Water Pipeline Leakage Detection Based on Machine Learning and Wireless Sensor Networks
Abstract
:1. Introduction
2. Water Pipeline Leakage Monitoring System Based on ZigBee Technology
3. Leakage Triggered ZigBee Networking
4. Leakage Detection by Using Machine Learning and Time-Frequency Features
4.1. Time-Frequency Analysis of the Acoustic Leakage Signal
4.1.1. Spectrum Density Feature
- (1)
- The number of extreme points is (including the minimum and maximum values), which is the same as or no more than one from the number of zero crossing points ,
- (2)
- At an arbitrary time within the time period, the mean of the upper envelope determined by the local maximum and the lower envelope determined by the local minimum is zero,
4.1.2. Signal Complexity Feature
4.1.3. Signal Principal Component Feature
4.2. Machine Learning Inspired Water Pipeline Leakage Detection
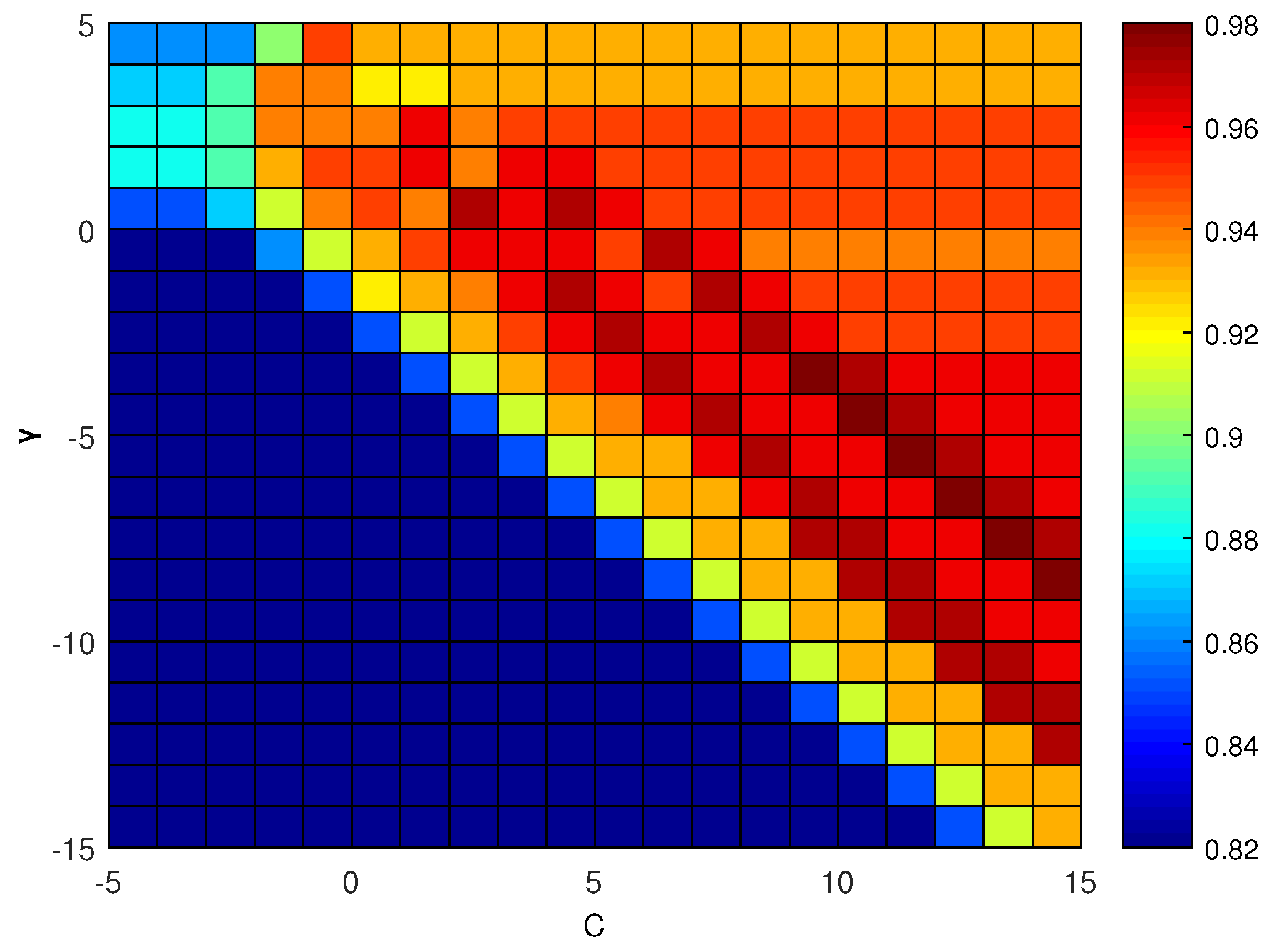
5. Simulation Results
5.1. Leakage Triggered Networking
5.2. Leakage Identification
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| WSNs | Wireless sensor networks |
| SVM | Support vector machine |
| LPCC | Linear predictive coding coefficient |
| HMM | Hidden Markov model |
| PCA | Principal component analysis |
| LOS | Line-of-sight |
| NLOS | Non-line-of-sight |
| RSSI | Received signal strength indicator |
| EMD | Empirical mode decomposition |
| IMFs | Intrinsic mode functions |
| ApEn | Approximate entropy |
| SD | Standard deviation |
References
- Tindall, J.A.; Campbell, A.A. Water security-national and global issues. Sex. Relatsh. Ther. 2010, 30, 314–324. [Google Scholar]
- Lang, X.; Li, P.; Hu, Z.; Ren, H.; Li, Y. Leak detection and location of pipelines based on LMD and least squares twin support vector machine. IEEE Access 2017, 5, 8659–8668. [Google Scholar] [CrossRef]
- Cataldo, A.; Cannazza, G.; Benedetto, E.D.; Giaquinto, N. A new method for detecting leaks in underground water pipelines. IEEE Sens. J. 2012, 12, 1660–1667. [Google Scholar] [CrossRef]
- Fang, D.; Chen, B. Ecological network analysis for a virtual water network. Environ. Sci. Technol. 2015, 49, 6722–6730. [Google Scholar] [CrossRef] [PubMed]
- Moore, N.M. The Green City: Sustainable homes, sustainable suburbs. Nicholas Low, Brendan Gleeson, Ray Green, and Darko Radović. Urban Geogr. 2009, 30, 927–928. [Google Scholar] [CrossRef]
- Martini, A.; Troncossi, M.; Rivola, A. Automatic leak detection in buried plastic pipes of water supply networks by means of vibration measurements. Shock Vibrat 2015, 2015, 1–13. [Google Scholar] [CrossRef]
