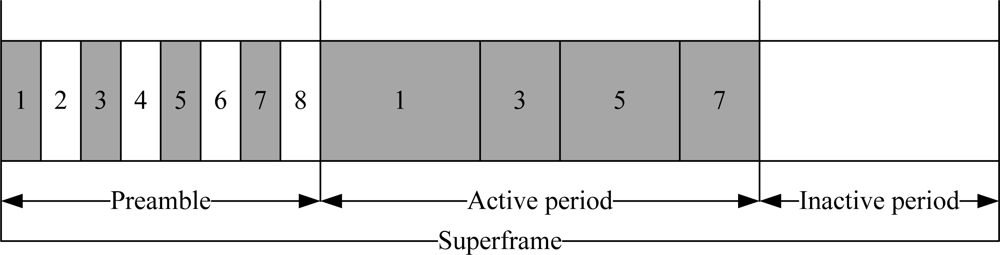
IEEE 802.15.4 is a low-power protocol designed for low data rate applications. It offers three operational frequency bands: 868 MHz, 915 MHz, and 2.4 GHz bands. There are 27 sub-channels allocated in IEEE 802.15.4, i.e., 16 sub-channels in 2.4 GHz band, 10 sub-channels in 915 MHz band and one sub-channel in the 868 MHz band, as given in Table 2. The table also shows the data rate and the modulation technique for each frequency band. IEEE 802.15.4 has two operational modes: a beacon-enabled mode and a non-beacon enabled mode. In a beacon-enabled mode, the network is controlled by a coordinator, which regularly transmits beacons for device synchronization and association control. The channel is bounded by a superframe structure as illustrated in Figure 2.

Table 2.
IEEE 802.15.4 frequency bands, data rates, and modulation methods.
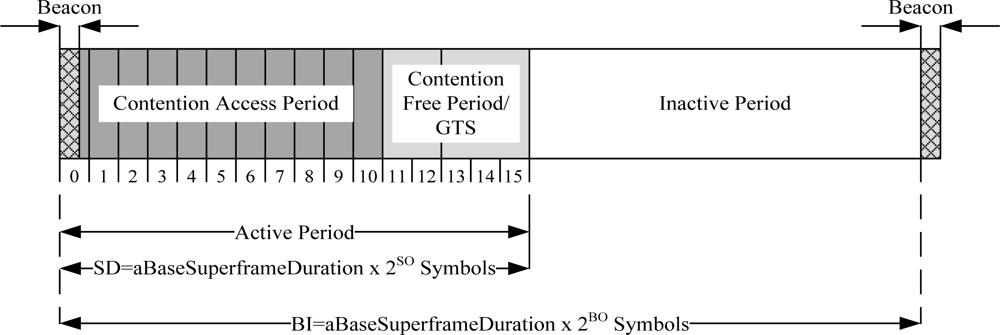
Figure 2.
IEEE 802.15.4 superframe structure.
The superframe consists of both active and inactive periods. The active period contains three components: a beacon, a Contention Access Period (CAP), and a Contention Free Period (CFP). The length of entire the superframe (Beacon Interval, BI) and the length of the active part of the superframe (Superframe Duration, SD) are defined as follows:
where:
- aBaseSuperframeDuration = 960 symbols (1 symbol = 16μs)
- BO = Beacon Order,
- SO = Superframe Order
The coordinator interacts with nodes during the active period and sleeps during inactive period. There are maximum seven Guaranteed Time Slots (GTS) in the CFP period to support time critical traffic. In a beacon-enabled mode, a slotted CSMA/CA protocol is used in the CAP period while in a non-beacon enabled mode, unslotted CSMA/CA protocol is used.
IEEE 802.15.4 has remained the main focus of many researchers during the past few years. Some of the main reasons of selecting IEEE 802.15.4 for a WBAN are low-power communication and support of low data rate WBAN applications. Nicolas et al. investigated the performance of a non-beacon IEEE 802.15.4 in [10], where low upload/download rates (mostly per hour) are considered. They concluded that the non-beacon IEEE 802.15.4 results in 10 to 15 years sensor lifetime for low data rate and asymmetric WBAN traffic. However, their work considers data transmission on the basis of periodic intervals, which is not a perfect scenario in a real WBAN. Furthermore, the data rate of in-body and on-body nodes is not always low, i.e., it ranges from 10 Kbps to 10 Mbps, and hence reduces the lifetime of the sensor nodes. Li et al. studied the behaviour of slotted and unslotted CSMA/CA protocols and concluded that the unslotted mechanism performs better than the slotted one in terms of throughput and latency, but with a high power consumption cost [11].
Intel Corporation conducted a series of experiments to analyze the performance of IEEE 802.15.4 for a WBAN [12]. They deployed a number of Intel Mote 2 [13] nodes on chest, waist, and the right ankle. Table 3 shows the throughput at a 0 dBm transmit power when a person is standing and sitting on a chair. The connection between ankle and waist cannot be established, even for a short distance of 1.5 m. All other connections show favourable performance.

Table 3.
Throughput at a 0 dBm Transmit Power
Dave et al. studied the energy efficiency and QoS performance of IEEE 802.15.4 and IEEE 802.11e [14] MAC protocols under two generic applications: a wave-form real time stream and a real-time parameter measurement stream [15]. Table 4 shows the throughput and the Power (in mW) for both applications. The AC_BE and AC_VO represent the access categories voice and best-effort in the IEEE 802.11e.

Table 4.
Throughput and Power (in mW) of IEEE 802.15.4 and IEEE 802.11e under AC_BE and AC_VO.
