Future Spaces: Reinventing the Home Network for Better Security and Automation in the IoT Era
Abstract
:1. Introduction
- “Virtual Places”, realizing the foundation of new smart home/environment CPS by logically representing and managing an administrative domain, voluntarily blurring the frontier between the physical and virtual environments to cope with new usages and needs of end-users. Challenges in realizing such a concept lie in the definition and implementation of the companion cloud infrastructure and network gateways, realizing a distributed testbed allowing to easily provision, deploy, dynamically extend to multiple geographical locations, and interconnect these Virtual Places;
- “Virtual Spaces”, allowing one to create secured, dynamic collections of resources regrouped by usage, and interconnecting these resources over one or more Virtual Places (i.e., crossing multiple administrative home domains). Realizing those Virtual Spaces requires on the one hand a mix of mechanisms to automatically adapt their content according to their definition and the current context. On the other hand, the historical control of Local Area Networks is revisited by using dynamically programmable “Software-Defined LANs” enabling the connection of the resources they regroup into isolated network slices, while ensuring network-based security in open and living environments;
- Simple tools and interfaces together with advanced automation mechanisms, allowing users to exercise better control over their digital assets and ultimately share them with others. Those mechanisms should act as a “digital butler” of future smart homes, reacting to orders from users, but also quietly enforcing users’ goals, privacy and security over their digital belongings.
2. Context and Related Work
2.1. The State of the Smart Home
2.2. Relevant Related Work on Home Networking and Security
3. Overview of the Future Spaces Solution
3.1. Problem Statement and Working Assumptions
- Fine-grained, context-aware access control, achieved by providing a dynamic, fine-grained and group-based connectivity layer, allowing or disallowing communications between physical and/or digital assets. In our solution, by default no communication is allowed between devices attached to the Virtual Place network. By defining Virtual Spaces for groups of devices sharing the same user-defined context of use (e.g., multimedia consumption, home security), communication is only enabled within these groups of devices (through dedicated slices whitelisting communication), even though each device can be attached to geographically distant network elements;
- Automatic security & privacy protection, achieved by providing strong network isolation along with automatic policy enforcement, and protecting data privacy and network integrity of resources. The slices realizing the virtual spaces are isolated from each other in terms of data traffic, meaning no traffic is allowed between e.g., a device in a Multimedia vSpace and a device in a Home Security vSpace. Furthermore, policies may be enforced to prevent unwanted communication when for example an untrusted device is added to a slice containing one or more sensitive devices;
- Cross-domain resource sharing, enabling easy discovery of and interaction with third party resources, and securely sharing resources with others. Through simple mechanisms, an authorized user can discover resources of a visited domain and request the establishment of a cross-domain Virtual Space, combining resources of the other domain with some of her own resources, de facto leading to the sharing of devices across authorized users of both domains;
- Ease-of-use & automation, allowing intuitive and secure management of all user connected resources and the deployment of task-specific automation processes to support users in different application contexts. Through a simple user interface, a user can see the status of the Virtual Place and manipulate its devices and Virtual Spaces and discover others’. To avoid overloading the user, automation mechanisms allow for dynamic creation and modification of virtual spaces and the associated connectivity.
3.2. Virtual Places and Virtual Spaces
3.3. The Future Spaces Solution
- a set of Virtualized Network Functions (DHCP, DNS, Internet Gateway and multiple Open vSwitches or OVS [27]), running either inside Future Spaces Gateways (FSGW) or the Future Spaces cloud,
- a SDN Controller (SDN-C) to pilot the virtual switches,
- a MajordHome component in charge of managing the vPlace resources, users and vSpaces, of interacting with the users or automation processes and of turning vSpaces definitions into SDN-C commands.
