Movable Platform-Based Topology Detection for a Geographic Routing Wireless Sensor Network
Abstract
:1. Introduction
2. Background
2.1. Common MAC Protocols
2.2. RSSI Algorithm
2.3. Space Spectrum Estimation
2.4. Location-Based Routing Protocols
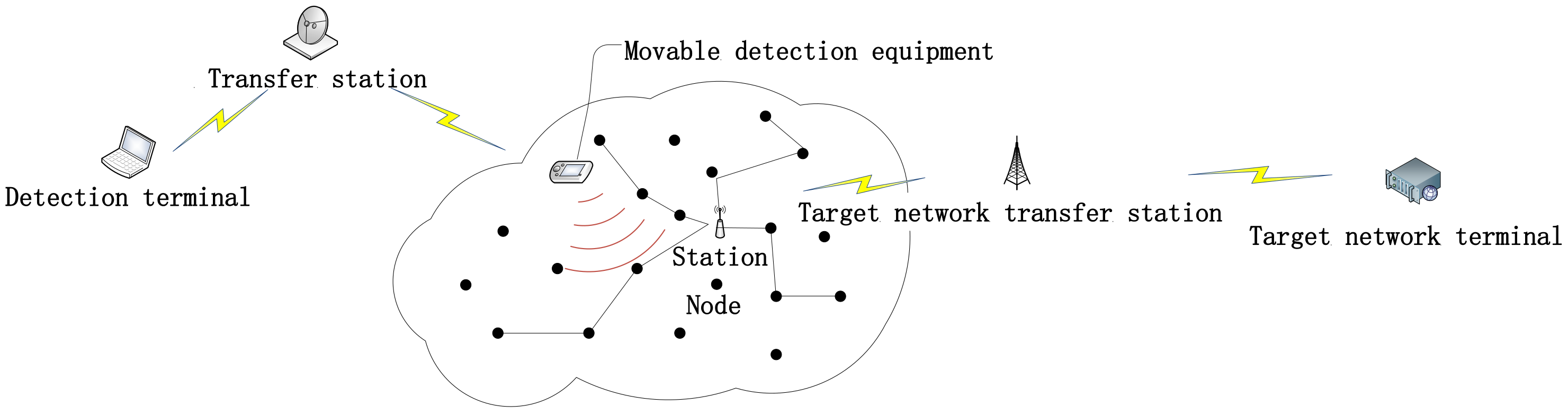
3. Workflow
- Capture node couples. The platform captures air data packets, determines the position of two nodes according to the direction and intensity of the electromagnetic wave that they send out and platform position in the process of data packet sending and receiving, and determines upstream nodes.
- Base address seeking. For the node couples detected, the downstream node and upstream node extension lines (defined as the direction line of node couple) should point at the station in at least one reference direction. The platform moves along the direction line of node couple and should move along the direction of new node couple after it captures node again. It will find station through changing direction line for many times.
- Global sampling. Upon arriving at station, the platform detects node couples and nodes of the whole network centering on the station according to the pre-determined design route.
- Construction of cost parameters. After the platform finishes detection, it will compare the neighbour nodes of midstream, upstream and downstream nodes according to nodes, calculate the range of cost parameter and determine the valuation of cost parameter.
- Reconstruction of network topology. Calculate all node couples of the whole network according to the cost parameters calculated, and re-calculate cost parameters and iterate as per the first result.
- Iteration and correction. Iterate the number of node hops again according to the estimated topology, and update node connection according to detection results and obtain the number of new node hops, iterate cost parameters and construct a new topology.
