Behavioral Acoustic Emanations: Attack and Verification of PIN Entry Using Keypress Sounds
Abstract
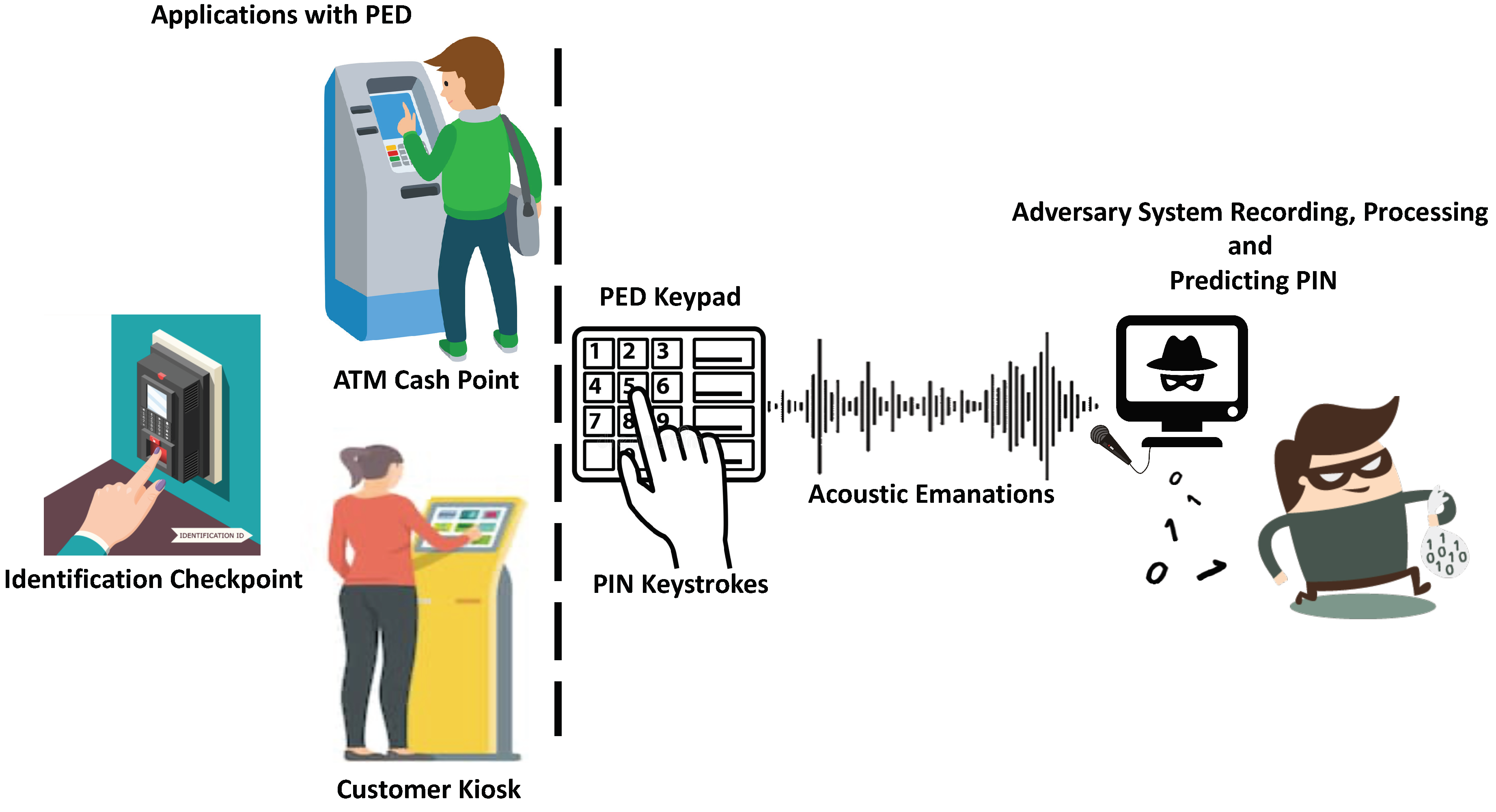
:1. Introduction
- An investigation into the security vulnerability of PEDs by performing a PIN key recover attack on the random six-digit PIN number by using the acoustic emanation generated by the PED keypads.
