A Lightweight RFID Mutual Authentication Protocol with PUF
Abstract
:1. Introduction
2. PUF Technique
3. Related Work
4. Proposed Protocol
4.1. Adversary Model
4.2. Assumptions
4.3. Notations
4.4. Proposed Ideal PUF-Based Authentication Protocol
4.4.1. Setup Phase
4.4.2. Authentication Phase
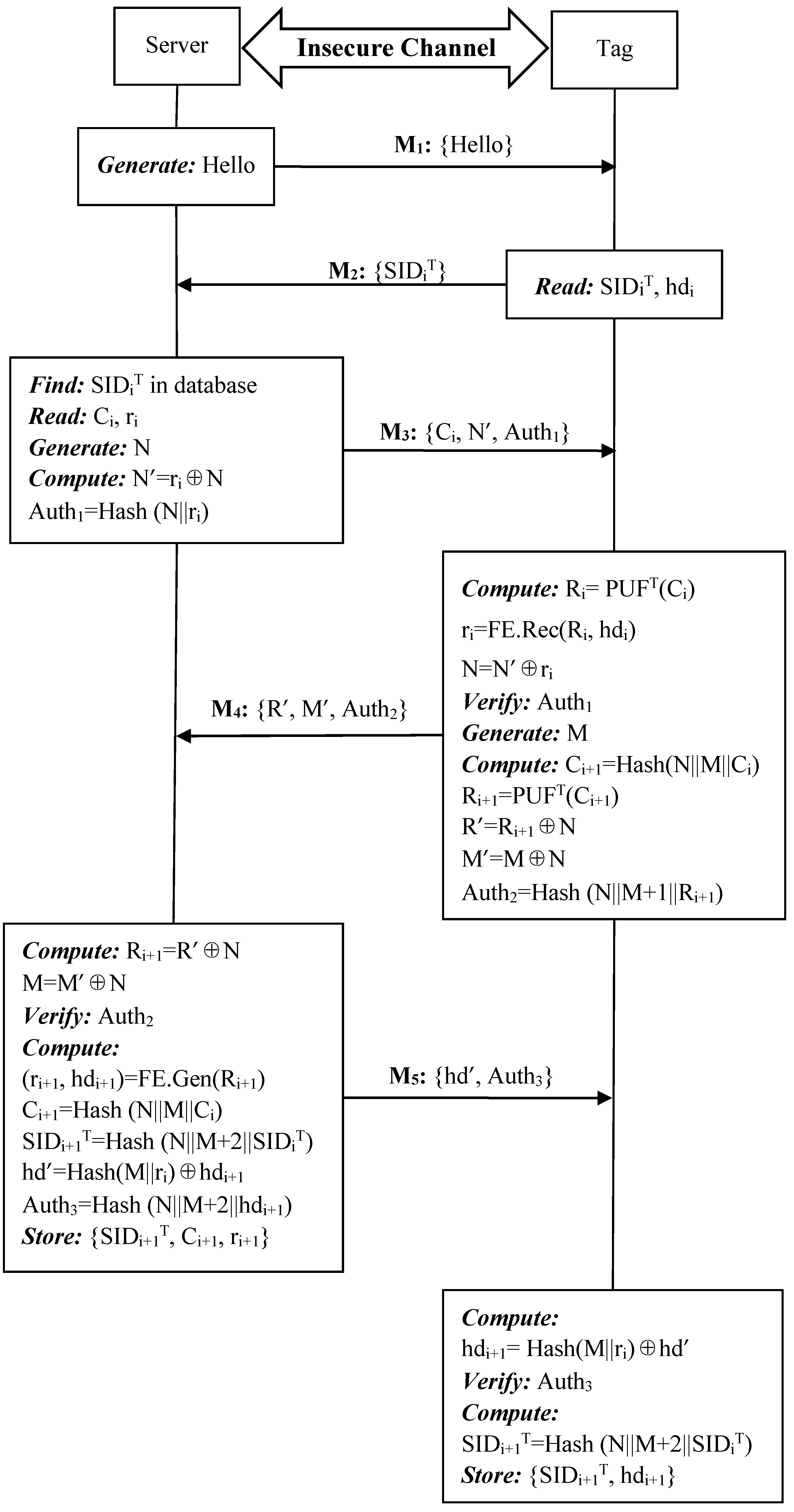
4.5. Proposed Noisy PUF-Based Authentication Protocol
4.5.1. Setup Phase
4.5.2. Authentication Phase
5. Formal Security Analysis
5.1. Adversarial Model
- Query(T, x1, m2): A sends x1 to T and receives m2 from T. This oracle models the adversary’s ability to interrogate tags in the system.
