Dynamical Jumping Real-Time Fault-Tolerant Routing Protocol for Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Work
- In order to guarantee real-time and fault-tolerant characteristics, jumping transmission mode is adopted. When node failure, network congestion or empty region is detected, or the remaining transmission time of the data packet is near to deadline, jumping transmission mode will be used to reduce the transmission delay, thus ensuring the data packets are sent to the destination node in specified time limit.
- Feedback mechanism is exploited to enhance the successful transmission ratio. Each node feeds back the information about node failure, network congestion and empty area to its upstream node and the message is forwarded to the data sources. Then the jumping probability can be dynamically adjusted by using the feedback information, which can prevent the subsequent transmission from the effect caused by failure node, network congestion or empty region.
- When using the hop-by-hop transmission mode, the node in FCS with the minimum times of transmission is selected as the next hop node, through which the average energy cost of each node can be balanced. Therefore, the whole network life time can be prolonged.
3. Preliminaries
- Definition 1: Node Failure State FAULTY. FAULTY indicates that the node is in failure state. If the states of the FCS nodes of the current node are all FAULTY, then the state of current node is set to JFAULTY, indicating the jumping transmission mode should be used to transmit data packet due to node failure.
- Definition 2: Node Congestion State CONG. CONG indicates that the node is in congestion state. If the states of the FCS nodes of the current node are all CONG, then the state of current node is set to JCONG, indicating the jumping transmission mode should be used to transmit data packet due to the congestion.
- Definition 3: Empty Area State VOID. VOID indicates that there is no node in the area. If the states of the FCS nodes of the current node are all VOID, then the state of the current node is set to VOID, indicating the jumping transmission mode should be used to transmit data packet due to the empty area.
- Definition 4: Jumping Probability pi. The pi indicates the probability of jumping from current node to the node i, the higher value of pi indicates the higher jumping probability.
- Definition 5: Confidence variable c. The c indicates the confidence level of reliability of the node, the higher value of c indicates the higher reliability of the node.
4. DMRF Protocol
4.1. Faulty Node Detection Method
| Data: FCS, confidence variable c. | |
| Result: Node State. | |
| 1 | Initialize the FCS and c. |
| 2 | IF the state of FCS is FAULTY or JFAULTY THEN |
| 3 | Set the state of the Node i as JFAULTY |
| 4 | ELSE |
| 5 | For each Node j in FCS of Node i |
| 6 | Node i sends a message to Node j |
| 7 | IF Node i receives no reply from Node j THEN |
| 8 | Decrease the confidence variable c of Node j |
| 9 | IF the confidence variable c of Node j less than the confidence threshold f THEN |
| 10 | Set the state of the Node j as FAULTY |
| 11 | ELSE update the delay and transmission rate of Node j |
4.2. Network Congestion Detection Method
| Data: FCS, occupy factor of the Node and congestion factor[29] | |
| Result: Node State. | |
| 1 | Initialize the FCS. |
| 2 | Predict the congestion using the method in [29]. |
| 3 | IF Congestion happens Node i THEN |
| 4 | Set the state of Node i as CONG. |
| 5 | IF the state of FCS is CONG or JCONG THEN |
