A Holistic Systems Security Approach Featuring Thin Secure Elements for Resilient IoT Deployments
Abstract
1. Introduction
1.1. Literaure Review and Proposed System Security Model Using Thin Secure Element
1.2. Design Model for Security
1.3. Contributions
- Investigation of the state of the art in hardware architectures for developing lightweight IoT security, the notion of security by design and a holistic approach for such security design.
- We deploy and demonstrate the usefulness of DREAD/STRIDE methodology for uncovering security flaws in SDLC for a real-world use case.
- Implementing Daedalus—a real-world energy platform with smart solar panels as a use case.
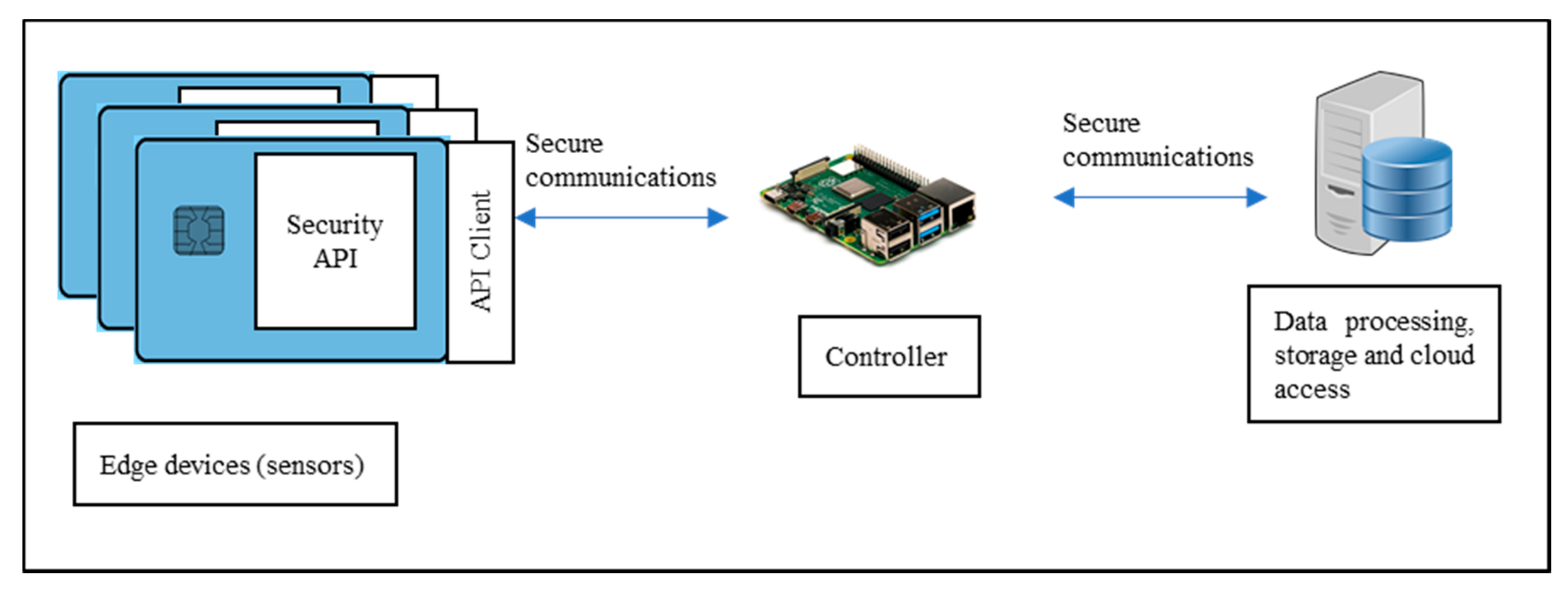
- Implementing a customized middleware that utilizes a thin secure element for enabling hardware and software security.
- Designing middleware smart circuitry that is embedded into the IoT device.
- We implement an on-board asymmetric key-pair generation so that the principle of freshness can be applied to the keys for signing the data.
- The security procedures for key management also have vulnerabilities, and we address this by implementing a zero-knowledge-password-proof (ZKPP) procedure called B_SPEKE to provide public key integrity for users of the public key needed to authenticate the data.
- We approach a service architecture by implementing a security API for accessing security functions.
- We implement a secure cloud computing service (REGUS) to hold data from all the IoT devices. REGUS forms the backbone to the computational process. It establishes a unique security mechanism through chip identity and timestamps usage, demonstrating anti-tampering and authentication with REGUS operations.
