Swarm-Intelligence-Centric Routing Algorithm for Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Works
2.1. Relevant Routing Algorithm for WSN
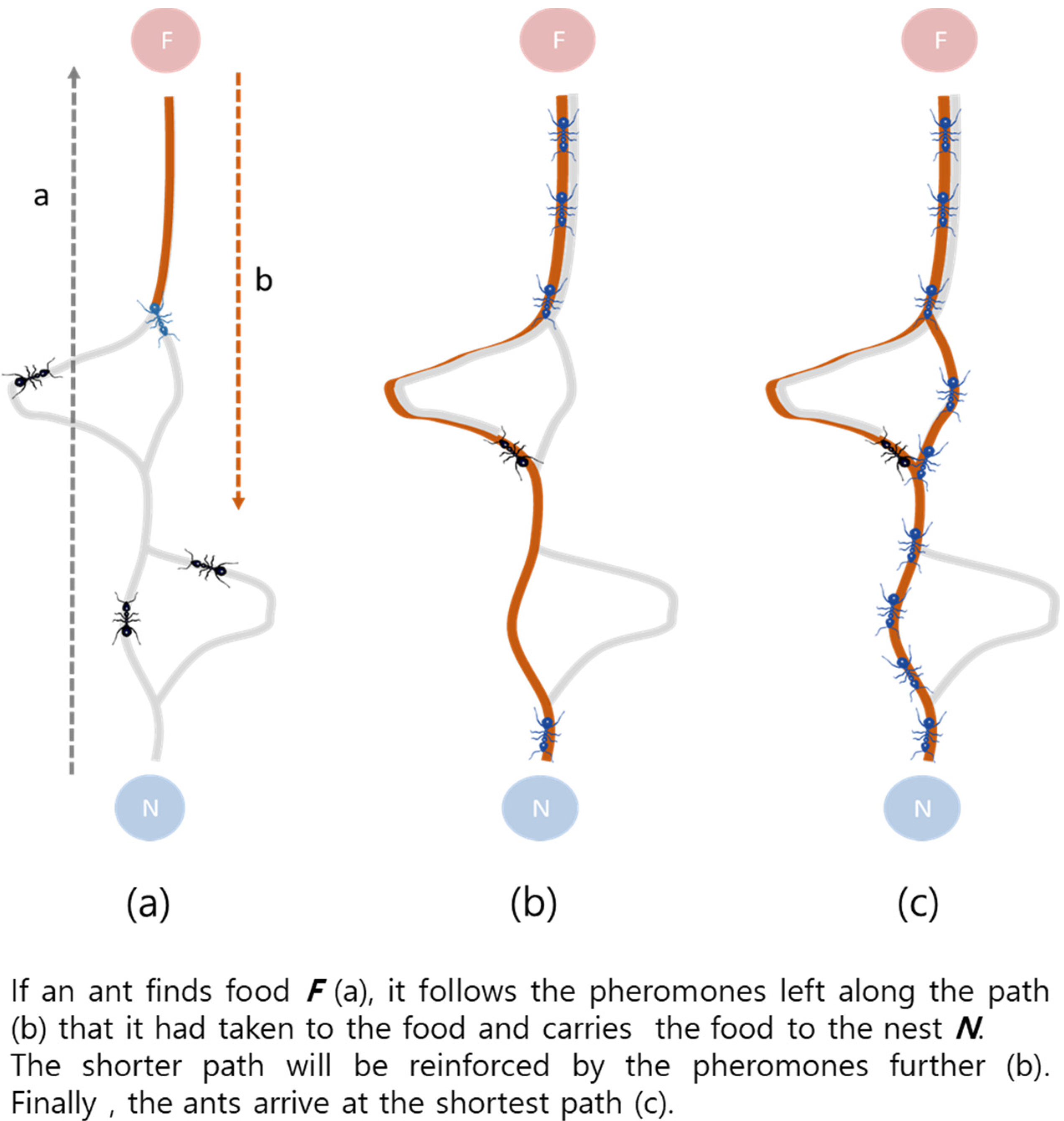
2.2. ACO Algorithm
3. Proposed SICROA
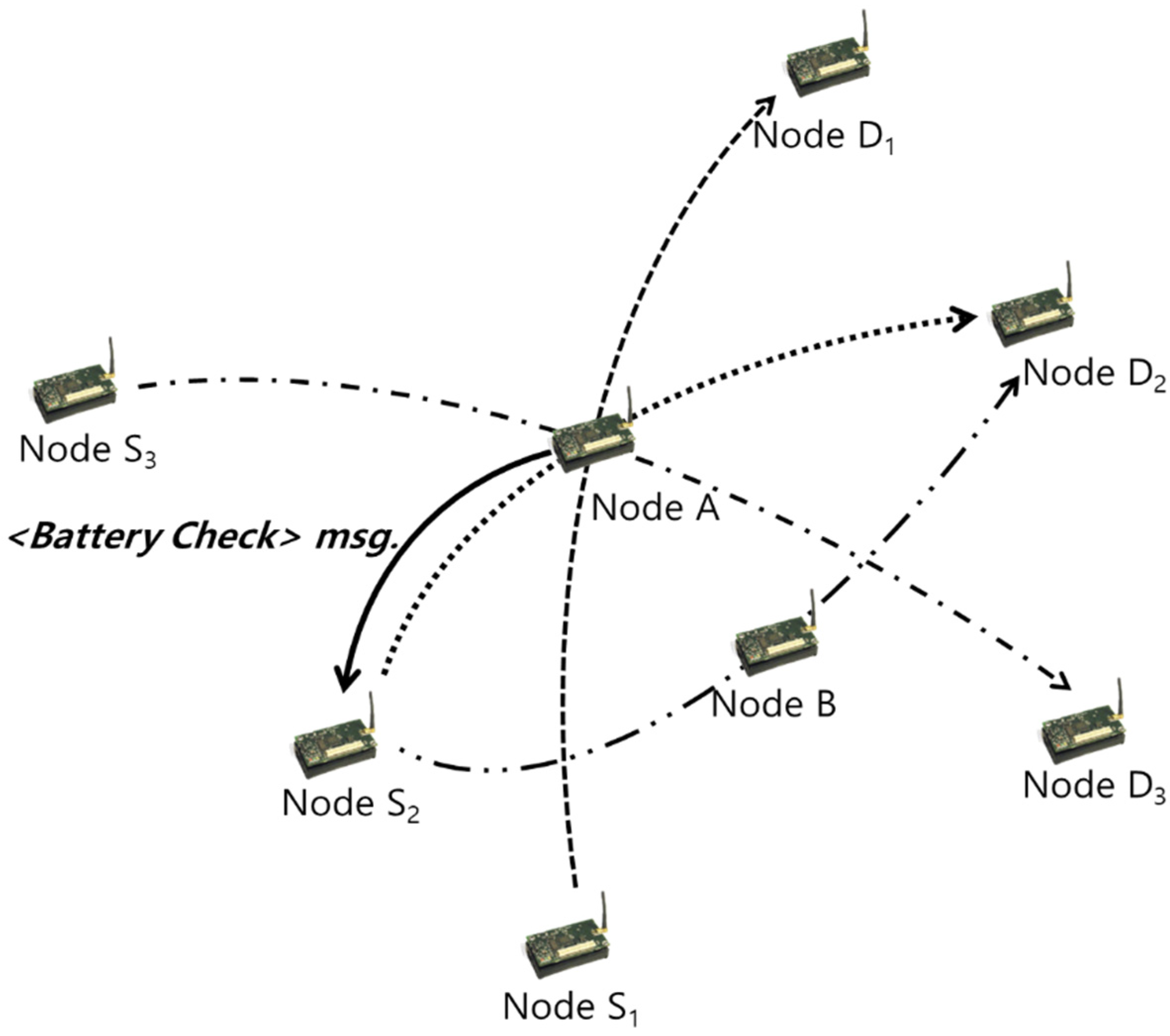
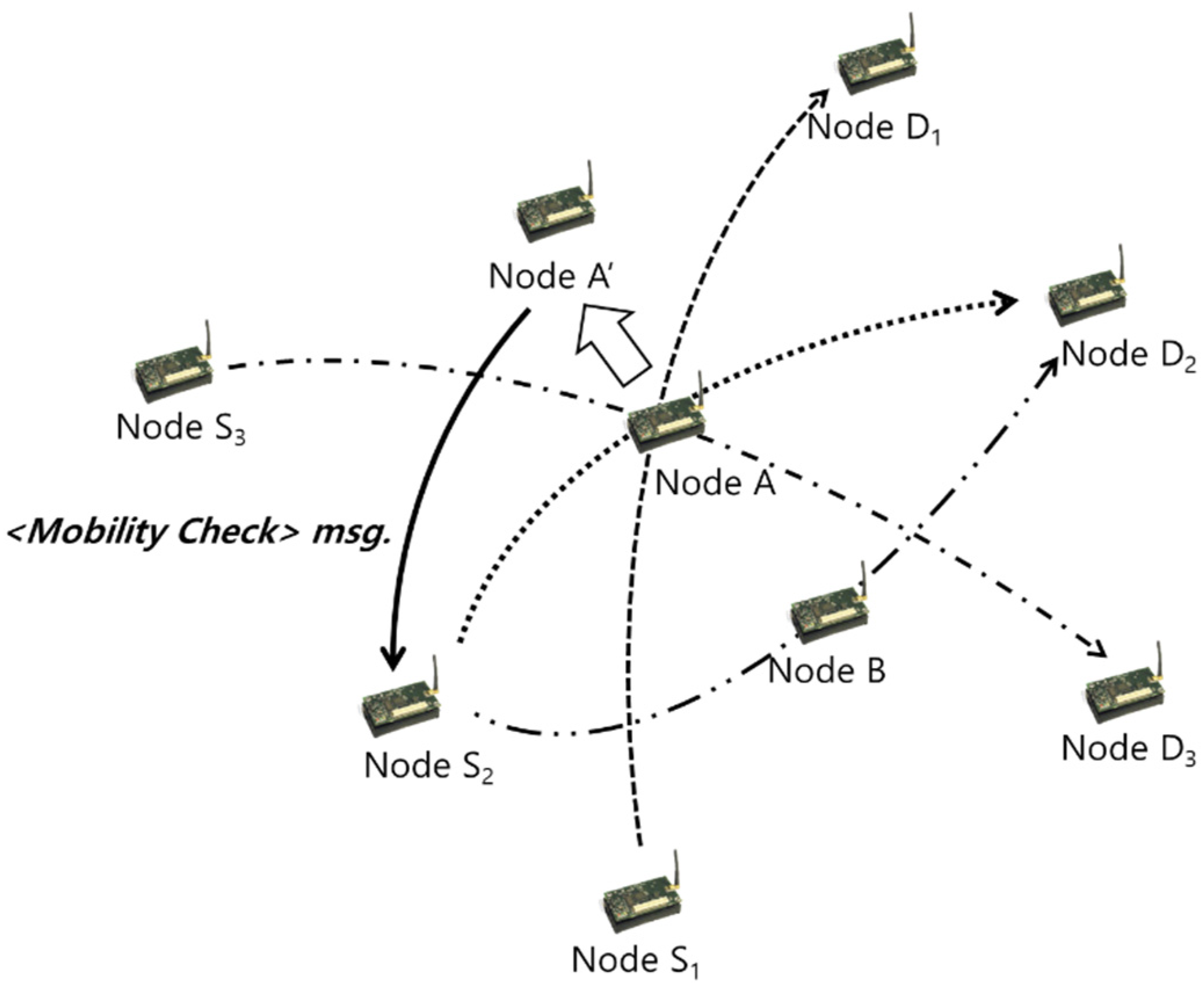
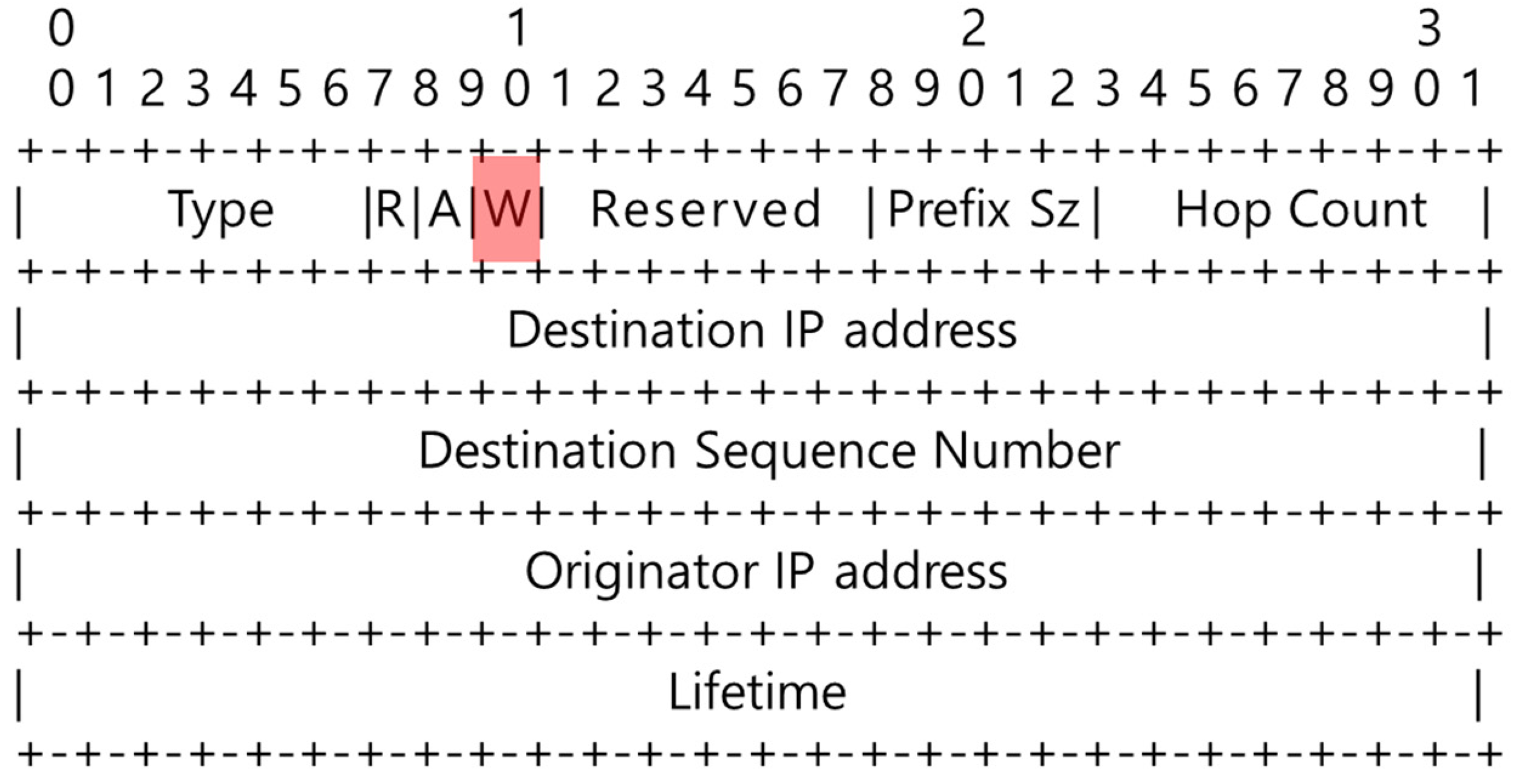
3.1. Collision Avoidance through Interrupts (CATI)
| Algorithm 1: Collision Avoidance through Interrupts |
| [When node A receives a packet] |
| if RREQ message in a packet |
| if node A is in the interrupt state for battery or mobility |
| ignore the packet |
| else |
| process the packet using the existing routing algorithm |
| else if receive interrupt message for battery or mobility |
| if the interrupt state is destined to node A |
| initiate the route-discovery mechanism of the existing routing algorithm |
| else |
| forward the packet with the alternative route |
| [At the end of a time interval (for lifetime & mobility)] |
| if # of forwarding packets for the time interval ≥ threshold |
| change the state to battery check or mobility check |
| send a <Battery Check> or <Mobility Check> message to the source of last received packet |
| if # of forwarding packets for the time interval < threshold |
| change the state to normal |
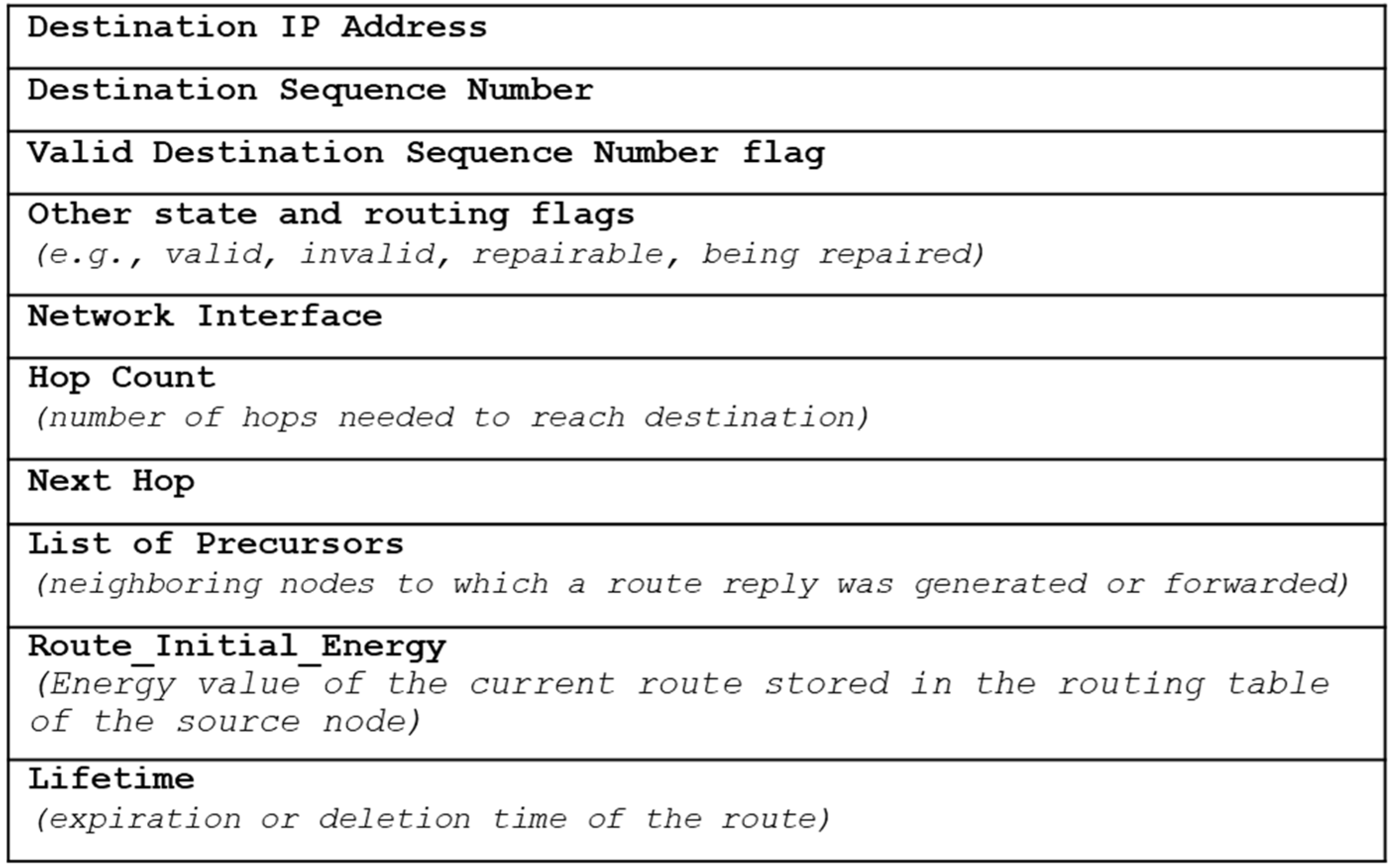
