Design of Secure Protocol for Cloud-Assisted Electronic Health Record System Using Blockchain
Abstract
:1. Introduction
1.1. Research Contributions
- We propose the secure protocol for cloud-assisted EHR system using blockchain. The proposed scheme combines cloud computing, blockchain, and authentication to provide a secure and effective medical diagnosis for legitimate patients.
- The proposed scheme withstands various attacks, including impersonation, session key disclosure, and replay attacks, and also provides secure mutual authentication and anonymity.
1.2. Organization
2. Related Works
3. Preliminaries
3.1. Adversary Model
- An attacker can delete, inject, eavesdrop, and intercept the messages transmitted over a public channel.
3.2. Hyperledger Fabric
- Membership Service Provider (MSP): MSP is a component that validates and authenticates credentials and defines the rules for accessing a network. The MSP manages user identities and authenticates all participants in the network, making hyperledger fabric available as both private and permissioned networks. This includes providing credentials for the clients to propose transactions. As a result, a single hyperledger fabric network can be controlled by multiple MSPs.
- Smart Contract: The smart contract of hyperledger fabric is called chaincode. Chaincode is software that defines assets and related transactions. The chaincode is called when the application needs to interact with the ledger. Every chaincode has an attached endorsement policy, which applies to all smart contracts defined in it. This identifies the organizations that need to sign transactions generated by smart contracts. In addition, smart contracts have the advantage of being able to make different smart contracts within the channel or across different channels.
- Ordering Service: The ordering service packages a transaction in blocks and delivers it to the channel’s peers. It ensures the transaction delivery via the network. It communicates with peers and endorsing peers.
- Identity: Each node in the network peer, client, ordered, and the manager has a digital identity with the format of certificate X.509. This identity is used to verify at every stage of the transaction to ensure if the source of the transaction is a valid source. In addition to multiple assurances, validation, and version control checks that occur, there are ongoing identity verifications happening during each stage of the transaction flow.
- Channels: Hyperledger fabric networks can have multiple channels. Channels allow organizations to use the same network while maintaining separation between multiple blockchain. Only the peer of the channel can provide to see transactions made by all members of the channel.
- Peer Nodes: Peer nodes constitute a fundamental element of the network as they host smart contracts within the ledger. Peer nodes execute chaincode, access ledger data, approve transactions, and interface with applications.
4. Cloud-Assisted EHR System Model Using Blockchain
- 1.
- Patient: A patient transmits the health data to the medical center in order to receive healthcare services through healthcare devices and wearable sensors. Health data of the patient are recorded in EHR with healthcare services provided by the medical center.
- 2.
- Medical Centers: The medical centers are registered by the network administrator and participate in the private blockchain. The medical centers generate EHR and store it to the cloud server for sharing with other medical centers. When the medical centers view the EHRs of other medical center’s the patient, they upload a log of EHR data to the blockchain as a transaction form.
- 3.
- Network Administrator: A network administrator is a trusted entity, responsible for the registration of participants, that manages the private blockchain.
- 4.
- Cloud Server: A cloud server is a trusted entity that has sufficient computing power and capacity. The cloud server stores and manages the patient’s EHRs to provide secure data sharing and storage resources. A cloud server receives the EHR data from the medical center and sends the EHR to other medical centers requesting the EHR using a pre-shared secret key.
- 1.
- Patient and doctor register their identities with the help of a network administrator to access EHR services.
- 2.
- Patient and doctor authenticate each other and establish a session key for future secure communication.
- 3.
- The medical center receives the information for a smart contract from the patient using a session key. Then, the medical center generates a patient’s smart contract and EHR. After that, the medical center uploads a smart contract at the blockchain.
- 4.
- The medical center encrypts EHRs of the legitimate patient using a pre-shared secret key and sends it to the cloud server. Then, the cloud server decrypts the encrypted EHR data and stores EHR data in the database.
- 5.
- The other medical center requests the EHR data of the medical center to the cloud server. Next, the cloud server encrypts EHR data of the medical center using a pre-shared secret key and sends it to the other medical center.
- 6.
- Finally, the medical center decrypts the encrypted EHR data and then uploads the log transaction, including the patient and medical center masked identities, signatures, and timestamps at the blockchain.
