On the Performance of Random Cognitive mmWave Sensor Networks
Abstract
:1. Introduction
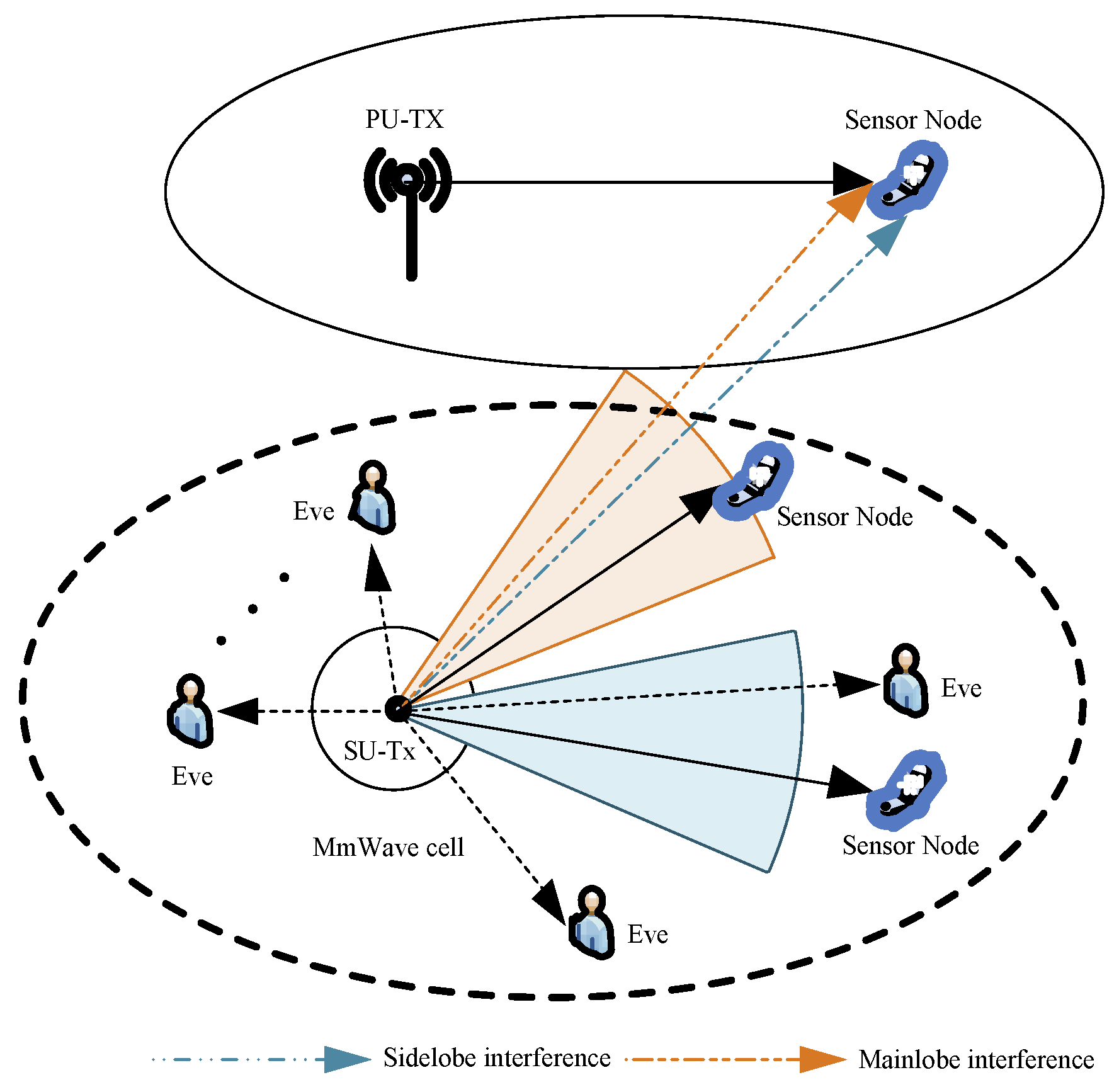
- By using stochastic geometry approaches, we model the cognitive mmWave wiretap sensor networks to characterize the random spatial locations of primary and secondary nodes, as well as the eavesdroppers. Taking into account the effect of blockage, the links are either LOS or NLOS. A sector secrecy guard zone, synonymously referred to as the eavesdropper-exclusion area, is invoked around the secondary transmitter (SU-Tx) for improving the PLS.
