Dynamic RFID Identification in Urban Traffic Management Systems
Abstract
:1. Introduction
2. RFID Communication Concepts
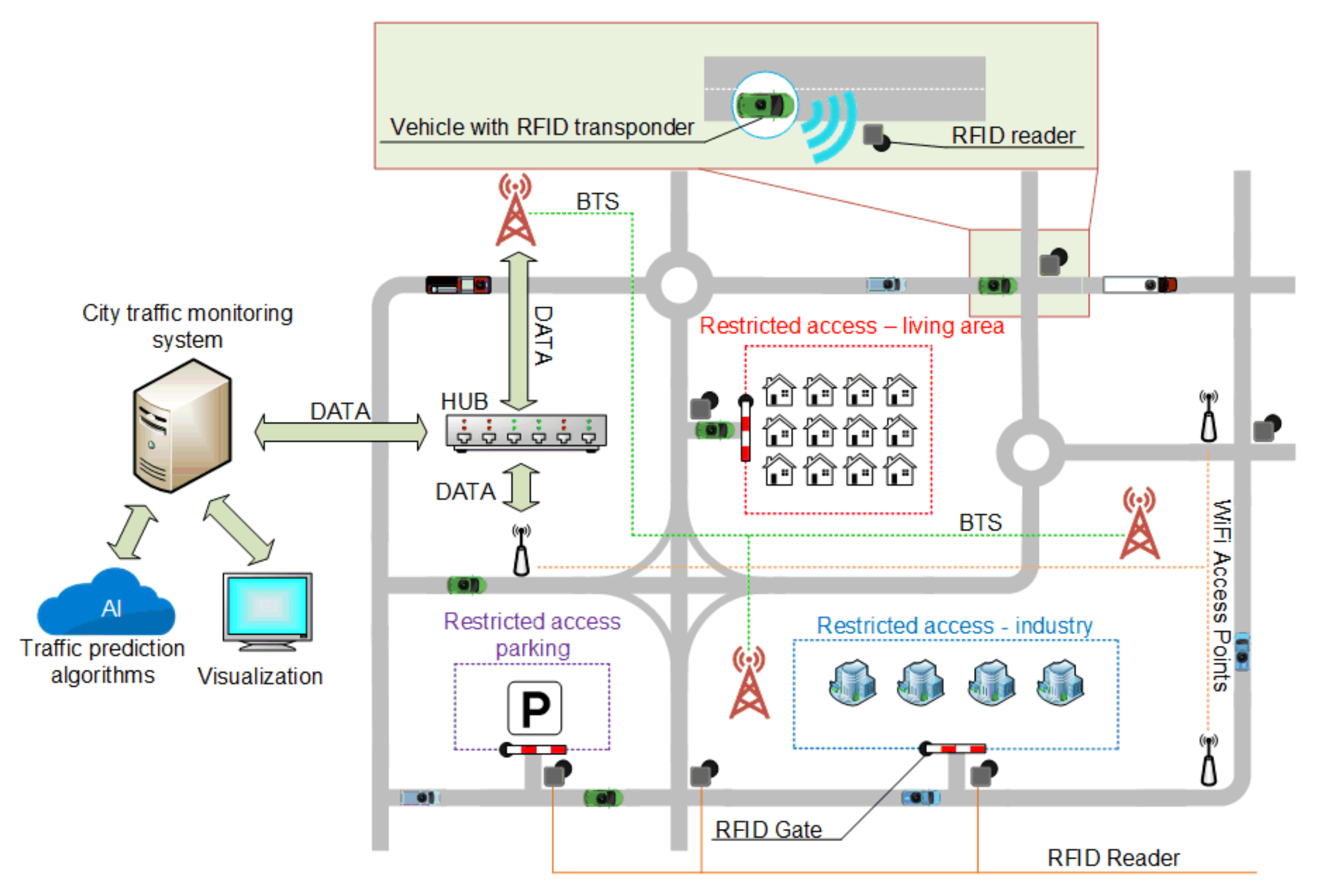
3. Smart City Traffic Solutions
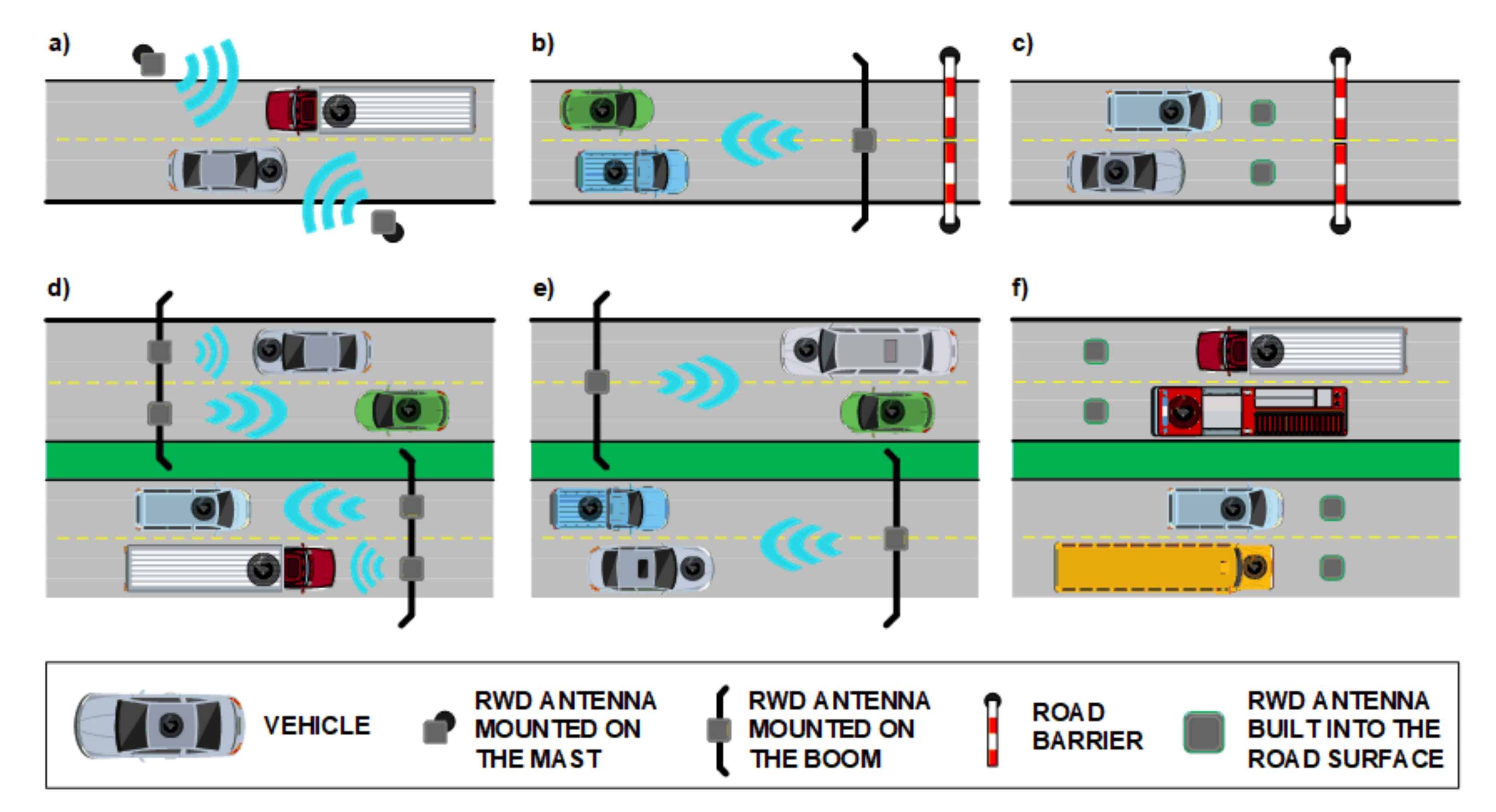
4. Improving Traffic Management with RFID Solutions
- RFID transponders installed in vehicles, and RWD devices in the road infrastructure [22],
