A Secure IoT-Based Authentication System in Cloud Computing Environment
Abstract
:1. Introduction
2. Related Works
2.1. Review of Zhou et al.’s Scheme
2.1.1. Registration Phase
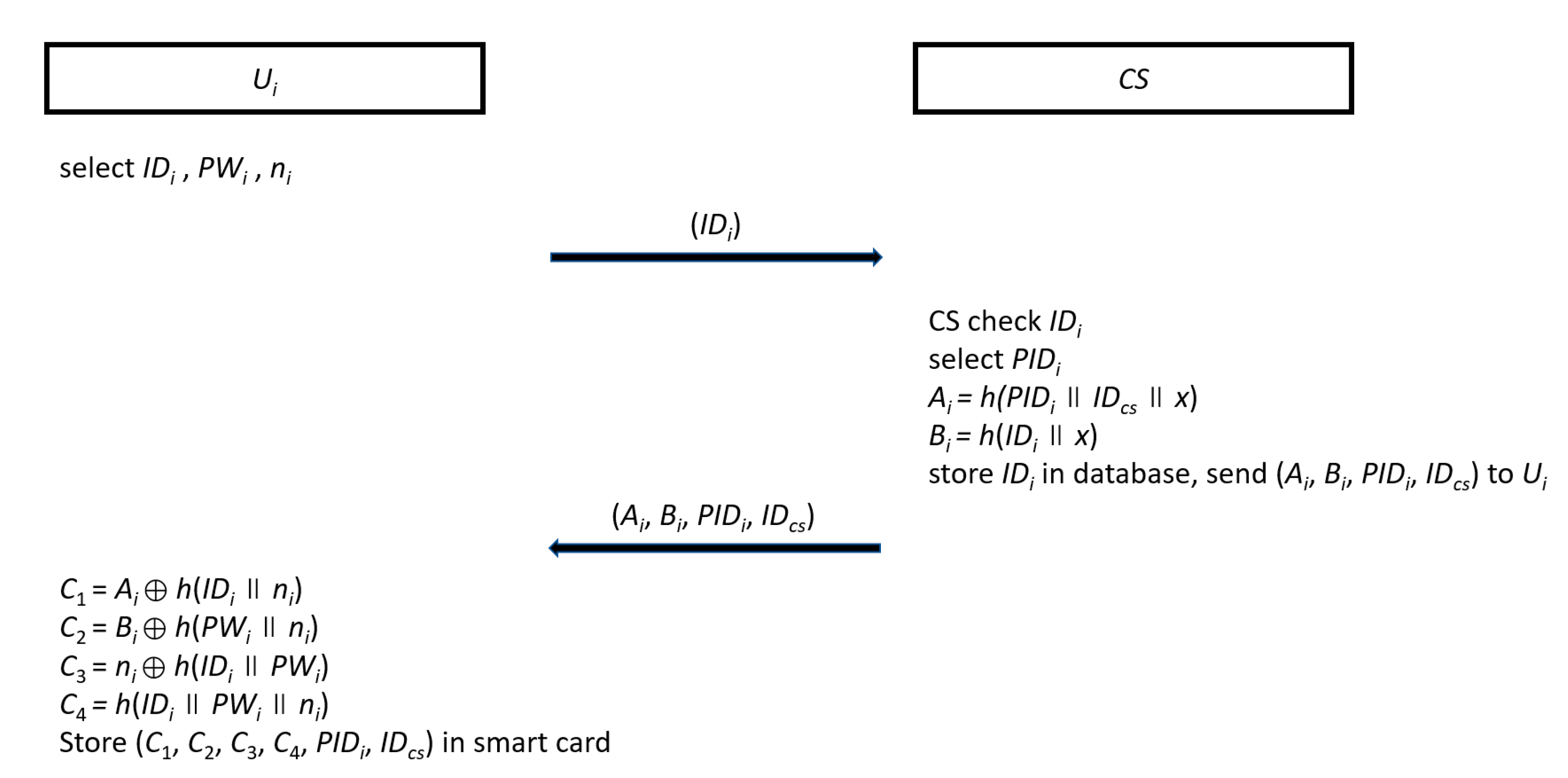
User Registration
Cloud Server Registration
2.1.2. Authentication Phase
2.2. Analysis of Zhou et al.’s Scheme
2.2.1. Zhou et al.’s Scheme Cannot Achieve Mutual Authentication
2.2.2. Zhou et al.’s Scheme Cannot Guarantee Anonymity in Authentication Phase
3. Proposed Scheme
3.1. Notations
3.2. Registration Phase
3.2.1. User Registration
3.2.2. Cloud Server Registration
3.3. Authentication Phase
3.4. Password Change Phase
4. Security Analysis
4.1. Mutual Authentication
4.1.1. CS Verifies the Identity of Ui through Checking D3? = h(IDi‖PIDi‖ru)
4.1.2. CS Verifies the Identity of Sj through Checking D7? = h(SIDj‖PSIDj‖PSIDj’‖rs‖D6)
4.1.3. Sj Verifies the Identity of CS through Checking D10? = h(SKs‖D8‖D9‖Bj)
4.1.4. Ui Verifies the Identity of CS through Checking D14? = h(SKu‖D12‖D13‖Bi)
4.2. Session Key for All Entities
4.3. User Anonymity
4.4. Resistance to Off-Line Guessing Attack
4.5. Resistance to Insider Attack
4.6. Resistance to Stolen Smart Card Attack
4.7. Resistance to De-Synchronization Attack
4.8. Resistance to Forgery Attack
4.9. Resistance to User Tracking Attack
5. Performance Evaluation
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Jing, Q.; Vasilakos, A.V.; Wan, J. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2507. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Qi, M.; Chen, J.; Chen, Y. A secure authentication with key agreement scheme using ECC for satellite communication systems. Int. J. Satell. Commun. Netw. 2019, 37, 234–244. [Google Scholar] [CrossRef]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brünig, M.; Carle, G. DTLS based security and two-way authentication for the Internet of Things. Ad Hoc Netw. 2013, 11, 2710–2723. [Google Scholar] [CrossRef]
- Pranata, I.; Athauda, R.; Skinner, G. Securing and governing access in ad-hoc networks of Internet of Things. In Proceedings of the IASTED International Conference on Engineering and Applied Science, Colombo, Sri Lanka, 27–29 December 2012; pp. 27–29. [Google Scholar]
- Durairaj, M.; Muthuramalingam, K. A new authentication scheme with elliptical curve cryptography for Internet of Things (IoT) environments. Int. J. Eng. Technol. 2018, 7, 119. [Google Scholar] [CrossRef] [Green Version]
- Hong, N. A security framework for the Internet of Things based on public key infrastructure. Adv. Mater. Res. 2013, 671–674, 3223–3226. [Google Scholar] [CrossRef]
- Hao, P.; Wang, X.; Shen, W. A collaborative PHY-aided technique for end-to-end IoT device authentication. IEEE Access 2018, 6, 42279–42293. [Google Scholar] [CrossRef]