Since the IEEE 802.15.4 operates in the 2.4 GHz unlicensed band, the possibilities of interference from other devices such as IEEE 802.11 and microwave are inevitable. A series of experiments to evaluate the impact of IEEE 802.11 and microwave ovens on the IEEE 802.15.4 transmission were carried out in [16]. The authors considered XBee 802.15.4 development kit that has two XBee modules. Table 5 shows the effects of microwave oven on the XBee remote module. When the microwave oven is ON, the packet success rate and the standard deviation is degraded to 96.85% and 3.22% respectively. However, there is no loss when the XBee modules are taken two meters away from the microwave oven.

Table 5.
Co-existence Test Results between IEEE 802.15.4 and Microwave Oven.
3.2. Heartbeat Driven MAC Protocol (H-MAC)
A Heartbeat Driven MAC protocol (H-MAC) is a TDMA-based protocol originally proposed for a star topology WBAN. The energy efficiency is improved by exploiting heartbeat rhythm information in order to synchronize the nodes. The nodes do not need to receive periodic information to perform synchronization. The heartbeat rhythm can be extracted from the sensory data and hence all the rhythms represented by peak sequences are naturally synchronized. The H-MAC protocol assigns dedicated time slots to each node to guarantee collision-free transmission. In addition, this protocol is supported by an active synchronization recovery scheme where two resynchronization schemes are implemented.
Although H-MAC protocol reduces the extra energy cost required for synchronization, it does not support sporadic events. Since the TDMA slots are dedicated and are not traffic adaptive, H-MAC protocol encounters low spectral/bandwidth efficiency in case of low traffic. For example, a blood pressure node may not need a dedicated time slot while an endoscope pill may require a number of dedicated time slots when deployed in a WBAN. But the slots should be released when the endoscope pill is expelled. The heartbeat rhythm information varies depending on the patient condition. It may not reveal valid information for synchronization all the time. One of the solutions is to assign the time slots based on the node’s traffic information and to receive synchronization packets when required, i.e., when a node has data to transmit/receive.
3.3. Reservation-Based Dynamic TDMA Protocol (DTDMA)
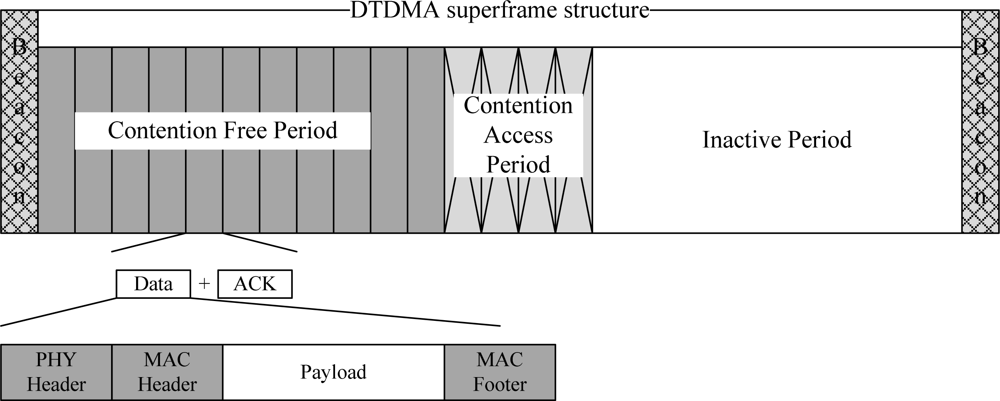
A Reservation-based Dynamic TDMA Protocol (DTDMA) was originally proposed for normal (periodic) WBAN traffic where slots are allocated to the nodes which have buffered packets and are released to other nodes when the data transmission/reception is completed. The channel is bounded by superframe structures. Each superframe consists of a beacon – used to carry control information including slot allocation information, a CFP period – a configurable period used for data transmission, a CAP period – a fixed period used for short command packets using slotted-ALOHA protocol, and a configurable inactive period – used to save energy. Unlike a beacon-enabled IEEE 802.15.4 superframe structure where the CAP duration is followed by CFP duration, in DTDMA protocol the CFP duration is followed by CAP duration in order to enable the nodes to send CFP traffic earlier than CAP traffic. In addition, the duration of an inactive period is configurable based on the CFP slot duration. If there is no CFP traffic, the inactive period will be increased. The DTDMA superframe structure is given in Figure 3.
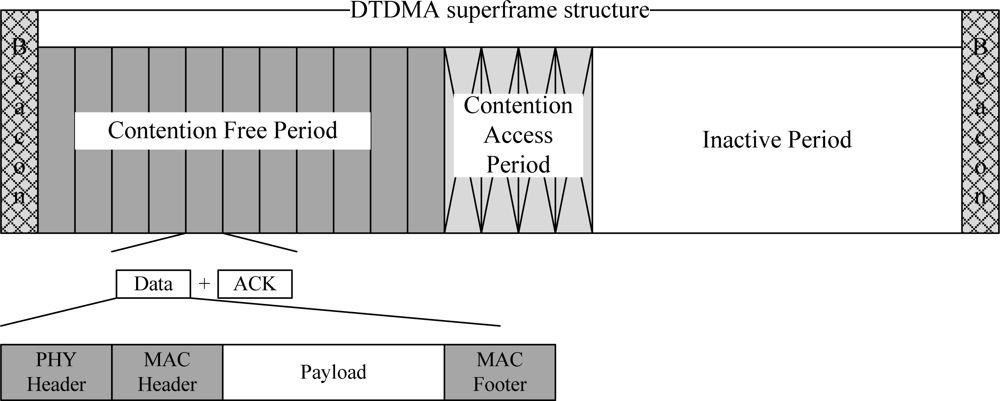
Figure 3.
