Secure Trust-Based Blockchain Architecture to Prevent Attacks in VANET
Abstract
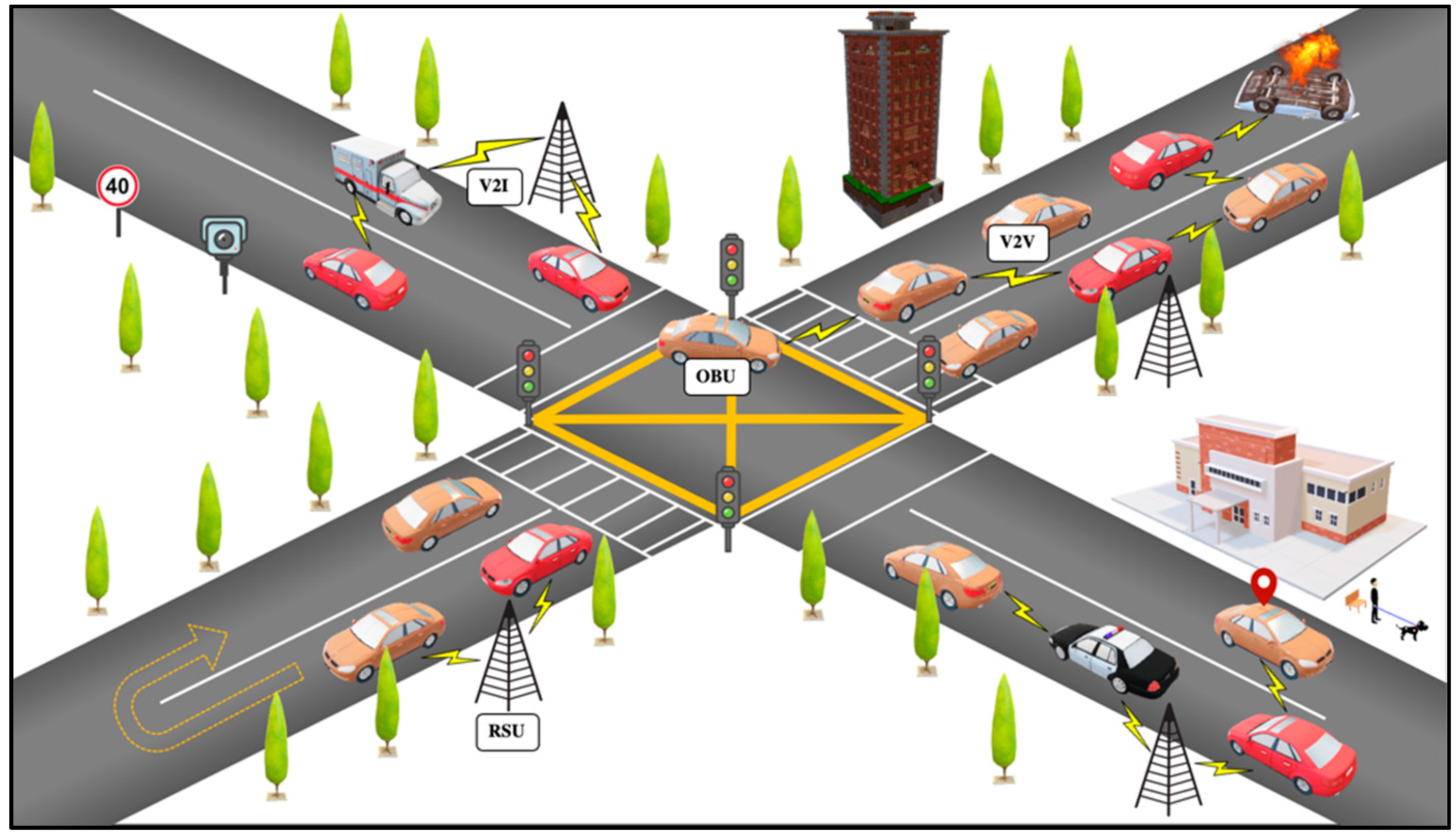
:1. Introduction
2. Related Works
3. Motivation
4. Proposed Blockchain in VANET
4.1. Design of Proposed Blockchain Architecture
4.1.1. System Initialization
4.1.2. System Authentication
4.1.3. Message Rating Generation
| Algorithm 1 Message rating generation |
| Require: Mj: Message group reporting event ej broadcasted by Vehicle Vi (i = 1, 2, …n); Cji: credibility of Mj as reported by Vi; Cj {}: credibility set for event ej; P(e/C): probability of event e; Thr: threshold of event probability; R’i: current rating of Vi Ensure: Ri: Updated rating of Vi |
| 1: if (i = 0) then |
| 2: Cji = 0 |
| 3: else for each Vi do |
| 4: calculate Cji |
| 5: Cj {}← Cji |
| 6: end for |
| 7: calculate P(e/C) using Cj {} |
| 8: if (P(e/C) > Thr) then |
| 9: for each (Mj = true) do |
| 10: Ri ← R’i + 1 |
| 11: end for |
| 12: else for each (Mj = false) do |
| 13: Ri ← R’i − 1 |
| 14: end for |
| 15: end if |
| 16: end if |
4.1.4. Trust Value Offset Calculation
| Algorithm 2 Trust value offset calculation |
| Require: Ri: Updated rating of Vi; T’i: current trust value of Vi; Or {}: RSU r set of offsets Ensure: Ti: Updated trust value of Vi |
| 1: if (i = 0) then |
| 2: Ti ← T’i + 0 |
| 3: else for each Vi do |
| 4: get Ri |
| 5: calculate offset |
| 6: Ti ← T’i |
| 7: Or {} ← Ti |
| 8: end for |
4.1.5. Miner Election and Block Generation
5. Simulation Tool and Set-Up
5.1. Selection of Simulation Tool
5.2. Simulation Environment Set-Up
6. Results and Discussion
6.1. Packet Delivery Ratio (PDR)
6.2. End-to-End Delay
6.3. Packet Loss
6.4. Transmission Overhead
6.5. Computational Cost
6.6. Security Analysis
6.7. Secure Routing Mechanism
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ghori, M.R.; Zamli, K.Z.; Quosthoni, N.; Hisyam, M.; Montaser, M. Vehicular ad-hoc network (VANET): Review. In Proceedings of the 2018 IEEE International Conference on Innovative Research and Development (ICIRD), Bangkok, Thailand, 11–12 May 2018. [Google Scholar]
- Gillani, S.; Shahzad, F.; Qayyum, A.; Mehmood, R. A survey on security in vehicular ad hoc networks. In Communication Technologies for Vehicles. Nets4Cars/Nets4Trains 2013. Lecture Notes in Computer Science; Berbineau, M., Jonsson, M., Bonnin, J., Cherkaoui, S., Aguado, M., Rico-Garcia, C., Ghannoum, H., Mehmood, R., Vinel, A., Eds.; Springer: Heidelberg/Berlin, Germany, 2013; pp. 59–74. [Google Scholar] [CrossRef]
- Abbasi, I.A.; Khan, A.S. A review of vehicle to vehicle communication protocols for VANETs in the urban environment. Future Internet 2018, 10, 14. [Google Scholar] [CrossRef]