- Kim, H.; Shin, E.S.; Chung, W.J. Energy demand and supply, energy policies, and energy security in the Republic of Korea. Energy Policy 2011, 39, 6882–6897. [Google Scholar] [CrossRef]
- Puust, R.; Kapelan, Z.; Savic, D.A.; Koppel, T. A review of methods for leakage management in pipe networks. Urban Water J. 2010, 7, 25–45. [Google Scholar] [CrossRef]
- Wang, F.; Lin, W.; Liu, Z.; Wu, S.; Qiu, X. Pipeline leak detection by using time-domain statistical features. IEEE Sens. J. 2017, 17, 6431–6442. [Google Scholar] [CrossRef]
- Lay-Ekuakille, A.; Vergallo, P. Decimated signal diagonalization method for improved spectral leak detection in pipelines. IEEE Sens. J. 2014, 14, 1741–1748. [Google Scholar] [CrossRef]
- Thompson, M.; Chapman, C.J.; Howison, S.D.; Ockendon, J.R. Noise generation by water pipe leaks. In Proceedings of the 40th European Study Group with Industry, Keele, UK, 9–12 April 2001; pp. 1–4. [Google Scholar]
- Yang, J.; Wen, Y.; Li, P. Leak acoustic detection in water distribution pipelines. In Proceedings of the 7th World Congress on Intelligent Control and Automation, Chongqing, China, 25–27 June 2008; pp. 3057–3061. [Google Scholar]
- Goulet, J.A.; Coutu, S.; Smith, I.F.C. Model falsification diagnosis and sensor placement for leak detection in pressurized pipe networks. Adv. Eng. Inform. 2013, 27, 261–269. [Google Scholar] [CrossRef]
- Cabrera, D.A.; Herrera, M.; Izquierdo, J.; Levario, S.J.O.; Garcia, R.P. GPR-based water leak models in water distribution systems. Sensors 2013, 13, 15912–15936. [Google Scholar] [CrossRef]
- Benkherouf, A.; Allidina, A.Y. Leak detection and location in gas pipelines. IEE Proc. D Control. Theory Appl. 1988, 135, 142–148. [Google Scholar] [CrossRef]
- Chen, H.; Ye, H.; Chen, L.V.; Su, H. Application of support vector machine learning to leak detection and location in pipelines. In Proceedings of the 21st IEEE Instrumentation and Measurement Technology, Como, Italy, 18–20 May 2004; pp. 2273–2277. [Google Scholar]
- Ellul, I.R. Advances in pipeline leak detection techniques. Pipes Pipelines Int. 1989, 34, 7–12. [Google Scholar]
- Wan, Q.; Koch, D.B.; Morris, K. Multichannel spectral analysis for tube leak detection. In Proceedings of the Southeastcon’93, Charlotte, NC, USA, 4–7 April 1993. [Google Scholar]
- Ai, C.S.; Zhao, H.; Ma, R.J.; Dong, X. Pipeline damage and leak detection based on sound spectrum LPCC and HMM. In Proceedings of the Sixth International Conference on Intelligent System Design and Applications, Jinan, China, 16–18 October 2006; pp. 829–833. [Google Scholar]