| 6 | Set the state of Node i as JCONG, inform to its upstream node. |
| 7 | IF Node i receives feedback message from Node j THEN |
| 8 | Set the state of Node j as CONG. |
| 9 | IF the state of Node i converts to normal THEN |
| 10 | Set the state of Node i as NORMAL, inform to its upstream node. |
| 11 | IF Node i receives the updating message THEN |
| 12 | Node i updates the record in the routing table. |
4.3. VOID Region Detection
| Data: FCS | |
| Result: Node state | |
| 1 | Initialize FCS. |
| 2 | IF Node i has not FCS THEN |
| 3 | Node i send feedback message to its upstream Node. |
| 4 | IF the states of all Nodes in FCS are VOID state THEN |
| 5 | Set the state of Node i VOID. |
| 6 | IF Node i receives feedback message from Node j THEN |
| 7 | Set the state of Node j VOID. |
4.4. The Jumping Transmission and Routing Selection
4.4.1. Jumping transmission
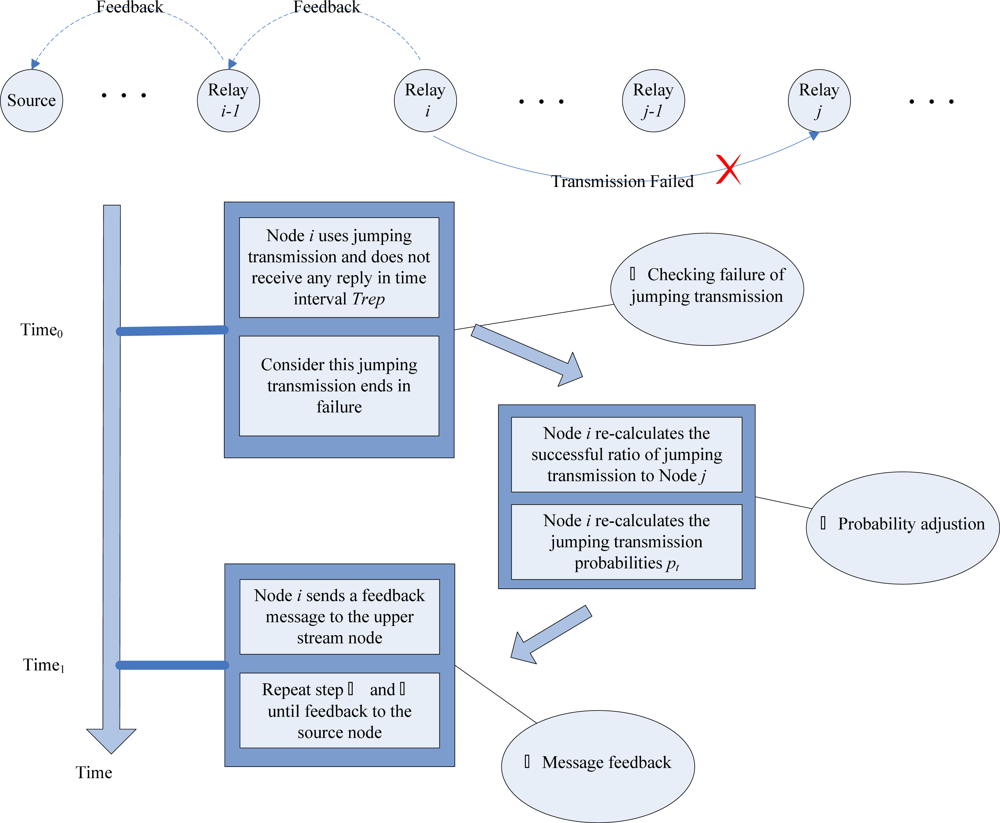
(1) Jumping probability adjustment when jumping transmission failure
(2) Jumping probability adjustment of the upstream node
4.4.2. Path Selection
| Data: FCS | |
| Result: Choose the next hop node and the transmitting mode. | |
| 1 | IF the state of node is JFAULTY or VOID or JCONG THEN |
| 2 | Utilize the jumping mode. |
| 3 | IF λ ≥ θlow THEN |
| 4 | Select the node with the maximum delay and minimum transmission times. Set the packet state as LOW. |
| 5 | IF θlow > λ ≥ θhigh THEN |
| 6 | Select the node with the maximum delay and minimum transmission times. Set the packet state as MEDIUM. |
| 7 | IF θhigh > λ > θjump THEN |
| 8 | Select the node with the maximum delay and minimum transmission times. Set the packet state as HIGH. |
| 9 | IF λ ≤ θjump THEN |
| 10 | Utilize the jumping mode. |
4.4.3. Calculation of θlow and θhigh
5. Feasibility Proof and Performance Analysis of DMRF
5.1. Feasibility Analysis of DMRF Protocol
5.2. Message Complexity Analysis
5.3. Energy Consumption Complexity Analysis
5.4. Time Complexity of Faulty Nodes, Congested Nodes and VOID Region Detection
6. Performance Evaluation
6.1. Times of Successful Transmission with Different Ratios of Faulty Nodes
6.2. Successful Transmission Ratio under Congestion Condition
6.3. The Effect of Network Topology on DMRF
6.4. Successful Transmission Ratio in Case of VOID Region
6.5. Average Transmission Delay in Case of Different VOID Region Radius
6.6. The Number of Control Packets in Case of Different VOID Region Radius
7. Conclusions and Future Work
- The jumping transmission mode is explored to guarantee real-time and fault-tolerant characteristics.
- Feedback mechanism is used to enhance the successful transmission ratio.
- The average energy cost of each node in the network is balanced and the life time of the whole network is prolonged by the selection method of next hop in which the node in FCS with the minimum times of transmission is selected as the next hop.
- The feasibility proof and performance analysis are presented to testify the superiority of DMRF.
Acknowledgments
References and Notes
- Akyildiz, I.F.; Melodia, T.; Kaushik, R. A survey on wireless multimedia sensor networks. Comput. Netw 2007, 5, 921–960. [Google Scholar]
- Ssu, K.F.; Chou, C.H.; Jiau, H.C.; Hu, W.T. Detection and diagnosis of data inconsistency failures in wireless sensor networks. Comput. Netw 2006, 50, 1247–1260. [Google Scholar]
- He, T.; Stankovic, J.A.; Lu, C.; Abdelzaher, T. SPEED: A stateless protocol for real-time communication in sensor networks. Proceedings of the 23rd International Conference on Distributed Computing Systems, Washington, DC, USA, October 27–31, 2003; pp. 46–55.
