A Lightweight Three-Factor Authentication and Key Agreement Scheme in Wireless Sensor Networks for Smart Homes
Abstract
:1. Introduction
1.1. Related Works
1.2. Research Contributions
- We analyze the most recent three-factor authentication and key agreement scheme of Jung et al.’s scheme and present its security weaknesses. We show that Jung et al.’s scheme [13] does not provide strong anonymity and the secrecy of the secret key of the gateway node. We also show that Jung et al.’s scheme is vulnerable to a tracing attack, information leakage attack, session key recovery attack, and user impersonation attack.
- We introduce a system model suitable for smart homes based on WSNs. Under this model, we propose a lightweight three-factor authentication and key agreement scheme as an improved version of Jung et al.’s scheme. The proposed scheme not only satisfies various security requirements but also uses lightweight operations, such as XOR and hash functions, which are very suitable for the resource constrained WSNs.
- We formally prove the security of the proposed scheme using both random oracle model and BAN (Burrows-Abadi-Needham) logic. We then verify the proposed scheme on popular and robust security verification tool, AVISPA (Automated Validation of Internet Security Protocols and Applications).
- Through informal security analysis, we show that the proposed scheme can satisfy the required security properties and withstand various attacks. We then compare it with other related schemes in terms of security features.
- Through a performance evaluation, we compare the performance of the proposed scheme with other related schemes in terms of their computational cost and communication cost.
1.3. Preliminary
- : Given a biometric template as an input, this probabilistic algorithm outputs a secret biometric key and a helper string .
- : Given a noisy biometric and a helper string as inputs, this deterministic algorithm reproduces the biometric key .
2. Review of Jung et al.’s Scheme
2.1. Registration Phase
- (1)
- chooses , and a random number u and imprints his/her biometrics . computes and and sends a registration request to .
- (2)
- Upon receiving the registration request, computes and . then issues a smart card by storing in its memory and sends the smart card to .
- (3)
- Upon receiving the smart card, computes and additionally stores it into the smart card.
2.2. Login Phase
- (1)
- inserts own smart card into a terminal, enters and , and imprints .
- (2)
- The smart card computes , and . The smart card then checks whether matches with the received . If it does not hold, the smart card terminates this phase. Otherwise, the smart card confirms the legitimacy of and computes and .
- (3)
- The smart card sends the login request to through a public channel.
2.3. Authentication Phase
- (1)
- checks the validity of and computes and . then checks whether matches with the received . If it does not hold, it terminates this phase. Otherwise, believes that is authentic and proceeds with the next step.
- (2)
- chooses a random number R and computes and . then sends the message to through a public channel.
- (3)
- Upon receiving the message, checks the validity of and computes and . checks whether matches with the received . If it does not hold, terminates this phase. Otherwise, believes the is authentic.
- (4)
- computes and . finally sends the message to through a public channel.
- (5)
- Upon receiving the message, checks the validity of and computes and . then checks whether matches with the received . If it does not hold, terminates this phase. Otherwise, believes that is authentic and proceeds with the next step.
- (6)
- computes and and sends the message to through a public channel.
- (7)
- Upon receiving the message, checks the validity of and computes and . then checks whether matches with the received . If it does not hold, this phase is terminated. Otherwise, believes that is authentic and successfully ends the authentication phase.
3. Security Weaknesses of Jung et al.’s Scheme
3.1. Tracing Attack
3.2. Insecurity of the Secret Key of the Gateway Node
3.3. Information Leakage Attack
- (1)
- intercepts the user ’s login message , where , , and .
- (2)
- computes and .
- (3)
- then computes .
3.4. Session Key Compromise
- (1)
- intercepts the last message sent from , where and .
- (2)
- computes .
- (3)
- discovers the session key between the user , , and the sensor node by computing .
3.5. User Impersonation Attack
- (1)
- computes and , where is the current time stamp used by . Of course, since and are the fixed values, it is possible to use the previously intercepted one.
- (2)
- sends the login message .
- (3)
- At , user authentication is successfully performed and calculates the session key after receiving the last message as described in Section 3.4.
4. Proposed Scheme for Smart Homes
4.1. System Setup Phase
- (1)
- generates randomly two master secrets and for all users and all sensor nodes, respectively, which are only known to .
- (2)
- selects a unique identity and computes for each sensor node .
- (3)
- Finally, each sensor node is deployed in the target field after storing and into its memory in a secure manner.