3.2. Link-Quality Prediction and Maintenance
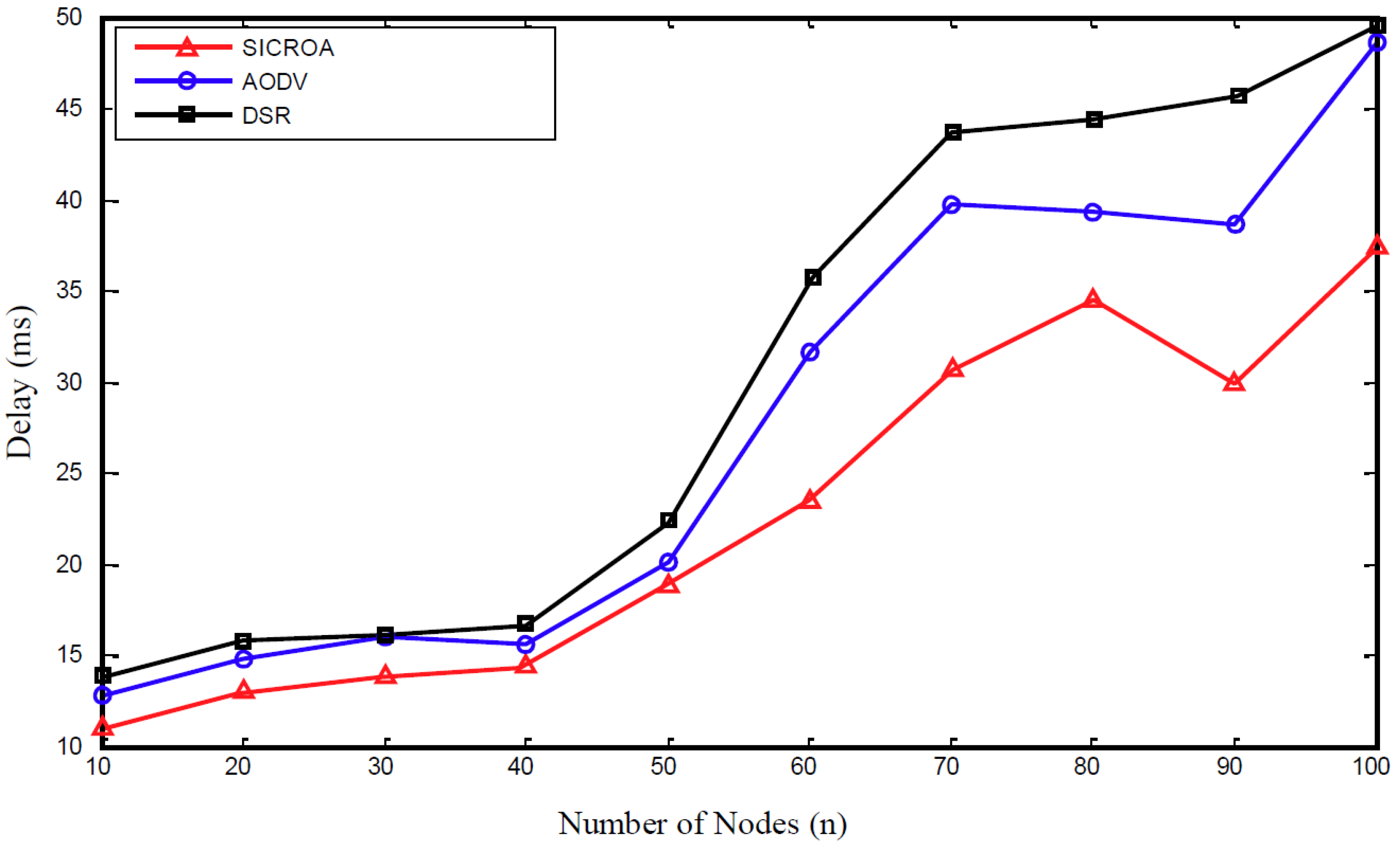
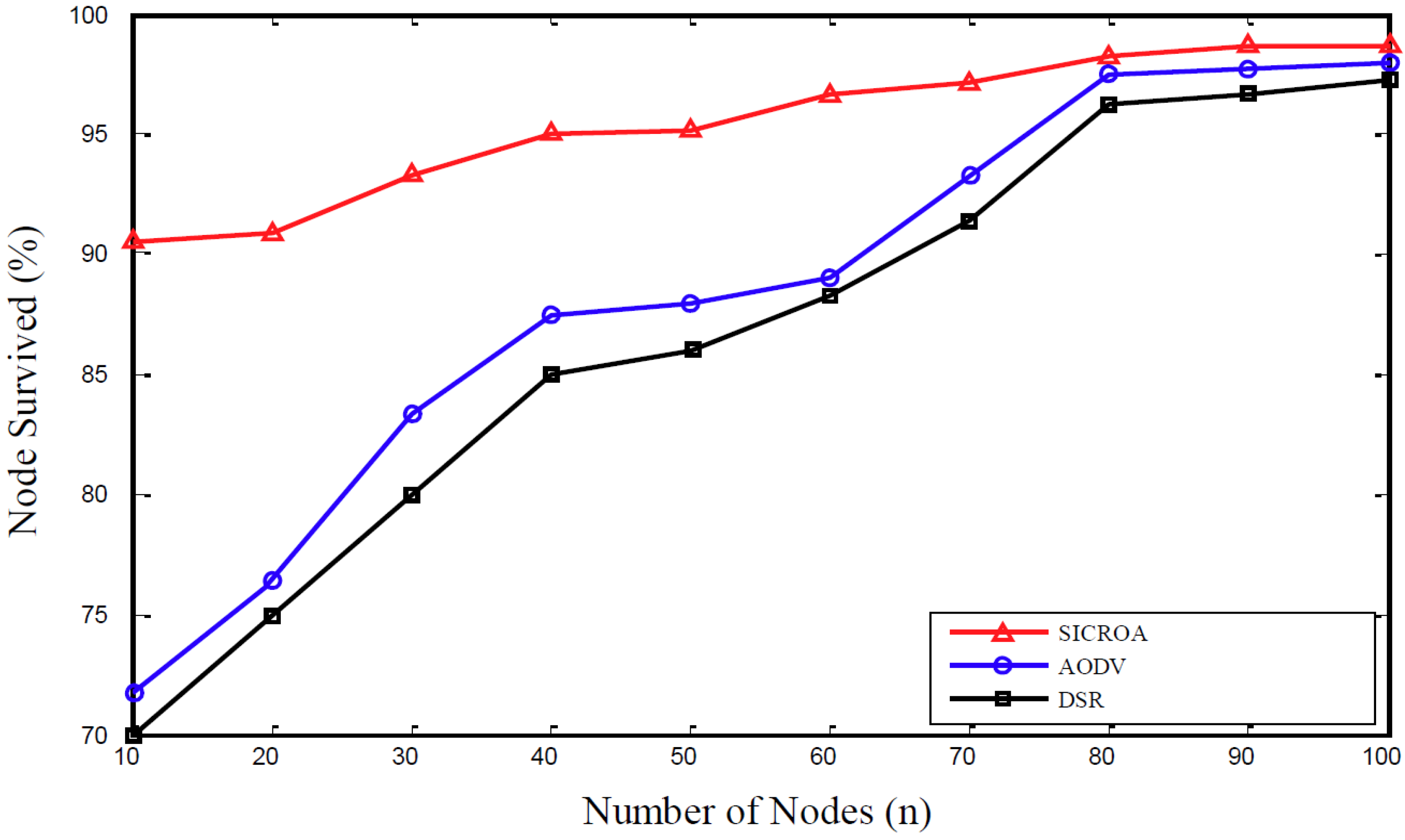
4. Performance Evaluation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Yang, X.-S.; Karamanoglu, M. Swarm intelligence and bio-inspired computation: An overview. In Swarm Intelligence and Bio-inspired Computation; Yang, X.-S., Cui, Z., Xiao, R., Gandomi, A.H., Karamanoglu, M., Eds.; Elsevier: Oxford, UK, 2013; pp. 3–23. [Google Scholar]
- Saka, M.P.; Doğan, E.; Aydogdu, I. Analysis of swarm intelligence–based algorithms for constrained optimization. In Swarm Intelligence and Bio-inspired Computation; Yang, X.-S., Cui, Z., Xiao, R., Gandomi, A.H., Karamanoglu, M., Eds.; Elsevier: Oxford, UK, 2013; pp. 25–48. [Google Scholar]
- Caro, G.D.; Ducatelle, F.; Gambardella, L.M. Swarm intelligence for routing in mobile ad hoc networks. In Proceedings of the 2005 IEEE Swarm Intelligence Symposium, Pasadena, CA, USA, 8–10 June 2005; pp. 76–83. [Google Scholar]
- Lee, M.; Kim, H.; Yoe, H. Wireless sensor networks based on bio-inspired algorithms. In Computational Science and Its Applications—ICCSA 2018; Gervasi, O., Murgante, B., Misra, S., Stankova, E., Torre, C.M., Rocha, A.M.A.C., Taniar, D., Apduhan, B.O., Tarantino, E., Ryu, Y., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 719–725. [Google Scholar]