- Martini, A.; Rivola, A.; Troncossi, M. Autocorrelation analysis of vibro-acoustic signals measured in a test field for water leak detection. Appl. Sci. 2018, 8, 2450. [Google Scholar] [CrossRef]
- Hunaidi, O.; Chu, W.T. Acoustical characteristics of leak signals in plastic water distribution pipes. Appl. Acoust. 1999, 58, 235–254. [Google Scholar] [CrossRef]
- Martini, A.; Troncossi, M.; Rivola, A. Vibroacoustic measurements for detecting water leaks in buried small-diameter plastic pipes. J. Pipeline Syst. Eng. Pract. 2017, 8, 1–10. [Google Scholar] [CrossRef]
- Kang, J.; Park, Y.; Lee, J.; Wang, S.; Eom, D. Novel leakage detection by ensemble CNN-SVM and graph-based localization in water distribution systems. IEEE Trans. Ind. Electron. 2018, 65, 4279–4289. [Google Scholar] [CrossRef]
- Chraim, F.; Erol, Y.B.; Pister, K. Wireless gas leak detection and localization. IEEE Trans. Ind. Inform. 2016, 12, 768–779. [Google Scholar] [CrossRef]
- Yoon, S.; Ye, W.; Heidemann, J.; Littlefield, B.; Shahabi, C. SWATS: Wireless sensor networks for steamflood and waterflood pipeline monitoring. IEEE Netw. 2011, 25, 50–56. [Google Scholar] [CrossRef]
- Jing, L.; Li, Z.; Li, Y.; Murch, R. Channel characterization of acoustic waveguides consisting of straight gas and water pipelines. IEEE Access 2018, 6, 6807–6819. [Google Scholar] [CrossRef]
- Poulakis, Z.; Valougeorgis, D.; Papadimitriou, C. Leakage detection in water pipe networks using a Bayesian probabilistic framework. Probabilistic Eng. Mech. 2003, 18, 315–327. [Google Scholar] [CrossRef]
- Ferrante, M.; Brunone, B.; Rossetti, A.G. Harmonic analysis of pressure signal during transients for leak detection in pressurized pipes. In Proceedings of the 4th International Conference on Water Pipeline Systems, York, UK, 28–30 March 2001; pp. 28–30. [Google Scholar]
- Wang, X.J.; Lambert, M.F.; Simpson, A.R.; Liggett, J.A.; Vítkovský, J.P. Leak detection in pipelines using the damping of fluid transients. J. Hydraulic Eng. 2002, 128, 697–711. [Google Scholar] [CrossRef]
- Almazyad, A.S. A proposed scalable design and simulation of wireless sensor network-based long-distance water pipeline leakage monitoring system. Sensors 2014, 14, 3557–3577. [Google Scholar] [CrossRef]
- Ali, S. SimpliMote: A wireless sensor network monitoring platform for oil and gas pipelines. IEEE Syst. J. 2018, 12, 778–789. [Google Scholar] [CrossRef]
- Hodge, V.J.; O’Keefe, S.; Weeks, M.; Moulds, A. Wireless sensor networks for condition monitoring in the railway industry: A survey. IEEE Trans. Intell. Transp. Syst. 2015, 16, 1088–1106. [Google Scholar] [CrossRef]
