Blockchain Reference System Architecture Description for the ISA95 Compliant Traditional and Smart Manufacturing Systems
Abstract
:1. Introduction
2. Method
3. Reference Architecture
3.1. Systems Requirements
3.1.1. Functional Requirements
- Use-case 1, node-to-ledger communications: In any blockchain ecosystem, nodes continuously communicate and synchronize (read and write) data over a peer-to-peer (P2P) network to establish the distributed ledger. This typical blockchain use-case, coupled with smart-contract, can facilitate machine-to-machine (M2M) communication. As per requirement, the proposed architecture should enable node-to-ledger communications, promote autonomous industrial internet of things (IIoT), and smart manufacturing concepts through M2M capabilities.
- Use-case 2, ledger-to-ledger communication: This particular use-case occurs when multiple permissioned ledgers are required to exchange data with each other. Cross subsidiaries and intercompany communication scenarios are examples of use-case 2. In order to maintain the internal ledger consistency, the proposed architecture should allow read-only data access among ledgers.
- Use-case 3, ledger-to-interplanetary file system (IPFS) communication: Distributed ledgers allow blockchain actors to share data with each other. However, when the transmitted data size exceeds certain limits, sharing data through the ledger might become impractical. IPFS provides an efficient way to share oversize data for the ledger platforms. The reference architecture should be able to accommodate the IPFS communication pattern to enable the distribution of oversize data through the ledger.
- Use-case 4, ledger-to-external data sources (Oracles) communication: Smart-contract and blockchain applications may sometimes need information not available on-chain. External data sources, Oracles, become handy to fetch information outside the ecosystem, and the reference architecture should support diverse data exchange patterns over Oracles.
3.1.2. Non-Functional Requirements
- Data protection is a fundamental security design requirement that is expected to be fulfilled by any modern IT system regardless of the business domain. The data protection becomes even more crucial for the blockchain-based systems, which copy the ledger content among several nodes. The distributed architecture with vast data replication imposes robust data protection mechanisms. Thus, the reference architecture should be equipped with technical controls to protect the data at rest, in transit, and during processing from unauthorized access.
- Logging, traceability, and auditability are essential security capabilities that ensure transparency and accountability. Auditability and traceability allow legitimate parties (3rd party verifications through auditors) to track the history of a user, system, and transactional events. Extensive logging mechanisms functioning on various system levels ensure auditability and traceability. Hence, the blockchain-based reference should be able to provide traceability and auditability along with robust, secure, and scalable logging services.
- Availability ensures that the system is accessible when desired under any circumstances. Highly available systems are fault-tolerant and robust to maintain the operational state. In the manufacturing industry, high availability plays a significant role. Although the criticality levels and maximum tolerable downtime might differ, most operational functions can be classified as mission-critical. Consequently, the reference architecture is expected to fulfill high availability requirements.
- Identity and access management mechanisms provide technologies to identify a broad range of ISA95 actors (i.e., subjects in IAM terms) and ensure that only privileged actors can access enterprise resources. Modern manufacturing organizations rely upon complex business processes that are interconnected with a variety of internal sub-organizational units and external partner associations. Therefore, the reference architecture should provide capabilities to identify, authenticate, and authorize a broad spectrum of unique actors spread across all ISA95 automation layers and dispersed on numerous organizational structures. Moreover, the reference architecture should have technical mechanisms to ensure fine-grained authorizations.
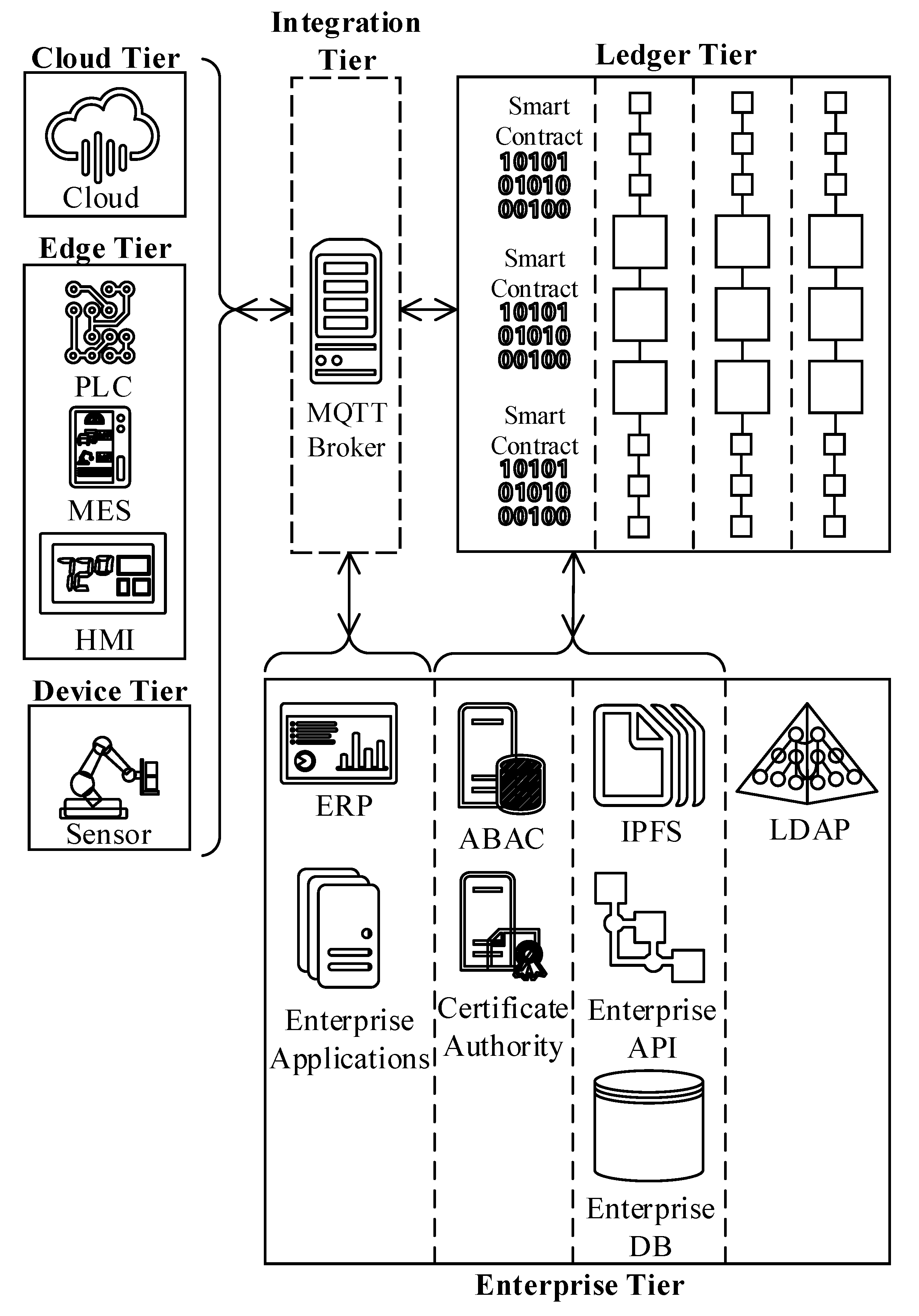
3.2. Reference Architecture Logical View and Components
- Device tier corresponds to the lowest ISA95 automation layer (level 0) where the field devices (i.e., cyber-physical systems including sensors, robots, actuators, etc.) are placed. The device tier traditionally has minimal processing power and may contain a wide range of next-generation (e.g., IIoT) and legacy (e.g., Modbus) devices. Thus, the device tier elements would need software agents and an integration layer to communicate with the ledger successfully.