- Correia, F.; Vazão, T.; Lobo, V.J. Models for pheromone evaluation in ant systems for mobile ad-hoc networks. In Proceedings of the 2009 First International Conference on Emerging Network Intelligence, Sliema, Malta, 11–16 October 2009; pp. 85–90. [Google Scholar]
- Chiang, F.; Braun, R. A nature inspired multi-agent framework for autonomic service management in ubiquitous computing environments. In Proceedings of the 2005 ICSC Congress on Computational Intelligence Methods and Applications, Istanbul, Turkey, 15–17 December 2005; p. 5. [Google Scholar]
- Dorigo, M.; Blum, C. Ant colony optimization theory: A survey. Theor. Comput. Sci. 2005, 344, 243–278. [Google Scholar] [CrossRef]
- Mohan, B.C.; Baskaran, R. A survey: Ant colony optimization based recent research and implementation on several engineering domain. Expert Syst. Appl. 2012, 39, 4618–4627. [Google Scholar] [CrossRef]
- Dorigo, M.; Birattari, M.; Stutzle, T. Ant colony optimization. IEEE Comput. Intell. Mag. 2006, 1, 28–39. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.-J. Energy efficient routing algorithm with mobile sink support for wireless sensor networks. Sensors 2019, 19, 1494. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wang, J.; Gu, X.; Liu, W.; Sangaiah, A.K.; Kim, H.-J. An empower Hamilton loop based data collection algorithm with mobile agent for WSNs. Hum. Cent. Comput. Inf. Sci. 2019, 9, 18. [Google Scholar] [CrossRef]