- Junaid, M.A.H.A.; Syed, A.; Warip, M.N.M.; Azir, K.N.F.K.; Romli, N.H. Classification of security attacks in VANET: A review of requirements and perspectives. In Proceedings of the Malaysia Technical Universities Conference on Engineering and Technology, Penang, Malaysia, 6–7 December 2017. [Google Scholar]
- Malik, N.; Nanda, P.; Arora, A.; He, X.; Puthal, D. Blockchain based secured identity authentication and expeditious revocation framework for vehicular networks. In Proceedings of the 2018 17 th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering, New York, NY, USA, 1–3 August 2018. [Google Scholar]
- Hasrouny, H.; Bassil, C.; Samhat, A.E.; Laouti, A. Group-based authentication in V2V communications. In Proceedings of the 2015 5th International Conference on Digital Information and Communication Technology and its Applications, Beirut, Lebanon, 29 April–1 May 2015. [Google Scholar]
- Patel, N.J.; Jhaveri, R.H. Trust based approaches for secure routing in VANET: A survey. Pro. Comp. Sci. 2015, 45, 592–601. [Google Scholar] [CrossRef]
- Zeadally, S.; Hunt, R.; Chen, Y.S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Bhoi, S.K.; Khillar, P.M.; Singh, M.; Sahoo, M.M.; Swain, R.R. A routing protocol for urban vehicular ad hoc networks to support non-safety applications. Digital Commun. Networks 2018, 4, 189–199. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deborah, L.J. Comprehensive survey on security services in vehicular ad-hoc networks. IET Intell. Transport Syst. 2016, 10, 379–388. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Razzaque, M.A.; Zainal, A. Mobility pattern based misbehavior detection in vehicular adhoc networks to enhance safety. In Proceedings of the 2014 International Conference on Connected Vehicles and Expo, Vienna, Austria, 3–7 November 2014. [Google Scholar]
- Qu, F.; Wu, Z.; Wang, F.Y.; Cho, W. A security and privacy review of VANETs. IEEE Trans. Intell. Transp. Syst. 2015, 10, 2985–2996. [Google Scholar] [CrossRef]
- Lai, C.; Zhang, K.; Cheng, N.; Li, H.; Shen, X. SIRC: A secure incentive scheme for reliable cooperative downloading in highway VANETs. IEEE Trans. Intell. Transp. Syst. 2017, 18, 1559–1574. [Google Scholar] [CrossRef]
- Engoulou, R.G.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Begum, R.; Raziuddin, S.; Prasad, V.K. A survey on VANETs applications and its challenges. In Proceedings of the International Conference on Advanced Computer Science & Software Engineering, Hyderabad, India, 11 March 2016. [Google Scholar]
- Xi, Y.; Sha, K.; Shi, W.; Schwiebert, L.; Zhang, T. Enforcing privacy using symmetric random key-set in vehicular networks. In Proceedings of the Eighth International Symposium on Autonomous Decentralized Systems, Phoenix, AZ, USA, 21–23 March 2007. [Google Scholar]
