1. Introduction
The development of payment technology in recent years is strongly simulated by the advancement of information technology and the high throughput of network bandwidth delivered by telecommunication networks and individual Wi-Fi hotspots. According to the survey performed by European Central Bank [
1], people are becoming accustomed with non-cash payment systems (either using credit or debit cards). The growth of non-cash payment systems is further driven by the integration of credit card payments with smartphone systems. Apple Pay [
2], Android Pay [
3], and Samsung Pay [
4] are several examples of payment systems that integrate non-cash payment systems into a smartphone.
In a traditional non-cash payment system, the customer’s credit card information will be sent to the back-end payment server through an Electronic Data Capture (EDC) machine by swiping the credit card at the corresponding machine slot. For a non-cash mobile payment system, all sensitive information of a credit card is stored inside the corresponding smartphone. In general, the modern non-cash payment system utilizes the Near Field Communication (NFC) interface and embedded module of a smartphone to accomplish data exchange between the smartphone and the Point-of-Sales (POS) device [
5,
6]. Although NFC technology offers short service-processing time, ease of use for the customer, and simplified payment process, deployed NFC implementations on smartphone suffer from widespread non-standard payment protocols. In other words, smartphone companies only support their home-grown NFC-enabled payment systems. In consequence, merchant stores have to install multiple NFC readers to support the various proprietary payment protocols. In addition, the prices of smartphones with NFC modules are generally much higher than those of ordinary ones as the NFC module is a privileged feature for high-end smartphones and it generates extra manufacturing costs.
The development of Bluetooth technology opens up another pathway to deliver new mobile payment systems. New Bluetooth Low Energy (BLE) technology requires less energy consumption than classic Bluetooth technology [
7], which allows energy-limited BLE-devices to communicate with nearby BLE devices with much less energy consumption. As most smartphones support BLE technology and are equipped with BLE communication modules, it is natural to construct a mobile payment system using BLE technology. Despite the advantages offered by BLE technology, the communication channel between the BLE-enabled smartphone and the BLE-enabled POS device has to be secured when sensitive data such as credit card information and payment amount is transmitted through the BLE-based mobile payment system.
For a BLE-based mobile payment system, it is necessary to have a robust security mechanism to defend against attacks through the payment transaction. One essential security criteria for the system is to support mutual authentication. Prevention of session hijacking is another important security requirement for mobile payment systems. A simple solution is to utilize a Bluetooth jammer [
8]; however, the usage of Bluetooth jammers may cause inconvenience to customers since a Bluetooth jammer will disturb or interfere with BLE signals transmitted from other customers’ devices within its signal coverage area. To enhance security strength of user authentication, multi-factor authentication schemes have emerged in recent years. For example, face recognition technology and Bluetooth beacon technology were adopted together to construct a two-factor authentication scheme for the proposed Zero-Effort mobile payment system [
9]. As facial recognition scheme generally involves with sophisticated computation and suffers with lower identification accuracy, the Zero-Effort system requires more computing resources at the backend server and consumes more time to establish an authenticated session.
In this paper, a new system design for a BLE-based mobile payment system is introduced. To secure the proposed system, a BLE-based user (customer) authentication protocol with mutual authentication features is invented. In addition, the proposed payment system utilizes Bluetooth beacon technology to accurately identify whether a customer has stepped into the payment-enabled area. Once a customer is detected in the payment-enabled area, the position information of the customer generated from the indoor positioning scheme will be adopted as a part of the user (customer) secret. The position information of customers is used to ensure the user presence during payment process. Based on the proposed authentication protocol, the user secret will be used later to authenticate the user and establish a payment session. In consequence, the proposed payment system supports mutually authenticated payment sessions for customers. In addition, an indoor positioning scheme is used to precisely identify a checking-out customer based on his position. This scheme is adopted to prevent session hijacking by malicious attackers who are not present in the payment-enabled area. Moreover, the authentication protocol dynamically constructs a session key based on the current user position information, the identity of the user’s smartphone, and the identity of the POS counter.
Based on the proposed system environment, there is a payment-enabled area in front of each POS terminal counter. Within each area, four Bluetooth beacons such as iBeacon [
10] and Estimote Beacon [
11] are deployed and installed along the frontage and rear of consecutive counters. When a customer steps into a payment-enabled area and is ready to pay for his purchases, he should activate the payment App installed in his smartphone. Then the App will drive the smartphone to scan for the Bluetooth beacon signals in the payment-enabled area. The smartphone (or the App) will capture beacon signals from three or four different beacon tags and use them as the input data to invoke the indoor positioning algorithm to determine the exact customer location. Once the App confirms the smartphone is inside the payment-enabled area, the App will connect with the Trusted Third Party (TTP) server and send the captured beacon signals through secure channel to retrieve a unique user secret, which is generated from the beacon signals received by TTP. The user secret will be used by the App to connect with the POS terminal associated with the identities of detected beacon tags in order to dynamically construct a session key based on a modified version of Juggling Password Authenticated Key Exchange (J-PAKE) protocol [
12,
13]. The contributions of this paper are as follows:
A new mobile payment system design using an indoor positioning-based service is proposed. In the proposed system, Bluetooth beacon technology is used to determine the current position of a checking-out customer. Based on the detected customer position, the system determines whether the customer could legitimately connect with the POS terminal corresponding to the target payment-enabled area through BLE technology, and perform check-out actions.
An indoor positioning-based authentication protocol using BLE technology is invented to support the proposed mobile payment system. Instead of adopting PKI-based authentication algorithms for protocol design, Shamir secret sharing and password-based key exchange algorithm are used to derive a key exchange protocol with mutual authentication feature.
Security analysis on the proposed protocol is conducted and a prototype is implemented to evaluate the performance of the proposed system. Based on the security analysis results, the proposed system defends against the impersonation attack, the man-in-the-middle attack, and the replay attack, and supports mutual authentication and session key security. The prototype based on BLE 4.2 takes approximately 10 s in average to accomplish one user authentication.