- Edge tier encapsulates the ISA95 level 1, 2, and 3 devices (i.e., programmable logic controller (PLC), manufacturing execution system (MES), human-machine interface (HMI), supervisory control and data acquisition (SCADA), etc.) that process the data feeds from the underlying layers and provide various process automation capabilities. Like the device tier, this tier also contains a broad spectrum of hardware appliances with varying abilities. Thereby, next-generation devices supporting TCP/IP based communication protocols can directly talk to the ledger, whereas legacy devices may require a software agent and an integration layer to exchange data with the blockchain.
- Cloud tier contains the cloud resources such as AI, ML, and IIoT hub. Some cloud services might require intermediaries to talk to the ledger, whereas others might directly talk to the blockchain. Thus, the integration layer is optional for the cloud tier.
- Integration tier plays a vital role in ensuring interoperability among various ISA95-CTS and SMMS layers. Because some systems, such as IIoT devices, are customizable by design and capable of exchanging data directly with the ledger tier, the integration tier is optional. Thus, the demarcation of this tier is marked with dashes. Although there are a few alternatives, the reference architecture adopts Message Queuing Telemetry Transport (MQTT) protocol for the integration tier. The rationale behind this design decision is that MQTT provides versatile and flexible data conversion capabilities with built-in data adaptors to support out of the box integration capabilities. Moreover, the MQTT protocol embodies an extensive library of numerous communication protocols and messaging standards that are useful to automate system integration.
- Enterprise tier is divided into four sub-regions as follows:
- (a)
- The first sub-region (Figure 1) consists of applications that belong to the ISA95 automation pyramid level 4 actors such as ERP and other enterprise applications.
- (b)
- The second sub-region embodies off-chain infrastructure services that are directly consumable by the blockchain IAM. These infrastructure services comprise enterprise certificate authority (CA) and attribute-based access control (ABAC) system components.
- (c)
- The third sub-region consists of off-chain data sources that are consumable through data oracles. These data sources can be in many forms, including, but not limited to, IPFS, enterprise APIs, and enterprise DB instances.
- (d)
- The fourth sub-region accommodates an enterprise directory service, LDAP, which is not directly consumable by the ledger. LDAP supplies additional identity attributes to enrich the basic identity profile produced by the CA.
- Ledger tier represents the reference architecture’s backbone, and obviously, the rest of the tiers are designed to support the ledger tier. The target group for the blockchain reference architecture is the manufacturing industry, for which the information security, privacy, and system performance requirements are at the highest level. In order to meet these requirements, the reference architecture is based on a permissioned blockchain solution where access to the blockchain ecosystem is restricted.
3.3. Realization of Systems Requirements
3.3.1. Realization of Functional Requirements
- Use-case 1, node-to-ledger communications: As per the design requirement, the proposed blockchain reference architecture should enable M2M communications and autonomous decision mechanisms. The ISA95-CTS is built upon a classical server-client application architecture, and the actors described in the automation pyramid (Figure 2) can generally only talk to one layer above or below. Given the ISA95 standard’s hierarchical structure, achieving M2M communications within the ISA95-CTS boundaries is not a straightforward integration pattern. Nevertheless, a ledger-based data communication pattern can overcome the hierarchy problem. This is because the ledger acts as a data integration layer that enables any ISA95 actor to directly communicate with any other actor within (or even beyond) the ISA95 ecosystem. For instance, a level 4 enterprise resource planning (ERP) application can directly talk to a level 0 sensor. Likewise, an IIoT device, such as a sensor, can communicate with another IIoT device on the same automation level without requiring to cascade the data through upper layers. Also, a smart-contract can initiate autonomous M2M actions by coupling sensors and actuators located on level 0. In fact, Afanasev et al. (2018) [21] studied M2M communication in the SMMS context and explored the smart-contract features with a proof of concept (POC) implementation. Their research article also focused on the M2M micropayments concept through blockchain.Figure 2 demonstrates “Use-case 1,” enabling all ISA95 actors to directly read and write to the blockchain. Because all designated actors can talk to each other through the blockchain, device interoperability becomes a key enabler to realize the proposed architecture. The following sections address interoperability requirements.
