1. Introduction
Advances in wireless sensor networks (WSNs) technology enable a number of emerging applications that were not even thought years ago. WSNs are composed of small components, denominated “sensor nodes”, which work cooperatively to achieve the desired functionalities of environmental/event surveillance or monitoring. They are in general dense networks and the sensor nodes are randomly deployed in the environment. This characteristic gives them high robustness, since alternative redundant communication paths are provided by the number of sensor nodes that cover a common area [
1]. Sensor nodes are expected to operate for a long time without human intervention, hence all the actions must be taken in the most energy-efficient fashion. This is the first concern while developing software for WSN, including networking protocols.
The main strategy to save energy and extend network lifetime is to reduce radio usage, since it is the main energy consumer of a sensor node. The amount of data transferred between nodes is very small in WSNs, then the radios are off almost all the time and are turned on for small intervals to receive and transmit data only. Some position estimation algorithm is employed in order to the nodes estimate their relative position, so that a geographic routing protocol can be used. This approach reduces the coordination effort to maintain updated knowledge of the network topology [
2]. Medium access control (MAC) layer protocols manage the duty-cycling [
3] of nodes, switching its state from sleep to awake and back to sleep. Duty-cycle is small (<10%) since the sleep state is very longer than awake state. All actions, measurements, processing, and communication, are made during the small awake state. Normally all the nodes in the network adopt the same duty-cycle, but synchronization is not always required. The use of duty-cycles increases the latency per hop due to the sleep-delay problem. A node that is going to send a message towards a destination must wait until the relay node (i.e., the next-hop node) is awake before sending the message [
4]. Some authors propose to stagger the wake up time of nodes in the path towards destination as strategy to overcome the sleep-delay problem [
5,
6,
7,
8,
9,
10,
11,
12]. Even though this is the most effective method to reduce the end-to-end latency in duty-cycled WSN, all the proposals face the difficulty to keep synchronism among the sensor nodes.
Another approach to mitigate the sleep-delay problem is the use of anycast protocols. Anycast is a communication pattern which exploits path redundancy available in dense wireless networks [
4,
13,
14,
15]. Normally, anycast based MACs interact with routing protocols, in a cross-layer approach. Decisions about the next relay in the route towards the destination node are taken considering information from both layers. The cross-layer design explores the possibility to retrieve and/or change parameters of two or more layers in order to achieve an optimization objective [
1,
16,
17]. Anycast protocols normally unify functionalities of asynchronous MAC, as X-MAC [
3], with a geographic routing protocol, as presented in [
4,
18]. The final decision about the next node to relay a data packet is taken in MAC layer. Among the nodes targeted in anycast communication, the first one to wake up and respond to the preamble is elected the next relay.
This work proposes PAX-MAC, Preamble ahead cross-layer MAC protocol. This asynchronous protocol employs some strategies to reduce end-to-end latency in duty-cycled WSNs. Anycast communication pattern reduces the time needed to achieve rendezvous with a next relay node. Preambles propagate ahead separated from data, in such a way that both packets advance in distinct points of the path towards destination, simultaneously. Preambles establish communication between relay nodes and stagger their wake up times in order to speed up data propagation. Differently from state-of-the-art approaches, PAX-MAC does not require energy to keep synchronism as [
6,
19,
20], and, at the same time, it is not restricted to one direction traffic as [
8] nor to burst traffic as [
7]. PAX-MAC achieves similar latency of a network without duty-cycling, maintaining the energy profile of protocols that use sleep/awake cycles. This is accomplished without any costly inter-node synchronization.
The seminal ideas of this protocol were first introduced in [
21]. The published article was an incomplete initial proposal since parameters of the protocol were selected empirically, collisions were not handled properly and the evaluation performed was not extensive. In the current article, a novel mathematical model to support optimal protocol parameters decision was introduced. In addition, a mechanism to handle possible collisions between packets of different transmission flows is also included. A much more extensive assessment of our protocol was accomplished, demonstrating its superior performance when compared to state-of-the-art. The results were obtained in scenarios with single transmission and environments with multiple concurrent data flows.
Besides this introduction, the rest of this paper is organized:
Section 2 discusses related works, presenting an extended literature review that provides the reader with a consistent base for comparisons.
Section 3 exposes the principles of Anycast Asynchronous MAC. The protocol is presented in
Section 4.
Section 5 provides details of the mathematical model describing the rationale behind PAX-MAC proposal.
Section 6 presents the experiments performed by means of simulations and the acquired results. Conclusions and discussions of future works are presented in
Section 7.
2. Related Work
In WSNs, communication between a source (S) and a destination (D) node is normally realized by multi-hop due to the limited transmission range, requiring a routing mechanism. In this process, several relay nodes are responsible to receive and send data packets further. This task must be executed with a reduced energy cost.
Medium access and routing protocols are at the core of multi-hop communication. Enhancements in energy efficiency of these two protocols may enlarge the life-time of a sensor network considerably. MAC protocols have to coordinate access to the medium maintaining very low energy consumption. On its turn, network protocols aim at reducing the communication latency in low power WSNs.
According to [
22,
23] there are two main approaches to develop MAC protocols for WSNs: contention-based and reservation-based approaches. Reservation-based approaches (like time division multiple access - TDMA - protocols) is less attractive due to its strict synchronization requirements, demanding large overhead and restricting its scalability. Contention-based MAC protocols can be divided in asynchronous, represented by the canonical Berkely-MAC (B-MAC) [
24], and those with common active period, as the canonical sensor-MAC (S-MAC) [
25].
In order to save energy, sensor nodes remain in low energy consumption state, called sleep mode, most of the time (>90%). The sensor nodes are periodically reactivated (awake) to perform data acquisition, computations and data communication during a short slot of time and then return to the low power (sleep) mode. MAC protocols are responsible to control this duty-cycled operation. In common active period approaches, a loose synchronization is required, so that all the nodes in the network wake up almost at the same time to execute those tasks before going back to sleep. With asynchronous protocols, all the nodes use the same duty-cycle, with the same sleep and awake intervals, but the wake-up times of the nodes are independent from each other. The awake interval is very shorter compared to the previous approach, which results in lower energy consumption in asynchronous networks. On the other hand, the MAC layer must have a mechanism to establish communication between nodes.