- Defrawy, K.E.; Tsudik, G. ALARM: Anonymous location-aided routing in suspicious MANETs. IEEE Trans. Mob. Comput. 2016, 10, 1345–1358. [Google Scholar] [CrossRef]
- Chaubey, N.K. Security analysis of vehicular ad hoc networks (VANETs): A comprehensive study. Int. J. Secur. Appl. 2016, 10, 261–274. [Google Scholar] [CrossRef]
- Florian, M.; Finster, S.; Baumgart, I. Privacy-preserving cooperative route planning. IEEE Internet Things J. 2014, 1, 590–599. [Google Scholar] [CrossRef]
- Li, J.; Lu, H.; Guizani, M. ACPN: A novel authentication framework with conditional privacy-preservation and non-repudiation for VANETs. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 938–948. [Google Scholar] [CrossRef]
- Rabieh, K.; Mahmoud, M.M.E.A.; Younis, M. Privacy-preserving route reporting schemes for traffic management systems. IEEE Trans. Veh. Technol. 2017, 66, 2703–2713. [Google Scholar] [CrossRef]
- Rabieh, K.; Mahmoud, M.M.E.A.; Guo, T.N.; Mohamed, M. Cross-layer scheme for detecting large-scale colluding Sybil attack in VANETs. In Proceedings of the 2015 IEEE International Conference on Communications, London, UK, 8–12 June 2015. [Google Scholar] [CrossRef]
- Zhang, Y.; Zheng, D.; Deng, R.H. Security and privacy in smart health: Efficient policy-hiding attribute-based access control. IEEE Internet Things J. 2018, 5, 2130–2145. [Google Scholar] [CrossRef]
- Lu, Z.; Qu, G.; Li, Z. A survey on recent advances in vehicular network security, trust, and privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Anonymous and lightweight authentication for secure vehicular networks. IEEE Trans. Veh. Technol. 2017, 66, 10626–10636. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Odelu, V.; Reddy, A.G.; Park, K.; Park, Y. Design of lightweight authentication and key agreement protocol for vehicular ad hoc networks. IEEE Access 2017, 5, 14966–14980. [Google Scholar] [CrossRef]
- Rajput, U.; Abbas, F.; Eun, H.; Oh, H. A hybrid approach for efficient privacy-preserving authentication in VANET. IEEE Access 2017, 5, 12014–12030. [Google Scholar] [CrossRef]
- Tangade, S.; Manvi, S.S. Scalable and privacy-preserving authentication protocol for secure vehicular communications. In Proceedings of the 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems, Bangalore, India, 6–9 November 2016. [Google Scholar] [CrossRef]
- Cui, J.; Zhang, J.; Zhong, H.; Xu, Y. SPACF: A secure privacy-preserving authentication scheme for VANET with CUCKOO Filter. IEEE Trans. Veh. Technol. 2017, 66, 10283–10295. [Google Scholar] [CrossRef]
- Lim, K.; Manivannan, D. An efficient protocol for authenticated and secure message delivery in vehicular ad hoc networks. Veh. Commun. 2016, 4, 30–37. [Google Scholar] [CrossRef]