- Miao, Y.; Li, W.; Tian, D.; Hossain, M.S.; Alhamid, M.F. Narrowband internet of things: Simulation and modelling. IEEE Internet Things J. 2018, 5, 2304–2314. [Google Scholar] [CrossRef]
- Zhang, T.; Fan, H.; Loo, J.; Liu, D. User preference aware caching deployment for device-to-device caching networks. IEEE Syst. J. 2019, 13, 226–237. [Google Scholar] [CrossRef]
- Stoianov, I.; Nachman, L.; Madden, S.; Tokmouline, T. PIPENET: A wireless sensor network for pipeline monitoring. In Proceedings of the 6th international conference on Information processing in sensor networks, Cambridge, MA, USA, 25–27 April 2007; pp. 264–273. [Google Scholar]
- Chang, Y.C.; Lai, T.T.; Chu, H.H.; Huang, P. Pipeprobe: Mapping spatial layout of indoor water pipelines. In Proceedings of the 2009 Tenth International Conference on Mobile Data Management: Systems, Services and Middleware, Taipei, Taiwan, 18–20 May 2009; pp. 391–392. [Google Scholar]
- Whittle, A.J.; Girod, L.; Preis, A.; Allen, M.; Lim, H.B.; Iqbal, M.; Goldsmith, D. WATERWISE@SG: A testbed for continuous monitoring of the water distribution system in Singapore. In Proceedings of the 12th Annual Conference on Water Distribution Systems Analysis (WDSA), Tucson, AZ, USA, 12–15 September 2010; pp. 1362–1378. [Google Scholar]
- Jang, E.H.; Park, B.J.; Kim, S.H.; Chung, M.A.; Park, M.S.; Sohn, J.H. Emotion classification based on bio-signals emotion recognition using machine learning algorithms. In Proceedings of the 2014 International Conference on Information Science, Electronics and Electrical Engineering, Sapporo, Japan, 26–28 April 2014; pp. 1373–1376. [Google Scholar]
- Siryani, J.; Tanju, B.; Eveleigh, T.J. A machine learning decision support system improves the internet of things’ smart meter operations. IEEE Internet Things J. 2017, 4, 1056–1066. [Google Scholar] [CrossRef]
- Pławiak, P.; Sośnicki, T.; Niedźwiecki, M.; Tabor, Z.; Rzecki, K. Hand body language gesture recognition based on signals from specialized glove and machine learning algorithms. IEEE Trans. Ind. Informat. 2016, 12, 1104–1113. [Google Scholar] [CrossRef]
- Ye, H.; Liang, L.; Li, G.Y.; Kim, J.; Lu, L.; Wu, M. Machine learning for vehicular networks: Recent advances and application examples. IEEE Veh. Technol. Mag. 2018, 13, 94–101. [Google Scholar] [CrossRef]
- Malfante, M. Machine learning for volcano seismic signals: Challenges and perspectives. IEEE Singal Process. Mag. 2018, 35, 20–30. [Google Scholar] [CrossRef]