- Falaghi, H.; Haghifam, M.-R. ACO based algorithm for distributed generation sources allocation and sizing in distribution systems. In Proceedings of the 2007 IEEE Lausanne Power Tech, Lausanne, Switzerland, 1–5 July 2007; pp. 555–560. [Google Scholar]
- Cai, W.; Jin, X.; Zhang, Y.; Chen, K.; Wang, R. ACO based QOS routing algorithm for wireless sensor networks. In Proceedings of the International Conference on Ubiquitous Intelligence and Computing, Wuhan, China, 3–6 September 2006; pp. 419–428. [Google Scholar]
- Okdem, S.; Karaboga, D. Routing in wireless sensor networks using an ant colony optimization (ACO) router chip. Sensors 2009, 9, 909–921. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Pantazis, N.A.; Nikolidakis, S.A.; Vergados, D.D. Energy-efficient routing protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2012, 2, 551–591. [Google Scholar] [CrossRef]
- Al-Karaki, J.N.; Kamal, A.E. Routing techniques in wireless sensor networks: A survey. IEEE Wirel. Commun. 2004, 6, 6–28. [Google Scholar] [CrossRef] [Green Version]
- Krishnamachari, B.; Estrin, D.; Wicker, S.B. The impact of data aggregation in wireless sensor networks. In Proceedings of the 22nd International Conference on Distributed Computing Systems workshops, Vienna, Austria, 2 July 2002; pp. 575–578. [Google Scholar]
