Privacy-Preserving Broker-ABE Scheme for Multiple Cloud-Assisted Cyber Physical Systems
Abstract
1. Introduction
1.1. Contributions
- Broker-based ABE. Most ABE schemes consider only the sender and receiver. In a ciphertext-policy ABE (CP-ABE) scheme, the sender must embed a policy-checking mechanism in the ciphertext generation process. Generally speaking, the computational cost of this process depends on the number of attributes included. When more attributes are taken into account, more computation power is required in the encryption process. That is, when applying CP-ABE in the MCCPS scenario, many attributes are required and the field sensor may not have sufficient resources to encrypt the collected data.
- Arbitrary policy support without dedicated keys. The broker-based ABE is a variant of the proxy-ABE, where the broker role is similar to that of a proxy. This intermediary step transforms the given ciphertext into a new ciphertext. The proxy-ABE requires a re-encryption key, which is often bundled with the new policy. However, this is not practical in the MCCPS scenario since there are many types of sensors, many CSPs, and having a re-encrypt key for each combination would be almost impossible. Besides, as described above, the sensor cannot complete the policy embedding task due to its limited computational resources. So, the broker does not transform the ciphertext from one policy into another, but rather adds a policy-checking step to an existing ciphertext. Moreover, without transformation by the broker, CSPs cannot decrypt these messages from the sensors. This ensures that a message from a field sensor must pass through the broker and have had the policy-checking step appended before being received by the CSP. Thirdly, although the broker is an intermediate entity that participates in the encryption process, it is not allowed to see the data from field sensors. This arrangement is known as a semi-trusted broker.
- Lightweight and blockwise deniable ABE. Deniable encryption is an encryption scheme in which the sender and receiver can persuade others that a given ciphertext is from a fake rather than a real message. Most deniable encryption schemes are bitwise encryption schemes that encrypt only one bit at a time. Undoubtedly, a bitwise encryption can support any kind of message by repeating the encryption process many times. However, in practice, this is not efficient especially, when considering the MCCPS scenario, since the sensor cannot support this approach due to its resource limitations.
