Recent Analysis of Forged Request Headers Constituted by HTTP DDoS
Abstract
:1. Introduction
1.1. Signature-Based Detection
1.2. Anomaly-Based Detection
1.3. Hybrid-Based Detection
2. Contribution of the Paper
- Eight forged request header patterns produced by HTTP DDoS have been revealed through extensive analysis by adopting actual HTTP DDoS attack scripts. Critical analysis has been made to acquire similarities and differences and a summary of the request header patterns.
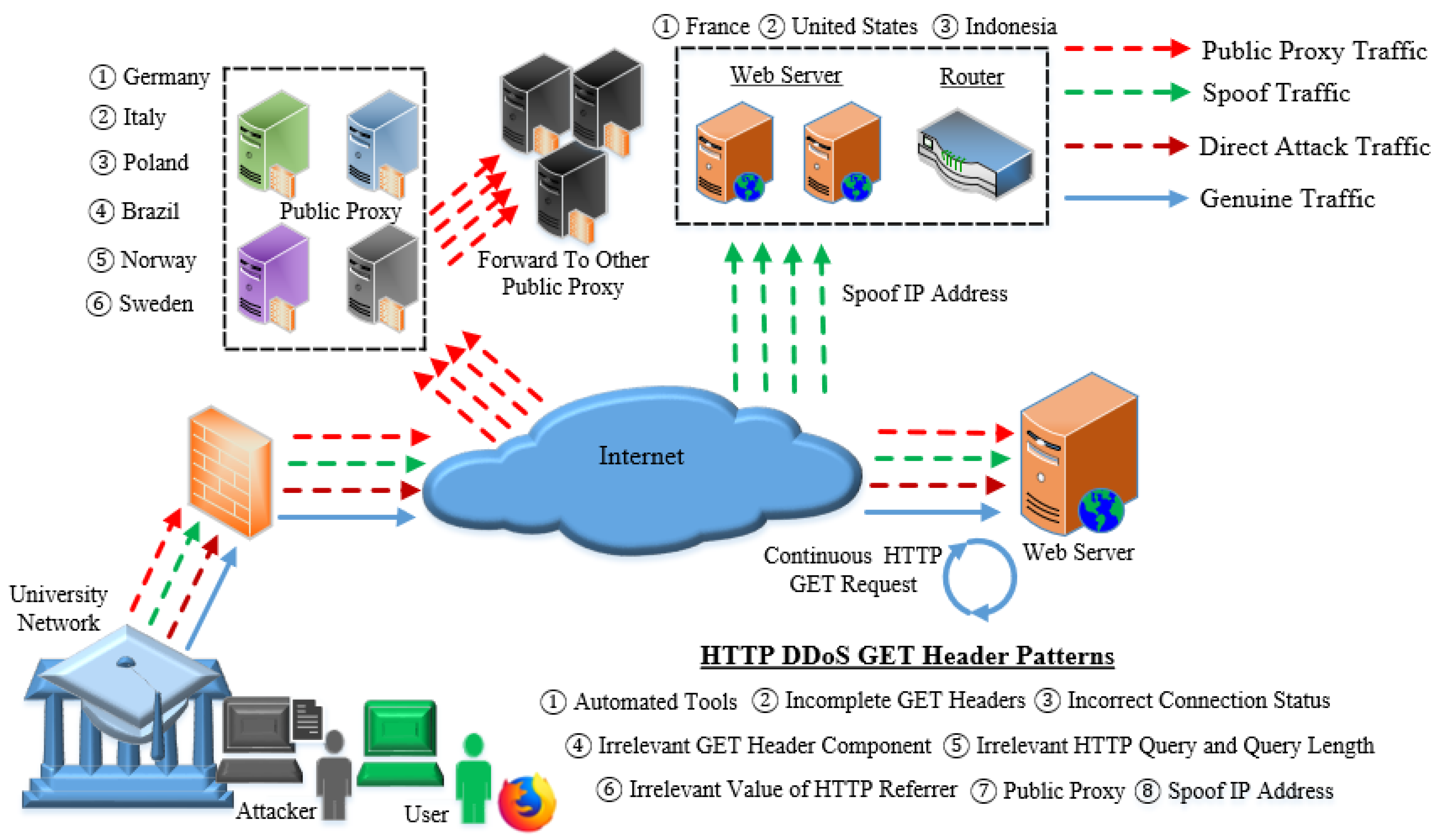
- The HTTP DDoS architecture has been introduced based on the usage of eight actual attack scripts. The attack scripts have been adapted to have different attack strategies which are capable of executing HTTP DDoS through Direct Attack, Proxy, and Spoof IP address.
- A taxonomy of HTTP DDoS attack patterns has been created by incorporating forged request headers noted by prior studies with false request headers unveiled in this study.
- A recent attack script to execute HTTP DDoS has been assigned to the existing attack strategy suggested by prior studies.
3. DDoS Attack at the Application Layer
4. DDoS Attack Strategy at Application Layer
- Server Load: Attacker uses botnet to continuously send malicious request against a web server aggressively, which will lead to the server to drop legitimate request as the resources of the web servers are running out.
- Increasing: Attacker uses low request value to initiate an attack and slowly increasing the value. This behavior of attack is difficult to detect as malicious HTTP traffic is not sent aggressively to a victim’s server during the occurrence of the attack.