- 2.
- Use-case 2, ledger-to-ledger communications: Cross-chain interoperable data exchange and cross-chain inter-executable smart-contract concepts are open research areas in the literature. There are a limited number of articles available in the literature focusing purely on this domain [22,23]. Ledger-to-ledger communication use-case typically occurs when two or more entities happen to utilize separate blockchain installations that are expected to operate or execute a cross-chain smart-contract. Although there are many challenges to realize the ledger-to-ledger use-case, the most prominent issue is maintaining internal data state consistency when the data is modified or created across multiple ledgers. Given the above restrictions, the reference architecture only partially fulfils the ledger-to-ledger communication use-case (Figure 3). Namely, ledgers can read data from each other but not allowed write, create or update data residing on another ledger instance.Data oracles enable smart-contracts to read off-chain data, including other blockchain instances. Therefore, a smart-contract allocated on a source ledger can access the target blockchain through a specially crafted oracle (Figure 3).
- 3.
- Use-case 3, ledger-to-interplanetary file system (IPFS) communications: The block and ledger sizes are the most crucial system properties that directly impact the blockchain scalability and performance. Qui et al. (2019) [24] studied various blockchain platforms relying on IPFS and reported significant performance improvements when IPFS is adopted for large data sets. The reference architecture is designed to reduce the blockchain footprint by hosting oversize data through IPFS based file share attached to the blockchain P2P network.“Use-case 1” above explained how the ISA95 automation pyramid is flattened when BCT is adopted. A similar design pattern also applies to the IPFS data communication scenario. Therefore, various actors shown in Figure 4 can directly read and write to IPFS via P2P network protocols (given that relevant access rights are granted).The “Use-case 3” can be realized with an operational data policy that is implemented as a blockchain smart-contract. The suggested policy can define thresholds, and if a file or transaction content is above the limit, then the blockchain operating system makes the actor write the file content to IPFS. Next, the file hash (acting as the pointer to the original file) is generated and inserted as a new block content to the blockchain.When an actor needs to access the file, first gets the file address on IPFS from the blockchain, and then the actor accesses the address location to read the file content.
- 4.
- Use-case 4, ledger-to-external data sources (Oracles) communications: ISA95-CTS and SMMS ecosystem are composed of several systems, including legacy and externally hosted applications. Not all pieces of this complex environment are compliant with the blockchain architecture. Thus, off-chain data sources will always contain crucial information to on-chain applications and blockchain smart-contracts. The data outside the blockchain system are made available to the blockchain environment through data Oracles. Rest interfaces, SQL database connectors, file parsers are just a few data sources that blockchain oracles can read and fetch data. Likewise, off-chain applications might also need to get data from the distributed ledger. Reverse oracles become handy to emit (write) the blockchain state data to the external world [25]. Figure 5 visualizes “Use-case 4” as follows.
- Smart-contract code (implementation of compliance requirement)
- State DB
- Auditor interface
- The edge and device tiers contain cyber-physical and IIoT systems that have limited processing power. Thereby, the transactional data can be signed with less process-intensive cryptographic signature algorithms to lower the system overhead. Aggregate signatures are considered the best fit for low processing ecosystems because the algorithm can compress n signatures of n messages belonging to n persons into one compact signature.
- Some business flows, such as financial use cases, require a higher level of assurance with separation of duties. In this case, multi-signature schemas can provide the desired level of trust and security.
- Preserving privacy without compromising authentication and non-repudiation of the signer might be necessary for some business scenarios. In the ISA95 “Product Shipping Admin 9.0” business function, for instance, the receiving customer can verify and track the shipping status without revealing the actual identity of the person who has shipped the goods from the factory. Sanchez et al. (2018) [28] focused on a similar problem in the context of the internet of things (IoT). They proposed a privacy-preserving data signature and verification algorithms based on the NI-ZKP concept. Sanchez et al. demonstrated and mathematically proved that the NI-ZKP concept ensures authentication and non-repudiation without revealing the underlying identities.
3.3.2. Realization of Non-Functional Requirements
- As part of application logic
- Extension of consensus protocol
- Policy-based violation behaviors enforced via smart-contracts
- Accept and log on violation policy is useful in occasional cases when the quality parameter is not within the expected range. For instance, some sensors might produce unreliable data that does not conform with the predefined quality characteristics during calibration and configuration phases. The application that is aware of the unusual situation can choose to accept the violation and register an event to the system log files.
- Alarm on violation policy concerns the default behavior when the quality parameter is outside the boundaries. In this case, the parameter value is rejected, and a warning is generated to inform the operator.
- Raise an event on violation policy incorporates actions to handle a violation. In other words, when a quality violation occurs, the system takes predefined measures to correct the situation. For instance, if a malfunctioning robotic arm causes a production line to produce distorted goods, the violation policy can immediately halt the production line to prevent further damage.
- Defer decision on violation policy is useful when a single violation is not sufficient to make a concrete decision. In other words, the system does not respond to a particular quality issue until a certain number of repetitions of the same violation occurs.
- a.
- Data protection
- ISA95 actors supporting TCP/IP and HTTPS protocols can connect to the MQTT integration bus over TLS protected communication channel.
- ISA95 actors supporting TCP/IP but not HTTPS protocols can connect to the MQTT service bus through a reverse proxy that hides the insecure endpoint address. The ISA95 actor is configured only to accept requests from the reverse proxy. Thereby, interacting directly with the actor through an insecure channel is not possible. The reverse proxy supports TLS; thus, the communication line towards the MQTT integration bus is fully encrypted.