1.4. Paper Organisation
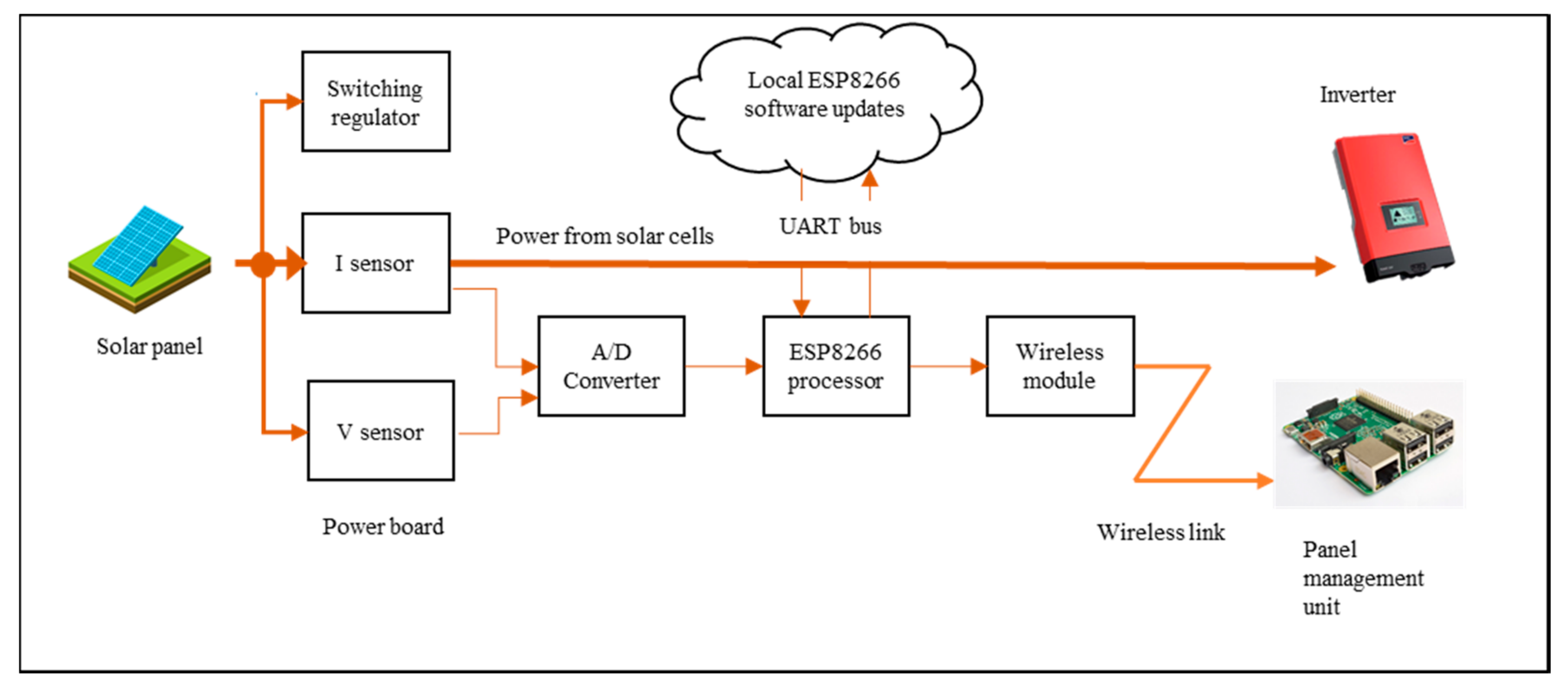
2. Daedalus: Smart Solar Panels—Use Case
Daedalus: Smart Solar Panel System
3. Phase I: System Design for Security
3.1. Threat Modelling for Daedalus
3.1.1. System Data Composition Based on Communications Diagram (Data Flow Diagrams—DFDs)
- TD1—Communication between A/D converter and ESP8266.
- TD2—Traffic from the Wi-Fi module to the database. The management module, M400 may maintain this.
- TD4—Communication-related to software update related to ESP8266.
- TD5—Communication between ESP8266 and management module, M400.
- TD3—Communication between the ESP8266 and secure element. This is the result of the threat model inclusion and its corresponding DFD is as shown in the Trust Domain and Data Flow Diagram in Section 3.3. This is covered separately in Section 3.2 where the introduction of the thin secure element is proposed.
3.1.2. Renewable Energy Generation Unit Server (REGUS) Server Architecture
3.1.3. STRIDE
3.1.4. DREAD
3.1.5. Countermeasures: Recommendations for Addressing Risk
3.2. Security Implementation
3.2.1. Daedalus Thin Secure Element
3.2.2. On-Boarding Protocols for Multos Functionalities and API
3.2.3. REGUS and System Security
3.3. Phase I: Results and Discussions
- i.
- the use of asymmetric keys for independent validation,
- ii.
- unpredictable raw data patterns that add to the quality of freshness,
- iii.
- and validation artefacts such as hashed pointers for the data assets using blockchain principles.