- Proposing the behavioral acoustic emanations as a countermeasure and verification method for a PIN key user’s identity.
2. Literature Review
2.1. Emission Security and Side-Channel Analysis
2.2. Key Recovery from Sensors
2.3. Preventative Measures against Key Recovery Approaches
2.3.1. Biometrics
2.3.2. Active Authentication
3. Acoustic Side-Channel PIN Recovery
3.1. Application-Threat Model: PIN Key Recovery by Using Acoustic Emanations at Customer Kiosks
3.2. Methodology
3.2.1. Data Collection
3.2.2. Feature Extraction
3.2.3. Time-Frequency Analysis
- Cross-Correlation: We use MATLAB’s xcorr function to calculate the cross-correlation between two acoustic signals normalized with respect to power. If the two signals are ‘f’ and ‘g’, the discretized cross-correlation measures the similarity between ‘f’ and shifted (lagged) copies of ‘g’ as a function of the lag. If ‘f’ and ‘g’ have different lengths, the function appends zeros at the end of the shorter vector. [56]The function, xcorr, yields different outputs based on the input lag parameter. To calculate the similarity between the two signals, we select the maximum cross-correlation value emitted for any input lag parameter.
- Frequency-Based Distance: The frequency domain distance between a pair of signals is calculated by measuring the Euclidean distance between the frequency spectrum of the two signals. Spectrum is calculated by evaluating the FFT coefficients in the range 0.4–22 kHz [55]. For the two signals ‘f’ and ‘g’, the frequency-based distance is measured using the following equations.
3.2.4. Machine-Learning Models and Assessments
- Machine Learning: This work evaluates three machine-learning models, specifically:
- (a)
- Gaussian Naïve Bayes (Gaussian NB)
- (b)
- Logistic Regression (LR), and
- (c)
- Support Vector Machines (SVM)
In our task, we know the input and we know what the output should be; however, we do not have an algorithm to transform the input to the output. When we meet this situation, we can try machine-learning. Our dataset can be labeled as positive and negative examples, e.g., if the PIN is entered by User 1, we mark it positive, otherwise we mark negative. Supervised learning is suitable for the labeled data [57]. We extract 10 kinds of features from the raw acoustic data, including inter-keystroke latency, hold time, hit peak, release peak, press time, release time, press volume, release volume, press spectrum, release spectrum. We want to find which feature contribute most to help us to make decision. Gaussian Naïve Bayes classifier distributes the same representational power to each feature [58]. Thus, we applied the Gaussian Naïve Bayes classifier to the dataset and found when we use latency and hold time as features, we can get the best result. The latency and hold time are categorical features, the expected outcomes, e.g., User 1 entered the PIN, are categorical as well. In this situation, logistic regression is suited to describe the relationship between features and outcomes [59]. The SVM can add exponents to the feature and raise the accuracy of the model [60], this can neutralize the negative effect of the small number of features in our case. In Section 3.3, our goal is to prove the threat that use acoustic emanation to recover a PIN is possible. Thus, we only trained a logistic regression model. In Section 4, the essential part of this paper, we tried 3 models to reach the best accuracy in user verification. - False Acceptance Rate (FAR), False Rejection Rate (FRR) and True Acceptance Rate (TAR): This section provides a description of metrics for the evaluation of Biometric performance. FAR and FRR are used in assessing authentication or verification system, e.g., [61,62]. True acceptance rate means the accuracy of the prediction model. Typically, setting a global acceptance threshold requires considering the tradeoff between the false acceptance rate and false rejection rate.
- (a)
- FAR: This is the measure of the likelihood that the security system will incorrectly accept an access attempt by an unauthorized user.
- (b)
- FRR: This is the measure of the likelihood that the security system will incorrectly reject an access attempt by an authorized user.
- (c)
- TAR: This is the measure of the likelihood that the security system will correctly accept an access attempt by an authorized user.
3.3. Experiment and Results
- An audio signal repository was established for the key presses 1, 5, 6, 8, 9, and 7 for a targeted user.