- Considering that the random-location of both eavesdroppers and the primary sensor node may reside in the signal beam of the secondary network, we derive analytical expressions of secrecy throughput (ST) for the secondary sensor node to measure secrecy performance of the system with arbitrary system parameters. Subsequently, an asymptotic expression is proposed to gain additional insight into the performance evaluation and design for the proposed system.
- The results show that the interference temperature constraint of the primary sensor node can be used to balance secrecy performance of the secondary network, which indicates losing the interference temperature constraint of the primary node would worsen secrecy performance. Increasing the radius of the sector guard zone can improve ST. Furthermore, it is also shown that increasing the transmit power or antenna gain of the secondary network does not necessarily lead to the improvement of ST, and sometimes deteriorate ST. Besides, blockages can also be used to improve ST of SU-Rx under certain conditions.
2. System Model
2.1. Network Topology
2.2. Directional Beamforming
2.3. Channel Model
2.4. Received SINR
3. Secrecy Performance Analysis
3.1. ST of the Secondary Sensor Node
3.2. Asymptotic Behavior
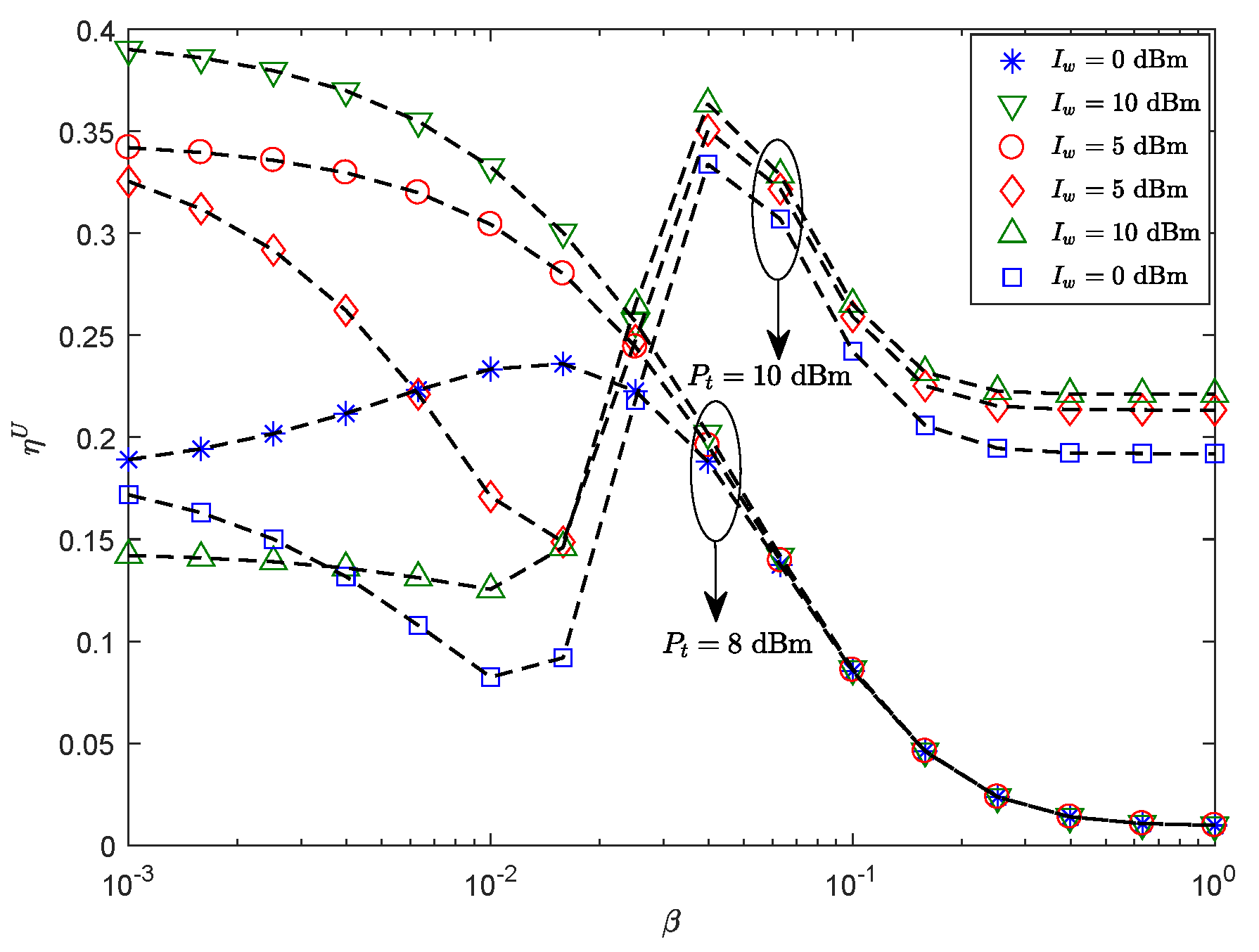
4. Numerical Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
Appendix B
References
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.-K.; Gao, X. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef]
- Hosseini, H.; Anpalagan, A.; Raahemifar, K.; Erkucuk, S. Wavelet-Based Cognitive SCMA System for mmWave 5G Communication Networks. IET Commun. 2017, 11, 831–836. [Google Scholar] [CrossRef]
- Hosseini, H.; Anpalagan, A.; Raahemifar, K.; Erkucuk, S.; Habib, S. Joint Wavelet-Based Spectrum Sensing and FBMC Modulation for Cognitive mmWave Small Cell Networks. IET Commun. 2016, 10, 1803–1809. [Google Scholar] [CrossRef]
- Park, J.; Andrews, J.G.; Heath, R.W. Inter-Operator Base Station Coordination in Spectrum-Shared Millimeter Wave Cellular Networks. IEEE Trans. Cogn. Commun. Netw. 2018, 4, 513–528. [Google Scholar] [CrossRef]
- Xu, X.; Yang, W.; Cai, Y.; Jin, S. On the Secure Spectral-Energy Efficiency Tradeoff in Random Cognitive Radio Networks. IEEE J. Sel. Areas Commun. 2016, 34, 2706–2722. [Google Scholar] [CrossRef]