- ISA95 actors not supporting TCP/IP protocols are hardwired to an MQTT publisher with protocol conversion capability. This integration pattern enables non-TCP/IP compliant actors to be able to communicate with the rest of the actors with an encrypted TLS tunnel.
- Data communication among suppliers, subsidiaries, and geographically dispersed manufacturing facilities are protected with secure tunneling protocols such as IPSec VPN.
- (a)
- Transactional data constitutes the heart of the blockchain system. The reference architecture embodies four distinct security controls to protect the transactional data as follows.1. Permissioned blockchain: The first layer of data protection is ensured with the permissioned blockchain deployment topology that allows only authorized actors to access the environment. Besides, the file system encryption is enabled for all peers and nodes per default.2. Channels: The data is replicated among all peers and nodes, even with the permissioned installation. The blockchain distributed design approach leads to data confidentiality and privacy concerns. The reference architecture addresses these challenges through virtual segmentation techniques. For instance, IHF can establish multiple virtually segmented ledger instances (i.e., channels) to isolate data among ledgers. The channels are also protected with robust access control mechanisms. Thus, only authorized and explicitly privileged actors can access the data residing on the blockchain [9]. According to Chowdhury et al. (2019) [33], IHF with channel capability significantly stands out from the rest of the blockchain platforms from the privacy standpoint.The ISA95 functional model defines 12 core enterprise functions to organize the manufacturing process [15]. Hence, an enterprise applying the reference architecture for all core ISA95 functions should establish at least 12 channels.3. On-chain transaction encryption: There are several ISA95 business flows (e.g., “Product Cost Account 8.0” function) that process sensitive data such as trade secrets and financial transactions. For scenarios when sensitive material is processed or transported over the ledger, the reference architecture protects the data at rest with robust symmetric encryption algorithms. Figure 9 illustrates the data encryption schema for the reference architecture. The design assumption is that the ISA95 actors at level 4 and 5 can encrypt the data on the application side, whereas the rest may need an intermediary agent software for encryption.The data processing life cycle begins when an actor encrypts sensitive information. Next, the ciphertext is supplied to a smart-contract over an encrypted communication channel. The encrypted data is not processable; thus, the encryption key is also provided to the smart-smart contract through a particular temporary parameter for decryption. IHF characterizes this parameter with the transient term to indicate that it is purged at the end of the smart-contract execution and not stored on-chain anytime. The next step after decryption is the processing phase, during which the sensitive data is protected inside a virtual enclave environment. Finally, the execution outcome is encrypted with the provided key before being recorded to the ledger [38]. The end-to-end encryption strategy maintains the confidentiality and privacy of data at all times.4. Off-chain transaction separation and encryption: Certain regulatory requirements, such as GDPR, restrain distributing sensitive data geographically. However, modern manufacturing organizations depend on complex international engagements. Therefore, restricting the ledger deployment on a geographical basis would seriously limit the reference architecture’s applicability. Hao et al. (2020) [39] studied a similar scenario where private organizations share data with governmental agencies. In their proof of concept work, the sensitive data is distributed through a network-attached file share without applying encryption, similar to the “Use-case 3” described in previous sections.The reference architecture attempts to address location restrictions by preserving the sensitive data on an IPFS based network storage that is geographically situated as per regulatory requirement. However, in order to add an extra layer of protection, individual data elements are encrypted, and hash to the files are distributed through the ledger. Figure 9 depicts the architectural components of the proposed off-chain encryption solution.An example scenario concerning the ISA95 would be the realization of the “Production Shipping Admin 9.0” flow constituting customer data in the form of personally identifiable information (PII), which is subject to GDPR and required to remain within the boundaries of the EU.
- (b)
- Smart-contract and smart-contract state protection: An ordinary blockchain system saves and replicates smart-contract logic (source code) and state data (an outcome of an execution) across the blockchain by default. In other words, the execution results, state data, and smart-contracts are visible to all peers and nodes. However, some business engagements and contractual terms are trade secrets, and unauthorized access is not acceptable. The reference architecture addresses these challenges with a two-folded approach adopted from IHF [9]. Firstly, any sensitive state data can be selectively encrypted, as shown in Figure 9. The encryption restricts access to the actors who have the decryption key. Secondly, sensitive smart-contracts can be deployed to an isolated containerized node where replication is prohibited. This deployment strategy decreases the availability of particular smart-contract in favor of increasing security.
- (c)
- User data protection: Traditional blockchain technologies, such as Bitcoin, are infamous for preserving user privacy and transactional anonymity. In other words, the transactions are traceable and linkable to a user profile. The reason is that traditional blockchain technologies rely on certificate-based authentication standards, such as X.509, and the certificate-based schemas are not able to hide nonessential attributes from the certificates. Hence, user privacy is profoundly disrupted [40]. Furthermore, actors always sign transactions with the same private key, and, even if the identities are secret, all the transactions signed by the same actor are still linkable to each other. Besides, in the case of identity theft, all the transactions committed by the stolen key become fully traceable and available to the public.Camenisch et al. (2013) [40] proposed a novel privacy-preserving attribute-based authentication (PPABA) schema to overcome the anonymity and transaction likability shortcomings. The strength of PPABA is that the issuer can generate separate tokens for each user attribute, and a user can produce (derive) unique transactional tokens (without requiring issuer interaction) that are verifiable with the issuer’s public key. Because the user forges a new token for each transaction, it is not feasible to trace back and associate the transactions with an individual even after a private key compromise. Besides, the PPABA schema ensures higher anonymity by excluding unnecessary user attributes from the transactional data.Commercially available IBM Identity Mixer (IIM) and Microsoft U-Prove provide pluggable PPABA libraries that can constitute a basis to ensure user data protection for the reference architecture.Figure 10 illustrates the reference architecture components adopted from IIM [38] to support the PPABA schema. Each ISA95 actor in Figure 10 is assigned a membership service provider (MSP) that secures certificates and private keys. According to the example shown in Figure 10, the CA issues a certificate to an ISA95 actor with three attributes, Attr_1, Attr_2, and Enr_ID. However, because the particular transaction in question does not require all identity attributes, the actor derives an entirely new certificate token only with Attr_2 to be able to sign the transaction with minimum identity information. The most significant advantage of the PPABA schema is that the signed transaction is still verifiable with the CA’s public key, even if the signature is based on a key that is not issued by the CA.On the permissioned blockchain platform side, Monero anonymizes the transactional origin and destination to protect privacy. The anonymization process produces a group signature that obfuscates the signer’s identity with the CryptoNote algorithm. Furthermore, a one-time generated stealth address hides transactional sources [41].