- Constant: To perform this attack strategy, cyber intruders must specify a specific number of request rate to be sent to the victim’s HTTP web server. The request number is referred to as constant, which will be the same as when the botnet sends a malicious request to a web server. Commonly, the request rate is between 100, 200 and 300 per second.
- Single Web Pages Attack: Attacker uses any single web page that belongs to a website. The botnet is commanded by the attacker, which will continuously send malicious HTTP requests to web server.
- Main Page Attack: Cyber intruders specifically focus on the main page of the websites to deny legitimate users from getting any access. To generate an attack, traffic botnet will be used to repeatedly send a malicious request to a web server. The impact of this attack only occurs on the main page of the website, while the subpages of the website are not affected.
- Dominant Page Attack: This category refers to a web page with a greater interest for authentic users to access. The attacker then focuses on that particular page to embark HTTP DDoS attack to prevent a legitimate user from browsing the contents of the web pages. This attack only gives an impact on web pages that have a greater interest for users to browse.
- Multiple Page Attack: A cyber attacker will initiate the attack at multiple web pages from a website. The purpose of this technique is to avoid detection as the malicious HTTP request will imitate the human access pattern. For instance, humans will open more than one web page to find information while surfing websites. When the attack occurs, more than one of the existing web pages will not be accessible as the attacker is interested in targeting multiple web pages.
- Reply Flood Attack: The botnet command by the attacker sends an HTTP traffic at an inflated rate to gain a resource of the web server to prevent web server from surfing legitimate HTTP request. The attacks work by gaining human access patterns to prohibit the detection system from blocking the malicious request.
- Random Attack: All web pages that belong to a website are not accessible regardless of its category.
- Rare Change Page Attack: The common structure of a web system will group a page into a specific group to make the page content more structured and user friendly. Since the arrangement of the web page is grouped, an attacker may compromise the group page by commanding botnet to the web page. Hence, the group web page will be the most targeted pages. Consequently, this attack will prevent a user from opening a web page that belongs to a specific group.
- Frequent Change Attack: An attacker performs an attack on a web page that belongs to different categories. This attack will rotate and send a malicious request to distinct web page categories. This attack only affects specific categories of the website. When the attack occurs, other web pages can still be accessed as usual.
- Hot Pages Attack: Each web-based system will have frequent open pages. Hence, this situation will give an opportunity for cyber intruders to initiate the attack on the most visited pages to prevent legitimate users from accessing as the main objective for a DDoS attack is to avoid users from opening the pages.
- Web Proxy Attack: Attackers use a proxy server as a representative to generate attack traffic. The use of a proxy server to generate attack traffic will cause difficulties in detecting the source of the attack. Multiple proxy servers would be used to generate plenty of HTTP requests to overwhelm the web server.
5. HTTP Manipulation
6. HTTP DDoS Request Headers
6.1. HTTP DDoS Request Headers (Session Flooding and Request Flooding)
6.2. HTTP DDoS Request Headers (Slow Rate)
7. Analysis of Forged Request Headers
8. Materials and Methods
9. Execute Attack Scripts
9.1. Analysis 1–Attack.py
9.2. Analysis 2–Chihulk.py
9.3. Analysis 3–High Orbit Ion Cannon (HOIC)
9.4. Analysis 4–Golden Eye.py
9.5. Analysis 5–BlackHorizon.py
9.6. Analysis 6–Wreckuests.py
9.7. Analysis 7–Hibernet.py
9.8. Analysis 8–UFONet.py
10. Overview of Critical Analysis
10.1. GET Header-User-Agent
10.2. GET Header–Request Query
10.3. GET Header-Referral
10.4. GET Header-Connection and Accept Language
10.5. Proxy Headers and IP Spoofing
11. Results
- Automated Tools: HTTP DDoS attack requires enormous HTTP requests to overwhelm web servers. Hence, attackers are required to adopt automated tools to generate massive requests which only require a minimal duration to create forged request traffics. A massive GET requests received results in the web server to become unresponsive due to overloading as it reaches beyond its capacity to process HTTP request.
