1. Introduction
The explosion of various wireless networking technologies and smart devices are demanding the exchange of rich multimedia contents and sensed data [
1,
2,
3,
4,
5]. As everyday devices are enabled with communication capabilities, we are entering into a new age of Internet of Things (IoT). IoT is expected to take us to a new era where everything is connected with the Internet. Therefore, the number of services and applications over IEEE 802.11 wireless LANs (WLANs) is rapidly increasing. As a device is expected to handle a large volume of data, power efficient policy is necessary for the long life of a network [
6]. To support high data rates, IEEE 802.11 standard provides more than one data rates by employing multiple sets of modulation and channel coding schemes [
7]. However, the transmission durations of control frames and inter-frame spaces are always of fixed value. In [
8], the authors showed that there is an upper bound for throughput, and performance enhancements cannot be obtained by simply increasing the data rate, even to infinitely high levels, without reducing the overhead.
A new block ACK (BA) mechanism was presented in the IEEE 802.11e, to reduce MAC overhead [
9]. A transmitter is assigned a fixed time duration called transmission opportunity (TXOP), during which a block of data frames is transmitted. Subsequently, the receiver aggregates the multiple ACK frames and sends a single BA that simultaneously acknowledges the status of all transmitted data frames by using a bitmap.
In IEEE 802.11n, the throughput enhancement is achieved by aggregating multiple packets before transmission [
10]. Aggregation has several advantages. Aggregation reduces the channel waiting time during the backoff process for transmitting consecutive frames. In addition, the time used up in preamble and frame headers transmission are also saved. Even though, aggregation of multiple frames improves the network throughput under error free channel, a large aggregated frame means stations have to wait longer period of time for the channel access. Furthermore, under erroneous channel conditions, corruption of a large aggregated frame will waste substantial channel time leading to decreased MAC efficiency. Therefore, in the error-prone network environment, aggregation may result in lower MAC efficiency. Therefore, adaptive frame size is more suitable in a practical situation [
11].
Thus, in this letter, we propose a scheme that can decrease the overhead of IEEE 802.11, without the use of aggregation techniques. We analyze the IEEE 802.11e BA scheme and propose an implicit BA request scheme. In addition, we discuss the proposed implicit BA scheme in detail and demonstrate how to improve IEEE 802.11e’s overall performance.