- Send(S, m1, x2, m3): A sends m1 to S and receives x2 from S. Then A sends m3 to S as a response. This oracle models the adversary’s ability to act as a legitimate tag in the system.
- Execute(T, S): A eavesdrops on the channel between T and S, and can also tamper with the protocol messages. This oracle models the adversary’s ability to continuously monitor the channel between T and S.
- Block( ): A blocks a part of the protocol and is able to break the synchronization between T and S. This query models the adversary’s ability to launch a denial of service attack.
- Reveal(T): A manages to access to the content in the memory of the tag T. The oracle models the adversary’s ability to physically crack a tag and obtain the secrets in its memory.
5.2. Security Analysis
5.2.1. Privacy
5.2.2. Mutual Authentication
5.2.3. Desynchronization Attacks
5.2.4. Physical Attacks
5.2.5. Clone Attacks
5.2.6. Modeling Attacks
5.3. Formal Security Verification Using Scyther Tool
6. Performance Analysis
6.1. Security Performance
6.2. Efficiency Performance
6.3. Highlights of Our Protocols
7. Implementation Discussion
7.1. The Proposed Protocol Based on Ideal PUF
7.2. The Proposed Protocol Based on Noisy PUF
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A. Implementation of Our Proposed Protocol in the Scyther Tool
References
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Gadh, R.; Roussos, G.; Michael, K.; Huang, G.Q.; Prabhu, B.S.; Chu, P. RFID—A Unique Radio Innovation for the 21st Century. Proc. IEEE 2010, 98, 1546–1549. [Google Scholar] [CrossRef]
- EPC. Global Gen2 Specification. Available online: https://www.gs1.org/sites/default/files/docs/epc/uhfc1g2_2_0_0_standard_20131101.pdf (accessed on 20 April 2019).
- Sun, H.; Ting, W. A Gen2-Based RFID Authentication Protocol for Security and Privacy. IEEE Trans. Mob. Comput. 2009, 8, 1052–1062. [Google Scholar]
- Kardaş, S.; Kiraz, M.S.; Bingöl, M.A.; Demirci, H. A Novel RFID Distance Bounding Protocol Based on Physically Unclonable Functions. In Proceedings of the International Workshop on Radio Frequency Identification: Security and Privacy Issues, Amherst, MA, USA, 26–28 June 2011; pp. 78–93. [Google Scholar]
- Arbit, A.; Livne, Y.; Oren, Y.; Wool, A. Implementing Public-key Cryptography on Passive RFID Tags is Practical. Int. J. Inf. Secur. 2015, 14, 85–99. [Google Scholar] [CrossRef]
- Manifavas, C.; Hatzivasilis, G.; Fysarakis, K.; Rantos, K. Lightweight Cryptography for Embedded Systems—A Comparative Analysis. In Data Privacy Management and Autonomous Spontaneous Security; Garcia-Alfaro, J., Lioudakis, G., Cuppens-Boulahia, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8247, pp. 333–349. [Google Scholar]
- Guo, J.; Peyrin, T.; Poschmann, A. The PHOTON Family of Lightweight Hash Functions. In Proceedings of the 31st Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011; pp. 222–239. [Google Scholar]
- Bogdanov, A.; Knežević, M.; Leander, G.; Toz, D.; Varıcı, K.; Verbauwhede, I. SPONGENT: A Lightweight Hash Function. In Proceedings of the 13th International Workshop on Cryptographic Hardware and Embedded Systems, Nara, Japan, 28 September–1 October 2011; pp. 312–325. [Google Scholar]