DTDMA superframe structure.
It has been shown that for normal (periodic) traffic, the DTDMA protocol provides more dependability in terms of low packet dropping rate and low energy consumption when compared with IEEE 802.15.4. However, it does not support emergency and on-demand traffic. Although the slot allocation based on the traffic information is a good approach, the DTDMA protocol has several limitations when considered for the MICS band. The MICS band has ten sub-channels where each sub-channel has 300 Kbps bandwidth. The DTDMA protocol could operate on one sub-channel but cannot operate on ten sub-channels simultaneously. In addition, the DTDMA protocol does not support the sub-channel allocation mechanism in the MICS band. This protocol can be further investigated for the MICS band by integrating the sub-channel information in the beacon frame. The new concept may be called Frequency-based DTDMA (F-DTDMA), i.e., the coordinator first selects one of the sub-channels in the MICS band and then divides the selected sub-channel in TDMA superframe (s) according to the DTDMA protocol. However the FCC has imposed several restrictions on the sub-channel selection/allocation mechanism in the MICS band (see Section 4.4), which further creates problems for the MAC designers.
3.4. PB-TDMA Protocol
The performance of a Preamble-based TDMA (PB-TDMA, see Section 4.3) for a WBAN has been analyzed in [17]. The authors used NS-2 for extensive simulations where the wireless physical parameters were considered according to low-power Nordic nRF2401 transceiver and the simulation area was 3 × 3 meters. For the performance comparison, many other protocols such as S-MAC and IEEE 802.15.4 were also simulated in the same environment. Simulation results showed that PB-TDMA protocol outperformed S-MAC and IEEE 802.15.4 protocol in terms of energy efficiency. The results are valid for normal traffic only and do not consider the behaviour of emergency and on-demand traffic.
3.5. BodyMAC Protocol
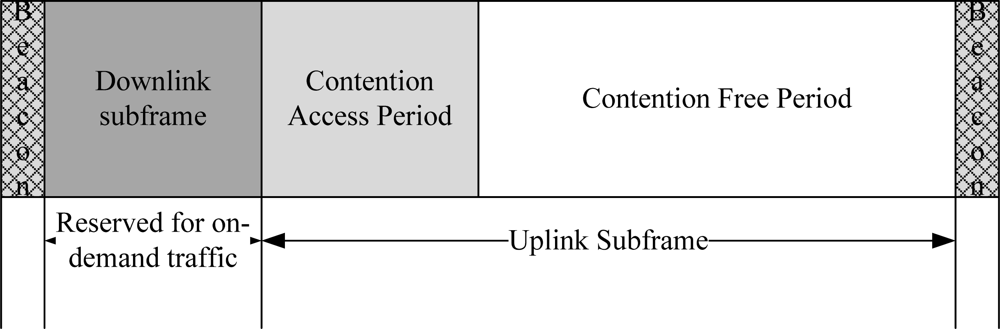
A BodyMAC protocol is a TDMA-based protocol where the channel is bounded by TDMA superframe structures with downlink and uplink subframes as given in Figure 4. The downlink frame is used to accommodate the on-demand traffic and the uplink frame is used to accommodate the normal traffic. There is no proper mechanism to handle the emergency traffic. The uplink frame is further divided into CAP and CFP periods. The CAP period is used to transmit small size MAC packets. The CFP period is used to transmit the normal data in a TDMA slot. The duration of the downlink and uplink superframes are defined by the coordinator.
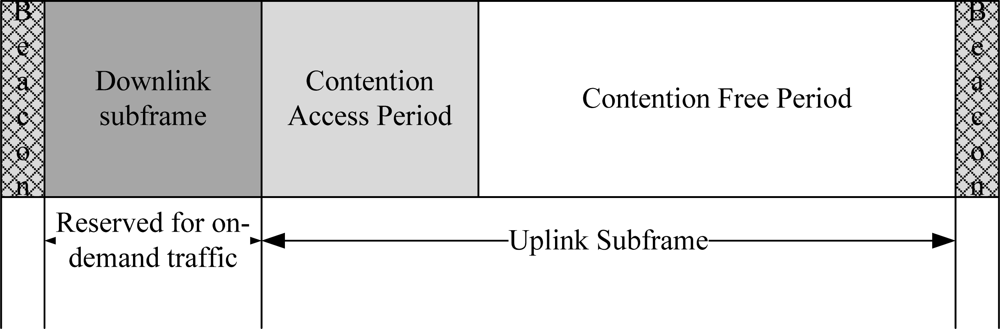
Figure 4.
BodyMAC superframe structure.
The advantage of the BodyMAC protocol is that it accommodates the on-demand traffic using the downlink subframe. However, in case of low-power implants (which should not receive beacons periodically), the coordinator has to wake up the implant first and then send synchronization packets. After synchronization, the coordinator can request/send data in the downlink subframe. The wake up procedure for low-power implants is not defined in the BodyMAC protocol. One of the solutions is to use a wakeup radio in order to wake up low-power implants before using the downlink subframe. In addition the wakeup packets can be used to carry control information such as sub-channel (MICS band) and slot allocation information from the coordinator to the nodes. Finally, the BodyMAC protocol uses the CSMA/CA protocol in the CAP period which is not reliable for a WBAN. This should be replaced by slotted-ALOHA as done in DTDMA.