- Krishnamachari, B.; Estrin, D.; Wicker, S. Modelling data-centric routing in wireless sensor networks. IEEE Infocom. 2002, 2, 39–44. [Google Scholar]
- Kim, S.; Lee, M.; Shin, C. IoT-based strawberry disease prediction system for smart farming. Sensors 2018, 18, 4051. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lee, M.; Yoe, H. Analysis of environmental stress factors using an artificial growth system and plant fitness optimization. BioMed Res. Int. 2015, 2015, 6. [Google Scholar] [CrossRef]
- Azni, A.; Saudi, M.M.; Azman, A.; Johari, A.S. Performance analysis of routing protocol for WSN using data centric approach. World Acad. Sci. Eng. Technol. 2009, 3, 1092–1095. [Google Scholar]
- Seah, W.K.; Eu, Z.A.; Tan, H.-P. Wireless sensor networks powered by ambient energy harvesting (wsn-heap)-survey and challenges. In Proceedings of the 2009 1st International Conference on Wireless Communication, Vehicular Technology, Information Theory and Aerospace and Electronic Systems Technology, Aalborg, Denmark, 17–20 May 2009; pp. 1–5. [Google Scholar]
- Rault, T.; Bouabdallah, A.; Challal, Y. Energy efficiency in wireless sensor networks: A top-down survey. Comput. Netw. 2014, 67, 104–122. [Google Scholar] [CrossRef] [Green Version]