4. Phase II: Enhancement of Security Measures
4.1. Enhanced API
4.2. Transport of Keys
4.3. The Integrity of Public Keys
5. Conclusions and Further Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kail, E.; Banati, A.; Lászlo, E.; Kozlovszky, M. Security survey of dedicated iot networks in the unlicensed ism bands. In Proceedings of the 2018 IEEE 12th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 17–19 May 2018. [Google Scholar]
- Xu, Y.; Liu, T.; Liu, P.; Sun, H. A Search-based Firmware Code Analysis Method for IoT Devices. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018. [Google Scholar]
- Geraldine, L.; Gregory, E.; Haider, A.-K.; Carsten, M. Security and privacy of things: Regulatory challenges and gaps for the security integration of cyber-physical systems. In Third International Congress on Information and Communication Technology; Yang, X.-S., Sherratt, S., Dey, N., Joshi, A., Eds.; Springer: Singapore, 2018. [Google Scholar]
- Brandl, H.; Rosteck, T. Technology, Implementation and Application of the Trusted Computing Group Standard (TCG) Secure platforms provide new levels of security. Infineon White Paper. In Datenschutz und Datensicherheit; BI-Wiss.-Verlag: Zürich, Switzerland, 2004. [Google Scholar]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Bhat, V.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Jangirala, S.; Das, A.K.; Vasilakos, A.V. Designing Secure Lightweight Blockchain-Enabled RFID-Based Authentication Protocol for Supply Chains in 5G Mobile Edge Computing Environment. IEEE Trans. Ind. Inform. 2020, 16, 7081–7093. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and Analysis of Secure Lightweight Remote User Authentication and Key Agreement Scheme in Internet of Drones Deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Rahman, F.; Farmani, M.; Tehranipoor, M.; Jin, Y. Hardware-Assisted Cybersecurity for IoT Devices. In Proceedings of the 18th International Workshop on Microprocessor and SOC Test and Verification (MTV), Austin, TX, USA, 11–12 December 2017. [Google Scholar]
- Torr, C. Using Established, Proven Standards to Build a Secure Smart Meter Infrastructure. 2017. Available online: https://www.multos.com/uploads/Using_Established_Proven_Standards_to_Build_a_Secure_Smart_Meter_Infrastructure.pdf (accessed on 11 September 2020).
- Malina, L.; Hajny, J.; Fujdiak, R.; Hosek, J. On perspective of security and privacy-preserving solutions in the internet of things. Comput. Netw. 2016, 102, 83–95. [Google Scholar] [CrossRef]
- Dinu, D.-D. Efficient and Secure Implementations of Lightweight Symmetric Cryptographic Primitives; University of Luxembourg: Luxembourg, 2017. [Google Scholar]
- Riahi Sfar, A.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Xue, Y.; Li, J.; Nazarian, S.; Bogdan, P. Fundamental challenges toward making the IoT a reachable reality: A model-centric investigation. ACM Trans. Des. Autom. Electron. Syst. 2017, 22, 1–25. [Google Scholar] [CrossRef]
- Razouk, W.; Sgandurra, D.; Sakurai, K. A new security middleware architecture based on fog computing and cloud to support IoT constrained devices. In Proceedings of the 1st International Conference on Internet of Things and Machine Learning, Association for Computing Machinery, Liverpool, UK, 22–25 October 2017; p. 35. [Google Scholar]
- Samonas, S.; Coss, D. The CIA Strikes Back: Redefining Confidentiality, Integrity and Availability in Security. J. Inform. Syst. Secur. 2014, 10, 21–45. [Google Scholar]
- Gremaud, P.; Durand, A.; Pasquier, J. A secure, privacy-preserving IoT middleware using intel SGX. In Proceedings of the Seventh International Conference on the Internet of Things, Linz, Austria, 22–25 October 2017. [Google Scholar]
- Gremaud, P.; Durand, A.; Pasquier, J. Privacy-preserving IoT cloud data processing using SGX. In Proceedings of the 9th International Conference on the Internet of Things, Bilbao, Spain, 22–25 October 2019. [Google Scholar]
- NXP. NXP EdgeLock SE050 “Plug & Trust” Secure Element Family Provides Deeper Security for the IoT. Product and Technology News, 12 June 2019. Available online: https://media.nxp.com/news-releases/news-release-details/nxp-edgelock-se050-plug-trust-secure-element-family-provides (accessed on 11 September 2020).
- Evanczuk, S. Add a Secure Element to Build. Edge-to-Cloud Security into an IoT Design. Digi-Key, 21 November 2019. Available online: https://media.nxp.com/news-releases/news-release-details/nxp-edgelock-se050-plug-trust-secure-element-family-provides. (accessed on 11 September 2020).
- Datko, J. An Initial Thoughts on Micro-Chips New ATECC608A; Cryptotronix: Fort Collins, CO, USA, 2017. [Google Scholar]
- Gemalto. Cinterion Secure Element: Building a Strong Foundation of Trust for IoT. 2019. Available online: https://www.crunchbase.com/organization/gemalto (accessed on 11 September 2020).
- Jablon, D. The SPEKE Password-Based Key Agreement Methods. 22 October 2003. Available online: https://tools.ietf.org/html/draft-jablon-speke-02#section-4.1 (accessed on 31 July 2020).
- Jablon, D.P. Strong password-only authenticated key exchange. Comput. Commun. Rev. 1996, 26, 5–26. [Google Scholar] [CrossRef]
- Jablon, D.P. Extended password key exchange protocols immune to dictionary attack. In Proceedings of the IEEE 6th Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises, Cambridge, MA, USA, 18–20 June 1997. [Google Scholar]
- Stallings, W. Cryptography and Network Security, 7th ed.; Pearson: London, UK, 2016. [Google Scholar]
- Michael, H.; Lipner, S. The Security Development Lifecycle; Microsoft Press: Redmond, WA, USA, 2006. [Google Scholar]
- Shevchenko, N.; Chick, T.A.; O’Riordan, P.; Scanlon, T.; Woody, C. Threat Modelling: A Summary of Available Methods; Carnegie Mellon University: Pittsburgh, PA, USA, 2019. [Google Scholar]
- Watts, S. IT Security Vulnerability vs. Threat vs. Risk: What Are the Differences? Security and Compliance Blog, 12 May 2017. Available online: https://www.bmc.com/blogs/security-vulnerability-vs-threat-vs-risk-whats-difference/ (accessed on 13 May 2020).
