The Design of Large Scale IP Address and Port Scanning Tool
Abstract
:1. Introduction
2. The Common Technology of HIRFL Scanner
2.1. High Concurrency of Golang Programming Language
2.2. GTK
2.3. ICMP Protocol
- (1)
- The ping command will build a fixed format ICMP request packet, and then the ICMP protocol will hand this packet to the IP layer protocol along with the destination host’s IP address. Ping can calculate the RTT (round trip time), which inserts the sending time in the data part of the packets.
- (2)
- The IP layer protocol takes the local IP address as the source address, appending some other control information, and constructs an IP packet. After finding the MAC address corresponding to the destination IP address in a mapping table, the packet will be handed over to the data link layer. If the destination host and the source host are not in the same network segment, this will turn to the routing process.
- (3)
- Construct a data frame at the data link layer, along with some control information. The destination address is the MAC address passed from the IP layer, and the source address is the physical address of the machine. Then, transfer them out according to the media access rules of Ethernet.
- (4)
- After receiving the data frame, the destination host first checks its destination address and compares it with the physical address of the machine. If it matches, the data frame will be received; otherwise, the data frame will be discarded. After receiving, the destination host will check the data frame, extract the IP data packet from the frame, and give it to the local IP layer protocol. Similarly, after checking at the IP layer, the useful information is extracted and handed over to the ICMP protocol. After the latter process, the ICMP response packet is immediately constructed and sent to the source host.
2.4. TCP Full Connection Port Scanning Technology and Classification
- (1).
- When establishing a connection, the client sends a syn packet (syn = j) to the server and enters the SYN_SEND state, waiting for the server to confirm. When the server receives the syn packet, it must confirm the client’s ACK (ack = j + 1), and also send a SYN packet (syn = k), that is, the SYN+ACK packet. After this process, the server enters the SYN_RECV state. If the port is closed, the RST packet will be returned.
