Enhancing Border Gateway Protocol Security Using Public Blockchain
Abstract
:1. Introduction
- Addition of a method for routers comprising an AS to learn all prefixes assigned to the AS automatically. This way we inhibit routers from advertising prefixes with their AS origin if those prefixes are not assigned to the AS.
- We implement proof-of-concept of our architecture in the public blockchain Ropsten test network. We use measured results to assess the time required to update routing information and cost in Gas based on the number of prefixes per transaction.
2. State of the Art
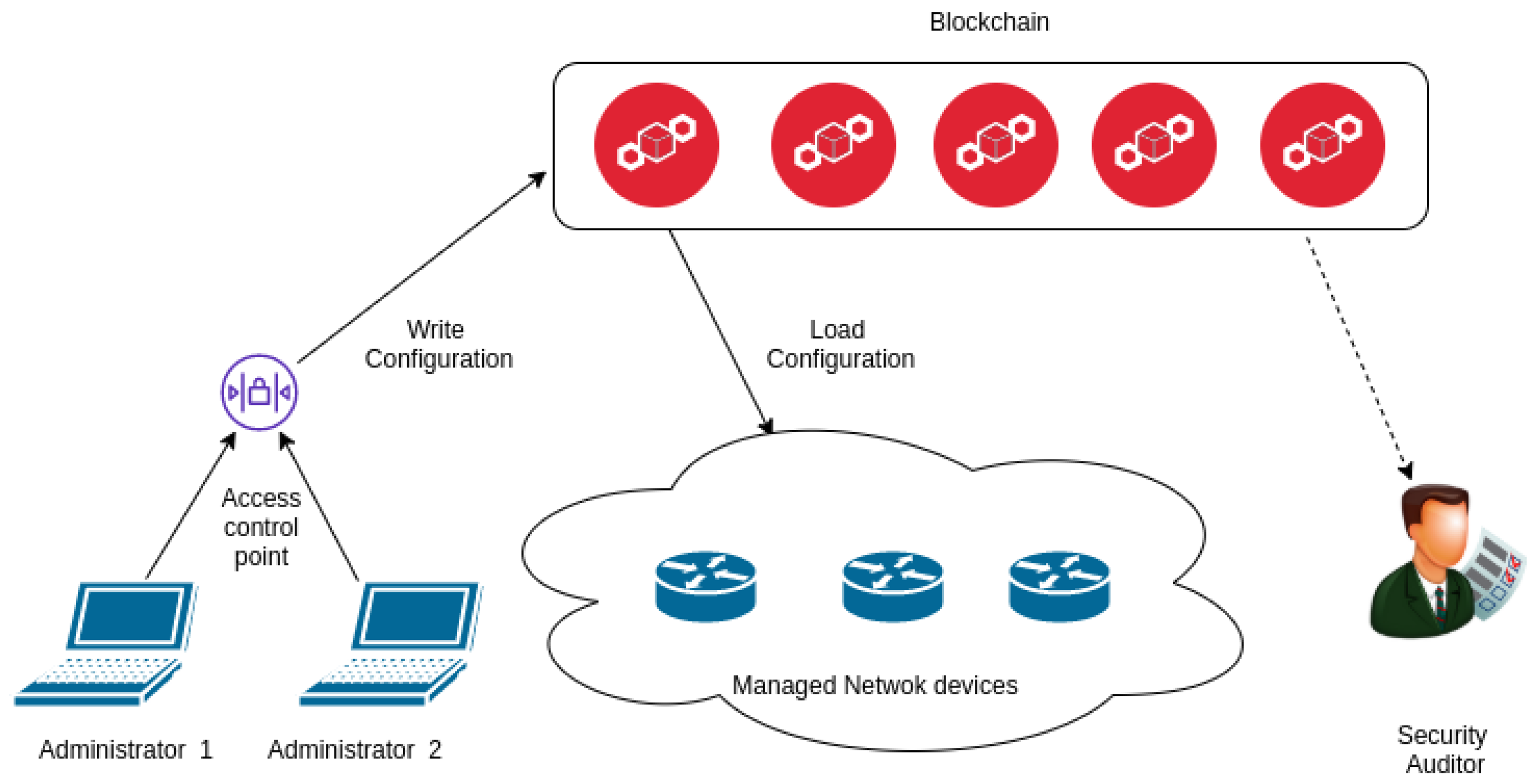
3. Design
- RIR Rx allocates prefixes.
- Rx registers to BGPMC, it is a main smart contract where are stored ROA entries and subconfiguration of the router.
