An Information-Centric Semantic Data Collection Tree for Wireless Sensor Networks
Abstract
1. Introduction
2. Related Work
3. The Proposed Semantic Data Collection Tree
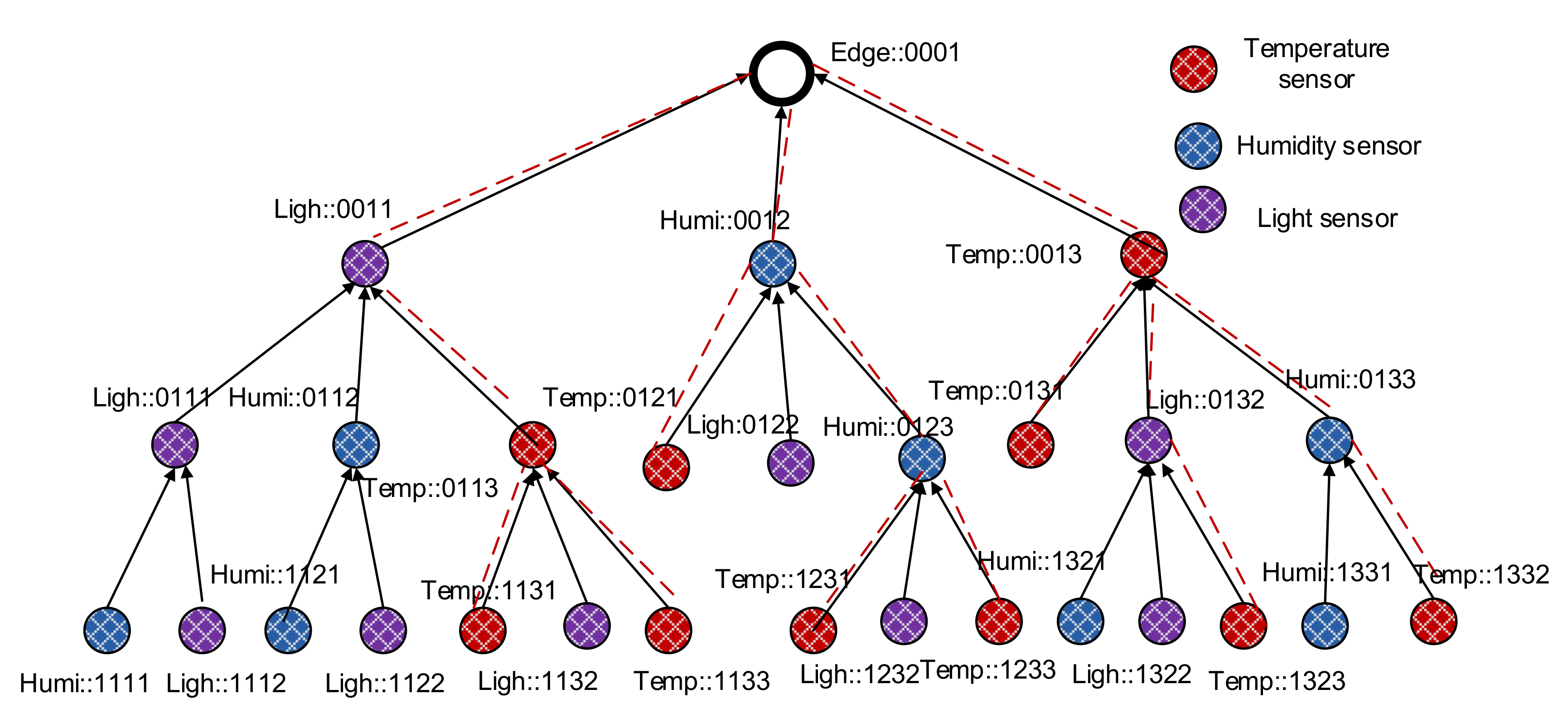
3.1. Semantic Naming Scheme
3.2. ID Construction
3.3. Packet Format and Traffic Patterns
3.4. Packet Forwarding for Different Types of Traffic Patterns
3.4.1. MP2P
3.4.2. P2P or Unicast Forwarding
3.4.3. P2MP
4. Performance Evaluation
4.1. Bootstrapping
4.2. P2MP Traffic
4.3. MP2P Traffic
4.4. P2P Traffic
5. Discussion and Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Park, Y.; Dinh, N.-T.; Kim, Y. A network monitoring system in 6LoWPAN networks. In Proceedings of the 2012 Fourth International Conference on Communications and Electronics (ICCE), Hue, Vietnam, 1–3 August 2012; pp. 69–73. [Google Scholar] [CrossRef]
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.W.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R.K. RPL: IPv6 Routing Protocol for Low Power and Lossy Networks; RFC6550; IETF Secretariat: Fremont, CA, USA, 2012. [Google Scholar]
- Dinh, N.; Kim, Y. Potential of information-centric wireless sensor and actor networking. In Proceedings of the 2013 International Conference on Computing, Management and Telecommunications (ComManTel), Ho Chi Minh City, Vietnam, 21–24 January 2013; pp. 163–168. [Google Scholar] [CrossRef]
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking Named Content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; Association for Computing Machinery (ACM): New York, NY, USA, 2009; pp. 1–12. [Google Scholar] [CrossRef]
- Dinh, N.T.; Dao, N.N.; Kim, Y. Sensing Content Correlation-Aware In-Network Caching Scheme at the Edge for Internet of Things. In Proceedings of the 6th ACM Conference on Information-Centric Networking, Macao, China, 24–26 September 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 161–162. [Google Scholar] [CrossRef]
- Vasseur, J.P.; Kim, M.; Pister, K.; Dejean, N.; Barthel, D. Routing Metrics Used for Path Calculation in Low-Power and Lossy Networks; RFC6551; IETF Secretariat: Fremont, CA, USA, 2012. [Google Scholar]