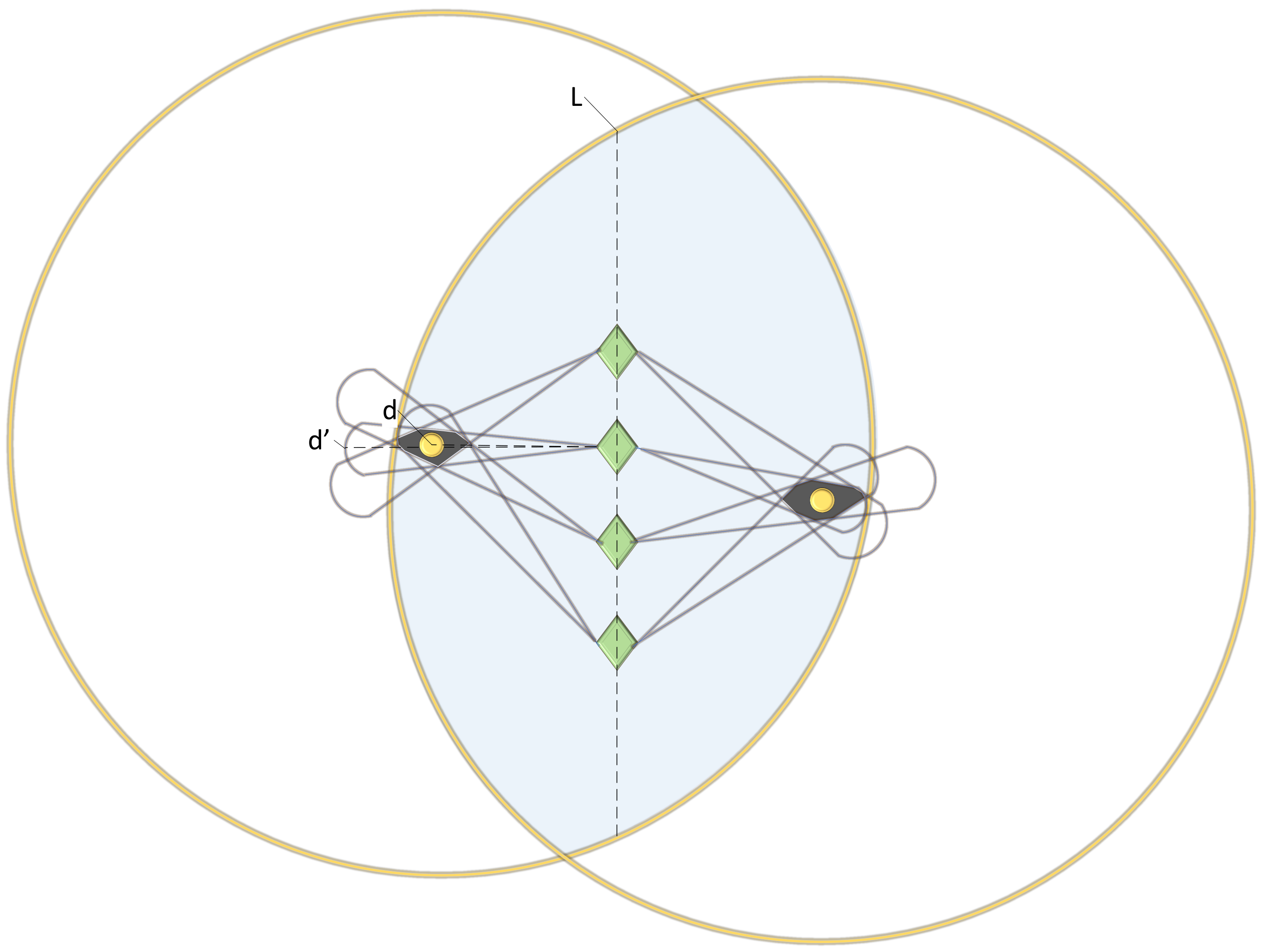
3.1. Node Couple Capture
3.2. Station Address Seeking
3.3. Node Acquisition
3.4. Topology Modeling
3.5. Topology Rebuilding
4. Evaluation
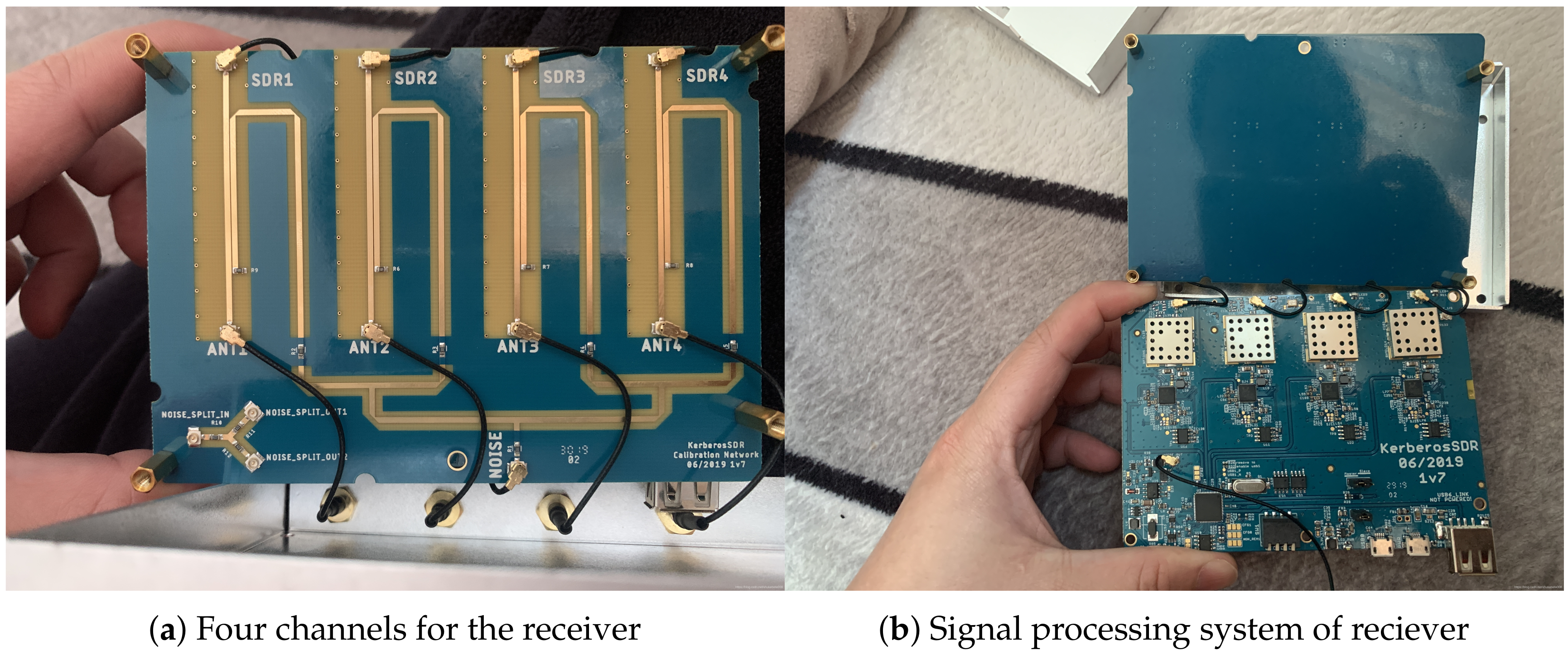
4.1. Experiment Setup
4.2. Setting of Prior Conditions
4.3. Accuracy Measurement
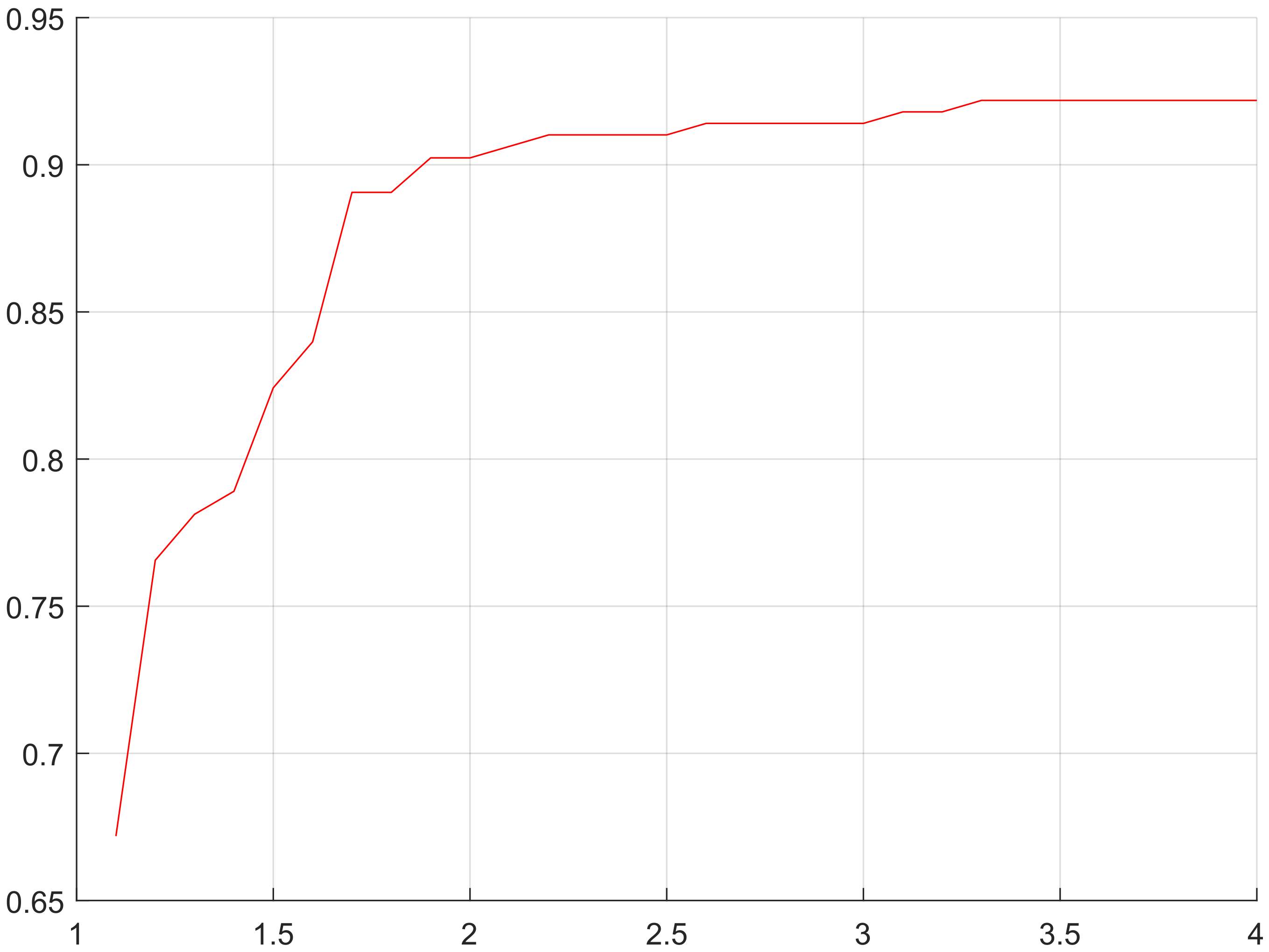
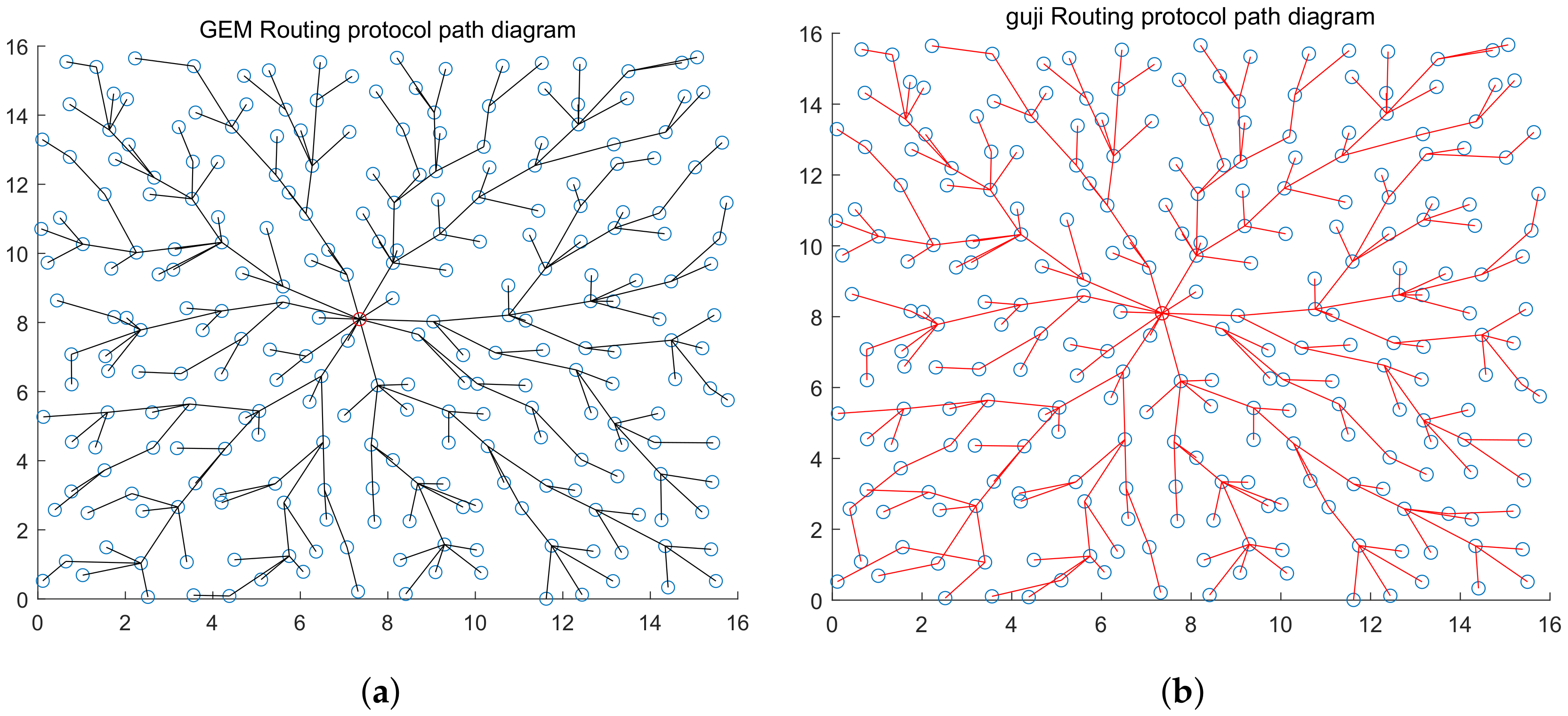
4.3.1. Accuracy of Topology
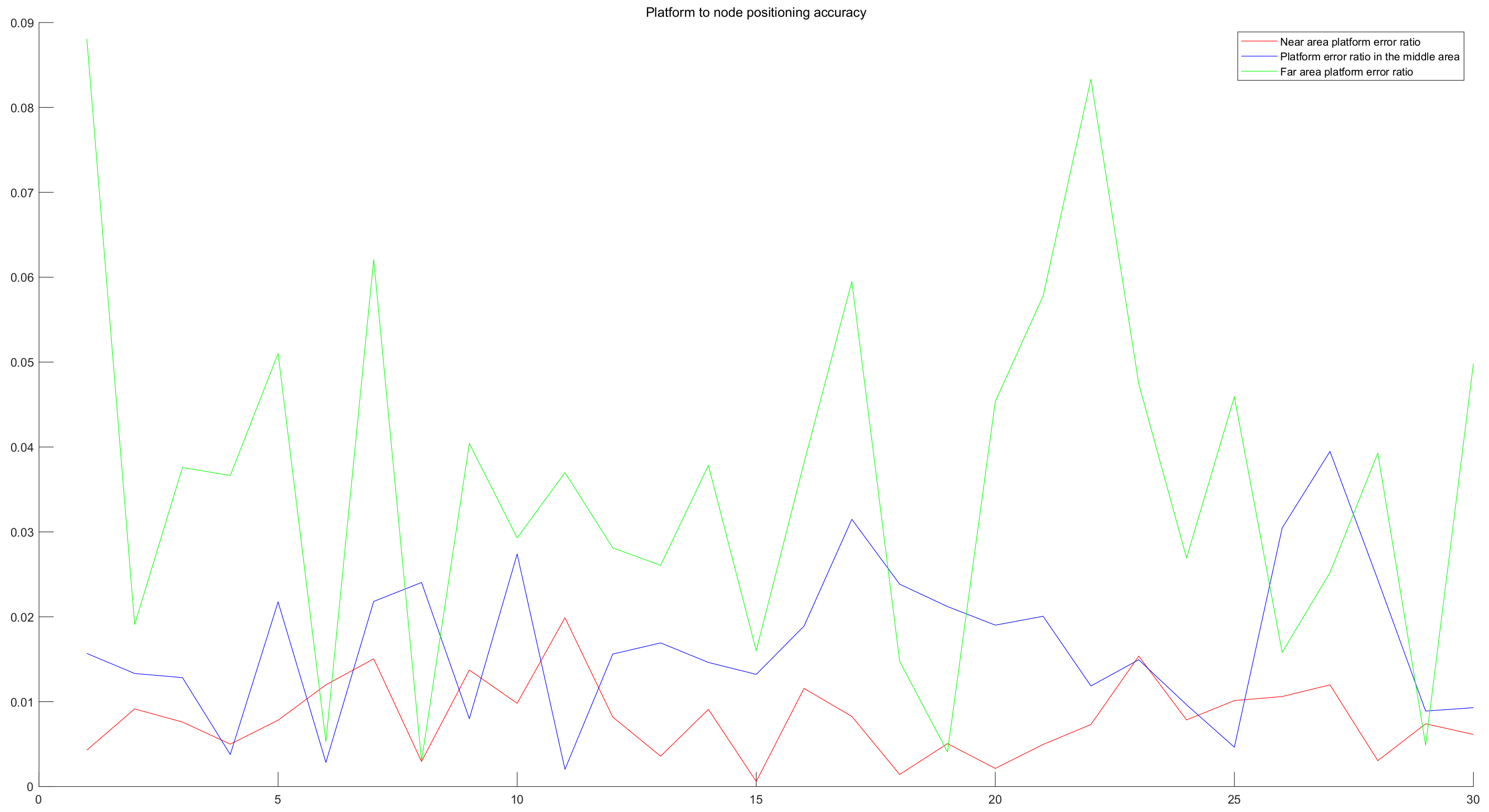
4.3.2. Accuracy of Node Positioning
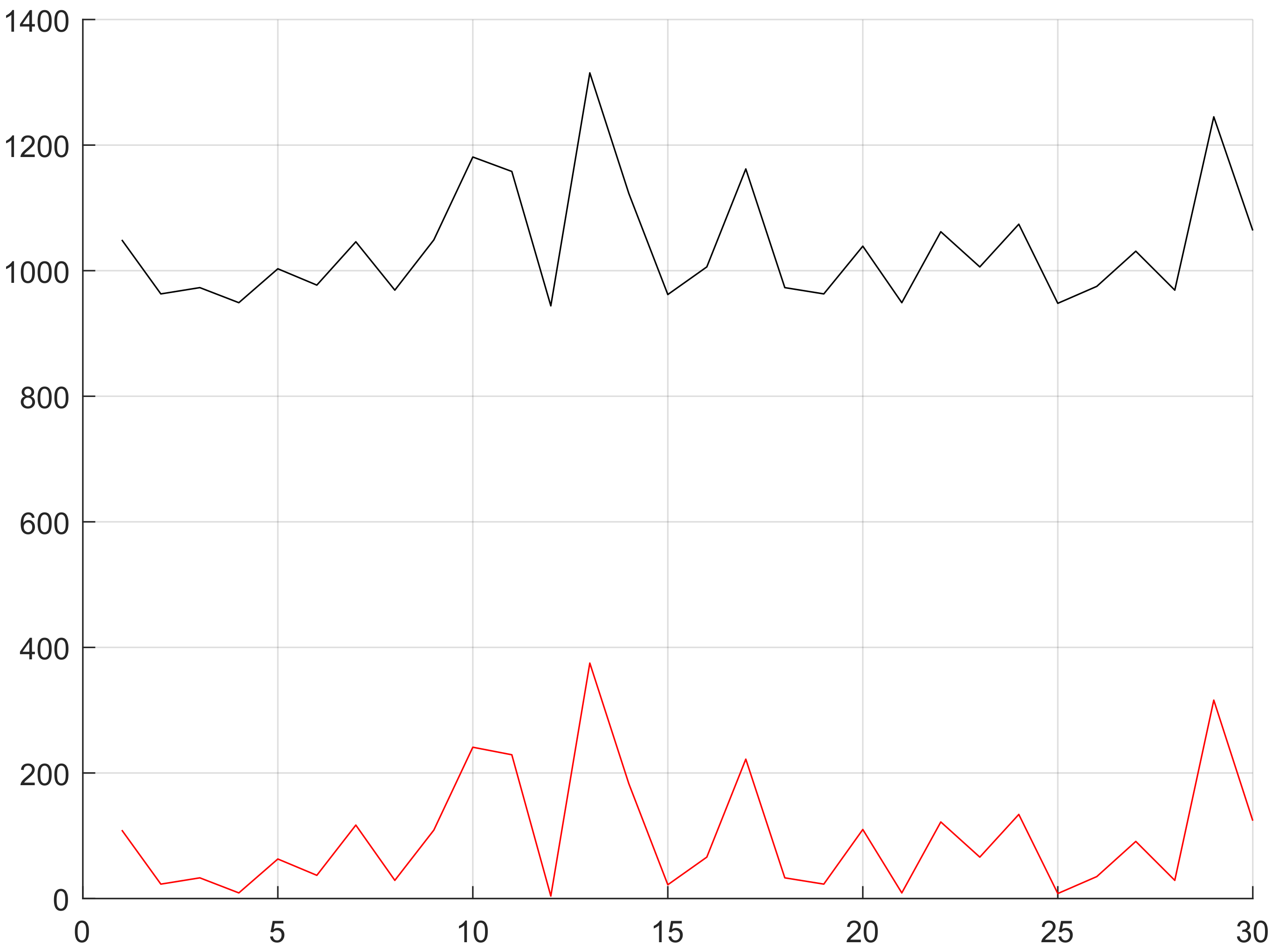
4.4. Performance Measurement
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Baccour, N.; Koubaa, A.; Mottola, L.; Zuniga, M.; Youssef, H.; Boano, C.A.; Alves, M. Radio link quality estimation in wireless sensor networks. ACM Trans. Sens. Netw. 2012, 8, 1–33. [Google Scholar] [CrossRef]
- Chaturvedi, P.; Daniel, A.K. Wireless sensor networks-a survey. In Proceedings of the International Conference on Recent Trends in Information, Telecommunication and Computing, Chandigarh, India, 21 March 2014; pp. 393–422. [Google Scholar]
- Meier, A.; Motani, M.; Siquan, H.; Künzli, S. DiMo: Distributed node monitoring in wireless sensor networks. In Proceedings of the 11th International Symposium on Modeling Analysis and Simulation of Wireless and Mobile Systems, Vancouver, BC, Canada, 27–31 October 2008. [Google Scholar]