- CERT Insider Threat Center. Security/OSSA-Metric; C.M.U. Software Engineering Institute: Pittsburgh, PA, USA, 2017. [Google Scholar]
- Zhang, S.; Ou, X.; Singhal, A.; Homer, J. An empirical study of a vulnerability metric aggregation method. In Proceedings of the 2011 World Congress in Computer Science, Las Vegas, NV, USA, 18–21 July 2011. [Google Scholar]
- Chaychian, S.; Mistretta, E.; Mallett, C.; Lee, M.; Pissanidis, G.; Ramalingam, S.; Gan, H.C.; Wisely, D. Embedded trusted monitoring and management modules for smart solar panels. In Proceedings of the IEEE WCST World Congress on Sustainable Technologies (WCST 2017), University of, Cambridge, Cambridge, UK, 11–14 December 2017. [Google Scholar]
- Ramalingam, S. Daedalus: Reaching the Sun with Solarcoins and Smart Solar Panels; EPSRC/Innovate UK Funded Project; University of Hertfordshire: Hatfield, UK, 2018. [Google Scholar]
- Edward, Y.; Constantine, L.L. Structured Design: Fundamentals of a Discipline of Computer Program and Systems Design; Yourdon Press: New York, NY, USA, 1979. [Google Scholar]
- Jones, N.; Tivnan, B. Cyber Risk Metrics Survey, Assessment, and Implementation Plan; Department of Homeland Security (DHS), Operated by the MITRE Corporation: McLean, VA, USA, 2018. [Google Scholar]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in internet-of-things. IEEE Intern. Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Microsoft® SQL Server® 2014 Service Pack 2 (SP2). 2014. Available online: https://www.microsoft.com/en-us/download/details.aspx?id=53168 (accessed on 9 September 2020).
- Microsoft®. Internet Information Services (IIS) 10.0 Express. 2017. Available online: https://www.microsoft.com/en-us/download/details.aspx?id=48264 (accessed on 9 September 2020).
- SOAP Version 1.2 Part. 0: Primer, 2nd ed.; W3C Recommendation 27 April 2007; World Wide Web Consortium (W3C): Cambridge, MA, USA, 2007; Available online: https://www.w3.org/TR/soap12-part0/ (accessed on 11 September 2020).
- Resnick, S.; Crane, R.; Bowen, C. Essential Windows Communication Foundation (WCF): For NET Framework 3.5; Addison-Wesley Professional: Boston, MA, USA, 2008. [Google Scholar]
- Lowy, J.; Montgomery, M. Programming WCF Services, 4th ed.; O’Reilly Media Inc.: Newton, MA, USA, 2015. [Google Scholar]
- Hanselman, S. Get Started with Azure Portal. Available online: https://azure.microsoft.com/en-gb/resources/videos/get-started-with-azure-portal/ (accessed on 11 September 2020).
- Christof, E.; Neve, P.D. Surviving global software development. IEEE Softw. 2001, 18, 62–69. [Google Scholar]
- Epihaneou, G.; Ramalingam, S.; Gan, H. Project Daedalus: Threat Modeling and Data Flow Decomposition for a Secure Smart Solar Panel System; University of Hertfordshire: Hatfield, UK, 2019. [Google Scholar]
- García-Morchón, Ó.; Kumar, S.; Keoh, S.; Hummen, R.; Struik, R. Security considerations in the IP-based internet of things. Wirel. Pers. Commun. 2013, 61, 527–542. [Google Scholar]
- Chin, S.-K. High-confidence design for security: Don’t trust—Verify. Commun. ACM 1999, 42, 33–37. [Google Scholar] [CrossRef]
- Iqbal, M.A.; Olaleye, O.G.; Bayoumi, M.A. A review on internet of things (IoT): Security and privacy requirements and the solution approaches. Glob. J. Comput. Sci. Technol. 2017, 16, 7. [Google Scholar]
- ISO. Identification Cards—Integrated Circuit Cards, in Part 4: Organization, Security and Commands for Interchange; ISO: Geneva, Switzerland, 2020; p. 176. [Google Scholar]
- Gutierrez, C.M.; Turner, J.M. The keyed-hash message authentication code (HMAC). In Cryptography Standards; National Institute of Standards and Technology: Gaithersburg, ML, USA, 2008; MD 20899-8900. [Google Scholar]
- Vines, R.D.; Krutz, R.L. Cloud Security: A Comprehensive Guide to Secure Cloud Computing; John Wiley & Sons: Hoboken, NJ, USA, 2010. [Google Scholar]
- Microsoft. NET Framework 4.8 Documentation; Microsoft: Albuquerque, NM, USA, 2020. [Google Scholar]
- Adler, J.; Berryhill, R.; Veneris, A.; Poulos, Z.; Veira, N.; Kastania, A. Astraea: A decentralised blockchain oracle. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar]
- ISO/IEC/IEEE International Standard. Systems and Software Engineering—Life Cycle Processes—Requirements Engineering; ISO/IEC/IEEE 29148:2011(E); ISO: Geneva, Switzerland, 2018; pp. 1–94. [Google Scholar]
- Björck, F.; Henkel, M.; Stirna, J.; Zdravkovic, J. Cyber resilience—Fundamentals for a definition. Adv. Intell. Syst. Comput. 2015, 353, 311–316. [Google Scholar]
- Lam, K.-Y.; Gollmann, D. Freshness assurance of authentication protocols. In Computer Security—ESORICS 92; Springer: Berlin/Heidelberg, Germany, 1992. [Google Scholar]