- Hui, J.; Kelsey, R. Multicast Protocol for Low-Power and Lossy Networks (MPL); RFC7731; IETF Secretariat: Fremont, CA, USA, 2016. [Google Scholar]
- Goyal, M.; Baccelli, E.; Philipp, M.; Brandt, A.; Martocci, J. Reactive Discovery of Point-to-Point Routes in Low Power and Lossy Networks; RFC6997; IETF Secretariat: Fremont, CA, USA, 2013.
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named Data Networking. SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Mars, D.; Gammar, S.M.; Lahmadi, A.; Saidane, L.A. Using Information Centric Networking in Internet of Things: A Survey. Wirel. Pers. Commun. 2019, 105, 87–103. [Google Scholar] [CrossRef]
- Djama, A.; Djamaa, B.; Senouci, M.R. Information-Centric Networking solutions for the Internet of Things: A systematic mapping review. Comput. Commun. 2020, 159, 37–59. [Google Scholar] [CrossRef]
- Seyfollahi, A.; Ghaffari, A. A lightweight load balancing and route minimizing solution for routing protocol for low-power and lossy networks. Comput. Netw. 2020, 179, 107368. [Google Scholar] [CrossRef]
- Vera-Amaro, R.; Rivero-Ángeles, M.E.; Luviano-Juárez, A. Data Collection Schemes for Animal Monitoring Using WSNs-Assisted by UAVs: WSNs-Oriented or UAV-Oriented. Sensors 2020, 20, 262. [Google Scholar] [CrossRef] [PubMed]
- Xu, Y.; Sun, G.; Geng, T.; He, J. Low-Energy Data Collection in Wireless Sensor Networks Based on Matrix Completion. Sensors 2019, 19, 945. [Google Scholar] [CrossRef]
- Yang, G.; Peng, Z.; He, X. Data Collection Based on Opportunistic Node Connections in Wireless Sensor Networks. Sensors 2018, 18, 3697. [Google Scholar] [CrossRef]
- Gnawali, O.; Fonseca, R.; Jamieson, K.; Kazandjieva, M.; Moss, D.; Levis, P. CTP: An Efficient, Robust, and Reliable Collection Tree Protocol for Wireless Sensor Networks. ACM Trans. Sens. Netw. 2013, 10. [Google Scholar] [CrossRef]