The usage of duty-cycles is the best way to save energy and enlarge lifetime [
5,
26] of whole WSN. On the other hand, it increases end-to-end latency due to sleep-delay [
11]. When a sensor node has a message to transmit, it must wait until the receiver stays awake and ready to receive. Several duty-cycled MAC protocols were proposed aiming to achieve minimal delays and high energy efficiency. Staggering the awake times of all nodes along the path towards destination is the best choice to reduce sleep-delay [
5,
6,
7,
8,
9,
10,
11,
12,
19,
20]. In this way, data can be forwarded in a pipelined fashion, coordinating the waiting time of all nodes in the path towards destination. In DMAC [
8] nodes do not keep a common sleep/awake scale as in S-MAC, but use a staggered wake-up schedule in the sink’s direction. The nodes closer to the sink (downstream) wake up a bit later than the nodes more distant (upstream). ADC-MAC [
12] and Joint Routing and MAC Protocol (JRAM) [
11] were inspired in DMAC. ADC-MAC is adaptable to traffic and distance to sink node by configuring the duty-cycle. JRAM is a protocol designed to support multiple sink nodes and keeps its synchronism using a special packet
SYNC as the S-MAC. Express-MAC (EX-MAC) [
7] is an asynchronous duty-cycled protocol designed for event detection applications. Differently from DMAC, it does not maintain synchronization between nodes. Transmitter nodes with EX-MAC send a preamble signal in order to achieve rendezvous with a targeted receiver, in a similar manner of B-MAC. EX-MAC sends a sequence of strobed short preambles as those encountered in X-MAC [
3] protocol.
EX-MAC was designed for WSNs dedicated to detecting events. Such networks remain inactive most of the time and have high activity periods when events of interest occur and messages are sent towards the sink. The first event message propagates towards the sink node in the same way of the asynchronous X-MAC, with a small difference, EX-MAC staggers the awake times of the nodes involved in the event report. When subsequent events are detected, communication latency is drastically reduced due to the alignment of the sensor nodes that are at the transmission path, as well as DMAC. The latency reduction occurs only in the transmission of burst events.
Some novel MAC protocols were inspired in EX-MAC. DuoMAC [
5] is a protocol adaptable to the type of traffic (real-time and non real-time). When the traffic is non real-time, its behavior mimics X-MAC protocol with a low duty-cycle. For real-time traffic, high duty-cycle with pipelined fashion transmissions is employed. RM-MAC [
10] is an asynchronous received initiated approach adaptable to the traffic pattern. When transmissions are frequent, the nodes are staggered and transmissions are made in pipeline as EX-MAC.
Another strategy to reduce sleep-delay in duty-cycled WSNs is to separate data from control messages. Control messages, as preambles and RTS (Request To Send), are transmitted ahead, in order to establish communication and reserve the channel for data transmission. RMAC - Routing-Enhanced MAC [
6] keeps a common scale of sleep/awake, in the same way of S-MAC [
25]. Differently from S-MAC, RMAC sends data messages separately from control messages. During the awake period, PION (PIONeer control frame) messages are sent several hops ahead. The communication channel is reserved for data transmission during the common sleep period. In the sleep time, only those nodes that will participate in the communication wake up in the scheduled time to receive and send data. Experimental results from performed simulations presented a 6-times reduction in the latency of RMAC compared to S-MAC. RMAC inspired other proposals, as those presented in [
19,
20].
Increased energy savings have been obtained with cross-layered WSNs. In the cross-layer approach, decisions about the way each layer will behave are taken jointly, though considering information coming from other layers [
1]. A great number of cross-layer proposals have been dedicated to the interaction of network (NET), medium access (MAC) and physical (PHY) layers [
5,
9,
10,
11,
12,
16,
17]. Interactions between a geographical routing (NET) with a preamble-based MAC protocols result in a special cross-layer group denominated anycast [
4,
13,
14,
27,
28,
29].
Anycast protocols take advantage of the path redundancy, i.e., multiple next-hop candidate nodes available in the network. Differently from the traditional unicast protocols, there is no unique choice of a relay node, but a subset of neighbors, denominated forwarding candidate set (FCS), with appropriate conditions to forward a message, as depicted in
Figure 1. In this example, FCS has two members, represented by gray circles. Sender node starts to transmit a series of short preambles, in the same way of X-MAC [
3]. The first FCS member that wakes up replies to the preamble packet and assumes the relay function. Therefore, communication is established more quickly, reducing the latency caused by sleep-delay.
GeRaF (Geographic Random Forwarding) [
29] was a pioneer anycast protocol aiming at reducing the latency in asynchronous protocols using probing. Sender node considers as FCS members all neighbors that give to the message advancement towards destination node. If node
a is the sender in
Figure 1, the neighbors
c,
d,
e,
f and
g will compose its FCS. Members closer to destination (
D) are given higher priority to forward data message.
Convergent MAC (CMAC) [
28] is an improvement of GeRaF. CMAC defines a minimum advancement required (
) as a criteria to select the members of FCS. The neighbors of the sender that do not provide an advancement towards the destination greater than
, are not allowed to reply to the preamble, even though one of them wakes up before a FCS member.
Figure 1 can represent a network using CMAC with
defined as
of radio range. If node
a is the sender, then only neighbors
c ad
d will take part in FCS. The authors consider negligible the length of data packets.
Restricting the number of members in FCS, with CMAC, the sender would take a longer time to receive an answer to the preambles than it would take with GeRaF, but the advancement of the data packet would be larger, since only neighbors closer to destination (D) are allowed to forward messages. The selection of , in CMAC, depends on traffic load and the network density. Data length is not taken into account. If the traffic is heavy, the is reduced in order to include more nodes in the FCS and reduce the advance time.
Another cross-layer protocol inspired in GeRaF is AGA-MAC (Adaptive Geographic Anycast Medium Access Control) [
18]. Following the same principle of CMAC, a threshold in the advancement towards the destination is imposed. In AGA-MAC, this threshold depends on data length. If data payload is short, threshold is reduced in order to reduce advance time. If data payload is long, threshold is enlarged in order to reduce the hops necessary to reach destination. This was the first paper addressing the influence of data packet length in the latency of WSNs that use anycast protocols. The authors demonstrated that there is an optimum threshold value for each data packet length that provides the smallest latency in the network.
