Exploiting Joint Base Station Equipped Multiple Antenna and Full-Duplex D2D Users in Power Domain Division Based Multiple Access Networks
Abstract
:1. Introduction
- In the presence of a downlink under support of multiple antenna based BS, two D2D users exhibit different outage performance. We individually investigated the performance of each end-user in such a MISO NOMA system. Compared to most existing cooperative PDMA schemes, FD scheme is enabled at the end-user. To look how good performance two far users have, two far D2D users with different QoS requirements can be paired with each other and get benefit from D2D transmission.
- Different from [25], transmit selection and full-duplex are joint investigated in this study. Most important is that we provide simulation results of integration of a D2D connection to a downlink two-user PDMA system.
- We provide simulation results showing that, under the fixed power allocation strategies, D2D users achieve outage behavior in the NOMA scheme. The results also indicate the probability that both D2D users obtain improved outage performance in MISO PDMA depends on the power level of the BS and the required target rates.
- For system performance evaluation, the closed-form expressions for the outage probabilities are derived for both two D2D users. To highlight the impact of the system parameters on the outage performance, outage probabilities achieved at both two D2D users are simulated to verify derived expressions.
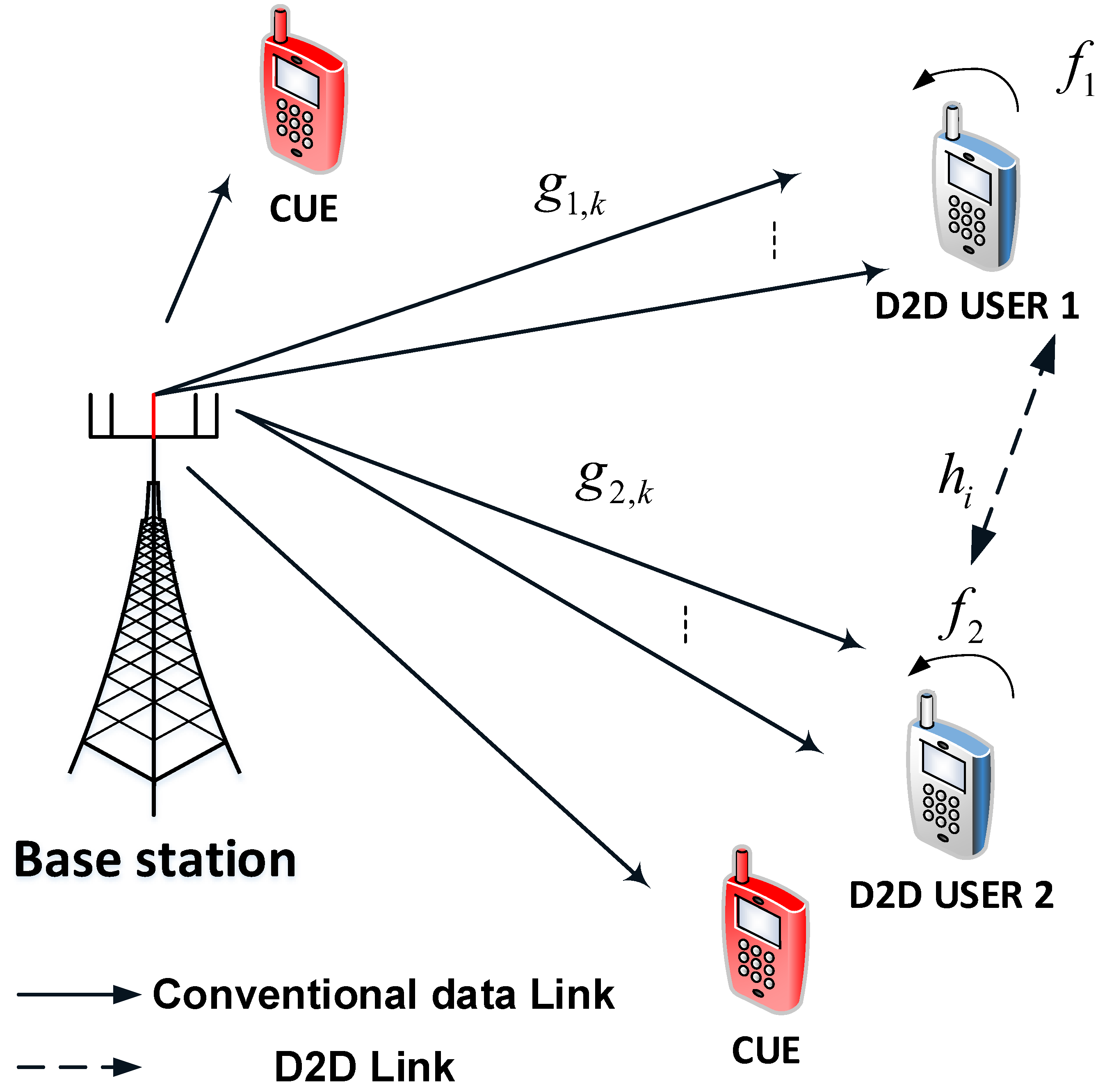
2. System Model
2.1. Calculation of Signal to Noise Ratio (SNR)
2.2. D2D Transmission
3. Outage Probability Performance Analysis
3.1. Outage Probability of D2D User 1
3.2. Outage Probability of D2D User 2
4. Analysis On Asymptotic Outage Probability
4.1. Asymptotic Outage Probability at D2D User 1
4.2. Asymptotic Outage Probability at D2D User 2
5. Numerical Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A.
Appendix B.
Appendix C.
References
- Do, D.-T.; Nguyen, H.-S.; Voznak, M.; Nguyen, T.-S. Wireless powered relaying networks under imperfect channel state information: System performance and optimal policy for instantaneous rate. Radioengineering 2017, 26, 869–877. [Google Scholar] [CrossRef]
- Nguyen, X.-X.; Do, D.-T. Optimal power allocation and throughput performance of full-duplex DF relaying networks with wireless power transfer-aware channel. EURASIP J. Wirel. Commun. Netw. 2017, 2017, 152. [Google Scholar] [CrossRef]
- Nguyen, X.-X.; Do, D.-T. Maximum Harvested Energy Policy in Full-Duplex Relaying Networks with SWIPT. Int. J. Commun. Syst. 2017, 30, e3359. [Google Scholar] [CrossRef]
- Nguyen, T.-L.; Do, D.-T. A new look at AF two-way relaying networks: Energy harvesting architecture and impact of co-channel interference. Ann. Telecommun. 2017, 72, 669–678. [Google Scholar]