- RWD devices installed in vehicles and transponders in the road infrastructure.
5. The Idea of the RFID System Dynamic Model
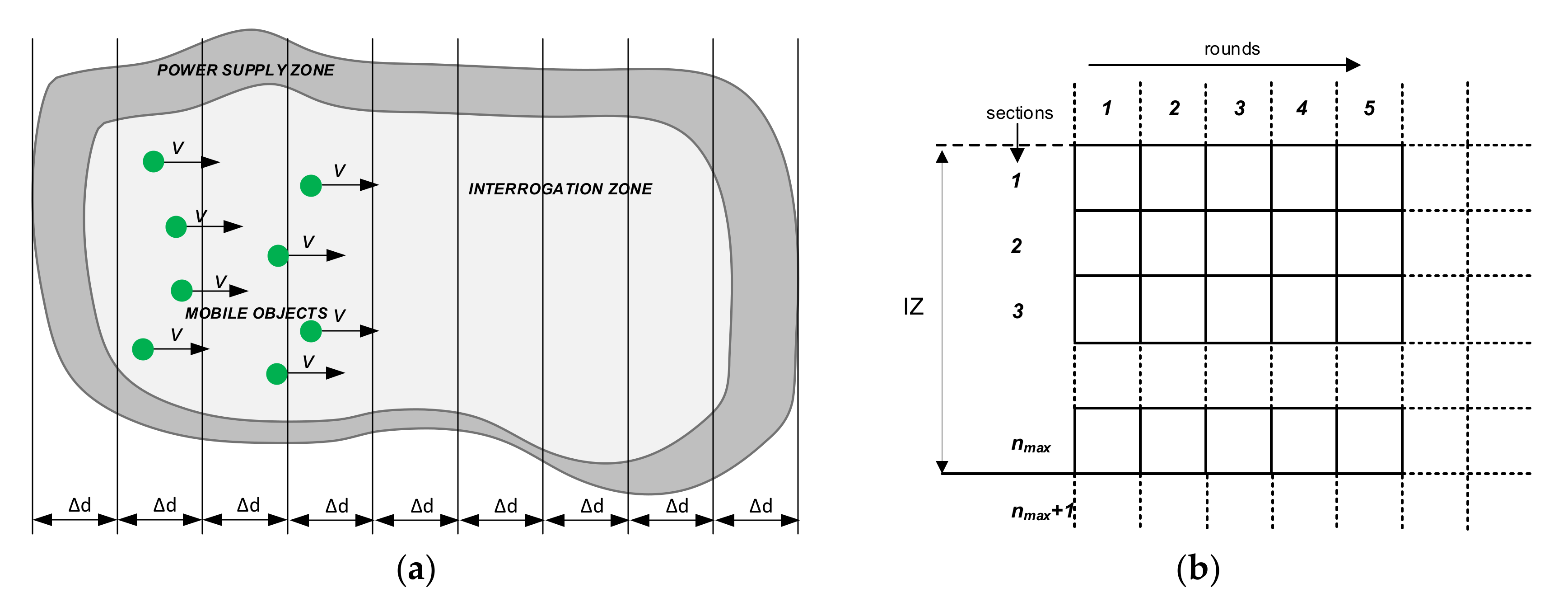
5.1. Dynamic RFID Interrogation Zone
5.2. Model Synthesis Assumptions
- Transponders in the entire PSZ are identified in a round.