- The repository was divided into testing and training sets.
- Then a similarity function was implemented using pairwise cross-correlation.
- Each testing and training keystroke ‘f’, was transformed into a feature vector that consisted of six elements. Each element describes the average similarity of ‘f’ against the acoustic emanations generated from a specific key source. (i.e., feature(f) = similarity to key 1, similarity to key 5, similarity to key 6 and so on)
- The features are then plotted for the press and release regions followed by min-max scaling.
3.3.1. Time-Frequency Analysis
3.3.2. Data Analysis
4. Behavioral Acoustics for Verification of a PIN Key Users
4.1. Authentication Based on Acoustic Analytics
4.2. Application-Threat Model: User Authentication Based on Acoustic Analytics of an ATM Machine
4.2.1. Data Analysis and Results
- Gaussian Naïve Bayes classifier with Latency features: In this analysis, every PIN sequence is encoded into a feature vector by extracting the latencies associated with all the five transitions in the six-digit numbered PINs. This vector is then fed into a Gaussian Naïve Bayes classifier that trains itself to output the predicted users.Figure 13 shows the class-conditioned probabilities of observing a particular latency feature ‘x’ for a given class ‘y’ for the first transition of a given PIN sequence. Likewise, the model trains itself for all five transition to discern various users in the training set. Once trained, we analyze the accuracy of this model on our testing set. Again, the test set consists of latency-based features with the vector cardinality being five. For every test instance, the model outputs a probability vector, which depicts the model’s confidence for every user. We derive a ranking order from the probability list. According to the formulation, rank ‘0’ is assigned to the user that the model believes is the correct answer, rank ’1’ is the second strongest prediction, and henceforth. The table in Figure 14 depicts the rankings awarded to the actual users during the testing stage. A model is considered good if the occurrences where it rewards the true user a rank ‘0’ is high. To better understand the predictions, we plot the False Acceptance Rate (FAR), False Rejection Rate (FRR) and True Acceptance Rate (TAR) yielded for various confidence threshold values.
- Gaussian Naïve Bayes classifier with Latency and Hold features: Here, we consider the case where the feature vector consists of latency and hold-based features. We retain the feature set collected from the previous section and concatenated it with the features acquired for the hold time. The hold time for a keystroke is evaluated by measuring the latency between the press and release starting points. Figure 15 provides a visual representation of the many non-overlapping features that assist the classifier to discriminate users.From Figure 15, it is evident by the increase in number of true users labeled ‘0’ that the classifier’s performance has incremented with the inclusion of hold time. This corroborates the claim that the ‘hold time’ exhibits user specific characteristics. Furthermore, it can be inferred from the figure that a confidence threshold value at around 80% (0.8), can yield an approximate 80% TAR, 20% FAR, and 20% FRR. In addition to that out of all the 37 instances that were incorrectly not ranked ‘0’, there was only one occurrence of two consecutive false rejections. This means that if a user is falsely rejected by an authentication system, then the likelihood of being rejected again in the next attempt is negligible.
- Logistic Regression with latency and hold features: In this segment, we consider a change in the machine-learning model as compared to the previous section of the paper. The generative Gaussian Naïve Bayes model is replaced with a discriminative Logistic Regression model, and the input only consists of latency and hold-based features.Compared to the previous techniques, Figure 16 shows an increase in performance. In fact, this model achieved the highest accuracy for this experiment. The number of actual users awarded the rank ‘0’ increased from 80% to 87%. Similarly, setting the threshold at a confidence value of 40% (0.4) achieved an 88% TAR, 12% FAR, and 12% FRR. Additionally, there was no such instance recorded where there were two consecutive false rejections. Since this data set only consists of 15 users, the occurrences of false rejection will be higher when rolled out for a vast user domain. Although rare, as we consider entry attempts by all false users and train on a small data set, it is important to counteract this scenario by letting the user type in the PIN sequence again. The likelihood of the user being rejected in the second attempt is low, and the user is challenged up to three times before complete access denial. However, on the downside, allowing three attempts could also have a detrimental impact on the false acceptance rate.
