Dynamic Cipher Puzzle for Efficient Broadcast Authentication in Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Works
3. Cipher Puzzle Overview
3.1. One-Way Key Chain
3.2. Puzzle Solution
3.3. Digital Signature
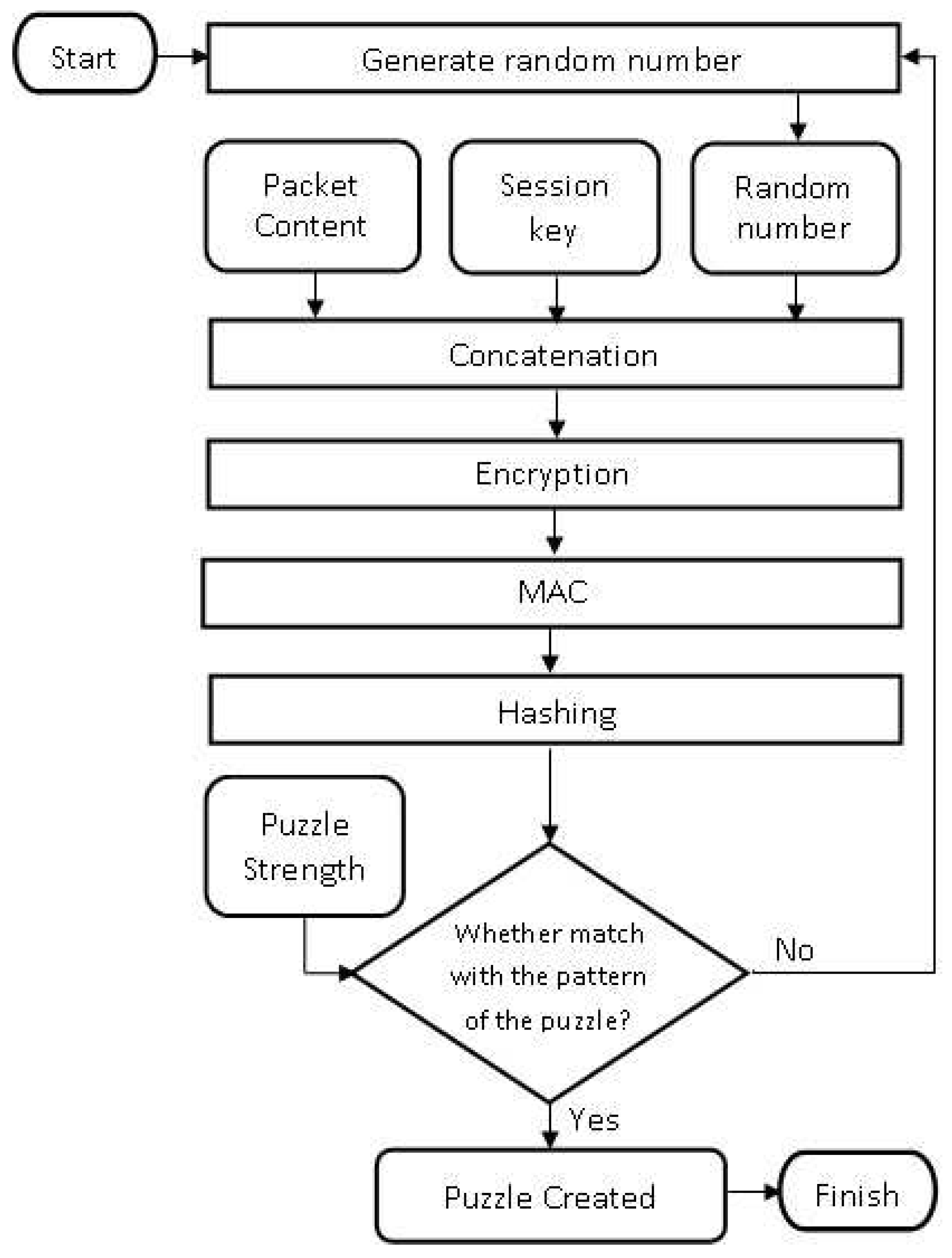
4. Dynamic Cipher Puzzle (DCP)
4.1. Offline Initialization
4.2. Real-Time Communication
| Algorithm 1: Dynamic Cipher Puzzle constructor at the sender-side |
 |
| Algorithm 2: Dynamic Cipher Puzzle verification at the receiver-side |
 |
5. Implementation and Performance Evaluation
5.1. Simulation Results
5.1.1. Zero Solution Probability
5.1.2. Mean Number of Hash Iterations
5.1.3. Standard Deviation
5.1.4. Maximum Number of Hash Iterations
5.2. Experimental Results
5.2.1. Resource Consumption for Tag Verification
5.2.2. Resource Consumption for Full Verification
6. Security Analysis
6.1. Puzzle Security
- Setup is the setup algorithm that on input outputs atr ,
- Gen is the generation algorithm which on input L randomly chosen , computes and outputs puzzle instance puz
- Find (puz is the solving algorithm that on input puz and the number of steps iteratively samples at most values sol until ETMsol
- Ver(puz, sol) is the algorithm that takes puz, sol as input and return one if ETMsol and zero otherwise.