4. Power-efficient Mechanisms for WBANs
Power-efficient mechanisms play an important role in the performance of a good MAC protocol. These mechanisms are categorized into Low-power Listening (LPL), Scheduled Contention, and TDMA mechanisms. The following sections briefly explain each mechanism with examples.
4.1. Low-power Listening (LPL) Mechanism
In a Low-power Listening (LPL) mechanism, nodes wake up for a short duration to check the channel activity without receiving any data. If the channel is idle the nodes go into sleep mode, otherwise they stay on the channel to receive the data. This is also called channel polling. The LPL is performed on regular basis regardless of synchronization among nodes. The sender sends a long preamble before each message in order to detect the polling at the receiving end.
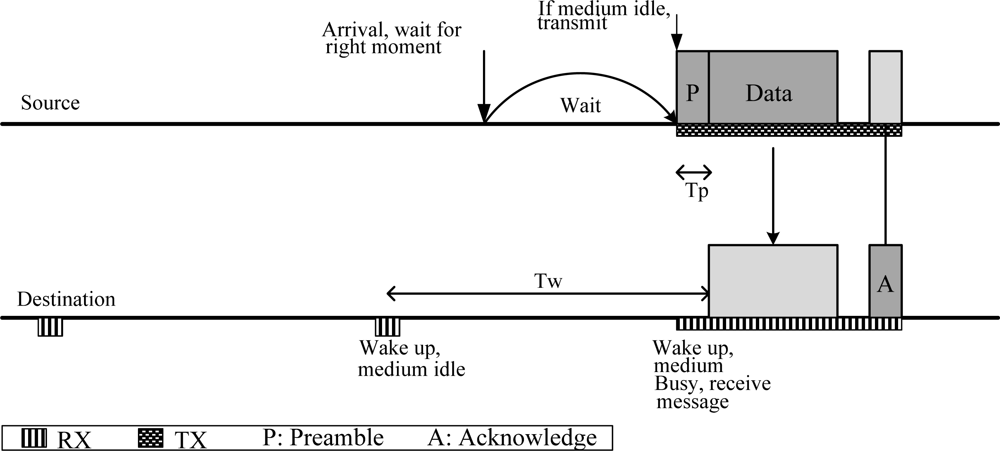
The WiseMAC [18] protocol is based on the LPL mechanism. In this protocol, a non-persistent CSMA and a preamble sampling technique is used to reduce idle listening. The preamble is used to alert the receiving node of a packet arrival. All the nodes in a network sample the medium periodically. If a node samples a busy medium, it continues to listen until it receives data or the medium becomes idle. Figure 5 shows the WiseMAC concept.
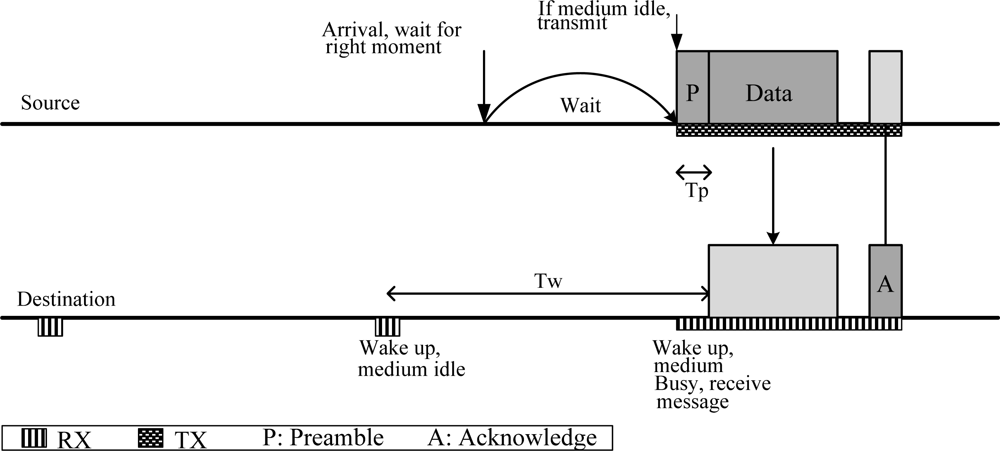
Figure 5.
WiseMAC concept.
In a WBAN, the LPL mechanism has several advantages and disadvantages. The periodic sampling is efficient for high-traffic nodes and performs well under variable traffic conditions. However, it is ineffective for low-traffic nodes, especially in-body nodes, where periodic sampling is not preferred due to strict power constraints. Since the WBAN topology is a star topology and most of the traffic is uplink, using LPL mechanism is not an optimal solution to support both in-body and on-body communication simultaneously.
4.2. Scheduled-Contention Mechanism
In a scheduled-contention mechanism, scheduled and contention based schemes are combined to incur scalability and collision avoidance. In this mechanism, the nodes adapt a common schedule for data communication. The schedules are exchanged periodically during a synchronization period. If two neighbouring nodes reside in two different clusters, they keep the schedules of both clusters, which results in extra energy consumption.
