Towards Deep-Learning-Driven Intrusion Detection for the Internet of Things
Abstract
1. Introduction
- Development of an anomaly-based intrusion-detection model using deep learning for IoT networks.
- Implementation and evaluation of the model for efficiency.
2. Related Work
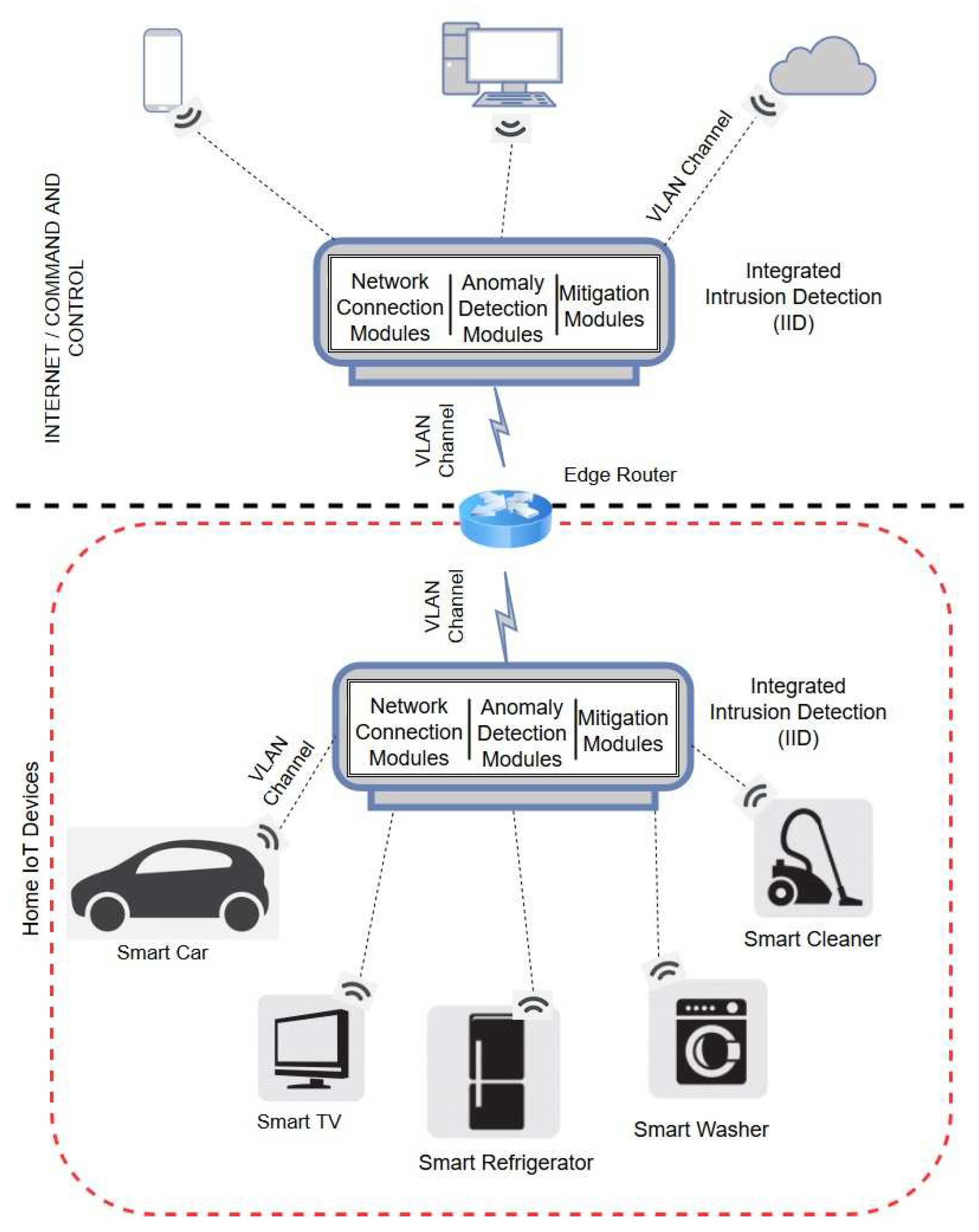
3. Intrusion-Detection Framework
3.1. System Architecture
3.2. Components of Detection System
3.2.1. Network Connection Phase
- (i)
- Connection Prober: The connection prober module is responsible for sending probe-signals and broadcast beacons to all the devices within the host IoT personal area network. The module is executed periodically and on-line, as the communication links are constructed dynamically within an IoT network. Connection Prober module maintains a list of all the active communications protocols that are being used in the network. It uses this list to maintain active network interfaces which can be used to intercept different wireless communication signals, transmitted in the surrounding environment. Consequently, it attempts to intercept broadcast beacons, handshake messages, or session requests to learn the communication protocols that are being used by IoT devices. On receiving a handshake or a session request, the connection prober module translates the data-packet into appropriate network packet format. Typically, the connection prober module is designed to use a secondary storage location as a default cache location that is simultaneously replicated in the physical memory using a cache-handle. After fetching the bit stream, it uses the known communication protocols to bisect the bit stream into different networks packets and then feeds these packets into cache and the data collection and transformation module (discussed in the next subsection).If the connection prober fails at intercepting the broadcast beacons, or handshake messages, it attempts to deduce the connection protocol by apprehending the data packets transmitted during regular data communication of surrounding IoT devices. This is made possible because CoAP communication cycle involves at least 4 successful messages and when connection prober fails to intercept a communication, it attempts to gather information from successive messages, resulting in CP’s probability of success, . The number of messages in an IoT communication cycle increases as bare IoT communication is loaded with payload. With increase in number of messages, probability of successful interception increases, resulting in , approaching towards unity. In worst-case scenario, if CP misses the entire IoT communication cycle, the IDS uses pre-trained neural networks to estimate the network behavior in the current period. Subsequently, with further training the IDS can be trained to respond to a new protocol.
