A Secure Mutual Batch Authentication Scheme for Patient Data Privacy Preserving in WBAN
Abstract
:1. Introduction
2. Proposed Solution Construction
2.1. Preliminaries
2.1.1. Elliptic Curve Cryptography (ECC)
2.1.2. Bilinear Pairings
- ♦
- Bilinearity:
- ♦
- Non-Degeneracy: ∃ A, B ∈ E1 such that e (A, B) ≠ 1, and 1 is the identity element of E2.
- ♦
- Computation: For any A, B ∈ , we have an efficient algorithm to compute e.
2.2. Security Assumption
- (i)
- Mutual authentication: It will ensure that exclusive genuine and approved C gets access privileges from AP and similarly just approved AP will receive and process data from C.
- (ii)
- Anonymity: This prerequisite guarantees that an attacker does not have access to the genuine partaker’s identity (C and AP) in their identification procedure.
- (iii)
- Unlinkability: This condition guarantees that an attacker cannot interface C’s identity to a particular session while asking for computations from AP.
- (iv)
- Furthermore, our proposed solution provides resilience to replay and impersonation attack. Further, used keys cannot be recovered by an attacker, and our solution does not use verification table.
2.3. Related Work
- ♦
- Initialization phase: It mainly consists of generating keys and system parameters and it is done by the NM shown below.
- (i)
- NM computes a large prime number q, two groups , , a pairing map
- (ii)
- NM selects two secured hashing maps h and H, where and .
- (iii)
- NM generates randomly a number as its secret key and compute as its public key.
- (iv)
- Finally, NM provides as public parameters .
- ♦
- Registration phase: It is during this step that C and AP get registered with NM to get their different partial private key.
- (i)
- The entity C/AP transmits his identity to NM.
- (ii)
- With , NM computes the partial secret key , where . NM then sends secret key to O through a secure channel.
- (iii)
- C/AP secretly stores its partial private key .
- ♦
- Authentication phase: At this phase C/AP mutually authenticates each other and computes secured keys to encrypt patient records as follows:
- (i)
- C generates a random number , calculates , . With, the current timestamp. Then, C sends a message to AP.
- (ii)
- With , AP verifies the freshness of and rejects if it is not fresh. AP computes and gets by decrypting . Then AP compares if and the decrypted one are equal. If not matching, AP cancels the access process. Else, AP computes randomly a number ∈ and computes session key , where is the actual time stamp. Then, AP transfers message to C.
- (iii)
- Receiving , C verifies the freshness of . If not, C stops the access demand. Otherwise, C computes , and checks the correctness of the equation . Then, C computes session key else the answer is rejected.
2.4. The Security Shortcoming
3. Proposed Solution
- (1)
- Subscriber authentication: AP should confirm the various C’s identity to guarantee their authenticity.
- (2)
- Provider validation: A client C is permitted to verify the different AP’s identity it visits to keep away from potential forgery and various malevolent attacks.
- (3)
- Key generation: A different encryption key is generated each time C and AP initiate a session to ensure the protection of the transferred data.
- (4)
- Anonymous Client: Apart NM, the client C is unknown and its operations are unlinkable to anybody including the AP.