4. Future Spaces Proof of Concept System Architecture and Design Choices
4.1. Distributed Cloud Architecture
4.2. Future Spaces Gateways
4.3. vPlace Cloud Orchestration and Lifecycle Management
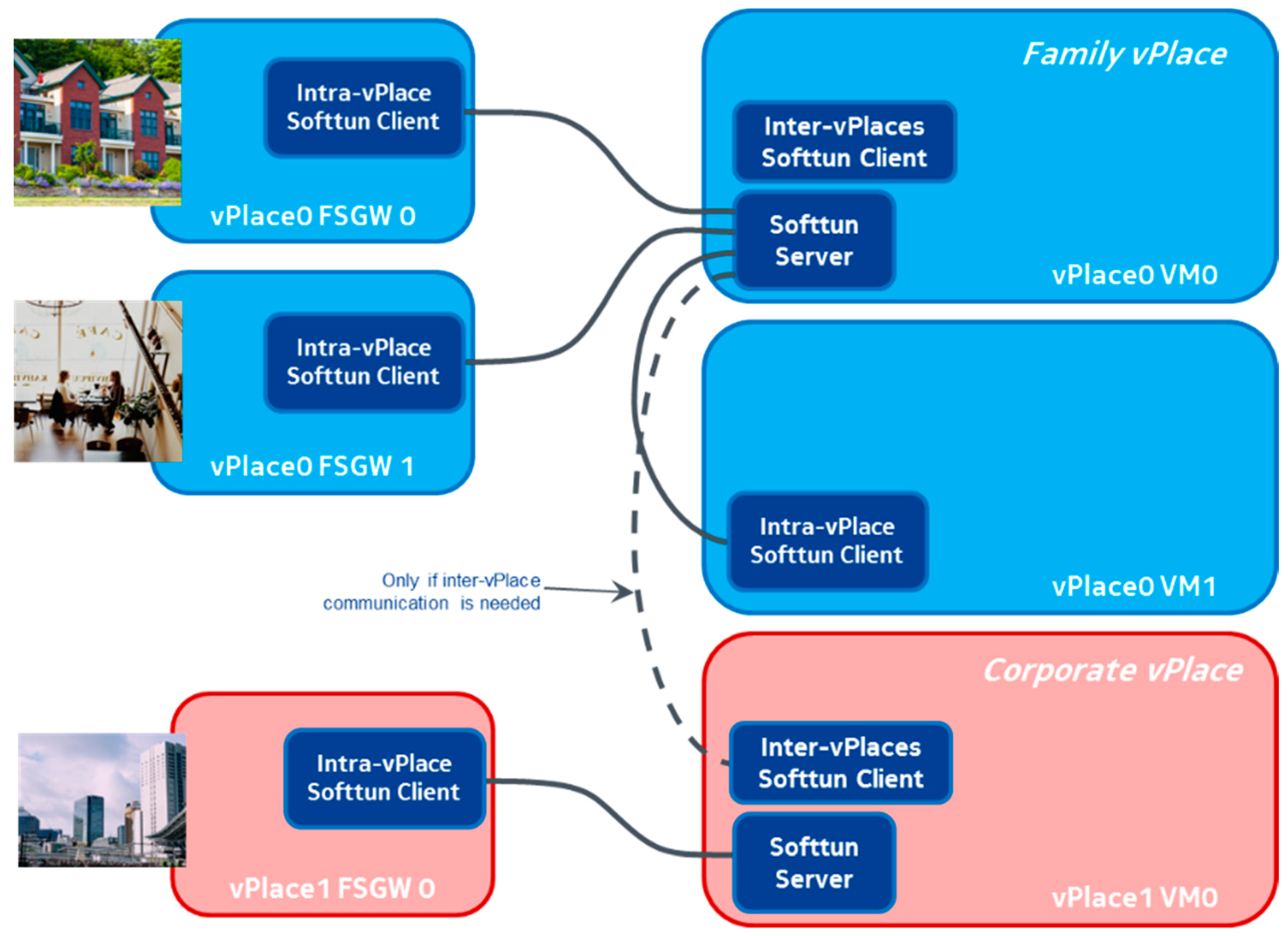
4.4. Inter-vPlace Connectivity for Cross-Domain Slice Establishment
5. Software-Defined LAN as the Networking Building Block
5.1. SD-LAN Characteristics
- SD-LANs are isolated from each other in terms of traffic, forming a logical partition of the local network at the data plane level. One could say that SD-LANs are equivalent to virtual LANs (VLANs defined in the IEEE 802.1Q standard), but contrary to the VLAN case, a device with a single network interface can be part of multiple SD-LANs at the same time;
- An SD-LAN can span across multiple domains (i.e., local networks of different vPlaces).
5.2. SD-LAN Underlay Architecture
5.3. Operation Description
- The MajordHome can send configuration orders to include/remove a device in/from the vSpace. The reason for such change can be the modification of the vSpace definition through user interaction, or the change of reachability of a device in this vSpace, or more generally because of an automated reevaluation of the vSpace content (see discussion on automation in Section 6.3). For example, a device discovered as compliant with a given property (e.g., “DLNA-compliancy”) would be automatically added to a vSpace regrouping all devices matching this property;
- A vPlace can be extended to a new physical location, through the addition of a new Future Spaces instance (FSGW);
- A vSpace can be extended to another existing vPlace, e.g., to include a device from a third party or to follow the mobility of a device in a visited vPlace.