- Wong, V.W.S.; Schober, R.; Ng, D.W.K.; Wang, L.-C. Key Technologies for 5G Wireless Systems, 1st ed.; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Zhu, J.; Wang, J.; Huang, Y.; He, S.; You, X.; Yang, L. On Optimal Power Allocation for Downlink Non-Orthogonal Multiple Access Systems. IEEE J. Select. Areas Commun. 2017, 35, 2744–2757. [Google Scholar] [CrossRef]
- Chen, Z.; Ding, Z.; Dai, X.; Karagiannidis, G.K. On the Application of Quasi-Degradation to MISO-NOMA Downlink. IEEE Trans. Signal Process. 2016, 64, 6174–6189. [Google Scholar] [CrossRef] [Green Version]
- Chen, X.; Zhang, Z.; Zhong, C.; Ng, D.W.K. Exploiting Multiple Antenna Techniques for Non-Orthogonal Multiple Access. IEEE J. Select. Areas Commun. 2017, 35, 2207–2220. [Google Scholar] [CrossRef]
- Do, D.-T.; Nguyen, M.-S.V.; Hoang, T.-A.; Voznak, M. NOMA-Assisted Multiple Access Scheme for IoT Deployment: Relay Selection Model and Secrecy Performance Improvement. Sensors 2019, 19, 736. [Google Scholar] [CrossRef]
- Do, D.-T.; Le, C.-B. Application of NOMA in Wireless System with Wireless Power Transfer Scheme: Outage and Ergodic Capacity Performance Analysis. Sensors 2018, 18, 3501. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, T.-L.; Do, D.-T. Power Allocation Schemes for Wireless Powered NOMA Systems with Imperfect CSI: System model and performance analysis. Int. J. Commun. Syst. 2018, 31, e3789. [Google Scholar] [CrossRef]
- Nguyen, T.-L.; Do, D.-T. Exploiting Impacts of Intercell Interference on SWIPT-assisted Non-orthogonal Multiple Access. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef]
- Molish, A.F.; Win, M.Z. Capacity of MIMO systems with antenna selection. IEEE Trans. Wirel. Commun. 2005, 4, 1759–1772. [Google Scholar] [CrossRef] [Green Version]
- Thoen, S.; Perre, L.V.; Gyselinckx, B.; Engels, M. Performance analysis of combined transmit-SC/receive-MRC. IEEE Trans. Commun. 2001, 49, 5–8. [Google Scholar] [CrossRef]
- Mumtaz, S.; Huq, K.M.S.; Rodriguez, J. Direct mobile-to-mobile communication: Paradigm for 5G. IEEE Wirel. Commun. 2014, 21, 14–23. [Google Scholar] [CrossRef]
- Doppler, K.; Rinne, M.; Wijting, C.; Ribeiro, C.B.; Hugl, K. Device-todevice communication as an underlay to LTE-advanced networks. IEEE Commun. Mag. 2009, 47, 42–49. [Google Scholar] [CrossRef]
- Lei, L.; Zhong, Z.; Lin, C.; Shen, X. Operator controlled device-to-device communications in LTE-advanced networks. IEEE Wirel. Commun. 2012, 19, 96–104. [Google Scholar] [CrossRef]
- Asadi, A.; Mancuso, V. Network-assisted outband D2D-clustering in 5G cellular networks: Theory and practice. IEEE Trans. Mob. Comput. 2017, 16, 2246–2259. [Google Scholar] [CrossRef]