3.1. Security System Settings
3.2. Registration Phase
3.2.1. The Client C Registration
3.2.2. Application Provider AP Registration
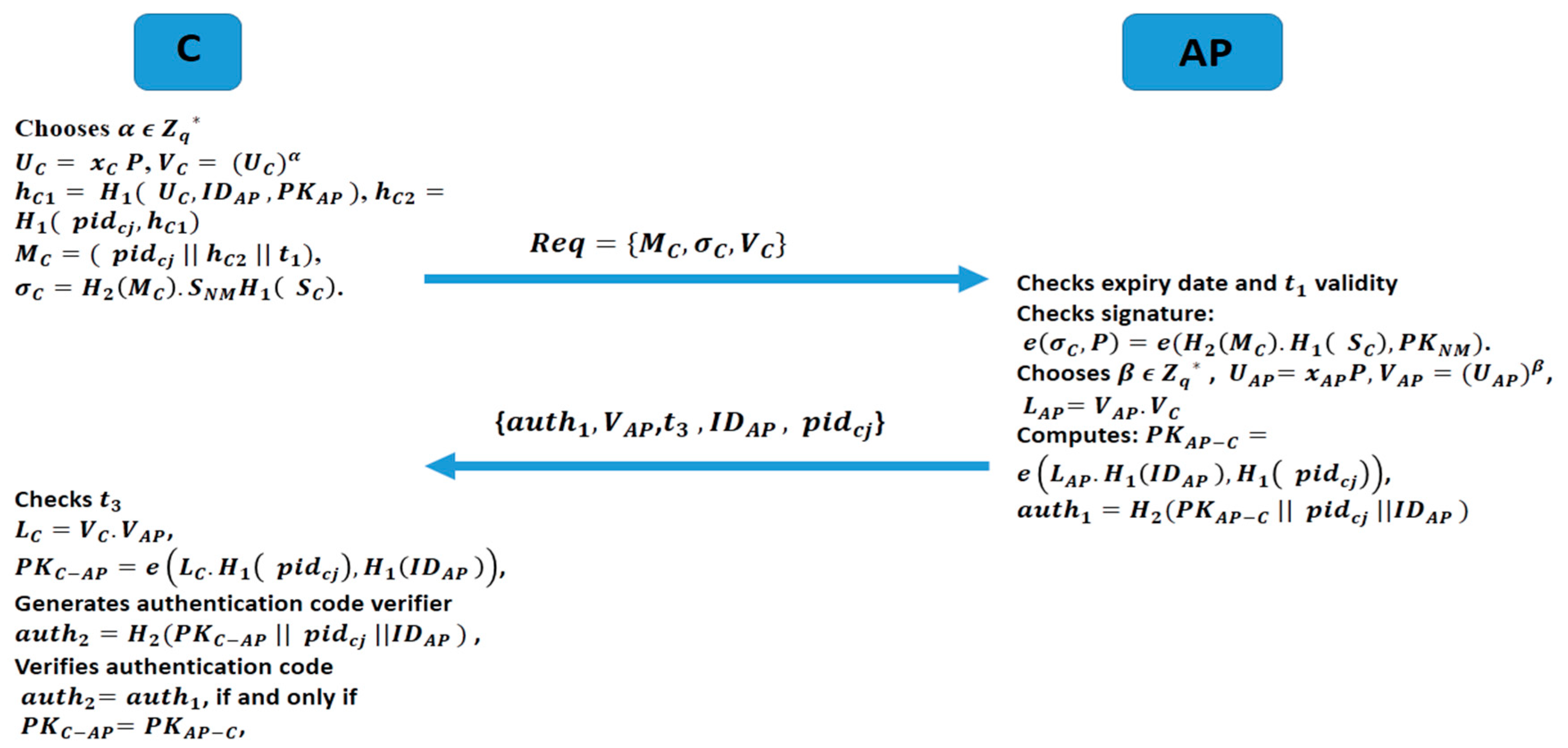
3.3. Authentication Phase
- (1).
- C picks a random unused pseudo-ID () and its corresponding partial private key . Then C chooses randomly and compute , and a session verifier .
- (2).
- C computes , and composes message .
- (3).
- The client C computes a signature and sends a request message to AP: with the valid transmission delay calculated by C.
- (4).
- Upon receiving the request message (Req) at time from C, AP first verifies the expiry date in . If the expiry date is valid, AP then checks the freshness of by verifying if If is fresh, AP with the public parameters params, verifies the validity of C’s signature by checking if the Equation (3) holds.Verification:
- (5).
- AP selects randomly and computes: (session verifier), and .
- (6).
- Then AP computes a private session key and generates an authentication code and sends {, } to C.
- (7).