- (ii)
- Virtual Network Client (VNC): The VNC module is a client-based network emulator responsible for establishing compatible network channels with various IoT devices after gathering information about their network protocols. VNC module transforms the packets from different network channels and switches the network protocol according to a specific IoT device.
- (iii)
- Controller: The Controller module is responsible for controlling and interfacing the exchange of data packets or commands between the data collection & transformation module and the VNC module. All the modules other than connection prober and VNC module are autonomous and not governed by the Controller module.
3.2.2. Anomaly-Detection Phase
- (i)
- Data Collection and Transformation (DCT): DCT module is responsible for stripping the data packets, extracting the header tags as features, populating the cached database, and feeding these tuples into machine-learning-based anomaly-detection module. The features extracted in this work is listed in Table 1. Algorithm 1 details the process where each input network packet is sliced into distinct layers of the TCP/IP stack, and thereafter, respective header tags are extracted for each layer in string format. Each non-empty layer is then designated a label for future reference. Consequently, the extracted header tags are added to a list under the label of their respective layer, thereby removing any repetition of header tags. The data collection and transformation module also pipelines these lists back to the cache.
Algorithm 1 Extracting tags from the sniffed network packets. Require: T - List of all header tags from all packets in network interface queue.
function PacketHandler() /*where pkt - captured network packet*/
Extract /*Get tagstring from the packet*/
Divide the for each
for every in do
Get
if then
Split the
end if
for every do
Add the to a list
end for
Assign the to /*assign list to layer*/
end for
end function - (ii)
- Machine-learning-based anomaly-detection (MLAD): This module is the principal machine-learning engine of the proposed IDS, responsible for classifying benign network traffic from malicious network traffic. It employs a perceptual learning model for performing anomaly detection. This module is activated when the IDS enters the Anomaly-Detection phase, which consists of two phases, i.e., the training phase and the detection phase. The training phase is performed across long intervals of time, and performed off-line. The perceptual model is trained using supervised learning over the tuples of features generated during the data-preprocessing. Before feeding the tuple into the perceptual learning model, each tuple is manually augmented with a binary-classification label representing malicious or benign nature of network packet. The perceptual learning model uses information gain at each perceptual layer to filter out the preferred features, before feeding to the next perceptual layer. We discuss the MLAD module in detail in Section 4.
- (iii)
- Trainer: This module is invoked when MLAD is required to train for an unknown tuple and it requires human intervention.
3.2.3. Mitigation Phase
- (i)
- Actuator ModuleThe Actuator module is responsible for identifying the most suitable mitigation response in the event of an attack within the IoT network. The mitigation response can either send an alarm signal or shut down the communication in the network. When the Actuator module is aware of an appropriate mitigation response, it would activate the Handler module to execute the response or generate an alarm for the end-user.
- (ii)
- Handler ModuleThe Handler module is primarily a set of mitigation procedures hard-coded within IID program to execute a mitigation procedure as a proof of concept. A mitigation procedure is invoked by the Actuator module in response to an intrusion, and is further executed by the Handler module. Once the mitigation response is executed successfully by the Handler module, it logs the type of attack and the mitigation response provided. If the Handler module is required to raise an alarm for the user, it flags the discovered intrusion for ’requiring user attention’ and logs this information in the log file.
4. Detection Using Deep Learning
4.1. Feature Set
Feature Extraction
4.2. Deep-Learning-Based Anomaly Detection
| Algorithm 2 Intrusion-Detection using Deep-Learning model |
| Require: N - List of all header tags from all packets in network interface queue. function Predict() /*where cachePipe - is the pipe established with cache*/ /*translate packets to matrices*/ Extract from matrix Define & Initialize - if then Compile- classifier - end if Training: if is complete then Prediction: if are correct then Re-Train the else Invoke end if end if Store: /*store the classifier model*/ end function |
Training Deep Neural Network
5. Implementation and Results
5.1. Data Preprocessing
5.2. Deep-Learning Implementation
5.3. Attack Model
- Blackhole Attack: In a blackhole attack, the malicious device falsely advertises shortest route to destination and then silently drops all packets on its path creating a blackhole in the network.