- Fragkiadakis, A.G.; Tragos, E.Z.; Askoxylakis, I.G. A Survey on Security Threats and Detection Techniques in Cognitive Radio Networks. IEEE Commun. Surv. Tutor. 2013, 15, 428–445. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.; Rodrigues, M.R.D.; McLaughlin, S.W. Wireless Information-Theoretic Security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Shi, H.; Yang, W.; Chen, D.; Luo, Y.; Cai, Y. Secure Transmission for Simultaneous Wireless Information and Power Transfer in AF Untrusted Relay Networks. Sensors 2018, 19, 76. [Google Scholar] [CrossRef]
- Tang, X.; Cai, Y.; Yang, W.; Yang, W.; Chen, D.; Hu, J. Secure Transmission of Cooperative Zero-Forcing Jamming for Two-User SWIPT Sensor Networks. Sensors 2018, 18, 331. [Google Scholar] [CrossRef]
- Xiang, Z.; Yang, W.; Pan, G.; Cai, Y.; Sun, X. Secure Transmission in Non-Orthogonal Multiple Access Networks with an Untrusted Relay. IEEE Wirel. Commun. Lett. 2019, 8, 905–908. [Google Scholar] [CrossRef]
- Xiang, Z.; Yang, W.; Pan, G.; Cai, Y.; Song, Y. Physical Layer Security in Cognitive Radio Inspired NOMA Network. IEEE J. Sel. Top. Signal Process. 2019, 13, 700–714. [Google Scholar] [CrossRef]
- Tang, X.; Cai, Y.; Huang, Y.; Duong, T.Q.; Yang, W.; Yang, W. Secrecy Outage Analysis of Buffer-Aided Cooperative MIMO Relaying Systems. IEEE Trans. Veh. Technol. 2017, 67, 2035–2048. [Google Scholar] [CrossRef]
- Li, B.; Qi, X.; Huang, K.; Fei, Z.; Zhou, F.; Hu, R.Q. Security-Reliability Tradeoff Analysis for Cooperative NOMA in Cognitive Radio Networks. IEEE Trans. Commun. 2019, 67, 83–96. [Google Scholar] [CrossRef]
- Atallah, M.; Kaddoum, G. Secrecy Analysis in Wireless Network with Passive Eavesdroppers by Using Partial Cooperation. IEEE Trans. Veh. Technol. 2019, 68, 7225–7230. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A Comprehensive Survey on Cooperative Relaying and Jamming Strategies for Physical Layer Security. IEEE Commun. Surv. Tutor. 2019. [Google Scholar] [CrossRef]
- Xu, X.; He, B.; Yang, W.; Zhou, X.; Cai, Y. Secure Transmission Design for Cognitive Radio Networks With Poisson Distributed Eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2016, 11, 373–387. [Google Scholar] [CrossRef]
- Cai, Y.; Xu, X.; Yang, W. Secure Transmission in the Random Cognitive Radio Networks with Secrecy Guard Zone and Artificial Noise. IET Commun. 2017, 10, 1904–1913. [Google Scholar] [CrossRef]