- Support Vector Machine with Latency and Hold: In this section, we gauge the performance of a Support Vector Machine model to classify the data.The performance was found to be similar to Gaussian Naïve Bayes, but less accurate compared to logistic regression, Table 2 shows the accuracy of SVM.
4.2.2. Enhanced Authentication Architecture
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Xu, L.D.; He, W.; Li, S. Internet of Things in Industries: A Survey. IEEE Trans. Ind. Informatics 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar]
- Zhou, L.; Yeh, K.H.; Hancke, G.; Liu, Z.; Su, C. Security and privacy for the industrial internet of things: An overview of approaches to safeguarding endpoints. IEEE Signal Process. Mag. 2018, 35, 76–87. [Google Scholar]
- Golla, M.; Beuscher, B.; Dürmuth, M. On the security of cracking-resistant password vaults. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1230–1241. [Google Scholar]
- Wang, D.; Zhang, Z.; Wang, P.; Yan, J.; Huang, X. Targeted online password guessing: An underestimated threat. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1242–1254. [Google Scholar]
- Yang, W.; Li, N.; Chowdhury, O.; Xiong, A.; Proctor, R.W. An empirical study of mnemonic sentence-based password generation strategies. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1216–1229. [Google Scholar]
- Chatterjee, R.; Athayle, A.; Akhawe, D.; Juels, A.; Ristenpart, T. pASSWORD tYPOS and how to correct them securely. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 799–818. [Google Scholar]
- Silver, D.; Jana, S.; Boneh, D.; Chen, E.; Jackson, C. Password managers: Attacks and defenses. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14), San Diego, CA, USA, 20–22 August 2014; pp. 449–464. [Google Scholar]
- Yan, J.; Blackwell, A.; Anderson, R.; Grant, A. Password memorability and security: Empirical results. IEEE Secur. Priv. 2004, 2, 25–31. [Google Scholar] [CrossRef]
- Payment Card Industry (PCI). PIN Transaction Security (PTS) Point of Interaction (POI); Security Standards Council: Wakefield, MA, USA, 2011; Available online: https://www.pci-dss.gr/media/1955/pci_pts_poi_vq_v4_final.pdf (accessed on 10 June 2013).
- Drimer, S.; Murdoch, S.J.; Anderson, R. Thinking inside the box: System-level failures of tamper proofing. In Proceedings of the 2008 IEEE Symposium on Security and Privacy (sp 2008), Oakland, CA, USA, 18–22 May 2008; pp. 281–295. [Google Scholar]
- Murdoch, S.J.; Drimer, S.; Anderson, R.; Bond, M. Chip and PIN is Broken. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 433–446. [Google Scholar]
- Anderson, R.; Murdoch, S.J. EMV: Why payment systems fail. Commun. ACM 2014, 57, 24–28. [Google Scholar]
- Bond, M.; Choudary, O.; Murdoch, S.J.; Skorobogatov, S.; Anderson, R. Chip and Skim: Cloning EMV cards with the pre-play attack. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; pp. 49–64. [Google Scholar]
- Kuhn, M.G.; Anderson, R.J. Soft tempest: Hidden data transmission using electromagnetic emanations. In Proceedings of the International Workshop on Information Hiding, Portland, OR, USA, 14–17 April 1998; pp. 124–142. [Google Scholar]
- Qiao, H.; Liu, Y.; Yang, A.; Hancke, G. Preventing overshadowing attacks in self-jamming audio channels. IEEE Trans. Dependable Secur. Comput. 2018. [Google Scholar] [CrossRef]
- Friedman, J. Tempest: A signal problem. NSA Cryptologic Spectr. 1972, 35, 76. [Google Scholar]
- Smulders, P. The threat of information theft by reception of electromagnetic radiation from RS-232 cables. Comput. Secur. 1990, 9, 53–58. [Google Scholar]