- The probability of identifying a transponder does not depend on its location in the PSZ. This is because the order in which transponders are read depends on the random numbers generated at the beginning of each round.
- The number of unread transponders in a moving group decreases over time (due to correct identification), i.e., the further the transponder group enters the PSZ, the smaller the number of unread transponders in this group.
- For a given number of transponders read in a round, their number per section is proportional to the (previous) number of unread transponders in this section.
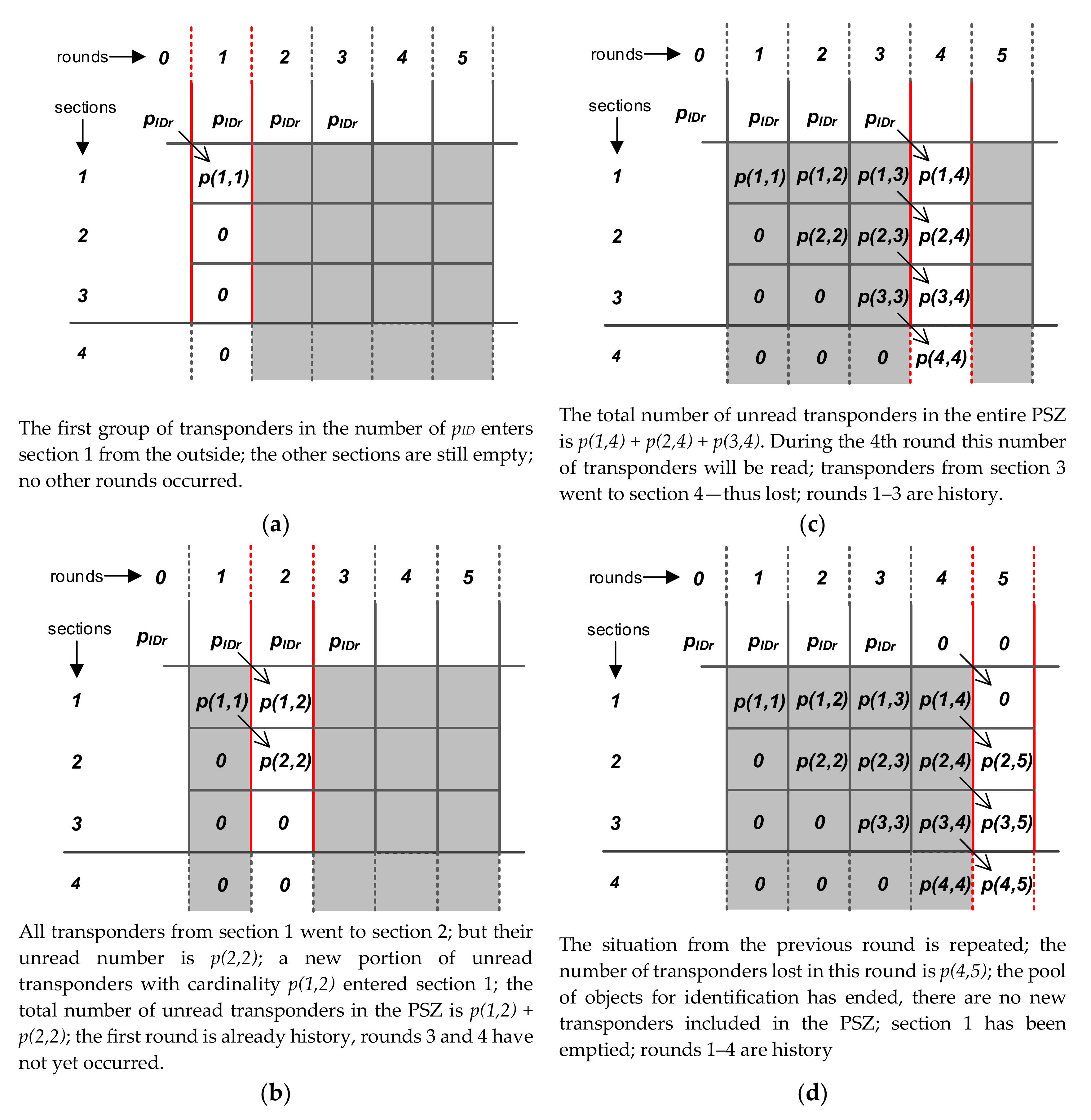
5.3. Representation of the System State
- P with the words p(n, k), which are equal to the number of unread transponders in the n-th section and the k-th round;
- PISR with the words pisr(n, k), equal to the numbers of correct identifications in the n-th section and the n-th round;
- PIR (single-line matrix) with the words pir(k), equal to the number of identifications in the entire PSZ-matrix in which the number of identifications in the k-th round is recorded;
- PS (single-line matrix) with the words ps(k), equal to the number of “lost” transponders in the k-th round. Lost transponders are transponders that were not read during the entire identification process—they left the PES and therefore will remain unread.
5.4. Communication Protocol in a Dynamic RFID System
- The limited time of the inventory round. The round consists three types of slots: identification, empty and collision. Every type of slot has different duration (Figure 10). The number of all slots is limited according to Q algorithm. The parameter Q can be changed during the inventory round. In addition, the duration of each round is determined by the RWD and if the maximum round time is reached, the RWD interrupts the current round despite the actual number of slots. Otherwise, when the assumed number of slots is reached before the end of the round, the RWD waits idly until the round time elapses.