5.4. SDN-C Architecture Solution
- Table 0 aims at filtering miss-formatted frames;
- Table 10 informs the controller of newly discovered devices (includes MAC learning);
- Table 20 differentiates multicast/broadcast from unicast traffic, and adds different tags to LAN-originated and WAN-originated traffic flows;
- Table 30 tests pair of source and destination addresses to determine if a unicast frame is to be dropped or forwarded (finer grain filtering is possible to isolate application services);
- Table 40 is updated through MAC learning and used to forward unicast frames within the local network;
- Table 50 sends unicast frames to the legitimate remote networks (vPlaces);
- Table 60 sends multicast frames to the legitimate remote networks (vPlaces);
- Table 70 sends multicast packets to the legitimate destinations in the local network;
- Table 80 is updated through MAC learning to forward multicast frames according to a new LAN multicast tree.
6. Automation and User Support in Future Spaces
6.1. Handling of User Interactions and Customizations
6.1.1. The Administration User Interfaces
6.1.2. The HTTP REST API
6.1.3. The OSGI Framework
6.2. Architecture and Data Model
- VirtualObjects: to model the devices connected to the network, and carry information concerning their capabilities and their attributes,
- VirtualSpaces: to model the SD-LANs and hold the composition of these SD-LANs in terms of devices,
- Behaviors: to model simple automata,
- Users and their Roles: to model the users and control their permissions in interacting with the MajordHome,
- Sharing policies: to model which constraints users want to enforce when sharing their devices (e.g., making sure that the door lock securing system of their house cannot be shared with untrusted devices).
6.3. Automation for Users
- Predicates in VirtualSpace agents: the composition of a VirtualSpace is determined by a Predicate (Boolean function). Every device for which the VirtualObject matches the predicate of a given VirtualSpace will be part of the corresponding SD-LAN. e.g., a vSpace can be composed out of a defined list of devices, or e.g., be automatically composed of every device matching a given characteristic (e.g., being multimedia capable), as soon as they connect to the network.
- Sharing Policies engine: every VirtualSpaces and VirtualObject agents contains such engine to ensure that their sharing policies are respected. Such policy typically expresses context in which their corresponding host should be used (e.g., a policy on a device may state that it cannot take part in a vSpace including devices not belonging to its owner). More details on sharing policies can be found in [32].
- Behaviors: MajordHome supports event-driven automated behaviors, which essentially are callback functions that are automatically triggered by specific events and then perform some modifications on the system (e.g., perform a given task to enrich the information contained in a VirtualObject when a device connects for the first time). These behaviors can be started, stopped and customized by the user. MajordHome plugins coming as OSGi bundles can augment the catalog of behaviors (see Section 6.1).
- Assistants: Third-party assistants handle focused intents of users, and support the automation required to handle these intents and translate those in a set of requests to the MajordHome REST API (limited to the scope of the permissions granted to the assistant). Assistants can be realized as software components external to the MajordHome, allowing to support more complex logic than Behaviors or even be hosted outside of the Future Spaces platform.
7. Proof of Concept Setup and Functional Use Case
7.1. Proof of Concept Setup
7.2. Overview of the Future Spaces UI
7.3. Step 1: Stay Connected to Your Smart Home on the Move
7.4. Step 2: Allow/Block Communication of a Group of Devices in a Single Click
7.5. Step 3: Interact with Other Smart Environments and Discover & Use New Devices
7.6. Step 4: Easily Provide a Secured Access to Visitors and Be Warned of New Events
7.7. Step 5: Safeguards on Devices and Virtual Spaces Sharing
8. Discussion