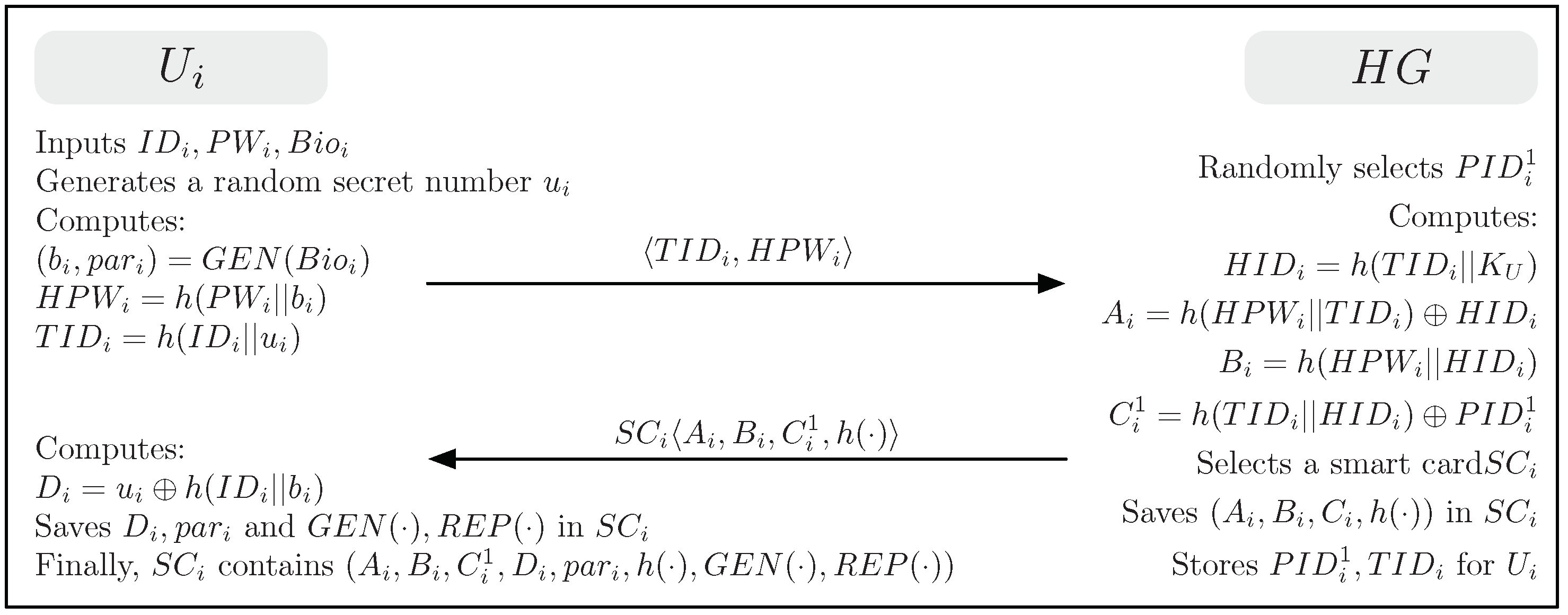
4.2. User Registration Phase
- (1)
- selects the desired identity and password and imprints his/her biometrics . generates a random secret number and computes , and . then sends a registration request to over a secure channel.
- (2)
- Upon receiving the user’s registration request, randomly selects a unique one-time pseudonym for . computes , , , and . issues a smart card for after saving in it. then sends to over a secure channel and stores into its memory.
- (3)
- After receiving the smart card , computes and saves , , , and in . Finally, contains .
4.3. Login Phase
- (1)
- inserts own , inputs his/her and , and imprints his/her biometrics into a terminal (i.e., a smart card reader or a smartphone embedded with ).
- (2)
- computes , , , , and . checks whether matches with the stored . If it matches ensures that has provided correct and . then selects a random number and computes and .
- (3)
- Finally, sends a login request to over a public channel.
4.4. Authentication Phase
- (1)
- checks the validity of the timestamp and searches using . computes , , , and . Then, compares with the received value . If this condition is not satisfied, terminates this phase. Otherwise, believes that is a legitimate user. then chooses an appropriate sensor node for the user’s needs and computes , , and . sends the message to over a public channel.
- (2)
- Upon receiving the message from , checks the validity of the timestamp and compute and . then compares with the received value . If this condition is not satisfied, terminates this phase since fails to prove to be a legitimate home gateway. Otherwise, believes that is authentic. then selects a random number and computes , , , and . sends the message to over a public channel.
- (3)
- Upon receiving the message from , checks the validity of the timestamp and computes , , , and . compares with the received value . If this condition is not satisfied, terminates this phase. Otherwise, believes that is a legitimate sensor node. then randomly selects another unique one-time pseudonym for ’s next login session and computes , , , and . Finally, sends the message to over a public channel and updates stored in its memory to for .