The remainder of this paper is organized as follows: Bluetooth technology and related literature on mobile payment systems are introduced in
Section 2. The proposed design of our indoor positioning-based mobile payment system is presented in
Section 3.
Section 4 describes the proposed mobile payment authentication protocol.
Section 5 addresses the prototype implementation and performance measurement. Security analysis for the proposed authentication protocol is presented in
Section 6. Finally, the concluding remarks are presented in
Section 7.
4. Proposed Mobile Payment Authentication Protocol
In this section, the proposed indoor positioning-based authentication protocol is addressed. There are three phases in the proposed authentication protocol: initialization phase, session key construction phase, and authentication phase. Notations used in this paper are listed in
Table 1.
4.1. Initialization Phase
Assume the customer activates the payment App before he walks to one of the BLE-enabled POS terminals. Once the customer enters the payment area of a BLE-based POS terminal, the payment App starts to get the session secret . First, the customer’s wearable device observes the surrounding environment to obtain a set of information broadcast by the four beacon tags associated with the POS terminal. Then, the collected information is sent from the customer’s wearable device to the TTP server.
In order to construct the secret
, the TTP server utilizes Shamir secret sharing method [
38] to identify which POS terminal that the customer’s wearable device could connect to. In this phase, both the user’s (customer) wearable device and the POS terminal will receive a secret
from the TTP server.
Figure 3 shows the initialization protocol in the proposed system.
The initialization phase is described as follows:
Step 1: User Wearable Device → TTP Server:
After the customer’s wearable device collects a set of information broadcast from beacon tags associated with the POS terminal , the wearable device generates a random value . The wearable device encrypts this message using the symmetric key . Then the wearable device will send the encrypted message to the TTP server along with the device’s identifier .
Step 2: Internal processing at TTP server
After receiving the encrypted message from the customer’s wearable device, the TTP server will decrypt it using to obtain and . Based on the received set of beacon information , the TTP server uses Shamir secret sharing construction function to obtain the corresponding POS terminal secret. By using the computed POS terminal secret, the TTP server searches its database to find the corresponding POS terminal identity . Afterwards, the TTP server constructs a user secret for the current session. After computing , the TTP server will encrypt two messages and . Then, the TTP server sends both and along with the identity of the TTP server to the user’s wearable device and the POS terminal as shown in Step 2a and Step 2b.
Step 2a: TTP Server → User Wearable Device:
The TTP server encrypts this message using the symmetric key of the customer’s wearable device . The encrypted message is sent to the customer’s wearable device along with the identity of TTP server . After the customer’s wearable device receives from the TTP server, it will be decrypted using to obtain the values of and , in which both values will be temporarily stored in the user’s wearable device.
Step 2b: TTP Server → POS:
The TTP server encrypts this message using the corresponding POS’ symmetric key . The encrypted message is sent to the POS terminal along with the identity of TTP server . After the POS terminal receives , it will be decrypted using POS terminal’s symmetric key to obtain the values of and , in which both values will be temporarily stored in the POS terminal.
4.2. Session Key Construction Phase
At the end of the initialization phase, both the customer’s wearable device and the POS terminal will automatically enter the session key construction phase. In the beginning of session key construction phase, the customer’s wearable device initiates a BLE connection to the POS terminal using the user secret and the MAC address of POS terminal . After the POS terminal receives the connection request from the customer’s smartphone, it will verify the customer’s wearable device and the secret data sent by the customer’s wearable device. Then both the POS terminal and the customer’s smartphone use Zero Knowledge Proof functions to individually construct partial secrets which will be utilized to construct a full session key later. Then, these partial secrets will be exchanged between the customer’s wearable device and the POS terminal. With the received partial secret information, both sides could successfully construct a full session key for the current payment transaction.
To practically execute this session key construction protocol, both the customer’s smartphone and the POS terminal should have pre-installed the common parameters
, where
denotes a subgroup of cyclic multiplicative group
and g is the generator of G. In order to construct a unique session key, a modified J-PAKE protocol [
12,
13] is derived and utilized in the session key construction phase. The modified J-PAKE protocol uses a unique and dynamic secret data instead of static password used in original J-PAKE protocol.
Figure 4 illustrates the modified J-PAKE protocol used in the proposed session key construction phase:
Step 1: Each party generates two random numbers based on the constructor and two result values by applying the Zero Knowledge Proof function. Then both parties exchange the newly generated Zero Knowledge Proof.
The user’s smartphone generates two random values ( and ) and computes , , and 2 zero knowledge proofs and . At the same time, the POS terminal also generates two random values ( and ) and computes , , and 2 zero knowledge proofs , and . Next, the user’s smartphone sends a message to the POS terminal. Likewise, the POS terminal sends a message to the user’s smartphone.
Step 2: Each party verifies the received Zero Knowledge Proof and constructs a new Zero Knowledge Proof based on the previously exchanged proof. Then both parties exchange the newly generated Zero Knowledge Proof again.
Both the user’s smartphone and the POS terminal verify the received zero knowledge proofs in the messages and , respectively. Once the received zero knowledge proofs have been verified, the user’s smartphone computes the value and its zero knowledge proof . Meanwhile, the POS terminal computes the value and its zero knowledge proof . Afterward, the user’s smartphone sends a message to the communicating POS terminal. Similarly, the POS terminal sends a message to the user’s smartphone.
Step 3: Each party verifies the received Zero Knowledge Proof and constructs a new session key by applying the random string extension function with the public parameter , and the calculated value . The calculated value is constructed from user secret and the verified random values from both parties.
Both the user’s smartphone and the POS terminal verify the received values of zero knowledge proofs in the messages and , respectively. After the received zero knowledge proof values have been verified, the user’s smartphone calculates a secret value and the POS terminal calculates a secret value . Both the user’s smartphone and POS terminal computed value should be equivalent based on the characteristic of Zero Knowledge Proof. The secret value is used to compute session key and nonce . Both parties will temporarily store the generated session key and the nonce for later usage during the authentication phase.