- Mahmood, K.; Chaudhry, S.A.; Naqvi, H.; Shon, T.; Ahmad, H.F. A lightweight message authentication scheme for smart grid communications in power sector. Comput. Electr. Eng. 2016, 52, 114–124. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Odelu, V.; Kumar, N.; Kumari, S.; Khan, M.K.; Vasilakos, A.V. An efficient ECC-based provably secure three-factor user authentication and key agreement protocol for wireless healthcare sensor networks. Comput. Electr. Eng. 2018, 69, 534–554. [Google Scholar] [CrossRef]
- Chung, Y.; Choi, S.; Lee, Y.; Park, N.; Won, D. An enhanced lightweight anonymous authentication scheme for a scalable localization roaming service in wireless sensor networks. Sensors 2016, 16, 1653. [Google Scholar] [CrossRef] [Green Version]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Jan, M.A.; Khan, F.; Alam, M.; Usman, M. A payload-based mutual authentication scheme for Internet of Things. Future Gener. Comput. Syst. 2019, 92, 1028–1039. [Google Scholar] [CrossRef]
- Sun, X.; Men, S.; Zhao, C.; Zhou, Z. A security authentication scheme in machine-to-machine home network service. Secur. Commun. Netw. 2015, 8, 2678–2686. [Google Scholar] [CrossRef]
- Lyu, C.; Gu, D.; Zeng, Y.; Mohapatra, P. PBA: Prediction-based authentication for vehicle-to-vehicle communications. IEEE Trans. Dependable Secur. Comput. 2016, 13, 71–83. [Google Scholar] [CrossRef]
- Gope, P.; Lee, J.; Quek, T.Q.S. Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Xu, H.; Ding, J.; Li, P.; Zhu, F.; Wang, R. A lightweight RFID mutual authentication protocol based on physical unclonable function. Sensors 2018, 18, 760. [Google Scholar] [CrossRef] [Green Version]
- Wazid, M.; Das, A.K.; K, V.B.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Jangirala, S.; Das, A.K.; Vasilakos, A.V. Designing secure lightweight blockchain-enabled RFID-based authentication protocol for supply chains in 5G mobile edge computing environment. IEEE Trans. Ind. Inform. 2020, 16, 7081–7093. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and Analysis of Secure Lightweight Remote User Authentication and Key Agreement Scheme in Internet of Drones Deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Katz, J.; MacKenzie, P.; Taban, G.; Gligor, V. Two-server password-only authenticated key exchange. J. Comput. Syst. Sci. 2012, 78, 651–669. [Google Scholar] [CrossRef] [Green Version]
- Xiang, T.; Wong, K.; Liao, X. Cryptanalysis of a password authentication scheme over insecure networks. J. Comput. Syst. Sci. 2008, 74, 657–661. [Google Scholar] [CrossRef] [Green Version]
- Sun, H.-M.; Yeh, H.-T. Password-based authentication and key distribution protocols with perfect forward secrecy. J. Comput. Syst. Sci. 2006, 72, 1002–1011. [Google Scholar] [CrossRef]