- (4)
- Upon receiving the message from , checks the validity of the timestamp and computes , , , and . then compares with the received value . If this condition is not verified, terminates this phase since fails to prove to be a legitimate home gateway. Otherwise, believes that is authentic and updates in to for the next session.
4.5. Password Change Phase
- (1)
- inserts own , inputs his/her , , and a new password and imprints his/her biometrics into a terminal.
- (2)
- computes , , , , , and . then compares with the stored . If this condition is not satisfied, terminates this phase. Otherwise, performs the next step.
- (3)
- computes , , and . replaces the stored values and with the newly computed values and , respectively. Finally, contains , where ℓ is the index of the next login.
5. Formal Security Analysis of the Proposed Scheme
5.1. Security Proof Using Random Oracle Model
| Algorithm 1 |
|
| Algorithm 2 |
|
5.2. Security Verification using BAN Logic
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- : :
- : :
- : :
- : :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- :
- According to , we get:
- According to and Rule 1, we get:
- According to and Rule 3, we get:
- According to , and Rule 2, we get:
- According to , we get:
- According to and Rule 1, we get:
- According to and Rule 3, we get:
- According to , and Rule 2, we get:
- According to , we get:
- According to and Rule 1, we get:
- According to and Rule 3, we get:
- According to , and Rule 2, we get:
- According to , we get:
- According to and Rule 1, we get:
- According to and Rule 3, we get:
- According to , and Rule 2, we get:
- As and combining , we get: (Goal 1)
- and combining , we get: (Goal 3)
- According to and Rule 4, we get: (Goal 2)
- According to and Rule 4, we get:
5.3. Security Verification Using AVISPA
5.3.1. HLPSL Specification of the Proposed Scheme
- Goal 1: The secrecy_of subs1 represents that are kept secret to () only.
- Goal 2: The secrecy_of subs2 represents that are kept secret to () only.
- Goal 3: The secrecy_of subs3 represents that are kept secret to () only.
- Goal 4: The secrecy_of subs4 represents the negotiated session key is only known to ().
- Goal 5: The secrecy_of subs5 represents that the secret key of is permanently kept secret, known to only ().
- Goal 6: The secrecy_of subs6 represents that the secret key of is permanently kept secret, known to only ().
- Goal 7: The secrecy_of subs7 represents that the shared secret is only known to ().
- Authentication Property 1: The authentication_on user_gateway_rri represents that generates . If securely receives through a message, it authenticates .
- Authentication Property 2: The authentication_on gateway_sensor_rrj represents that generates . If securely receives through a message, it authenticates .
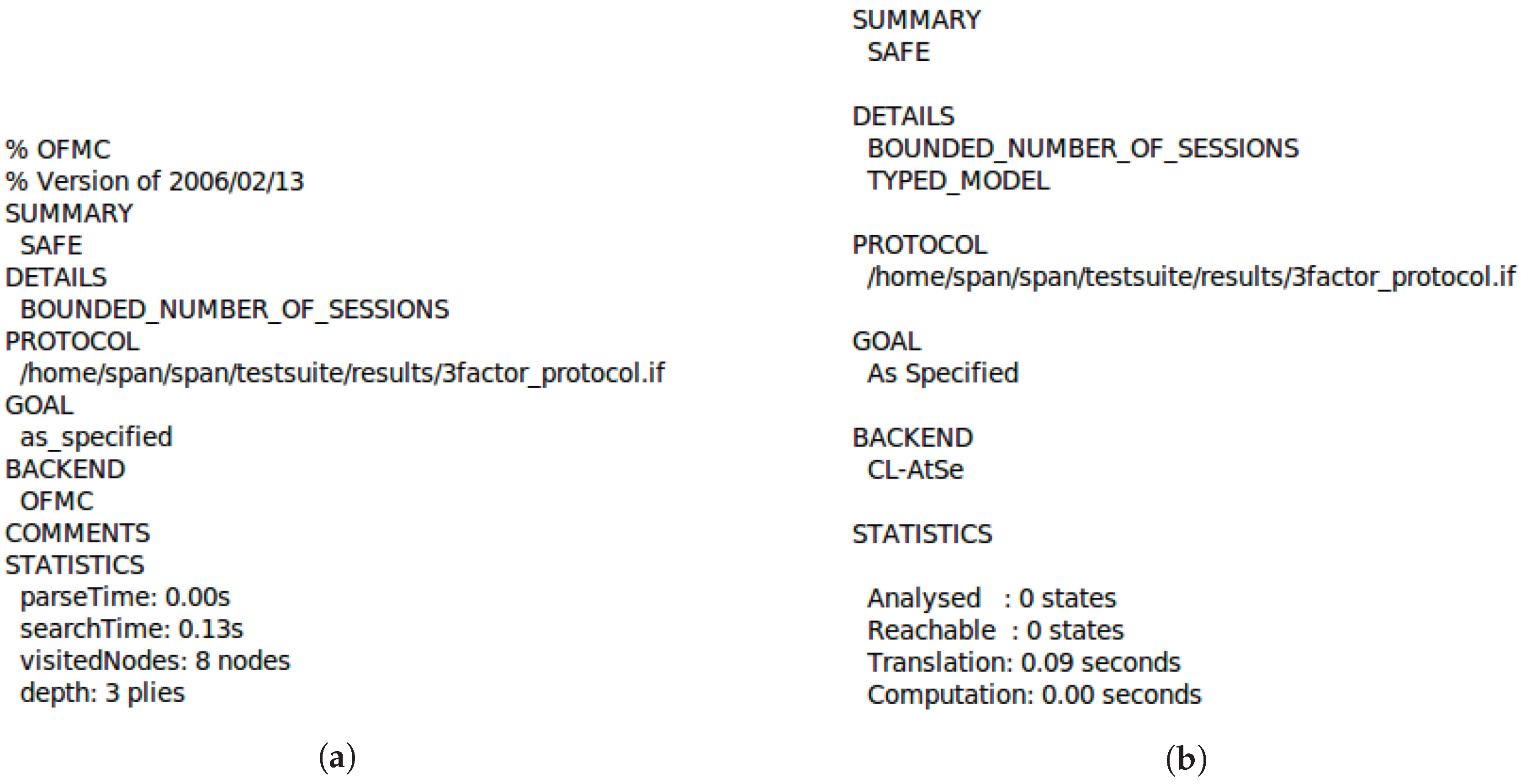
5.3.2. Simulation Results
6. Implication of Security Analysis
6.1. Security Properties
6.1.1. Mutual Authentication
6.1.2. Session Key Agreement
6.1.3. User Anonymity with Untraceability
6.1.4. Resisting Stolen Smart Card Attack
6.1.5. Resisting Offline Guessing Attack
6.1.6. Resisting Privileged Insider Attack
6.1.7. Resisting Stolen-Verifier Attack