- (2).
- The client receives the SYN+ACK packet from the server and sends an acknowledgment packet ACK (ack = k + 1) to the server. After the packet is sent, the client and server enter the ESTABLISHED state to complete the connection establishment.
- (1).
- Horizontal scanning: For a specific port, scan different target hosts, as shown in Figure 3 below.
- (2).
- Vertical scanning: Scan different ports for a specific host as shown in Figure 4 below.
- (3).
- Block scanning: Block scanning is a combination of horizontal and vertical scanning. It scans multiple times for different ports of different hosts, as shown in Figure 5 below.
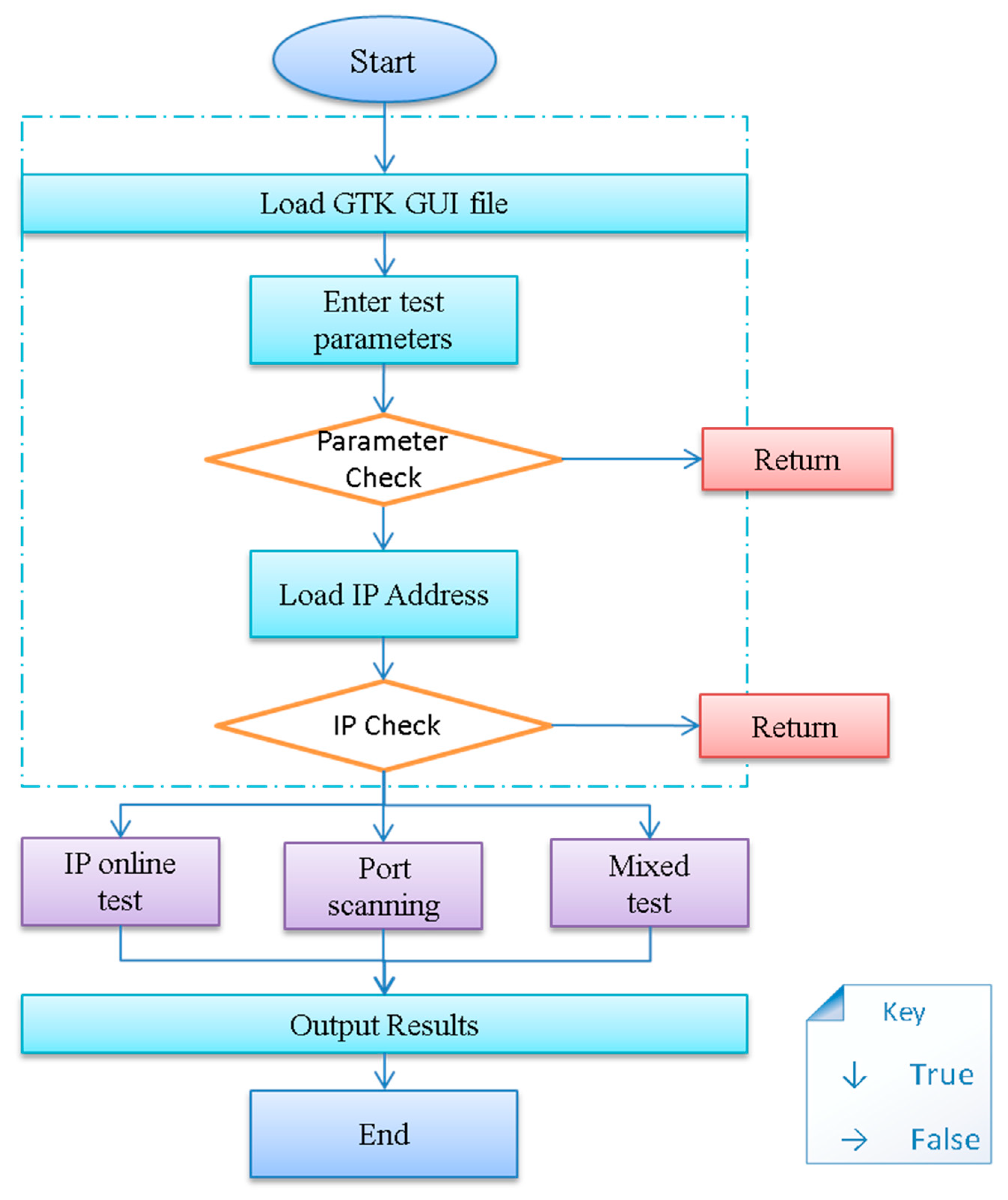
3. Structure of the HIRFL Scanner
4. Experiment and Result
4.1. Data Description and Preprocess
4.2. The Comparisons of IP Address Online and Port State Independent Detection
4.3. The Comparisons of Scanning Results of IP Devices with Different Port Numbers in Accelerator Control Network
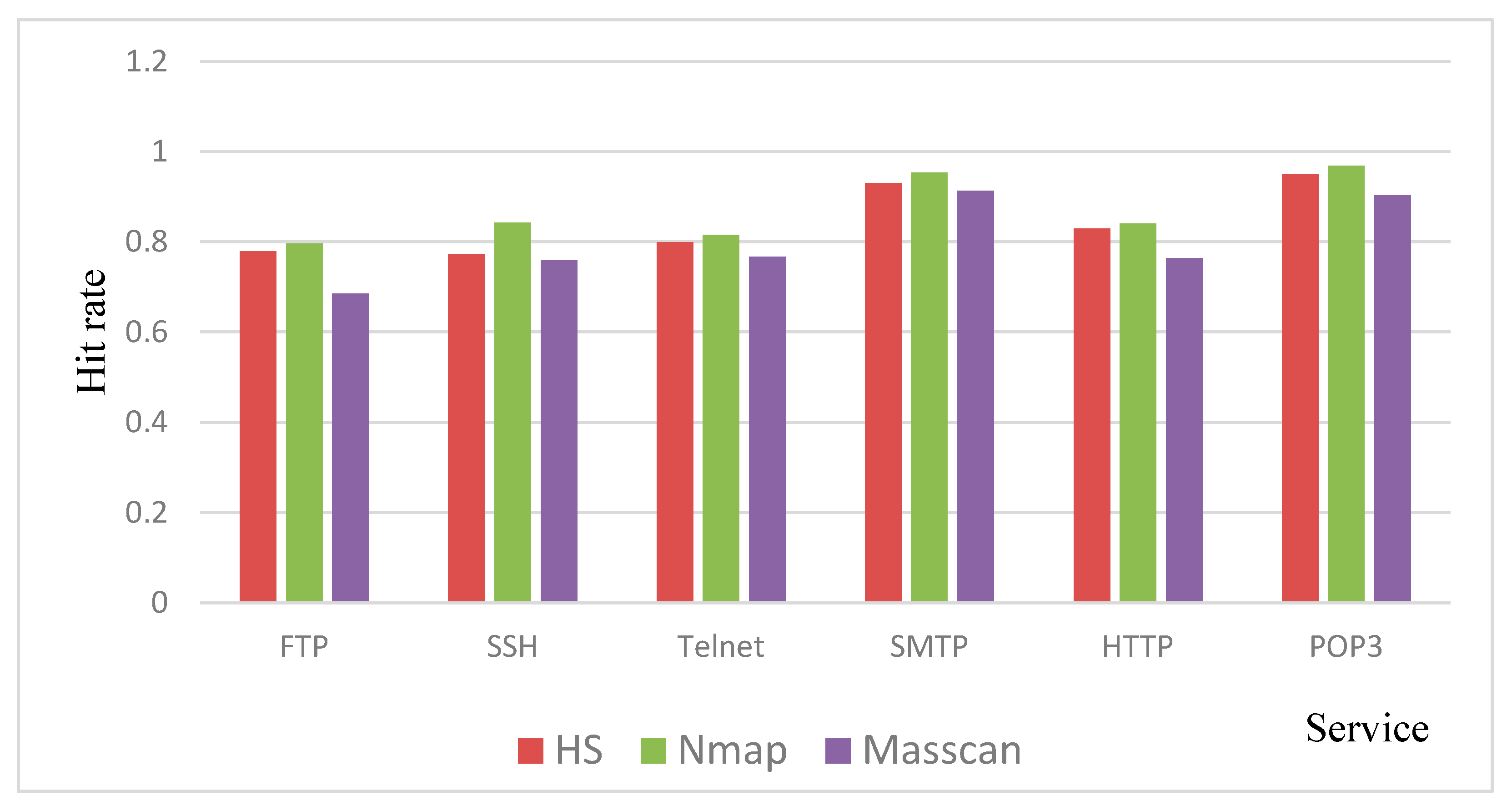
4.4. The Comparison of Hit Rate when Using the Shodan Dataset
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Galeano-Brajones, J.; Carmona-Murillo, J.; Valenzuela-Valdes, J.F.; Luna-Valero, F. Detection and mitigation of dos and ddos attacks in iot-based stateful sdn: An experimental approach. Sensors 2020, 20, 816. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Iyamuremye, B.; Shima, H. Network Security Testing Tools for SMES (Small and Medium Enterprises); IEEE: New York, NY, USA, 2018; pp. 414–417. [Google Scholar]
- Lai, Y.; Gao, H.; Liu, J. Vulnerability mining method for the modbus tcp using an anti-sample fuzzer. Sensors 2020, 20, 2040. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Birkinshaw, C.; Rouka, E.; Vassilakis, V.G. Implementing an intrusion detection and prevention system using software-defined networking: Defending against port-scanning and denial-of-service attacks. J. Netw. Comput. Appl. 2019, 136, 71–85. [Google Scholar] [CrossRef] [Green Version]