- Ko, J.; Dawson-Haggerty, S.; Gnawali, O.; Culler, D.; Terzis, A. Evaluating the Performance of RPL and 6LoWPAN in TinyOS. In Proceedings of the IPSN 2011, Chicago, IL, USA, 12–14 April 2011; Association for Computing Machinery (ACM): New York, NY, USA, 2011; pp. 1–6. [Google Scholar] [CrossRef]
- Long, N.T.; De Caro, N.; Colitti, W.; Touhafi, A.; Steenhaut, K. Comparative performance study of RPL in Wireless Sensor Networks. In Proceedings of the 2012 19th IEEE Symposium on Communications and Vehicular Technology in the Benelux (SCVT), Eindhoven, The Netherlands, 16 November 2012; pp. 1–6. [Google Scholar]
- Rehan, W.; Fischer, S.; Rehan, M. A Critical Review of Surveys Emphasizing on Routing in Wireless Sensor Networks—An Anatomization under General Survey Design Framework. Sensors 2017, 17, 1713. [Google Scholar] [CrossRef] [PubMed]
- Ogundile, O.O.; Alfa, A.S. A Survey on an Energy-Efficient and Energy-Balanced Routing Protocol for Wireless Sensor Networks. Sensors 2017, 17, 1084. [Google Scholar] [CrossRef]
- Watteyne, T.; Molinaro, A.; Richichi, M.G.; Dohler, M. From MANET To IETF ROLL Standardization: A Paradigm Shift in WSN Routing Protocols. IEEE Commun. Surv. Tutor. 2011, 13, 688–707. [Google Scholar] [CrossRef]
- Arshad, S.; Azam, M.A.; Rehmani, M.H.; Loo, J. Recent Advances in Information-Centric Networking-Based Internet of Things (ICN-IoT). IEEE Internet Things J. 2019, 6, 2128–2158. [Google Scholar] [CrossRef]
- Aboodi, A.; Wan, T.; Sodhy, G. Survey on the Incorporation of NDN/CCN in IoT. IEEE Access 2019, 7, 71827–71858. [Google Scholar] [CrossRef]
- Din, I.U.; Asmat, H.; Guizani, M. A review of information centric network-based internet of things: Communication architectures, design issues, and research opportunities. Multimed. Tools Appl. 2019, 78, 30241–30256. [Google Scholar] [CrossRef]
- Nour, B.; Sharif, K.; Li, F.; Biswas, S.; Moungla, H.; Guizani, M.; Wang, Y. A survey of Internet of Things communication using ICN: A use case perspective. Comput. Commun. 2019, 142–143, 95–123. [Google Scholar] [CrossRef]