6.1.8. Resisting Known Session-Specific Temporary Information Attack
6.1.9. Resisting User Impersonation Attack
6.1.10. Resisting Sensor Node Impersonation and Node Capture Attacks
6.2. Comparison of Security Features
7. Performance Analysis of the Proposed Scheme
7.1. Computational Cost Analysis
- : time for executing a one-way hash function
- : time for executing a biohash function
- : time for executing a fuzzy extractor
- : time for executing an ECC point multiplication
- : time for a modular exponentiation
7.2. Communication Cost Analysis
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Shih, C.S.; Chou, J.J.; Lin, K.J. WuKong: Secure Run-Time Environment and Data-Driven IoT Applications for Smart Cities and Smart Buildings. J. Internet Serv. Inf. Secur. 2018, 8, 1–17. [Google Scholar]
- Zion Market Research. Available online: https://www.zionmarketresearch.com/news/smart-home-market (accessed on 2 February 2019).
- Wong, K.H.M.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC’06), Taichung, Taiwan, 5–7 June 2006; Volume 1. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Vaidya, B.; Makrakis, D.; Mouftah, H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2012, 9, 171–183. [Google Scholar] [CrossRef]
- Kim, J.; Lee, D.; Jeon, W.; Lee, Y.; Won, D. Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks. Sensors 2014, 14, 6443–6462. [Google Scholar] [CrossRef] [PubMed]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Chang, I.P.; Lee, T.F.; Lin, T.H.; Liu, C.M. Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks. Sensors 2015, 15, 29841–29854. [Google Scholar] [CrossRef] [PubMed]
- Park, Y.; Park, Y. Three-Factor User Authentication and Key Agreement Using Elliptic Curve Cryptosystem in Wireless Sensor Networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Jung, J.; Moon, J.; Lee, D.; Won, D. Efficient and Security Enhanced Anonymous Authentication with Key Agreement Scheme in Wireless Sensor Networks. Sensors 2017, 17, 644. [Google Scholar] [CrossRef] [PubMed]
- Shin, S.; Kwon, T. Two-Factor Authenticated Key Agreement Supporting Unlinkability in 5G-Integrated Wireless Sensor Networks. IEEE Access 2018, 6, 11229–11241. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and Security Improvements of Two-Factor User Authentication in Wireless Sensor Networks. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Chen, T.H.; Shih, W.K. A Robust Mutual Authentication Protocol for Wireless Sensor Networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Huang, H.F.; Chang, Y.F.; Liu, C.H. Enhancement of Two-Factor User Authentication in Wireless Sensor Networks. In Proceedings of the 6th International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP’10), Darmstadt, Germany, 15–17 October 2010; pp. 27–30. [Google Scholar]
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An Enhanced Two-factor User Authentication Scheme in Wireless Sensor Networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Shin, S.; Kwon, T. Cryptanalysis of the Anonymous Authentication with Key Agreement Scheme in Wireless Sensor Networks. In Research Briefs on Information & Communication Technology Evolution (ReBICTE); ISYOU: Seoul, Korea, 2018; Volume 4. [Google Scholar]