- Li, Z.; Yu, X.; Wang, D.; Liu, Y.; He, S. Supereye: A distributed port scanning system. In Proceedings of the International Conference on Artificial Intelligence and Security, New York, NY, USA, 26–28 July 2019; pp. 45–56. [Google Scholar]
- Sanz, I.J.; Lopez, M.A.; Mattos, D.M.F.; Duarte, O.C.M.B. A cooperation-aware virtual network function for proactive detection of distributed port scanning. In Proceedings of the Cyber Security in Networking Conference, Rio de Janeiro, Brazil, 18–20 October 2017. [Google Scholar]
- Dhivvya, J.P.; Muralidharan, D.; Raj, N.; Kumar, B.K. Network simulation and vulnerability assessment tool for an enterprise network. In Proceedings of the International Conference on Computing Communication and Networking Technologies, Kanpur, India, 6–8 July 2019. [Google Scholar]
- Bowie, W.S.; Linders, J.G. A software trace facility for os/mvt. Softw. Pract. Exp. 1979, 9, 535–545. [Google Scholar] [CrossRef]
- Borgerson, B.; Godfrey, M.; Hagerty, P.; Rykken, T. The architecture of sperry univac 1100 series systems. Proc. Annu. Symp. Comput. Archit. 1979, 137–146. [Google Scholar]
- Arce, I.J.N.S. Vulnerability management at the crossroads. Netw. Secur. 2008, 5, 11–13. [Google Scholar]
- Millwater, H.R.; Wu, Y.T.; Dias, J.B.; Mcclung, R.C.; Raveendra, S.T.; Thacker, B.H. In The nessus software system for probabilistic structural analysis. Struct. Saf. Reliab. ASCE 1989, 3, 2283–2290. [Google Scholar]
- Shah, M.; Ahmed, S.; Saeed, K.; Junaid, M.; Khan, H.; Ata-ur-Rehman. Penetration testing active reconnaissance phase—optimized port scanning with nmap tool. In Proceedings of the 2nd International Conference on Computing, Mathematics and Engineering Technologies, Sukkur, Pakistan, 30–31 January 2019. [Google Scholar]
- De Vivo, M.; Carrasco, E.; Isern, G.; de Vivo, G.O.J.A.S.C.C.R. A review of port scanning techniques. Comput. Commun. Rev. 1999, 29, 41–48. [Google Scholar] [CrossRef]
- Rohrmann, R.R.; Ercolani, V.J.; Patton, M.W. In Large scale port scanning through tor using parallel nmap scans to scan large portions of the ipv4 range. In Proceedings of the IEEE International Conference on Intelligence & Security Informatics, Beijing, China, 22–24 July 2017. [Google Scholar]