- Juels, A.; Weis, S.A. Authenticating Pervasive Devices with Human Protocols. In Proceedings of the 25th International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; pp. 293–308. [Google Scholar]
- Bringer, J.; Chabanne, H.; Dottax, E. HB++: A Lightweight Authentication Protocol Secure against Some Attacks. In Proceedings of the 2nd International Workshop on Security, Privacy and Trust in Pervasive and Ubiquitous Computing, Lyon, France, 29–29 June 2006; pp. 28–33. [Google Scholar]
- Piramuthu, S. HB and Related Lightweight Authentication Protocols for Se-cure RFID Tag/Reader Authentication Title. In Proceedings of the Collaborative Elelctronic Commerce Technology and Research Europe 2006, Basel, Switzerland, 9–10 June 2006; pp. 239–247. [Google Scholar]
- Peris-Lopez, P.; Hernandez-Castro, J.C.; Estévez-Tapiador, J.M.; Ribagorda, A. LMAP: A Real Lightweight Mutual Authentication Protocol for Low-cost RFID Tags. In Proceedings of the 2nd Workshop on RFID Security, Graz, Austria, 12–14 July 2006; pp. 6–17. [Google Scholar]
- Peris-Lopez, P.; Hernandez-Castro, J.C.; Estevez-Tapiador, J.M.; Ribagorda, A. M2AP: A Minimalist Mutual-authentication Protocol for Low-cost RFID Tags. In Proceedings of the 3rd International Conference on Ubiquitous Intelligence and Computing, Wuhan, China, 3–6 September 2006; pp. 912–923. [Google Scholar]
- Li, T. Employing Lightweight Primitives on Low-Cost RFID Tags for Authentication. In Proceedings of the IEEE 68th Vehicular Technology Conference, Calgary, BC, Canada, 21–24 September 2008; pp. 1–5. [Google Scholar]
- Gilbert, H.; Robshaw, M.; Sibert, H. Active Attack against HB+: A Provably Secure Lightweight Authentication Protocol. Electron. Lett. 2005, 41, 1169–1170. [Google Scholar] [CrossRef]
- Ouafi, K.; Overbeck, R.; Vaudenay, S. On the Security of HB# against A Man-in-the-middle Attack. In Proceedings of the 14th International Conference on the Theory and Application of Cryptology and Information Security, Melbourne, Australia, 7–11 December 2008; pp. 108–124. [Google Scholar]
- Safkhani, M.; Bagheri, N.; Naderi, M.; Sanadhya, S.K. Security Analysis of LMAP++, an RFID Authentication Protocol. In Proceedings of the 2011 International Conference for Internet Technology and Secured Transactions, Abu Dhabi, United Arab Emirites, 11–14 December 2011; pp. 689–694. [Google Scholar]
- Wang, S.H.; Zhang, W.W. Passive Attack on RFID LMAP++ Authentication Protocol. In Proceedings of the 10th International Conference on Cryptology and Network Security, Sanya, China, 10–12 December 2011; pp. 185–193. [Google Scholar]
- Wang, S.H.; Liu, S.J.; Chen, D.W. Efficient Passive Full-disclosure Attack on RFID Light-weight Authentication Protocols LMAP++ and SUAP. Telkomnika 2012, 10, 1458–1464. [Google Scholar]
- Chien, H.Y. SASI: A New Ultralightweight RFID Authentication Protocol Providing Strong Authentication and Strong Integrity. IEEE Trans. Dependable Secur. Comput. 2007, 4, 337–340. [Google Scholar] [CrossRef]
- Cao, T.; Bertino, E.; Lei, H. Security Analysis of the SASI Protocol. IEEE Trans. Dependable Secur. Comput. 2009, 6, 73–77. [Google Scholar]