- The actual duration of every type of time slot (Figure 10). The duration of the slot depends on the time parameters of the ISO1800-63 protocol. The duration of RWD commands depends on Tari (6.25; 12.5 and 25 µs) reference time interval, the command type (Select, Query, QueryAdjust and QueryRepeat), and the type of encoding [62]. In turn, the time interval provided for transponder responses depends mainly on the type of channel coding [62], the subcarrier frequency BLF, and the type of event that occurs in the given time slot.
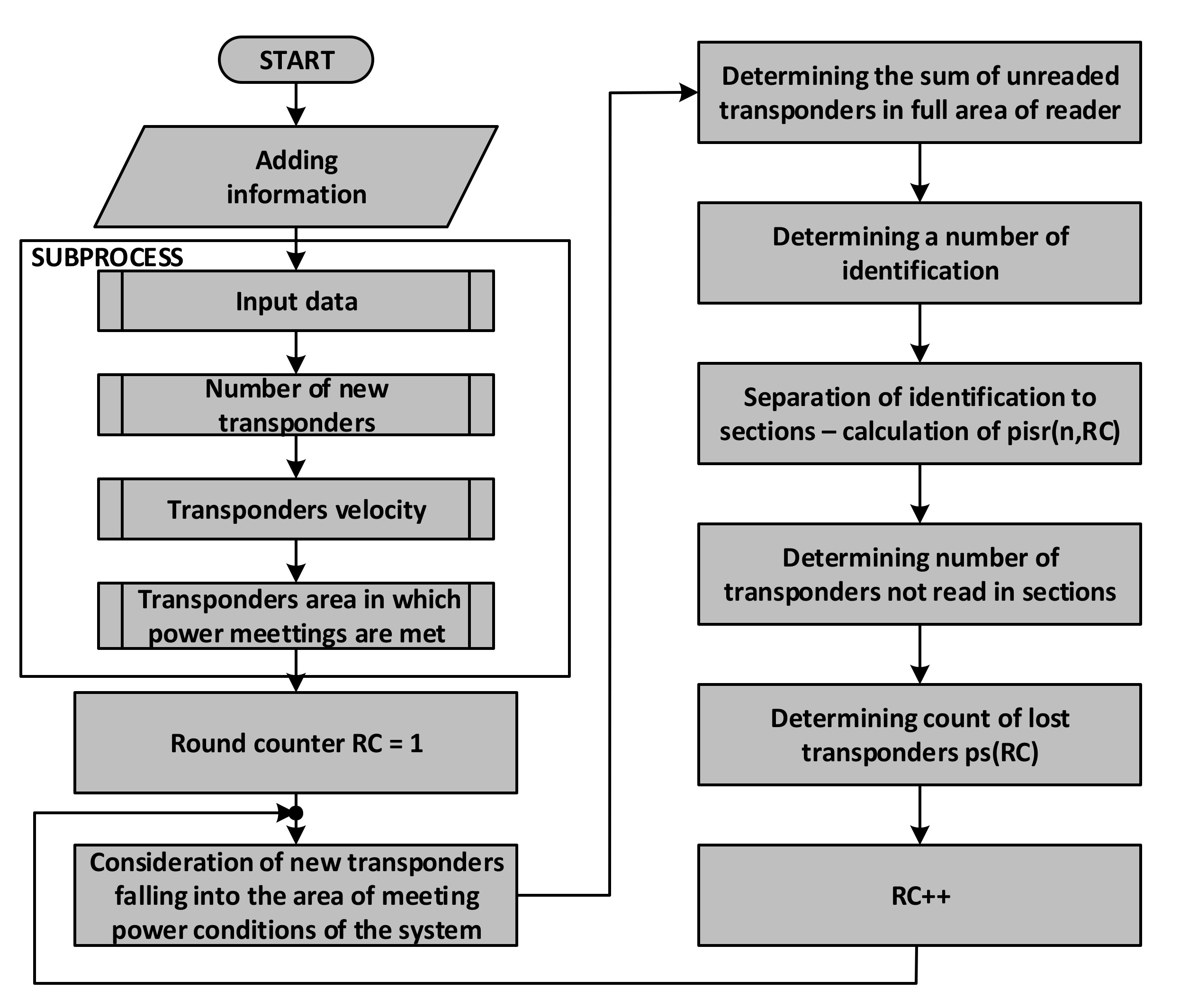
6. Synthesis of the Model of Dynamic RFID System
6.1. Determination of the Time Slot Type in a Single Round
6.2. Simulation of Single Inventory Round
- dynamically determining the number of all slot types;
- parameters determining the duration of communication between RWD and transponders;
- parameter limiting the length of the inventory round and providing the ability to calculate the inventory round time.