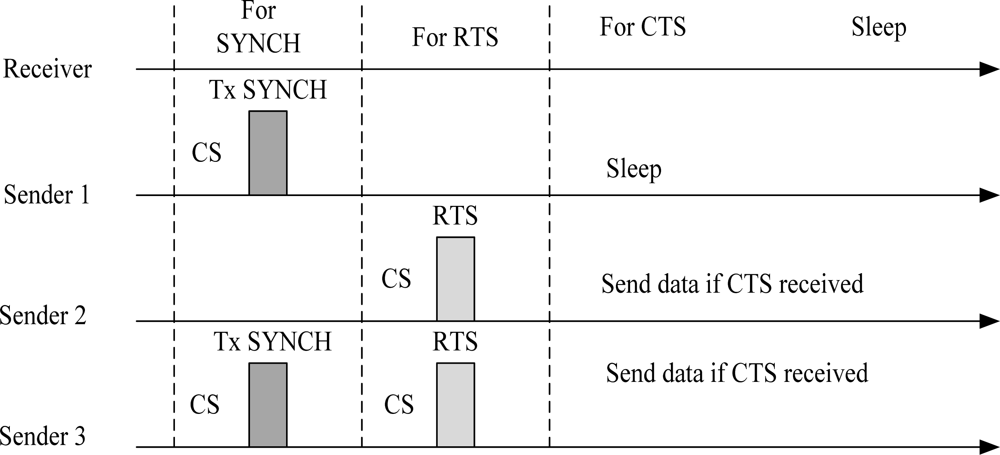
The S-MAC [19] protocol is a good example of a scheduled-contention mechanism. S-MAC is a power-efficient and a contention-based MAC protocol designed for multi-hop Wireless Sensor Networks (WSNs). In this protocol, the low duty cycle mode is default operation of all nodes. This protocol introduces the concept of coordinated sleeping among neighbouring nodes. The node is active when it has data to send otherwise its radio is completely turned off. The energy is reduced from all the sources of energy waste, i.e., idle listening, collision, overhearing and control overhead. A complete cycle of listen and sleep is called frame. Each frame begins with a wake up period, which is used by nodes to exchange control information. The wakeup period is usually followed by a sleep period. If a node has data to send while in the sleep mode, it must defer its transmission until the next wakeup slot. The state of the channel is determined using physical and virtual carrier sense mechanism. For each unicast frame transmission, Request to Send/Clear to Send (RTS/CTS) mechanism is followed. Broadcast frames are sent without using RTS/CTS mechanism. If a node fails to access the medium, it turns off its radio until the Network Allocation Vector (NAV) is zero. Nodes maintain synchronization by sending SYNCH packet. The size of SYNCH packet is very short and includes information about next sleep period. The listen period of a node is divided into two parts when both SYNCH and data packets are received at the same time. Figure 6 illustrates the timing relationship between receive and different senders. Sender 1 sends a SYNCH packet only. Sender 2 sends a unicast data packet only. Sender 3 sends both a SYNCH and a data packet.
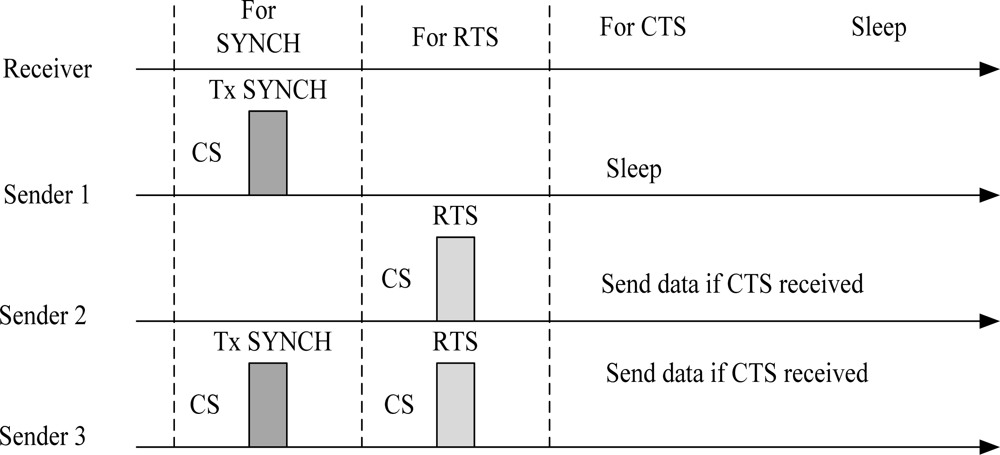
Figure 6.
Timing relationship between a receiver and different senders. CS is carrier sense.
A scheduled-contention mechanism reduces idle listening using sleep schedules and performs well for multi-hop WSNs. However, considering this mechanism for a WBAN reveals several problems for low-power in-body/on-body nodes such as pacemakers and defibrillator nodes/implants, which are not required to wake up periodically in order to exchange their schedules with other nodes. Furthermore, scheduled-contention mechanism may perform well for on-body applications but it does not provide reliable solutions to handle sporadic events including emergency and on-demand events. Handling sporadic events (emergency) require new innovative solutions that allow in-body/on-body nodes to update the coordinator within strictly limited amount of time.
4.3. TDMA Mechanism
In a TDMA mechanism, the channel is bounded by a superframe structure that consists of a number of time slots allocated by a base-station or a coordinator. The time slots are allocated according to the traffic requirements, i.e., a node gets a time slot whenever it has data to send or receive. Otherwise, it goes into sleep mode. Although it performs well in terms of power consumption but consumes extra energy due to frequent synchronization.
The PB-TDMA protocol is based on the TDMA mechanism. In this protocol, the nodes are assigned specified slots for collision-free data transmission. These slots are repeated in fixed cycle. A complete cycle of these slots is called a frame. In the PB-TDMA protocol, each TDMA frame contains a preamble and a data transmission slot as illustrated in Figure 7. A node always listens to the channel during preamble and transmits in a data transmission slot. The preamble contains a dedicated subslot for every node. These subslots are used to activate the destination node by broadcasting the destination node ID of outgoing packet. After receiving the preamble, the destination node identifies the source node. Each node turns off its radio when it has no data to transmit. This mechanism avoids unnecessary power consumption of sensor nodes. The radio is turned on when the node finds its ID in the preamble or when the node has data to transmit.