- Phan, R.C.W. Cryptanalysis of A New Ultralightweight RFID Authentication Protocol—SASI. IEEE Trans. Dependable Secur. Comput. 2009, 6, 316–320. [Google Scholar] [CrossRef]
- Sun, H.M.; Ting, W.C.; Wang, K.H. On the Security of Chien’s Ultralightweight RFID Authentication Protocol. IEEE Trans. Dependable Secur. Comput. 2011, 8, 315–317. [Google Scholar] [CrossRef]
- Peris-Lopez, P.; Hernandez-Castro, J.C.; Tapiador, J.M.; Ribagorda, A. Advances in Ultralightweight Cryptography for Low-cost RFID Tags: Gossamer Protocol. In Proceedings of the 9th International Workshop on Information Security Applications, Jeju Island, Korea, 23–25 September 2008; pp. 56–68. [Google Scholar]
- Bilal, Z.; Masood, A.; Kausar, F. Security Analysis of Ultra-Lightweight Cryptographic Protocol for Low-cost RFID Tags: Gossamer Protocol. In Proceedings of the 2009 International Conference on Network-Based Information Systems, Indianapolis, IN, USA, 19–21 August 2009; pp. 260–267. [Google Scholar]
- Fan, K.; Ge, N.; Gong, Y.; Li, H.; Su, R.; Yang, Y. An Ultra-lightweight RFID Authentication Scheme for Mobile Commerce. Peer Peer Netw. Appl. 2017, 10, 368–376. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H. Security Analysis of an Ultra-lightweight RFID Authentication Protocol for M-commerce. Int. J. Commun. Syst. 2019, 32, 3837–3852. [Google Scholar] [CrossRef]
- Pappu, R.; Recht, B.; Taylor, J.; Gershenfeld, N. Physical One-way Functions. Science 2002, 297, 2026–2030. [Google Scholar] [CrossRef] [PubMed]
- Gassend, B.; Clarke, D.; Van Dijk, M.; Devadas, S. Silicon Physical Random Functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 148–160. [Google Scholar]
- Li, X.; Ma, J.; Wang, W.; Xiong, Y.; Zhang, J. A Novel Smart Card and Dynamic ID based Remote User Authentication Scheme for Multi-Server Environments. Math. Comput. Model. 2013, 58, 85–95. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Liao, J.; Liang, W. An Enhancement of a Smart Card Authentication Scheme for Multi-Server Architecture. Wirel. Pers. Commun. 2015, 80, 175–192. [Google Scholar] [CrossRef]
- Maiti, A.; Gunreddy, V.; Schaumont, P. A Systematic Method to Evaluate and Compare the Performance of Physical Unclonable Functions. In Proceedings of the Embedded Systems Design with FPGAs; Springer: New York, NY, USA, 2013; pp. 245–267. [Google Scholar]
- Rührmair, U.; Holcomb, D.E. PUFs at a Glance. In Proceedings of the Design, Automation and Test in Europe, Dresden, Germany, 24–28 March 2014; pp. 347–352. [Google Scholar]
- Gao, Y.; Li, G.; Ma, H.; Al-Sarawi, S.F.; Kavehei, O.; Abbott, D.; Ranasinghe, D.C. Obfuscated Challenge-response: A Secure Lightweight Authentication Mechanism for PUF-based Pervasive Devices. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communication Workshops, Sydney, Australia, 14–18 March 2016; pp. 1–6. [Google Scholar]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical Unclonable Functions and Applications: A Tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Devadas, S.; Suh, E.; Paral, S.; Sowell, R.; Ziola, T.; Khandelwal, V. Design and Implementation of PUF-Based “Unclonable” RFID ICs for Anti-Counterfeiting and Security Applications. In Proceedings of the 2008 IEEE International Conference of RFID, Las Vegas, NV, USA, 16–17 April 2008; pp. 58–64. [Google Scholar]
