Performance Analysis of the IEEE 802.11ax MAC Protocol for Heterogeneous Wi-Fi Networks in Non-Saturated Conditions
Abstract
:1. Introduction
2. Related Work
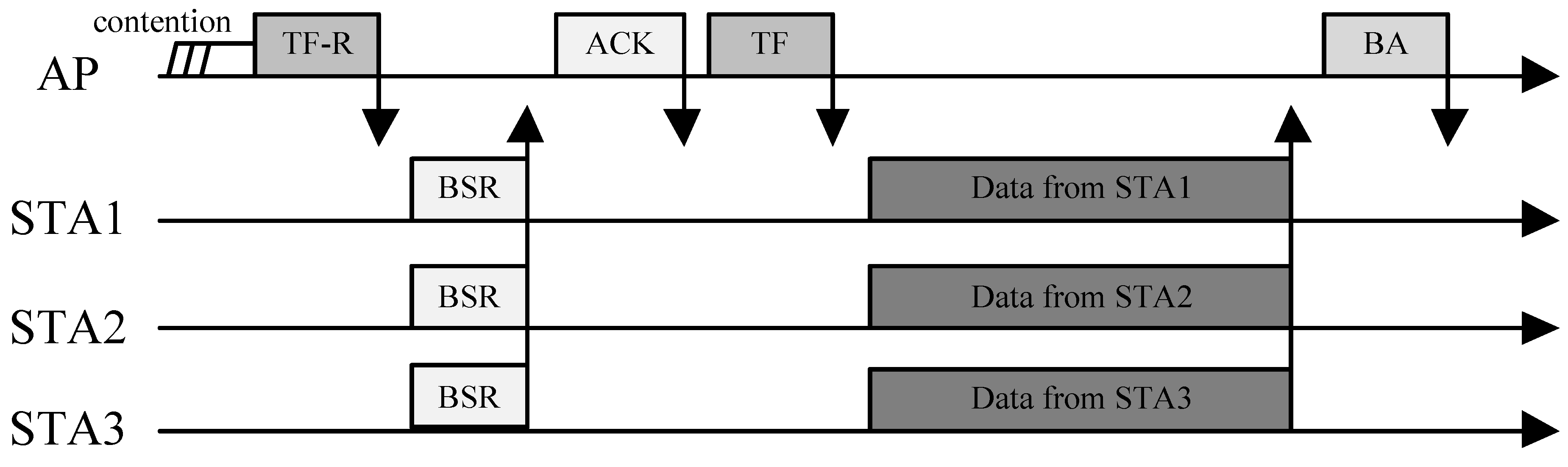
3. OFDMA Multi-User Transmissions in 802.11ax
4. Modeling of the 802.11ax MAC Protocol
4.1. Network Model and Assumptions
4.2. Analytical Model Based on Markov Chains
4.2.1. Model of the AP and LE STAs
4.2.2. Model for AX STAs
4.3. Throughput
4.3.1. Calculation of
4.3.2. Calculation of
4.4. Delay
4.4.1. Calculation of
4.4.2. Calculation of
5. Performance Evaluation
5.1. Evaluation Setting
5.2. Model Validation
5.3. Varying N
5.4. Varying
5.5. Varying K
5.6. Varying
5.7. Varying EDCA Parameter Sets
6. Conclusions
Funding
Conflicts of Interest
References
- Global Mobile Data Traffic Forecast Update, 2016–2021; White Paper 1454457600805266; Cisco VNI: San Jose, CA, USA, 2017.
- 802.11ac. Wireless LAN Medium Access Control and Physical Layer Specification; IEEE Std. 802.11ac Draft 5.0; IEEE: Piscataway, NJ, USA, 2013. [Google Scholar]
- Xie, X.; Zhang, X.; Sundaresan, K. Adaptive Feedback Compression for MIMO Networks. In Proceedings of the 19th Annual International Conference on Mobile Computing & Networking, Miami, FL, USA, 30 September–4 October 2013. [Google Scholar]
- Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. Amendment 6: Enhancements for High Efficiency WLAN; P802.11ax/D4.0; IEEE: Piscataway, NJ, USA, 2019.