- Upon receiving {, } at from AP, the client C verifies the freshness of by checking if , with ∆ the valid transmission delay calculated by AP. If is fresh, C computes , and a private symmetric session key with AP like: Furthermore, C generates an authentication verification code and compares with . If , then C can ascertain the identity of AP as legitimate; otherwise, C stops the communication process with AP and reports it to NM. In this scenario C can verifies if if and only if :
4. Security and Performance Analysis
4.1. Security Analysis
- ♦
- Anonymity: Each C gets a set of pseudo-identity and its related partial secret key uring registration process from NM. These pseudo-identities, rather than C’s real identity, provide strong privacy protection. Not any involved entity, not even AP, can identify C or recollect different transactions launched by the same C except NM. In practice, C sends a random message request each time to AP. This message request contains secret values () and pseudo-ID that are random (not constant) values each time that C initiates an authentication process with AP. Only C can compute and since these values require both secret values () and partial private keys for their calculation. Therefore, an attacker including NM, in order to compute must solve the inherited CDH problem; that is, he should perform and then for unknown random secret values , which contradicts the CDH assumption. Therefore, C is anonymous and cannot be impersonated through our scheme. Therefore, our scheme guarantees data anonymity and identicalness (aggregated values) based on BDBH assumption in random oracle to resist chosen-plaintext attacks.
- ♦
- Mutual Authentication: The client C’s signature is in fact a signed based pseudo-identity. Therefore, it is impracticable to fake a genuine signature without prior access to the secret values and due to the NP-hard calculation complexity of the Diffie–Hellman assumption in . Thereby it is very hard to deduce the partial private key using , and . Similarly, an attacker with no prior knowledge of AP’s partial private key and secret values and cannot make a legitimate authentication code . Further an adversary cannot compute and verify the equation since he cannot solve CDH (definition 1) as described in the section above. Furthermore, only legitimate C and AP can compute , due to the randomness and secrecy of and respectively. Therefore, a secured authentication process between C and AP is achieved by our scheme.
- ♦
- Unlinkability: Recall that C uses different pseudo-identity during each authentication process with an AP. Furthermore, only NM is aware of the relation between a given pseudo-identity and its original C’s identity. For that reason, excluding NM and C, no other entity is able to determine C or relate different authentication processes launched by the same C.
- ♦
- Leaked key security: As described in Section 3, our scheme provides a random distinct session key each time an authentication process is initiated by C with AP. It is due to the randomness of the choice of secret values α by C and AP. Doing so, an attacker with a used key has a very slight chance to compromise succeeding sessions.
- ♦
- Impersonation attack: To impersonate C or AP, an adversary should generate the correct values of and , respectively, which is practically infeasible, as explained above (mutual authentication process section). Further an AP cannot generate a correct C’s signature and in the message request, since he cannot access and otherwise the attack can be detected by C in verifying . Likewise, an adversary that intercepts the message and tries to impersonate AP has a negligible chance of success due to the CDH assumption (mutual authentication process section) that is believed to be difficult. The performance analysis section highlights the security functional results comparison between our scheme and related works [7,8,9].
- ♦
- Data Aggregation: Moreover, aggregated values in our proposed solution hide the accrued single value that enforces the privacy preservation of single C compared to related works [7,8,9]. To achieve this additional aggregated data feature, we designed a modified additively homomorphic IBE scheme from the Boneh–Franklin IBE cryptosystem [33]. The security proof lies on BDDH assumption in a random oracle (refer to security analysis section). This cryptosystem [33] is appropriate for our proposed solution (small sensing data reading) to achieve data aggregation and batch authentication. Our modified IBE scheme has four algorithms and we use , of prime order q, P as generator of , and a bilinear mapping e: × → , such that , , and e(P, Q) ≠ whenever .