6.2. Adversary Model
- C-1.
- is able to control of the exchange message between sender or administrator, base station and sensor nodes.
- C-2.
- can enlist all the combination item of tag within polynomial time, where , and refer to the space of , current puzzle-strength (L) and previous puzzle-strength(), respectively.
- C-3.
- can compromise and reveal parameters stored in several sensor nodes.
- C-4.
- can create and transmit fake puzzle as if a legitimate user.
6.2.1. Probability Attack
- Step 1:
- Pick a combination from dictionary , and .
- Step 2:
- Compute .
- Step 3:
- Validate correctness of by checking if the first bits of the and the intercepted are the same.
- Step 4:
- Repeat Steps 1–3 until the correct combination is found to form a valid .
- Step 5:
- Calculate from the hash result of the concatenation of the first bits of the intercepted and the first () bits of the rest intercepted message after .
- Step 6:
- Calculate the predicted position of encrypted message, session key and puzzle solution as in the rest of the intercepted message after .
- Step 7:
- Validate correctness of the puzzle solution by checking if the ETM of the using the last stored session key and the are the same.
6.2.2. Signature-Based DoS Attacks
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Eldefrawy, M.H.; Khan, M.K.; Alghathbar, K.; Cho, E.S. Broadcast Authentication for Wireless Sensor Networks Using Nested Hashing and the Chinese Remainder Theorem. Sensors 2010, 10, 8683–8695. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Zheng, X.L.; Wan, M. A Survey on Data Dissemination in Wireless Sensor Networks. J. Comput. Sci. Technol. 2014, 29, 470–486. [Google Scholar] [CrossRef]
- Grover, K.; Lim, A. A survey of broadcast authentication schemes for wireless networks. Ad Hoc Netw. 2015, 24, 288–316. [Google Scholar] [CrossRef]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security protocols for sensor networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Liu, D.; Ning, P. Multilevel μ TESLA: Broadcast Authentication for Distributed Sensor Networks. ACM Trans. Embed. Comput. Syst. 2004, 3, 800–836. [Google Scholar] [CrossRef]
- Groza, B. Broadcast authentication with practically unbounded one-way chains. J. Softw. 2008, 3, 11–20. [Google Scholar] [CrossRef]
- Kwon, T.; Hong, J. Secure and efficient broadcast authentication in wireless sensor networks. IEEE Trans. Comput. 2010, 59, 1120–1133. [Google Scholar] [CrossRef]
- Liu, A.; Ning, P. TinyECC: A Configurable Library for Elliptic Curve Cryptography in Wireless Sensor Networks. In Proceedings of the 7th International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 245–256. [Google Scholar] [CrossRef]
- Ren, K.; Yu, S.; Lou, W.; Zhang, Y. Multi-user broadcast authentication in wireless sensor networks. IEEE Trans. Veh. Technol. 2009, 58, 4554–4564. [Google Scholar] [CrossRef]
- Liu, Y.; Li, J.; Guizani, M. PKC based broadcast authentication using signature amortization for WSNs. IEEE Trans. Wirel. Commun. 2012, 11, 2106–2115. [Google Scholar] [CrossRef]
- Cheng, C.Y.; Lin, I.C.; Huang, S.Y. An RSA-Like Scheme for Multiuser Broadcast Authentication in Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 11, 743623. [Google Scholar] [CrossRef]
- Dong, Q.; Liu, D.; Ning, P. Providing DoS resistance for signature-based broadcast authentication in sensor networks. ACM Trans. Embed. Comput. Syst. 2013, 12, 1–26. [Google Scholar] [CrossRef]