- Durumeric, Z.; Wustrow, E.; Halderman, J.A. Zmap: Fast internet-wide scanning and its security applications. In Proceedings of the 22nd USENIX Security Symposium, Washington, DC, USA, 14–16 August 2013. [Google Scholar]
- Mazel, J.; Strullu, R. Identifying and characterizing zmap scans: A cryptanalytic approach. arXiv 2019, arXiv:1908.04193. [Google Scholar]
- Lee, S.; Im, S.Y.; Shin, S.H.; Roh, B.H.; Lee, C. Implementation and vulnerability test of stealth port scanning attacks using zmap of censys engine. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016. [Google Scholar]
- De Santis, G.; Lahmadi, A.; Francois, J.; Festor, O. Modeling of ip scanning activities with hidden markov models: Darknet case study. In Proceedings of the 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Larnaca, Cyprus, 21–23 November 2016. [Google Scholar]
- Dilley, N.; Lange, J. An empirical study of messaging passing concurrency in go projects. In Proceedings of the IEEE 26th International Conference on Software Analysis, Evolution and Reengineering (SANER), Hangzhou, China, 24–27 February 2019. [Google Scholar]
- Fava, D.S.; Steffen, M. Ready, Set, Go! Data-Race Detection and the Go Language; Elsevier: Amsterdam, The Netherlands, 2019; Volume 195. [Google Scholar]
- Emoto, M.; Shibata, K.; Watanabe, K.; Ohdachi, S.; Ida, K.; Sudo, S. Development of a flexible visualization tool. Fusion Eng. Des. 2002, 60, 367–371. [Google Scholar] [CrossRef]
- Garea, A.S.; Heras, D.B.; Argüello, F. An open source desktop application for classification of remote sensing data. In Proceedings of the IEEE International Conference on Intelligent Data Acquisition & Advanced Computing Systems: Technology & Applications, Warsaw, Poland, 24–26 September 2015. [Google Scholar]
- Patel, S.K.; Sonker, A. In Internet protocol identification number based ideal stealth port scan detection using snort. In Proceedings of the International Conference on Computational Intelligence and Communication Networks, Tehri, India, 23–25 December 2016; pp. 422–427. [Google Scholar]