- Xiao, J.; Zeng, P.; Yu, H. A survey of testing and debugging testbeds for sensor networks. In Proceedings of the 11th World Congress on Intelligent Control and Automation, Shenyang, China, 29 June–4 July 2014; pp. 150–155. [Google Scholar]
- Baronti, P.; Pillai, P.; Chook, V.W.; Chessa, S.; Gotta, A.; Hu, F. Wireless sensor networks: A survey on the state of the art and the 802.15.4 and ZigBee standards. Comput. Commun. 2007, 30, 1655–1695. [Google Scholar] [CrossRef]
- Ramanathan, N.; Chang, K.; Kapur, R.; Girod, L.; Kohler, E.; Estrin, D. Sympathy for the sensor network debugger. In Proceedings of the 3rd International Conference on Embedded Networked Sensor Systems, San Diego, CA, USA, 2–4 November 2005. [Google Scholar]
- Rost, S.; Balakrishnan, H. Memento: A Health Monitoring System for Wireless Sensor Networks. In Proceedings of the 3rd Annual IEEE Communications Society on Sensor and Ad Hoc Communications and Networks, Reston, VA, USA, 28–28 September 2006; pp. 575–584. [Google Scholar]
- Girod, L.; Ramanathan, N.; Elson, J.; Stathopoulos, T.; Lukac, M.; Estrin, D. Emstar: a software environment for developing and deploying heterogeneous sensor–actuator networks. ACM Trans. Sen. Netw. 2007, 3, 13. [Google Scholar] [CrossRef]