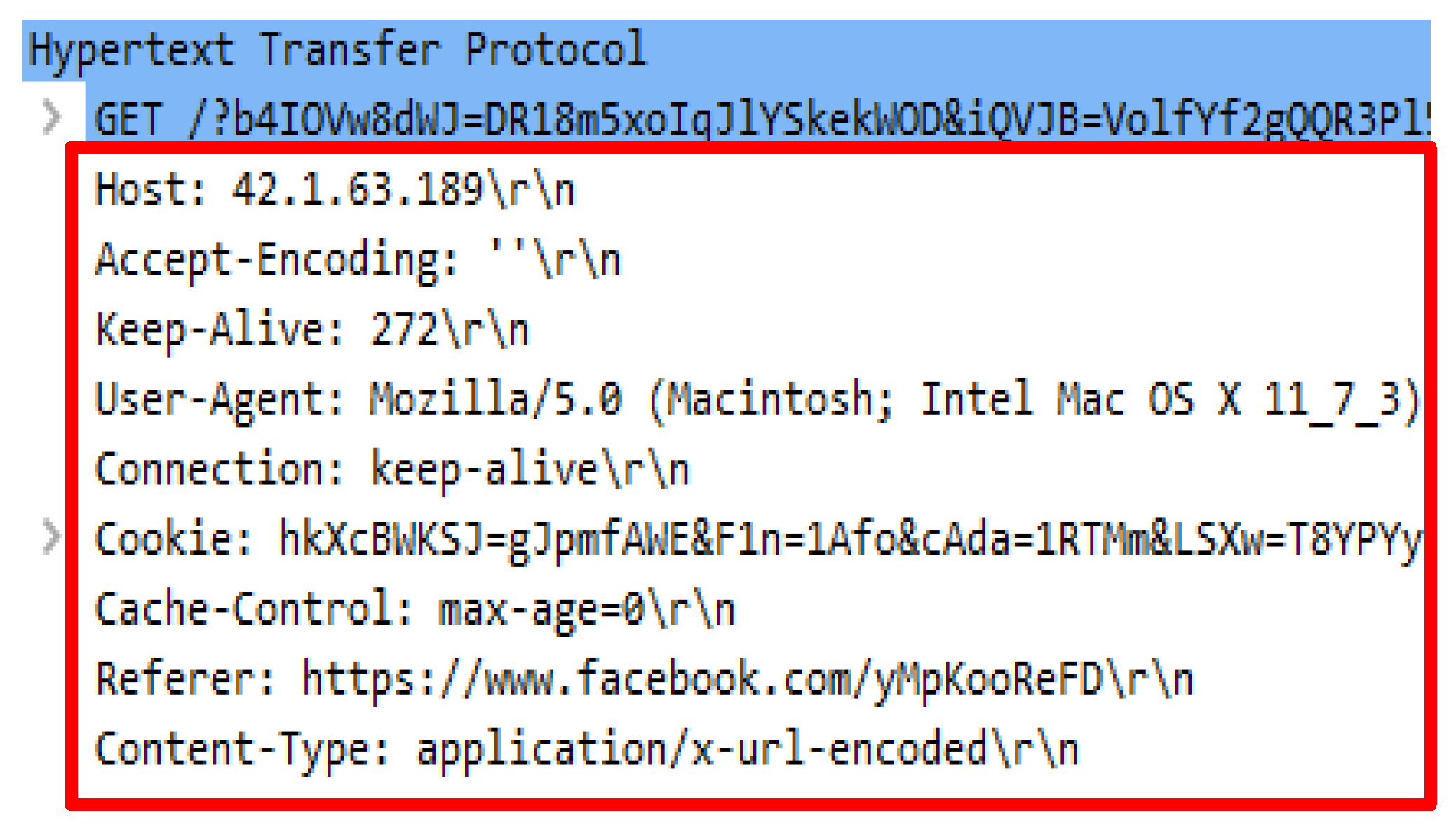
- Incomplete Request Headers: HTTP DDoS attacks generate an incomplete request header as it is unnecessary to supply complete headers as the purpose of the attack is to gain a server’s resources to cause the web server to be unresponsive. Attackers are able to generate substantial HTTP requests without a request header. However, to create complexities in detecting the attack, attackers must supply the request headers to emulate user’s access pattern to avoid from being detected.
- Incorrect Connection Status: The connection status header in an HTTP request presents the status of the client which has an active connection with a web server. However, during an occurrence of HTTP DDoS attack, the status is marked as close with continuous HTTP requests received. Apart from that, the existence of Keep-Alive in the request header is a sign of HTTP DDoS as it is not the header for an HTTP request.
- Irrelevant Request Header Component: The existence of request headers in an HTTP request has been explained in the request for comments (RFC) which is hosted by the Internet Engineering Task Force (IETF). Hence, the appearance of non-standard request headers in a repeated HTTP request provides a strong indicator that the source of the request originates from an attacker.
- Irrelevant Request Query and Query Length: A client will search for information that relates to the web server’s content and adopts a human language. This search will then be translated into a request query to forward the search to the web server to be processed. An HTTP DDoS attack emulates this process by creating a request query which contains either special characters such as ‘!’, ‘@’, ‘#’, ‘$’, and ‘^’ or a longer query.
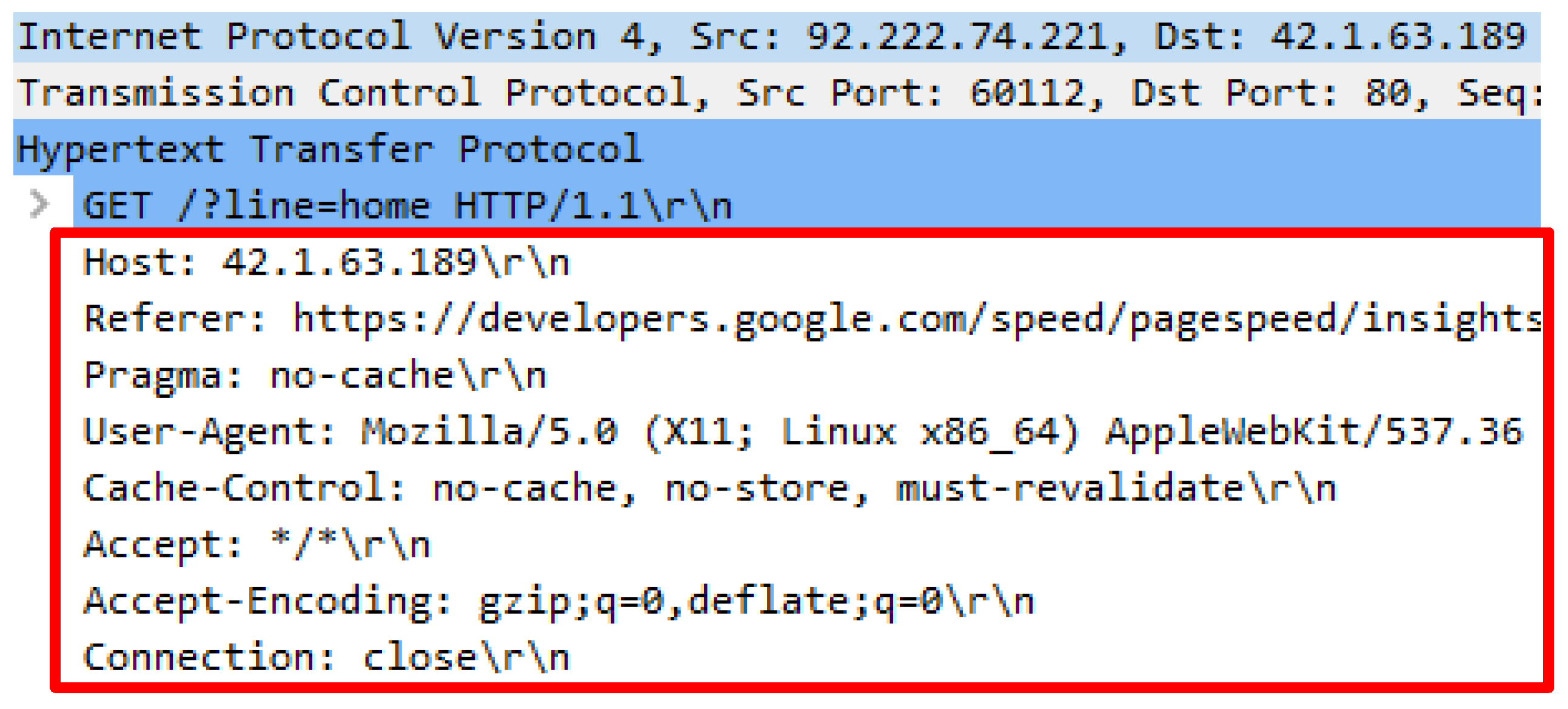
- Irrelevant Value for HTTP Referrer: The value for HTTP referrer is the previous URL accessed by a user. An HTTP DDoS attack is capable of mimicking this operation by attaching a valid URL. Although the attack is able to supply the valid URL, it is irrelevant to be the referrer of the current web page or website. A genuine request will indicate that the source of the referral must come from valid resources.
- False Proxy Header: The existence of a public proxy that can be utilized freely causes the service to be misused by attackers to execute HTTP DDoS attacks. Besides, there is no restriction to adopt the public proxy which further increases attackers’ capability to launch attacks without being detected. HTTP DDoS attacks launched through a public proxy deliver inconsistent proxy headers that pose difficulties in recognizing whether the source of a request originates from proxy or directly from the client as well as in detecting whether the source request was legitimate or malicious.