- Myers, D.; Foo, E.; Radke, K. Internet-wide scanning taxonomy and framework, artificial intelligence and symbolic computation. In Proceedings of the 13th Australasian Information Security Conference, Sydney, Australia, 27–30 January 2015; pp. 61–65. [Google Scholar]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Surveying port scans and their detection methodologies. Comput. J. 2011, 54, 1565–1581. [Google Scholar] [CrossRef]
- Bou-Harb, E.; Debbabi, M.; Assi, C. On fingerprinting probing activities. Comput. Secur. 2014, 43, 35–48. [Google Scholar] [CrossRef]
- Durumeric, Z.; Bailey, M.; Halderman, J.A.; Assoc, U. An internet-wide view of internet-wide scanning. In Proceedings of the 23rd USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 65–78. [Google Scholar]
- Sivanathan, A.; Gharakheili, H.H.; Sivaraman, V. Can we classify an iot device using tcp port scan? In Proceedings of the IEEE International Conference on Information and Automation for Sustainability (ICIAFS), Sri Lanka, India, 21–22 December 2018. [Google Scholar]
- Kumar, S.; Dutta, K.; Asati, A. Two Pass Port Scan Detection Technique Based on Connection Pattern and Status on Sampled Data. J. Comput. Commun. 2015, 3, 1–8. [Google Scholar] [CrossRef] [Green Version]
- Jajal, B.; Iyer, S.; Chauhan, D. Mitigating illicit entry using website port scanning tools in indian context. In Proceedings of the International Conference on Computing for Sustainable Global Development, New Delhi, India, 13–15 March 2019. [Google Scholar]
- Gupta, S. Port. Scanning: Uncover key Concepts of Website and Network Security; Springer: Berlin, Germany, 2019. [Google Scholar]
- Ensafi, R.; Park, J.C.; Kapur, D.; Crandall, J.R. Idle port scanning and non-interference analysis of network protocol stacks using model checking. In Proceedings of the Usenix Security Symposium, Washington, DC, USA, 11–13 August 2010. [Google Scholar]
- Bodenheim, R.; Butts, J.; Dunlap, S.; Mullins, B. Evaluation of the ability of the shodan search engine to identify internet-facing industrial control devices. Int. J. Crit. Infrastruct. Prot. 2014, 7, 114–123. [Google Scholar] [CrossRef]