8.1. SD-LANs as a Solution for Fine-Grained, Context-Aware Access Control
8.2. Cross-Domain Resource Sharing via Virtual Spaces
8.3. Automatic Security & Privacy Protection
8.4. Ease-of-Use & Automation
9. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Grinter, R.E.; Edwards, W.K.; Chetty, M.; Poole, E.S.; Sung, J.Y.; Yang, J.; Crabtree, A.; Tolmie, P.; Rodden, T.; Greenhalgh, C.; et al. The Ins and Outs of Home Networking: The Case for Useful and Usable Domestic Networking. ACM Trans. Comput. Hum. Interact. 2009, 16, 8. [Google Scholar] [CrossRef]
- Mozer, M.C. Lessons from an Adaptive Home. In Smart Environments; Wiley-Blackwell: Hoboken, NJ, USA, 2005; Chapter 12; pp. 271–294. [Google Scholar] [Green Version]
- Kientz, J.A.; Patel, S.N.; Jones, B.; Price, E.; Mynatt, E.D.; Abowd, G.D. The Georgia Tech Aware Home. In Proceedings of the CHI ’08 Extended Abstracts on Human Factors in Computing Systems (CHI EA ’08), Florence, Italy, 5–10 April 2008; pp. 3675–3680. [Google Scholar] [CrossRef]
- Harper, R. (Ed.) Inside the Smart Home; Springer: Berlin, Germany, 2003. [Google Scholar]
- Koskela, T.; Väänänen-Vainio-Mattila, K. Evolution Towards Smart Home Environments: Empirical Evaluation of Three User Interfaces. Pers. Ubiquitous Comput. 2004, 8, 234–240. [Google Scholar] [CrossRef]
- Intille, S.S. Designing a home of the future. IEEE Pervasive Comput. 2002, 1, 76–82. [Google Scholar] [CrossRef]
- Brush, A.B.; Lee, B.; Mahajan, R.; Agarwal, S.; Saroiu, S.; Dixon, C. Home Automation in the Wild: Challenges and Opportunities. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI ’11), Vancouver, BC, Canada, 7–12 May 2011; pp. 2115–2124. [Google Scholar] [CrossRef]
- Edwards, W.K.; Grinter, R.E. At Home with Ubiquitous Computing: Seven Challenges. In Proceedings of the 3rd International Conference on Ubiquitous Computing (UbiComp ’01), Atlanta, GA, USA, 30 September–2 October 2001; pp. 256–272. [Google Scholar]
- Gizmodo. The House that Spied on Me. Available online: http://gizmodo.com/the-house-that-spied-on-me-1822429852 (accessed on 3 July 2018).
- Edwards, W.K.; Grinter, R.E.; Mahajan, R.; Wetherall, D. Advancing the State of Home Networking. Commun. ACM 2011, 54, 62–71. [Google Scholar] [CrossRef]
- Schneier on Security. Security and the Internet of Things. Available online: https://www.schneier.com/blog/archives/2017/02/security_and_th.html (accessed on 3 July 2018).
- Fernandes, E.; Jung, J.; Prakash, A. Security Analysis of Emerging Smart Home Applications. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 636–654. [Google Scholar] [CrossRef]
- Sivaraman, V.; Gharakheili, H.H.; Fernandes, C.; Clark, N.; Karliychuk, T. Smart IoT Devices in the Home: Security and Privacy Implications. IEEE Technol. Soc. Mag. 2018, 37, 71–79. [Google Scholar] [CrossRef]
- Plume WiFi. Available online: https://blog.plumewifi.com/guest-access-needed-an-ssid-kicking-3de53d2182a7 (accessed on 3 July 2018).
- Cujo. Available online: https://www.getcujo.com/smart-firewall-cujo (accessed on 3 July 2018).
- Sherwood, R.; Gibb, G.; Yap, K.K.; Appenzeller, G.; Casado, M.; McKeown, N.; Parulkar, G. Can the Production Network Be the Testbed? In Proceedings of the 9th USENIX Conference on Operating Systems Design and Implementation (OSDI’10), Vancouver, BC, Canada, 4–6 October 2010; pp. 365–378. [Google Scholar]
- Berman, M.; Chase, J.S.; Landweber, L.; Nakao, A.; Ott, M.; Raychaudhuri, D.; Ricci, R.; Seskar, I. GENI: A Federated Testbed for Innovative Network Experiments. Comput. Netw. 2014, 61, 5–23. [Google Scholar] [CrossRef]
- Bera, S.; Misra, S.; Vasilakos, A.V. Software-Defined Networking for Internet of Things: A Survey. IEEE Internet Things J. 2017, 4, 1994–2008. [Google Scholar] [CrossRef]
- Yiakoumis, Y.; Yap, K.K.; Katti, S.; Parulkar, G.; McKeown, N. Slicing Home Networks. In Proceedings of the 2nd ACM SIGCOMM Workshop on Home Networks (HomeNets ’11), Toronto, ON, Canada, 15 August 2011; pp. 1–6. [Google Scholar] [CrossRef]
- Gharakheili, H.H.; Exton, L.; Sivaraman, V.; Matthews, J.; Russell, C. Third-party customization of residential Internet sharing using SDN. In Proceedings of the 2015 International Telecommunication Networks and Applications Conference (ITNAC), Sydney, NSW, Australia, 18–20 November 2015; pp. 214–219. [Google Scholar] [CrossRef]