- b.
- Logging, traceability, and auditability:
- c.
- Availability:
- (a)
- Single region, single availability zone, and single worker node
- (b)
- Single region, single availability zone, and multiple worker nodes
- (c)
- Single region, multi-availability zones, and multiple worker nodes
- (d)
- Multi-region, single availability zone, and multiple worker nodes
- d.
- Identity and Access Management (IAM):
- The transaction validation nodes make sure that the signer’s public key is not in the certificate revocation list (CRL), and the signature is computationally correct.
- The transaction validation nodes confirm that the signer is authorized to perform the demanded operation. Furthermore, the MSP access policy can leverage the attributes defined by the signer’s public certificate. However, some complex MSP policies may require additional attributes outside the standard X.509 certificate format. In such scenarios, the certificate content can be enriched with the information ingested from the enterprise LDAP. The externally provided LDAP attributes can contain a broad range of information, including group memberships (access privilege) of actors. Hence, the access control capability of the reference architecture is extended to support the RBAC model.
3.4. Soft Dimensions of Reference Architecture
- Viability: Ivanov and Dolgui (2020) [3] researched the effects of the COVID-19 outbreak on the global supply chain networks. The COVID-19 pandemic has sadly shown the fragility of the supply chains under extreme conditions. This is because the modern supply chains are either designed in linear or network topology. Ivanov and Dolgui criticized that most supply chains are designed to maintain high production output and performance. Thereby, the supply chains usually disregard the survivability aspect to ensure society’s mobility and communication under extraordinary situations. Ivanov and Dolgui proposed the intertwined supply network concept that constitutes highly interconnected entities, guaranteeing the provision of goods to the communities in any condition.Lack of trust among suppliers and infrastructure fragility are two main challenges affecting supply chain viability. Kumar et al. (2020) [47] highlighted how blockchain-based supply chain platforms could establish trust among untrusted suppliers by ensuring high transparency. Likewise, we elaborated in the availability section on how the reference architecture is designed to withstand significant disruptions with robust infrastructure deployment options. Thereby, the reference architecture can significantly improve supply chain viability.
- Sustainability: The importance of sustainability has become significant in recent years, especially since UN member states’ SDG adaptation. Leng et al. (2020) [4] studied SDGs and correlated “Goal 12: Responsible consumption and production” and “Goal 9: Industry, innovation, and infrastructure” with sustainable manufacturing practices. They also identified that distributed manufacturing, including crowd and clustered manufacturing, are the primary driver for these goals and surveyed different BCTs available in the literature from the manufacturing sustainability perspective. The survey conducted by Leng et al. highlighted that the BCT could enhance efficiency, reduce the system complexity with high interoperability, increase the manufacturing system security, boost operational transparency with traceability and ensure end-product authenticity.Jabbour et al. (2020) [48] surveyed the sustainability aspects of various supply chain networks. They concluded that BCT and big data analysis methods could improve the agriculture industry’s efficiency by shortening the supply-chain networks. Likewise, BCT could enhance the accuracy of procurement forecasts in the agriculture industry.Wamba et al. (2020) [49] empirically explored dynamics between blockchain determinants and supply chain performance. Their research justifies the positive relationship between blockchain adaptation and supply chain performance through increased transparency.In a nutshell, the reference architecture’s design specifications are compliant with the BCT empowered sustainability outcomes presented by multiple researchers. Thereby, the reference architecture constitutes a crucial blueprint to enable the manufacturing industry to meet UN SDGs.
- Social and economic inclusion: Several rural societies are disconnected from developed cities. Due to insufficient economic opportunities, the gap between developed and underdeveloped regions is getting wider. Thereby, social and economic inequality has become prevalent in developing countries. Schuetz and Venkatesh (2020) [5] studied India and financial inclusion from this perspective. Their research highlights that rural India can gain momentum on economic and social development by expanding global supply chain networks to the remote villages. Schuetz and Venkatesh also proposed to adopt blockchain-based technologies to extend the global supply chain coverage towards the rural areas. Thereby, blockchain-enabled ISA95 enterprise functions focusing on supply chain use cases can support resolving the social and economic inclusion issues in developing countries.