- Spoof IP Address: An attacker utilizes a spoof IP address to execute HTTP DDoS attack to conceal the activity of overwhelming a web server. The analysis conducted in Section 9.6 indicates that the Wreckuests.py attack script adopted several machines and used public IP addresses with an attachment of proxy headers to make the source request to appear as if they originate from a proxy. The execution of this attack script provides a significant finding with regards to HTTP DDoS attack strategy discussed earlier in Section 4.
12. Attack Category Associated with Real HTTP DDoS
13. Conclusions
14. Future Work
15. Possible Solutions and Open Issues
- (a)
- Development of a web browser without adopting secure socket layers to encrypt the GET header and its value to prevent header manipulation.
- (b)
- Analysis of other devices acted as botnets which come from IoT devices to observe the forged GET header patterns.
- (c)
- Execution of HTTP DDoS through HTTPS protocol and HTTP version 2 to explore the possible GET header manipulation.
- (d)
- Development of new standards to reject HTTP request originating from a non-browser as done by HTTP DDoS adopted attack scripts to generate substantial requests.
- (a)
- The appearance of HTTP DDoS as the service increases the occurrence of the attack and becomes simpler to be executed.
- (b)
- The existence of public proxies scattered around the world that provides opportunity for cyber intruders to utilize the service to launch HTTP DDoS attacks. The usage of proxies to execute HTTP DDoS increases the complexity to trace the source of the request. Besides that, the usage of proxies does not require any authentication which allows both genuine users and attackers to adopt the same proxy.
- (c)
- A web server accepts any requestor without performing an inspection of the platform’s source such as whether it comes through scripting, tools or web browsers. A web server is supposed to be more selective when accepting eligible clients to be connected to a web server to gain access to the web server’s content.
- (d)
- The structure of the HTTP protocol allows the request headers and its data to be edited which leads to manipulation of request headers. A restriction should be applied to allow only specific request headers to prevent any header manipulation executed by attackers.
- (e)
- The request header presented in HTTP request transaction should take note of the requestor information such as the web browser’s name, language, operating system, etc. However, these headers are not compulsory to appear in each HTTP request transaction. Due to this circumstance, attackers are only required to generate an HTTP request without having any request header to overwhelm a web server. Besides, attackers often adopt request headers to make the header to appear authentic which lead to further complication in detecting both the DDoS and the authenticity of the request at the application layer.
- (f)
- The existence of attack tools and scripts available on the Internet allows an HTTP DDoS to be easily executed. The appearance to the attack script provides an opportunity for researchers in conducting further research. However, the same attack script could also be adopted by an attacker as a medium to launch an attack.