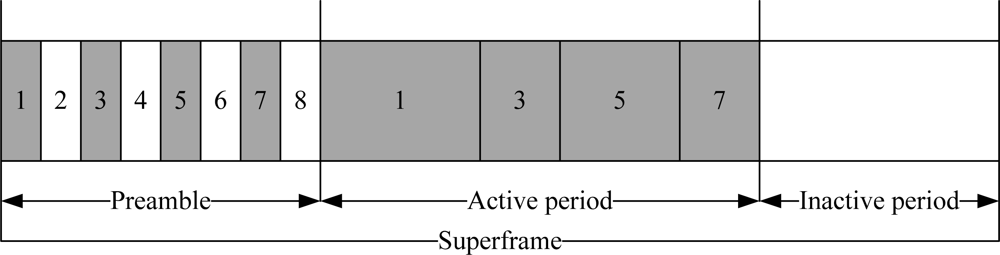
Figure 7.
PB-TDMA superframe structure.
As discussed in Section 2, the CSMA/CA protocol is not a reliable protocol for a WBAN due to unreliable CCA, traffic correlation, and heavy collision problems. The alternative is to adapt a TDMA protocol that can solve the aforementioned problems in a power-efficient manner. However, traditional TDMA protocols such as PB-TDMA have several problems, i.e., preamble overhearing and limitation of handling sporadic events. Solving these problems (including many others) towards a WBAN can accommodate the heterogeneous WBAN traffic in a power-efficient manner. Furthermore, new techniques are required to solve the sporadic events problems in a reliable way.
4.4. Comparison of LPL, Scheduled-contention and TDMA Mechanisms for a WBAN
Table 6 presents the characteristics of the LPL, schedule-contention, and TDMA mechanisms for a WBAN [20]. The table shows that LPL and scheduled-contention are unable to accommodate the heterogeneous WBAN traffic including sporadic events. Although it is possible to develop new MAC protocols based on these mechanisms, they will not be able to satisfy all the requirements. For example, LPL mechanisms may perform well in case of periodic traffic but they are unable to accommodate aperiodic (unpredictable sporadic events) traffic and low duty cycle nodes. Furthermore, the scheduled-contention mechanisms are unable to cover in-body nodes, which do not require frequent synchronization or exchange of their schedules. The TDMA mechanisms provide good solutions to the variable WBAN traffic. The slots can be assigned according to the traffic volume of a node. Although in traditional TDMA protocols, nodes are required to synchronize at the beginning of each superframe boundary, but this approach can be optimized for nodes that do not require frequent synchronization. One way is to skip the synchronization control packets such as the beacon. The control packets (beacons) can be received when the low duty cycle nodes have data to send or receive. A detailed comparison of MAC protocols based on LPL, scheduled-contention, and TDMA mechanisms for a WBAN is given in Table 7 (the protocols are not explained here due to space limitation problems, but they are available in the existing literature. The table is a result of a comprehensive study of the existing protocols in the context of a WBAN).

Table 6.
Comparison of LPL, Scheduled-contention, and TDMA mechanisms for a WBAN.

Table 7.
Summary of existing MAC Protocols for a WBAN.
From the following table, it can be seen that LPL-based protocols such as WiseMAC and BMAC [21] protocols are good for high traffic applications while STEM [22] performs well for low traffic applications. Furthermore, STEM can also accommodate the sporadic events by using a separate control channel. However, increase in the traffic load decreases the probability of handling sporadic events. Schedule-contention protocols such as SMAC and TMAC [23] are suitable for high traffic applications, PMAC [24] for delay sensitive applications, and DMAC [25] for priority-based applications (where the nodes have different priorities). As mentioned earlier, TDMA-based protocols can easily accommodate the heterogeneous WBAN traffic since they are adaptable to the traffic load, i.e., slots can be assigned according to the traffic volume. However, traditional TDMA-based protocols such as FLAMA [26], LEACH [27], and HEED [28] are unable to satisfy the WBAN requirements as mentioned in the above table. In addition, all of the existing MAC protocols are designed for a single channel only, i.e., they do not operate on Multi-PHYs simultaneously. The MAC transparency has been a hot topic for the MAC designers since different bands have different characteristics in terms of data rate, number of sub-channels in a particular frequency band/channel, and data prioritization. A good MAC protocol for a WBAN should enable reliable operation on MICS, ISM, and UWB etc bands simultaneously. With regards to MICS band, the FCC has imposed several restrictions [29]. According to the FCC:
“Within 5 seconds prior to initiating a communications session, circuitry associated with a medical implant programmer/control transmitter must monitor the channel (sub-channel) or channels (sub-channels) the MICS system devices intend to occupy for a minimum of 10 milliseconds per channel.”