4. Conclusions
5. Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Yalcinkaya, E.; Maffei, A.; Akillioglu, H.; Onori, M. Empowering ISA95 Compliant Traditional and Smart Manufacturing Systems with the Blockchain Technology. Sensors 2020. submitted for publication. [Google Scholar]
- Yalcinkaya, E.; Maffei, A. Blockchain Suitability Assessment of Manufacturing Functions Defined by the ISA95 Standard. Ind. Eng. Manag. Syst. 2020. submitted for publication. [Google Scholar]
- Ivanov, D.; Dolgui, A. Viability of intertwined supply networks: Extending the supply chain resilience angles towards survivability. A position paper motivated by COVID-19 outbreak. Int. J. Prod. Res. 2020, 58, 2904–2915. [Google Scholar] [CrossRef] [Green Version]
- Leng, J.; Ruan, G.; Jiang, P.; Xu, K.; Liu, Q.; Zhou, X.; Liu, C. Blockchain-empowered sustainable manufacturing and product lifecycle management in industry 4.0: A survey. Renew. Sustain. Energy Rev. 2020, 132, 110112. [Google Scholar] [CrossRef]
- Schuetz, S.; Venkatesh, V. Blockchain, adoption, and financial inclusion in India: Research opportunities. Int. J. Inf. Manag. 2020, 52, 101936. [Google Scholar] [CrossRef]
- Maier, M.W.; Emery, D.; Hilliard, R. Software architecture: Introducing IEEE standard 1471. Computer 2001, 34, 107–109. [Google Scholar] [CrossRef]
- ISO. ISO/IEC 25010:2011 Software Engineering—Software product Quality Requirements and Evaluation (SQuaRE). 2005. Available online: https://www.iso.org/obp/ui/#iso:std:iso-iec:25010:ed-1:v1:en (accessed on 9 November 2020).
- Haoues, M.; Sellami, A.; Ben-Abdallah, H.; Cheikhi, L. A guideline for software architecture selection based on ISO 25010 quality related characteristics. Int. J. Syst. Assur. Eng. Manag. 2017, 8, 886–909. [Google Scholar] [CrossRef]
- IBM. Hyperledger-Fabricdocs Documentation; IBM: Armonk, NY, USA, 2019. [Google Scholar]
- Du, M.; Ma, X.; Zhang, Z.; Wang, X.; Chen, Q. A review on consensus algorithm of blockchain. In Proceedings of the 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Banff, AB, Canada, 5–8 October 2017. [Google Scholar]
- Docker: Empowering App Development for Developers. 2020. Available online: https://www.docker.com/ (accessed on 9 November 2020).
- Kubernetes. 2020. Available online: https://kubernetes.io/ (accessed on 9 November 2020).
- Barenji, A.V.; Li, Z.; Wang, W.M.; Huang, G.Q.; Guerra-Zubiaga, D.A. Blockchain-based ubiquitous manufacturing: A secure and reliable cyber-physical system. Int. J. Prod. Res. 2020, 58, 2200–2221. [Google Scholar] [CrossRef]
- Bamakan, S.M.H.; Motavali, A.; Babaei Bondarti, A. A survey of blockchain consensus algorithms performance evaluation criteria. Expert Syst. Appl. 2020, 154, 113385. [Google Scholar] [CrossRef]
- ANSI. ISA-95.00.01-2010, ISA-95.00.02-2010, ISA-95.00.03-2013, ISA-95.00.04-2012, ISA-95.00.05-2013; ANSI: New York, NY, USA, 2010. [Google Scholar]
- Rondón, R.; Gidlund, M.; Landernäs, K. Evaluating Bluetooth Low Energy Suitability for Time-Critical Industrial IoT Applications. Int. J. Wirel. Inf. Netw. 2017, 24, 278–290. [Google Scholar] [CrossRef] [Green Version]
- Ferrari, P.; Sisinni, E.; Brandão, D.; Rocha, M. Evaluation of communication latency in industrial IoT applications. In Proceedings of the 2017 IEEE International Workshop on Measurement and Networking (M&N), Naples, Italy, 27–29 September 2017. [Google Scholar]
- Sund, T.; Lööf, C.; Nadjm-Tehrani, S.; Asplund, M. Blockchain-based event processing in supply chains—A case study at IKEA. Robot. Comput. Integr. Manuf. 2020, 65, 101971. [Google Scholar] [CrossRef]
- Abebe, E.; Behl, D.; Govindarajan, C.; Hu, Y.; Karunamoorthy, D.; Novotny, P.; Pandit, V.; Ramakrishna, V.; Vecchiola, C. Enabling Enterprise Blockchain Interoperability with Trusted Data Transfer (industry track). In Proceedings of the 20th International Middleware Conference Industrial Track, Davis, CA, USA, 9–13 December 2019; pp. 29–35. [Google Scholar]
- ISO/IEC 25012. Available online: https://iso25000.com/index.php/en/iso-25000-standards/iso-25012?limit=5&limitstart=0 (accessed on 9 November 2020).