- Levis, P.; Madden, S.; Polastre, J.; Szewczyk, R.; Whitehouse, K.; Woo, A.; Gay, D.; Hill, J.; Welsh, M.; Brewer, E.; et al. TinyOS: An Operating System for Sensor Networks. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2005; pp. 115–148. [Google Scholar]
- Buschmann, C.; Pfisterer, D.; Fischer, S.; Fekete, S.P.; Kröller, A. SpyGlass: A wireless sensor network visualizer. SIGBED Rev. 2005, 2, 1–6. [Google Scholar] [CrossRef]
- Turon, M. MOTE-VIEW: A sensor network monitoring and management tool. In EmNets ’05: Proceedings of the 2nd IEEE Workshop on Embedded Networked Sensors; IEEE Computer Society: Washington, DC, USA, 2005. [Google Scholar]
- Shu, L.; Wu, C.; Zhang, Y.; Chen, J.; Wang, L.; Hauswirth, M. NetTopo: Beyond simulator and visualizer for wireless sensor networks. SIGBED Rev. 2008, 5, 1–8. [Google Scholar] [CrossRef]
- Castillo, J.A.; Ortiz, A.M.; López, V.; Olivares, T.; Orozco-Barbosa, L. WiseObserver: A real experience with wireless sensor networks. In Proceedings of the 3rd ACM workshop on Performance Monitoring and Measurement of Heterogeneous Wireless and Wired Networks, Vancouver, BC, Canada, 27–31 October 2008. [Google Scholar]
- Jurdak, R.; Ruzzelli, A.G.; Barbirato, A.; Boivineau, S. Octopus: monitoring, visualization, and control of sensor networks. Wirel. Commun. Mob. Comput. 2009, 11, 1073–1091. [Google Scholar] [CrossRef] [Green Version]