A cross-layer proposal called Any-MAC (Anycast MAC) [
4] considers existing NET and MAC protocols with small modifications in both of them. Only asynchronous MAC protocols are considered. Any-MACs of the probe-based type use MAC protocols that perform periodic channel sampling to identify transmissions in the neighborhood as the X-MAC [
3]. Hybrid asynchronous protocols use both wake-up schedule exchange and probing. The latency reduction is obtained following the same opportunistic routing principle used by GeRaF [
29]. The FCS is determined in the sender’s network layer according to the calculated routing cost for each neighbor. The network layer informs the FCS to the MAC layer. The first FCS member that replies to the sender signal is elected the next-hop node. A greater number of FCS members results in a lower average time to data packets to proceed forwarding. However, as negative effect, there is an increment in the chance of collisions in sending answer signals when two or more FCS members wake up in time to listen and reply to the preamble. The authors present simulation results for the probe-based Any-MAC using an extension of the X-MAC protocol with two and three members in FCS. An average latency reduction of
was obtained by Any-MAC in comparison to the X-MAC protocol.
The proposed PAX-MAC belongs to the group of anycast protocols following the principle of opportunistic routing as GeRaF. Besides that, PAX-MAC incorporates the staggering method to perform fast data packet transmission and the advanced sending of preambles used by RMAC. The result is a cross-layer protocol involving routing and MAC for duty-cycled asynchronous WSNs with enhanced efficiency compared to the previous approaches. Our protocol presents low latency results, close to networks without duty-cycles for a diverse data packet lengths.
3. Anycast Asynchronous MAC
The anycast strategy is employed in asynchronous MAC protocols in order to reduce the sleep-delay caused by the independent sleep/awake cycles of each node. This class of protocols combines MAC layer and Network layer functions, exploring concepts of geographical routing combined with a preamble sampling strategy to ensure that a receiver will be awake in order to receive data. The concept of anycast is to explore the inherent redundancy in the network, i.e., multiple next-hop candidate nodes available in the network, reducing sleep-latency. Differently from unicast, this is accomplished by opportunistically forwarding data packets to a next hop selected from a group of possible relays (forwarding candidate set (FCS)), as depicted in
Figure 1. Nodes have no information about wake-up schedules of the neighbors.
In an anycast asynchronous MAC, a sensor node with data to transmit first sends a series of short preambles in order to rendezvous with an awakening relay. After each preamble the sender settles the radio in the reception mode and waits during an interval for an answer. Neighboring nodes are performing the sleep/awake cycles, i.e., they only wake up and check whether the channel is busy. Occasionally, a member of the FCS will wake up and notice the presence of a preamble in the channel. This node answers to the preamble with an early-acknowledgment (eACK) signal in order to interrupt the preambles sequence and establish communication.
Design decisions of an anycast protocol are the FCS cardinality, its selection criteria and the definition of which node is responsible for the choice. The FCS cardinality has consequences in the end-to-end latency of a packet. A higher number of nodes in the FCS leads to, on average, smaller response times, reducing the one-hop latency. Nevertheless, the average size of the hop is reduced, increasing the number of hops spent to route the message to destination, which may increase the total latency. For different packet sizes and network densities, an optimal FCS cardinality can be employed to accomplish the minimal total latency. This phenomenon was studied in our previous work [
18].
The criteria to select the FCS members is related to, for example, distance to final destination, battery residual energy and node connectivity. Most anycast asynchronous MAC employ as selection metric the advancement towards destination, i.e., how much closer to destination the next relay is.
The decision whether a given node is included in the FCS may be realized in the sender or receiver side. When the sender is responsible to select this group, it must know the position and other relevant state information from the neighboring nodes (as in [
4,
14,
15,
30]). Based on that, the FCS members are selected and their identifiers are informed in the preamble messages. When the decision is taken in the receiver side, the sender transmits in the preamble the necessary parameters to support the decision process. Each potential next-hop decides whether it is candidate to relay the packet or not based on the received information (as in [
1,
27,
28,
29]).
4. The PAX-MAC Protocol
In this section, our novel protocol is presented in details. The cross-layer nature of PAX-MAC comes from the interaction of network and MAC layers. Final routing decisions are taken in MAC layer, according to parameters provided by NET layer and current local conditions of WSN.
4.1. Overview
PAX-MAC combines a geographical routing with an anycast based protocol. Geographical routing means that a packet is relayed based on the position of the nodes, being a stateless protocol. An example of geographical routing is the GPSR (Greedy Perimeter Stateless Routing) [
31], where, in greedy mode, the node nearest to the destination is chosen as next hop. Since our protocol is anycast, the next relay is selected from a set of candidates (FCS). This set is comprised by nodes which gave the greatest advancement towards destination. For that, the relay node is aware of neighboring positions. In the case of PAX-MAC, the destination is not a specific node ID but the node that is nearest to a given destination position. For the sake of simplicity, in this paper, we will call this node as destination
D.
An example of application suitable to our protocol is the control of a oil refinement station. Lets suppose that wireless sensors are installed on the pipes, in order to detect liquid leaks. Instead of each sensor sending the flow information to a central control, in order to calculate whether the inflow from various pipes sum up and check with the outflow, nodes can exchange information themselves in order to detect pipe leaks and raise an alarm when necessary. In this manner, a node positioned in a outflow pipe may send messages to input positions, to verify updated flows. The nodes nearest to these positions can answer the request, and for that they can use the position provided by the initiator of the procedure. Fast responses are important in such an environment.
Since time is a concern to many applications, the main goal of PAX-MAC is to reduce the high latency present in duty-cycled WSNs caused by sleep-delay. In order to save energy, all the nodes in the network adopt the same cycle interval, but their awake times are not synchronized. When a sender node has a message to transmit, it starts sending a series of short preambles to rendezvous with a relay node. Sender node interleaves the preambles with short hearing intervals to wait for an eACK packet. Besides the use of anycast communication pattern, PAX-MAC manages to further reduce the latency transmitting data packet separately from the preambles.