2. IEEE 802.11e
The MAC Service Data Unit (MSDU) is passed to IEEE 802.11e from upper layers. MSDU can be broken down into one or more MAC Protocol Data Units (MPDUs). In IEEE 802.11e, once a station successfully access the channel, the station is assigned a TXOP. During the TXOP, a station can transmit multiple MPDUs. TXOP is granted with both a start time and a maximum usable duration bounded by a threshold, referred to as the TXOP limit.
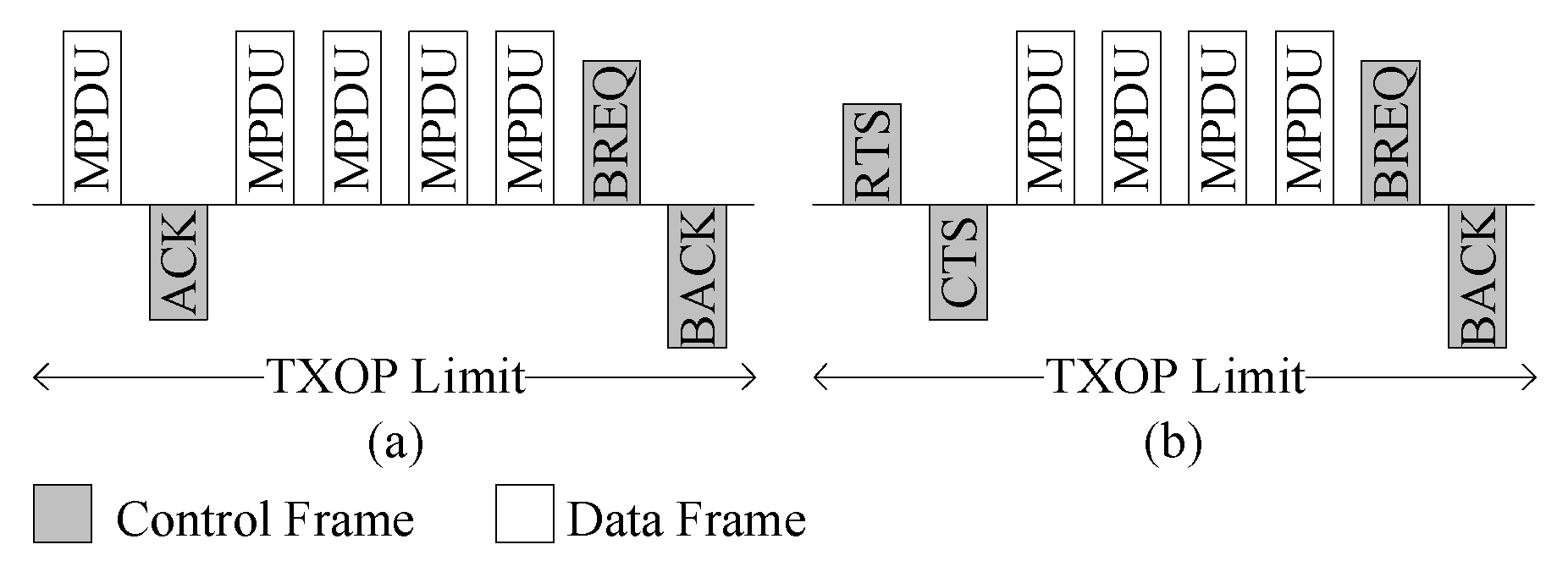
IEEE 802.11e introduced the BA scheme as shown in
Figure 1 to reduce the overhead caused by multiple ACK transmissions. Basically, the BA allows multiple MPDUs transmission in a burst with a gap of short inter-frame space (SIFS) duration and acknowledged by BA frame (BACK). Upon receiving the BA request (BREQ) frame, the BACK frame is transmitted. BACK contains status regarding the success/failure reception of individual MPDU in the form of a bitmap. Transmission of both BREQ and BACK frames are done at data transmission rate. The transmitter and receiver must establish agreements before using the BA scheme. BA consists of setup and teardown phases. In the setup phase, capability information such as buffer size and BA policy are negotiated with the receiver. Similarly, the BA agreement is torn down with a so-called DELBA frame. Once BA setup is complete, multiple MPDUs can be transmitted in a block, with the expectation of a single BACK frame. After receiving the BACK, the sender retransmits the error MPDUs, either in the next TXOP or individually. The maximum limit of MPDUs that can be transmitted in the TXOP is defined in the setup phase. However, the number of MPDUs in a block is not dependent on the TXOP limit. The sender can divide the MPDUs that belongs to the same MSDU into multiple TXOPs. The BREQ can be sent in the same TXOP, or in the next TXOP. If there is no response until the expiration of the BREQ timer, the BREQ is retransmitted.
Figure 1.
IEEE 802.11e block ACK in (a) basic access mode and (b) RTS/CTS access mode.
Figure 1.
IEEE 802.11e block ACK in (a) basic access mode and (b) RTS/CTS access mode.
The head of burst (HOB) frame must be immediately acknowledged for the immediate detection of the collision. The RTS/CTS frame can be exchanged before starting communication for protecting the data burst. However, for the basic access modes, the first data frame is immediately acknowledged, as shown in
Figure 1.
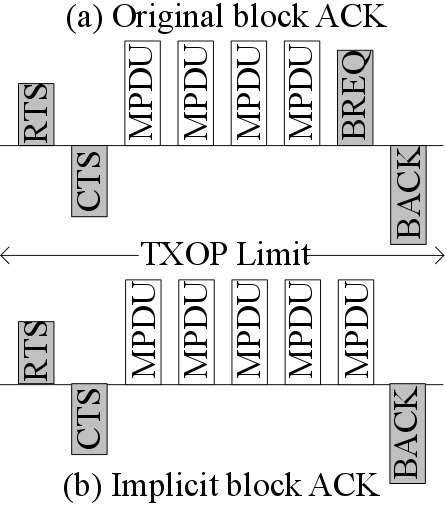
Figure 2.