- Cao, Y.-Y.; Fu, C. An Efficient Implementation of RSA Digital Signature Algorithm. In Proceedings of the 2008 International Conference on Intelligent Computation Technology and Automation (ICICTA), Changsha, China, 20–22 October 2008; pp. 100–103. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inform. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Wu, T. The secure remote password protocol. In Network and Distributed System Security (NDSS) Symposium; The Internet Society: San Diego, CA, USA, 1998; pp. 97–111. [Google Scholar]
- Krawczyk, H. Cryptographic extraction and key derivation: The HKDF scheme. In Proceedings of the 30th Annual Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2010; pp. 631–648. [Google Scholar]
- Savari, M.; Montazerolzohour, M.; Thiam, Y.E. Comparison of ECC and RSA algorithm in multipurpose smart card application. In Proceedings of the 2012 International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec), Kuala Lumpur, Malaysia, 26–28 June 2012. [Google Scholar]
- Toradmalle, D.; Singh, R.; Shastri, H.; Naik, N.; Panchidi, V. Prominence of ECDSA over RSA digital signature algorithm. In Proceedings of the 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC)I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 30–31 August 2018; pp. 253–257. [Google Scholar]
- Boyko, V.; Mackenzie, P.; Patel, S. Provably secure password-authenticated key exchange using diffie-hellman. In International Conference on Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2000. [Google Scholar]
- Zhao, Z.; Dong, Z.; Wang, Y. Security analysis of a password-based authentication protocol proposed to IEEE 1363. Theor. Comput. Sci. 2006, 352, 280–287. [Google Scholar]
- Green, M. A Few Thoughts on Cryptographic Engineering. 2020. Available online: https://blog.cryptographyengineering.com/ (accessed on 12 August 2020).
- CISCO. The Internet of Things Reference Model. 2014. Available online: http://cdn.iotwf.com/resources/71/IoT_Reference_Model_White_Paper_June_4_2014.pdf (accessed on 11 September 2020).













| DF ID | Data Process | DF Label | DF Description | Trust Domain | Threat Entry/Exit |
|---|---|---|---|---|---|
| 1 | Database Access | VC2 | Data transmission (input) | TD2 & TD5 | Wi-fi Module |
| 2 | VC5a | Data processing (input) | TD5 | SQL Database | |
| 3 | VC5b | Data processing (output) | TD5 | SQL Database | |
| 4 | ESP 8266 Processor | VC1 | Data from A/D converter | TD1 | ESP 8266 Processor |
| 5 | VC4a | Local software update reception | TD4 | ESP 8266 Processor | |
| 6 | VC4b | Local software update probe | TD4 | ESP 8266 Processor & Local ESP8266 Software updates | |
| 7 | VC0a | Output to security module | TD4 & TD3 | ESP 8266 Processor & Security Module & Local ESP8266 Software updates | |
| 8 | VC0b | Input from security module | TD4 & TD3 | ESP 8266 Processor & Security Module | |
| 10 | VC3b | Input to Multos software update | TD3 | Security module & local Multos software update |
| DF ID | Trust Domain | DF Label | Threat Entry/Exit | STRIDE Count | Threat ID | Threat Event |
|---|---|---|---|---|---|---|
| 1 | TD2 & TD5 | VC2 | Wi-fi Module | S = 1 | 1 | Attempting 802.11 Shared Key Authentication with guessed, vendor default or cracked WEP keys |
| S = 2 | 2 | Application login theft | ||||
| T = 1 | 3 | 802.11 frame injection | ||||
| T = 2 | 4 | 802.11 data replay | ||||
| I = 1 | 5 | Krack WPA2 attack | ||||
| I = 2 | 6 | TLS logjam attack | ||||
| I = 3 | 7 | MITM in wireless communication | ||||
| D = 1 | 8 | Wi-fi jamming | ||||
| 2&3 | TD5 | VC5a &VC5b | SQL Database | S = 1 | 9 | Unauthorised access through replay attack(s) |
| S = 2 | 10 | Network Eavesdropping | ||||
| T = 1 | 11 | SQL Injection | ||||
| T = 2 | 12 | Unauthorised access | ||||
| I = 1 | 13 | Unauthorised access | ||||
| I = 2 | 14 | Network Eavesdropping | ||||
| I = 3 | 15 | Timing analysis | ||||
| I = 4 | 16 | Error analysis | ||||
| I = 5 | 17 | Malicious data mining | ||||
| D = 1 | 18 | D-DoS, DoS, E-DoS attack(s) | ||||
| E = 1 | 19 | SQL Injection | ||||
| E = 2 | 20 | Unauthorised access | ||||
| E = 3 | 21 | Network Eavesdropping |
| STRIDE Count | Threat ID | Threat Event | Impact | DREAD: 1 = Low, 5 = High | |||||
|---|---|---|---|---|---|---|---|---|---|
| D | R | E | A | D | Avg Score | ||||
| DFID = 1 | |||||||||
| S = 1 | 1 | Attempting 802.11 Shared Key Authentication with guessed, vendor default or cracked WEP keys | Unauthorised access and/or impersonating a legitimate account | 1 | 2 | 3 | 4 | 4 | 2.8 |
| S = 2 | 2 | Application login theft | Capturing user credentials | 1 | 3 | 3 | 4 | 5 | 3.2 |
| T = 1 | 3 | 802.11 frame Injection | Crafting packets | 1 | 3 | 2 | 4 | 3 | 2.6 |
| T = 2 | 4 | 802.11 data Replay | Capturing 802.11 data frames for later (modified) replay | 2 | 2 | 4 | 4 | 3 | 3 |