Differently from other anycast protocols, PAX-MAC does not send data just after receiving the eACK signal. Preamble packet is propagated ahead by relay nodes and is used as a way to perform channel reservation for data transmission. Data transmission is started only a predefined interval after the preamble. The idea of PAX-MAC is to send the preambles ahead in order to wake up the relay nodes and to reserve the communication channel for the time when data packets will be sent. Preambles carry the information about the time in which the data will be transmitted from one relay to the next. This time is incremented by a data transmission time each hop. This way, the preambles stagger the time the relays will wake up in order to transmit data. At the same time of data transmission, preambles are scheduling the next relays some hops ahead. This process is denominated split phase transmission.
In the first phase, preambles propagate asynchronously hop-by-hop, while in second phase, data travels through the established route in a synchronous form. Preamble propagation speed is not constant, even though its average speed is made equal to data propagation speed. Therefore, it is possible that data transmissions take place close to preambles, occurring a packet collision. To avoid collisions between preamble and data packets, source node must separate the transmissions of these packets by a suitable amount of time. This is accomplished by an initial delay before sending data. This time should be long enough in order to avoid collisions between data and preamble in a given node in the path, but it should not be too long, otherwise it would increase the overall latency.
As already presented,
Figure 1 outlines a sample transmission of an anycast protocol. In PAX-MAC context, the split phase transmission process can be exemplified by this Figure combined with
Figure 2. In our example, the source node
S sends a data packet to a destination
D. The transmission is depicted partially by both Figures (four hops). In this example, FCS cardinality employed was two. The packet received from upper layer engenders the transmission of a series of preambles in the source node, interleaved with listening periods for
eACK reception. PAX-MAC does not define a special
eACK packet as CMAC [
28] and X-MAC [
3]. When a FCS member wakes up and receives a preamble, it starts to send its own series in order to probe for the next hop. The first of these preambles is understood by the sender as an
eACK signal, making it stop transmissions.
The FCS of the source node
S comprises nodes
a and
b (
Figure 1). The time line presented in
Figure 2 shows that, after
S started to send the series of preambles, node
a woke up in
. This is before node
b, which would wake up at
. In an anycast protocol such as PAX-MAC, the first node from the FCS which receives the preamble assumes the role of next relay towards destination
D. Immediately, it begins to send a new series of preambles in order to signal its intention to transmit to a relay node of its own FCS (nodes
c and
d). The first preamble also acts as
eACK for node
S. At the same time, node
a is scheduled to wake up immediately before the source node
S starts to send data, in the future.
This process continues as presented in
Figure 1. Node
d becomes the next relay, after node
a, as soon as it wakes up earlier than node
c. Due to the asynchronous nature of our MAC protocol, the number of preambles spent in each hop to achieve rendezvous with the next relay may vary, as presented in
Figure 2. In the sequence, node
d starts to send preambles and programs its time to receive data packet. As explained, the first preamble is used as
eACK in node
a. After three preambles, node
i wakes up and assumes the role of the next relay, starting its own preamble sequence. While node
i is transmitting its preambles, node
S undertakes the transmission of data packet to node
a, which has just woken up to receive data. From here on, a simultaneous transmission of packet and preambles takes place. It is important to remark that these communications do not interfere with each other, in view of the distance held between the two transmitting nodes. Care is taken by the source node to delay data packet delivery by a time long enough to ensure its transmission takes place in a region far from preambles, with a distance larger than two times the radio range. The process of sending preambles ahead and data packet some hops behind continues until reaching destination node
D.
It is important to note that we are not considering collisions of other data transmissions, we analyze the behavior of just one data sending at a time. We consider that all sender nodes encounter at least one neighbor to forward the packet in destination direction. If this condition fails, another algorithms must be used, as the right-hand rule [
31].
In order to avoid collisions between both the packets, the propagation speed of preambles must be, on average, at least the same of data. The average time necessary to find an awake node among the selected set is adjusted accordingly with FCS cardinality. Thus, the number of FCS members depends on data packet size, such that, the smaller is data size, the larger is FCS cardinality. The average distance between the node sending data packet and the one transmitting the series of preambles is constant. Our protocol identifies imminent collisions due to deviations in preamble speed and manages to avoid them.
4.2. FCS Selection
PAX-MAC uses anycast communication pattern to speed up preamble advancement. If a small data packet has to be transmitted, more nodes must be included in FCS to reduce the mean time spent to establish preamble communication between the sender node and the next relay node. In other words, FCS cardinality has to be adjusted so that the average speed of preamble propagation will be at least the same as the data packet. Among the nodes that promote any advancement towards the destination, the best choices to compose FCS are those that can provide the greatest advancement. This guidance will reduce the total number of hops to reach the destination. As a consequence, less energy will be spent in this data transmission. The average preamble propagation speed is closely related to the number
r of preambles sent until the sender node receives an
eACK, which depends on
v, the number of FCS members, as demonstrated by Equation (
1):
is the maximum number of preambles to be sent in a cycle time. In our protocol, the time to transmit these preambles must be less or equal than the data packet transmission time. Then, Equation (
1) can be used to obtain FCS cardinality in order to fit the average number of preambles (
).
In our protocol, the decision to include nodes in the FCS is taken in the sender side. So, during each hop, the sender is aware of its own position, its neighbors’ positions and the position of the destination. Then, the sender will determine which neighbors will take part of the FCS. This information will be included in the preambles that will be sent. Only members of the FCS are allowed to answer with an eACK upon preamble reception.
4.3. Imminent Collision
A collision occurs when two or more radio messages sent in the same communication channel reach a receiver node, resulting in signal jamming. As a consequence, the receiving node can not decode any of the messages. For example, in
Figure 2, if node
i had waken up later than
and node
d would have to send 3 more preambles, a collision would occur in node
a, since it would hear the preamble from node
d while it was receiving data packet from source node
S. PAX-MAC employs two mechanisms to avoid collision. The first one is the delayed delivery of data packet, in order to maintain a secure distance between the regions where both messages, data and preambles, take place. The second one is “imminent collision” detection. The node transmitting preambles can identify when a collision is about to happen.