- Vuagnoux, M.; Pasini, S. Compromising Electromagnetic Emanations of Wired and Wireless Keyboards. In Proceedings of the 18th USENIX Security Symposium, Montreal, QC, Canada, 10–14 August 2009; pp. 1–16. [Google Scholar]
- Backes, M.; Dürmuth, M.; Gerling, S.; Pinkal, M.; Sporleder, C. Acoustic Side-Channel Attacks on Printers. In Proceedings of the 19th USENIX Security symposium, Washington, DC, USA, 11–13 August 2010; pp. 307–322. [Google Scholar]
- Loughry, J.; Umphress, D.A. Information leakage from optical emanations. ACM Trans. Inf. Syst. Secur. (TISSEC) 2002, 5, 262–289. [Google Scholar] [CrossRef] [Green Version]
- Van Eck, W. Electromagnetic radiation from video display units: An eavesdropping risk? Comput. Secur. 1985, 4, 269–286. [Google Scholar] [CrossRef] [Green Version]
- Kuhn, M.G. Optical time-domain eavesdropping risks of CRT displays. In Proceedings of the 2002 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 12–15 May 2002; pp. 3–18. [Google Scholar]
- Kuhn, M.G. Compromising emanations of LCD TV sets. IEEE Trans. Electromagn. Compat. 2013, 55, 564–570. [Google Scholar] [CrossRef] [Green Version]
- Shumailov, I.; Simon, L.; Yan, J.; Anderson, R. Hearing your touch: A new acoustic side channel on smartphones. arXiv 2019, arXiv:1903.11137. [Google Scholar]
- Yu, J.; Lu, L.; Chen, Y.; Zhu, Y.; Kong, L. An indirect eavesdropping attack of keystrokes on touch screen through acoustic sensing. IEEE Trans. Mob. Comput. 2019. [Google Scholar] [CrossRef]
- Zhou, M.; Wang, Q.; Yang, J.; Li, Q.; Jiang, P.; Chen, Y.; Wang, Z. Stealing Your Android Patterns via Acoustic Signals. IEEE Trans. Mob. Comput. 2019. [Google Scholar] [CrossRef]
- Hayashi, Y.; Homma, N.; Miura, M.; Aoki, T.; Sone, H. A threat for tablet pcs in public space: Remote visualization of screen images using em emanation. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 954–965. [Google Scholar]
- Kocher, P.C. Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 1996; pp. 104–113. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; pp. 388–397. [Google Scholar]
- Gandolfi, K.; Mourtel, C.; Olivier, F. Electromagnetic analysis: Concrete results. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Paris, France, 14–16 May 2001; pp. 251–261. [Google Scholar]
- Genkin, D.; Shamir, A.; Tromer, E. RSA key extraction via low-bandwidth acoustic cryptanalysis. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2014; pp. 444–461. [Google Scholar]
- Mangard, S.; Oswald, E.; Popp, T. Power Analysis Attacks: Revealing the Secrets of Smart Cards; Springer Science & Business Media: Berlin, Germany, 2008; Volume 31. [Google Scholar]
- Ledwaba, L.P.; Hancke, G.P.; Venter, H.S.; Isaac, S.J. Performance costs of software cryptography in securing new-generation Internet of energy endpoint devices. IEEE Access 2018, 6, 9303–9323. [Google Scholar] [CrossRef]
- Hu, Q.; Zhang, J.; Mitrokotsa, A.; Hancke, G. Tangible security: Survey of methods supporting secure ad-hoc connects of edge devices with physical context. Comput. Secur. 2018, 78, 281–300. [Google Scholar] [CrossRef]
- Asonov, D.; Agrawal, R. Keyboard acoustic emanations. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 12 May 2004; pp. 3–11. [Google Scholar]
- Zhuang, L.; Zhou, F.; Tygar, J.D. Keyboard acoustic emanations revisited. ACM Trans. Inf. Syst. Secur. (TISSEC) 2009, 13, 1–26. [Google Scholar] [CrossRef]