6.3. A Finite and Infinite Stream of Transponders
6.4. Determination of the Number of Lost Transponders in a Round
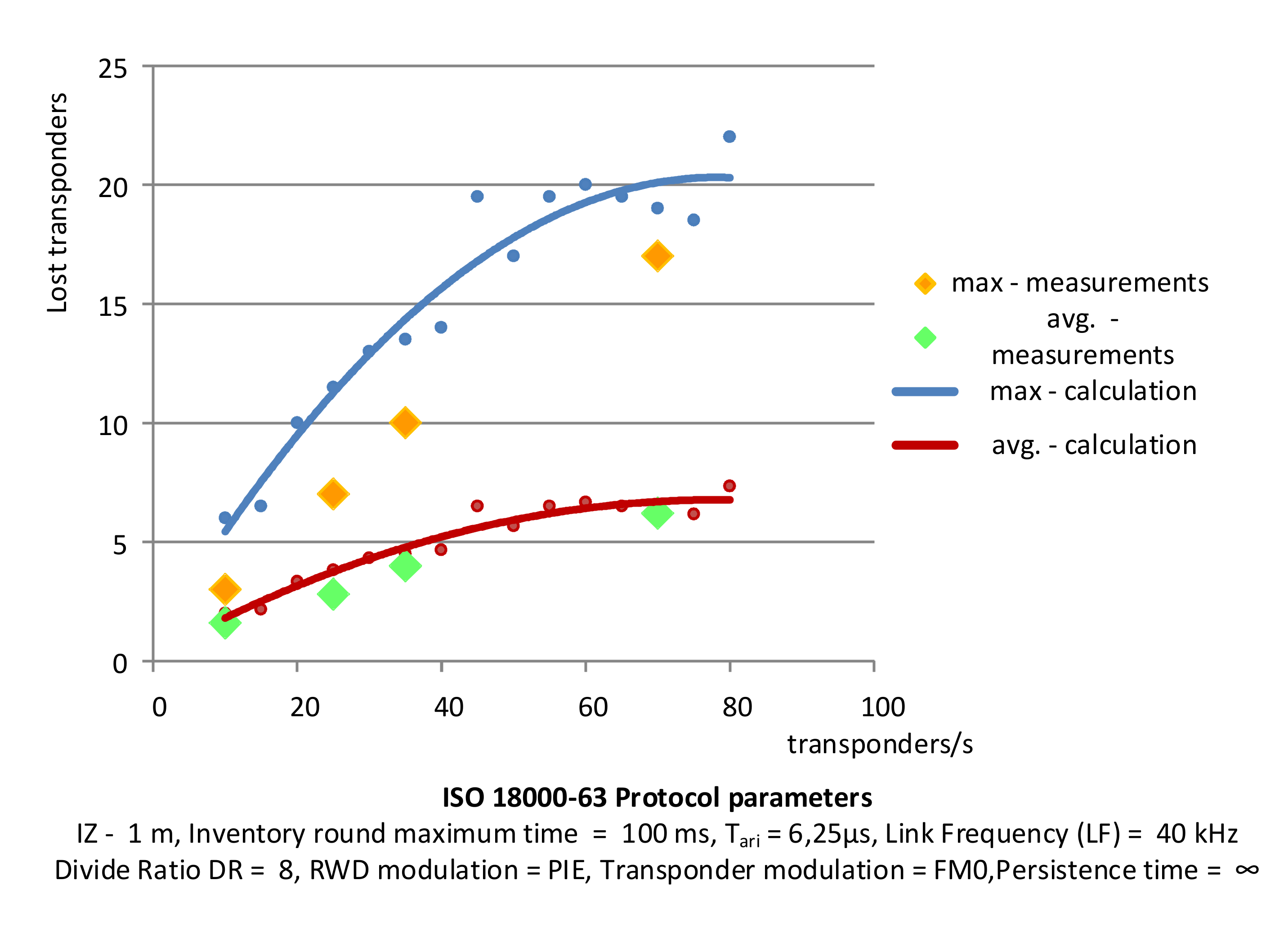
7. Identification Efficiency Tests and Results
8. Conclusions
- A convenient concept of system state was introduced.
- A computationally effective representation of the state using a matrix set was presented.
- A determination of the number of individual events in round time slots based on random processes with assumed expected values was adopted.
- It became possible to change these values during the round as the identification progressed.
- The ability to set the probability of identification failure due to transmission errors not related to collisions was introduced.
Author Contributions
Funding
Conflicts of Interest
References
- Ustundag, A. (Ed.) The Value of RFID. Benefits vs. Costs, 1st ed.; Springer: London, UK, 2013. [Google Scholar]
- Giusto, D.; Iera, A.; Morabito, G.; Atzori, L. (Eds.) The Internet of Things, 20th Tyrrhenian Workshop on Digital Communications; Springer: New York, NY, USA, 2010. [Google Scholar]
- Traub, K. (Ed.) The GS1 EPCglobal Architecture Framework, Version 1.6; GS1: Brussels, Belgium, 2014. [Google Scholar]
- Xiao, C.; Chen, N.; Li, D.; Lv, Y.; Gong, J. SCRMS: An RFID and Sensor Web-Enabled Smart Cultural Relics Management System. Sensors 2017, 17, 60. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chung, Y.W. Modeling and Performance Analysis of Movement-Based Group Location Management Using RFID Sensing in Public Transportation Systems. Sensors 2012, 12, 16077–16098. [Google Scholar] [CrossRef] [PubMed]
- Mora-Mora, H.; Iglesias-Gilart, V.; Gil, D.; Sirvent-Llamas, A. A Computational Architecture Based on RFID Sensors for Traceability in Smart Cities. Sensors 2015, 15, 13591–13626. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Oya, J.R.G.; Clemente, R.M.; Fort, E.H.; Carvajal, R.G.; Chavero, F.M. Passive RFID-Based Inventory of Traffic Signs on Roads and Urban Environments. Sensors 2018, 18, 2385. [Google Scholar]
- Pérez, J.; Seco, F.; Milanés, V.; Jiménez, A.; Diaz, J.C.; Pedro, T. An RFID-Based Intelligent Vehicle Speed Controller Using Active Traffic Signals. Sensors 2010, 10, 5872–5887. [Google Scholar] [CrossRef] [Green Version]
- Dobkin, D.M. The RF in RFID: UHF RFID in Practice, 2nd ed.; Newnes: Oxford, UK, 2012. [Google Scholar]
- Pawłowicz, B.; Salach, M.; Trybus, B. Infrastructure of RFID-Based Smart City Traffic Control System: Progress in Automation, Robotics and Measurement Techniques; Springer International Publishing: Cham, Switzerland, 2019; Volume 920. [Google Scholar]
- Ukkonen, L.; Sydanheimo, L.; Kivikoski, M. Read Range Performance Comparison of Compact Reader Antennas for a Handheld UHF RFID Reader. IEEE Commun. Mag. 2007, 45, 24–31. [Google Scholar] [CrossRef]
- Jankowski-Mihułowicz, P.; Węglarski, M. Definition, Characteristics and Determining Parameters of Antennas in Terms of Synthesizing the Interrogation Zone in RFID Systems, Radio Frequency Identification; Crepaldi, P.C., Pimenta, T.C., Eds.; Intech: London, UK, 2017; Chapter 5; pp. 65–119. ISBN 978-953-51-3630-9. [Google Scholar]
- Jankowski-Mihułowicz, P.; Węglarski, M. Factors affecting the synthesis of autonomous sensors with RFID interface. Sensors 2019, 19, 4392. [Google Scholar]
- GS1 EPCglobal. EPC Radio-Frequency Identity Protocols Generation-2 UHF RFID; Specification for RFID Air Interface Protocol for Communications at 860 MHz–960 MHz; Version 2.1; EPCglobal: Brussels, Belgium, 2018. [Google Scholar]
- Jankowski-Mihułowicz, P.; Pawłowicz, B.; Pitera, G. Zagadnienie wymiany danych w systemie RFID pasma HF z autonomicznym identyfikatorem półpasywnym. Przegląd Elektrotechniczny 2015, 91, 74–77. [Google Scholar] [CrossRef]
- Abad, E.; Mazzolai, B.; Juarros, A.; Gómez, D.; Mondini, A.; Sayhan, I.; Krenkow, A.; Becker, T. Fabrication process for a flexible tag microlab. Proc. SPIE 2007. [Google Scholar] [CrossRef]
- Oprea, A.; Courbat, J.; Bârsan, N.; Briand, D.; de Rooij, N.F.; Weimar, U. Temperature, humidity and gas sensors integrated on plastic foil for low power applications. Sens. Actuators B Chem. 2009, 140, 227–232. [Google Scholar] [CrossRef]