5. Proposed Protocol for Cloud-Assisted EHR System Using Blockchain
5.1. Registration Phase
5.1.1. Patient Registration Phase
- Step 1:
- The requests registration to the network administrator . First, inputs identity and password . Then, the generates a random number and computes and sends to the .
- Step 2:
- The chooses a random number and computes using the received from the . Then, the stores into the smartcard and issues it to the in the blockchain. Finally, the stores in secure database.
- Step 3:
- After the receives smartcard from the , the generates a random number as a secret key. computes , , , and . And then, the generates a public key and replaces with in a smartcard. Finally, stores in the smartcard.
5.1.2. Medical Center Registration Phase
- Step 1:
- A medical center chooses a unique identity and generates a random number as a its secret key. Then, the computes a masked identity and generates a public key . sends to the .
- Step 2:
- After receiving registration request message, the chooses a random number and retrieves in secure database. Then, the computes . The stores with and sends to .
- Step 3:
- After the receives the messages, the stores in secure database.
5.2. Authentication Phase
- Step 1:
- The inputs his/her , , and smartcard. Then, the smartcard computes , , , , , and . Then, the smartcard checks whether . If it is correct, the generates a timestamp and encrypts messages and computes . Next, the sends a message to via a public channel.
- Step 2:
- After receiving the message , the decrypts . After that, the retrieves in secure database and checks whether . If it is correct, the computes and checks whether . If it is valid, the generates a random number and timestamp and calculates , . updates at the proper period. After that, the generates a session key . Finally, sends message to over an open channel.
- Step 3:
- When the receives the message from the , the computes , and . Then, the checks whether . If it is valid, the computes a session key .
5.3. Smart Contract Uploading Phase
- Step 1:
- The generates message and encrypts his/her information with ; . Then, the sends to the .
- Step 2:
- The computes and checks . If it is valid, decrypts and generates a smart contract using . Finally, the uploads in the blockchain.
5.4. EHR Storing Phase
- Step 1:
- The generates including , , an information of health record , and EHR’s uploading time . Then, the encrypts using a secure pre-shared key and computes . Finally, the sends to the .
- Step 2:
- The decrypts with , computes and checks . If it is correct, the stores in the server database.
5.5. EHR Requesting Phase
- Step 1:
- The generates request messages and encrypts using and computes . Then, the sends to the .
- Step 2:
- After receiving the messages , the decrypts with . After that, the computes and checks . If it is correct, the retrieves corresponding request. The encrypts with and calculates . After then, the sends to the .
- Step 3:
- decrypts the received with and computes . Then, the checks . If it is not valid, the eliminates communication and received data.
5.6. Log Transaction Uploading Phase
6. Security Analysis
6.1. Informal Security Analysis
6.1.1. Impersonation Attack
6.1.2. Session Key Disclosure Attack
6.1.3. Perfect Forward Secrecy
6.1.4. Replay Attack
6.1.5. Privileged Insider Attack
6.1.6. Anonymity
6.1.7. Mutual Authentication
6.2. BAN Logic Analysis
6.2.1. BAN Logic Rules
- 1.
- Message meaning rule:
- 2.
- Nonce verification rule:
- 3.
- Jurisdiction rule:
- 4.
- Freshness rule:
- 5.
- Belief rule:
6.2.2. Goals
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
6.2.3. Idealized Forms
- :
- :
- :
- :
6.2.4. Assumptions
- :
- :
- :
- :
- :
- :
- :
- :
6.2.5. Proof Using BAN Logic
- Step 1:
- From we can get,
- Step 2:
- From the message meaning rule with and ,
- Step 3:
- We use the freshness rule with and ,
- Step 4:
- Using the nonce verification rule with and ,
- Step 5:
- By the Belief rule with and ,
- Step 6:
- Because of the session key , from and ,
- Step 7:
- Using the jurisdiction rule with and ,
- Step 8:
- From we can get,
- Step 9:
- From the message meaning rule with and ,
- Step 10:
- We use the freshness rule with and ,
- Step 11:
- Using the nonce verification rule with and ,
- Step 12:
- By the belief rule with and ,
- Step 13:
- Because of the session key , from and ,
- Step 14:
- Using the jurisdiction rule with and ,
6.3. AVISPA Analysis
7. Performance Analysis
7.1. Computation Cost
- The computation time of a bilinear pairing operation ≈ 4.211 ms.