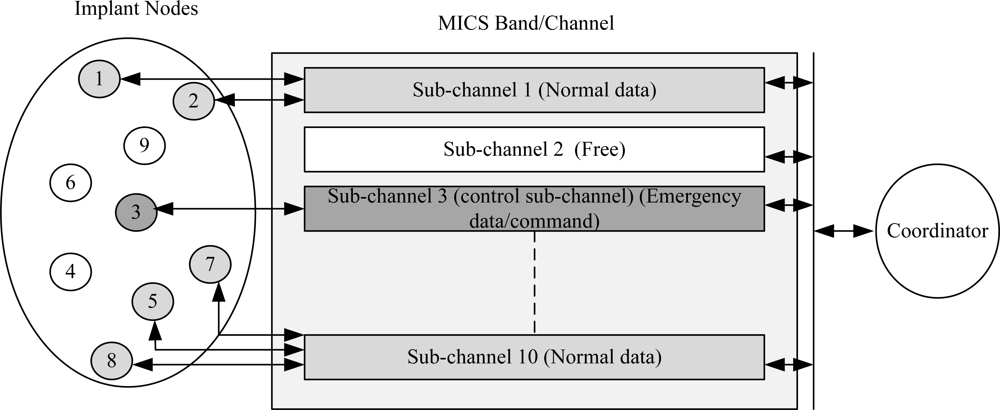
In other words, the coordinator must perform Listen-before-talking (LBT) criteria prior to a MICS communication session. The sub-channels are solely assigned by the coordinator, i.e., the implants cannot initiate a communication session except in case of an emergency event. Furthermore, the implants are not allowed to perform LBT which creates problems to handle emergency events. Sending an emergency data regardless of LBT may result in heavy collision since the selected sub-channel may have data from another implant. The LBT restriction prevents MAC designers to develop a reliable mechanism for emergency traffic. One of the solutions is to use a wakeup radio or a control sub-channel dedicated temporarily to emergency traffic since the FCC does not allow the permanent dedication of a sub-channel in MICS band. The sub-channel information can be updated using control frames such as the beacon frame. Figure 8 illustrates an example of a control sub-channel used to send emergency data. It shows that five nodes (1, 2, 5, 7 and 8) are transmitting normal data and one node (3) is transmitting emergency data. The remaining nodes (4, 6 and 9) are in sleep mode. Normal transmission requires beacon to allocate resources. While in emergency case, nodes are not required to wait for the beacon. The communication is initiated by the implants and a control sub-channel can be used to send the emergency data/command as given in the figure.
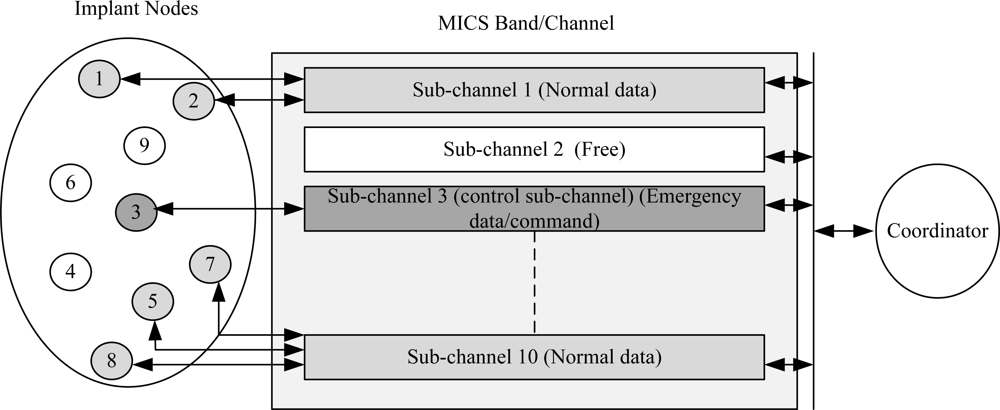
Figure 8.
An example of a control sub-channel for emergency traffic.
5. Conclusions
This paper presented a comprehensive study of existing/proposed MAC protocols for a WBAN with useful suggestions. In addition, different power-efficient mechanisms such as LPL, schedule-contention, and TDMA mechanisms are analyzed and discussed in the context of a WBAN. It is shown that CSMA/CA protocol encounters heavy collision and unreliable CCA problems, therefore TDMA protocol is considered the most reliable and power-efficient protocol for a WBAN. However, existing TDMA protocols have a number of limitations such as synchronization overhead, dynamic slot assignment, and Multi-PHYs communication. Therefore, a novel low-power MAC protocol is required that should satisfy the traffic heterogeneity and correlation, MAC transparency, and reliability requirements. This study can be used as a guideline towards the design and development of a new low-power MAC protocol for a WBAN.
Acknowledgments
This research was supported by the The Ministry of Knowledge Economy (MKE), Korea, under the Information Technology Research Center (ITRC) support program supervised by the Institute for Information Technology Advancement (IITA) (IITA-2009-C1090-0902-0019).
References
- IEEE Std.802.15.4: Wireless medium access control (MAC) and physical layer (PHY) specifications for low data rate wireless personal area networks (WPAN); IEEE: Piscataway, NJ, USA, 2006.
- Li, H.M.; Tan, J.D. Heartbeat driven MAC for body sensor networks. Proceedings of the 1st ACM SIGMOBILE international workshop on systems and networking support for healthcare and assisted living environments, San Juan, Puerto Rico, 2007; pp. 25–30.
- Li, C.; Li, H.B.; Kohno, R. Reservation-based dynamic TDMA protocol for medical body area networks. IEICE Trans. Commun 2009, 92, 387–395. [Google Scholar]
- Ullah, S.; Islam, S.M.R.; Nessa, A.; Zhong, Y.; Kwak, K.S. Performance analysis of preamble based TDMA protocol for wireless body area network. J. Commun. Softw. Syst 2008, 4, 222–226. [Google Scholar]
- Fang, G.; Dutkiewicz, E. BodyMAC: Energy efficient TDMA-based MAC protocol for wireless body area networks. Proceedings of IEEE ISCIT 2009, Incheon, Korea, 2009.
- IEEE 802.15.6, Technical Requirements Document; IEEE: Piscataway, NJ, USA, 2008.
- Li, H.M.; Tan, J.D. An ultra-low-power medium access control protocol for Body Sensor Network. Proceedings of 27th Annual International Conference of the Engineering in Medicine and Biology Society, Shanghai, China, 2005; pp. 2451–2454.