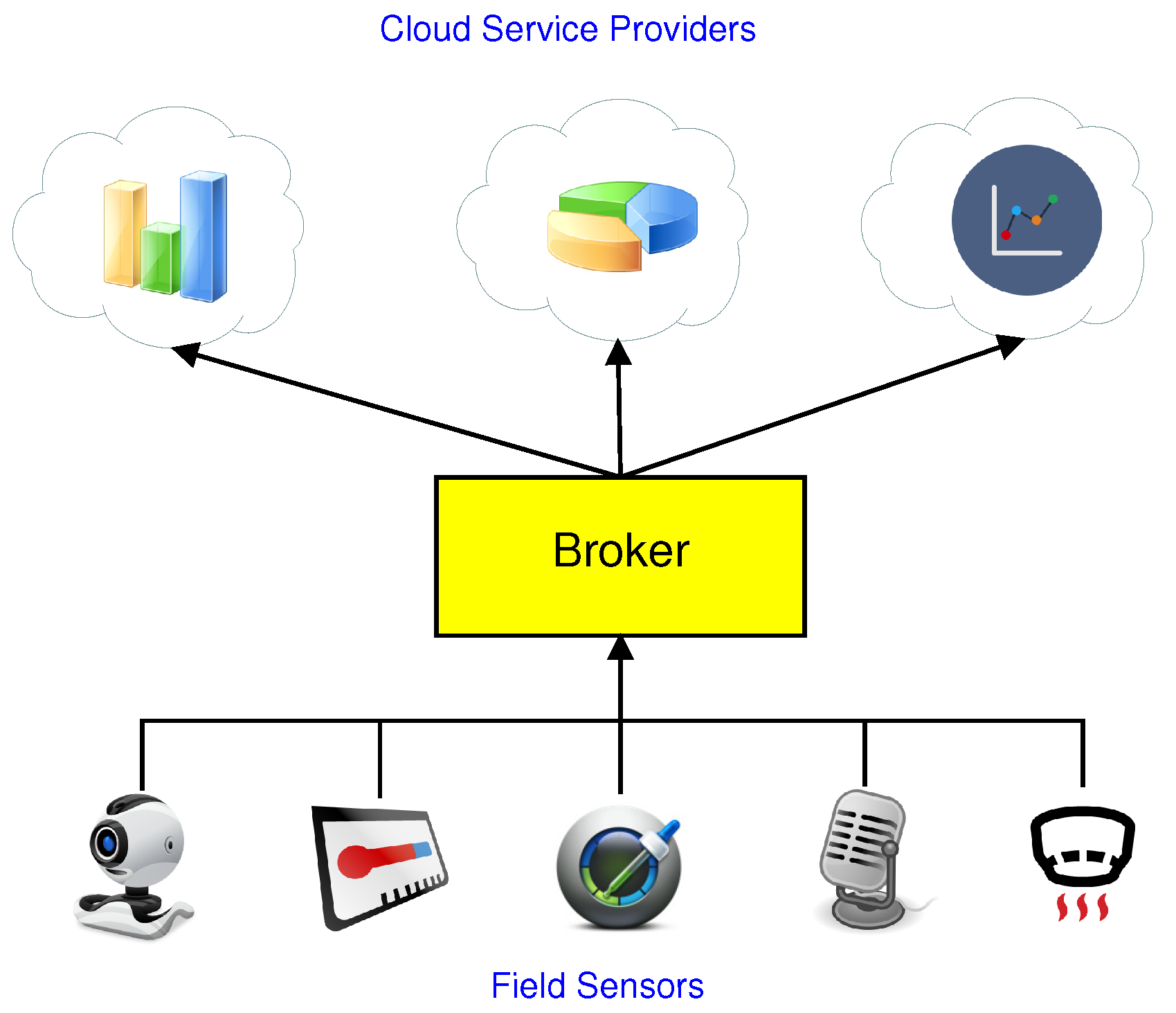
- Multiple brokers support. In the MCCPS scenario, there are many cloud services that may be shared by sensors from different fields. That is, one cloud service must simultaneously support multiple brokers and the sensors that are under these brokers. It is a trivial matter that each broker and CSP share one unique encryption environment, which is usually the public key. However, this will increase the management complexity since many brokers and multiple public keys are required.
1.2. Organization
2. Related Works
2.1. Previous Works on Attribute-Based Encryption
2.2. Previous Works on Deniable Encryption
2.3. Preliminaries
2.3.1. Prime Order Bilinear Groups
- Bilinearity: and , .
- Non-degeneracy: .
- Computability: the group action in and map function e can be computed efficiently.
2.3.2. Waters CP-ABE Scheme
- 1.
- The shares for each party form a vector over .
- 2.
- There exists an matrix M called the share-generating matrix for Π. For all , the i’th row of M is labeled by party , where ρ is a mapping function from to party field . When considering column vector , where is the secret to be shared and are randomly chosen, is the vector of l shares of secret s according to Π. The share belongs to party .
- Setup: This algorithm chooses a bilinear group of prime order p with generator g, random elements , and hash function . The public key is and the system secret key is .
- Encrypt: Given message M and LSSS access structure , this algorithm first chooses a random vector . Let be an matrix and denote the ith row of . This algorithm calculates . Next, this algorithm chooses . The output ciphertext will be as follows:with a description of .
- KeyGen: Given set S of attributes, this algorithm chooses randomly and outputs the private key as:
- Decrypt: Suppose that S satisfies the access structure and let be defined as . This algorithm then finds a set of constants such that . The decryption algorithm computesand derives M from the ciphertext.
2.3.3. Composite Order Bilinear Groups
2.3.4. Chameleon Hash
- Setup: Given a security parameter, the scheme outputs public parameter and secret trapdoor .
- Hash: An efficient and probabilistic algorithm, with inputs , a message m, and a random string r, outputs a hash value h.