- The computation time of a scalar multiplication operation on bilinear pairing ms.
- The computation time of a point addition operation on bilinear pairing ms.
- The computation time of a scalar multiplication operation on elliptic curve cryptography ms.
- The computation time of a point addition operation on elliptic curve cryptography ms.
- The computation time of a encryption with elliptic curve cryptography ms.
- The computation time of a decryption with elliptic curve cryptography ms.
- The computation time of a one-way hash function operation ms.
- The computation time of an exponentiation operation ms.
7.2. Communication Cost
7.3. Security Properties
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Greenhalgh, T.; Hinder, S.; Stramer, K.; Bratan, T.; Russell, J. Adoption, non-adoption, and abandonment of a personal electronic health record: Case study of healthspace. Br. Med. J. 2010, 341, c5814. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Tang, F.; Ma, S.; Xiang, Y.; Lin, C. An efficient authentication scheme for blockchain-based electronic health records. IEEE Access 2019, 7, 41678–41689. [Google Scholar] [CrossRef]
- Fan, K.; Ren, Y.; Wang, Y.; Li, H.; Yang, Y. Blockchain-based efficient privacy preserving and data sharing scheme of content-centric network in 5G. IET Commun. 2018, 12, 527–532. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Malina, L.; Dzurenda, P.; Srivastava, G. Optimized blockchain model for internet of things based healthcare applications. In Proceedings of the 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 1–3 July 2019; pp. 135–139. [Google Scholar]
- Dwivedi, A.; Srivastava, G.; Dhar, S.; Singh, R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [Green Version]
- Rathee, G.; Sharma, A.; Iqbal, R.; Aloquaily, M.; Jaglan, N.; Kumar, R. A blockchain framework for securing connected and autonomous vehicles. Sensors 2019, 19, 3165. [Google Scholar] [CrossRef] [Green Version]
- Tseng, L.; Wong, L.; Otoum, S.; Aloqaily, M.; Othman, J.B. Blockchain for managing heterogeneous internet of things: A perspective architecture. IEEE Netw. 2020, 34, 16–23. [Google Scholar] [CrossRef]
- Kuo, T.T.; Rojas, H.Z.; Ohno-Machado, L. Comparison of blockchain platforms: A systematic review and healthcare examples. J. Am. Med. Inform. 2019, 26, 462–478. [Google Scholar] [CrossRef]
- Chukwu, E.; Garg, L. A systematic review of blockchain in healthcare: Frameworks, prototypes, and implementations. IEEE Access 2020, 8, 2169–3536. [Google Scholar] [CrossRef]
- Hyperledger: Open Source Blockchain Technologies. Available online: https://www.hyperledger.org/ (accessed on 8 March 2020).
- Ma, H.; Huang, E.X.; Lam, K.Y. Blockchain-based mechanism for fine-grained authorization in data crowdsourcing. Future Gener. Comput. Syst. 2020, 106, 121–134. [Google Scholar] [CrossRef]
- Thwin, T.T.; Vasupongayya, S. Blockchain-based access control model to preserve privacy for personal health record systems. Secur. Commun. Netw. 2019, 2019, 8315614. [Google Scholar] [CrossRef]
- Zhu, X.; Shi, J.; Lu, C. Cloud health resource sharing based on consensus-oriented blockchain technology: Case study on a breast tumor diagnosis service. J. Med. Internet Res. 2019, 21, e13767. [Google Scholar] [CrossRef] [PubMed]
- Li, M.; Yu, S.; Ren, K.; Lou, W. Securing personal health records in cloud computing: Patient-centric and fine-grained data access control in multi-owner settings. In Proceedings of the 6th International ICST Conference on Security and Privacy in Communication Networks (SecureComm 2010), Singapore, 7–9 September 2010; pp. 89–106. [Google Scholar]
- Ridhawi, I.A.; Otoum, S.; Aloquaily, M.; Jararweh, Y.; Baker, T. Providing secure and reliable communication for next generation networks in smart cities. Sustain. Cities Soc. 2020, 56, 102080. [Google Scholar] [CrossRef]
- Park, Y.; Park, Y. A selective group authentication scheme for IoT-based medical information system. J. Med. Syst. 2017, 41, 48. [Google Scholar] [CrossRef] [PubMed]
- Kaur, H.; Alam, M.A.; Jameel, R.; Mourya, A.K.; Chang, V. A proposed solution and future direction for blockchain-based heterogeneous medicare data in cloud environment. J. Med. Syst. 2018, 42, 156. [Google Scholar] [CrossRef] [Green Version]
- Nagasubramanian, G.; Sakthivel, R.K.; Patan, R.; Gandomi, A.H.; Sankayya, M.; Balusamy, B. Securing e-health records using keyless signature infrastructure blockchain technology in the cloud. Neural Comput. Appl. 2020, 32, 639–647. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Lee, J.Y.; Yu, S.J.; Park, K.S.; Park, Y.H.; Park, Y.H. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [Green Version]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 8 March 2020).