- Prieto, M.D. Bearing fault detection by a novel condition monitoring scheme based on statistical time features and neural networks. IEEE Trans. Ind. Electron. 2013, 60, 3398–3407. [Google Scholar] [CrossRef]
- Becari, W.; de Oliveira, A.M.; Peres, H.E.M.; Correra, F.S. Microwave-based system for non-destructive monitoring water pipe networks using support vector machine. IET Sci. Meas. Technol. 2016, 10, 910–915. [Google Scholar] [CrossRef]
- Gomaa, R.I. Real-time radiological monitoring of nuclear facilities using Zigbee technology. IEEE Sens. J. 2014, 14, 4007–4013. [Google Scholar] [CrossRef]
- Zheng, K. Energy efficient localization and tracking of mobile devices in wireless sensor networks. IEEE Trans. Veh. Technol. 2017, 66, 2714–2726. [Google Scholar] [CrossRef] [Green Version]
- Huang, N.E.; Shen, Z.; Long, S.R. The empirical mode decomposition and the Hilbert spectrum for nonlinear non-stationary time series analysis. Proc. R. Soc. A Math. Phys. Eng. Sci. 1998, 454, 903–995. [Google Scholar] [CrossRef]
- Yang, J.; Wen, Y.; Li, P. Leak location using blind system identifi-cation in water distribution pipelines. J. Sound Vibrat. 2008, 310, 134–148. [Google Scholar] [CrossRef]
- Pincus, S.M. Approximate entropy: A complexity measure for biological time series data. In Proceedings of the 1991 IEEE Seventeenth Annual Northeast Bioengineering Conference, Hartford, CT, USA, 4–5 April 1991; pp. 35–36. [Google Scholar]
- Cortes, C.; Vapnik, V. Support-vector networks. Mach. Learn. 1995, 20, 273–297. [Google Scholar] [CrossRef]
- Müller, K.R.; Mika, S.; Rätsch, G.; Tsuda, K.; Schölkopf, B. An introduction to kernel-based learning algorithms. IEEE Trans. Neural Netw. 2001, 12, 181–201. [Google Scholar] [CrossRef]
- Ayat, N.E.; Cheriet, M.; Suen, C.Y. Automatic model selection for the optimization of SVM kernels. Pattern Recognit. 2005, 38, 1733–1745. [Google Scholar] [CrossRef]
- Hsu, C.W.; Lin, C.J. A comparison of methods for multiclass support vector machines. IEEE Trans. Neural Netw. 2002, 13, 415–425. [Google Scholar] [PubMed]
- Huang, C.L.; Wang, C.J. A GA-based feature selection and parameters optimization for support vector machines. Expert Syst. Appl. 2006, 31, 231–240. [Google Scholar] [CrossRef]
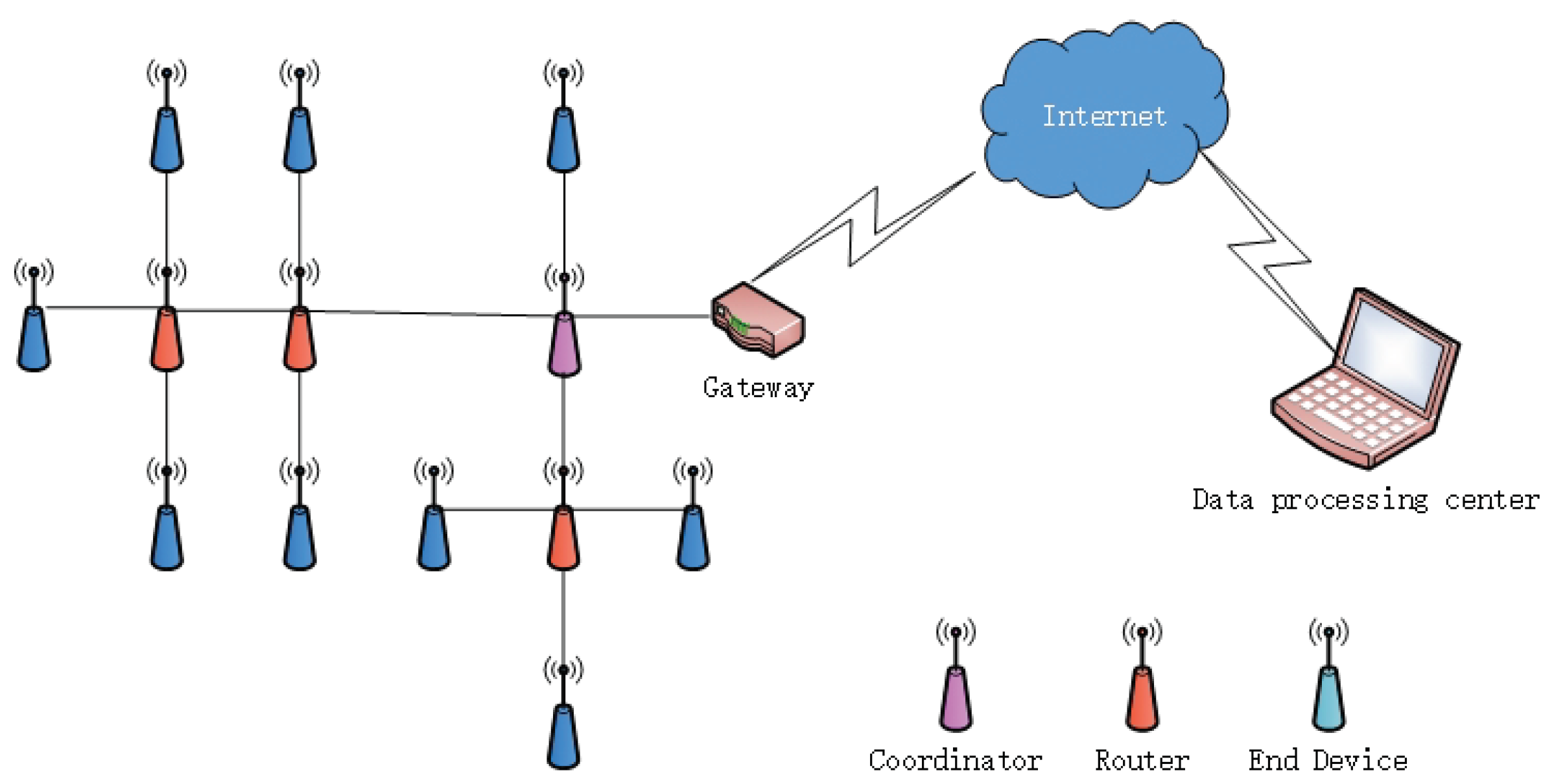














| Field Name | PANID | Des_address | Sou_address | Join_result | Channel |
|---|---|---|---|---|---|
| Length | 16 bits | 16 bits | 16 bits | 1 bit | 32 bits |
| Instructions | Network ID | Destination | Source | Results | Channel |
| Field Name | PAN ID | Sou_address | Act_address |
|---|---|---|---|
| Length | 16 bits | 16 bits | 16 bits |
| Instructions | Network ID | Source | Active Node |