- Forgery: An efficient and probabilistic algorithm, with a given message , a random , the trapdoor and another message , outputs a random string that satisfies the following equation:
3. Privacy-Preserving Broker-ABE Scheme
3.1. Overview and Attack Model
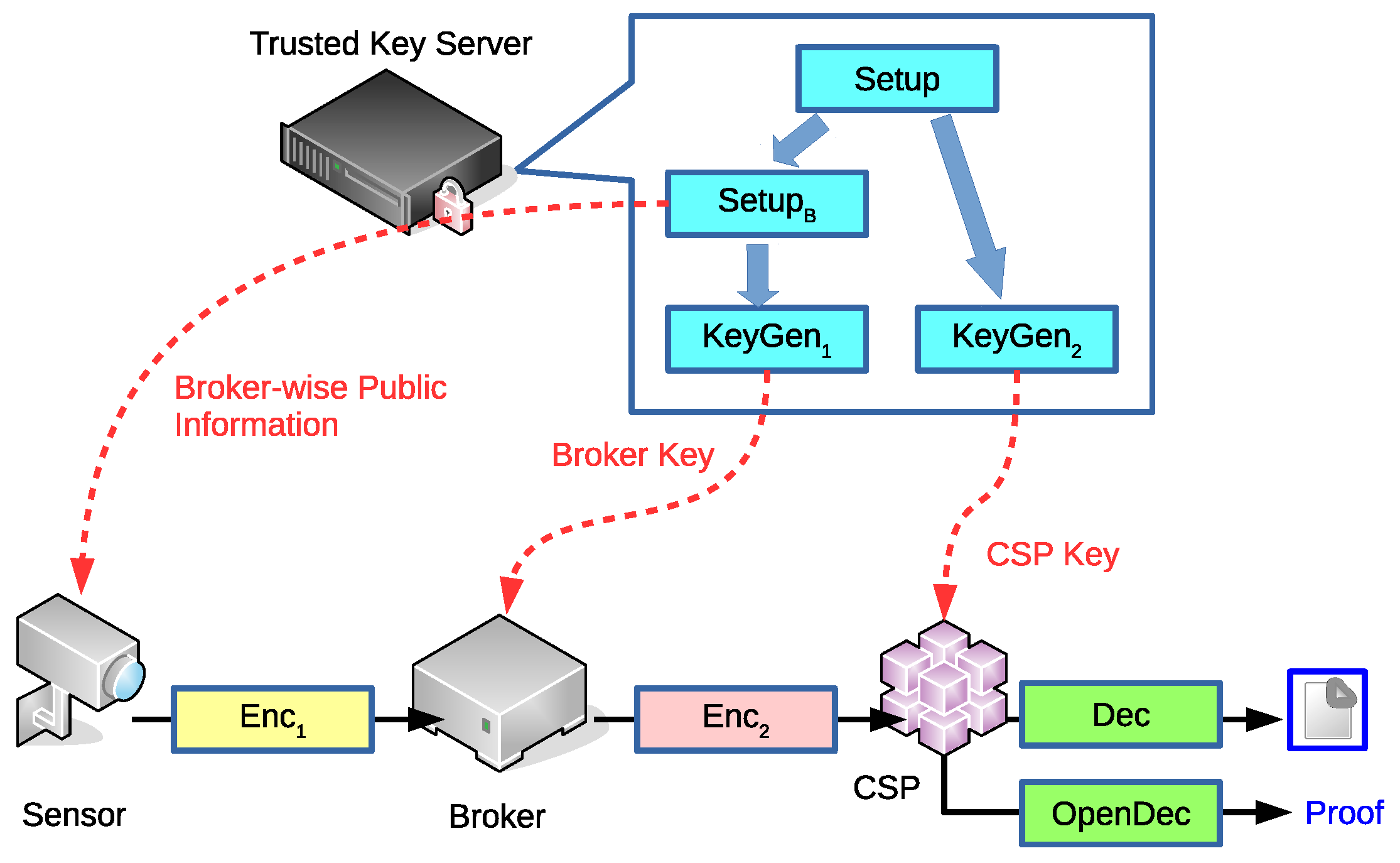
3.2. Definition
- Setup: This algorithm takes security parameter as input and returns public parameter and system master key .
- Setup: This algorithm takes the broker ID and system-wise information as input and outputs broker-wise public parameter and broker-wise master key . Note that this information is only for the broker and the sensors under that broker. This algorithm enables the whole system to simultaneously support multiple brokers.
- KeyGen: This algorithm takes as input and returns for the broker.
- KeyGen: Given an attribute set S of a CSP and , this algorithm outputs private key for the CSP.
- Enc: The phase 1 encryption is performed in the sender. Given the message M and , the sender can output a ciphertext C that will be delivered to the broker.
- Enc: The phase 2 encryption is performed in the broker. Given the ciphertext C, and LSSS access structure A, the broker can re-encrypt C to a new ciphertext .
- Dec: The decryption is performed in the CSP. If S satisfies A, the decryption algorithm returns M; otherwise, ⊥.
- OpenDec: The algorithm is used to release evidence for proving that is the encryption result from M.
- DenSetup: This is the deniable version of Setup algorithm. Except for and , the algorithm also generates the system public information . is known by all sensors and CSPs, and is kept secret from outsiders. Note that the broker is not in charge of the deniable part so is also kept secret from the broker.
- DenKeyGen: This is the deniable version of KeyGen algorithm. Except for , which is derived from the normal function, the algorithm also returns a fake key , which is used later to generate fake proof.
- DenEnc: Except for the inputs of the normal encryption algorithm, this deniable encryption algorithm requires public key and a pre-defined fake message . The output ciphertext must be indistinguishable from the output of Enc.