- Felemban, E.; Lee, C.G.; Ekici, E. MMSPEED: multipath Multi-SPEED protocol for QoS guarantee of reliability and Timeliness in wireless sensor networks. IEEE Trans. Mob. Comput 2006, 5, 738–754. [Google Scholar]
- Lei, Z.; Kan, B.Q.; Xu, Y.J.; Li, X.W. FT-SPEED: A fault-tolerant, real-time routing protocol for wireless sensor networks. Proceedings of 2007 International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, September 21–23, 2007; pp. 2531–2534.
- Prabh, K.S.; Abdelzaher, T.F. On scheduling and real-time capacity of hexagonal wireless sensor networks. Proceedings of the 19th Euromicro Conference on Real-Time Systems, Washington, DC, USA, July 4–6, 2007; pp. 136–145.
- Chipara, O.; He, Z.; Xing, G.L.; Chen, Q.; Wang, X.R.; Lu, C.Y.; Stankovic, J.; Abdelzaher, T. Real-time power-aware routing in sensor networks. Proceedings of the 14th IEEE International Workshop on Quality of Service, New Haven, CT, USA, June 19–21; 2006; pp. 83–92. [Google Scholar]
- Akkaya, K.; Younis, M. An energy-aware qos routing protocol for wireless sensor networks. Proceedings of the 23rd IEEE International Conference on Distributed Computing Systems, Washington, DC, USA, May 19–22, 2003; pp. 710–715.
- Yuan, L.F.; Cheng, W.Q.; Du, X. An energy-efficient real-time routing protocol for sensor networks. Comp. Commun 2007, 30, 2274–2283. [Google Scholar]
- Pothuri, P.K.; Sarangan, V.; Thomas, J.P. Delay-constrained, energy-efficient routing in wireless sensor networks through topology control. Proceedings of the 2006 IEEE International Conference on Networking, Sensing and Control, Lauderdale, FL, USA, April 23–25, 2006; pp. 35–41.
- Peng, S.L.; Li, S.S.; Peng, Y.X.; Tang, W.S.; Xiao, N. Real-time data delivery in wireless sensor networks: a data-aggregated, cluster-based adaptive approach. Proceedings of the 4th International Conference on Ubiquitous Intelligence and Computing, Hong Kong, China, July 11–13, 2007; pp. 514–523.
- Li, Y.J.; Chung, S.C; Ye, Q. A two-hop based real-time routing protocol for wireless sensor networks. Proceedings of the 7th IEEE International Workshop on Factory Communication Systems, Dresden, Germany, May 20–23, 2008; pp. 65–74.
- Tsai, M.J.; Yang, H.Y.; Liu, B.H.; Huang, W.Q. Virtual-coordinate-based delivery-guaranteed routing protocol in wireless. IEEE/ACM Trans. Netw 2009, 17, 1228–1241. [Google Scholar]
- Kulkarni, S.; Wang, L. Energy-efficient multihop reprogramming for sensor networks. ACM Trans. Sens. Netw 2009, 5, 1–40. [Google Scholar]
- Heo, J.Y; Hong, J.A; Cho, Y.K. EARQ: Energy aware routing for real-time and reliable communication in wireless industrial sensor networks. IEEE Trans. Ind. Inf 2009, 5, 3–11. [Google Scholar]
- Mengjie, Y.; Hala, M.; Madjid, M. A self-organized middleware architecture for wireless sensor network management. Int. J. Ad Hoc Ubiquit. Comput 2008, 3, 135–145. [Google Scholar]
- Mikko, K.; Jukka, S.; Mauri, K.; Kaseva, V.; Hännikäinen, M.; Hämäläinen, T.D. Energy-efficient neighbor discovery protocol for mobile wireless sensor networks. Ad Hoc Netw 2009, 7, 24–41. [Google Scholar]
- Jennifer, Y.; Biswanath, M.; Dipak, G. Wireless sensor network survey. Comput. Netw.: Intell. J. Comput. Telecommun. Netw 2008, 52, 2292–2330. [Google Scholar]
- Vehbi, C.G.; Ozgur, B.A.; Akyildiz, I.F. A real-time and reliable transport protocol for wireless sensor and actor networks. IEEE/ACM Trans. Netw 2008, 16, 359–370. [Google Scholar]
- Chao, H.L.; Chang, C.L. A fault-tolerant routing protocol in wireless sensor networks. Int. J. Sens. Netw 2008, 3, 66–73. [Google Scholar]
- Zhu, D.Q.; Bai, J.; Simon, X.Y. A multi-fault diagnosis method for sensor systems based on principle component analysis. Sensors 2010, 10, 241–253. [Google Scholar]
- Liu, M.; Cao, J.N.; Chen, G.H; Wang, X.M. An energy-aware routing protocol in wireless sensor networks. Sensors 2009, 9, 445–462. [Google Scholar]
- Jiang, P. A new method for node fault detection in wireless sensor networks. Sensors 2009, 9, 1282–1294. [Google Scholar]
- Luis, J.G.; Ana, L.S.; Alicia, T.C.; Cláudia, J.B. Routing protocols in wireless sensor networks. Sensors 2009, 9, 8399–8421. [Google Scholar]
- Chen, J.L.; Ma, Y.W.; Lai, C.P.; Hu, C.C; Huang, Y.M. Multi-hop routing mechanism for reliable sensor computing. Sensors 2009, 9, 10117–10135. [Google Scholar]
- Ding, M.; Cheng, X.Z. Fault-tolerant target tracking in sensor networks. Proceedings of ACM MOBIHOC 2009, New Orleans, LA, USA, May 18–21, 2009; pp. 125–134.