- Tseng, H.-W.; Yu, Y.-J.; Wu, B.-S.; Kuo, C.-F.; Chen, P.-S. A resource allocation scheme for device-to-device communication over ultra-dense 5G cellular networks. In Proceedings of the 2017 International Conference on Applied System Innovation (ICASI), Sapporo, Japan, 13–17 May 2017; pp. 80–83. [Google Scholar]
- Ma, R.; Chang, Y.-J.; Chen, H.-H.; Chiu, C.-Y. On relay selection schemes for relay-assisted D2D communications in LTE-A systems. IEEE Trans. Veh. Technol. 2017, 66, 8303–8314. [Google Scholar] [CrossRef]
- Tehrani, M.N.; Uysal, M.; Yanikomeroglu, H. Device-to-device communication in 5G cellular networks: Challenges, solutions, and future directions. IEEE Commun. Mag. 2014, 52, 86–92. [Google Scholar] [CrossRef]
- Lien, S.-Y.; Chien, C.-C.; Liu, G.S.-T.; Tsai, H.-L.; Li, R.; Wang, Y.J. Enhanced LTE device-to-device proximity services. IEEE Commun. Mag. 2016, 54, 174–182. [Google Scholar] [CrossRef]
- Osseiran, A.; Boccardi, F.; Braun, V.; Kusume, K.; Marsch, P.; Maternia, M.; Queseth, O.; Schellmann, M.; Schotten, H.; Taoka, H.; et al. Scenarios for 5G mobile and wireless communications: The vision of the METIS project. IEEE Commun. Mag. 2014, 52, 26–35. [Google Scholar] [CrossRef]
- Madani, N.; Sodagari, S. Performance Analysis of Non-Orthogonal Multiple Access With Underlaid Device-to-Device Communications. IEEE Access 2018, 6, 39820–39826. [Google Scholar] [CrossRef]
- Bithas, P.S.; Maliatsos, K.; Foukalas, F. An SINR-Aware Joint Mode Selection, Scheduling, and Resource Allocation Scheme for D2D Communications. IEEE Trans. Veh. Technol. 2019. [Google Scholar] [CrossRef]
- Zheng, H.; Hou, S.; Li, H.; Song, Z.; Hao, Y. Power Allocation and User Clustering for Uplink MC-NOMA in D2D Underlaid Cellular Networks. IEEE Wirel. Commun. Lett. 2018, 7, 1030–1033. [Google Scholar] [CrossRef]
- Diao, X.; Zheng, J.; Wu, Y.; Cai, Y. Joint Computing Resource, Power, and Channel Allocations for D2D-Assisted and NOMA-Based Mobile Edge Computing. IEEE Access 2019, 7, 9243–9257. [Google Scholar] [CrossRef]






© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Do, D.-T.; Van Nguyen, M.-S.; Hoang, T.-A.; Lee, B.M. Exploiting Joint Base Station Equipped Multiple Antenna and Full-Duplex D2D Users in Power Domain Division Based Multiple Access Networks. Sensors 2019, 19, 2475. https://doi.org/10.3390/s19112475
Do D-T, Van Nguyen M-S, Hoang T-A, Lee BM. Exploiting Joint Base Station Equipped Multiple Antenna and Full-Duplex D2D Users in Power Domain Division Based Multiple Access Networks. Sensors. 2019; 19(11):2475. https://doi.org/10.3390/s19112475
Chicago/Turabian StyleDo, Dinh-Thuan, Minh-Sang Van Nguyen, Thi-Anh Hoang, and Byung Moo Lee. 2019. "Exploiting Joint Base Station Equipped Multiple Antenna and Full-Duplex D2D Users in Power Domain Division Based Multiple Access Networks" Sensors 19, no. 11: 2475. https://doi.org/10.3390/s19112475