PAX-MAC proposes the identification of this imminent collision and a mechanism to handle it so that it can be avoided. The current relay node, when sending preamble in order to contact the next relay, is aware of the data packet schedule of the previous relay nodes. When an imminent collision is identified, i.e., the current relay perceives that the next preamble to be sent is about to collide with the data coming from the previous relay, it suspends the preamble transmission. The current relay will wait for the data reception and only then it restarts preamble transmissions, acting as the source node (the first sender).
Following the previous example, consider node d is sending preambles when source node S is about to start sending data to node a. In this case, node d ceases the transmissions and waits until it receives the data packet from node a. So, node d must wait for a time corresponding to two data transmission intervals. After receiving data packet, node d starts to send preambles, and schedules the data release time based on the waiting time (), in the same way of the source node S.
The smaller the waiting time (in the source node), the shorter is the latency. However, smaller waiting times increase the chance of an imminent collision event. As a consequence, the overhead of restarting the transmission process increases the latency. The challenge then is to find the optimum waiting time in the source node.
The optimum waiting time is calculated in
Section 6.2.1. This is the average number of hops separating preambles and data, which is expected to be less than ten. The node sending preambles must consider a guard interval to detect imminent collisions, in order to compensate the clock drift. low-power clocks employ 32 kHz tuning fork crystals, which are susceptible to significant drift over the industrial temperature range
to
. Its drift can reach values as low as −200 ppm (parts per million) [
32]. It means that in the worst case, the guard interval can reach
, or
of the interval needed to transmit a data packet. If a temperature compensated resonator is used, a clock drift of ±50 ppm is verified, resulting in a lower guard interval.
4.4. Protocol State Machine
This section describes the state machine of PAX-MAC protocol as illustrated in
Figure 3.
Table 1 and
Table 2 respectively present the meanings of the states and of the transitions.
Most of the time, when there is not any message being transmitted in the network, nodes repeat sleep/awake cycle. Each node toggles between states Sl (sleeping) and PC (probing channel) through transitions 1 and 2. The duty-cycle determines the probing time in relation to the total cycle.
In the case of a message coming from upper layers, a new transmission is started, initiating with a
CS (carrier sensing) state (transition 18). If the channel is clear, there is not any transmission taking place in the communication channel near the sender node, transition 19 changes to the
SP (sending preamble) state. In this state, a preamble packet is transmitted in broadcast. By transition 20, the state is changed to
WR (waiting for a reply). In this state, the MAC protocol waits for an answer from a neighbor node belonging to the FCS. When an FCS member wakes up and receives the preamble, it starts to send its own preambles ahead. The first preamble functions as an
eACK packet to previous node. If there is no FCS member awake to reply with a preamble packet, the transition 21 returns the protocol to the
SP state. If a reply message is received, the transition 22 leads the protocol to the state
Wt (waiting
). In this state, the source node waits a computed time to send a data packet, according to the FCS cardinality. The optimal value for
is determined employing the mathematical model presented in
Section 5. This time is necessary to avoid collisions between the control packets (preambles) and the data packet. After this, transition 23 leads source node to the
SM (sending message) state. By the end of the transmission, the protocol returns to the
Sl state by transition 24.
When there is no message to be sent, the protocol alternates between states Sl and PC, as already explained. When a preamble is detected in the PC state, the MAC enters the state VF by the transition 3. In this state, the node that has received the preamble verifies whether it belongs to the FCS of the sender node. If the receiver is not a FCS member, it returns to Sl (by transition 4). All the nodes that receive a preamble and are not members of FCS, are not allowed to answer to other preambles, in order to avoid collisions with concurrent traffic. These nodes will remain in this state until data packet crosses the region. In this way, a possible concurrent traffic is prevented from interfering with this transmission. If the receiver node is an FCS member, the state switches to CS2 by the transition 5. In this state, the sender node puts the radio in listen mode to detect any transmitting signal in the communication channel. If a signal is detected, the node goes to Sleep state Sl through transition 6 to try a new transmission later. If the channel is empty, transition 7 takes the node to SP2. If this node is the final destination D of the message, it sends back a preamble packet with an empty FCS, just to signal the reception. After this, it goes to SR state by transition 8 and waits for data message. If this node is not the final destination D, it assumes the function of the current relay and starts to send its own preambles in order to find the next relay in the route. The first preamble sent by current relay acts at the same time as an eACK for the previous relay. After sending a preamble, the protocol takes the transition 9 and changes to WR2 state to wait for a reply from one of its FCS members. It is important to highlight that states SP and SP2 are similar in what they perform, but in the first one, the protocol is sending a starting message while the second one is reached during the relaying between intermediary nodes. When a node is waiting for a reply, in WR2 state, if no signal is detected in the channel after a specific amount of time, the protocol returns to SP2, by transition 10. If a reply is received, transition 11 drives the protocol to the state SR. In this state, the radio is deactivated until the instant of receiving data packet. When the waiting time is elapsed, the protocol reaches RM state by transition 12. In this state, data packet is received by the sensor node. After this reception, the final destination address is verified. If the message is addressed to the receiving node, the packet is sent to the upper layer and the protocol returns to the sleep state by transition 13. If the receiving node is not the destination D, the message has to be transmitted to the next relay node. Thus, the protocol reaches the state SM by transition 14. After data transmission, the sending node enters the Sl state through transition 24 and goes back to the sleep/awake cycle.
When an imminent collision is identified in WR2 state, the transition 15 drives the state machine to SR2 state in order to avoid collision between data and preamble packets in the upstream relay. In this state, the node interrupts the transmission of preambles and awaits the arrival of the data packet. Transition 16 leads the protocol to the state RM2 in which the data message is received. After this, the relay assumes the role of initiator S, and goes to the state CS by transition 17 and the communication process is restarted. Since preambles were interrupted, the transition 17 is responsible for restart their transmissions in the same way it was done in the source node.
5. Mathematical Model
In this section, we present an analytical model that enables the determination of optimal period
. This is an interval between the time when sender node starts to send preambles and the time it releases data packet. This interval is necessary to avoid imminent collision. In order to calculate
we have to know the probability of using
k preambles to achieve an awake node in the hop
n. This is the probability of avoiding an imminent collision.
k must comprise a total time smaller than the one employed by the data message to achieve hop (
). Our mathematical model uses a large number of variables. In order to facilitate the reading task,
Table 3 describe them.