- (g)
- The proxy provider adopted a distinct name to indicate that a HTTP request originates from a proxy. The usage of a different name for a proxy header leads to confusion. Besides, the same proxy is likely to be adopted by both an authentic client and an attacker to access the same web server.
- (h)
- A high-speed Internet delivers an advantage to users to browse online contents. However, the Internet speed provides a significant impact to substantial amount of HTTP requests that can be generated through a single requestor within a specific time period.
- (i)
- The attack scripts adopted in this research were publicly available and are compulsory to be executed in the real network. A researcher requires a sound technical skill to configure those devices to simulate the attack in the Local Area Network (LAN) or Wide Area Network (WAN). The impact of an attack executed in the WAN network requires a higher attention as the Internet Service Provider (ISP) has possibly blocked the traffic therefore jeopardizing the research results.
- (j)
- The development of a defense system which utilizes either signature-based, anomaly-based and hybrid detection methods must be selected with precaution as each detection method has its own strengths and limitations.
Author Contributions
Funding
Conflicts of Interest
References
- Behal, S.; Kumar, K. Trends in validation of DDoS research. In International Conference on Computational Modeling and Security (CMS 2016); Elsevier: Amsterdam, The Netherlands, 2016; Volume 85, pp. 7–15. [Google Scholar]
- Jazi, H.H.; Gonzalez, H.; Stakhanova, N.; Ghorbani, A.A. Detecting HTTP-based application layer DoS attacks on web servers in the presence of sampling. Comput. Netw. 2017, 121, 25–36. [Google Scholar] [CrossRef]
- Singh, K.; Singh, P.; Kumar, K. Application layer HTTP-GET flood DDoS attacks: Research landscape and challenges. Comput. Secur. 2017, 65, 344–372. [Google Scholar] [CrossRef]
- Behal, S.; Kumar, K. Detection of DDoS attacks and flash events using novel information theory metrics. Comput. Netw. 2017, 116, 96–110. [Google Scholar] [CrossRef]
- Dhanapal, A.; Nithyanandam, P. An effective mechanism to regenerate HTTP flooding DDoS attack using real time data set. In Proceedings of the 2017 International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), Kannur, India, 6–7 July 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 570–575. [Google Scholar]
- Singh, K.; Singh, P.; Kumar, K. User behavior analytics-based classification of application layer HTTP-GET flood attacks. J. Netw. Comput. Appl. 2018, 112, 97–114. [Google Scholar] [CrossRef]
- Prasad, K.M.; Reddy, A.R.M.; Rao, K.V. BIFAD: Bio-Inspired Anomaly Based HTTP-Flood Attack Detection. Wirel. Pers. Commun. 2017, 97, 281–308. [Google Scholar] [CrossRef]
- Zargar, S.T.; Joshi, J.; Tipper, D. A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE Commun. Surv. Tutor. 2013, 15, 2046–2069. [Google Scholar] [CrossRef] [Green Version]
- Kumar, V.; Kumar, K. Classification of DDoS attack tools and its handling techniques and strategy at application layer. In Proceedings of the 2016 International Conference on Advances in Computing, Communication, & Automation (ICACCA) (Fall), Bareilly, India, 30 September–1 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar]
- Osanaiye, O.; Choo, K.-K.R.; Dlodlo, M. Distributed denial of service (DDoS) resilience in cloud: Review and conceptual cloud DDoS mitigation framework. J. Netw. Comput. Appl. 2016, 67, 147–165. [Google Scholar] [CrossRef]
- Ye, J.; Cheng, X.; Zhu, J.; Feng, L.; Song, L. A DDoS Attack Detection Method Based on SVM in Software Defined Network. Secur. Commun. Netw. 2018, 2018, 1–8. [Google Scholar] [CrossRef]
- Gu, Y.; Wang, Y.; Yang, Z.; Xiong, F.; Gao, Y. Multiple-Features-Based Semisupervised Clustering DDoS Detection Method. Math. Probl. Eng. 2017, 2017, 1–10. [Google Scholar] [CrossRef] [Green Version]
- Cheng, J.; Li, M.; Tang, X.; Sheng, V.S.; Liu, Y.; Guo, W. Flow Correlation Degree Optimization Driven Random Forest for Detecting DDoS Attacks in Cloud Computing. Secur. Commun. Netw. 2018, 2018, 1–14. [Google Scholar] [CrossRef]