4.3. Authentication Phase
Once the customer confirms to pay his purchase through the payment App interface, the payment App initiates the authentication phase immediately before transmitting the user’s payment information to the backend payment-processing server. The proposed authentication protocol is shown in
Figure 5.
Step 1: User Wearable Device → POS:
First, the customer’s smartphone generates a random value and uses to compute and . The newly computed is used as the hash key for the following hash computation . Then the smartphone will send both and to the POS along with the smartphone’s identity .
Step 2: POS → User Wearable Device:
After the POS receives and , it generates a random value . Afterwards, the POS will calculate and use it to compute the hash key . After computing , the POS compares the received value with the calculated value to verify the freshness and the correctness of the session key . If the verification test passes, then the POS will calculate the value . Otherwise, the authentication process will be aborted. After computing , the POS calculates another hash key and uses it to generate a hashed value . Afterwards, the values and are sent to the customer’s smartphone along with the POS terminal identity .
Step 3: User Wearable Device → POS:
When the smartphone receives and , it will compute and . After computing and , the customer’s smartphone will compare the received value with the hashed value . If both values are equivalent, then the customer’s smartphone computes a new hash key . Otherwise the authentication process is aborted. After computing a new hash key , the customer’s smartphone will calculate the encrypted message and calculate a new hash key . Notice that is a message containing information of the current payment transaction and is the current timestamp generated by the user’s smartphone. The newly computed hash key is used to compute . Next, both the hashed value and the encrypted message are sent to the POS.
Step 4: Internal processing at POS
In the final step of the authentication process, the POS creates a decryption key after receiving both and from the customer’s smartphone. Afterwards, the POS will decrypt the received using to obtain and . After obtaining , the POS will check whether the value of is within an acceptable time duration based on its own system clock. Otherwise, the process will be aborted. Then the POS will compute a new hash key and use it to compare the received hash value with the computed hash value . If both values are equivalent, then the POS will send the message that contains customer’s payment information to the backend payment-processing server.
5. Prototype Implementation and Experiments
A prototype of the proposed mobile payment system was implemented. The POS terminal App prototype was deployed on a Samsung Galaxy S5 phone, while the mobile payment App prototype was installed on a Samsung Galaxy S6. For the Bluetooth beacon tag, iBeacon-based tags are used in the prototype. Other Bluetooth beacon protocols such as Eddystone, AltBeacon, and FatBeacon could be utilized to build similar mobile payment prototype systems. All devices used in the experiments and some of their features are listed in
Table 2.
5.1. Prototype Implementation
In our prototype, four Estimote proximity beacon tags are placed separately in each corner of a square surface with the distance between each neighboring beacon tag set to 75 cm by 75 cm.
Figure 6 shows a photograph of practical implementation of the proposed mobile payment system. As shown in
Figure 6a, each beacon tag is placed on a horizontal surface at the same height. In addition, each beacon tag is configured as follows:
Advertising interval: 300 ms
Transmitting power (Tx): −20 dBm
Maximum signal range: up to 3.5 m (11.48 ft.).
Notice that the maximum signal range of a Bluetooth beacon tag is up to 3.5 m, however, the range could be set to 1 m (3.28 ft.) by setting the signal transmitting power of the beacon tag. Google’s Firebase platform is used to imitate the TTP server. In addition, the prototype of payment App includes a JSON file that contains API key to access the database in Firebase.
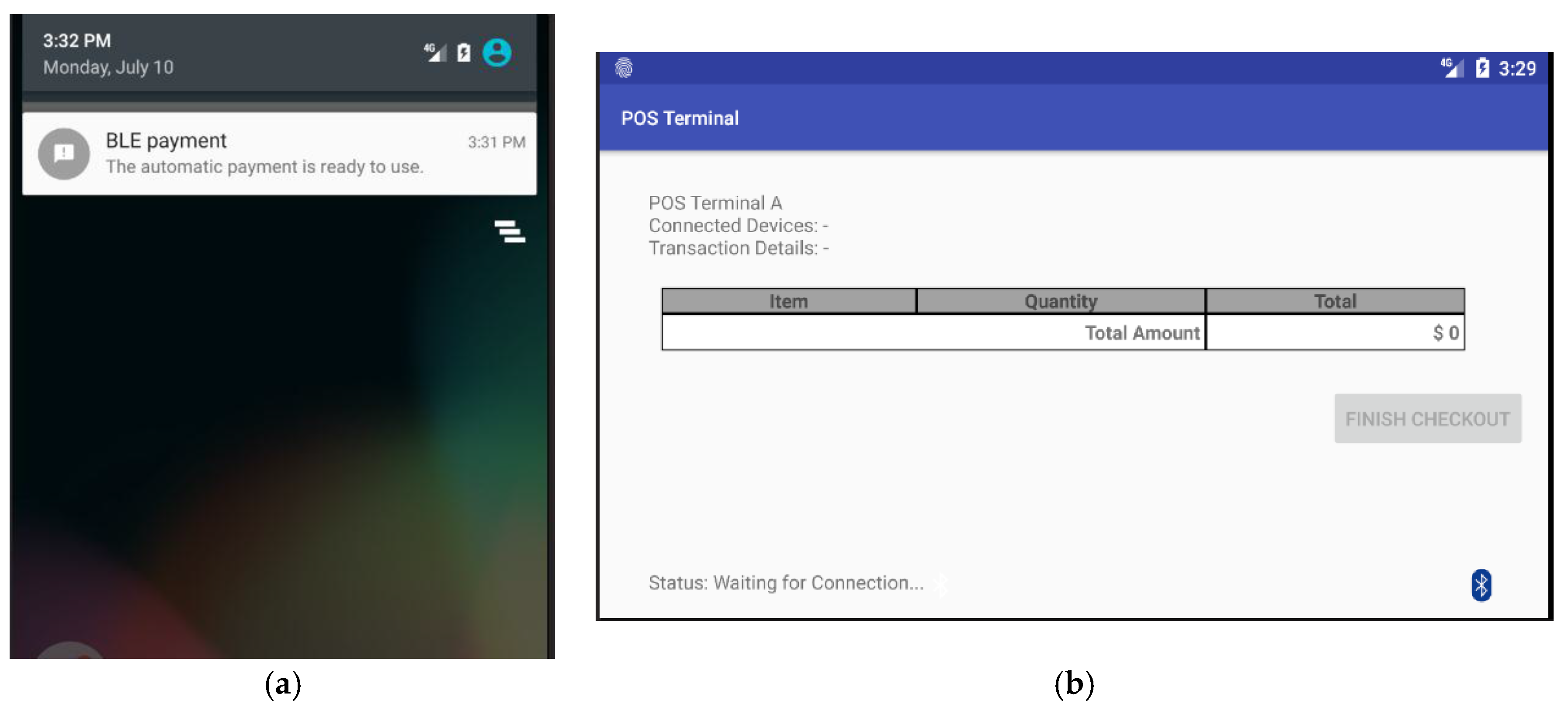
Figure 7a shows a display of notification message sent by the payment App, which is executed as an agent process in the customer’s smartphone.