- Chien, H.-Y.; Jan, J.-K.; Tseng, Y.-M. An efficient and practical solution to remote authentication: Smart card. Comput. Secur. 2002, 21, 372–375. [Google Scholar] [CrossRef]
- Xu, J.; Zhu, W.-T.; Feng, D.-G. An improved smart card based password authentication scheme with provable security. Comput. Stand. Interfaces 2009, 31, 723–728. [Google Scholar] [CrossRef]
- Kumar, M.; Gupta, K.; Kumari, S. An improved efficient remote password authentication scheme with smart card over insecure networks. Int. J. Netw. Secur. 2011, 13, 167–177. [Google Scholar]
- Challa, S.; Das, A.K.; Gope, P.; Kumar, N.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber–physical systems. Future Gener. Comput. Syst. 2020, 108, 1267–1286. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Huang, X.; Choo, K.-K.R.; Vasilakos, A.V.; BSeIn: A blockchain-based secure mutual authentication with fine-grained access control system for industry 4.0. J. Netw. Comput. Appl. 2018, 116, 42–52. [CrossRef]
- Liao, Y.-P.; Wang, S.-S. A secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 2009, 31, 24–29. [Google Scholar] [CrossRef]
- Hsiang, H.-C.; Shih, W.-K. Improvement of the secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 2009, 31, 1118–1123. [Google Scholar] [CrossRef]
- Sood, S.K.; Sarje, A.K.; Singh, K. A secure dynamic identity based authentication protocol for multi-server architecture. J. Netw. Comput. Appl. 2011, 34, 609–618. [Google Scholar] [CrossRef]
- Lee, C.-C.; Lin, T.-H.; Chang, R.-X. A secure dynamic ID based remote user authentication scheme for multi-server environment using smart cards. Expert Syst. Appl. 2011, 38, 13863–13870. [Google Scholar] [CrossRef]
- Xue, K.; Hong, P.; Ma, C. A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. J. Comput. Syst. Sci. 2014, 80, 195–206. [Google Scholar] [CrossRef]
- Amin, R.; Kumar, N.; Biswas, G.P.; Iqbal, R.; Chang, V. A light weight authentication protocol for IoT-enabled devices in distributed cloud computing environment. Future Gener. Comput. Syst. 2018, 78, 1005–1019. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese Remainder Theorem Based Conditional Privacy-preserving Authentication Scheme in Vehicular Ad-hoc Networks. IEEE Trans. Dependable Secur. Comput. 2019, 1. [Google Scholar] [CrossRef] [Green Version]
- Cui, J.; Zhang, J.; Zhong, H.; Xu, Y. SPACF: A Secure Privacy-Preserving Authentication Scheme for VANET with Cuckoo Filter. IEEE Trans. Veh. Technol. 2017, 66, 10283–10295. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deboarh, K.J. EAAP: Efficient Anonymous Authentication with Conditional Privacy-Preserving Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Kong, W.; Shen, J.; Vijayakumar, P.; Cho, Y.; Chang, V. A practical group blind signature scheme for privacy protection in smart grid. J. Parallel Distrib. Comput. 2020, 136, 29–39. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.-H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Li, C.-T.; Weng, C.-Y.; Lee, C.-C.; Wang, C.-C. Secure user authentication and user anonymity scheme based on quadratic residues for the integrated EPRIS. Procedia Comput. Sci. 2015, 52, 21–28. [Google Scholar] [CrossRef] [Green Version]