- Myint, O.M.; Kamolphiwong, S.; Kamolphiwong, T.; Vasupongayya, S. Advanced Support Vector Machine- (ASVM-) Based Detection for Distributed Denial of Service (DDoS) Attack on Software Defined Networking (SDN). J. Comput. Netw. Commun. 2019, 2019, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Cepheli, O.; Buyukcorak, S.; Karabulut Kurt, G. Hybrid Intrusion Detection System for DDoS Attacks. J. Electr. Comput. Eng. 2016, 2016, 1–8. [Google Scholar] [CrossRef] [Green Version]
- Suroto, S. A review of defense against slow HTTP attack. JOIV Int. J. Inform. Vis. 2017, 1, 127–134. [Google Scholar] [CrossRef] [Green Version]
- Yevsieieva, O.; Helalat, S.M. Analysis of the impact of the slow HTTP DOS and DDOS attacks on the cloud environment. In Proceedings of the 2017 4th International Scientific-Practical Conference Problems of Infocommunications. Science and Technology (PIC S&T), Kharkiv, Ukraine, 10–13 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 519–523. [Google Scholar]
- Nithyanandam, P.; Dhanapal, A. The Slow HTTP Distributed Denial of Service Attack Detection in Cloud. Scalable Comput. Pract. Exp. 2019, 20, 285–298. [Google Scholar]
- Subramanian, K.; Gunasekaran, P.; Selvaraj, M. Two Layer Defending Mechanism against DDoS Attacks. Int. Arab J. Inf. Technol. (IAJIT) 2015, 12, 317–324. [Google Scholar]
- Hoque, N.; Bhattacharyya, D.K.; Kalita, J.K. Botnet in DDoS Attacks: Trends and Challenges. IEEE Commun. Surv. Tutor. 2015, 17, 2242–2270. [Google Scholar] [CrossRef]
- Beitollahi, H.; Deconinck, G. ConnectionScore: A statistical technique to resist application-layer DDoS attacks. J. Ambient Intell. Humaniz. Comput. 2013, 5, 425–442. [Google Scholar] [CrossRef]
- Wang, J.; Yang, X.; Zhang, M.; Long, K.; Xu, J. HTTP-SoLDiER: An HTTP-flooding attack detection scheme with the large deviation principle. Sci. China Inf. Sci. 2014, 57, 1–15. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Y.; Zhang, W.; Feng, Y.; Yu, B. A Classification Detection Algorithm Based on Joint Entropy Vector against Application-Layer DDoS Attack. Secur. Commun. Netw. 2018, 2018, 1–8. [Google Scholar] [CrossRef]
- Niakanlahiji, A.; Chu, B.-T.; Al-Shaer, E. PhishMon: A machine learning framework for detecting phishing webpages. In Proceedings of the 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Miami, FL, USA, 9–11 November 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 220–225. [Google Scholar]
- Gahagan, I.V.J.; Bhansali, D.; Gratian, M.; Cukier, M. A comprehensive evaluation of http header features for detecting malicious websites. In Proceedings of the 2019 15th European Dependable Computing Conference (EDCC), Naples, Italy, 17–20 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 75–82. [Google Scholar]
- Tyson, G.; Huang, S.; Cuadrado, F.; Castro, I.; Perta, V.C.; Sathiaseelan, A.; Uhlig, S. Exploring http header manipulation in-the-wild. In Proceedings of the 2017 26th International Conference on World Wide Web, Perth, Australia, 3–7 April 2017; pp. 451–458. [Google Scholar]
- Mansoori, M.; Hirose, Y.; Welch, I.; Choo, K.-K.R. Empirical analysis of impact of HTTP referer on malicious website behaviour and delivery. In Proceedings of the 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 23–25 March 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 941–948. [Google Scholar]
- Xu, F.; Pan, H.; Cao, Z.; Li, Z.; Xiong, G.; Guan, Y.; Yiu, S.-M. Identifying malware with HTTP content type inconsistency via header-payload comparison. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–7. [Google Scholar]
- Liu, S.; Wang, J.; Wang, H.; Wang, H.; Liu, Y. WRT: Constructing users’ web request trees from http header logs. In Proceedings of the ICC 2019 International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7. [Google Scholar]
- La, V.H.; Fuentes, R.; Cavalli, A.R. Network monitoring using mmt: An application based on the user-agent field in http headers. In Proceedings of the 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 23–25 March 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 147–154. [Google Scholar]
- Niu, W.; Li, T.; Zhang, X.; Hu, T.; Jiang, T.; Wu, H. Using XGBoost to Discover Infected Hosts Based on HTTP Traffic. Secur. Commun. Netw. 2019, 2019. [Google Scholar] [CrossRef] [Green Version]
- Saleh, M.A.; Manaf, A.A. A Novel Protective Framework for Defeating HTTP-Based Denial of Service and Distributed Denial of Service Attacks. Sci. World J. 2015, 2015, 238230. [Google Scholar] [CrossRef] [PubMed]