Proposed block ACK (BA) in (a) basic access mode and (b) RTS/CTS access mode.
Figure 2.
Proposed block ACK (BA) in (a) basic access mode and (b) RTS/CTS access mode.
4. Analytical Framework
We consider a network composed of
n stations, and operate in saturated conditions. All stations are assumed to generate traffic with the same priority and have the same probability of winning channel. We assumed that source and destination are always fixed, thus, the BA setup phase overhead is omitted. Finally, we assume that stations experience uniform channel conditions,
i.e., they experience the same error rate. The discrete-time Markov chain of our model is same with the Markov chain employed in [
12,
13]. Furthermore, HOB refers to the data frame in the case of basic access or the RTS frame in the case of RTS/CTS access. Similarly, HACK is the HOB acknowledgment which is an ACK for the basic access and CTS for RTS/CTS access. Likewise, end of block (EOB) is the BREQ in the case of the original method, whereas EOB is the data frame in the case of the proposed method. When multiple stations try to access at the same slot, they contend via the random backoff procedure. Therefore, the probability
τ that a station transmits in a randomly chosen slot time is expressed as derived in [
13],
where
is the minimum backoff window size,
m’ is the maximum backoff stage, and
m is the maximum retransmission limit. Each packet is transmitted with a header of
h bytes. A packet is corrupted if at least one bit is received in error. Therefore, the probability of successful transmissions (PST) of all bits [
14] is given by
A station is unable to access the channel because of collision or due to loss of HOB or HACK frame [
15]. However, if HOB and HACK frames are successfully exchanged, then data transmission burst starts. The probability
p that a packet collides or unsuccessful due to error is derived as
where
PST and
PST are the frame success rates of HOB and HACK frames, respectively. Among
n stations, the probability
that there is at least one transmission in a time slot is given by
Channel access is successful if both HOB and HACK frames are exchanged successfully. The probability that a channel access attempt is successful (
) and the probability that all control frames are transmitted successfully (
) are expressed as
where,
PST and
PST are the frame success rates of EOB and BACK frames, respectively. The probability
that a HOB or HACK are received in error is given by
Finally, the system throughput
S can be easily expressed as
where
E[P] represents payload bits and
E[slot] represents the average duration of transmission. It is to be noted that
E[slot] consists of two parts: the idle time because of channel backoff, and the channel usage time due to successful burst transmissions, channel errors, or collisions,
i.e.,
where
σ represents the slot time,
E[bo] represents the average number of backoff slots used,
E[T] is the average time for transmission,
E[T] is the average time wasted in collision,
E[T] is the average error time of HOB frames and
E[T] is the average error time of EOB frames, respectively.
Let
r’ and
r be the employed control frame and data rate in Mbps, respectively. Let
RTS,
CTS,
ACK,
BREQ,
BACK, and
DATA represent channel occupancy times of corresponding frames. Similarly,
P is the payload. Common physical header is included in every frame transmitted. Therefore,
H should be added to every frame.
Table 1 shows the time durations of all the relevant frames in
μs. In this analysis, we assume each TXOP always ends with a BACK transmission.
Table 1.
Transmission time in μs.
Table 1.
Transmission time in μs.
| RTS | CTS | ACK | BREQ | BACK | DATA | H
|
|---|
| 160/r’ | 112/r’ | 112/r’ | 192/r | 1261/r | (224+P)/r | 192 |
The station can transmit multiple MPDUs for the TXOP period. The channel occupancy time can be split into three parts: (i) overhead for the channel access
AO, (ii) the data transmission burst, and (iii) overhead for the channel release
RO.
Table 2 shows the values of these components. The maximum number of MPDUs
d, that can be transferred in a TOXP can be derived as
Table 2.
Decomposition of channel utilization times.
Table 2.