- Afanasev, M.Y.; Fedosov, Y.V.; Krylova, A.A.; Shorokhov, S.A. An application of blockchain and smart contracts for machine-to-machine communications in cyber-physical production systems. In Proceedings of the 2018 IEEE Industrial Cyber-Physical Systems (ICPS), St. Petersburg, Russia, 15–18 May 2018; pp. 13–19. [Google Scholar]
- Konashevych, O. Cross-Blockchain Protocol for Public Registries. Int. J. Web Inf. Syst. 2020, 1–45. [Google Scholar] [CrossRef]
- Qiu, H.; Wu, X.; Zhang, S.; Leung, V.C.M.; Cai, W. ChainIDE: A cloud-based integrated development environment for cross-blockchain smart contracts. In Proceedings of the 11th IEEE International Conference on Cloud Computing Technology and Science (CloudCom 2019), Sydney, Australia, 11–13 December 2019; pp. 317–319. [Google Scholar]
- Zheng, Q.; Li, Y.; Chen, P.; Dong, X. An Innovative IPFS-Based Storage Model for Blockchain. In Proceedings of the 2018 IEEE/WIC/ACM International Conference on Web Intelligence (WI), Santiago, Chile, 3–6 December 2018; pp. 704–708. [Google Scholar]
- Xu, X.; Pautasso, C.; Zhu, L.; Lu, Q.; Weber, I. A pattern collection for blockchain-based applications. In Proceedings of the 23rd European Conference on Pattern Languages of Programs, Irsee, Germany, 4–8 July 2018. [Google Scholar]
- Zhang, W.; Yuan, Y.; Hu, Y.; Nandakumar, K.; Chopra1, A.; Sim, S.; Caro, A. De Blockchain-Based Distributed Compliance in Multinational Corporations’ Cross-Border Intercompany Transactions. In Future of Information and Communication Conference; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Fang, W.; Chen, W.; Zhang, W.; Pei, J.; Gao, W.; Wang, G. Digital signature scheme for information non-repudiation in blockchain: A state of the art review. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 1–15. [Google Scholar] [CrossRef] [Green Version]
- Sanchez, J.L.C.; Bernabe, J.B.; Skarmeta, A.F. Towards privacy preserving data provenance for the Internet of Things. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018. [Google Scholar] [CrossRef]
- Gaetani, E.; Aniello, L.; Baldoni, R.; Lombardi, F.; Margheri, A.; Sassone, V. Blockchain-based database to ensure data integrity in cloud computing environments. CEUR Workshop Proc. 2017, 1816, 146–155. [Google Scholar]
- Ioini, N.E.; Pahl, C. Trustworthy orchestration of container based edge computing using permissioned blockchain. In Proceedings of the 2018 Fifth International Conference on Internet of Things: Systems, Management and Security, Valencia, Spain, 15–18 October 2018; pp. 147–154. [Google Scholar]
- Macdonald, M.; Liu-Thorrold, L.; Julien, R. The Blockchain: A Comparison of Platforms and Their Uses Beyond Bitcoin. Univ. Queensl. 2017. [Google Scholar] [CrossRef]
- Sukhwani, H.; Wang, N.; Trivedi, K.S.; Rindos, A. Performance modeling of hyperledger fabric (permissioned blockchain network). In Proceedings of the 2018 IEEE 17th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 1–3 November 2018. [Google Scholar]
- Chowdhury, M.J.M.; Ferdous, M.S.; Biswas, K.; Chowdhury, N.; Kayes, A.S.M.; Alazab, M.; Watters, P. A comparative analysis of distributed ledger technology platforms. IEEE Access 2019, 7, 167930–167943. [Google Scholar] [CrossRef]
- Akhtar, Z. From Blockchain to Hashgraph: Distributed Ledger Technologies in the Wild. In Proceedings of the 2019 International Conference on Electrical, Electronics and Computer Engineering (UPCON), Aligarh, India, 8–10 November 2019; pp. 1–6. [Google Scholar]
- Ramachandran, G.S.; Wright, K.-L.; Krishnamachari, B. Trinity: A Distributed Publish/Subscribe Broker with Blockchain-based Immutability. arXiv 2018, arXiv:1807.03110. [Google Scholar]
- Cappiello, C.; Comuzzi, M.; Daniel, F.; Meroni, G. Data Quality Control in Blockchain Applications. In International Conference on Business Process Managemen; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Kumar, A.; Kashyap, A.; Phegade, V.; Schrater, J. Self-Defending Key Management Service with Intel® Software Guard Extensions; Intel: Santa Clara, CA, USA, 2018; pp. 1–9. [Google Scholar]
- Chakraborty, S.; Jayachandran, P. Blockchains Architecture, Design and Use Cases—Blockchain Security III. Natl. Programme Technol. Enhanc. Learn. 2019. Available online: https://drive.google.com/file/d/1qWsAnGJKlHuxeM4Q8oIHKpdjdgEVBClc/view (accessed on 9 November 2020).
- Hao, Y.; Piao, C.; Zhao, Y.; Jiang, X. Privacy Preserving Government Data Sharing Based on Hyperledger Blockchain. In International Conference on e-Business Engineering; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Camenisch, J.; Dubovitskaya, M.; Lehmann, A.; Neven, G.; Paquin, C.; Preiss, F.-S. Concepts and Languages for Privacy-Preserving Attribute-Based Authentication. In IFIP Working Conference on Policies and Research in Identity Management; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Kuo, T.T.; Zavaleta Rojas, H.; Ohno-Machado, L. Comparison of blockchain platforms: A systematic review and healthcare examples. J. Am. Med. Inform. Assoc. 2019, 26, 462–478. [Google Scholar] [CrossRef]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the Attack Surface of Blockchain: A Systematic Overview. arXiv 2019, arXiv:1904.03487. [Google Scholar]
- From Distributed Consensus Algorithms to the Blockchain Consensus Mechanism. Alibaba Cloud, 2019. Available online: https://medium.com/datadriveninvestor/from-distributed-consensus-algorithms-to-the-blockchain-consensus-mechanism-75ee036abb65 (accessed on 9 November 2020).
- IBM. IBM Blockchain Platform High Availability (HA). 2019. Available online: https://cloud.ibm.com/docs/blockchain-sw?topic=blockchain-sw-ibp-console-ha (accessed on 9 November 2020).
- Chakraborty, S.; Jayachandran, P. Blockchains Architecture, Design and Use Cases—Fabric Membership and Identity Management. Natl. Programme Technol. Enhanc. Learn. 2019. Available online: https://drive.google.com/file/d/13P8uNQN0LIj8LSQz_WB7FqZqQMo8ifT3/view (accessed on 9 November 2020).