- Yadav, S.; Selvakumar, S. Detection of application layer DDoS attack by modeling user behavior using logistic regression. In Proceedings of the 2015 4th International Conference on Reliability, Infocom Technologies and Optimization (ICRITO) (Trends and Future Directions), Noida, India, 2–4 September 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–6. [Google Scholar]
- Aceto, G.; Pescape, A. Internet censorship detection: A survey. Comput. Netw. 2015, 83, 381–421. [Google Scholar] [CrossRef]
- Sree, T.R.; Bhanu, S.M.S. HADM: Detection of HTTP GET flooding attacks by using Analytical hierarchical process and Dempster-Shafer theory with MapReduce. Secur. Commun. Netw. 2016, 9, 4341–4357. [Google Scholar] [CrossRef]
- Bravo, S.; Mauricio, D. DDoS attack detection mechanism in the application layer using user features. In Proceedings of the 2018 International Conference on Information and Computer Technologies (ICICT), DeKalb, IL, USA, 23–25 March 2018; pp. 97–100. [Google Scholar]
- Sreeram, I.; Vuppala, V.P.K. HTTP flood attack detection in application layer using machine learning metrics and bio inspired bat algorithm. Appl. Comput. Inform. 2017. [Google Scholar] [CrossRef]
- Liao, Q.; Li, H.; Kang, S.; Liu, C. Application layer DDoS attack detection using cluster with label based on sparse vector decomposition and rhythm matching. Secur. Commun. Netw. 2015, 8, 3111–3120. [Google Scholar] [CrossRef]
- Dhanapal, A.; Nithyanandam, P. An OpenStack based cloud testbed framework for evaluating HTTP flooding attacks. Wirel. Netw. 2019. [Google Scholar] [CrossRef]
- Rahman, R.; Tomar, D.S.; Jijin, A.V.J. Application Layer DDOS Attack Detection Using Hybrid Machine Learning Approach. Int. J. Secur. Appl. 2017, 11, 85–96. [Google Scholar] [CrossRef]
- Ghafar, A.J.; Shahidan, M.A.; Adli, S. Review of Recent Detection Methods for HTTP DDoS Attack. J. Comput. Netw. Commun. 2019, 2019, 1–10. [Google Scholar]
- Idhammad, M.; Afdel, K.; Belouch, M. Detection System of HTTP DDoS Attacks in a Cloud Environment Based on Information Theoretic Entropy and Random Forest. Secur. Commun. Netw. 2018, 2018, 1–13. [Google Scholar] [CrossRef] [Green Version]
- Singh, K.J.; Thongam, K.; De, T. Entropy-Based Application Layer DDoS Attack Detection Using Artificial Neural Networks. Entropy 2016, 18, 350. [Google Scholar] [CrossRef]
- Shiaeles, S.N.; Papadaki, M. FHSD: An Improved IP Spoof Detection Method for Web DDoS Attacks. Comput. J. 2014, 58, 892–903. [Google Scholar] [CrossRef] [Green Version]
- Hameed, S.; Ali, U. HADEC: Hadoop-based live DDoS detection framework. EURASIP J. Inf. Secur. 2018, 2018, 11. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Mekky, H.; Zhang, Z.L.; Torres, R.; Lee, S.J.; Tongaonkar, A.; Mellia, M. Detecting malicious activities with user-agent-based profiles. Int. J. Netw. Manag. 2015, 25, 306–319. [Google Scholar] [CrossRef] [Green Version]
- Gou, G.; Bai, Q.; Xiong, G.; Li, Z. Discovering abnormal behaviors via HTTP header fields measurement. Concurr. Comput. Pract. Exp. 2017, 29, e3926. [Google Scholar] [CrossRef]
- Fielding, R.T.; Reschke, J.F. Message Syntax and Routing. IETF RFC 7230. June 2014. Available online: https://tools.ietf.org/pdf/rfc7230 (accessed on 27 March 2019).
- Reid, F. 4—HTTP: Communicating with Web Servers. In Network Programming in NET; Reid, F., Ed.; Digital Press: Burlington, NJ, USA, 2004; pp. 87–130. [Google Scholar]
- Fielding, R.; Gettys, J.; Mogul, J.; Frystyk, H.; Berners-Lee, T. RFC 2068: Hypertext Transfer Protocol—HTTP/1.1, January 1997. Status: Proposed Standard 1997. Available online: https://tools.ietf.org/pdf/rfc2616 (accessed on 27 March 2019).
- Fielding, R.; Reschke, J. Hypertext transfer protocol (HTTP/1.1): Semantics and Content. 2070-1721. 2014. Available online: https://tools.ietf.org/pdf/rfc7231 (accessed on 27 March 2019).
- Dolnak, I. Implementation of referrer policy in order to control HTTP Referer header privacy. In Proceedings of the 2017 15th International Conference on Emerging eLearning Technologies and Applications (ICETA), Prešovský, Slovakia, 26–27 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–4. [Google Scholar]
- Wall, D. Chapter 3—HTTP in PHP. In Multi-Tier Application Programming with PHP; Wall, D., Ed.; Morgan Kaufmann: San Francisco, CA, USA, 2004; pp. 21–43. [Google Scholar]
- Petersson, A.; Nilsson, M. Forwarded HTTP Extension. 2014. Available online: https://tools.ietf.org/pdf/rfc7239 (accessed on 27 March 2019).