- Saleem, M.; Di Caro, G.A.; Farooq, M. Swarm intelligence-based routing protocol for wireless sensor networks: Survey and future directions. Inf. Sci. 2011, 181, 4597–4624. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Wang, K.; Sangaiah, A.K.; Lim, S.-J. An affinity propagation-based self-adaptive clustering method for wireless sensor networks. Sensors 2019, 19, 2579. [Google Scholar] [CrossRef] [Green Version]
- Dorigo, M.; Stützle, T. Ant colony optimization: Overview and recent advances. In Handbook of metaheuristics; Springer: Cham, Switzerland, 2019; Volume 272, pp. 311–351. [Google Scholar]
- Blum, C. Ant colony optimization: Introduction and recent trends. Phys. Life Rev. 2005, 2, 353–373. [Google Scholar] [CrossRef] [Green Version]
- Bell, J.E.; McMullen, P.R. Ant colony optimization techniques for the vehicle routing problem. Adv. Eng. Inf. 2004, 18, 41–48. [Google Scholar] [CrossRef]
- Sim, K.M.; Sun, W.H. Ant colony optimization for routing and load-balancing: Survey and new directions. IEEE Trans. Syst. Man Cybern. Part A Syst. Humans 2003, 33, 560–572. [Google Scholar]
- Ding, N.; Liu, P.X. Data gathering communication in wireless sensor networks using ant colony optimization. In Proceedings of the 2004 IEEE International Conference on Robotics and Biomimetics, Shenyang, China, 22–26 August 2004; pp. 822–827. [Google Scholar]