5.1. Probability of Using k Preambles
The number
k of preambles spent until an awake node is encountered in hop
n is the sum of preambles used in each hop. So the probability of using
k preambles depends on the probability of using a certain number
i of preambles per hop. The probability function of using
i preambles to encounter an awake FCS member in the next hop is given by:
where
v is the cardinality of the FCS and
is the maximum amount of preambles in a cycle time.
This formulation comes from the question: what is the probability of the sender to obtain an answer after preamble
i when the number of FCS members is
v? It is the sum of all combinations of answers of all the
v FCS members only after the preamble
i. In other words, none of the FCS members answered the sender before the preamble
. All of them would wake up and hear the preamble numbered from
to
. This probability is calculated as:
Using this result, we can calculate the probability of obtaining an answer exactly on preamble
i, given by the difference:
which gives Equation (
2).
The probability of spending k preambles until a sensor node wakes up in hop n is the combination of the probabilities of all hops, from 1 to n. For example, suppose a sensor network that uses a cycle time (the sleep/awake cycle) with the same duration of 3 cycles of sending preamble and waiting eACK (). If we want to know the probability of achieving an awake FCS member in the fourth hop, using 6 preambles () since the first one in the sender node, we have to consider all combinations of sent preambles (i) in all four hops that totalize 6: (1,1,1,3); (1,1,2,2); (1,1,3,1); (1,2,1,2); (1,2,2,1); (1,3,1,1); (2,1,1,2); (2,1,2,1); (2,2,1,1) or (3,1,1,1). Then we have to compute the sum of probabilities of all these combinations. This calculation can be made recursively as explained bellow.
Equation (
5) extends
to embrace
n hops. The probability of advancing
n hops with
k preambles (FCS with cardinality
v) is given by the multi-part recursive equation:
Equation (
5) is derived from (
2). The probability of advancing 0 hops with 0 preambles is 1. The probability of using
k preambles to advance 0 hops is 0, whereas the probability of advancing
hops using 0 or less preambles is also 0.
In the other cases, Equation (
5) returns the sum of all probabilities of using different combinations of preambles in the different hops to achieve hop
n. A restriction is that the sum of preambles used in the hops
,
, …,
must be
k.
The first part of the sum () returns the probability of using i preambles in the last hop, whereas the recursive part () calculates the probability of using preambles in all previous hops in combination. This is done for all possible amounts of preambles in the last hop, i.e., from to .
5.2. Average Number of Preambles
As stated in
Section 4.2, the average number of preambles necessary to encounter an awake node in the FCS, in each hop is given by Equation (
1):
This equation can be explained as following: in order to calculate the average number of preambles, a sum of all preamble numbers
i multiplied by the probability of obtaining an answer in that preamble
is performed, as detailed in Equation (
6).
5.3. Probability of Successful Transmission of n Hops
In order to calculate the delay time to release the data packet, it is important to estimate the probability of transmitting preambles successfully through
n hops. This probability is evaluated in Equation (
7). This means that, with probability of
, no imminent collision event occurs during the transmission.
is the initial delay to release data packet. This delay is calculated as a number of preamble propagation time (average value). Since
is given in seconds, the relation between
and
is given by
. The preamble length is given by
and
is the remission interval to wait for an
eACK message. Intervals are given in seconds.
n is the target number of hops.
The probability of transmitting the packet
n hops without collision is calculated based on
, which is the probability of using
k preambles to encounter an awake FCS member in all
n hops, i.e., to deliver the preamble
n-hops successfully. The main idea of Equation (
7) is to sum the probability of successful transmission for all combinations of the number of preambles used in each hop. A successful transmission is characterized by a fast enough preamble advancement. This avoids collision with the data packet.
The transposition of the first three hops must be realized in at most
preambles to avoid collision since the data packet is released after this period. This is modeled by the first summation (
). Here
is used, which is the probability of using
preambles to overcome three hops. When considering the fourth hop, a restriction
in the number of preambles (
) must be satisfied. The total number of preambles that may be employed to wake up the four first hops can not exceed
. This is the sum of the data release time with the time necessary for transmitting the packet one hop further. The probability of transposing the three first hops is multiplied by the probability of transposing the fourth at the right number of preambles (
). This pattern is followed by the next hops
,
, etc. The restrictions are generalized as
. Summarizing, Equation (
7) takes into account that no collision can happen in any intermediary hop, i.e., all steps must have successful transmission to result in a
n hop collision-free transmission.
As already stated, with this equation, it is possible to calculate the probability of transmitting a packet n hops without restarting due to imminent collision. If the recovery mechanism is not implemented, it is possible to select an initial delay to release the data packet () that avoids collisions altogether with a desired probability.
5.4. Optimal Initial Delay to Release Data Packet for n Hops
In this section, the formulation of an optimization problem to find the optimal initial delay to release the data packet is presented. Equation (
8) presents the optimization problem for
n hops.
is the average total latency, measured in data packet length, in the optimal case, to relay a packet
n hops using our MAC scheme. It is the sum of the time spent by the packet to be transmitted
n hops plus additional latency brought by the reservation of the channel and possible collisions (
).
is the initial delay to release the packet (this time interval is measured in data packet length), which should be optimized.
is the probability of colliding (imminent collision) on hop
i when the initial delay
is employed.
The idea of the equation is to minimize the latency by means of selecting the appropriate initial delay for the current situation, i.e., the expected number of hops remaining to the packet destination. The expected latency is given by the transmission of the packet through n hops added to the protocol overhead . This overhead comprises of the initial delay () to release data packet for n hops, in addition to the probability of imminent collision in each hop multiplied by the overhead caused by the event. The probability of imminent collision in the hop i is given by . It is important to remark that this is a recursive optimization function, since for each imminent collision the whole process starts over. In this case, an optimal overhead is calculated again for the remaining path using the same method (recursive call to the minimization function ).