- Opportunistic Service Attack: In an opportunistic service attack, the malicious device increases its trust value by providing highly dependable services at first and then later resorts to providing inferior service for its own profit.
- Distributed Denial-of-Service (DDoS) Attack: In a DDoS attack, multiple compromised IoT devices attack a target server or other network resources resulting in denial of service for users of the targeted resource.
- Sinkhole Attack: In a sinkhole attack, the malicious node may announce beneficial route or falsified path to attract all nodes to redirect their packets through it, acting as a sink.
- Wormhole Attack: In a wormhole tunnel attack, pair of attacker devices collude with each other through a virtual private connection. The network packets received by the victim device is first forwarded through the wormhole, and replayed later, resulting in non-optimized routes.
5.4. Evaluation Results
6. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of Things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Smith, S. IoT Connected Devices to Triple to Over 38Bn Units; Juniper Research: Basingstoke, Hampshire, UK, 2015. [Google Scholar]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed Internet of Things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Khan, A. Overview of Security in Internet of Things. In Proceedings of the 3rd International Conference on Recent Trends in Engineering Science and Management, Bundi, Rajasthan, India, 10 April 2016. [Google Scholar]
- Abomhara, M.; Koien, G.M. Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Shieh, S.W. Emerging Security Threats and Countermeasures in IoT. In Proceedings of the ACM Asia Conference on Computer and Communications Security, Singapore, 14–17 April 2015. [Google Scholar]
- Williams, R.; McMahon, E.; Samtani, S.; Patton, M.; Chen, H. Identifying vulnerabilities of consumer Internet of Things (IoT) devices: A scalable approach. In Proceedings of the 2017 IEEE International Conference on Intelligence and Security Informatics (ISI), Beijing, China, 22–24 July 2017; pp. 179–181. [Google Scholar]
- Hilton, S. Dyn Analysis Summary Of Friday October 21 Attack. Dyn Blog, 26 October 2016. [Google Scholar]
- Solon, O. Team of hackers take remote control of Tesla Model S from 12 miles away. The Guardian, 20 September 2016. [Google Scholar]
- Pycroft, L.; Aziz, T.Z. Security of implantable medical devices with wireless connections: The dangers of cyber-attacks. Expert Rev. Med. Devices 2018, 15, 403–406. [Google Scholar] [CrossRef] [PubMed]
- Kasinathan, P.; Costamagna, G.; Khaleel, H.; Pastrone, C.; Spirito, M.A. DEMO: An IDS Framework for Internet of Things Empowered by 6LoWPAN. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013. [Google Scholar]
- Krimmling, J.; Peter, S. Integration and Evaluation of Intrusion Detection for CoAP in smart city applications. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), San Francisco, CA, USA, 29–31 October 2014. [Google Scholar]
- Le, A.; Loo, J.; Lasebae, A.; Aiash, M.; Luo, Y. 6LoWPAN: A study on QoS security threats and countermeasures using intrusion detection system approach. Int. J. Commun. Syst. 2012, 25, 1189–1212. [Google Scholar] [CrossRef]
- Chawla, S.; Thamilarasu, G. Security As a Service: Real-time Intrusion Detection in Internet of Things. In Proceedings of the Fifth Cybersecurity Symposium, CyberSec ’18, Coeur d’ Alene, ID, USA, 9–11 April 2018; pp. 12:1–12:4. [Google Scholar]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 10th International Conference on Frontiers of Information Technology, Islamabad, India, 17–19 December 2012. [Google Scholar]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Security of IoT Systems: Design Challenges and Opportunities. In Proceedings of the International Conference on Computer-Aided Design, San Jose, CA, USA, 3–6 November 2014. [Google Scholar]
- Heer, T.; Garcia-Morchon, O.; Hummen, R.; Keoh, S.L.; Kumar, S.S.; Wehrle, K. Security Challenges in the IP-based Internet of Things. Wirel. Person. Commun. 2011, 61, 527–542. [Google Scholar] [CrossRef]
- Sfar, A.R.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The Effect of IoT New Features on Security and Privacy: New Threats, Existing Solutions, and Challenges Yet to Be Solved. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Zhao, K.; Ge, L. A Survey on the Internet of Things Security. In Proceedings of the 2013 9th International Conference on Computational Intelligence and Security (CIS), Leshan, Sichuan, China, 14–15 December 2013. [Google Scholar]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar]