- Wang, J.; Osagie, E.; Thulasiraman, P.; Thulasiram, R.K. Hopnet: A hybrid ant colony optimization routing algorithm for mobile ad hoc network. Ad Hoc Netw. 2009, 7, 690–705. [Google Scholar] [CrossRef]
- Singh, G.; Kumar, N.; Verma, A.K. Ant colony algorithms in MANETs: A review. J. Netw. Comput. Appl. 2012, 35, 1964–1972. [Google Scholar] [CrossRef]
- Lee, M.; Yoe, H. WiBiA: Wireless sensor networks based on biomimicry algorithms. Int. J. Comput. Intell. Syst. 2019, 12, 1212–1220. [Google Scholar] [CrossRef] [Green Version]
- Perkins, C.E.; Royer, E.M. Ad-hoc on-demand distance vector routing. In Proceedings of the WMCSA’99 Second IEEE Workshop on Mobile Computing Systems and Applications, New Orleans, LA, USA, 25–26 February 1999; pp. 90–100. [Google Scholar]
- Maltz, D.A.; Broch, J.; Johnson, D.; Hu, Y.-C.; Jetcheva, J. A performance comparison of multi-hop wireless ad hoc network routing protocols. In Proceedings of the 4th Annual ACM/IEEE International Conference on Mobile Computing and Networking, New York, NY, USA, 25 October 1998; pp. 85–97. [Google Scholar]
- Akyildiz, I.F.; Wang, X.; Wang, W. Wireless mesh networks: A survey. Comput. Netw. 2005, 47, 445–487. [Google Scholar] [CrossRef]
- Abolhasan, M.; Wysocki, T.; Dutkiewicz, E. A review of routing protocols for mobile ad hoc networks. Ad Hoc Netw. 2004, 2, 1–22. [Google Scholar] [CrossRef] [Green Version]