| I = 1 | 5 | Krack WPA2 attack | 3rd party eavesdrop confidential information transmitted | 4 | 1 | 5 | 5 | 5 | 4 |
| I = 2 | 6 | TLS logjam attack | 3rd party eavesdrop confidential information transmitted | 3 | 4 | 3 | 4 | 3 | 3.4 |
| I = 3 | 7 | MITM in wireless communication | Running traditional man-in-the-middle attack tools on an evil twin AP to intercept TCP sessions | 2 | 4 | 4 | 3 | 4 | 3.4 |
| D = 1 | 8 | Wi-fi jamming | An adversary interrupts communication (data flow) Transmission can be interrupted or blocked | 3 | 2 | 4 | 4 | 4 | 3.4 |
| DFID = 2&3 | |||||||||
| S = 1 | 9 | Unauthorized access through replay attack(s) | Falsification of data | 2 | 3 | 4 | 3 | 3 | 3 |
| S = 2 | 10 | Network Eavesdropping | Impersonating user accounts, stolen credentials | 1 | 2 | 3 | 3 | 3 | 2.4 |
| T = 1 | 11 | SQL Injection | Run arbitrary commands in the database, manipulate, erase data | 2 | 5 | 4 | 4 | 4 | 3.8 |
| T = 2 | 12 | Unauthorized access | Alteration of tables, modification of data | 2 | 3 | 4 | 3 | 4 | 3.2 |
| I = 1 | 13 | Unauthorized access | Stolen records | 1 | 3 | 4 | 4 | 5 | 3.4 |
| I = 2 | 14 | Network Eavesdropping | Unauthorized interception of information | 1 | 2 | 3 | 3 | 3 | 2.4 |
| I = 3 | 15 | Timing analysis | Recovering private entries from private columns | 1 | 2 | 3 | 3 | 3 | 2.4 |
| I = 4 | 16 | Error analysis | Exception conditionsTarget non-validated user inputWeak dynamic SQL queries | 1 | 4 | 3 | 3 | 3 | 2.8 |
| I = 5 | 17 | Malicious data mining | Information gatheringSQL injection | 1 | 2 | 2 | 3 | 2 | 2 |
| D = 1 | 18 | D-DoS, DoS, E-DoS attack(s) | Limit or prohibit access to legitimate usersExecuting non-optimized codeBad resource allocation and management policy | 3 | 4 | 1 | 3 | 4 | 3 |
| E = 1 | 19 | SQL Injection | Run system commands | 2 | 5 | 4 | 4 | 4 | 3.8 |
| E = 2 | 20 | Unauthorized access | Unauthorized command execution, table creation, deletion | 1 | 3 | 4 | 4 | 5 | 3.4 |
| E = 3 | 21 | Network Eavesdropping | Execute arbitrary commandsDatabase alteration, deletion | 2 | 4 | 3 | 3 | 4 | 3.2 |
| STRIDE Count | Threat ID | Threat Event | Impact | DREAD | Recommended Action | Resolution ID |
|---|---|---|---|---|---|---|
| DFID = 1 | ||||||
| S = 1 | 1 | Attempting 802.11 Shared Key Authentication with guessed, vendor default or cracked WEP keys | Unauthorised access and or impersonating a legitimate account | 2.8 | Disable WEP/WPA. Provide 802.11X and investigate options | 5, 13 |
| S = 2 | 2 | Application login theft | Capturing user credentials | 3.2 | Strong encryption, strong passwords, adequate password policy | 5, 2, 16 |
| T = 1 | 3 | 802.11 frame Injection | Crafting packets | 2.6 | Consider a Robust Secure Network implementation | 5, 13, 18 |
| T = 2 | 4 | 802.11 data Replay | Capturing 802.11 data frames for later (modified) replay | 3 | Use of Kerberos for authentication within IEEE 802.1X | 5, 13, 18 |
| I = 1 | 5 | Krack WPA2 attack | 3rd party eavesdrop confidential information transmitted | 4 | Use available counter-measure patches | 5, 3, 18 |
| I = 2 | 6 | TLS logjam attack | 3rd party eavesdrop confidential information transmitted | 3.4 | Disable support for export- grade cipher suites, Use ECDHE instead of DHE, Reduce TLS handshake timeout | 5, 3, 10 |
| I = 3 | 7 | Man-In-The-Middle in wireless communication | Running traditional man-in-the-middle attack tools on an evil twin Access Point (AP) to intercept TCP sessions | 3.4 | TLS encryption, RADIUS authentication server, consider mTesla protocol in the given architecture | 5, 3 |
| D = 1 | 8 | Wi-fi jamming | An adversary interrupts communication (data flow) Transmission can be interrupted or blocked | 3.4 | Explore anti-jamming features, difficult to block | 13 |
| DFID = 2&3 | ||||||
| S = 1 | 9 | Unauthorised access through replay attack(s) | Falsification of data | 3 | Strong authentication, identity management, key freshness. Use of Windows authentication | 5, 2, 1, 15 |
| S = 2 | 10 | Network Eavesdropping | Impersonating user accounts, stolen credentials | 2.4 | Use authentication based on key exchange. Discovery scanners. Use an access control list. Reject packets originating from outside your local network that claim to originate from within | 5 |
| T = 1 | 11 | SQL Injection | Run arbitrary commands in the database, manipulate, erase data | 3.8 | Input sanitisation | 13, 8, 17 |
| T = 2 | 12 | Unauthorised access | Alteration of tables, modification of data | 3.2 | Strong hashing for tampering detection purposes, timestamps, salting. Use of Windows authentication | 1, 6, 17 |
| I = 1 | 13 | Unauthorized access | Stolen records | 3.4 | Encrypted database systems including transactions. Use of Windows authentication | 5, 1, 3, 16 |