- Lx requests to create LIR contract.
- Rx allocates prefixes for LIR which LIR will assign ISPes.
- Rx adds LIR to ACL in BGPMC smart contract.
- ISPx requests LIR to assign an IP prefix to it.
- The prefix is verified to see if ROA record already exists with this IP prefix.
- Verified IP prefix is recorded in a new block together with mask and max length as ROA entry in the blockchain.
- ISPx adds a new subconfiguration for border router.
- For every prefix of the subconfiguration is checked ROA entry in the blockchain.
- Verified subconfiguration is uploaded to the blockchain.
- Affected router downloads the block and loads the new subconfiguration.
3.1. Operations
- BGP Prefixes Manager Contract (BGPPMC) is the leading smart contract that is common to all participants. It is built by the central authority of IANA. It keeps ROA entries and subconfigurations of routers in the one place.
- RIR contract is designed for Regional Internet registry. It is responsible for allocation of IP prefixes and create smart contracts to LIR.
- LIR contract is intended for local/national Internet registry. They lease prefixes with the right to create ROA entries that are bound on their resources.
3.2. Known Limitations
4. Results
5. Discussion
6. Materials and Methods
- 0xd57a1aAD0fD9f1E27Fadb659136A868D360b4251
- 0x5bF128C371BCD858e398F1432701c38938bCe066
- 0xf8F78b24819b0219aF51905DE88Adb39a560a296
7. Conclusions and Future work
Author Contributions
Funding
Conflicts of Interest
References
- Rekhter, Y.; Tony, L.; Susan, H. A Border Gateway Protocol 4 (BGP-4). Available online: https://www.hjp.at/doc/rfc/rfc4271.html (accessed on 5 August 2020).
- Cho, S.; Fontugne, R.; Cho, K.; Dainotti, A.; Gill, P. BGP hijacking classification. In Proceedings of the 2019 Network Traffic Measurement and Analysis Conference (TMA), Paris, France, 19–21 June 2019; pp. 25–32. [Google Scholar]
- Mitseava, A.; Panchenko, A.; Engel, T. The state of affairs in BGP security: A survey of attacks and defenses. Comput. Commun. 2018, 124, 45–60. [Google Scholar] [CrossRef]
- Lepinski, M.; Sriram, K. BGPsec Protocol Specification. Available online: https://www.hjp.at/doc/rfc/rfc8205.html (accessed on 5 August 2020).
- Lepinski, M.; Kent, S. An Infrastructure to Support Secure Internet Routing. Available online: https://www.hjp.at/doc/rfc/rfc6480.html (accessed on 5 August 2020).
- Arslanian, H.; Fischer, F. Blockchain As an Enabling Technology. In The Future of Finance; Palgrave Macmillan: Cham, London, UK, 2019; pp. 113–121. [Google Scholar]
- Lai, R.; Chuen, D.L.K. Blockchain—From public to private. In Handbook of Blockchain, Digital Finance, and Inclusion; Academic Press: Cambridge, MA, USA, 2018; Volume 2, pp. 145–177. [Google Scholar]
- Helebrandt, P.; Belluš, M.; Ries, M.; Kotuliak, I.; Khilenko, V. Blockchain Adoption for Monitoring and Management of Enterprise Networks. In Proceedings of the 2018 9th IEEE Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 1–5. [Google Scholar]
- Xing, Q.; Wang, B.; Wang, X. BGPcoin: Blockchain-Based Internet Number Resource Authority and BGP Security Solution. Symmetry 2018, 10, 408. [Google Scholar] [CrossRef] [Green Version]
- Saad, M.; Anwar, A.; Ahmad, A.; Alasmary, H.; Yuksel, M.; Mohaisen, A. RouteChain: Towards Blockchain-based Secure and Efficient BGP Routing. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Korea, 14–17 May 2019; pp. 210–218. [Google Scholar]
- Hari, A.; Lakshmaan, T.V. The internet blockchain: A distributed, tamper-resistant transaction framework for the internet. In Proceedings of the 15th ACM Workshop on Hot Topics in Networks, Atlanta, GA, USA, 16 November 2016; pp. 204–210. [Google Scholar]
- Ma, X.; Xu, D.; Dang, H. BGP-LSChain: An Inter-domain Link State Sharing Framework Based on Blockchain. In Proceedings of the 2019 International Conference on Blockchain Technology, Honolulu, HI, USA, 15–17 March 2019; pp. 19–23. [Google Scholar]
- Shapira, T.; Shavitt, Y. A Deep Learning Approach for IP Hijack Detection Based on ASN Embedding. In Proceedings of the Workshop on Network Meets AI & ML, Virtual Event, New York, NY, USA, 23 August 2020; pp. 35–41. [Google Scholar]
- McGlynn, K.; Acharya, H.B.; Kwon, M. Detecting BGP Route Anomalies with Deep Learning. In Proceedings of the 2019 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 1039–1040. [Google Scholar]
- Martinez-Garcia, M.; Zhang, Y.; Suzuki, K.; Zhang, Y.D. Deep Recurrent Entropy Adaptive Model for System Reliability Monitoring. IEEE Trans. Ind. Informatics 2020. [Google Scholar] [CrossRef]
- Košťál, K.; Helebrandt, P.; Belluš, M.; Ries, M.; Kotuliak, I. Management and Monitoring of IoT Devices Using Blockchain. Sensors 2019, 19, 856. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ropsten Testnet Explorer. Available online: https://ropsten.etherscan.io (accessed on 3 August 2020).