4.2. Performance Analysis
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bourouis, A.; Feham, M.; Bouchachia, A. Ubiquitous mobile health monitoring system for elderly (UMHMSE). arXiv, 2011; arXiv:1107.3695. [Google Scholar] [CrossRef]
- Latre, B.; Braem, B.; Moerman, I.; Blondia, C.; Demeester, P. A survey on wireless body area networks. Wirel. Netw. 2011, 17, 1–18. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two- factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J.H. Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 2016, 99, 1–12. [Google Scholar] [CrossRef]
- Shamir, A. Advances in cryptology. In Proceedings of the CRYPTO 84, Chap. Identity-Based Cryptosystems and Signature Schemes; Springer: Berlin, Germany, 1985; pp. 47–53. [Google Scholar] [CrossRef]
- Li, F.; Zheng, Z.; Jin, C. Secure and efficient data transmission in the internet of things. Telecommun. Syst. 2016, 62, 111–122. [Google Scholar] [CrossRef]
- Wang, C.; Zhang, Y. New authentication scheme for wireless body area networks using the bilinear pairing. J. Med. Syst. 2015, 39, 1–8. [Google Scholar] [CrossRef] [PubMed]
- Liu, J.; Zhang, Z.; Chen, X.; Kwak, K.S. Certificate-less remote anonymous authentication schemes for wireless body area networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 332–342. [Google Scholar] [CrossRef]
- Zhao, Z. An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 2014, 38, 1–7. [Google Scholar] [CrossRef] [PubMed]
- Abi-Char, P.E.; Mhamed, A.; El-Hassan, B. A fast and secure elliptic curve based authenticated key agreement protocol for low power mobile communications. In Proceedings of the International Conference on Next Generation Mobile Applications, Services and Technologies (NGMAST 2007), Cardiff, UK, 12–14 September 2007; pp. 235–240. [Google Scholar] [CrossRef]
- Li, X.; Hamada Ibrahim, M.; Kumari, S.; Kumar Sangaiah, A.; Gupta, V.; Raymond Choo, K. Anonymous Mutual Authentication and Key Agreement Scheme for Wearable Sensors in Wireless Body Area Networks. Comput. Netw. 2017, 129, 429–443. [Google Scholar] [CrossRef]
- Koya, A.; Deepthi, P.P. Anonymous hybrid mutual authentication and key agreement scheme for wireless body area network. Comput. Netw. 2018, 140, 138–151. [Google Scholar] [CrossRef]
- Kompara, M.; Islam, S.K.H.; Hölbl, M. A Robust and Efficient Mutual Authentication and Key Agreement Scheme with Untraceability for WBANs. Comput. Netw. 2018, 148, 196–213. [Google Scholar] [CrossRef]
- Das, A.K.; Kumar, S.A.; Odelu, V.; Goswami, A. A Secure Smartcard-Based Anonymous User Authentication Scheme for Healthcare Applications Using Wireless Medical Sensor Networks. Wirel. Pers. Commun. 2017, 94, 1899–1933. [Google Scholar] [CrossRef]
- Chen, R.; Peng, D. A Novel NTRU-Based Handover Authentication Scheme for Wireless Networks. IEEE Commun. Lett. 2017, 22, 586–589. [Google Scholar] [CrossRef]
- Jiang, C.; Li, B.; Xu, H. An efficient scheme for user authentication in wireless sensor networks. In Proceedings of the 21st International Conference on Advanced Information Networking and Applications Workshops, Niagara Falls, ON, Canada, 21–23 May 2007; pp. 438–442. [Google Scholar] [CrossRef]
- Li, F.; Han, Y.; Jin, C. Practical access control for sensor networks in the context of the internet of things. Comput. Commun. 2016, 89, 154–164. [Google Scholar] [CrossRef]
- Xiong, H. Cost-effective scalable and anonymous certificate-less remote authentication protocol. IEEE Trans. Inf. Forensics Secur. 2014, 9, 23–39. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A survey on sensor networks. IEEE Commun. Mag. 2002, 40, 102–114. [Google Scholar] [CrossRef]
- Cherukuri, S.; Venkatasubramanian, K.K.; Gupta, S.K.S. Biosec: A biometric based approach for securing communication in wireless networks of biosensors implanted in the human body. In Proceedings of the International Conference on Parallel Processing Workshops, Kaohsiung, Taiwan, 6–9 October 2003; pp. 432–439. [Google Scholar] [CrossRef]
- Aydos, M.; Sunar, B.; Koc, C.K. An elliptic curve cryptography based authentication and key agreement protocol for wireless communication. In Proceedings of the Second International Workshop on Discrete Algorithm and Methods for Model Computation and Communication, Dallas, TX, USA, 30 October 1998. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Advances in Cryptology. In Proceedings of the ASIACRYPT 2003: 9th International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; pp. 452–473. [Google Scholar] [CrossRef]
- Kim, S.J.; Chung, J.Y. Eeg encryption scheme with junk data using chaos maps. In Proceedings of the 6th International Conference on Intelligent Systems, Modelling and Simulation, Kuala Lumpur, Malaysia, 9–11 February 2015; pp. 132–134. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of Elliptic Curves in Cryptography. In Advances in Cryptology—CRYPTO ’85 Proceedings. CRYPTO 1985; Lecture Notes in Computer Science, 218; Williams, H.C., Ed.; Springer: Berlin/Heidelberg, Germany, 1985. [Google Scholar]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Dong, C. Jpair: A Quick Introduction. Available online: https://personal.cis.strath.ac.uk/changyu.dong/jpair/intro.html (accessed on 20 June 2010).