- Yeo, J.; Youssef, M.; Agrawala, A. A framework for wireless LAN monitoring and its applications. In Proceedings of the 3rd ACM Workshop on Wireless Security, Philadelphia, PA, USA, 1 October 2004. [Google Scholar]
- Cheng, Y.-C.; Bellardo, J.; Benkö, P.; Snoeren, A.C.; Voelker, G.M.; Savage, S. Jigsaw: Solving the puzzle of enterprise 802.11 analysis. SIGCOMM Comput. Commun. Rev. 2006, 36, 39–50. [Google Scholar] [CrossRef]
- Mahajan, R.; Rodrig, M.; Wetherall, D.; Zahorjan, J. Analyzing the MAC-level behavior of wireless networks in the wild. In Proceedings of the 2006 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications; Association for Computing Machinery: New York, NY, USA, 2006. [Google Scholar]
- Chen, B.-R.; Peterson, G.; Mainland, G.; Welsh, M. LiveNet: Using Passive Monitoring to Reconstruct Sensor Network Dynamics. In Distributed Computing in Sensor Systems; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Ringwald, M.; Römer, K. Snif: A Comprehensive Tool for Passive Inspection of Sensor Networks; 6. Fachgespräch Sensornetzwerke; RWTH Aachen University: Aachen, Germany, 2007. [Google Scholar]
- Khan, M.M.H.; Luo, L.; Huang, C.; Abdelzaher, T. SNTS: Sensor Network Troubleshooting Suite. In Distributed Computing in Sensor Systems; Springer: Berlin/Heidelberg, Germany, 2007; pp. 142–157. [Google Scholar]