- Tan, H.; Ostry, D.; Zic, J.; Jha, S. A confidential and DoS-resistant multi-hop code dissemination protocol for wireless sensor networks. Comput. Secur. 2013, 32, 36–55. [Google Scholar] [CrossRef]
- Aura, T.; Nikander, P.; Leiwo, J. DOS-resistant authentication with client puzzles. In International Workshop on Security Protocols; Springer: Berlin/Heidelberg, Germany, 2000; pp. 170–177. [Google Scholar]
- Ning, P.; Liu, A.N. Mitigating DoS Attacks against Broadcast Authentication in Wireless Sensor Networks. ACM Trans. Sens. Netw. 2008, 4, 1–35. [Google Scholar] [CrossRef]
- Du, X.; Chen, H.H. Defending DoS Attacks on Broadcast Authentication in Wireless Sensor Networks. In Proceedings of the 2008 IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 1653–1657. [Google Scholar] [CrossRef]
- Dong, Q.; Liu, D. Pre-Authentication Filters: Providing DoS Resistance for Signature-Based Broadcast Authentication in Sensor Networks. In Proceedings of the First ACM Conference on Wireless Network Security, Alexandria, VA, USA, 31 March–2 April 2008; pp. 2–12. [Google Scholar]
- Afianti, F.; Wirawan, I.; Suryani, T. Dynamic Message Puzzle as Pre-Authentication Scheme in Wireless Sensor Networks. Int. J. Adv. Sci. Eng. Inf. Technol. 2018, in press. [Google Scholar]
- Wijaya, D.R.; Sarno, R.; Zulaika, E.; Sabila, S.I. Development of mobile electronic nose for beef quality monitoring. Procedia Comput. Sci. 2017, 124, 728–735. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef] [Green Version]
- Afianti, F.; Wirawan, I.; Suryani, T. Filtering methods for broadcast authentication against PKC-based denial of service in WSN: A survey. In Proceedings of the Fifth International Conference on Wireless and Optical Communications, Singapore, 7–9 July 2017; Volume 10465, p. 1046503. [Google Scholar] [CrossRef]
- Meulenaer, G.D.; Gosset, F.; Standaert, F.X.; Pereira, O. On the Energy Cost of Communication and Cryptography in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Wireless and Mobile Computing (WIMOB’08), Avignon, France, 12–14 October 2008; pp. 580–585. [Google Scholar] [CrossRef]
- Sethi, M.; Arkko, J.; Keranen, A. End-to-end Security for Sleepy Smart Object Networks. In Proceedings of the IEEE 37th Conference onLocal Computer Networks Workshops (LCN Workshops), Clearwater, FL, USA, 22–25 October 2012; pp. 964–972. [Google Scholar]
- Xu, A.; Li, M.; Cai, J.; Xue, N.; Zhang, J.; Liu, D.; Craig, P.; Huang, X. Improving Efficiency of Authenticated OpenFlow Handshake using Coprocessors. In Proceedings of the IEEE 8th International Conference on Information Technology in Medicine and Education (ITME), Fuzhou, China, 23–25 December 2016; pp. 576–580. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef] [Green Version]
- Cao, X.; Kou, W.; Dang, L.; Zhao, B. IMBAS: Identity-based multi-user broadcast authentication in wireless sensor networks. Comput. Commun. 2008, 31, 659–667. [Google Scholar] [CrossRef]
- Jech, T. Set Theory; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-Factor Authentication with Security beyond Conventional Bound. IEEE Trans. Dependable Secur. Comput. 2018, 15, 708–722. [Google Scholar] [CrossRef]
- Xu, G.; Qiu, S.; Ahmad, H.; Xu, G.; Guo, Y.; Zhang, M.; Xu, H. A multi-server two-factor authentication scheme with un-traceability using elliptic curve cryptography. Sensors 2018, 18, 2394. [Google Scholar] [CrossRef] [PubMed]