- DenOpenDec: Compared to the normal version algorithm, the algorithm takes additional inputs and . The output is evidence that is from instead of M.
- Security: the outputs of Enc and Enc must be proved to be confidential under the security model, which is described in Section 3.3. The first protects the segment between the sensor and the broker, whereas the latter protects the segment between the broker and the CSP. The security of Enc also maintains secrecy from the broker. Note that here we do not mention the security of DenEnc because the outputs of Enc and DenEnc must be indistinguishable. If one is secure and the other is not, this will make these two algorithms distinguishable. So, here, the indistinguishability proof also implies the security proof.
- Deniability: the proposed scheme is a receiver-DE scheme. That is, given public parameter , the two distribution tuples and are computationally indistinguishable, where are claimed messages, are normally and deniably encrypted ciphertexts, respectively, and are proofs generated from the normal and deniable open algorithms, respectively. That is, there is no PPT algorithm A for whichis non-negligible. Note that the deniably encrypted ciphertexts are the outputs of Enc since no entity should be able to decrypt the outputs of Enc or DenEnc. Deniability in the sensor is not considered since it makes no sense for a sensor to provide lots of storage for evidence.
- Deniable proof consistency: in the MCCPS scenario, a cloud service may be used by many sensors. Some sensors may use the privacy-preserving encryption scheme and some may not. When releasing a deniable proof of a CSP, the proof should look convincing not only to the sensor that uses the DE algorithms, but also to the sensor that uses the normal encryption algorithms. That is, given a set of ciphertexts , including normally encrypted ciphertexts and deniably encrypted ciphertexts, normal proof and deniable proof , there is no PPT algorithm A for whichis non-negligible.
3.3. Security Model
- Setup: the challenger first runs Setup and outputs to the adversary.
- Phase 1: the adversary generates queries for the challenger. Query can be one of the following two types of queries:
- –
- Key query: the adversary asks the challenger a key for some entity and obtains its private key from the challenger.
- –
- Decryption query: the adversary asks the challenger to decrypt ciphertext and obtains its plaintext.
- Challenge: the adversary chooses two plaintexts for the challenger. The adversary also provides a challenge condition , which cannot be authorized by the entities used in . The challenger randomly chooses one bit and encrypts the message via Enc. The challenger sends to the adversary as the challenge ciphertext.
- Phase 2: As in Phase 1, the adversary generates queries for the challenger. Query can be one of the following two types of queries:
- –
- Key query: the adversary asks the challenger a key for some entity and obtains its private key from the challenger. Note that the entity cannot be the one who is authorized to decrypt the challenge ciphertext.
- –
- Decryption query: the adversary asks the challenger to decrypt ciphertext and obtains its plaintext. cannot be .
- Guess: The adversary returns guess result . The adversary wins if .
3.4. Assumptions
3.5. Construction
- Setup: this algorithm generates a bilinear group of order , where are distinct primes with the bilinear map function . Note that is also order N. can be separated into three orthogonal subgroups . This algorithm picks three generators for respectively. The algorithm also randomly picks and and chooses a hash function . The output will be:
- Setup: taking and as inputs, the algorithm generates a new public information and a new master key in a broker domain. is the broker identity and acts an index for recording the secret of a broker. The algorithm first randomly picks . The output will be:
- KeyGen: the algorithm generates for the broker as follows:
- KeyGen: the algorithm generates for the CSP based on its attributes S. It chooses randomly and outputs private key as follows:Note that, in this system, each CSP will share the same K.
- Enc: given message M, the algorithm randomly picks . Then, the algorithm sets up a one-way hash function H. Note that hash function H can be any kind of one-way function, including pseudo random permutation functions. Next, the algorithm flips two coins and selects two random strings . The output ciphertext C will be:where,
- Enc: given a ciphertext C and an LSSS access structure , the algorithm first removes the part in and as follows:Let where is a matrix and is a mapping function from to the attribute field. The algorithm randomly generates two vectors and . Then it calculates . The output ciphertext will be as follows:whereare directly derived from C and are not changed. is also appended to .
- Dec: to decrypt ciphertext for access structure , the algorithm first checks if attribute set S of satisfies . Suppose S satisfies and let be defined as . The algorithm is able to find a set of constants such that . This algorithm computes as follows:The algorithm then checks tag V as follows:If is equal to V, then is a true message. Otherwise, this algorithm returns ⊥.
- OpenDec: to show that is encrypted from M, the algorithm simply returns .