- Adi, E.; Baig, Z.; Hingston, P. Stealthy Denial of Service (DoS) attack modelling and detection for HTTP/2 services. J. Netw. Comput. Appl. 2017, 91, 1–13. [Google Scholar] [CrossRef]
- Tripathi, N.; Hubballi, N. Slow rate denial of service attacks against HTTP/2 and detection. Comput. Secur. 2018, 72, 255–272. [Google Scholar] [CrossRef]
- Ludin, S.; Garza, J. Learning HTTP/2: A Practical Guide for Beginners; O’Reilly Media, Inc.: Newton, MA, USA, 2017. [Google Scholar]

























| Hardware | Software | Software Function |
|---|---|---|
| Web Server Processor Intel(R) Core (TM) i7-6700 CPU @ 3.40GHz 8GB Memory | Python coding editor and Compiler | Edit and execute attack scripts |
| Notepad++ | View and edit attack scripts | |
| Proxy Switcher | Identify active public proxies | |
| Client Processor Intel(R) Core (TM) i7-3770 CPU @ 3.40GHz 12GB Memory | Nmap | Identify port usage |
| Wireshark | Analyze HTTP request traffics | |
| Firewall | Attack Script | HTTP DDoS Code |
| Open Source Operating System: Ubuntu | Provide platform to execute HTTP DDoS attack | |
| Windows Server 2016 Windows 8 Pro | To host web-based application and initiate HTTP request |
| No. | Script Name | Attack Scale | Attack Pattern | Attack Duration | Target URL |
|---|---|---|---|---|---|
| 1. | Attack.py | Internal Attack | High rate direct attack | 10 Min | http://lab.com.my |
| 2. | Chihulk.py | High rate direct attack | 10 Min Internal | http://lab.com.my | |
| 3. | HOIC | ||||
| 4. | Golden Eye.py | External Attack | High rate direct attack | 5 Min | http://42.1.63.189 |
| 5. | BlackHorizon.py | ||||
| 6. | Wreckuests.py | External Attack | High rate through proxy | 5 Min | http://42.1.63.189 |
| 7. | Hibernet.py | ||||
| 8. | UFONet.py |
| No. | User Agent String | Request Query |
|---|---|---|
| 1. | Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.2; Win64; x64; Trident/4.0) | KEAWOCO = ZFSUSO |
| 2. | Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US) | QJCQABP=MIGMQXRML |
| 3. | Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.9.1.3) Gecko/20090824 Firefox/3.5.3 (.NET CLR 3.5.30729) | QJCQABP=MIGMQXRML |
| 4. | Mozilla/4.0 (compatible; MSIE 6.1; Windows XP) | DYH=GFOUW |
| 5. | Opera/9.80 (Windows NT 5.2; U; ru) Presto/2.5.22 Version/10.51 | GQHCIZNYO=ZHILUY |
| 6. | Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US) | DYH=GFOUW |
| No. | User Agent String | Request Query |
|---|---|---|
| 1. | Mozilla/5.0 (iPad; U; CPU OS 3_2 like Mac OS X; en-us) AppleWebKit/531.21.10 (KHTML, like Gecko) Version/4.0.4 Mobile/7B334b Safari/531.21.10 | \357\277\275\357\277\275{\357\277\275\177 =\357\277\275\357\277\275y |
| 2. | BlackBerry8300/4.2.2 Profile/MIDP-2.0 Configuration/CLDC-1.1 VendorID/107 UP.Link/6.2.3.15.0 | \357\277\275\357\277\275\357\277\275 =\357\277\275\357\277\275\357\277\275 |
| 3. | BlackBerry9000/5.0.0.93 Profile/MIDP-2.0 Configuration/CLDC-1.1 VendorID/179 | y\357\277\275\357\277\275\357\277\275\357\277\275\357\277\275 {\357\277\275=\357\277\275\357\277\275\357\277\275 |
| 4. | Mozilla/5.0 (compatible; bingbot/2.0; +http://www.bing.com/bingbot.htm) | ~\357\277\275\357\277\275z}\357\277\275 {~=\357\277\275\357\277\275\357\277\275\357\277\275 |
| 5 | Googlebot/2.1 (http://www.googlebot.com/bot.html) | }\357\277\275\357\277\275=\357\277\275\357\277 \275z\357\277\275\357\277\275~\357\277\275 |
| 6. | Mozilla/5.0 (PLAYSTATION 3; 2.00) | z\357\277\275\357\277\275\357\277\275y=\357\277\275 |
| Complete GET Header (Genuine) | Incomplete GET Header (HTTP DDoS) |
|---|---|
 |  |
| Valid Keep Alive from HTTP Response | Invalid Keep-Alive from GET Header |
|---|---|
 |  |
| No | Attack Strategy | Attack Script Name |
|---|---|---|
| 1. | Web Proxies | Hibernet.py |
| UFONet.py | ||
| 2. | Spoofing | Wreckuests.py |
| 3. | Server Load | Chihulk, High Orbit Ion Canon (HOIC), Golden Eye, BlackHorizon |
| 4. | Main Page Attack | |
| 5. | Random Attack |
| Request 1 # Total Bytes 220 | Request 2 # Total Byte 230 |
|---|---|
| : Authority: www.akamai.com : Method: GET : Path:/ : scheme: https accept: text/html,application/xhtml+xml accept-languange:en-US,en;q=0.8 cookie:last_page=286A7F3DE upgrade-insecure-request:1 user-agent:mozilla http2 | : Authority: www.akamai.com : Method: GET : Path:/style.css : scheme: https accept: text/html,application/xhtml+xml accept-languange:en-US,en;q=0.8 cookie:last_page=*398AB8E8F upgrade-insecure-request:1 user-agent:mozilla http2 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jaafar, A.G.; Ismail, S.A.; Abdullah, M.S.; Kama, N.; Azmi, A.; Yusop, O.M. Recent Analysis of Forged Request Headers Constituted by HTTP DDoS. Sensors 2020, 20, 3820. https://doi.org/10.3390/s20143820
Jaafar AG, Ismail SA, Abdullah MS, Kama N, Azmi A, Yusop OM. Recent Analysis of Forged Request Headers Constituted by HTTP DDoS. Sensors. 2020; 20(14):3820. https://doi.org/10.3390/s20143820
Chicago/Turabian StyleJaafar, Abdul Ghafar, Saiful Adli Ismail, Mohd Shahidan Abdullah, Nazri Kama, Azri Azmi, and Othman Mohd Yusop. 2020. "Recent Analysis of Forged Request Headers Constituted by HTTP DDoS" Sensors 20, no. 14: 3820. https://doi.org/10.3390/s20143820
APA StyleJaafar, A. G., Ismail, S. A., Abdullah, M. S., Kama, N., Azmi, A., & Yusop, O. M. (2020). Recent Analysis of Forged Request Headers Constituted by HTTP DDoS. Sensors, 20(14), 3820. https://doi.org/10.3390/s20143820