- Zou, Y.; Li, X.; Liang, Y.-C. Secrecy Outage and Diversity Analysis of Cognitive Radio Systems. IEEE J. Sel. Areas Commun. 2017, 32, 2222–2236. [Google Scholar] [CrossRef]
- Atallah, M.; Kaddoum, G. Design and Performance Analysis of Secure Multicasting Cooperative Protocol for Wireless Sensor Network Applications. IEEE Wirel. Commun. Lett. 2019. [Google Scholar] [CrossRef]
- Valliappan, N.; Lozano, A.; Heath, R.W. Antenna Subset Modulation for Secure Millimeter-Wave Wireless Communication. IEEE Trans. Commun. 2013, 61, 3231–3245. [Google Scholar] [CrossRef] [Green Version]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Renzo, M.D. Safeguarding 5G Wireless Communication Networks Using Physical Layer Security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Yang, W.; Tao, L.; Sun, X.; Ma, R.; Cai, Y.; Zhang, T. Secure on-off transmission in mmWave systems with randomly distributed eavesdroppers. IEEE Access. 2019, 7, 32681–32692. [Google Scholar] [CrossRef]
- Vuppala, S.; Biswas, S.; Ratnarajah, T. An Analysis on Secure Communication in Millimeter/Micro-Wave Hybrid Networks. IEEE Trans. Commun. 2015, 64, 3507–3519. [Google Scholar] [CrossRef]
- Wang, L.; Elkashlan, M.; Duong, T.Q.; Heath, R.W. Secure Communication in Cellular Networks: The Benefits of Millimeter Wave Mobile Broadband. In Proceedings of the 2014 IEEE 15th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Toronto, ON, Canada, 22–25 June 2014; pp. 115–119. [Google Scholar]
- Wang, C.; Wang, H.-M. Physical Layer Security in Millimeter Wave Cellular Networks. IEEE Trans. Wirel. Commun. 2016, 15, 5569–5585. [Google Scholar] [CrossRef] [Green Version]
- Zhu, Y.; Wang, L.; Wong, K.-K.; Heath, R.W. Secure Communications in Millimeter Wave Ad Hoc Networks. IEEE Trans. Wirel. Commun. 2017, 16, 3205–3217. [Google Scholar] [CrossRef] [Green Version]
- Sun, X.; Yang, W.; Cai, Y.; Xiang, Z.; Tang, X. Secure Transmissions in Millimeter Wave SWIPT UAV-Based Relay Networks. IEEE Wirel. Commun. Lett. 2019, 8, 785–788. [Google Scholar] [CrossRef]
- Zhu, Y.; Zheng, G.; Fitch, M. Secrecy Rate Analysis of UAV-Enabled mmWave Networks Using Matérn Hardcore Point Processes. IEEE J. Sel. Areas Commun. 2018, 36, 1397–1409. [Google Scholar] [CrossRef]
- Rangan, S.; Rappaport, T.S.; Erkip, E. Millimeter-Wave Cellular Wireless Networks: Potentials and Challenges. arXiv 2014, arXiv:1401.2560. [Google Scholar] [CrossRef]