- Das, A.K.; Goswami, A. A robust anonymous biometric-based remote user authentication scheme using smart cards. J.King Saud Univ. Comput. Inf. Sci. 2015, 27, 193–210. [Google Scholar] [CrossRef]
- Burnett, A.; Byrne, F.; Dowling, T.; Duffy, A. A Biometric Identity Based Signature Scheme. Int. J. Netw. Secur. 2007, 5, 317–326. [Google Scholar]
- Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-to-Peer Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Adavoudi-Jolfaei, A.; Ashouri-Talouki, M.; Aghili, S.F. Lightweight and anonymous three-factor authentication and access control scheme for real-time applications in wireless sensor networks. Peer-to-Peer Netw. Appl. 2017, 12, 43–59. [Google Scholar] [CrossRef]
- Rahman, M.S.; Nakamura, T.; Base, A.; Takasaki, H.; Kiyomoto, S. PPM: Privacy Policy Manager for Home Energy Management System. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2018, 9, 42–56. [Google Scholar]
- Jiang, Q.; Ma, J.; Wei, F.; Tian, Y.; Shen, J.; Yang, Y. An untraceable temporal-credential-based two-factor authentication scheme using ECC for wireless sensor networks. J. Netw. Comput. Appl. 2016, 76, 37–48. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A Logic of Authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- AVISPA (Automated Validation of Internet Security Protocols and Applications). Available online: http://www.avispa-project.org/ (accessed on 15 April 2019).
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA Tool for the Automated Validation of Internet Security Protocols and Applications. In Computer Aided Verification; Etessami, K., Rajamani, S.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential Power Analysis. In Advances in Cryptology, Proceedings of the CRYPTO’ 99; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Mahanta, H.J.; Azad, A.K.; Khan, A.K. Power analysis attack: A vulnerability to smart card security. In Proceedings of the 2015 International Conference on Signal Processing and Communication Engineering Systems, Guntur, India, 2–3 January 2015; pp. 506–510. [Google Scholar]
- SPAN a Security Protocol ANimator for AVISPA. Available online: http://people.irisa.fr/Thomas.Genet/span/ (accessed on 2 February 2019).
- Wang, D.; He, D.; Wang, P.; Chu, C. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals are Beyond Attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Certicom Research. Standards for Efficient Cryptography, SEC 2: Recommended Elliptic Curve Domain Parameters. Available online: http://www.secg.org/download/aid-784/sec2-v2.pdf (accessed on 5 March 2019).
- Wazid, M.; Das, A.K.; Kummari, S.; Li, X.; Wu, F. Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for TMIS. Secur. Commun. Netw. 2016, 9, 1983–2001. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.; Sherratt, R.S. Enhanced Three-factor Security Protocol for Consumer USB Mass Storage Devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar]
- Sankar, R.; Le, X.; Lee, S.; Wang, D. Protection of data confidentiality and patient privacy in medical sensor networks. In Implantable Sensor Systems for Medical Applications; Inmann, A., Hodgins, D., Eds.; Woodhead Publishing Series in Biomaterials; Woodhead Publishing: Sawston/Cambridge, UK, 2013; pp. 279–298. [Google Scholar]