- SPAN: A Security Protocol Animator for AVISPA. Available online: http://www.avispa-project.org/ (accessed on 8 March 2020).
- Kumar, P.; Lee, S.G.; Lee, H.J. E-SAP: Efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 2012, 12, 1625–1647. [Google Scholar] [CrossRef] [Green Version]
- Wu, Z.Y.; Chen, L.; Wu, J.C. A reliable RFID mutual authentication scheme for healthcare environments. J. Med. Syst. 2013, 37, 9917. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, Z.; Chen, X.; Kwak, K.S. Certificateless remote anonymous authentication schemes for wireless body area networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 332–342. [Google Scholar] [CrossRef]
- Renuka, K.; Kumari, S.; Li, X. Design of a secure three-factor authentication scheme for smart healthcare. J. Med. Syst. 2019, 43, 133. [Google Scholar] [CrossRef] [PubMed]
- Pandey, P.; Litoriya, R. Securing e-health networks from counterfeit medicine penetration using blockchain. Wirel. Pers. Commun. 2020. [Google Scholar] [CrossRef]
- Agbo, C.C.; Mahmoud, Q.H. Comparison of blockchain frameworks for healthcare applications. Internet Technol. Lett. 2019, 2, e122. [Google Scholar] [CrossRef] [Green Version]
- Tanwar, S.; Parekh, K.; Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 2020, 50, 102407. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, A.; Zhang, P.; Wang, H. Cloud-assisted EHR sharing with security and privacy preservation via consortium blockchain. IEEE Access 2019, 7, 136704–136719. [Google Scholar] [CrossRef]
- Chen, Y.; Ding, S.; Xu, Z.; Zheng, H.; Yang, S. Blockchain-based medical records secure storage and medical service framework. J. Med. Syst. 2019, 43, 5. [Google Scholar] [CrossRef]
- Cheng, X.; Chen, F.; Xie, D.; Sun, H.; Huang, C. Design of a secure medical data sharing scheme based on blockchain. J. Med. Syst. 2020, 44, 52. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Li, C.T.; Lee, C.C.; Weng, C.Y.; Chen, S.J. A secure dynamic identity and chaotic maps based user authentication and key agreement scheme for e-Healthcare systems. J. Med. Syst. 2016, 40, 233. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference (CRYPTO), Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Yu, S.J.; Lee, J.Y.; Lee, K.K.; Park, K.S.; Park, Y.H. Secure authentication protocol for wireless sensor networks in vehicular communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef] [Green Version]