- DenSetup: tuple is generated as Setup. The algorithm also randomly picks . is generated as follows:Note that is kept secret from outsiders, including the broker, since it does not participate in the deniable encryption process. For the same reason, there is no DenSetup algorithm.
- DenKeyGen: is derived from KeyGen and is generated as follows:
- DenEnc: the algorithm needs one more input which is the pre-determined fake message (that is, a fake message is given by users. If the fake message is obviously far from the normal message, it is the user’s responsibility rather than that of the proposed scheme). This algorithm first runs Enc and gets and . Next, this algorithm sets up a chameleon hash function . The output deniable ciphertext C will be:where,Since a chameleon hash function is a trapdoor pseudo-random permutation function, it is easy to find to generate a collision, which implies that M and can both be valid in decryption.
- DenOpenDec: to show that is encrypted from the fake message , the algorithm simply returns .
3.6. Correctness
- When using the normal key to decrypt a normally encrypted ciphertext C, the decryption process will be as follows:With the hash function H and V, the receiver can correctly get the message M.
- When using the normal key to decrypt a deniably encrypted ciphertext C, the decryption process will be as follows:With the chameleon hash function and V, the receiver can correctly get the message M.
- When using the deniable key to decrypt a deniably encrypted ciphertext C, the decryption process will be as follows:With the chameleon hash function and V, the receiver can correctly get message rather than the real message M.
- When using the deniable key to decrypt a normally encrypted ciphertext C, the decryption process will be as follows:With the hash function H and V, the receiver can correctly get the message M.
3.7. Implementation Issues
4. Evaluation
4.1. Security Proof
- Setup: first picks two different prime numbers and . Next, generates group with order . Note that the subgroup with order in should be the same as . then randomly picks and picks a generator for . then shows the following to :Note that and are the same as the given function from .
- Phase 1: when receives a key generation query for attribute set S from , simply relays the query to and obtains as follows:then generates and outputs to as follows:
- Challenge: outputs two messages , with access structure to , and directly relays , and to as the challenge and obtains the following from .whereis chosen by . setups a chameleon hash function and randomly picks from . also randomly picks . Finally, outputs C to as follows:where,Note that a chameleon hash function is used instead of a common hash function. To , without the trapdoor, a chameleon hash function is simply a one-way function. Here we ensure that the verification tag V is valid for both and , so the verification process will lease no information to .