- Seo, S.C.; Han, D.G.; Kim, H.C.; Hong, S. TinyECCK: Efficient Elliptic Curve Cryptography Implementation over GF(2M) on 8-Bit Micaz Mote. IEICE Trans. Inf. Syst. 2008, E91-D, 1338–1347. [Google Scholar] [CrossRef]



| Notation | Description | Notation | Description |
|---|---|---|---|
| Remote user | u | Random number of | |
| Sensor node | R | Random number | |
| Gateway node | K | Secret key generated by the | |
| Identity and password of | Session key | ||
| Biometric information of | Pseudo-random function of variable v with key k | ||
| Temporary identity of ’s next login | One-way hash function and biohash function | ||
| Identity of | Timestamp and the transmission delay time |
| Notation | Description | Notation | Description |
|---|---|---|---|
| Home Gateway | Smart card for | ||
| Temporary identity of | Session key | ||
| One-time pseudonym of for the l-th login | Fuzzy generator function | ||
| Secret key generated by the for users | Fuzzy reproduction function | ||
| Secret key generated by the for sensor nodes |
| Notation | Description | Notation | Description |
|---|---|---|---|
| P believes X | X is fresh | ||
| P sees X | K is the shared key between P and Q | ||
| P said X | X combined with the formula Y | ||
| P has jurisdiction over X | X hashed under the key K |
| Rule | Description |
|---|---|
| [Rule 1: Message-meaning rule] if P believes that the K is shared with Q and P sees X combined with K, then P believes Q said X | |
| [Rule 2: Nonce-verification rule] if P believes that X is fresh and P believes Q said X, then P believes that Q believes X | |
| [Rule 3: Freshness-conjuncation rule] if P believes that X is fresh, then P believes that is fresh | |
| [Rule 4: Jurisdiction rule] if P believes that X has jurisdiction over X and P believes that Q believes X, then P also believes X |
| 1: role user(Ui, HG, Sj: agent, SKey1: symmetric_key, SKey2: symmetric_key, |
| H, GEN, REP: hash_func, Snd, Rcv: channel(dy)) |
| 2: played_by Ui |
| 3: def= |
| 4: local State: nat, IDi, PWi, Bioi, BBi, Pari, TIDi, HPWi, HIDi, PID1i, Si, Ai, Bi, Ci, C1i, C2i, Di, RRi, RRj, Ri, |
| T1, T4: text, Mi, Muig, SKij, P2i, Mg, Mgui: message, |
| 5: Inc: hash_func |
| 6: const user_gateway, gateway_user, sensor_user, subs1, subs2, subs3, subs4, subs5, subs6, subs7: protocol_id |
| 7: init State :=0 |
| 8: transition |
| 9: 1. State = 0 ∧ Rcv(start) =|> |
| 10: State’ := 1 ∧ IDi’ := new() ∧ PWi’ := new() ∧ Si’ := new() ∧ BBi’ := GEN(Bioi) ∧ Pari’ := GEN(Bioi) |
| ∧ HPWi’ := H(PWi’.BBi’) ∧ TIDi’ := H(IDi’.Si’) ∧ Snd(TIDi’.HPWi’_SKey1) ∧ secret(IDi,PWi, subs1, Ui) |
| 11: 2. State = 1 ∧ Rcv({Ai’.Bi’.C1i’}_SKey1) =|> |
| 12: State’ := 2 ∧ Ri’ := new() ∧ T1’ := new() ∧ BBi’ := GEN(Bioi) ∧ Di’ := xor(ui,H(IDi.BBi’)) ∧ TIDi’ := H(IDi.ui) |
| ∧ HPWi’ := h(PWi.BBi’) ∧ Ai’ := xor(HIDi, H(HPWi’.TIDi’)) ∧ Bi’ := H(HPWi’.HIDi) |
| ∧ PID1i’ := xor(C1i’, H(TIDi’.HIDi)) ∧ RRi’ := H(TIDi’.PID1i’.Ri’) ∧ Mi’ := xor(Ri’, H(TIDi’.HIDi.T1’)) |
| ∧ Muig’ := H(TIDi’.HIDi.PID1i’.RRi’.T1’) |