- Raya, M.; Jungels, D.; Papadimitratos, P.; Aad, I.; Hubaux, J.-P. Certificate revocation in vehicular networks; Laboratory for computer Communications and Applications (LCA), School of Computer and Communication Sciences, EPFL: Lausanne, Switzerland, 2006. [Google Scholar]
- La, V.H.; Cavalli, A.R. Security attacks and solutions in vehicular ad hoc networks: A survey. Int. J. AdHoc networking Syst. 2014, 4, 1–20. [Google Scholar]
- Abbasi, I.A.; Khan, A.S.; Ali, S. A Reliable Path Selection and Packet Forwarding Routing Protocol for Vehicular Ad hoc Networks. EURASIP J. Wirel. Commun. Networking 2018, 1, 236. [Google Scholar] [CrossRef]
- Wu, Q.; Liu, Q.; Zhang, L.; Zhang, Z. A trusted routing protocol based on GeoDTN+Nav in VANET. China Commun. 2014, 11, 166–174. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/en/bitcoin-paper (accessed on 31 October 2008).
- Hammad, B.T.; Jamli, N.; Rusli, M.E.; Z’aba, M.R. A survey of lightweight cryptographic hash function. Inter. J. Sci. Eng. Res. 2017, 8, 806–814. [Google Scholar]
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.K.; Zhang, J.Z.C. “What Will 5G Be?”. IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Cheng, N.; Lyu, F.; Chen, J.; Xu, W.; Zhou, H.; Zhang, S.; Shen, X. Big Data Driven Vehicular Networks. IEEE Network 2018, 32, 1–8. [Google Scholar] [CrossRef]
- Chen, S.; Hu, J.; Shi, Y.; Peng, Y.; Fang, J.; Zhao, R.; Zhao, L. Vehicle-to-everything (V2X) services supported by LTE-based systems and 5G. IEEE Commun. Stand. Mag 2017, 1, 70–76. [Google Scholar] [CrossRef]
- Farooq, S.; Hussain, S.; Kiran, S.; Ustun, T. Certificate based security mechanisms in vehicular ad-hoc networks based on IEC 61850 and IEEE WAVE standards. Electronics 2019, 8, 96. [Google Scholar] [CrossRef]
- Balan, K.; Khan, A.S.; Julaihi, A.A.; Tarmizi, S.; Pillay, K.S. RSSI and Public Key Infrastructure based Secure Communication in Autonomous Vehicular Networks. Inter. J. Adv. Comput. Sci. Appl. 2018, 9, 298–304. [Google Scholar] [CrossRef]
- Draz, U.; Ali, T.; Yasin, S.; Shaf, A. Evaluation based analysis of packet delivery ratio for AODV and DSR under UDP and TCP environment. In Proceedings of the 2018 International Conference on Computing, Mathematics and Engineering Technologies, Sukkur, Pakistan, 3–4 March 2018. [Google Scholar] [CrossRef]
- Shorfuzzaman, M.; Masud, M.; Rahman, M.M. Characterizing end-to-end delay performance of randomized TCP using an analytical model. Int. J. Adv. Comput. Sci. Appl. 2016, 7, 406–412. [Google Scholar] [CrossRef] [Green Version]
- Pukale, P.; Gupta, P. Analysis of end-to-end delay in vehicular networks. Int. J. Sci. Res. 2013, 5, 1122–1125. [Google Scholar]
- Luo, J.; Gu, X.X.; Zhao, T.; Yan, W. A mobile infrastructure based VANET routing protocol in the urban environment in Communications and Mobile Computing (CMC). In Proceedings of the 2010 International Conference on Communications and Mobile Computing, Shenzhen, China, 12–14 April 2010. [Google Scholar]