- Phase 2: the query and response process is the same as that in Phase 1.
- Guess: finally, outputs guess to and forwards guess to .
4.2. Deniability Proof
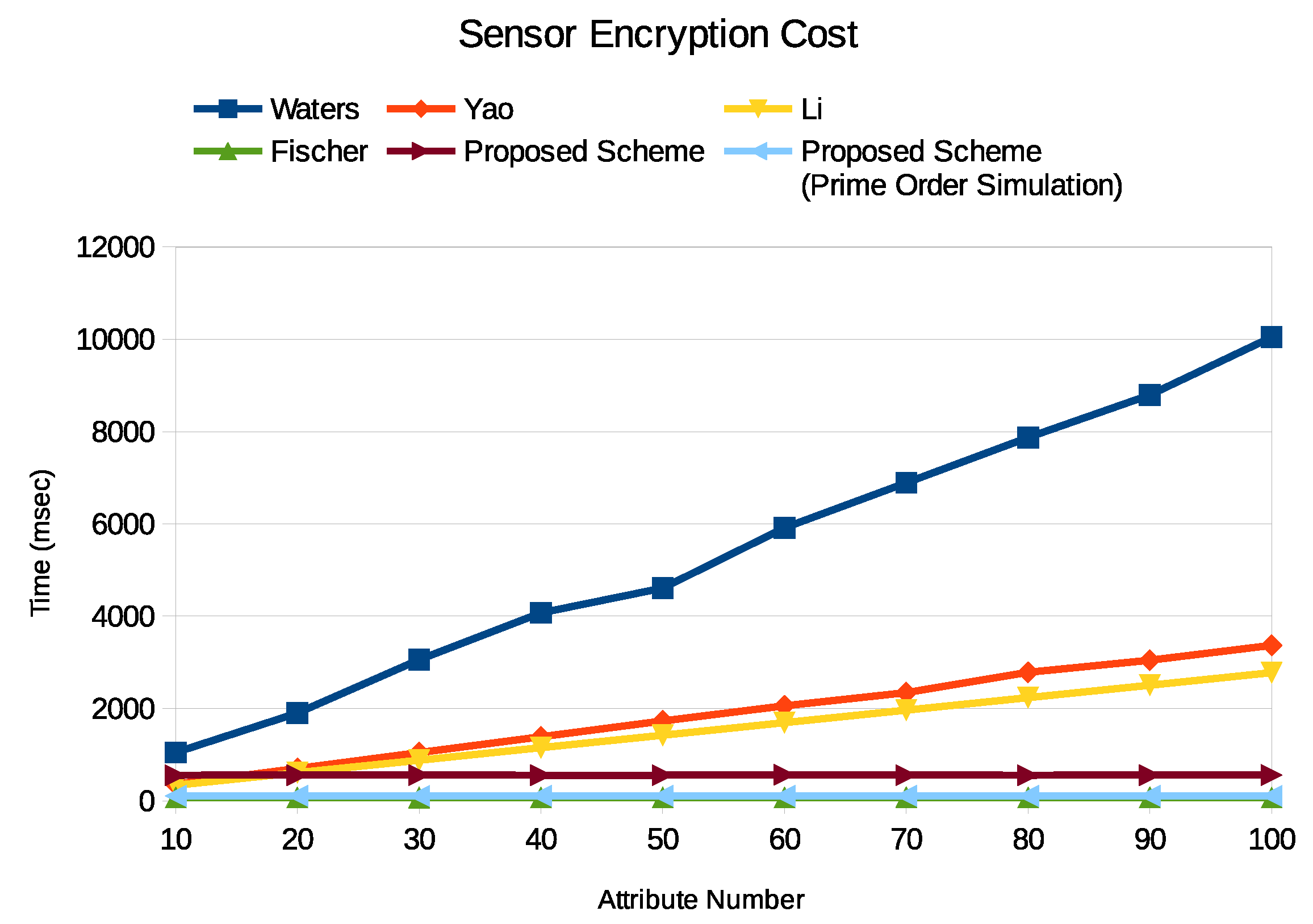
4.3. Performance Evaluation
5. Discussion
5.1. CCA-Security
- Setup: Aside from the original Setup, the algorithm additionally setup a hash function and randomly picks . The algorithm then appends to .
- Enc: The sensor first runs the original Enc algorithm and gets . Then the algorithm calculates and the output ciphertext will be as follows:where
- Enc: The broker first verifies the following equations:whereIf the above two equations do not hold, the algorithm simply drops the and returns. Otherwise, the algorithm runs the original Enc algorithm and gets . Then the algorithm calculates and the output ciphertext will be as follows:where
- Dec: The CSP first verifies the following two equations:whereIf the above two equations do not hold, the algorithm simply returns ⊥. Otherwise, it simply runs Dec and outputs the result.
- If and do not hold, the oracle responds ⊥.
- In phase 2, if the queried ciphertext is the same as the challenged ciphertext, the oracle responds ⊥.
- The oracle uses the master secret s to calculate and to decrypt the queried ciphertext. The oracle then returns the decryption result to the adversary.
5.2. Chameleon Hash Issues
6. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
References
- Rajkumar, R.R.; Lee, I.; Sha, L.; Stankovic, J. Cyber-physical systems: the next computing revolution. In Proceedings of the 47th Design Automation Conference, Anaheim, CA, USA, 13–18 June 2010; pp. 731–736. [Google Scholar]
- Lee, J.; Bagheri, B.; Kao, H.A. A cyber-physical systems architecture for industry 4.0-based manufacturing systems. Manuf. Lett. 2015, 3, 18–23. [Google Scholar] [CrossRef]
- Wan, J.; Xia, M. Cloud-Assisted Cyber-Physical Systems for the Implementation of Industry 4.0. Mob. Netw. Appl. 2017, 22, 1157–1158. [Google Scholar] [CrossRef]
- Mattern, F.; Floerkemeier, C. From the Internet of Computers to the Internet of Things. In From Active Data Management to Event-Based Systems and More; Springer: Berlin/Heidelberg, Germany, 2010; pp. 242–259. [Google Scholar]
- Simmon, E.; Kim, K.S.; Subrahmanian, E.; Lee, R.; De Vaulx, F.; Murakami, Y.; Zettsu, K.; Sriram, R.D. A Vision of Cyber-Physical Cloud Computing for Smart Networked Systems; US Department of Commerce, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2013.