- Jiang, D.; Chong, C.N. Anti-counterfeiting Using Phosphor PUF. In Proceedings of the 2nd International Conference on Anti-counterfeiting, Security and Identification, Guiyang, China, 20–23 August 2008; pp. 59–62. [Google Scholar]
- Kulseng, L.; Yu, Z.; Wei, Y.; Guan, Y. Lightweight Secure Search Protocols for Low-cost RFID Systems. In Proceedings of the 29th International Conference on Distributed Computing Systems, Montreal, QC, Canada, 22–26 June 2009; pp. 40–48. [Google Scholar]
- Akgun, M.; Caglayan, M.U. Providing Destructive Privacy and Scalability in RFID Systems using PUFs. Ad Hoc Netw. 2015, 32, 32–42. [Google Scholar] [CrossRef]
- Aysu, A.; Gulcan, E.; Moriyama, D.; Schaumont, P.; Yung, M. End-to-end Design of a PUF-based Privacy Preserving Authentication Protocol. In Proceedings of the 17th International Conference of Cryptographic Hardware and Embedded Systems, Saint-Malo, France, 13–16 September 2015; pp. 556–576. [Google Scholar]
- Huth, C.; Aysu, A.; Guajardo, J.; Duplys, P.; Güneysu, T. Secure and Private, yet Lightweight, Authentication for the IoT via PUF and CBKA. In Proceedings of the 19th International Conference on Information Security and Cryptology, Seoul, Korea, 30 November–2 December 2016; pp. 28–48. [Google Scholar]
- Burmester, M.; De Medeiros, B.; Motta, R. Anonymous RFID Authentication Supporting Constant-cost Key-lookup Against Active Adversaries. Int. J. Appl. Cryptogr. 2008, 1, 79–90. [Google Scholar] [CrossRef]
- Kulseng, L.; Yu, Z.; Wei, Y.; Guan, U. Lightweight Mutual Authentication and Ownership Transfer for RFID Systems. In Proceedings of the 29th IEEE International Conference on Computer Communications, San Diego, CA, USA, 14–19 March 2010; pp. 1–5. [Google Scholar]
- Xu, H.; Ding, J.; Li, P.; Zhu, F.; Wang, R. A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function. Sensors 2018, 18, 760. [Google Scholar] [CrossRef]
- Bendavid, Y.; Bagheri, N.; Safkhani, M.; Rostampour, S. IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”. Sensors 2018, 18, 4444. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the Security of Public Key Protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Xie, W.; Xie, L.; Zhang, C.; Zhang, Q.; Tang, C. Cloud-based RFID Authentication. In Proceedings of the 7th Annual IEEE International Conference on RFID, Orlando, FL, USA, 30 April–2 May 2013; pp. 168–175. [Google Scholar]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. Modeling Attacks on Physical Unclonable Functions. In Proceedings of the 17th ACM conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 237–249. [Google Scholar]
- Cremers, C.J. The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols. In Proceedings of the 20th International Conference on Computer Aided Verification, Princeton, NJ, USA, 7–14 July 2008; pp. 414–418. [Google Scholar]
- Differences between Active and Passive Tags. Available online: https://www.rfidjournal.com/faq/show?68 (accessed on 5 June 2019).