- Gündogan, C.; Kietzmann, P.; Schmidt, T.C.; Lenders, M.; Petersen, H.; Wählisch, M.; Frey, M.; Shzu-Juraschek, F. Information-Centric Networking for the Industrial IoT. In Proceedings of the 4th ACM Conference on Information-Centric Networking, Berlin, Germany, 26–28 September 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 214–215. [Google Scholar] [CrossRef]
- Waltari, O.; Kangasharju, J. Content-Centric Networking in the Internet of Things. In Proceedings of the 2016 13th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 73–78. [Google Scholar]
- Ali, Z.; Shah, M.A.; Almogren, A.; Ud Din, I.; Maple, C.; Khattak, H.A. Named Data Networking for Efficient IoT-based Disaster Management in a Smart Campus. Sustainability 2020, 12, 930. [Google Scholar] [CrossRef]
- Dinh, T.; Kim, Y. Information centric sensor-cloud integration: An efficient model to improve wireless sensor networks’ lifetime. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Dinh, T.; Kim, Y. A Novel Location-Centric IoT-Cloud Based On-Street Car Parking Violation Management System in Smart Cities. Sensors 2016, 16, 930. [Google Scholar] [CrossRef]
- Dinh, N.; Kim, Y. Information-centric dissemination protocol for safety information in vehicular ad-hoc networks. Wirel. Netw. 2017, 23, 1359–1371. [Google Scholar] [CrossRef]
- Lachowski, R.; Pellenz, M.E.; Jamhour, E.; Penna, M.C.; Brante, G.; Moritz, G.; Souza, R.D. ICENET: An Information Centric Protocol for Big Data Wireless Sensor Networks. Sensors 2019, 19, 930. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Quevedo, J.; Corujo, D.; Molinaro, A.; Iera, A.; Aguiar, R.L.; Vasilakos, A.V. Information-centric networking for the internet of things: Challenges and opportunities. IEEE Netw. 2016, 30, 92–100. [Google Scholar] [CrossRef]
- Nour, B.; Sharif, K.; Li, F.; Wang, Y. Security and Privacy Challenges in Information-Centric Wireless Internet of Things Networks. IEEE Secur. Priv. 2020, 18, 35–45. [Google Scholar] [CrossRef]
- Kim, K.S.; Sahni, S. Efficient Construction of Pipelined Multibit-Trie Router-Tables. IEEE Trans. Comput. 2007, 56, 32–43. [Google Scholar] [CrossRef]