- Awad, A.; Nebel, R.; German, R.; Dressler, F. On the Need for Passive Monitoring in Sensor Networks. In Proceedings of the 2008 11th EUROMICRO Conference on Digital System Design Architectures, Methods and Tools, Parma, Italy, 3–5 September 2008; pp. 693–699. [Google Scholar]
- Beutel, J.; Dyer, M.; Meier, L.; Thiele, L. Scalable topology control for deployment-support networks. In Proceedings of the IPSN 2005. Fourth International Symposium on Information Processing in Sensor Networks, Boise, ID, USA, 15–15 April 2005; pp. 359–363. [Google Scholar]
- Kuang, X.; Shen, J. SNDS: A Distributed Monitoring and Protocol Analysis System for Wireless Sensor Network. In Proceedings of the 2010 Second International Conference on Networks Security, Wireless Communications and Trusted Computing, Wuhan, China, 24–25 April 2010; pp. 422–425. [Google Scholar]
- Zhao, Z.; Huangfu, W.; Sun, L. NSSN: A network monitoring and packet sniffing tool for wireless sensor networks. In Proceedings of the 2012 8th International Wireless Communications and Mobile Computing Conference (IWCMC), Limassol, Cyprus, 27–31 August 2012; pp. 537–542. [Google Scholar]
- Garcia, F.P.; Andrade, R.M.C.; Oliveira, C.T.; De Souza, J.N. EPMOSt: An Energy-Efficient Passive Monitoring System for Wireless Sensor Networks. Sensors 2014, 14, 10804–10828. [Google Scholar] [CrossRef] [PubMed]
- Afroz, F.; Braun, R. Energy-efficient MAC protocols for wireless sensor networks: A survey. Int. J. Sens. Netw. 2020, 32, 150–173. [Google Scholar] [CrossRef]