- Zhu, T.; Ma, Q.; Zhang, S.; Liu, Y. Context-free attacks using keyboard acoustic emanations. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 453–464. [Google Scholar]
- Owusu, E.; Han, J.; Das, S.; Perrig, A.; Zhang, J. Accessory: Password inference using accelerometers on smartphones. In Proceedings of the Twelfth Workshop on Mobile Computing Systems & Applications, San Diego, CA, USA, 28–29 February 2012; pp. 1–6. [Google Scholar]
- Liu, X.; Zhou, Z.; Diao, W.; Li, Z.; Zhang, K. When good becomes evil: Keystroke inference with smartwatch. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 1273–1285. [Google Scholar]
- Simon, L.; Anderson, R. Pin skimmer: Inferring pins through the camera and microphone. In Proceedings of the Third ACM Workshop on Security and Privacy in Smartphones & Mobile Devices, Berlin, Germany, 8 November 2013; pp. 67–78. [Google Scholar]
- Cardaioli, M.; Conti, M.; Balagani, K.; Gasti, P. Your PIN Sounds Good! On The Feasibility of PIN Inference Through Audio Leakage. arXiv 2019, arXiv:1905.08742. [Google Scholar]
- de Souza Faria, G.; Kim, H.Y. Differential audio analysis: A new side-channel attack on PIN pads. Int. J. Inf. Secur. 2019, 18, 73–84. [Google Scholar] [CrossRef]
- Kong, J.; Aciiçmez, O.; Seifert, J.P.; Zhou, H. Hardware-software integrated approaches to defend against software cache-based side channel attacks. In Proceedings of the 2009 IEEE 15th International Symposium on High Performance Computer Architecture, Raleigh, NC, USA, 14–18 February 2009; pp. 393–404. [Google Scholar]
- Ambrose, J.A.; Ragel, R.G.; Parameswaran, S.; Ignjatovic, A. Multiprocessor information concealment architecture to prevent power analysis-based side channel attacks. IET Comput. Digit. Tech. 2011, 5, 1–15. [Google Scholar] [CrossRef] [Green Version]
- Ambrose, J.A.; Parameswaran, S.; Ignjatovic, A. MUTE-AES: A multiprocessor architecture to prevent power analysis based side channel attack of the AES algorithm. In Proceedings of the 2008 IEEE/ACM International Conference on Computer-Aided Design, San Jose, CA, USA, 10–13 November 2008; pp. 678–684. [Google Scholar]
- Okeya, K.; Sakurai, K. On insecurity of the side channel attack countermeasure using addition-subtraction chains under distinguishability between addition and doubling. In Proceedings of the Australasian Conference on Information Security and Privacy, Melbourne, Australia, 3–5 July 2002; pp. 420–435. [Google Scholar]
- Dinca, L.M.; Hancke, G.P. The fall of one, the rise of many: A survey on multi-biometric fusion methods. IEEE Access 2017, 5, 6247–6289. [Google Scholar] [CrossRef]
- Qureshi, U.M.; Hancke, G.P.; Gebremichael, T.; Jennehag, U.; Forsström, S.; Gidlund, M. Survey of proximity based authentication mechanisms for the Industrial Internet of Things. In Proceedings of the IECON 2018-44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 5246–5251. [Google Scholar]
- Miller, B. Vital signs of identity [biometrics]. IEEE Spectr. 1994, 31, 22–30. [Google Scholar] [CrossRef]
- Monrose, F.; Rubin, A.D. Keystroke dynamics as a biometric for authentication. Future Gener. Comput. Syst. 2000, 16, 351–359. [Google Scholar] [CrossRef] [Green Version]
- Ogihara, A.; Matsumura, H.; Shiozaki, A. Biometric verification using keystroke motion and key press timing for atm user authentication. In Proceedings of the 2006 International Symposium on Intelligent Signal Processing and Communications, Tottori, Japan, 12–15 December 2006; pp. 223–226. [Google Scholar]
- Guidorizzi, R.P. Security: Active authentication. IT Prof. 2013, 15, 4–7. [Google Scholar] [CrossRef]