- Vuppala, S.; Tolossa, Y.J.; Member, S.S.; Kaddoum, G.; Abreu, G.; Member, S.S. On the Physical Layer Security Analysis of Hybrid Millimeter Wave Networks. IEEE Trans. Commun. 2018, 66, 1139–1152. [Google Scholar] [CrossRef]
- Tao, L.; Yang, W.; Yang, W.; Cai, Y. Capacity Threshold-based On-off Transmission in mmWave Systems with Randomly Distributed Eavesdroppers. In Proceedings of the 10th International Conference on Wireless Communications and Signal Processing (WCSP 2018), Hangzhou, China, 18–20 October 2018; pp. 1–6. [Google Scholar]
- Song, Y.; Yang, W.; Xiang, Z.; Wang, B.; Cai, Y. Secure Transmission in mmWave NOMA Networks With Cognitive Power Allocation. IEEE Access. 2019, 7, 76104–76119. [Google Scholar] [CrossRef]
- Turgut, E.; Gursoy, M.C. Coverage in Heterogeneous Downlink Millimeter Wave Cellular Networks. IEEE Trans. Commun. 2017, 65, 4463–4477. [Google Scholar] [CrossRef]
- He, B.; Member, S.; Zhou, X.; Abhayapala, T.D.; Member, S. Achieving Secrecy Without Knowing the Number of Eavesdropper Antennas. IEEE Trans. Wirel. Commun. 2015, 14, 7030–7043. [Google Scholar] [CrossRef] [Green Version]
- Kolawole, O.Y.; Vuppala, S.; Sellathurai, M.; Ratnarajah, T. On the Performance of Cognitive Satellite-Terrestrial Networks. IEEE Trans. Cogn. Commun. Netw. 2017, 3, 668–683. [Google Scholar] [CrossRef] [Green Version]
- MacCartney, G.R.; Rappaport, T.S.; Sun, S.; Deng, S. Indoor Office Wideband Millimeter-wave Propagation Measurements and Channel Models at 28 and 73 GHz for Ultra-Dense 5G Wireless Networks. IEEE Access. 2015, 3, 2388–2424. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic Press: New York, NY, USA, 2007. [Google Scholar]



© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, Y.; Yang, W.; Xiang, Z.; Wang, B.; Cai, Y. On the Performance of Random Cognitive mmWave Sensor Networks. Sensors 2019, 19, 3184. https://doi.org/10.3390/s19143184
Song Y, Yang W, Xiang Z, Wang B, Cai Y. On the Performance of Random Cognitive mmWave Sensor Networks. Sensors. 2019; 19(14):3184. https://doi.org/10.3390/s19143184
Chicago/Turabian StyleSong, Yi, Weiwei Yang, Zhongwu Xiang, Biao Wang, and Yueming Cai. 2019. "On the Performance of Random Cognitive mmWave Sensor Networks" Sensors 19, no. 14: 3184. https://doi.org/10.3390/s19143184
APA StyleSong, Y., Yang, W., Xiang, Z., Wang, B., & Cai, Y. (2019). On the Performance of Random Cognitive mmWave Sensor Networks. Sensors, 19(14), 3184. https://doi.org/10.3390/s19143184