- Ad Hoc On-Demand Distance Vector (AODV) Routing. Available online: https://www.rfc-editor.org/info/rfc3561 (accessed on 1 September 2020).
- Issariyakul, T.; Hossain, E. Introduction to network simulator 2 (NS2); Springer: Boston, MA, USA, 2012; pp. 21–40. [Google Scholar]
- The Dynamic Source Routing Protocol (DSR) for Mobile ad Hoc Networks for IPV4. Available online: https://tools.ietf.org/html/rfc4728 (accessed on 1 September 2020).
- Wang, J.; Gao, Y.; Yin, X.; Li, F.; Kim, H.-J. An enhanced PEGASIS algorithm with mobile sink support for wireless sensor networks. Wirel. Commun. Mob. Comput. 2018, 2018, 9472075. [Google Scholar] [CrossRef]

© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shin, C.; Lee, M. Swarm-Intelligence-Centric Routing Algorithm for Wireless Sensor Networks. Sensors 2020, 20, 5164. https://doi.org/10.3390/s20185164
Shin C, Lee M. Swarm-Intelligence-Centric Routing Algorithm for Wireless Sensor Networks. Sensors. 2020; 20(18):5164. https://doi.org/10.3390/s20185164
Chicago/Turabian StyleShin, Changsun, and Meonghun Lee. 2020. "Swarm-Intelligence-Centric Routing Algorithm for Wireless Sensor Networks" Sensors 20, no. 18: 5164. https://doi.org/10.3390/s20185164
APA StyleShin, C., & Lee, M. (2020). Swarm-Intelligence-Centric Routing Algorithm for Wireless Sensor Networks. Sensors, 20(18), 5164. https://doi.org/10.3390/s20185164