- Fridman, L.; Weber, S.; Greenstadt, R.; Kam, M. Active authentication on mobile devices via stylometry, application usage, web browsing, and GPS location. IEEE Syst. J. 2016, 11, 513–521. [Google Scholar] [CrossRef] [Green Version]
- Halevi, T.; Saxena, N. Keyboard acoustic side channel attacks: Exploring realistic and security-sensitive scenarios. Int. J. Inf. Secur. 2015, 14, 443–456. [Google Scholar] [CrossRef]
- Rabiner, L.; Schafer, R. Digital Processing of Speech Signals; Prentice-Hall: Upper Saddle River, NJ, USA, 1978. [Google Scholar]
- Alpaydin, E. Introduction to Machine Learning; MIT Press: Cambridge, MA, USA, 2020. [Google Scholar]
- Langley, P.; Iba, W.; Thompson, K. An analysis of Bayesian classifiers. In Proceedings of the Tenth National Conference on Artificial Intelligence (AAAI-92), San Jose, CA, USA, 12–16 July 1992; Volume 90, pp. 223–228. [Google Scholar]
- Peng, C.Y.J.; Lee, K.L.; Ingersoll, G.M. An introduction to logistic regression analysis and reporting. J. Educ. Res. 2002, 96, 3–14. [Google Scholar]
- Schölkopf, B.; Simard, P.; Smola, A.J.; Vapnik, V. Prior knowledge in support vector kernels. In Proceedings of the Advances in Neural Information Processing Systems, Denver, CO, USA, 30 November–5 December 1998; pp. 640–646. [Google Scholar]
- Vatsa, M.; Singh, R.; Noore, A. Reducing the false rejection rate of iris recognition using textural and topological features. Int. J. Signal Process. 2005, 2, 2. [Google Scholar]
- Le Saint, E.F.; Wen, W.; Hamid, L. Method for Improving False Acceptance Rate Discriminating for Biometric Authentication Systems. U.S. Patent 8,014,570, 6 September 2011. [Google Scholar]
















| Feature | Unit |
|---|---|
| Inter-Keystroke latency | Time |
| Hold time | Time duration |
| Hit Peak | Time |
| Release Peak | Time |
| Press Time | Time duration |
| Release Time | Time duration |
| Press Volume | Volume against Time |
| Release Volume | Volume against Time |
| Press Spectrum | FFT coefficients |
| Release Spectrum | FFT coefficients |
| Rank | Occurrences | Percentage |
|---|---|---|
| 0 | 163 | 81.9096 |
| 1 | 21 | 10.5528 |
| 2 | 7 | 3.5179 |
| 3 | 1 | 0.5025 |
| 4 | 2 | 1.0050 |
| 5 | 1 | 0.5025 |
| 6 | 1 | 0.5025 |
| 7 | 1 | 0.5025 |
| 8 | 2 | 0.0050 |
| Model | Feature | FAR | FRR | TAR |
|---|---|---|---|---|
| Gaussian NB | Latency | 22% | 22% | 75% |
| Gaussian NB | Latency and Hold | 20% | 20% | 81% |
| Logistic Regression | Latency and Hold | 12% | 12% | 88% |
| Support Vector Machines | Latency and Hold | 18 | 18 | 82% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Panda, S.; Liu, Y.; Hancke, G.P.; Qureshi, U.M. Behavioral Acoustic Emanations: Attack and Verification of PIN Entry Using Keypress Sounds. Sensors 2020, 20, 3015. https://doi.org/10.3390/s20113015
Panda S, Liu Y, Hancke GP, Qureshi UM. Behavioral Acoustic Emanations: Attack and Verification of PIN Entry Using Keypress Sounds. Sensors. 2020; 20(11):3015. https://doi.org/10.3390/s20113015
Chicago/Turabian StylePanda, Sourav, Yuanzhen Liu, Gerhard Petrus Hancke, and Umair Mujtaba Qureshi. 2020. "Behavioral Acoustic Emanations: Attack and Verification of PIN Entry Using Keypress Sounds" Sensors 20, no. 11: 3015. https://doi.org/10.3390/s20113015
APA StylePanda, S., Liu, Y., Hancke, G. P., & Qureshi, U. M. (2020). Behavioral Acoustic Emanations: Attack and Verification of PIN Entry Using Keypress Sounds. Sensors, 20(11), 3015. https://doi.org/10.3390/s20113015