Figure 7b shows the default display of POS terminal while it is waiting for incoming BLE connection from the payment App.
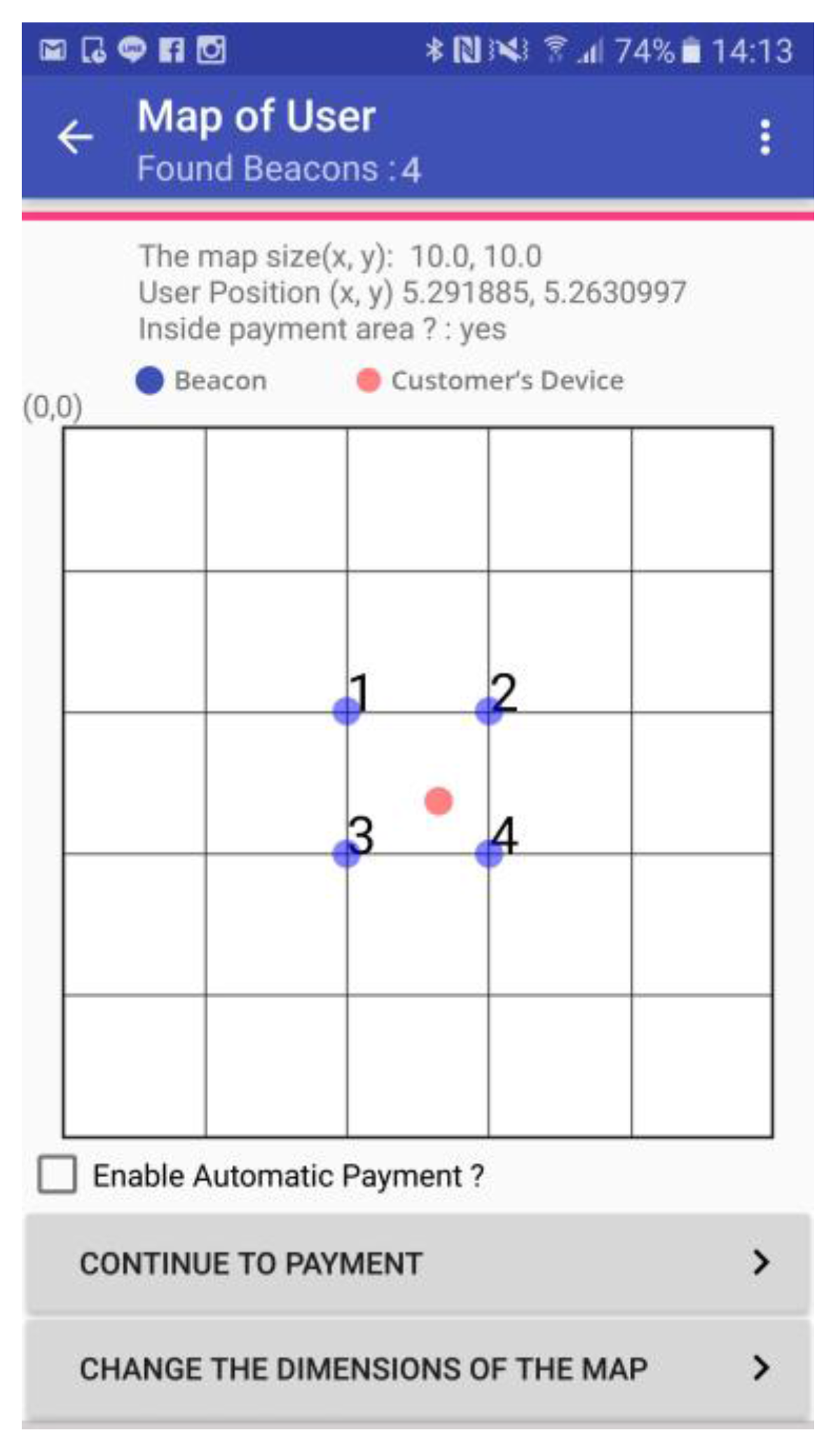
During our experiments, the POS terminal (Samsung Galaxy S5) is placed beside the payment-enabled area composed by the four beacon tags. In addition, a position-monitoring App is developed to detect whether the position of the customer’s smartphone is located in the payment-enabled area. The position-monitoring App shown in
Figure 8 displays the position of the user’s device against the positions of four beacon tags. The blue dots shown in the map represent the beacon tags, while the red dot indicates the position of the customer’s smartphone.