- Honeywell. Intermec RFID Tags & Media, Meeting the Scalable RFID Challenge; Honeywell International Inc.: Charlotte, NC, USA, 2013. [Google Scholar]
- International Organization for Standardization/International Electrotechnical Commission. Identification Cards—Contactless Integrated Circuit Cards—Proximity Cards; ISO/IEC: Geneva, Switzerland, 2016; p. 14443-4. [Google Scholar]
- International Organization for Standardization/International Electrotechnical Commission. Identification Cards—Contactless Integrated Circuit Cards—Vicinity Cards; ISO/IEC: Geneva, Switzerland, 2006; p. 15693. [Google Scholar]
- International Organization for Standardization/International Electrotechnical Commission. 2013 Information Technology—Radio Frequency Identification for Item Management—Part 6: Parameters for Air Interface Communications at 860 MHz to 960 MHz General; ISO/IEC: Geneva, Switzerland, 2013; p. 18000-6. [Google Scholar]
- Chowdhury, P.; Bala, P.; Addy, D.; Giri, S.; Chaudhuri, A.R. RFID and Android based smart ticketing and destination announcement system. In Proceedings of the 2016 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Jaipur, India, 21–24 September 2016; pp. 2587–2591. [Google Scholar]
- Smart Cities 1.0, 2.0, 3.0. What’s Next? Available online: http://smartcityhub.com/collaborative-city/smart-cities-1-0-2-0-3-0-whats-next/ (accessed on 2 June 2020).
- Salgues, B. The City and Mobility 3.0. In Society 5.0: Industry of the Future, Technologies, Methods and Tools, 1st ed.; ISTE Ltd. and John Wiley & Sons, Inc.: London, UK, 2018; pp. 67–74. [Google Scholar]
- Salgues, B. Society 5.0, Its Logic and Its Construction. In Society 5.0: Industry of the Future, Technologies, Methods and Tools, 1st ed.; ISTE Ltd. and John Wiley & Sons, Inc.: London, UK, 2018; pp. 1–21. [Google Scholar]
- Pla-Castells, M.; Martinez-Durá, J.J.; Samper-Zapater, J.J.; Cirilo-Gimeno, R.V. Use of ICT in smart cities. A practical case applied to traffic management in the city of Valencia. In Proceedings of the 2015 Smart Cities Symposium Prague (SCSP), Prague, Czech Republic, 24–25 June 2015; pp. 167–170. [Google Scholar]
- Mora, H.; Gilart-Iglesias, V.; Hoyo, R.P.; Andújar-Montoya, M.D. A Comprehensive System for Monitoring Urban Accessibility in Smart Cities. Sensors 2017, 17, 1834. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Akhter, F.; Khandivizand, S.; Siddiquei, H.R.; Alahi, M.E.; Mukhopadhyay, S. IoT Enabled Intelligent Sensor Node for Smart City: Pedestrian Counting and Ambient Monitoring. Sensors 2019, 19, 3374. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Barthélemy, J.; Verstaevel, N.; Forehead, H.; Perez, P. Edge-Computing Video Analytics for Real-Time Traffic Monitoring in a Smart City. Sensors 2019, 19, 2048. [Google Scholar] [CrossRef] [Green Version]
- Rathod, R.; Khot, S.T. Smart assistance for public transport system. In Proceedings of the 2016 International Conference of Inventive Computation Technologies, Coimbatore, India, 6–27 August 2016. [Google Scholar]
- Martin, J.; Khatib, E.J.; Lázaro, P.; Barco, R. Traffic Monitoring via Mobile Device Location. Sensors 2019, 19, 4505. [Google Scholar] [CrossRef] [Green Version]
- McClellan, S.; Jimenez, J.; Koutitas, G. Applications, Technologies, Standards, and Driving Factors. In Smart Cities; Springer International Publishing: Cham, Switzerland, 2018; p. 125. [Google Scholar]
- Dominguez, J.M.L.; Sanguino, T.J.M. Review on V2X, I2X, and P2X Communications and Their Applications: A Comprehensive Analysis over Time. Sensors 2019, 19, 2756. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bhatti, F.; Shah, M.A.; Maple, C.; Islam, S.U. A Novel Internet of Things-Enabled Accident Detection and Reporting System for Smart City Environments. Sensors 2019, 19, 2071. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ksiksi, A.; Al Shehhi, S.; Ramzan, R. Intelligent Traffic Alert System for Smart Cities. In Proceedings of the 2015 IEEE International Conference on Smart City/SocialCom/SustainCom (SmartCity), Chengdu, China, 19–21 December 2015; pp. 165–169. [Google Scholar]