- Samundiswary, P.; Sathian, D.; Dananjayan, P. Secured greedy perimeter stateless routing for wireless sensor networks. Inter. J. Ad hoc. Sens. Ubiquitous Comput. 2010, 1, 9–20. [Google Scholar]
- Lyamin, N.; Vinel, A.; Jonsson, M.; Bellalta, B. Cooperative awareness in VANETs: On ETSI EN 302 637-2 performance. IEEE Trans. Veh. Technol. 2018, 67, 17–28. [Google Scholar] [CrossRef]
- Lyamin, N.; Vinel, A.; Jonsson, M. Poster: On the performance of ETSI EN 302 637-2 CAM generation frequency management. In Proceedings of the 2014 IEEE Vehicular Networking Conference, Paderborn, Germany, 3–5 December 2014. [Google Scholar] [CrossRef]




















| Notation | Description |
|---|---|
| Vi | Vehicle i |
| PUi | Public Key of Vi |
| PRi | Private Key of Vi |
| Ci | Certificate of Vi |
| CertBC | Certificate Blockchain |
| RevBC | Revocation Blockchain |
| IDi | Identity of Vi |
| Mi | Message i from Vehicle i |
| TrustBC | Trust Blockchain |
| P(e/c) | Probability of Event e |
| MesBC | Message Blockchain |
| Or | Set of Offsets of Road Side Unit r |
| SR | Hash Threshold of RSU r |
| RSSIi | Relative Signal Strength Indicator Value of Vehicle i |
| ti | Timestamp of Vehicle i |
| hn | Hash Value of block |
| Parameter | Values |
|---|---|
| Number of Nodes | 100 |
| Maximum Vehicle Speed | 33 m/s |
| Maximum Acceleration | 2.6 m/s2 |
| Maximum Deceleration | 4.5 m/s2 |
| Vehicle Length | 5 m |
| Vehicle Width | 3.5 m |
| Number of RSUs | 10 |
| RSU Coverage Driver Imperfection | 1 km 0.5 |
| Parameter | Values |
|---|---|
| Sim-Time-Limit | 6000 s |
| Mac.queuelength | 5 |
| Mac.maxTxAttempts | 14 |
| Mac.bitrate | 11 Mbps |
| Mac.txpower | 100 mW |
| Mac.contentionWindow | 20 |
| Mac.slotduration | 0.04 s |
| Phy. Sensitivity | −80 dBm |
| UpdateInterval | 0.1 s |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, A.S.; Balan, K.; Javed, Y.; Tarmizi, S.; Abdullah, J. Secure Trust-Based Blockchain Architecture to Prevent Attacks in VANET. Sensors 2019, 19, 4954. https://doi.org/10.3390/s19224954
Khan AS, Balan K, Javed Y, Tarmizi S, Abdullah J. Secure Trust-Based Blockchain Architecture to Prevent Attacks in VANET. Sensors. 2019; 19(22):4954. https://doi.org/10.3390/s19224954
Chicago/Turabian StyleKhan, Adnan Shahid, Kuhanraj Balan, Yasir Javed, Seleviawati Tarmizi, and Johari Abdullah. 2019. "Secure Trust-Based Blockchain Architecture to Prevent Attacks in VANET" Sensors 19, no. 22: 4954. https://doi.org/10.3390/s19224954
APA StyleKhan, A. S., Balan, K., Javed, Y., Tarmizi, S., & Abdullah, J. (2019). Secure Trust-Based Blockchain Architecture to Prevent Attacks in VANET. Sensors, 19(22), 4954. https://doi.org/10.3390/s19224954