Two indoor positioning algorithms are implemented in the payment App: least squares algorithm and trilateration algorithm. Once the customer enters the payment-enabled area, the user’s smartphone (or the payment App) will automatically capture the broadcast signals from the four beacons tags. This event invokes the proposed mobile payment system. Afterwards, the prototype payment App executes the indoor positioning algorithm to determine the user device position. After the payment App obtains the user secret constructed by the TTP server, the payment App will establish a BLE connection to the POS terminal which also receives the same user secret from the TTP server.
After the customer’s smartphone establishes a BLE connection to the POS terminal, both parties start to construct the session key individually.
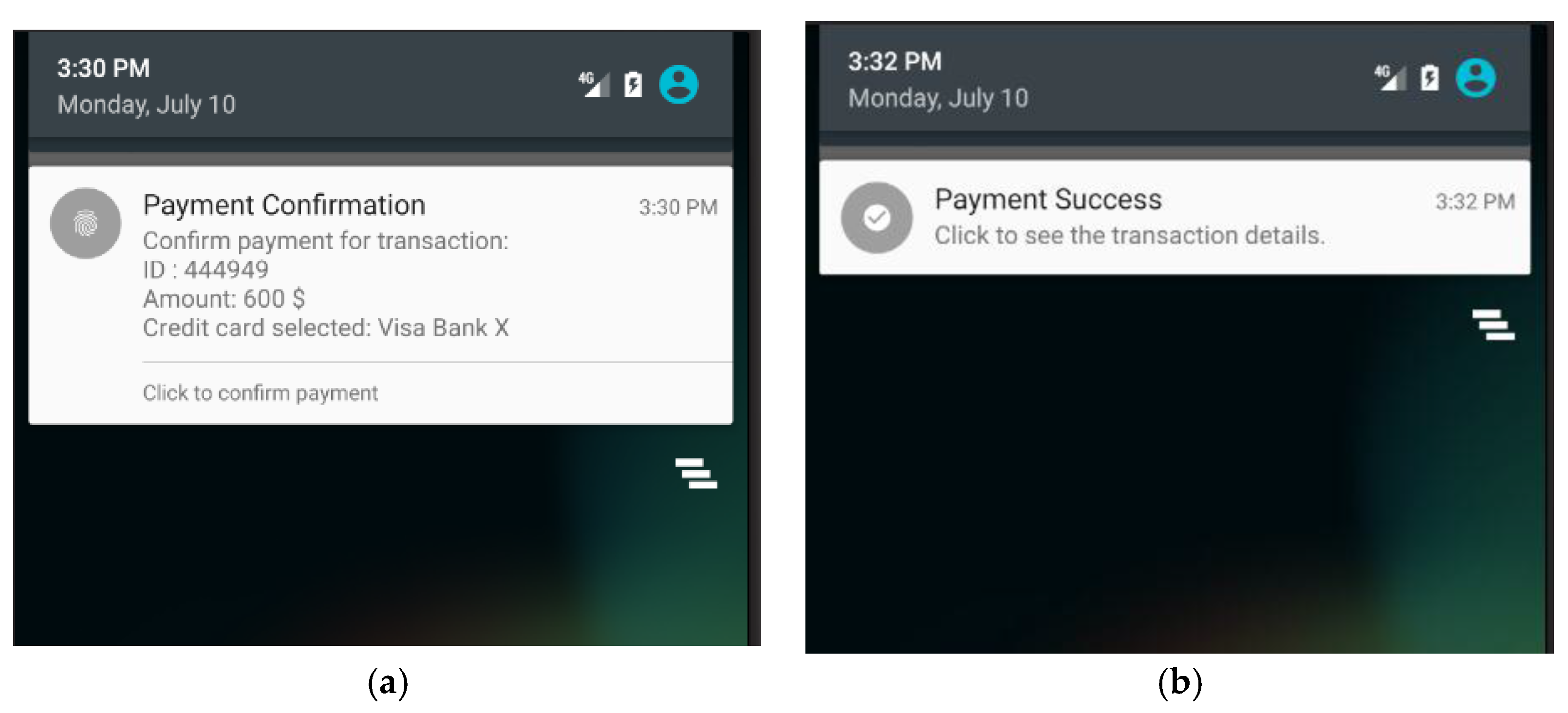
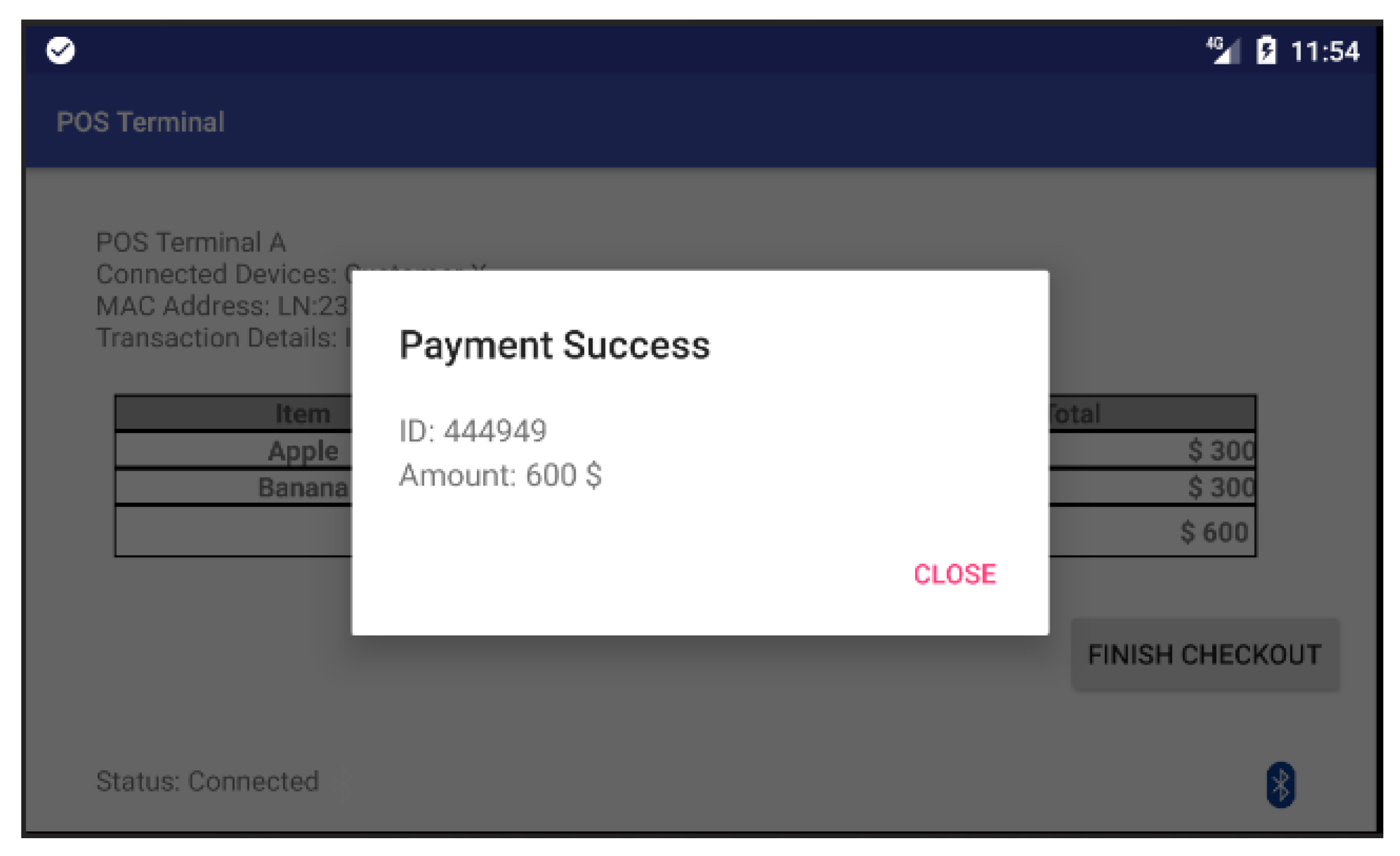
Figure 9 shows the screen of POS terminal in which the POS terminal has already connected with the customer’s smartphone and ready to execute the payment process. When the customer clicks on the “Finish checkout” button in the touch screen of the POS terminal, the POS terminal will send a payment-confirmation message to the payment App as shown in
Figure 10a. Once the customer receives the payment-confirmation message and clicks the payment confirmation button in the payment App, the authentication phase of the proposed protocol is executed to mutually authenticate both the customer’s smartphone and the corresponding POS terminal. Then, the payment transaction process is activated by transmitting session-key-encrypted payment transaction messages from the payment App to the POS terminal. Afterwards, both the payment App and the screen of the POS terminal will display a notification message regarding the current payment transaction as shown in
Figure 10b and
Figure 11.
5.2. Experiment Results
Several experiments are conducted on the prototype to assess the accuracy of the indoor positioning functionality and the protocol’s performance in terms of time consumption. The location-positioning accuracy of both least square algorithm and trilateration algorithm implemented in the payment App are evaluated in terms of the distance difference between the real position and the detected position of the customer’s smartphone. The accuracy rate for a target indoor positioning algorithm is defined by the following formula . Variable denotes the observation region, which has the size of payment-enabled area (i.e., 75 cm by 75 cm in our experimental case). The total number of experiments is symbolized with variable . Variable represents the prediction result of the -th experiment based on the observation region , in which the value of is set to 1 if the real position of the user’s smartphone is correctly predicted by the selected indoor-positioning algorithm in terms of whether the user’s smartphone is located within the observation region or not. The value of is set to 