- Yalcinkaya, E.; Maffei, A.; Onori, M. Application of Attribute Based Access Control Model for Industrial Control Systems. Int. J. Comput. Netw. Inf. Secur. 2017, 9, 12–21. [Google Scholar] [CrossRef] [Green Version]
- Kumar, M.S.; Raut, D.R.D.; Narwane, D.V.S.; Narkhede, D.B.E. Applications of industry 4.0 to overcome the COVID-19 operational challenges. Diabetes Metab. Syndr. Clin. Res. Rev. 2020, 14, 1283–1289. [Google Scholar] [CrossRef] [PubMed]
- Jabbour, C.J.C.; Fiorini, P.D.C.; Ndubisi, N.O.; Queiroz, M.M.; Piato, É.L. Digitally-enabled sustainable supply chains in the 21st century: A review and a research agenda. Sci. Total Environ. 2020, 725, 138177. [Google Scholar] [CrossRef]
- Wamba, S.F.; Queiroz, M.M.; Trinchera, L. Dynamics between blockchain adoption determinants and supply chain performance: An empirical investigation. Int. J. Prod. Econ. 2020, 229, 107791. [Google Scholar] [CrossRef]











| Requirements | Requirement Specifications | Realization of Requirements | ||
|---|---|---|---|---|
| Functional requirements | Regulatory compliance | Ensure regulatory compliance | 1. Smart-contract implementation of compliance requirements 2. Dedicated state database to safeguard compliance parameters 3. Regulators and auditors are provided with a read-only interface to perform compliance verification activities | |
| Data integrity and signing | Support a broad range of data integrity and digital signature schemas | 1. Tamper-proof data blocks linked to each other with a hash-based pointer 2. Pluggable cryptographic library extensions to support various blockchain signature algorithms such as aggregate, multi-signatures, and privacy-preserving NI-ZKP 3. Off-chain data hash and signatures are stored on the ledger | ||
| Automation | Promote and allow manufacturing automation capabilities | 1. Deterministic process automation with tamper-proof smart-contract execution 2. Smart-contracts emit event messages to contribute autonomous decision mechanisms | ||
| Non-functional requirements | Scalability | Ensure horizontal and vertical scalability | 1. A fully virtualized container environment ensuring horizontal and vertical scalability for processing capacity and storage area 2. Big files are stored on IPFS to reduce ledger footprint | |
| Performance | Keep latency below 300 ms and ensure 6000 to 8000 tps | 1. Permissioned ledgers with trivial RAFT consensus algorithm exceed 10,000 tps 2. At least four CPU instances per ordering service 3. At least four individual ordering nodes 4. Block size of 80 transactions to ensure latency | ||
| Interoperability | Ensure interoperability and seamless integration across ISA95 automation layers | 1. MQTT based integration layer ensures technical and syntactic interoperability 2. Systems compliant with ISA95 standard are already semantically interoperable3. Smart-contracts ensure governance interoperability | ||
| Data quality | Define a set of quality violation policies as unified system behaviors | 1. Accept and log on violation policy when a quality parameter is not in the range 2. Alarm on violation policy when a quality parameter is outside the range 3. Raise an event on violation policy to correct the situation 4. Defer decision on violation policy when a single violation is not sufficient to make a concrete decision | ||
| Information Security | Data protection | Protect data at rest, in transit, and during processing from unauthorized access | 1. Protecting data in transit with TLS 2. Protecting data while in use with Containerized TEE technology 3. Protecting data at rest through permissioned blockchain and virtual segmentation techniques. 4. Robust symmetric encryption algorithms to protect on-chain data, smart-contract state data, and IPFS at rest 5. Isolated containerized nodes to protect smart-contract source code during deployment 6. PPABA schema to overcome anonymity and transaction unlikability challenges | |
| Logging, traceability, and auditability | Ensure traceability and auditability along with robust, secure, and scalable logging services | 1. Consolidated system logs across on a dedicated blockchain instance 2. Restricted system log access and sensitive information masking 3. Threshold cryptography and key escrowing to allow auditability for the on-chain encrypted data 4. Issuer ID encryption with auditor public key to allow PPABA anonymized transactions auditability | ||
| Availability | Ensure high availability and system robustness | 1. RAFT crash tolerant consensus algorithm 2. High availability ensured with a single region, multi-availability zones, and multiple worker node deployments 3. At least five dedicated nodes to operate RAFT 4. All peers ensure duality principle per client application type for each channel | ||
| Identity and access management | Provide capabilities to identify, authenticate, and authorize actors and embody technical mechanisms to ensure fine-grained authorizations | 1. Access to IPFS is protected with SSO based protocols such as OAuth and SAML 2. IAM operations are managed on the blockchain ecosystem through MSP 3. Certificate-based identification and authentication services 4. MSP content is protected with HSM, Keystore, and smart cards 5. RBAC and ABAC are supported for the scenarios where fine-grained access control capabilities are demanded | ||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yalcinkaya, E.; Maffei, A.; Onori, M. Blockchain Reference System Architecture Description for the ISA95 Compliant Traditional and Smart Manufacturing Systems. Sensors 2020, 20, 6456. https://doi.org/10.3390/s20226456
Yalcinkaya E, Maffei A, Onori M. Blockchain Reference System Architecture Description for the ISA95 Compliant Traditional and Smart Manufacturing Systems. Sensors. 2020; 20(22):6456. https://doi.org/10.3390/s20226456
Chicago/Turabian StyleYalcinkaya, Erkan, Antonio Maffei, and Mauro Onori. 2020. "Blockchain Reference System Architecture Description for the ISA95 Compliant Traditional and Smart Manufacturing Systems" Sensors 20, no. 22: 6456. https://doi.org/10.3390/s20226456
APA StyleYalcinkaya, E., Maffei, A., & Onori, M. (2020). Blockchain Reference System Architecture Description for the ISA95 Compliant Traditional and Smart Manufacturing Systems. Sensors, 20(22), 6456. https://doi.org/10.3390/s20226456