- Sheng-hai, A.; Byung-Hyug, L.; Dong-Ryeol, S. A Survey of Intelligent Transportation Systems. In Proceedings of the 2011 Third International Conference on Computational Intelligence, Communication Systems and Networks, Bali, Indonesia, 26–28 July 2011. [Google Scholar]
- Naseer, S.; Liu, W.; Sarkar, N.I. Energy-Efficient Massive Data Dissemination through Vehicle Mobility in Smart Cities. Sensors 2019, 19, 4735. [Google Scholar] [CrossRef] [Green Version]
- Chiu, C.; Lee, W. Design and Implementation of a Smart Traffic Signal Control System for Smart City Applications. Sensors 2020, 20, 508. [Google Scholar]
- Bagula, A.; Castelli, L.; Zennaro, M. On the Design of Smart Parking Networks in the Smart Cities: An Optimal Sensor Placement Model. Sensors 2015, 15, 15443–15467. [Google Scholar] [CrossRef] [Green Version]
- Awan, F.M.; Saleem, Y.; Minerva, R.; Crespi, N. A Comparative Analysis of Machine/Deep Learning Models for Parking Space Availability Prediction. Sensors 2020, 20, 322. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lanza, J.; Sánchez, L.; Gutiérrez, V.; Galache, J.A.; Santana, J.R.; Sotres, P.; Muñoz, L. Smart City Services over a Future Internet Platform Based on Internet of Things and Cloud: The Smart Parking Case. Energies 2016, 9, 719. [Google Scholar] [CrossRef] [Green Version]
- Kazi, S.; Khan, S.; Ansari, U.; Mane, D. Smart Parking based System for smarter cities. In Proceedings of the 2018 International Conference on Smart City and Emerging Technology (ICSCET), Mumbai, India, 5 January 2018; pp. 590–595. [Google Scholar]
- Sotres, P.; Lanza, J.; Sánchez, L.; Santana, J.R.; López, C.; Muñoz, L. Breaking Vendors and City Locks through a Semantic-enabled Global Interoperable Internet-of-Things System: A Smart Parking Case. Sensors 2019, 19, 229. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Rassia, S.; Pardalos, P. Through the Internet of Things. In Smart City Networks; Springer International Publishing: Cham, Switzerland, 2017; Volume 125, p. 88. [Google Scholar]
- Haroon, P.S.; Eranna, U.; Irudayaraj, I.R.; Ulaganathan, J.; Harish, R. Paradoxical monitoring of urban areas & mailbags tracking system using RFID & GPS. In Proceedings of the 2017 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques (ICEECCOT), Mysuru, India, 15–16 December 2017; pp. 1–4. [Google Scholar]
- Arbi, Z.; Driss, O.B.; Sbai, M.K. A multi-agent system for monitoring and regulating road traffic in a smart city. In Proceedings of the 2017 International Conference on Smart, Monitored and Controlled Cities, Sfax, Tunisia, 17–19 February 2017. [Google Scholar]
- Pawłowicz, B.; Salach, M.; Trybus, B. Smart city traffic monitoring system based on 5G cellular network, RFID and machine learning. In Engineering Software Systems: Research and Praxis; Springer: Cham, Switzerland, 2018; Volume 830, pp. 5–9. [Google Scholar]
- Bartneck, N.; Klaas, V.; Schönherr, H. Optimizing Processes with RFID and Auto ID; Wiley: Hoboken, NJ, USA, 2009. [Google Scholar]
- Hoang, T.M.; Baek, N.R.; Cho, S.W.; Kim, K.W.; Park, K.R. Road Lane Detection Robust to Shadows Based on a Fuzzy System Using a Visible Light Camera Sensor. Sensors 2017, 17, 2475. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hernández, D.C.; Kurnianggoro, L.; Filonenko, A.; Jo, K.H. Real-Time Lane Region Detection Using a Combination of Geometrical and Image Features. Sensors 2016, 16, 1935. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kim, J.G.; Yoo, J.-H.; Koo, J.C. Road and Lane Detection Using Stereo Camera. In Proceedings of the 2018 IEEE International Conference on Big Data and Smart Computing (BigComp), Shanghai, China, 15–17 January 2018; pp. 649–652. [Google Scholar]
- Hoang, T.M.; Hong, H.G.; Vokhidov, H.; Park, K.R. Road Lane Detection by Discriminating Dashed and Solid Road Lanes Using a Visible Light Camera Sensor. Sensors 2016, 16, 1313. [Google Scholar] [CrossRef]
- Dias, C.; Jagetiya, A.; Chaurasia, S. Anonymous Vehicle Detection for Secure Campuses: A Framework for License Plate Recognition using Deep Learning. In Proceedings of the 2019 2nd International Conference on Intelligent Communication and Computational Techniques (ICCT), Jaipur, India, 28–29 September 2019; pp. 79–82. [Google Scholar]