| I = 2 | 14 | Network Eavesdropping | Unauthorized interception of information | 2.4 | SSL, IPSEC | 5, 3 |
| I = 3 | 15 | Timing analysis | Recovering private entries from private columns | 2.4 | 5, 3 | |
| I = 4 | 16 | Error analysis | Exception conditions Target non-validated user input Weak dynamic SQL queries | 2.8 | Effective filtering. Trusted connections to the database. Exception handling | 5, 3 |
| I = 5 | 17 | Malicious data mining | Information gathering SQL injection | 2 | 5, 3 | |
| D = 1 | 18 | D-DoS, DoS, E-DoS attack(s) | Limit or prohibit access to legitimate users Executing non-optimized code Bad resource allocation and management policy | 3 | No effective countermeasure at the database level | 13 |
| E = 1 | 19 | SQL Injection | Run system commands | 3.8 | Restricted accounts | 14, 13 |
| E = 2 | 20 | Unauthorized access | Unauthorized command execution, table creation, deletion | 3.4 | 9, 13 | |
| E = 3 | 21 | Network Eavesdropping | Execute arbitrary commands Database alteration, deletion | 3.2 | Use an access control list | 5, 3 |
| ID | Resolution |
|---|---|
| 1 | Windows authentication used on SQL DB (Regus). |
| 2 | The broker and clients authenticate their secured IDs. |
| 3 | In Daedalus, confidentiality was not a major concern as it related to meter reading. |
| 4 | Disable Over the Air firmware updates |
| 5 | End-to-end cryptography (signatures) deployed |
| 6 | Salting not implemented (out of scope) |
| 7 | Clock security has not been dealt with |
| 8 | Sanitisation to be considered (out of scope) |
| 9 | Standard administrative privileges (ACL) set |
| 10 | Not applicable in the present version |
| 11 | Considered as a low probability threat based on complexity and cost implications |
| 12 | The ‘embedded’ systems approach does not permit external access to memory |
| 13 | Not mitigated in this version |
| 14 | Account restriction to be considered (out of scope) |
| 15 | Integrity of public key to be considered (out of scope) |
| 16 | End-to-end Encryption to be considered (out of scope) |
| 17 | Means to independently validate data assets considered, possibly blockchain (out of scope) |
| 18 | Proposed solution. Part of the end-to-end key management in Section 4 |
| Security Feature | Example Algorithms/Protocols | Remarks |
|---|---|---|
| Asymmetric (public) Key Encryption | RSA | Allow the simple generation of key pairs, encryption & decryption operations, and provide secure on chip storage of private keys |
| ECC | ||
| Symmetric Encryption | AES | Allow the simple generation or input of secret keys, encryption & decryption operations, and provide secure on chip storage for secret keys |
| DES | ||
| Cryptographic Hash | SHA/1/2/3 | Allow simple generation of hash digests from data |
| Keyed Cryptographic Hash | HMAC-SHA1/2/3 | Allow simple generation of HMAC digests from data and a secret key. Provide secure storage for secret keys |
| Asymmetric Key Signature | RSA-SSA | Allow the simple generation of key pairs, signing & verification operations, and provide secure on chip storage of private keys |
| ECDSA | ||
| DSA | ||
| Key Exchange | PAKE | Built in PAKE protocol for bootstrapping/on-boarding using unique ID & secret for each secure chip. Allow simple use of DH protocol, securely store session keys. |
| DH/ECDH | ||
| Certification | CA root certificates | Have common CA root certificates built into the system. Allow simple verification of certificates signed by different CA’s |
| Command APDU | ||
|---|---|---|
| Field Name | Length (Bytes) | Description |
| CLA | 1 | Instruction class - indicates the type of command, e.g., interindustry or proprietary |
| INS | 1 | Instruction code - indicates the specific command, e.g., “write data” |
| P1 | 1 | Instruction parameter for the command |
| P2 | 1 | Instruction parameter for the command |
| Lc | 0,1 or 3 | Encodes the number of bytes of command data as follows: |
| 0 bytes denotes 0 | ||
| 1 byte with a value from 1 to 255 denotes the same value | ||
| 3 bytes, the first of which must be 0, denote in the range 1 to 65 535 (all three bytes may not be zero) | ||
| Data | 0 to 65535 | Command data |
| Le | 0,1, 2 or 3 | Encodes the maximum number of response bytes expected. |
| 0 bytes denotes 0 | ||
| 1 byte in the range 1 to 255 denotes that value, or 0 denotes 256 | ||
| 2 bytes (if 3 byte Lc was present in the command) in the range 1 to 65 535 denotes that value, or two zero bytes denotes 65 536 | ||
| 3 bytes (if Lc was not present in the command), the first of which must be 0, denote the same way as two-byte Le | ||
| Response APDU | ||
| Data | 0 to 65536 | Response data |