- Islam, S.H. Design and analysis of an improved smartcard-based remote user password authentication scheme. Int. J. Commun. Syst. 2016, 29, 1708–1719. [Google Scholar] [CrossRef]
- Omala, A.A.; Kibiwott, K.P.; Li, F. An Efficient Remote Authentication Scheme for Wireless Body Area Network. J. Med. Syst. 2016, 41, 1–9. [Google Scholar] [CrossRef] [PubMed]
- Dolev, D.; Yao, A.C. On the security of public key protocols. In Proceedings of the 22nd Annual Symposium on Foundations of Computer Science (sfcs 1981), Nashville, TN, USA, 28–30 October 1981; pp. 350–357. [Google Scholar] [CrossRef]
- Dimitrakakis, C.; Gkoulalas-Divanis, A.; Mitrokotsa, A.; Verykios, S.V.; Saygin, Y. Privacy and Security Issues in Data Mining and Machine Learning; Springer-Verlag: Berlin/Heidelberg, Germany; Barcelona, Spain, 2010. [Google Scholar]
- Raya, M.; Hubaux, J.-P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M.K. Identity-Based Encryption from the Weil Pairing. In Proceedings of the 21st Annual International Cryptology Conference on Advances in Cryptology, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Scott, M. Multiprecision Integer and Rational Arithmetic C/C++ Library (MIRACL); Shamus Software Ltd. Available online: http://urlm.co/www.shamus.ie (accessed on 16 November 2018).


| Symbols | Description |
|---|---|
| NM | Network manager |
| AP | Application provider |
| C | WBAN client/controller |
| q | Large prime number |
| Additive group with order q | |
| Secure hash function with i = 1, 2 | |
| Network manager private key | |
| Elliptic curve over prime field | |
| Prime field | |
| e || f | Concatenation of strings e and f |
| Generator of group G | |
| Client pseudo-ID, with j = 1, 2, 3 | |
| Application identity | |
| Network manager public key |
| Scheme | Wang and Zhang [7] | Liu [8] | Zhao [9] | Omala, A.A. et al. [29] | Our Scheme |
|---|---|---|---|---|---|
| Data aggregation | × | × | × | × | √ |
| Mutual authentication | √ | √ | √ | √ | √ |
| Anonymity | √ | √ | × | √ | √ |
| Impersonation attack | × | √ | √ | √ | √ |
| Unlinkability | √ | × | √ | √ | √ |
| Leaked key security | √ | √ | √ | √ | √ |
| Batch authentication | × | × | × | × | √ |
| AP (ms) | C (ms) | |
|---|---|---|
| TME | 13.21 | 63.51 |
| TSM | 6.38 | 30.67 |
| TP | 20.04 | 96.35 |
| THG | 3.04 | 14.62 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Konan, M.; Wang, W. A Secure Mutual Batch Authentication Scheme for Patient Data Privacy Preserving in WBAN. Sensors 2019, 19, 1608. https://doi.org/10.3390/s19071608
Konan M, Wang W. A Secure Mutual Batch Authentication Scheme for Patient Data Privacy Preserving in WBAN. Sensors. 2019; 19(7):1608. https://doi.org/10.3390/s19071608
Chicago/Turabian StyleKonan, Martin, and Wenyong Wang. 2019. "A Secure Mutual Batch Authentication Scheme for Patient Data Privacy Preserving in WBAN" Sensors 19, no. 7: 1608. https://doi.org/10.3390/s19071608