| ∧ Snd(PID1i’.Mi’.Muig’.T1’) ∧ secret({TIDi,HIDi}, subs2, {Ui, HG}) ∧ witness(Ui, HG, user_gateway, RRi’) |
| 13: 3. State = 2 ∧ Rcv(P2i’.Mg’.Mgui’.T4’) =|> |
| 14: State’ := 3 ∧ RRj’ := xor(Mg’, H(PID1i.HIDi)) ∧ SKij’ := H(RRi.RRj’) |
| ∧ secret({RRi,RRj}, subs3, {Ui, HG, Sj}) ∧ secret({SKij}, subs4, {Ui, HG, Sj}) |
| 15: end role |
| 1: role gateway(Ui, HG, Sj: agent, SKey1: symmetric_key, SKey2: symmetric_key, |
| H, GEN, REP: hash_func, Snd, Rcv: channel(dy)) |
| 2: played_by HG |
| 3: def= |
| 4: local State: nat, Ku, Ks, TIDi, HPWi, PID1i, PID2i, HIDi, Ai, Bi, C1i, C2i, SIDj, Xsj, RRi, RRj, Ri, Rj, |
| T1, T2, T3, T4: text, Mi, Muig, Mg, Mg2, Mgsj, Mgui, Mj, Msjg, SKij, P2i: message, |
| 5: Inc: hash_fun |
| 6: const user_gateway, gateway_user, sensor_user, subs1, subs2, subs3, subs4, subs5, subs6, subs7: protocol_id |
| 7: init State :=0 |
| 8: transition |
| 9: 1. State = 0 ∧ Rcv({TIDi’.HPWi’}_SKey1) =|> |
| 10: State’ := 1 ∧ PID1i’ := new() ∧ HIDi’ := H(TIDi’.Ku) ∧ Ai’ := xor(HIDi’, H(HPWi’.TIDi’)) |
| ∧ Bi’ := H(HPWi’.HIDi’) ∧ C1i’ := xor(PID1i’, H(TIDi’.HIDi’)) ∧ Snd({Ai’.Bi’.C1i’}_SKey1) |
| ∧ SIDj’ := new() ∧ Xsj’ := H(SIDj’.Ks) |
| ∧ Snd({SIDj’.Xsj’}_SKey2) ∧ secret(Ku, subs5, HG) ∧ secret(Ks, subs6, HG) ∧ secret(Xsj, subs7, HG, Sj) |
| 11: 2. State = 1 ∧ Rcv(PID1i’.Mi’.Muig’.T1’) =|> |
| 12: State’ := 2 ∧ HIDi’ := H(TIDi.Ku) ∧ Ri’ := xor(Mi’, H(TIDi.HIDi’.T1’)) ∧ RRi’ := H(TIDi.PID1i.Ri’) |
| ∧ T2’ := new() ∧ Xsj’ := H(SIDj.Ks) ∧ Mg2’ := xor(RRi’, H(Xsj’.T2’)) ∧ Mgsj’ := H(PID1i’.SIDj.Xsj’.RRi’.T2’) |
| ∧ Snd(PID1i’.Mg2’.Mgsj’.T2’) |
| 13: 3. State = 2 ∧ Rcv(Mj’.Msjg’.T3’) =|> |
| 14: State’ := 3 ∧ Rj’ := xor(Mj’, H(Xsj.T3’)) ∧ RRj’ := H(SIDj.Rj’) ∧ SKij’ := H(RRi.RRj’) ∧ PID2i’ := new() |
| ∧ T4’ := new() ∧ C2i’ := xor(PID2i’, H(TIDi.HIDi)) ∧ P2i’ := xor(C2i’, H(HIDi.T4’)) |
| ∧ Mg’ := xor(RRj’, H(PID1i.HIDi)) ∧ Mgui’ := H(PID1i.HIDi.C2i’.RRj’.SKij’.T4’) |
| ∧ Snd(P2i’.Mg’.Mgui’.T4’) |
| 15: end role |
| 1: role sensor(Ui, HG, Sj: agent, SKey1: symmetric_key, SKey2: symmetric_key, |
| H, GEN, REP: hash_func, Snd, Rcv: channel(dy)) |
| 2: played_by Sj |
| 3: def= |
| 4: local State: nat, PID1i, SIDj, Xsj, RRi, RRj, Rj, T2, T3: text, Mg2, Mgsj, Mgui, Mj, Msjg, SKij: message, |
| 5: Inc: hash_func |
| 6: const user_gateway, gateway_sensor, sensor_user, subs1, subs2, subs3, subs4, subs5, subs6, subs7: protocol_id |
| 7: init State :=0 |
| 8: transition |
| 9: 1. State = 0 ∧ Rcv({SIDj’.Xsj’}_SKey2) =|> |
| 10: State’ := 1 ∧ T3’ := new() |
| 11: 2. State = 1 ∧ Rcv(PID1i’.Mg2’.Mgsj’.T2’) =|> |
| 12: State’ := 2 ∧ RRi’ := xor(Mg2’, H(Xsj.T2’)) ∧ Rj’ := new() ∧ T3’ := new() ∧ RRj’ := H(SIDj.Rj’) |
| ∧ Mj’ := xor(Rj’, H(Xsj.T3’)) ∧ SKij’ := H(RRi’.RRj’) ∧ Msjg’ := H(PID1i’.SIDj.Xsj.Rj’.SKij’.T3’) |
| ∧ Snd(Mj’.Msjg’.T3’) ∧ witness(Sj, HG, gateway_sensor, RRj’) |
| 13: end role |
| 1: role session(Ui, HG, Sj:agent, SKey1: symmetric_key, SKey2: symmetric_key, |
| H, GEN, REP: hash_func) |
| 2: def= |
| 3: local SI, SJ, RI, RJ, PI, PJ: channel(dy) |
| 4: composition |
| 5: user(Ui, HG, Sj, SKey1, SKey2, H, GEN, REP, SI, RI) |
| 6: ∧ gateway(Ui, HG, Sj, SKey1, SKey2, H, GEN, REP, SJ, RJ) |
| 7: ∧ sensor(Ui, HG, Sj, SKey1, SKey2, H, GEN, REP, PI, PJ) |
| 8: end role |