- Hanan, S.; Michael, S. Low-energy fault-tolerant bounded-hop broadcast in wireless networks. IEEE/ACM Trans. Netw 2009, 17, 582–590. [Google Scholar]
- Tian, H.; Shen, H.; Roughan, M. Maximizing networking lifetime in wireless sensor networks with regular topologies. Proceedings of the 9th International Conference on Parallel and Distributed Computing, Applications and Technologies, Otago, New Zealand, December 1–4, 2008; pp. 211–217.
- Li, S.S.; Liao, X.K.; Zhu, P.D. Congestion avoidance, detection and mitigation in wireless sensor networks. Comp. Res. Dev 2007, 44, 1348–1356. [Google Scholar]
- JProwler. Available online: http://w3.isis.vanderbilt.edu/projects/nest/jprowler/ (accessed on 14 March 2010).








| Variable | Description |
|---|---|
| FAULTY & JFAULTY | Faulty & JFaulty state |
| CONG & JCONG & NORMAL | Congestion & JCongestion & Normal state |
| VOID | Void region |
| Sucj | Successful transmission ratio to node j |
| pi | Jumping probabilities to node i |
| λ | Remaining transmission time factor |
| θlow, θhigh | Lower or Upper threshold of remaining transmission time factor |
| θjump | Jumping threshold |
| delayi j | Delay between node i and node j |
| LOW & MEDIUM & HIGH | LOW & MEDIUM & HIGH transmission rate of data packets |
| T | Estimated transmission time |
| L | Remaining transmission time of data packet |
| ν | Average transmission rate |
| t | Maximum remaining transmission time of data packet |
| h | Average length of one hop |
| e | Average energy consumption of each transmission |
| d | Node density |
| r | Sensing radius of node |
| c | Confidence variable of node |
| Routing Protocol | SPEED, SPEED-T, SPEED-S, MMSPEED, FTSPEED, DMRF |
|---|---|
| MAC Layer | 802.11 |
| MAC Protocol | CSMA/CA |
| Bandwidth | 200 Kb/s |
| Buffer Size | 100 Bytes |
| Data packet Size | 32 Bytes |
| Region Size | (20 m, 20 m) |
| Node Number | 400 |
| Node Distribution | Random and Uniform |
| Maximum Transmission Distance | 30 m |
© 2010 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Wu, G.; Lin, C.; Xia, F.; Yao, L.; Zhang, H.; Liu, B. Dynamical Jumping Real-Time Fault-Tolerant Routing Protocol for Wireless Sensor Networks. Sensors 2010, 10, 2416-2437. https://doi.org/10.3390/s100302416
Wu G, Lin C, Xia F, Yao L, Zhang H, Liu B. Dynamical Jumping Real-Time Fault-Tolerant Routing Protocol for Wireless Sensor Networks. Sensors. 2010; 10(3):2416-2437. https://doi.org/10.3390/s100302416
Chicago/Turabian StyleWu, Guowei, Chi Lin, Feng Xia, Lin Yao, He Zhang, and Bing Liu. 2010. "Dynamical Jumping Real-Time Fault-Tolerant Routing Protocol for Wireless Sensor Networks" Sensors 10, no. 3: 2416-2437. https://doi.org/10.3390/s100302416
APA StyleWu, G., Lin, C., Xia, F., Yao, L., Zhang, H., & Liu, B. (2010). Dynamical Jumping Real-Time Fault-Tolerant Routing Protocol for Wireless Sensor Networks. Sensors, 10(3), 2416-2437. https://doi.org/10.3390/s100302416