- Groza, B.; Warinschi, B. Cryptographic puzzles and DoS resilience, revisited. Des. Codes Cryptogr. 2014, 73, 177–207. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Jan, M.A.; Nanda, P.; He, X.; Liu, R.P. A Sybil Attack Detection Scheme for a Centralized Clustering-based Hierarchical Network. In Proceedings of the Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 318–325. [Google Scholar]
- Zheng, Z.; Liu, A.; Cai, L.X.; Chen, Z.; Shen, X.S. Energy and Memory Efficient Clone Detection in Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2016, 15, 1130–1143. [Google Scholar] [CrossRef]
- Al-Riyami, A.; Zhang, N.; Keane, J. An Adaptive Early Node Compromise Detection Scheme for Hierarchical WSNs. IEEE Access 2016, 4, 4183–4206. [Google Scholar] [CrossRef]
















| Notation | Description |
|---|---|
| Hash iteration | |
| Mean of hash iteration | |
| Length of message | |
| Number of packet transmissions | |
| Signature | |
| Session key for index | |
| Puzzle solution for index | |
| L | Puzzle-strength |
| Maximum value of puzzle-strength | |
| Number of keys | |
| Hash Function | |
| Success probability in the puzzle-strength equal to i | |
| Success probability of the system | |
| Failure probability of the system | |
| Zero solution probability | |
| Number of hash iteration in the DCP | |
| Standard deviation of the puzzle-strength set |
| No | Description | Client Puzzle [14] | MSP [15] | Cipher Puzzle [13] |
|---|---|---|---|---|
| 1 | The role of parties in puzzle generation | Server creates and verifies the puzzle; Client solves the puzzle from the server. | Sender creates and solves the puzzle; Receiver verifies the puzzle. | Sender creates and solves the puzzle; Receiver verifies the puzzle. |
| 2 | Security property guarantee | Authentication based on puzzle and main signature. | Authentication based on puzzle and main signature. | Authentication based on puzzle and main signature; Confidentiality based on encryption of the message content. |
| 3 | Pattern of the puzzle solution | Consecutive zero bits. | Consecutive zero bits. | Hash result of the message’s signature. |
| 4 | Procedure composition | Hash function and main signature (plaintext packet content). | Hash function and main signature (plaintext packet content). | Hash function, encrypt-then-MAC to provide high security level on the transmitted packet, and main signature. |
| 5 | Session key | - | One-way key chain. | One-way key chain. |
| Area | Success Probability on Puzzle Strength | Parameter | ||
|---|---|---|---|---|
| L = 1 | L = 2 | Optimum | Worst | |
| I | LOW | LOW | , | |
| II | HIGH | LOW | ||
| III | LOW | HIGH | ||
| IV | HIGH | HIGH | , | |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Afianti, F.; Wirawan; Suryani, T. Dynamic Cipher Puzzle for Efficient Broadcast Authentication in Wireless Sensor Networks. Sensors 2018, 18, 4021. https://doi.org/10.3390/s18114021
Afianti F, Wirawan, Suryani T. Dynamic Cipher Puzzle for Efficient Broadcast Authentication in Wireless Sensor Networks. Sensors. 2018; 18(11):4021. https://doi.org/10.3390/s18114021
Chicago/Turabian StyleAfianti, Farah, Wirawan, and Titiek Suryani. 2018. "Dynamic Cipher Puzzle for Efficient Broadcast Authentication in Wireless Sensor Networks" Sensors 18, no. 11: 4021. https://doi.org/10.3390/s18114021