- Park, Y.H.; Park, Y.H. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Novo, O. Blockchain meets IoT: An architecture for scalable access management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Lu, N.; Zhang, Y.; Shi, W.; Kumari, S.; Choo, K.K.R. A secure and scalable data integrity auditing scheme based on hyperledger fabric. Comput. Secur. 2020, 92, 101741. [Google Scholar] [CrossRef]
- Von Oheimb, D. The high-level protocol specification language HLPSL developed in the EU project avispa. In Proceedings of the APPSEM 2005 Workshop, Tallinn, Finland, 13–15 September 2005; pp. 1–2. [Google Scholar]
- Lei, A.; Cruickshank, H.; Cao, Y.; Asuquo, P.; Ogah, C.P.A.; Sun, Z. Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet Things J. 2017, 4, 1832–1843. [Google Scholar] [CrossRef] [Green Version]
- Islam, S.K.H.; Obaidat, M.S.; Vijayakumar, P.; Abdulhay, E.; Li, F.; Reddy, M.K.C. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Future Gener. Comput. Syst. 2018, 84, 216–227. [Google Scholar] [CrossRef]
- Zhang, Q.; Wang, X.; Yuan, J.; Liu, L.; Wang, R.; Huang, H.; Li, Y. A hierarchical group key agreement protocol using orientable attributes for cloud computing. Inform. Sci. 2019, 480, 55–69. [Google Scholar] [CrossRef]
- Lee, H.; Lee, D.; Moon, J.; Jung, J.; Kang, D.; Kim, H.; Won, D. An improved anonymous authentication scheme for roaming in ubiquitous networks. PLoS ONE 2018, 13, e0193366. [Google Scholar] [CrossRef] [Green Version]
- Ying, B.; Nayak, A. Lightweight remote user authentication protocol for multi-server 5G networks using self-certified public key cryptography. J. Netw. Comput. Appl. 2019, 131, 66–74. [Google Scholar] [CrossRef]










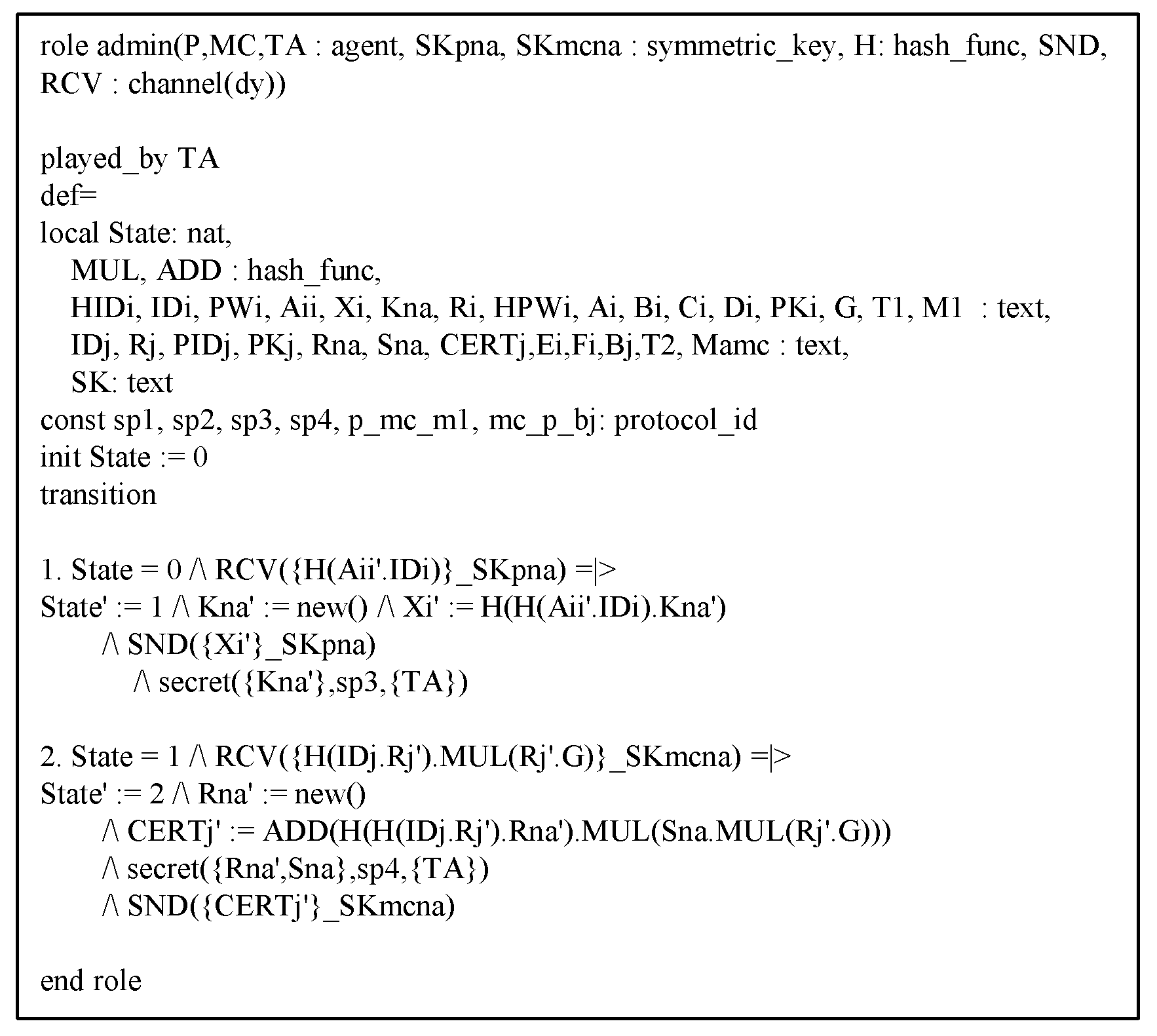


| Notations | Meanings |
|---|---|
| i-th patient | |
| j-th medical center | |
| Network Administrator | |
| Identity of and | |
| Password of | |
| Secret keys of and | |
| Secret key of | |
| Timestamps | |
| Uploading/accessing time of EHR | |
| Random numbers generated by | |
| Public keys of and | |
| Certificates of and | |
| A nonsingular elliptic curve (mod p) | |
| G | A base point for elliptic curve |