- Khanafer, M.; Guennoun, M.; Mouftah, H.T. A Survey of Beacon-Enabled IEEE 802.15.4 MAC Protocols in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2013, 16, 856–876. [Google Scholar] [CrossRef]
- Mistry, H.P.; Mistry, N.H. RSSI Based Localization Scheme in Wireless Sensor Networks: A Survey. In Proceedings of the 2015 Fifth International Conference on Advanced Computing & Communication Technologies, Haryana, India, 21–22 February 2015; pp. 647–652. [Google Scholar]
- Chen, Z.; Gokeda, G.; Yu, Y. Introduction to Direction-of-Arrival Estimation; Artech House: Norwood, MA, USA, 2010. [Google Scholar]
- Khan, Z.I.; Kamal, M.M.; Hamzah, N.; Othman, K.; Khan, N.I. Analysis of performance for multiple signal classification (MUSIC) in estimating direction of arrival. In Proceedings of the 2008 IEEE International RF and Microwave Conference, Kuala Lumpur, Malaysia, 2–4 December 2008; pp. 524–529. [Google Scholar]
- Roy, R.; Kailath, T. ESPRIT-estimation of signal parameters via rotational invariance techniques. IEEE Trans. Signal Process. 1989, 37, 984–995. [Google Scholar] [CrossRef] [Green Version]
- Kondaiah, K.; Babu, R.B.; Umar, S. A Study on Routing Protocols in Wireless Sensor Networks. Int. J. Comput. Sci. Eng. Technol. 2013, 3, 94. [Google Scholar]