- Infura. Available online: https://infura.io (accessed on 3 August 2020).
- Web3.py Python Library. Available online: https://web3py.readthedocs.io/en/latest (accessed on 3 August 2020).
- Ubuntu Server 20.04 LTS. Available online: https://releases.ubuntu.com/20.04/ (accessed on 3 August 2020).
- Ma, J. Gwei. Available online: https://academy.binance.com/glossary/gwei (accessed on 3 August 2020).
- Ethereum Network Status. Available online: https://ethstats.net (accessed on 3 August 2020).
- Eth Gas Station. Available online: https://ethgasstation.info (accessed on 3 August 2020).
- Kouhizadeh, M.; Sarkis, J. Blockchain Practices, Potentials, and Perspectives in Greening Supply Chains. Sustainability 2018, 10, 3652. [Google Scholar] [CrossRef] [Green Version]
- Young, M. Ethereum 2.0 Final Testnet Set to Launch on August 4. Available online: https://cointelegraph.com/news/ethereum-20-final-testnet-set-to-launch-on-august-4 (accessed on 3 August 2020).
- Zhang, R.; Chan, W.K.V. Evaluation of Energy Consumption in Block-Chains with Proof of Work and Proof of Stake. J. Phys. Conf. Ser. 2020, 1584, 012023. [Google Scholar] [CrossRef]
- Blockchain Size. Available online: https://www.blockchain.com/charts/blocks-size (accessed on 3 August 2020).
- Nizamuddin, N.; Salah, K.; Azad, M.A.; Arshad, J.; Rehman, M.H. Decentralized document version control using ethereum blockchain and IPFS. Comput. Electr. Eng. 2019, 76, 183–197. [Google Scholar] [CrossRef] [Green Version]
- Naz, M.; Al-zahrani, F.A.; Khalid, R.; Javaid, N.; Qamar, A.M.; Afzal, M.K.; Shafiq, M. A Secure Data Sharing Platform Using Blockchain and Interplanetary File System. Sustainability 2019, 11, 7054. [Google Scholar] [CrossRef] [Green Version]
- Mastilak, L. Source Code. 2020. Available online: https://gitlab.com/luka73/bgp-blck.git (accessed on 3 August 2020).
- Bach, L.M.; Mihaljevic, B.; Zagar, M. Comparative analysis of blockchain consensus algorithms. In Proceedings of the 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018; pp. 1545–1550. [Google Scholar]






© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mastilak, L.; Galinski, M.; Helebrandt, P.; Kotuliak, I.; Ries, M. Enhancing Border Gateway Protocol Security Using Public Blockchain. Sensors 2020, 20, 4482. https://doi.org/10.3390/s20164482
Mastilak L, Galinski M, Helebrandt P, Kotuliak I, Ries M. Enhancing Border Gateway Protocol Security Using Public Blockchain. Sensors. 2020; 20(16):4482. https://doi.org/10.3390/s20164482
Chicago/Turabian StyleMastilak, Lukas, Marek Galinski, Pavol Helebrandt, Ivan Kotuliak, and Michal Ries. 2020. "Enhancing Border Gateway Protocol Security Using Public Blockchain" Sensors 20, no. 16: 4482. https://doi.org/10.3390/s20164482
APA StyleMastilak, L., Galinski, M., Helebrandt, P., Kotuliak, I., & Ries, M. (2020). Enhancing Border Gateway Protocol Security Using Public Blockchain. Sensors, 20(16), 4482. https://doi.org/10.3390/s20164482