- Lucas-Simarro, J.L.; Aniceto, I.S.; Moreno-Vozmediano, R.; Montero, R.S.; Llorente, I.M. A cloud broker architecture for multicloud environments. In Large Scale Network-Centric Distributed Systems; Wiley-IEEE Computer Society Press: Hoboken, NJ, USA, 2013; pp. 359–376. [Google Scholar]
- Li, X.; Ma, H.; Zhou, F.; Yao, W. T-broker: A trust-aware service brokering scheme for multiple cloud collaborative services. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1402–1415. [Google Scholar] [CrossRef]
- Canetti, R.; Dwork, C.; Naor, M.; Ostrovsky, R. Deniable Encryption. In Advances in Cryptology; Kaliski, B.S., Jr., Ed.; Springer: Berlin/Heidelberg, Germany, 1997; pp. 90–104. [Google Scholar]
- Chi, P.W.; Lei, C.L. Audit-Free Cloud Storage via Deniable Attribute-based Encryption. IEEE Trans. Cloud Comput. 2018, 6, 414–427. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy Identity-Based Encryption. In Eurocrypt; Cramer, R., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Advances in Cryptology; Blakley, G.R., Chaum, D., Eds.; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Waters, B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization. In Public Key Cryptography; Catalano, D., Fazio, N., Gennaro, R., Nicolosi, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Lewko, A.B.; Okamoto, T.; Sahai, A.; Takashima, K.; Waters, B. Fully Secure Functional Encryption: Attribute-Based Encryption and (Hierarchical) Inner Product Encryption. In Eurocrypt; Gilbert, H., Ed.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 62–91. [Google Scholar]
- Attrapadung, N.; Herranz, J.; Laguillaumie, F.; Libert, B.; de Panafieu, E.; Ràfols, C. Attribute-based encryption schemes with constant-size ciphertexts. Theor. Comput. Sci. 2012, 422, 15–38. [Google Scholar] [CrossRef]
- Tysowski, P.K.; Hasan, M.A. Hybrid Attribute- and Re-Encryption-Based Key Management for Secure and Scalable Mobile Applications in Clouds. IEEE Trans. Cloud Comput. 2013, 1, 172–186. [Google Scholar] [CrossRef]
- Luo, S.; Hu, J.; Chen, Z. Ciphertext Policy Attribute-Based Proxy Re-encryption. In Information and Communications Security; Soriano, M., Qing, S., López, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 401–415. [Google Scholar]
- Li, K. Matrix access structure policy used in attribute-based proxy re-encryption. arXiv 2013, arXiv:1302.6428. [Google Scholar]
- Liang, K.; Fang, L.; Susilo, W.; Wong, D.S. A ciphertext-policy attribute-based proxy re-encryption with chosen-ciphertext security. In Proceedings of the 2013 5th International Conference on Intelligent Networking and Collaborative Systems (INCoS), Xi’an, China, 9–11 September 2013; pp. 552–559. [Google Scholar]
- Chandar, P.P.; Mutkuraman, D.; Rathinrai, M. Hierarchical attribute based proxy re-encryption access control in cloud computing. In Proceedings of the 2014 International Conference on Circuits, Power and Computing Technologies [ICCPCT-2014], Nagercoil, India, 20–21 March 2014; pp. 1565–1570. [Google Scholar] [CrossRef]
- Touati, L.; Challal, Y. Instantaneous Proxy-Based Key Update for CP-ABE. In Proceedings of the 2016 IEEE 41st Conference on Local Computer Networks (LCN), Dubai, UAE, 7–10 November 2016; pp. 591–594. [Google Scholar] [CrossRef]
- Yao, X.; Chen, Z.; Tian, Y. A lightweight attribute-based encryption scheme for the Internet of Things. Future Gener. Comput. Syst. 2015, 49, 104–112. [Google Scholar] [CrossRef]
- Oualha, N.; Nguyen, K.T. Lightweight Attribute-Based Encryption for the Internet of Things. In Proceedings of the 2016 25th International Conference on Computer Communication and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Jiang, Y.; Susilo, W.; Mu, Y.; Guo, F. Ciphertext-policy attribute-based encryption against key-delegation abuse in fog computing. Future Gener. Comput. Syst. 2018, 78, 720–729. [Google Scholar] [CrossRef]
- Zuo, C.; Shao, J.; Wei, G.; Xie, M.; Ji, M. CCA-secure ABE with outsourced decryption for fog computing. Future Gener. Comput. Syst. 2018, 78, 730–738. [Google Scholar] [CrossRef]