| SW1-SW2 | 2 | Command processing status, e.g., 90 00 (hexadecimal) indicates success |
| Command | Description | Input | Output |
|---|---|---|---|
| HASH | Creates a hash digest of data using the desired algorithm | Desired hash algorithm & Data to hash | Hash digest |
| RSASSA-GENKEYPAIR | Generates a key pair for use with the RSA-SSA algorithm | Required key size & public exponent | Index to key pair in secure storage |
| RSASSA-GETPUBKEY | Returns the public key information from an RSA-SSA key pair | Key pair index | Public key data |
| RSASSA-SIGN | Signs data using the private key from an RSA-SSA key pair | Key pair index, desired hash algorithm, desired encoding scheme & data to sign | Signature |
| RSASSA-VERIFY | Verifies an RSA-SSA signature | Hash algorithm used, encoding scheme used, Public key information of signer, data signed & signature | True or false indicating if signature is valid |
| ECDSA-GENKEYPAIR | Generates a key pair for use with the ECDSA algorithm | Desired curve | Index to key pair in secure storage |
| ECDSA-GETPUBKEY | Returns the public key information from an ECDSA key pair | Key pair index | Public key data |
| ECDSA-SIGN | Signs data using the private key from an ECDSA key pair | Key pair index, desired hash algorithm & data to sign | Signature |
| ECDSA-VERIFY | Verifies an ECDSA signature | Curve used, hash algorithm used, public key information of signer, data signed & signature | True or false indicating if signature is valid |
| BSPEKE-INIT | Performs initial steps of the B-SPEKE protocol | None | ID & calculated client data (A) |
| BSPEKE-CALC | Calculates the shared secret | Calculated server data (B) | Client secret verification message (M1) |
| BSPEKE-VERIFY | Verifies the shared secret is correct & derives the secret key from the shared secret | Server secret verification message (M2), desired key length & desired key derivation function | True or false indicating if M2 is valid |
| BSPEKE-GETKEY | Returns any stored public key signed with a HMAC digest using the generated secret key. | Key pair index, desired HMAC algorithm | Public key data & HMAC digest |
| Commands | Input-Output Parameters | ||
|---|---|---|---|
| 1. | Generate key pair | a. | Input desired parameters such as key size. |
| b. | The output is an index to the key pair. | ||
| 2. | Retrieve public key | a. | Input is an index to a key pair. |
| b. | The output is the public key relating to the index. | ||
| 3. | Sign data | a. | Input is an index to a key pair and the data to be signed as well as any encoding schemes. |
| b. | The output is the signature. | ||
| 4. | Verify signature | a. | Input would be the parameters from the originator such as their public key, the signature and the data being signed. |
| b. | The output would be true or false depending on if it is valid. |
| Algorithm | Remarks |
|---|---|
| Secure Remote Password (SRP) [65] | A patent free augmented PAKE algorithm made at a time when algorithms such as SPEKE (and variants, below) were under patent. SRP requires a large exponentiation, the Multos platform does not support the use of an exponent of the size required. |
| Simple Password Exponential Key Exchange (SPEKE) [24]. | A Simpler algorithm to SRP. Uses smaller exponentiations. SPEKE is a balanced PAKE algorithm, so the secret key must be stored on the server. The server being compromised would allow an attacker to masquerade as a client. |
| B-SPEKE [23,25] | An augmented version of SPEKE. The server stores a verifier, Loss of the verifier would not allow an attacker to masquerade as a client, unless the discrete logarithm problem was solved. |
| W-SPEKE IEEE P1363 [36] | Another augmented version of SPEKE. Uses a larger exponentiation like SRP. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramalingam, S.; Gan, H.; Epiphaniou, G.; Mistretta, E. A Holistic Systems Security Approach Featuring Thin Secure Elements for Resilient IoT Deployments. Sensors 2020, 20, 5252. https://doi.org/10.3390/s20185252
Ramalingam S, Gan H, Epiphaniou G, Mistretta E. A Holistic Systems Security Approach Featuring Thin Secure Elements for Resilient IoT Deployments. Sensors. 2020; 20(18):5252. https://doi.org/10.3390/s20185252
Chicago/Turabian StyleRamalingam, Soodamani, Hock Gan, Gregory Epiphaniou, and Emilio Mistretta. 2020. "A Holistic Systems Security Approach Featuring Thin Secure Elements for Resilient IoT Deployments" Sensors 20, no. 18: 5252. https://doi.org/10.3390/s20185252
APA StyleRamalingam, S., Gan, H., Epiphaniou, G., & Mistretta, E. (2020). A Holistic Systems Security Approach Featuring Thin Secure Elements for Resilient IoT Deployments. Sensors, 20(18), 5252. https://doi.org/10.3390/s20185252