- Zhen, B.; Li, H.B.; Kohno, R. IEEE body area networks and medical implant communications. Proceedings of the ICST 3rd International Conference on Body Area Networks, Tempe, AZ, USA, 2008.
- Ullah, S.; Kwak, D.; Lee, C.; Lee, H.; Kwak, K.S. Numerical Analysis of CSMA/CA for Pattern-Based WBAN System. Proceedings of Biomedical Engineering and Informatics, Tianjin, China, 2009.
- Timmons, N.F.; Scanlon, W.G. Analysis of the performance of IEEE 802.15.4 for medical sensor body area networking. Proceedings of IEEE SECON, Santa Clara, CA, USA, 2004; pp. 4–7.
- Li, C.; Li, H.B.; Kohno, R. Performance evaluation of IEEE 802.15.4 for wireless body area network (WBAN). Proceedings of IEEE International Conference on ICC Workshops, Dresden, Germany, 2009.
- Shah, R.C.; Yarvis, M. Characteristics of on-body 802.15.4 networks. Proceedings of 2nd IEEE Workshop on Wireless Mesh Networks, Reston, VA, USA, 2006; pp. 138–139.
- Adler, R.; Flanigan, M.; Huang, J.; Kling, R.; Kushalnagar, N.; Nachman, L.; Wan, C.Y.; Yarvis, M. Intel Mote 2: An advanced platform for demanding sensor network applications. Proceedings of Demo Session, San Diego, CA, USA, 2005.
- IEEE 802.11e Std “Amendment to Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications: Medium Access Control Quality of Services Enhancements; IEEE: Piscataway, NJ, USA, 2005.
- Cavalcanti, D.; Schmitt, R.; Soomro, A. Performance Analysis of 802.15.4 and 802.11e for body sensor network applications. Proceedings of 4th International Workshop on Wearable and Implantable Body Sensor Networks, Aachen, Germany, 2007.
- Chen, C.; Carlos, P.R. Monitoring human movements at home using wearable wireless sensors. Proceedings of ISMICT 09, Montreal, QC, Canada, 2009.
- Ullah, S.; Higgins, H.; Islam, S.M.R; Khan, P.; Kwak, K.S. On PHY and MAC performance in body sensor networks. EURASIP J. Wirel. Commun. Netw 2009. [Google Scholar] [CrossRef]
- El-Hoiydi, A.; Decotignie, J.D. WiseMAC: An ultra low power MAC protocol for the downlink of infrastructure wireless sensor networks. Proceedings of the Ninth IEEE Symposium on Computers and Communication, ISCC’04, Alexandria, Egypt, 2004; pp. 244–251.
- Ye, W.; Estrin, H.J. An energy-efficient MAC protocol for wireless sensor networks. Proceedings of Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 2002; pp. 1567–1576.
- Chebbo, H. Literature Review of Energy Efficient MAC in WSN/BAN; IEEE: Piscataway, NJ, USA, 2008. [Google Scholar]
- Polastre, J.; Hill, J.; Culler, D. Versatile low power media access for wireless sensor networks. Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, New York, NY, USA, 2004; pp. 95–107.
- Schurgers, C.; Tsiatsis, V.; Srivastava, M.B. STEM: Topology management for energy efficient sensor networks. Proceedings of Aerospace Conference, Manhattan Beach, CA, USA, 2004; 3, pp. 3-1099–3-1108.
- Dam, V.T.; Langendoen, K. An adaptive energy-efficient mac protocol for WSNs. Proceedings of the 1st ACM Conference on Embedded Networked Sensor Systems (Sen-Sys), Los Angeles, CA, 2003; pp. 171–180.
- Khan, N.P.; Boncelet, C. PMAC: Energy efficient medium access control protocol for wireless sensor networks. Proceedings of IEEE Military Communications Conference, Washington, DC, USA, 2006.
- Lu, G.; Krishnamachari, B.; Raghavendra, C. An Adaptive Energy-Efficient and Low-Latency MAC dor Data Gathering in Sensor Networks. Proceedings of the 4th International Workshop on Algorithms for Wireless, Mobile, Ad Hoc and Sensor Networks, Santa Fe, Mexico, 2004.
- Rajendran, V.; Garcia-Luna-Aveces, J.J.; Obraczka, K. Energy-efficient, application-aware medium access for sensor networks. Proceedings of IEEE Mobile Adhoc and Sensor Systems Conference, Washington, DC, USA, 2005; p. 8630.
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui Kula, HI, USA, 2000.
- Younis, O.; Fahmy, S. Heed: A hybrid, energy-efficient, distributed clustering approach for ad hoc sensor networks. IEEE Trans. Mob. Comp 2004, 3, 366–379. [Google Scholar]
- Index of Bureaus. Available online: http://www.fcc.gov/Bureaus/ (accessed on 16 August 2009).
Additional Notes
- In-body Nodes: Nodes implanted under the human skin, also called implants/invasive nodes.
- On-body Nodes: Nodes deployed on the human skin, also called wearable/non-invasive nodes.
- Normal Traffic: Traffic in a normal condition and is generated on regular or periodic intervals.
- On-demand Traffic: Initiated by a coordinator or a physician to acquire certain information.
- Emergency Traffic: Refers to unpredictable sporadic events and is initiated by the in-body/on-body nodes.
- Channel: Refers to a frequency band as a whole.
- Sub-channel: Refers to the number of channels in a particular frequency band/channel such as 10 sub-channels in MICS frequency band/channel.
©2010 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/)