| 1: role environment() |
| 2: def= |
| 3: const ui, hg, sj: agent, skey1 : symmetric_key, skey2 : symmetric_key, h, gen, rep: hash_func, |
| 4: idi, bioi, sidj, pwi, ai, bi, ci, t1, t2, t3, t4, rri, rrj, skij, mi, mj, mg, mg2, muig, mgui, mgsj, msjg: text, |
| 5: user_gateway_rri, gateway_sensor_rrj, sensor_user, |
| 6: subs1, subs2, subs3, subs4, subs5, subs6, subs7: protocol_id |
| 7: intruder_knowledge = ui, hg, sj, h, gen, rep, mi, muig, mg2, mgsj, mj, msjg, mg, mgui |
| 8: composition |
| 9: session(hg, ui, sj, skey1, skey2, h, gen, rep) |
| 10: ∧ session(ui, hg, sj, skey1, skey2, h, gen, rep) |
| 11: ∧ session(sj, ui, hg, skey1, skey2, h, gen, rep) |
| 12: end role |
| 1: goal |
| 2: secrecy_of subs1 secrecy_of subs2 secrecy_of subs3 secrecy_of subs4 |
| 3: secrecy_of subs5 secrecy_of subs6 secrecy_of subs7 |
| 4: authentication_on user_gateway_rri authentication_on gateway_sensor_rrj 5: end goal |
| environment() |
| Security Feature | Amin et al. [11] | Park et al. [9] | Jung et al. [13] | Jiang et al. [12] | Proposed Scheme |
|---|---|---|---|---|---|
| Mutual authentication | O | O | O | O | O |
| Session key security | O | O | X | O | O |
| User anonymity | O | O | O | O | O |
| Untraceability | X | X | X | O | O |
| Resistance to | |||||
| Stolen smart card attack | X | O | X | O | O |
| Offline guessing attack | O | O | O | O | O |
| Privileged insider attack | O | O | O | O | O |
| Stolen-verifier attack | O | X | O | O | O |
| Known session-specific | X | O | O | O | O |
| temporary information attack | |||||
| User impersonation attack | O | O | X | O | O |
| Sensor node | O | O | O | O | O |
| impersonation attack |
| Entity | Amin et al. [11] | Park et al. [9] | Jung et al. [13] | Jiang et al. [12] | Proposed Scheme |
|---|---|---|---|---|---|
| User | |||||
| Gateway node | |||||
| Sensor node | |||||
| Total cost | |||||
| Total running time | ms | ms | ms | ms | ms |
| Communication | Amin et al. [11] | Park et al. [9] | Jung et al. [13] | Jiang et al. [12] | Proposed Scheme |
|---|---|---|---|---|---|
| User→Gateway node | 768 bits (6) | 1536 bits (5) | 512 bits (4) | 1408 bits (4) | 512 bits (4) |
| Gateway node→Sensor node | 640 bits (5) | 1408 bits (4) | 512 bits (4) | 640 bits (5) | 512 bits (4) |
| Sensor node→Gateway node | 384 bits (3) | 1280 bits (3) | 256 bits (2) | 384 bits (3) | 384 bits (3) |
| Gateway node→User | 384 bits (3) | 1408 bits (4) | 384 bits (3) | 256 bits (2) | 512 bits (4) |
| Total | 2176 bits | 5632 bits | 1664 bits | 2688 bits | 1920 bits |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shin, S.; Kwon, T. A Lightweight Three-Factor Authentication and Key Agreement Scheme in Wireless Sensor Networks for Smart Homes. Sensors 2019, 19, 2012. https://doi.org/10.3390/s19092012
Shin S, Kwon T. A Lightweight Three-Factor Authentication and Key Agreement Scheme in Wireless Sensor Networks for Smart Homes. Sensors. 2019; 19(9):2012. https://doi.org/10.3390/s19092012
Chicago/Turabian StyleShin, Sooyeon, and Taekyoung Kwon. 2019. "A Lightweight Three-Factor Authentication and Key Agreement Scheme in Wireless Sensor Networks for Smart Homes" Sensors 19, no. 9: 2012. https://doi.org/10.3390/s19092012