- Yeh, K.-H.; Lo, N.-W.; Kuo, R.-Z.; Su, C.; Chen, H.-Y. Formal analysis on RFID authentication protocols against de-synchronization attack. J. Internet Technol. 2017, 18, 765–773. [Google Scholar]
- Maitra, T.; Islam, S.H.; Amin, R.; Giri, D.; Khan, M.; Kumar, K.N. An enhanced multi-server authentication protocol using password and smart-card: Cryptanalysis and design. Secur. Commun. Netw. 2016, 9, 4615–4638. [Google Scholar] [CrossRef]




| Property | R1 | R2 | R3 | R4 | R5 | R6 | R7 | R8 | R9 |
|---|---|---|---|---|---|---|---|---|---|
| Amin et al.’s scheme [36] | O | O | O | X | O | O | O | O | X |
| Maitra et al.’s scheme [45] | O | X | O | X | O | O | O | O | X |
| Zhou et al.’s [42] | X | O | X | O | O | O | O | O | O |
| Ours | O | O | O | O | O | O | O | O | O |
| Entities | Registration Phase | Login Phase | Authentication Phase | Password Change Phase | Total Operations of Login and Authentication | |
|---|---|---|---|---|---|---|
| Amin et al.’s scheme [36] | Ui | 2 Th | 6 Th | 3 Th | 7 Th | 23 Th |
| Sj | 0 Th | 0 Th | 4 Th | 0 Th | ||
| CS | 4 Th | 0 Th | 10 Th | 0 Th | ||
| Maitra et al.’s scheme [45] | Ui | 3 Th | 6 Th | 4 Th | 9 Th | 19 Th + 6 Ts |
| Sj | 0 Th | 0 Th + 1 Ts | 4 Th + 2 Ts | 0 Th | ||
| CS | 3 Th + 1 Ts | 0 Th | 5 Th + 3 Ts | 2 Th + 2 Ts | ||
| Zhou et al.’s [42] | Ui | 3 Th | 0 Th | 10 Th | 11 Th | 36 Th |
| Sj | 0 Th | 0 Th | 7 Th | 0 Th | ||
| CS | 4 Th | 0 Th | 19 Th | 8 Th | ||
| Ours | Ui | 4 Th | 0 Th | 12 Th | 6 Th | 39 Th |
| Sj | 0 Th | 0 Th | 8 Th | 0 Th | ||
| CS | 4 Th | 0 Th | 19 Th | 0 Th |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, H.-L.; Chang, C.-C.; Zheng, Y.-Z.; Chen, L.-S.; Chen, C.-C. A Secure IoT-Based Authentication System in Cloud Computing Environment. Sensors 2020, 20, 5604. https://doi.org/10.3390/s20195604
Wu H-L, Chang C-C, Zheng Y-Z, Chen L-S, Chen C-C. A Secure IoT-Based Authentication System in Cloud Computing Environment. Sensors. 2020; 20(19):5604. https://doi.org/10.3390/s20195604
Chicago/Turabian StyleWu, Hsiao-Ling, Chin-Chen Chang, Yao-Zhu Zheng, Long-Sheng Chen, and Chih-Cheng Chen. 2020. "A Secure IoT-Based Authentication System in Cloud Computing Environment" Sensors 20, no. 19: 5604. https://doi.org/10.3390/s20195604
APA StyleWu, H.-L., Chang, C.-C., Zheng, Y.-Z., Chen, L.-S., & Chen, C.-C. (2020). A Secure IoT-Based Authentication System in Cloud Computing Environment. Sensors, 20(19), 5604. https://doi.org/10.3390/s20195604