- Ahlgren, B.; Lindgren, A.; Wu, Y. Demo: Experimental Feasibility Study of CCN-lite on Contiki Motes for IoT Data Streams. In Proceedings of the 3rd ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; Association for Computing Machinery (ACM): New York, NY, USA, 2016; pp. 221–222. [Google Scholar] [CrossRef]
- Kugler, P.; Nordhus, P.; Eskofier, B. Shimmer, Cooja and Contiki: A new toolset for the simulation of on-node signal processing algorithms. In Proceedings of the 2013 IEEE International Conference on Body Sensor Networks, Cambridge, MA, USA, 6–9 May 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Dinh, T.; Kim, Y.; Gu, T.; Vasilakos, A.V. An Adaptive Low-Power Listening Protocol for Wireless Sensor Networks in Noisy Environments. IEEE Syst. J. 2018, 12, 2162–2173. [Google Scholar] [CrossRef]
- Dinh, T.; Kim, Y.; Gu, T.; Vasilakos, A.V. L-MAC: A wake-up time self-learning MAC protocol for wireless sensor networks. Comput. Netw. 2016, 105, 33–46. [Google Scholar] [CrossRef]
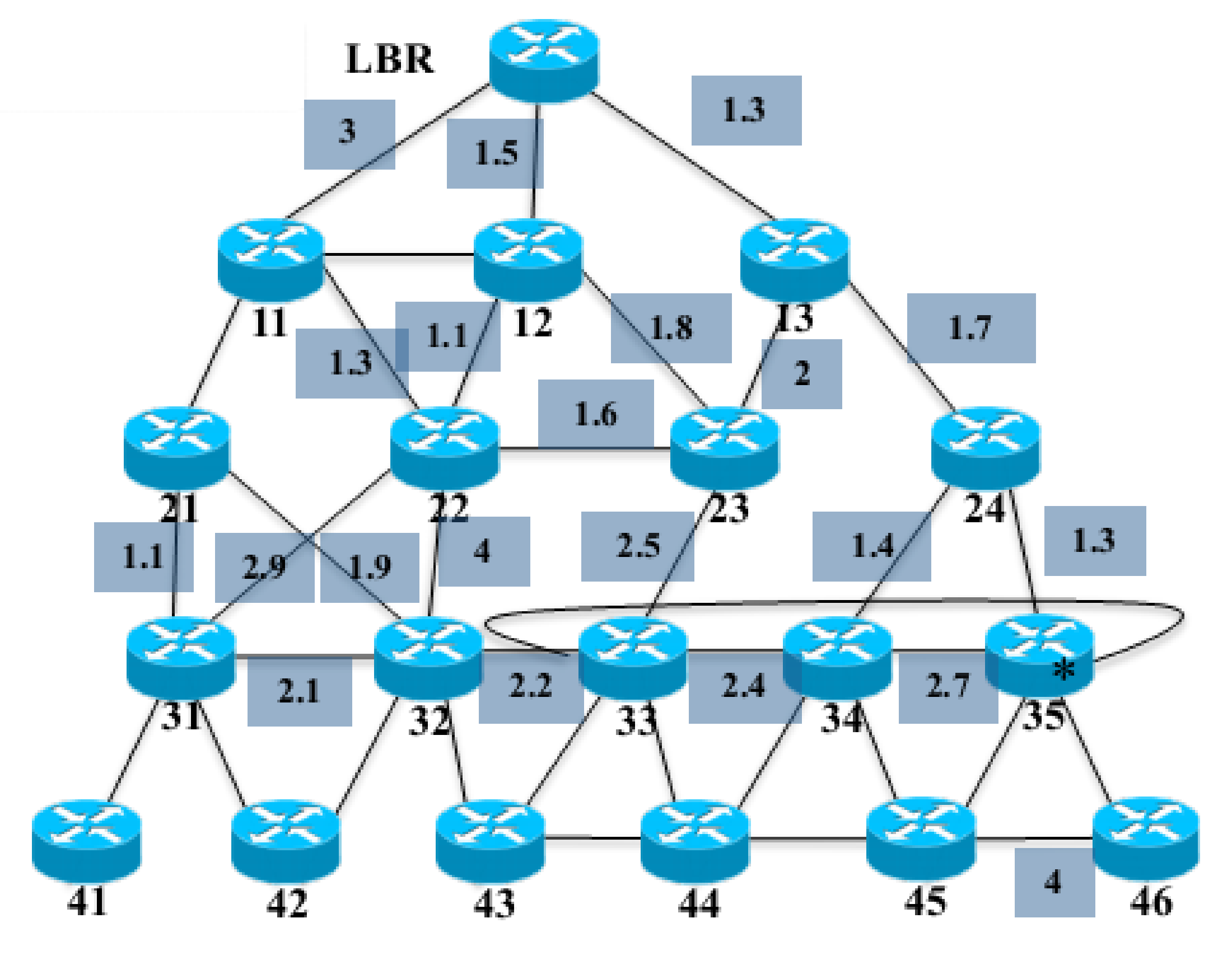










| Parameter | Value | Parameter | Value |
|---|---|---|---|
| CCA check parameter | 400 times | channel sampling | 10 ms |
| transmission range | 50 m | simulation time | 60 min |
| maximum number of child nodes | 15 | Noise model | CPM |
| confidence interval | 95 % | packet size | 127 octets |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dinh, N.-T.; Kim, Y. An Information-Centric Semantic Data Collection Tree for Wireless Sensor Networks. Sensors 2020, 20, 6168. https://doi.org/10.3390/s20216168
Dinh N-T, Kim Y. An Information-Centric Semantic Data Collection Tree for Wireless Sensor Networks. Sensors. 2020; 20(21):6168. https://doi.org/10.3390/s20216168
Chicago/Turabian StyleDinh, Ngoc-Thanh, and Younghan Kim. 2020. "An Information-Centric Semantic Data Collection Tree for Wireless Sensor Networks" Sensors 20, no. 21: 6168. https://doi.org/10.3390/s20216168
APA StyleDinh, N.-T., & Kim, Y. (2020). An Information-Centric Semantic Data Collection Tree for Wireless Sensor Networks. Sensors, 20(21), 6168. https://doi.org/10.3390/s20216168