0 if the real position of the user’s smartphone is wrongly predicted by the selected indoor-positioning algorithm. The accuracy rate is defined as the number of times for correctly predicting the position of the user’s smartphone over the total number of experiment times. To evaluate the performance of the prototype, the time consumption to establish a session is measured and a detailed time distribution for each phase within a session is analyzed.
As a user may accidentally trigger the payment App installed on his/her smartphone while he/she is still shopping around in the store, it is necessary to adopt indoor-positioning sensor technology to precisely identify the user’s location in order to confirm user’s intention to check-out. In addition, by adopting indoor-positioning sensor technology the proposed mobile payment system does not need to use a Bluetooth jammer to secure the user’s Bluetooth connection with the POS counter. In the proposed mobile payment system, once the user steps outside the payment-enabled area, then the payment App will directly terminate the payment process and abort the current session. In order to provide secure payment functionalities, the proposed mobile payment system heavily relies on the accuracy of indoor positioning sensor technology.
In order to assess the accuracy of indoor positioning function, thirty seven times of position-detection experiments for customer’s smartphone are conducted. In each experiment, the payment App will collect around thirty points of predicted position for the user smartphone based on the selected indoor positioning algorithm. After that, the payment App calculates the average value from these collected points and determines whether the user smartphone is currently located inside the payment area or not.
The experimental results using a least squares algorithm are shown in
Figure 12. The size of the square area shown in
Figure 12 is 75 cm by 75 cm. In those experiments, two test strategies are used to detect the position of the customer’s smartphone: one without applying any filter and the other using the average filter. Note that the average filter indicates the averaged position value of all the computed positions of the customer’s smartphone is calculated and returns as the final estimated position. Based on the experiment results, it is clear that the indoor-positioning function implemented with the least squares algorithm plus the average filter performs better than the one without applying any filter. The error of distance measurement between the real device position and the detected device position is around 10 cm to 14 cm.
Table 3 shows the experiment data from 148 experiments using least squares algorithm. Based on the experiment data, the least squares algorithm-based positioning function associated with the average filter has 97.29% of accuracy rate. The least squares algorithm-based positioning function without any filter can only achieve 93.24% of accuracy rate.