- Li, Z.; Li, W.; Jin, Z.; Zhang, H.; Wen, Q. An Efficient ABE Scheme With Verifiable Outsourced Encryption and Decryption. IEEE Access 2019, 7, 29023–29037. [Google Scholar] [CrossRef]
- Fischer, M.; Scheerhorn, A.; Tönjes, R. Using Attribute-Based Encryption on IoT Devices with instant Key Revocation. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 126–131. [Google Scholar] [CrossRef]
- Dürmuth, M.; Freeman, D.M. Deniable Encryption with Negligible Detection Probability: An Interactive Construction. In Eurocrypt; Paterson, K.G., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 610–626. [Google Scholar]
- O’Neill, A.; Peikert, C.; Waters, B. Bi-Deniable Public-Key Encryption. In Crypto; Rogaway, P., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 525–542. [Google Scholar]
- Gasti, P.; Ateniese, G.; Blanton, M. Deniable Cloud Storage: Sharing Files via Public-Key Deniability; WPES: New York, NY, USA, 2010; pp. 31–42. [Google Scholar]
- Beimel, A. Secure Schemes for Secret Sharing and Key Distribution. Ph.D. Thesis, Israel Institute of Technology, Haifa, Israel, 1996. [Google Scholar]
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF Formulas on Ciphertexts. In TCC; Springer: Berlin/Heidelberg, Germany, 2005; pp. 325–341. [Google Scholar]
- Lewko, A.B. Tools for Simulating Features of Composite Order Bilinear Groups in the Prime Order Setting. In Eurocrypt; Pointcheval, D., Johansson, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 318–335. [Google Scholar]
- Krawczyk, H.; Rabin, T. Chameleon Signatures. In NDSS; The Internet Society: San Diego, CA, USA, 2000. [Google Scholar]
- Boneh, D. Bilinear Groups of Composite Order. In Pairing-Based Cryptography—Pairing 2007; Takagi, T., Okamoto, T., Okamoto, E., Okamoto, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Cao, Z.; Liu, L. A Note on Bilinear Groups of a Large Composite Order. Cryptology ePrint Archive, Report 2013/812. 2013. Available online: https://eprint.iacr.org/2013/812 (accessed on 1 October 2019).
- Iorga, M.; Feldman, L.; Barton, R.; Martin, M.; Goren, N.; Mahmoudi, C. The NIST Definition of Fog Computing; NIST: Gaithersburg, MD, USA, 2017.
- Barker, E.; Barker, W.; Burr, W.; Polk, W.; Smid, M. Recommendation for Key Management: Part 1: General (Revision 3); Technical Report; NIST: Gaithersburg, MD, USA, 2012.
- Boneh, D.; Canetti, R.; Halevi, S.; Katz, J. Chosen-Ciphertext Security from Identity-Based Encryption. SIAM J. Comput. 2007, 36, 1301–1328. [Google Scholar] [CrossRef]



| Symbol | Meaning |
|---|---|
| System-wise public information and master key. | |
| Broker-wise public information and master key. | |
| The broker’s secret key and the CSP’s secret key. | |
| The ciphertext encrypted by the sensor, the ciphertext re-encrypted by the broker and the ciphertext deniably encrypted by the sensor. | |
| The access structure for a ciphertext and an attribute set. | |
| The message and the predefined fake message. | |
| System-wise public information but not known to outsiders. That is, is claimed to be not existent. |
| Role | Algorithms |
|---|---|
| Trusted Key Server | Setup, Setup, KeyGen, KeyGen, DenSetup, DenKeyGen |
| CSP | Dec, OpenDec, DenOpenDec |
| Broker | Enc |
| Sensor | Enc, DenEnc |
| Order | Time (ms) | Simulation Time (ms) |
|---|---|---|
| 69.128 | - | |
| 418.222 | 148.912 | |
| 1321.734 | 222.367 | |
| 2999.380 | 296.672 | |
| 5676.130 | 373.077 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chi, P.-W.; Wang, M.-H. Privacy-Preserving Broker-ABE Scheme for Multiple Cloud-Assisted Cyber Physical Systems. Sensors 2019, 19, 5463. https://doi.org/10.3390/s19245463
Chi P-W, Wang M-H. Privacy-Preserving Broker-ABE Scheme for Multiple Cloud-Assisted Cyber Physical Systems. Sensors. 2019; 19(24):5463. https://doi.org/10.3390/s19245463
Chicago/Turabian StyleChi, Po-Wen, and Ming-Hung Wang. 2019. "Privacy-Preserving Broker-ABE Scheme for Multiple Cloud-Assisted Cyber Physical Systems" Sensors 19, no. 24: 5463. https://doi.org/10.3390/s19245463
APA StyleChi, P.-W., & Wang, M.-H. (2019). Privacy-Preserving Broker-ABE Scheme for Multiple Cloud-Assisted Cyber Physical Systems. Sensors, 19(24), 5463. https://doi.org/10.3390/s19245463