- Wang, W.C.; Yona, Y.; Diggavi, S.N.; Gupta, P. Design and Analysis of Stability-guaranteed PUFs. IEEE Trans. Inf. Forensics Secur. 2017, 13, 978–992. [Google Scholar] [CrossRef]
- Van Herrewege, A.; Katzenbeisser, S.; Maes, R.; Peeters, R.; Sadeghi, A.R.; Verbauwhede, I.; Wachsmann, C. Reverse Fuzzy Extractors: Enabling Lightweight Mutual Authentication for PUF-enabled RFIDs. In Proceedings of the 16th International Conference on Financial Cryptography and Data Security, Kralendijk, Bonaire, 27 Februray–2 March 2012; pp. 374–389. [Google Scholar]






| Symbol | Definition |
|---|---|
| ⊕ | Exclusive OR operation |
| || | Concatenation operation |
| PUFT | The physically unclonable function on tag T |
| Hash | One-way hash function shared by tag T and server S |
| Claim | Status | Comments | |||
|---|---|---|---|---|---|
| ideal_PUF | S | ideal_PUF,S1 | Secret N | OK | No attacks within bounds |
| ideal_PUF,S2 | Secret Ri | OK | No attacks within bounds | ||
| ideal_PUF,S3 | Niagree | OK | No attacks within bounds | ||
| ideal_PUF,S4 | Nisynch | OK | No attacks within bounds | ||
| ideal_PUF,S5 | Alive | OK | No attacks within bounds | ||
| ideal_PUF,S6 | Weakagree | OK | No attacks within bounds | ||
| T | ideal_PUF,T1 | Secret M | OK | No attacks within bounds | |
| ideal_PUF,T2 | Secret Ri+1 | OK | No attacks within bounds | ||
| ideal_PUF,T3 | Niagree | OK | No attacks within bounds | ||
| ideal_PUF,T4 | Nisynch | OK | No attacks within bounds | ||
| ideal_PUF,T5 | Alive | OK | No attacks within bounds | ||
| ideal_PUF,T6 | Weakagree | OK | No attacks within bounds |
| Vulnerability | Ideal PUF-based Protocols | Noisy PUF-based Protocols | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| [40] | [44] | [45] | [46] | [47] | Ours | [41] | [42] | [47] | Ours | |
| Traceability | √ | |||||||||
| Lack of Forward Secrecy | √ | √ | √ | √ | ||||||
| Impersonation | ||||||||||
| Desynchronization | √ | √ | ||||||||
| Physical Attacks | √ | √ | √ | √ | ||||||
| Protocols | Computation | Storage (bits) | Bandwidth (bits) | Scalability | |
|---|---|---|---|---|---|
| Ideal PUF-Based Protocols | [40] | 4Hash + 2PUF + RNG | 512 | 384 | No |
| [44] | 3LFSR + 2PUF | 512 | 384 | Yes | |
| [45] | 2PUF + RNG | 384 | 256 | Yes | |
| [46] | 5Hash + 6PUF + RNG | 512 | 384 | Yes | |
| [47] | 4Hash + 2PUF + RNG | 128 + 64n * | 320 | Yes | |
| Ours | 5Hash + 2PUF + RNG | 128 | 384 | Yes | |
| Noisy PUF-Based Protocols | [41] | 3Hash + 2PUF + RNG + SKE + FE.Gen | 192 | 2168 | No |
| [42] | 3Hash + 2PUF + RNG + SKE + CBKA + FE.Rec | 1804 | 2168 | No | |
| [47] | 5Hash + 2PUF + RNG + FE.Rec | 1456 + 1392n * | 1392 | Yes | |
| Ours | 6Hash + 2PUF + RNG + FE.Rec | 1392 | 1392 | Yes |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, F.; Li, P.; Xu, H.; Wang, R. A Lightweight RFID Mutual Authentication Protocol with PUF. Sensors 2019, 19, 2957. https://doi.org/10.3390/s19132957
Zhu F, Li P, Xu H, Wang R. A Lightweight RFID Mutual Authentication Protocol with PUF. Sensors. 2019; 19(13):2957. https://doi.org/10.3390/s19132957
Chicago/Turabian StyleZhu, Feng, Peng Li, He Xu, and Ruchuan Wang. 2019. "A Lightweight RFID Mutual Authentication Protocol with PUF" Sensors 19, no. 13: 2957. https://doi.org/10.3390/s19132957
APA StyleZhu, F., Li, P., Xu, H., & Wang, R. (2019). A Lightweight RFID Mutual Authentication Protocol with PUF. Sensors, 19(13), 2957. https://doi.org/10.3390/s19132957