- Kim, H.; Sundaresan, S.; Chetty, M.; Feamster, N.; Edwards, W.K. Communicating with Caps: Managing Usage Caps in Home Networks. In Proceedings of the ACM SIGCOMM 2011 Conference (SIGCOMM ’11), Toronto, ON, Canada, 15–19 August 2011; pp. 470–471. [Google Scholar] [CrossRef]
- Mortier, R.; Rodden, T.; Lodge, T.; McAuley, D.; Rotsos, C.; Moore, A.W.; Koliousis, A.; Sventek, J. Control and understanding: Owning your home network. In Proceedings of the 2012 Fourth International Conference on Communication Systems and Networks (COMSNETS 2012), Bangalore, India, 3–7 January 2012; pp. 1–10. [Google Scholar] [CrossRef]
- Fratczak, T.; Broadbent, M.; Georgopoulos, P.; Race, N. HomeVisor: Adapting Home Network Environments. In Proceedings of the 2013 Second European Workshop on Software Defined Networks, Berlin, Germany, 10–11 October 2013; pp. 32–37. [Google Scholar] [CrossRef]
- Nobakht, M.; Sivaraman, V.; Boreli, R. A Host-Based Intrusion Detection and Mitigation Framework for Smart Home IoT Using OpenFlow. In Proceedings of the 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 147–156. [Google Scholar] [CrossRef]
- Giotis, K.; Argyropoulos, C.; Androulidakis, G.; Kalogeras, D.; Maglaris, V. Combining OpenFlow and sFlow for an effective and scalable anomaly detection and mitigation mechanism on SDN environments. Comput. Netw. 2014, 62, 122–136. [Google Scholar] [CrossRef]
- Feamster, N. Outsourcing Home Network Security. In Proceedings of the 2010 ACM SIGCOMM Workshop on Home Networks (HomeNets ’10), New Delhi, India, 3 September 2010; pp. 37–42. [Google Scholar] [CrossRef]
- Open vSwitch. Available online: https://www.openvswitch.org/ (accessed on 3 July 2018).
- Pankratov, A. Hamachi. 2004. Available online: http://www.swapped.cc/#!/hamachi (accessed on 22 August 2018).
- Kindervag, J. Build Security into Your Network’s DNA: The Zero Trust Network Architecture; Forrester Research Inc.: Cambridge, MA, USA, 2010; pp. 1–26. [Google Scholar]
- Bui, D.T.; Douville, R.; Boussard, M. Supporting multicast and broadcast traffic for groups of connected devices. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft), Seoul, Korea, 6–10 June 2016; pp. 48–52. [Google Scholar] [CrossRef]
- Boussard, M.; Bui, D.T.; Ciavaglia, L.; Douville, R.; Pallec, M.L.; Sauze, N.L.; Noirie, L.; Papillon, S.; Peloso, P.; Santoro, F. Software-Defined LANs for Interconnected Smart Environment. In Proceedings of the 2015 27th International Teletraffic Congress, Ghent, Belgium, 8–10 September 2015; pp. 219–227. [Google Scholar] [CrossRef]
- Peloso, P.; Bui, D.T.; Boussard, M. Enforcing users’ constraints in dynamic, software-defined networks of devices. In Proceedings of the 2017 19th Asia-Pacific Network Operations and Management Symposium (APNOMS), Seoul, Korea, 27–29 September 2017; pp. 106–111. [Google Scholar] [CrossRef]















© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boussard, M.; Thai Bui, D.; Douville, R.; Justen, P.; Le Sauze, N.; Peloso, P.; Vandeputte, F.; Verdot, V. Future Spaces: Reinventing the Home Network for Better Security and Automation in the IoT Era. Sensors 2018, 18, 2986. https://doi.org/10.3390/s18092986
Boussard M, Thai Bui D, Douville R, Justen P, Le Sauze N, Peloso P, Vandeputte F, Verdot V. Future Spaces: Reinventing the Home Network for Better Security and Automation in the IoT Era. Sensors. 2018; 18(9):2986. https://doi.org/10.3390/s18092986
Chicago/Turabian StyleBoussard, Mathieu, Dinh Thai Bui, Richard Douville, Pascal Justen, Nicolas Le Sauze, Pierre Peloso, Frederik Vandeputte, and Vincent Verdot. 2018. "Future Spaces: Reinventing the Home Network for Better Security and Automation in the IoT Era" Sensors 18, no. 9: 2986. https://doi.org/10.3390/s18092986
APA StyleBoussard, M., Thai Bui, D., Douville, R., Justen, P., Le Sauze, N., Peloso, P., Vandeputte, F., & Verdot, V. (2018). Future Spaces: Reinventing the Home Network for Better Security and Automation in the IoT Era. Sensors, 18(9), 2986. https://doi.org/10.3390/s18092986