For example, with , we are calculating the protocol overhead in terms of latency for ten hops. This is the result of the initial delay for releasing the data packet added to the probability of imminent collision after the first transmission multiplied by the overhead caused by this event. In addition, all other possible imminent collisions (in the second relay, third, etc) should be also considered.
5.5. Average Advancement
In the last section, the optimal initial delay to release data packet for a given number of hops was determined. Since the positions of source (S) and destination (D) of the packet are known, the source can estimate the number of hops necessary to reach the final destination, employing the formulation presented in this section. For that, a mathematical model for the average advancement accomplished per hop is presented. When a relay node achieve rendezvous with one of its FCS members, the FCS member starts to send its own preambles. We say preambles make a “progress”. Since the FCS member is closer to destination D than the current relay, we say the preamble takes an advancement. The advancement is the difference between the distance measured from the relay nodes to destination (D).
Equation (
9) presents the average advancement in each hop for a FCS cardinality of
v nodes.
where
is the average advancement offered by the
node of the FCS, hereinafter referred to as node
m. The advancements are organized in decreasing order, i.e.,
is the average advancement of the node of the FCS which brings the largest progress in the direction of the destination,
is the average advancement of the node which brings the second largest advancement and so on. Thus, node
m is the node with the
largest advancement.
The calculation of
is presented in Equations (
10)–(
13). Here we are considering that the distance from the current sender (relay
y) to the destination
much larger than the radio range
R, thus
. This enables the approximation of the advancement by a chord in the circle centered by the sender with radios
R and perpendicular to the line
, as depicted in
Figure 4.
Equation (
10) integrates from zero to the radio range
R. The integration variable
x covers all possible advancements of the node with the
largest advancement, which can be from zero to the radio range. An intermediary value of this variable is presented in the
Figure 4.
presents the probability density of finding the
node over the chord in the position
x.
is presented in Equation (
12). It calculates the probability of a node to be placed in the range area after the displacement given by
x, i.e., being in the interval
. This area is identified as posterior in Equation (
10). Since
nodes should be in this area,
is powered by
to calculate this probability.
The probability of a node to be located in the anterior area is
, which is powered by
since the probability of encountering
nodes in this region is required.
, presented in Equation (
13) returns the number of possible combinations derived from a scenario with the total of
n nodes where the average advancement of the
m-th node is in consideration. The