- Yu, Y.; Govindan, R.; Estrin, D. Geographical and Energy Aware Routing: A Recursive Data Dissemination Protocol for Wireless Sensor Networks; Technical Report; UCLA Computer Science Department: Los Angeles, CA, USA, 2001. [Google Scholar]
- Newsome, J.; Song, D. GEM: Graph Embedding for routing and data-centric storage in sensor networks without geographic information. In Proceedings of the 1st ACM Conf on Embedded Networked Sensor Systems (SenSys’03), Los Angeles, CA, USA, 5–7 November 2003. [Google Scholar]
- Chuku, N.; Nasipuri, A. Performance evaluation of an RSSI based localization scheme for wireless sensor networks to mitigate shadowing effects. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 3124–3129. [Google Scholar]











© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, R.; Wang, J.; Chen, J. Movable Platform-Based Topology Detection for a Geographic Routing Wireless Sensor Network. Sensors 2020, 20, 3726. https://doi.org/10.3390/s20133726
Li R, Wang J, Chen J. Movable Platform-Based Topology Detection for a Geographic Routing Wireless Sensor Network. Sensors. 2020; 20(13):3726. https://doi.org/10.3390/s20133726
Chicago/Turabian StyleLi, Runzhi, Jian Wang, and Jiongyi Chen. 2020. "Movable Platform-Based Topology Detection for a Geographic Routing Wireless Sensor Network" Sensors 20, no. 13: 3726. https://doi.org/10.3390/s20133726