Decomposition of channel utilization times.
| | AO | RO |
|---|
| Basic access | ACK+SIFS | BREQ+2SIFS+BACK |
| Proposed basic access | ACK+SIFS | SIFS+BACK |
| RTS/CTS access | RTS+2SIFS+CTS | BREQ+2SIFS+BACK |
| Proposed RTS/CTS access | RTS+2SIFS+CTS | SIFS+BACK |
Once a station gains the channel, regardless of the error in a data frame, the station transmits all data frames. Therefore, the total transmission time is given by:
However, because of the transmission error, the number of successfully transmitted data frames can be less than
d. The average number of data frames per data burst and overall payload are given by
Similarly, the average collision time experienced by a station can be expressed as:
where
HOB is the time utilized for the HOB transmission. The time wasted due to error is determined by the length of the corrupted frames. The error in HACK can only occur if the HOB frame is received successfully. Therefore, the average error time experienced by a station can be expressed as
Likewise, the average time wasted due to error in EOB or BACK frames is given by
where PST
and PST
are the frame success rates of EOB and BACK frames, respectively.
5. Numerical Results
The numerical results presented here is obtained from the derived analytical framework. IEEE 802.11b was utilized as the underlying PHY. Unless specified, the default values of data payload size is of 1 KB and TXOP is 20 ms.
Figure 4 depicts the network throughput for
n = 10,
r’ = 1 Mbps,
r = 11 Mbps, and BER = 0 with the various TXOP limits in both access modes. Note that the x-axis is in the logarithm scale. In the case of the error free channel, the minimum TXOP value is 2.2 ms; the time required for the transmission single MPDU (
i.e.,
d = 1). As the value of TXOP limit increases, the number of data unit that can be transmitted in a TXOP also increases.
Figure 4 depicts a step increment whenever the number of MSDUs that can be transmitted in TXOP increases by one unit.
Figure 4.
Throughput for n = 10, r = 1 Mbps, r = 11 Mbps, and bit error probability (BER) = 0.
Figure 4.
Throughput for n = 10, r = 1 Mbps, r = 11 Mbps, and bit error probability (BER) = 0.
The figure depicts the significant performance improvement resulting from the implementation of the proposed method. The RTS/CTS and basic access modes with TXOP limit=2.2 ms give overall throughput equal to 3.42 Mbps and 3.85 Mbps, respectively. However, the proposed scheme is able to increase the throughput of RTS/CTS access and basic access modes to 3.77 Mbps and 4.3 Mbps, respectively. Because the number of contending stations is less, meaning less collision probability, the basic access mode exhibits better throughput performance than the RTS/CTS access mode.
Figure 5 depicts the system throughput in the case of
n = 10,
r’ = 1 Mbps, and
r = 11 Mbps for various payload sizes. The graphs show the throughput for both ideal channel with BER=0 and for moderate error of BER = 10
when TXOP is 20 ms. In the case of BER = 0, as the payload size increases, the RTS/CTS method outperformed basics access method because of the high probability of collision in the case of basic access mode. Similar results were observed in the case of BER = 10
. As the payload size increases, the probability of error also increases. The results verify that in the error-prone channel, larger payload size is not suitable [
11]. Because HOB size of RTS/CTS access mode is much smaller as compared to basic access mode, RTS/CTS method exhibited better performance in the presence of channel error. The important observation is that the proposed method always gave better throughput than the original method. The reason for the performance improvement is because of decrement in the control packet overheads as compared to the original method.
Figure 5.
Throughput for n = 10, r’ = 1 Mbps, r = 11 Mbps.
Figure 5.
Throughput for n = 10, r’ = 1 Mbps, r = 11 Mbps.
To observe the performance for higher data rates under ideal channel condition, the basic rate, and data rate were set to 54 Mbps and 300 Mbps, respectively as in IEEE 802.11n. The obtained results are shown in
Figure 6. As shown in the figure, the performance of the proposed BA scheme improves with the increase in data rate.
Figure 6.
Throughput for n = 10, r’ = 54 Mbps, r = 300 Mbps, and BER = 0.
Figure 6.
Throughput for n = 10, r’ = 54 Mbps, r = 300 Mbps, and BER = 0.