The experimental results using a trilateration algorithm are shown in
Figure 13. The size of square area shown in
Figure 13 is 75 cm by 75 cm. Similarly, two test strategies, one without applying any filter and the other using the average filter, are applied. In general, the positioning function using the trilateration algorithm does not produce better results than the one using the least squares algorithm. The error of distance measurement between the real device position and the detected device position is around 25–35 cm.
Table 4 shows the experiment data from 148 experiments in each case using trilateration algorithm. Based on the experiment data, the trilateration algorithm-based positioning function without any filter has 78.37% of accuracy rate. The trilateration algorithm-based positioning function associated with average filter can only achieve 72.97% of accuracy rate.
When the prototype is executed to establish a session, almost 64% of the time is consumed during the session key construction phase. Meanwhile, the initial BLE connection process such as the BLE service discovery and pairing process consumes 29% of the total processing time, and the remaining 7% of the time is used for the authentication phase.
Figure 14 shows the time consumption of the prototype to establish one payment session in fourteen experiments.
Within the same set of experiments, the construction process of 80-bits session key takes around six to seven seconds on average. In order to observe the behavior of modified J-PAKE protocol used in the session key construction phase, further experiments are conducted by observing the time consumption for each step in the session key construction phase.
Figure 15 shows the average duration of each step in the session key construction phase based on the key size used in the modified J-PAKE protocol. In these experiments, three key sizes are chosen: 80-bits, 112-bits, and 128-bits.
With the key size set to 80-bits in
Figure 15, it shows that the messages transmission time between the user’s smartphone and the POS terminal during the session key construction phase consumes 6340 ms. Nevertheless, the total time consumption for the session key construction phase is 6587.8 ms. It indicates that 96% of the total time consumption is spent on the message transmission through Bluetooth channel. Based on the BLE core specification 4.2 [
7], the theoretical bandwidth of BLE 4.0 and BLE 4.1 is up to 236.7 kbps. However, the measured bandwidth of BLE 4.0 and BLE 4.1 using a CC2540 Bluetooth sniffer [
39] is only 50 kbps in our experiments. In comparison with BLE 4.0 and BLE 4.1, new BLE 5.0 specification [
40] has increased the bandwidth capacity from 236.7 to 1400 kbps, which is 5.91 times larger. Even though there is no device equipped with BLE 5.0 module currently, it is assumed that the practical bandwidth of BLE 5.0 will be around 5.91 times larger than the previous BLE 4.0 and BLE 4.1. If the transmission bandwidth of BLE module can be raised up to 5.91 times larger, then the time consumption for message transmission in the session key construction phase can be reduced to 1072.75 ms.
Based on this assumption, the total time consumption for the session key construction phase can be reduced to 1320.55 ms. The average time for authentication process with the key size set to 80-bits is 704.3 ms as shown in
Figure 16. In terms of the time consumption for initial connection of two BLE modules in our experiments, it is around 3 s in average as shown in
Figure 14. Nevertheless, the time required to establish initial connection between two BLE modules is inevitable and hard to reduce without introducing new BLE hardware module. In brief, with new BLE 5.0 module, the proposed user authentication mechanism could establish a secure payment session with dynamically constructed session key around 2 s without counting the time consumption of BLE channel establishment.
On the other hand, the increase of key size in the modified J-PAKE protocol does not have much effect on time consumption of the authentication phase in the proposed system. The time consumption between 80-bits, 112-bits and 128-bits of key sizes in the modified J-PAKE protocol only produces a slight 5–22 ms difference on the duration of the authentication process.
Figure 16 shows the average time duration of authentication process over different key sizes used in the modified J-PAKE protocol.
6. Security Analysis of the Proposed Authentication Protocol
Security analysis for the proposed authentication protocol is conducted to evaluate mutual authentication and the security strength of session key generation. In addition, the proposed protocol defends against impersonation attack, replay attack, and man-in-the-middle attack. We assume the cryptographic hash function used in the proposed protocol is able to withstand all known types of cryptanalytic attacks. In other words, the hash function has the characteristics of collision resistance, and is able to counteract the pre-image attacks and the second pre-image attacks. Moreover, a Cryptographically Secure Pseudorandom Value Generator (CSPRVG) is assumed to be used to generate all the random values in the proposed protocol. The CSPRVG satisfies all statistical tests and the output value is unpredictable to attackers.
Theorem 1. The proposed protocol supports mutual authentication.
Proof. Due to the computational difficulty of the Diffie-Hellman problem, the secret value to construct session secret can be computed only by legitimate customer’s smartphone and legitimate POS terminal. Both the legitimate customer’s smartphone and legitimate POS terminal will use the following formula and respectively; then both of them use the session secret to create a unique session key and a unique nonce at both ends. Next, the legitimate customer’s smartphone could compute hash key and the hashed message . The hashed message is sent to the legitimate POS terminal afterwards. After receiving , the legitimate POS terminal computes the random value and the hash key . The random value and the hash key are used by the POS terminal to authenticate the customer’s smartphone by evaluating whether the received message value is equivalent to the hashing computation result .
For the legitimate customer’s smartphone to authenticate the POS terminal, the POS terminal first computes a secret value and a hash key . The secret value and the hash key are used to produce a hashed message , in which the hashed message will be sent to the legitimate customer’s smartphone. After receiving and , the legitimate customer’s smartphone could compute the random value and the hash key . Next, the legitimate customer’s smartphone authenticates the POS terminal by evaluating whether the received message value is equivalent to the hashing computation result . Based on these two proofs, it can be concluded that the proposed protocol supports mutual authentication. ☐
Theorem 2. The proposed protocol provides session key security.
Proof. Assume that an adversary 𝒜 learns a session key from the previous successful session. The adversary 𝒜 cannot derive the previous secret value from the session key because the output of random string extension function cannot be used to easily derived its input parameter . The only way to derive the value of is to apply brute-force computation to find the matched value of based on the session key construction formula . Even if the adversary 𝒜 could successfully derives the , it is impossible for the adversary to generate the current secret value from the previous secret value as the value of is constructed from the values of and , which are always freshly generated for each session.