- Fernandez-Carames, T.M.; Fraga-Lamas, P. Teaching and learning iot cybersecurity andvulnerability assessment with shodan through practical use cases. Sensors 2020, 20, 3048. [Google Scholar] [CrossRef] [PubMed]





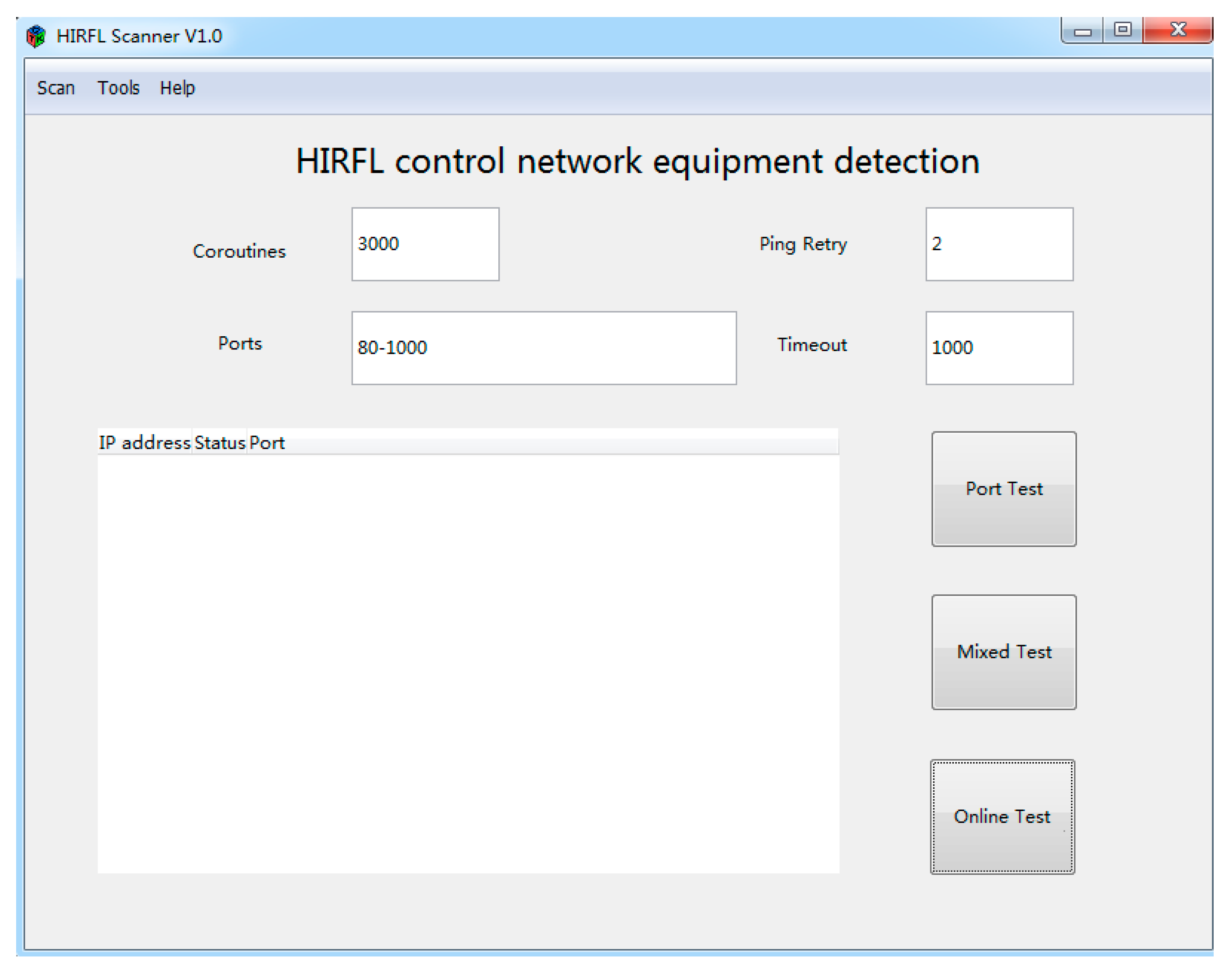
| VLAN | IP Address | VLAN_DESC | VLAN | IP Address | VLAN_DESC |
|---|---|---|---|---|---|
| 10 | 10.10.2.0/24 | Central room | 107 | 10.10.107.0/24 | CSRm |
| 14 | 10.10.14.0/24 | Single particle | 108 | 10.10.108.0/24 | CSRm |
| 15 | 10.10.15.0/24 | Single particle | 109 | 10.10.109.0/24 | CSRm |
| 16 | 10.10.16.0/24 | SSC | 110 | 10.10.110.0/24 | CSRm |
| 17 | 10.10.17.0/24 | SSC | 111 | 10.10.111.0/24 | CSRm |
| 41 | 10.10.41.0/24 | T128 | 112 | 10.10.112.0/24 | CSRm |
| 42 | 10.10.42.0/24 | T128 | 113 | 10.10.113.0/24 | Langdao North |
| 43 | 10.10.43.0/24 | T128 | 114 | 10.10.114.0/24 | Langdao North |
| 45 | 10.10.45.0/24 | SFC | 115 | 10.10.115.0/24 | Langdao North |
| 46 | 10.10.46.0/24 | SFC | 116 | 10.10.116.0/24 | Langdao South |
| 48 | 10.10.48.0/24 | SFC | 117 | 10.10.117.0/24 | Langdao South |
| 51 | 10.10.51.0/24 | HIRFL | 118 | 10.10.118.0/24 | Langdao South |
| 52 | 10.10.52.0/24 | HIRFL | 119 | 10.10.119.0/24 | Langdao South |
| 53 | 10.10.53.0/24 | HIRFL | 120 | 10.10.120.0/24 | RIBLL2 |
| 54 | 10.10.54.0/24 | HIRFL | 121 | 10.10.121.0/24 | RIBLL2 |
| 90 | 10.10.90.0/24 | HIRFL | 122 | 10.10.122.0/24 | RIBLL2 |
| 91 | 10.10.91.0/24 | HIRFL | 123 | 10.10.123.0/24 | RIBLL2 |
| 92 | 10.10.92.0/24 | HIRFL | 124 | 10.10.124.0/24 | RIBLL2 |
| 95 | 10.10.95.0/24 | HIRFL | 125 | 10.10.125.0/24 | RIBLL2 |
| 96 | 10.10.96.0/24 | HIRFL | 126 | 10.10.126.0/24 | CSRe |
| 99 | 10.10.99.0/24 | RIBLL1 | 127 | 10.10.127.0/24 | CSRe |
| 100 | 10.10.100.0/24 | RIBLL1 | 128 | 10.10.128.0/24 | CSRe |
| 101 | 10.10.101.0/24 | RIBLL1 | 129 | 10.10.129.0/24 | CSRe |
| 102 | 10.10.102.0/24 | CSRm | 130 | 10.10.130.0/24 | CSRe |
| 103 | 10.10.103.0/24 | CSRm | 131 | 10.10.131.0/24 | CSRe |
| 104 | 10.10.104.0/24 | CSRm | 998 | 172.16.110.0/24 | virtualization |
| 105 | 10.10.105.0/24 | CSRm | 999 | 172.16.100.0/24 | virtualization |