| Field Name | PAN ID | Des_address | Sou_address | Position | Value |
|---|---|---|---|---|---|
| Length | 16 bits | 16 bits | 16 bits | 64 bits | 128 bits |
| Instructions | Network ID | Destination | Source | Leakage Point | Information |
| Application Layer Parameters | |
| Packet Size | Constant (512) |
| Packet Interarrival Time | Exponential (5) |
| Start Time | 120 s |
| Stop Time | Infinity |
| MAC Layer Parameters | |
| ACK Wait Duration | 0.05 s |
| Minimum Backoff Exponent | 3 |
| Maximum Number of Backoffs | 4 |
| Channel Sensing Duration | 0.5 |
| Physical Layer Parameters | |
| Transmission Bands | 2450 MHz Band |
| Data Rate | 240 kbps |
| Packet Reception-Power Threshold | −85 dBm |
| Transmission Power | 1 mW |
| Receive Power | 0.4 mW |
| Idle Power | 0.1 mW |
| SNR(dB) | 0 | 3 | 6 | 9 | 12 | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| (c,g) | |||||||||||
| 34 | 42 | 60 | 83 | 85 | 88 | 91 | 93 | 96 | |||
| 34 | 42 | 60 | 82 | 85 | 87 | 91 | 92 | 96 | |||
| 34 | 42 | 60 | 82 | 85 | 87 | 89 | 93 | 96 | |||
| Gaussian Noise | 37 | 42 | 60 | 82 | 84 | 87 | 88 | 93 | 95 | ||
| 34 | 42 | 60 | 82 | 85 | 87 | 91 | 93 | 96 | |||
| 34 | 42 | 59 | 82 | 85 | 87 | 91 | 93 | 96 | |||
| 34 | 42 | 59 | 82 | 85 | 87 | 91 | 83 | 96 | |||
| 31 | 32 | 56 | 84 | 85 | 88 | 90 | 94 | 96 | |||
| 31 | 32 | 54 | 82 | 84 | 87 | 89 | 93 | 95 | |||
| 31 | 32 | 59 | 81 | 84 | 87 | 90 | 93 | 95 | |||
| Impulsive Noise | 31 | 32 | 56 | 81 | 85 | 87 | 90 | 93 | 95 | ||
| 31 | 32 | 55 | 81 | 84 | 87 | 90 | 93 | 95 | |||
| 31 | 33 | 55 | 81 | 84 | 87 | 91 | 93 | 96 | |||
| 31 | 32 | 55 | 80 | 84 | 87 | 91 | 93 | 95 | |||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Y.; Ma, X.; Li, Y.; Tie, Y.; Zhang, Y.; Gao, J. Water Pipeline Leakage Detection Based on Machine Learning and Wireless Sensor Networks. Sensors 2019, 19, 5086. https://doi.org/10.3390/s19235086
Liu Y, Ma X, Li Y, Tie Y, Zhang Y, Gao J. Water Pipeline Leakage Detection Based on Machine Learning and Wireless Sensor Networks. Sensors. 2019; 19(23):5086. https://doi.org/10.3390/s19235086
Chicago/Turabian StyleLiu, Yang, Xuehui Ma, Yuting Li, Yong Tie, Yinghui Zhang, and Jing Gao. 2019. "Water Pipeline Leakage Detection Based on Machine Learning and Wireless Sensor Networks" Sensors 19, no. 23: 5086. https://doi.org/10.3390/s19235086
APA StyleLiu, Y., Ma, X., Li, Y., Tie, Y., Zhang, Y., & Gao, J. (2019). Water Pipeline Leakage Detection Based on Machine Learning and Wireless Sensor Networks. Sensors, 19(23), 5086. https://doi.org/10.3390/s19235086