| Pseudo-identities of and | |
| Log transaction | |
| Secure pre-shared key among and | |
| Electronic health record | |
| Information of health record | |
| Request message of EHR | |
| Common session key shared among and | |
| Collision resistant one-way hash function | |
| ⊕ | XOR operation |
| Concatenation operation |
| Notation | Description |
|---|---|
| Xbelieves statement Q | |
| X once said Q | |
| Xcontrols statement Q | |
| #Q | Statement Q is fresh |
| Xsees statement Q | |
| Formula Q is combined with formula Z | |
| Q is encrypted under key K | |
| Y has K as a public key | |
| X and Y may use shared key K to communicate | |
| Session key used in the current session |
| Liu et al. [25] | Renuka et al. [26] | Proposed | |
|---|---|---|---|
| Patient/Client | ms | ms | ms |
| Medical center | ms | ms | ms |
| Liu et al. [25] | Renuka et al. [26] | Proposed | |
|---|---|---|---|
| Patient/Client | bits | bits | bits |
| Medical center | bits | bits | bits |
| Liu et al. [25] | Renuka et al. [26] | Proposed | |
|---|---|---|---|
| Impersonation attack | X | O | O |
| Session key disclosure attack | X | O | O |
| Perfect forward secrecy | X | O | O |
| Replay attack | O | O | O |
| Privileged insider attack | X | O | O |
| Single point of failure | X | X | O |
| Anonymity | O | O | O |
| Mutual authentication | X | O | O |
| Bottleneck | X | X | O |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, M.; Yu, S.; Lee, J.; Park, Y.; Park, Y. Design of Secure Protocol for Cloud-Assisted Electronic Health Record System Using Blockchain. Sensors 2020, 20, 2913. https://doi.org/10.3390/s20102913
Kim M, Yu S, Lee J, Park Y, Park Y. Design of Secure Protocol for Cloud-Assisted Electronic Health Record System Using Blockchain. Sensors. 2020; 20(10):2913. https://doi.org/10.3390/s20102913
Chicago/Turabian StyleKim, MyeongHyun, SungJin Yu, JoonYoung Lee, YoHan Park, and YoungHo Park. 2020. "Design of Secure Protocol for Cloud-Assisted Electronic Health Record System Using Blockchain" Sensors 20, no. 10: 2913. https://doi.org/10.3390/s20102913
APA StyleKim, M., Yu, S., Lee, J., Park, Y., & Park, Y. (2020). Design of Secure Protocol for Cloud-Assisted Electronic Health Record System Using Blockchain. Sensors, 20(10), 2913. https://doi.org/10.3390/s20102913