| 106 | 10.10.106.0/24 | CSRm |
| Num of IP | HS Time (s) | Nmap Time (s) | HS Result | Nmap Result | ||||
|---|---|---|---|---|---|---|---|---|
| T3 | T4 | T5 | T3 | T4 | T5 | |||
| 253 | 4.12 | 21.83 | 21.53 | 20.77 | 47 | 47 | 47 | 47 |
| 2530 | 5.98 | 102.85 | 96.77 | 87.75 | 201 | 201 | 201 | 201 |
| 5060 | 11.45 | 184.58 | 175.52 | 159.10 | 442 | 441 | 441 | 441 |
| 7590 | 16.57 | 267.90 | 247.58 | 228.15 | 657 | 656 | 656 | 656 |
| 10,120 | 30.42 | 329.27 | 311.39 | 286.92 | 843 | 839 | 840 | 841 |
| 13,915 | 44.08 | 436.21 | 415.03 | 378.50 | 1143 | 1140 | 1139 | 1140 |
| Num of Ports | HS Time (s) | Nmap T5 Time (s) | HS Result | Nmap T5 result | ||
|---|---|---|---|---|---|---|
| sS | sT | sS | sT | |||
| 1000 | 0.31 | 18.77 | 65.10 | 9 | 9 | 9 |
| 10,000 | 4.12 | 21.36 | 251.92 | 12 | 12 | 12 |
| 20,000 | 7.32 | 23.68 | 456.72 | 11 | 12 | 12 |
| 30,000 | 10.84 | 27.18 | 662.92 | 13 | 13 | 13 |
| 40,000 | 14.99 | 29.00 | 868.51 | 15 | 15 | 15 |
| 65,535 | 20.65 | 37.34 | 1391.98 | 16 | 17 | 17 |
| Port | Service | HS Count | Nmap Count | Variance |
|---|---|---|---|---|
| 80 | http | 262 | 256 | 6 |
| 3389 | ms-wbt-server | 155 | 148 | 7 |
| 445 | microsoft-ds | 143 | 147 | 4 |
| 22 | ssh | 139 | 143 | 4 |
| 111 | rpcbind | 107 | 110 | 3 |
| 49,152 | unknow | 106 | 110 | 4 |
| 23 | telnet | 102 | 107 | 5 |
| 49,153 | unknow | 99 | 101 | 2 |
| 5064 | channel access | 92 | 97 | 5 |
| 59,110 | ni-psp | 80 | 83 | 3 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yuan, C.; Du, J.; Yue, M.; Ma, T. The Design of Large Scale IP Address and Port Scanning Tool. Sensors 2020, 20, 4423. https://doi.org/10.3390/s20164423
Yuan C, Du J, Yue M, Ma T. The Design of Large Scale IP Address and Port Scanning Tool. Sensors. 2020; 20(16):4423. https://doi.org/10.3390/s20164423
Chicago/Turabian StyleYuan, Chao, Jinze Du, Min Yue, and Tao Ma. 2020. "The Design of Large Scale IP Address and Port Scanning Tool" Sensors 20, no. 16: 4423. https://doi.org/10.3390/s20164423
APA StyleYuan, C., Du, J., Yue, M., & Ma, T. (2020). The Design of Large Scale IP Address and Port Scanning Tool. Sensors, 20(16), 4423. https://doi.org/10.3390/s20164423