As and , the other way for the adversary to derive the current session key is by directly computing the values of , , , , and . As both the customer’s smartphone and the POS terminal always generate new random values and for each session and is generated based on key agreement mechanism derived from Diffie-Hellman problem, hence, the adversary 𝒜 needs to solve the Diffie-Hellman problem to acquire the current . ☐
Theorem 3. The proposed protocol defends against impersonation attack.
Proof. Assume that an adversary 𝒜 impersonates the client (the customer’s smartphone) to establish a secure session with the legitimate POS terminal. The adversary 𝒜 must have the symmetric key of a legitimate customer , which is obtained by the legitimate customer during the registration phase of the system. The symmetric key is stored in the secure element of the smartphone; therefore, it is impossible for the adversary 𝒜 to learn the correct symmetric key from a legitimate customer’s smartphone. Hence, the adversary cannot decrypt the encrypted value sent by the TTP server during the initialization phase. Therefore, the adversary 𝒜 is unable to initiate a genuine secure session with the legitimate POS terminal. The BLE connection initiated by the adversary 𝒜 to the legitimate POS terminal will always be refused, because the adversary 𝒜 cannot derive the user secret constructed by the TTP server. The adversary 𝒜 is not able to construct a genuine session key , because the session secret is constructed using the user secret as one of its input parameters in this formula .
The other case is that where an adversary 𝒜 launches an impersonation attack to make itself appear as a POS terminal to legitimate customer’s smartphones. Then, the adversary 𝒜 needs to have the symmetric key of a legitimate POS terminal to decrypt the encrypted message and obtain the correct user secret sent by the TTP server during the initialization phase. As the adversary 𝒜 could not learn the correct user secret , then the adversary 𝒜 would be unable to construct the proper session secret . Once the adversary 𝒜 is unable to construct the correct session secret , he would be unable to generate the session key from the random string extension function . ☐
Theorem 4. The proposed protocol defends against replay attack.
Proof. Assume an adversary 𝒜 has successfully learnt the previous user secret to perform a replay attack. The adversary 𝒜 will send two message sets and to the legitimate POS terminal during the session key construction phase, in which the message set is generated with the previous user secret . The two message sets are used to construct a session secret for generating the current session key . However, the legitimate POS terminal will receive a different value of user secret from the TTP server since a new random value is used to construct user secret for the current session. Hence, the session secret generated by the adversary 𝒜 is not equivalent to the session secret generated by the legitimate POS terminal. Therefore, the session key generated by the adversary will not be equivalent to the session key generated by the legitimate POS terminal. In consequence, the replay attack cannot launch successfully.
In case the adversary 𝒜 performs a replay attack during the authentication phase of the payment process, the adversary 𝒜 should have the encrypted message , and the hashed value from the previous session. When the adversary 𝒜 performs the replay attack, the POS terminal will know that the adversary 𝒜 does not use the current session key because the received hashed value is not equivalent to the calculated hashed value , where the hash key . As the result, the replay attack cannot launch successfully. Even if the adversary 𝒜 performs the replay attack using the encrypted message from the previous session, the POS terminal is able to detect the timestamp used in the received encrypted message has already expired. ☐
Theorem 5. The proposed protocol defends against man-in-the-middle attack.
Proof. Based on the proof given from Theorem 1, the proposed protocol provides mutual authentication between the legitimate user’s smartphone and the legitimate POS terminal. Hence, the proposed authentication protocol is able to defend against man-in-the-middle attack. □
7. Conclusions
New mobile payment systems are emerging in recent years such as NFC-based payment systems and smart card based payment systems (i.e., the card is embedded in a smartphone). As NFC-embedded smartphones are more expensive than ordinary ones in general, proposing a novel mobile payment system for most people who only have low-end or medium-end smartphones is a practical user demand. Since most smartphones have embedded BLE modules to support communication with nearby devices through Bluetooth technology, it is plausible to construct a BLE-based mobile payment system for common people. In this paper, we introduced a BLE-based mobile payment system such that people carrying BLE-enabled wearable devices can perform Over-the-Air payment actions through a Bluetooth communication channel between their wearable devices and the BLE-enabled POS terminal. To secure the payment process, an indoor-positioning based authentication protocol is proposed to dynamically generate the session key for each user payment session, in which the session key is used by both communicating parties to encrypt and decrypt payment information transmitted between them. The session key is generated from the user secret, which is created by the Trusted Third Party server with a set of received Bluetooth beacon signals indicating the current position of the user. The proposed protocol includes three phases: initialization phase, session key construction phase, and authentication phase. Two indoor positioning algorithms, a trilateration algorithm and a least squares algorithm, are adopted to determine whether the user is at the payment-enabled area.
Based on the proposed authentication protocol, a prototype of the mobile payment system is implemented and the system performance is evaluated. According to the experiment results, the indoor positioning algorithms shows an acceptable accuracy rate for determining whether the customer is located within the payment-enabled area. The best accuracy rate for customer position prediction is 97.29% when using the least squares algorithm combined with an average filter. As the bandwidth of BLE 4.0 and 4.1 modules is only up to 236.7 kbps, the time consumption for message transmission during user authentication is heavy. With the session key set at 80 bits, the total communication cost is 6.5340 s on average. Therefore, the prototype requires 6.5878 s to accomplish one session authentication on average. By applying a new BLE 5.0 module with 1400 kbps bandwidth, we estimate the proposed system should be able to accomplish a mutual authentication operation within 2 s.
Security analysis is conducted to evaluate the security strength of the proposed protocol. Based on the analysis results, the customer’s smartphone and the communicating POS terminal can securely and mutually authenticate each other. In addition, an adversary cannot derive or successfully guess the session key, which will be generated for the next authentication session between two communicating parties, based on the knowledge learned from the previous session key. Moreover, the proposed protocol withstands impersonation attacks, replay attacks, and man-in-the-middle attacks.