- Danda, J.M.R.; Hota, C. Attack Identification Framework for IoT Devices. In Information Systems Design and Intelligent Applications; Springer India: New Delhi, India, 2016; pp. 505–513. [Google Scholar]
- Le, A.; Loo, J.; Chai, K.K.; Aiash, M. A Specification-Based IDS for Detecting Attacks on RPL-Based Network Topology. Information 2016, 7, 25. [Google Scholar] [CrossRef]
- Surendar, M.; Umamakeswari, A. InDReS: An Intrusion Detection and response system for Internet of Things with 6LoWPAN. In Proceedings of the 2016 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 23–25 March 2016. [Google Scholar]
- Bostani, H.; Sheikhan, M. Hybrid of anomaly-based and specification-based IDS for Internet of Things using unsupervised OPF based on MapReduce approach. Comput. Commun. 2017, 98, 52–71. [Google Scholar] [CrossRef]
- Fu, Y.; Yan, Z.; Cao, J.; Koné, O.; Cao, X. An Automata Based Intrusion Detection Method for Internet of Things. Mobile Inf. Syst. 2017, 2017, 1750637. [Google Scholar] [CrossRef]
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time Intrusion Detection in the Internet of Things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Liu, C.; Yang, J.; Chen, R.; Zhang, Y.; Zeng, J. Research on immunity-based intrusion detection technology for the Internet of Things. In Proceedings of the 2011 Seventh International Conference on Natural Computation, Shanghai, China, 26–28 July 2011; pp. 212–216. [Google Scholar]
- Arrington, B.; Barnett, L.; Rufus, R.; Esterline, A. Behavioral Modeling Intrusion Detection System (BMIDS) Using Internet of Things (IoT) Behavior-Based Anomaly Detection via Immunity-Inspired Algorithms. In Proceedings of the 2016 25th International Conference on Computer Communication and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016. [Google Scholar]
- Liu, L.; Xu, B.; Zhang, X.; Wu, X. An intrusion detection method for internet of things based on suppressed fuzzy clustering. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 113. [Google Scholar] [CrossRef]
- Nielsen, M.A. Neural Networks and Deep Learning; Determination Press, 2015; Available online: http://neuralnetworksanddeeplearning.com/ (accessed on 25 April 2019).
- Thomson, C.; Romdhani, I.; Al-Dubai, A.; Qasem, M.; Ghaleb, B.; Wadhaj, I. Cooja Simulator Manual; Edinburgh Napier University: Edinburgh, UK, 2016. [Google Scholar]
- Alghuried, A. A Model for Anomalies Detection in Internet of Things (IoT) Using Inverse Weight Clustering and Decision Tree. Masters’s Thesis, Dublin Institute of Technology, Dublin, Ireland, 2017. [Google Scholar]










| transmission rate | reception rate |
| transmission to reception ratio | activity duration |
| transmission mode | source IP |
| destination IP | datavalue in formation |
| Method | Precision | TPR | F1 Score |
|---|---|---|---|
| DL-Sim | 97.2% | 96.4% | 0.97 |
| IWC | 89% | 95% | 0.92 |
| Method | Precision | TPR | F1 Score |
|---|---|---|---|
| DL-Sim | 95.7% | 98% | 0.97 |
| IWC | 94% | 98% | 0.96 |
| Method | Precision | TPR | F1 Score |
|---|---|---|---|
| DL | 96% | 98.7% | 0.973 |
| IWC | 91% | 95% | 0.93 |
| Method | Precision | TPR | F1 Score |
|---|---|---|---|
| DL-Sim | 99.5% | 99% | 0.99 |
| DL-Testbed | 98.47% | 97% | 0.97 |
| IWC | 98.37% | 91.2% | 0.94 |
| Method | Precision | TPR | F1 Score |
|---|---|---|---|
| DL-Sim | 96% | 98% | 0.97 |
| DL-Testbed | 93% | 91% | 0.92 |
| IWC | 98.37% | 97% | 0.97 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Thamilarasu, G.; Chawla, S. Towards Deep-Learning-Driven Intrusion Detection for the Internet of Things. Sensors 2019, 19, 1977. https://doi.org/10.3390/s19091977
Thamilarasu G, Chawla S. Towards Deep-Learning-Driven Intrusion Detection for the Internet of Things. Sensors. 2019; 19(9):1977. https://doi.org/10.3390/s19091977
Chicago/Turabian StyleThamilarasu, Geethapriya, and Shiven Chawla. 2019. "Towards Deep-Learning-Driven Intrusion Detection for the Internet of Things" Sensors 19, no. 9: 1977. https://doi.org/10.3390/s19091977
APA StyleThamilarasu, G., & Chawla, S. (2019). Towards Deep-Learning-Driven Intrusion Detection for the Internet of Things. Sensors, 19(9), 1977. https://doi.org/10.3390/s19091977