- Son, Y.; Kim, S.; Byeon, S.; Choi, S. Symbol Timing Synchronization for Uplink Multi-User Transmission in IEEE 802.11ax WLAN. IEEE Access 2018, 6, 72962–72977. [Google Scholar] [CrossRef]
- Lanante, L.; Uwai, H.O.T.; Nagao, Y.; Kurosaki, M.; Ghosh, C. Performance analysis of the 802.11ax UL OFDMA random access protocol in dense networks. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Naik, G.; Bhattarai, S.; Park, J. Performance Analysis of Uplink Multi-User OFDMA in IEEE 802.11ax. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Lee, J. OFDMA-based Hybrid Channel Access for IEEE 802.11ax WLAN. In Proceedings of the 2018 14th International Wireless Communications Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 188–193. [Google Scholar] [CrossRef]
- Bellalta, B.; Kosek-Szott, K. AP-initiated Multi-User Transmissions in IEEE 802.11ax WLANs. CoRR 2017. abs/1702.05397. [Google Scholar] [CrossRef]
- Khorov, E.; Loginov, V.; Lyakhov, A. Several EDCA parameter sets for improving channel access in IEEE 802.11ax networks. In Proceedings of the 2016 International Symposium on Wireless Communication Systems (ISWCS), Poznan, Poland, 20–23 September 2016; pp. 419–423. [Google Scholar] [CrossRef]
- Kwon, H.; Seo, H.; Kim, S.; Lee, B.G. Generalized CSMA/CA for OFDMA systems: Protocol design, throughput analysis, and implementation issues. IEEE Trans. Wirel. Commun. 2009, 8, 4176–4187. [Google Scholar] [CrossRef]
- Fallah, Y.P.; Khan, S.; Nasiopoulos, P.; Alnuweiri, H. Hybrid OFDMA/CSMA Based Medium Access Control for Next-Generation Wireless LANs. In Proceedings of the 2008 IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 2762–2768. [Google Scholar] [CrossRef]
- Lou, H.; Wang, X.; Fang, J.; Ghosh, M.; Zhang, G.; Olesen, R. Multi-user Parallel Channel Access for high efficiency carrier grade wireless LANs. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 3868–3870. [Google Scholar] [CrossRef]
- Deng, D.; Chen, K.; Cheng, R. IEEE 802.11ax: Next generation wireless local area networks. In Proceedings of the 10th International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness, Rhodes, Greece, 18–20 August 2014; pp. 77–82. [Google Scholar] [CrossRef]
- Takai, M.; Martin, J.; Bagrodia, R.; Ren, A. Directional Virtual Carrier Sensing for Directional Antennas in Mobile Ad Hoc Networks. In Proceedings of the 3rd ACM International Symposium on Mobile Ad Hoc Networking & Computing, Lausanne, Switzerland, 9–11 June 2002; ACM: New York, NY, USA, 2002; pp. 183–193. [Google Scholar] [CrossRef]
- Lin, K.C.J.; Gollakota, S.; Katabi, D. Random Access Heterogeneous MIMO Networks. SIGCOMM Comput. Commun. Rev. 2011, 41, 146–157. [Google Scholar] [CrossRef]
- Babich, F.; Comisso, M.; Crismani, A.; Dorni, A. On the Design of MAC Protocols for Multi-Packet Communication in IEEE 802.11 Heterogeneous Networks Using Adaptive Antenna Arrays. IEEE Trans. Mob. Comput. 2015, 14, 2332–2348. [Google Scholar] [CrossRef]
- Karthik, R.M.; Palaniswamy, S. Resource Unit (RU) based OFDMA Scheduling in IEEE 802.11ax system. In Proceedings of the 2018 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Bangalore, India, 19–22 September 2018; pp. 1297–1302. [Google Scholar] [CrossRef]
- Deng, D.; Lien, S.; Lee, J.; Chen, K. On Quality-of-Service Provisioning in IEEE 802.11ax WLANs. IEEE Access 2016, 4, 6086–6104. [Google Scholar] [CrossRef]
- Khorov, E.; Kiryanov, A.; Lyakhov, A.; Bianchi, G. A Tutorial on IEEE 802.11ax High Efficiency WLANs. IEEE Commun. Surv. Tutor. 2019, 21, 197–216. [Google Scholar] [CrossRef]
- Random Access with Trigger Frames Using OFDMA; IEEE 802.11-15/0875r1; IEEE: Piscataway, NJ, USA, 2015.
- Bankov, D.; Didenko, A.; Khorov, E.; Lyakhov, A. OFDMA Uplink Scheduling in IEEE 802.11ax Networks. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, K.; Psounis, K. Scheduling and Resource Allocation in 802.11ax. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications, Honolulu, HI, USA, 15–19 April 2018; pp. 279–287. [Google Scholar] [CrossRef]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Babich, F.; Comisso, M.; D’Orlando, M.; Dorni, A. Deployment of a reliable 802.11e experimental setup for throughput measurements. Wirel. Commun. Mob. Comput. 2012, 12, 910–923. [Google Scholar] [CrossRef]
- Cantieni, G.R.; Ni, Q.; Barakat, C.; Turletti, T. Performance Analysis Under Finite Load and Improvements for Multirate 802.11. Comput. Commun. 2005, 28, 1095–1109. [Google Scholar] [CrossRef]
- Malone, D.; Duffy, K.; Leith, D. Modeling the 802.11 Distributed Coordination Function in Nonsaturated Heterogeneous Conditions. IEEE/ACM Trans. Netw. 2007, 15, 159–172. [Google Scholar] [CrossRef]
- Lee, K.; Yoo, J. Performance of the Full-Duplex MAC Protocol in Non-Saturated Conditions. IEEE Commun. Lett. 2017, 21, 1827–1830. [Google Scholar] [CrossRef]









| Parameter | Value |
|---|---|
| 32 | |
| m | 5 |
| L | 6000 Bytes |
| Bandwidth | 20 MHz |
| Data Rate | 36 Mbps |
| Basic Rate | 6.5 Mbps |
| N | 20 |
| 0.5 | |
| 100 frames/s | |
| 100 frames/s | |
| K | 9 |
| 20 s | |
| 1458 s | |
| 1478 s | |
| 1478 s | |
| 1478 s | |
| 341.574 s | |
| 1675 s |
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, K.-h. Performance Analysis of the IEEE 802.11ax MAC Protocol for Heterogeneous Wi-Fi Networks in Non-Saturated Conditions. Sensors 2019, 19, 1540. https://doi.org/10.3390/s19071540
Lee K-h. Performance Analysis of the IEEE 802.11ax MAC Protocol for Heterogeneous Wi-Fi Networks in Non-Saturated Conditions. Sensors. 2019; 19(7):1540. https://doi.org/10.3390/s19071540
Chicago/Turabian StyleLee, Kyu-haeng. 2019. "Performance Analysis of the IEEE 802.11ax MAC Protocol for Heterogeneous Wi-Fi Networks in Non-Saturated Conditions" Sensors 19, no. 7: 1540. https://doi.org/10.3390/s19071540
APA StyleLee, K.-h. (2019). Performance Analysis of the IEEE 802.11ax MAC Protocol for Heterogeneous Wi-Fi Networks in Non-Saturated Conditions. Sensors, 19(7), 1540. https://doi.org/10.3390/s19071540