m-th node can be any of the total of nodes, therefore the first term in the
equation is
n. The possibility of different node selections for the posterior is given by
, which is the second term. Since all not selected
nodes must be in the anterior, the last term in the multiplication is one.
In the example presented in
Figure 4,
is the advancement of node 2,
is of node 3 and
of node 1. The figure presents an example of calculation of
, i.e.,
.
Equation (
14) presents the estimation of
n based on the node density
. Based on this value and the desired FCS cardinality, it is possible to appraise the average advancement reached by each hop in the network. Since the sender has the location of the destination, it is possible to assess the average number of hops necessary to reach it and to use this information to select the best initial delay to release the packet after the start of the preamble series.
7. Conclusions
Anycast protocols were proposed for reducing the sleep-delay problem in asynchronous wireless sensor networks. They exploit the path redundancy in densely deployed networks by selecting a group of nodes as good candidates to forward a message. This group of nodes is denominated FCS (Forwarding Candidate Set). The anycast protocol PAX-MAC proposed in this work splits the communication process in two phases. In the first one, the source node transmits a series of short preambles ahead in order to rendezvous with a next-hop node. This process is repeated for a number of hops before starting the second phase. In the latter stage, the source node releases data packet. With this process, simultaneous transmissions of preambles and data are explored, achieving further latency reduction. All the nodes belonging to the route between source and destination receive a data transmission schedule from the preamble packet. Then, these nodes stagger their wake-up time to receive and forward data packet with the shortest delay.
In PAX-MAC, the cardinality of FCS is selected to promote the same propagation speed of a preamble series and a data packet. In average, the distance between the node transmitting preambles and the one sending data is kept constant. In the case of lateness of preamble propagation, PAX-MAC presents a procedure to handle imminent collisions.
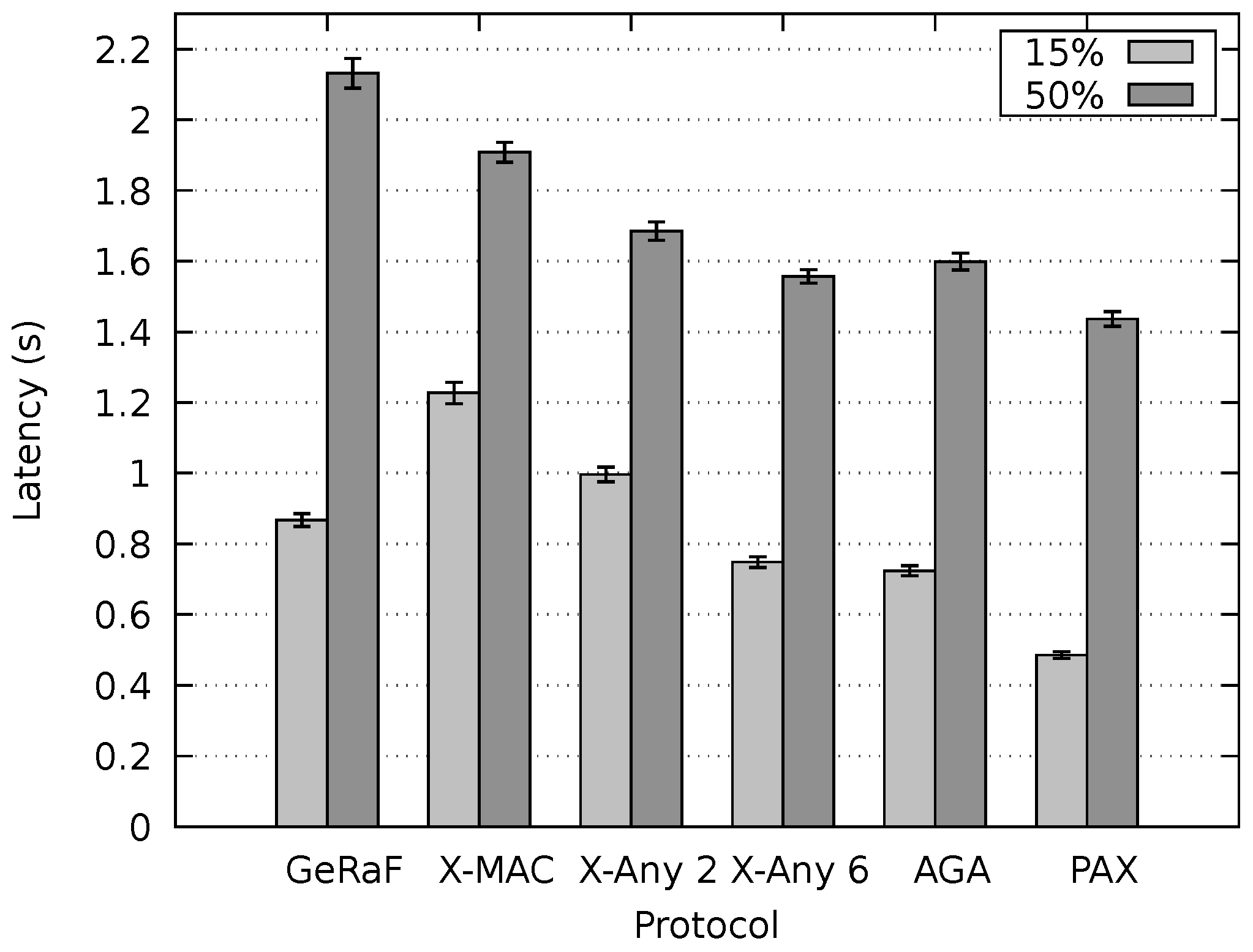
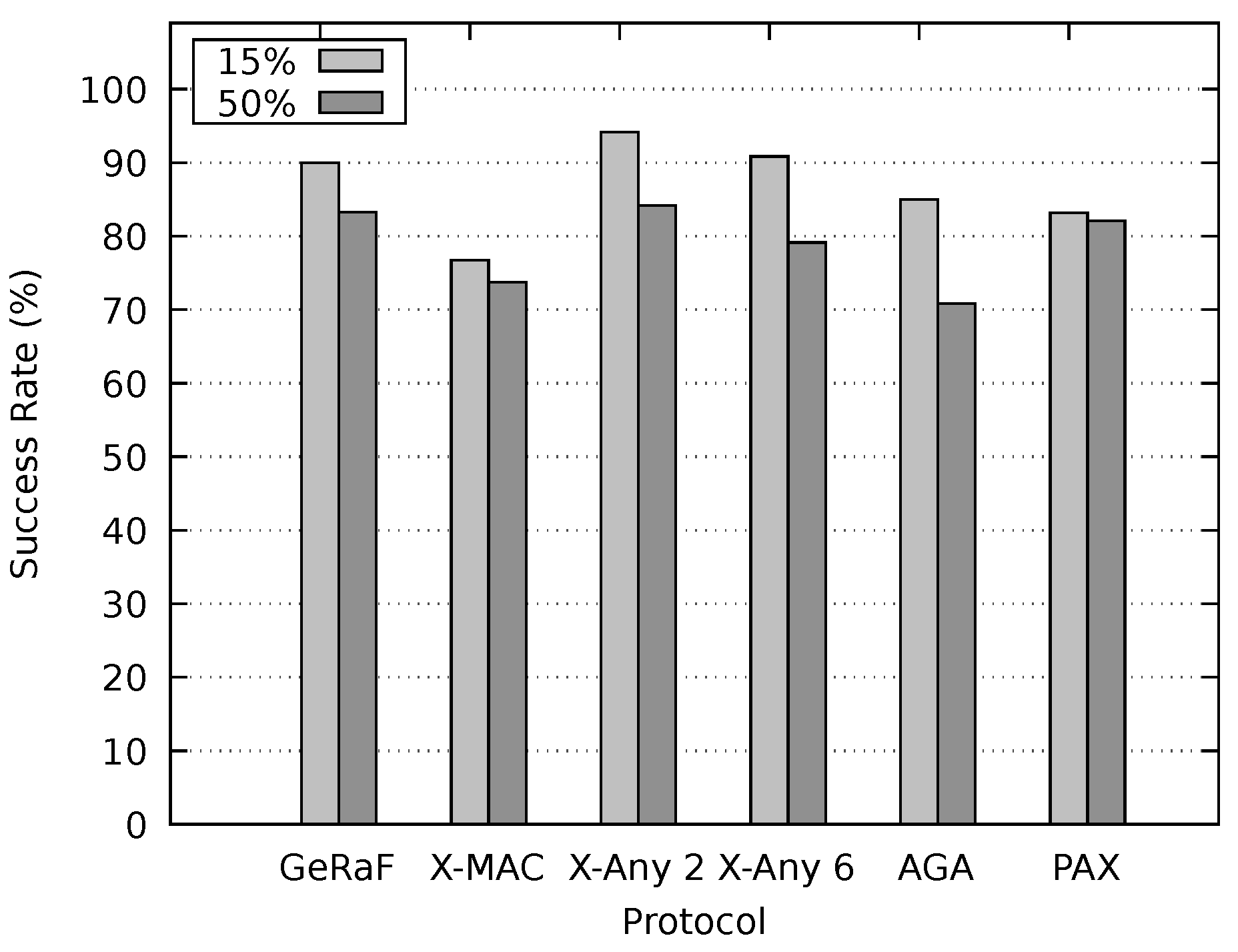
Our protocol was compared to X-MAC, AGA-MAC and an enhanced version of GeRaF based on CMAC. Two versions of the AnyMac protocol were also investigated, denominated here as X-MAC Anycast 2 and X-MAC Anycast 6. Simulations demonstrated that the proposed protocol outperforms all of them in latency for different network densities. In this evaluation, differently from previous ones, data packet sizes were taken into account. In comparison to the protocols assessed, for different inspected scenarios, our method presented results closer to a network that maintains nodes always on.
The PAX-MAC energy expenditure was similar to the best one for all scenarios. In worst case, it spent more energy than the best one. This is a small price to pay inasmuch as a gain of in latency was obtained.