- Wong, S.F.; Mak, H.C.; Ku, C.H.; Ho, W.I. Developing advanced traffic violation detection system with RFID technology for smart city. In Proceedings of the 2017 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Singapore, 10–13 December 2017; pp. 334–338. [Google Scholar]
- Hall, E.R. The Vision of a Smart City. In Proceedings of the 2nd International Life Extension Technology Workshop, Paris, France, 28 September 2000; p. 2. [Google Scholar]
- Prinsloo, J.; Malekian, R. Accurate Vehicle Location System Using RFID, an Internet of Things Approach. Sensors 2016, 16, 825. [Google Scholar] [CrossRef] [Green Version]
- Wang, J.; Ni, D.; Li, K. RFID-Based Vehicle Positioning and Its Applications in Connected Vehicles. Sensors 2014, 14, 4225–4238. [Google Scholar] [CrossRef] [Green Version]
- Huang, Y.; Qian, L.; Feng, A.; Wu, Y.; Zhu, W. RFID Data-Driven Vehicle Speed Prediction via Adaptive Extended Kalman Filter. Sensors 2018, 18, 2787. [Google Scholar] [CrossRef] [Green Version]
- Gotfryd, M.; Pawłowicz, B. Modeling of a Dynamic RFID System. In Proceedings of the Eighteenth IEEE symposium on Computers and Communications ISCC13, Split, Croatia, 7–10 July 2013; pp. 747–752. [Google Scholar]
- Jankowski-Mihułowicz, P.; Węglarski, M. Interrogation Zone Determination in HF RFID Systems with Multiplexed Antennas. Arch. Electr. Eng. 2015, 64, 459–470. [Google Scholar] [CrossRef] [Green Version]
- Mak, C.L. Passive UHF RFID tag designs for automatic vehicle identification. In Proceedings of the 2017 IEEE International Conference on Computational Electromagnetics (ICCEM), Kumamoto, Japan, 8–10 March 2017; pp. 61–63. [Google Scholar]
- International Organization for Standardization/International Electrotechnical Commission. Information Technology—Radio Frequency Identification for Item Management—Part 63: Parameters for Air Interface Communications at 860 MHz to 960 MHz Type C; ISO/IEC: Geneva, Switzerland, 2015; p. 18000-63. [Google Scholar]
- Espin, J.J.A.; Egea-Lopez, E.; Vales-Alonso, J.; Haro, J.G. Dynamic system model for optimal configuration of mobile RFID systems. Comput. Netw. 2011, 55, 74–83. [Google Scholar]
- Floerkemeier, C.; Wille, M. Comparison of transmission schemes for framed ALOHA based RFID protocols. In Proceedings of the International Symposium on Applications and the Internet Workshops—SAINT Workshops, Phoenix, AZ, USA, 23–27 January 2006; pp. 94–97. [Google Scholar]
- Aiguo, L.; Weikang, Y. Dynamic Frame Slotted ALOHA Algorithm Based on Improved Tag Estimation. In Proceedings of the 2018 10th International Conference on Intelligent Human-Machine Systems and Cybernetics (IHMSC), Hangzhou, China, 25–26 August 2018; pp. 328–331. [Google Scholar]
- Wen-Tzu, C. An accurate tag estimate method for improving the performance of an RFID anticollision algorithm based on dynamic frame length ALOHA. IEEE Trans. Autom. Sci. Eng. 2008, 6, 9–15. [Google Scholar] [CrossRef]
- Bueno-Delgado, M.V.; Vales-Alonso, J.; Gonzalez-Castano, F.J. Analysis of DFSA anti-collision protocols in passive RFID environments. In Proceedings of the 2009 35th Annual Conference of IEEE Industrial Electronics, Porto, Portugal, 3–5 November 2009; pp. 2610–2617. [Google Scholar]
- Vogt, H. Multiple object identification with passive RFID tags. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics, Yasmine Hammamet, Tunisia, 6–9 October 2002; p. 6. [Google Scholar]














© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pawłowicz, B.; Trybus, B.; Salach, M.; Jankowski-Mihułowicz, P. Dynamic RFID Identification in Urban Traffic Management Systems. Sensors 2020, 20, 4225. https://doi.org/10.3390/s20154225
Pawłowicz B, Trybus B, Salach M, Jankowski-Mihułowicz P. Dynamic RFID Identification in Urban Traffic Management Systems. Sensors. 2020; 20(15):4225. https://doi.org/10.3390/s20154225
Chicago/Turabian StylePawłowicz, Bartosz, Bartosz Trybus, Mateusz Salach, and Piotr Jankowski-Mihułowicz. 2020. "Dynamic RFID Identification in Urban Traffic Management Systems" Sensors 20, no. 15: 4225. https://doi.org/10.3390/s20154225
APA StylePawłowicz, B., Trybus, B., Salach, M., & Jankowski-Mihułowicz, P. (2020). Dynamic RFID Identification in Urban Traffic Management Systems. Sensors, 20(15), 4225. https://doi.org/10.3390/s20154225





