A Survey for the Ranking of Trajectory Prediction Algorithms on Ubiquitous Wireless Sensors
Abstract
1. Introduction
2. Existing Trajectory Prediction Algorithms
2.1. Markov Model
2.2. Hidden Markov Model
2.3. T-pattern Tree
2.4. Bayesian Network
2.5. Apriori-Traj Algorithm
2.6. Traj-Prefix-Span Algorithm
2.7. Query Triggered Revision
2.8. Hybrid Genetic Algorithm
2.9. Seman-Predict
2.10. The Hybrid Prediction Model
2.11. State Predictor Method
2.12. Trajectory Similarity-Based Approach for Location Prediction (TLP)
2.13. Gaussian Process Regression (GPR)
3. Related Work
4. Datasets
4.1. American Time-Use Survey (ATUS)
4.2. Microsoft Multi-person Location Survey (MSMLS)
4.3. Phonetic
4.4. GeoLife
4.5. CenceMe
4.6. TIGER
4.7. Thomas Brinkhoff
4.8. MIT Reality
4.9. Augsburg Indoor Location Tracking Benchmarks
5. Public and Propriety Datasets
6. Our Approach
7. Results and Discussion
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Jensen, F.V. An Introduction to Bayesian Networks; UCL Press: London, UK, 1996; Volume 210. [Google Scholar]
- Rabiner, L.; Juang, B. An introduction to Hidden Markov Models. IEEE ASSP Mag. 1986, 3, 4–16. [Google Scholar] [CrossRef]
- Quinlan, J.R. Induction of decision trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef]
- Specht, D.F. Probabilistic neural networks. Neural Netw. 1990, 3, 109–118. [Google Scholar] [CrossRef]
- Garnier, J.; Osguthorpe, D.J.; Robson, B. Analysis of the accuracy and implications of simple methods for predicting the secondary structure of globular proteins. J. Mol. Biol. 1978, 120, 97–120. [Google Scholar] [CrossRef]
- Petzold, J.; Bagci, F.; Trumler, W.; Ungerer, T. Next location prediction within a smart office building. Cogn. Sci. Res. Pap. Univ. Sussex CSRP 2005, 577, 69. [Google Scholar]
- Scellato, S.; Musolesi, M.; Mascolo, C.; Latora, V.; Campbell, A.T. Nextplace: A spatio-temporal prediction framework for pervasive systems. In Proceedings of the International Conference on Pervasive Computing, Seattle, WA, USA, 21–25 March 2011; pp. 152–169. [Google Scholar]
- Krumm, J. A markov model for driver turn prediction. In Proceedings of the SAE 2008 World Congress, Detroit, MI, USA, 14–17 April 2008. [Google Scholar]
- Kim, B.; Kang, S.; Ha, J.Y.; Song, J. Agatha: Predicting daily activities from place visit history for activity-aware mobile services in smart cities. Int. J. Distrib. Sens. Netw. 2015, 11, 867602. [Google Scholar] [CrossRef]
- Wikimedia Foundation. Markov Chain. 2020. Available online: https://en.wikipedia.org/wiki/Markov_chain (accessed on 12 September 2020).
- Jurafsky, D. Speech & Language Processing; Pearson Education India: New Delhi, India, 2000. [Google Scholar]
- Monreale, A.; Pinelli, F.; Trasarti, R.; Giannotti, F. Wherenext: A location predictor on trajectory pattern mining. In Proceedings of the 15th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Paris, France, 28 June–1 July 2009; pp. 637–646. [Google Scholar]
- Samira, A.; Mansoureh, J.; Abdollah, D. Distracted Driving Prediction Model Using a Bayesian Network Approach. In Proceedings of the International Conference on Transportation and Development 2020, Seattle, WA, USA, 26–29 May 2020; American Society of Civil Engineers: Reston, VA, USA, 2020; pp. 212–221. [Google Scholar]
- Morzy, M. Prediction of moving object location based on frequent trajectories. In Proceedings of the International Symposium on Computer and Information Sciences, Istanbul, Turkey, 1–3 November 2006; pp. 583–592. [Google Scholar]
- Morzy, M. Mining frequent trajectories of moving objects for location prediction. In Proceedings of the Machine Learning and Data Mining in Pattern Recognition, Leipzig, Germany, 18–20 July 2007; pp. 667–680. [Google Scholar]
- Xu, B.; Wolfson, O. Time-series prediction with applications to traffic and moving objects databases. In Proceedings of the 3rd ACM International Workshop on Data Engineering for Wireless and Mobile Access, San Diego, CA, USA, 19 September 2003; pp. 56–60. [Google Scholar]
- Ying, J.J.C.; Lee, W.C.; Weng, T.C.; Tseng, V.S. Semantic trajectory mining for location prediction. In Proceedings of the 19th ACM SIGSPATIAL International Conference on Advances in Geographic Information Systems, Chicago, IL, USA, 1–4 November 2011; pp. 34–43. [Google Scholar]
- Jeung, H.; Liu, Q.; Shen, H.T.; Zhou, X. A hybrid prediction model for moving objects. In Proceedings of the 24th International Conference on Data Engineering Workshops (ICDE 2008), Cancun, Mexico, 7–12 April 2008; pp. 70–79. [Google Scholar]
- Petzold, J.; Bagci, F.; Trumler, W.; Ungerer, T. Confidence estimation of the state predictor method. In Proceedings of the EUSAI, Eindhoven, The Netherlands, 8–11 November 2004; pp. 375–386. [Google Scholar]
- Liu, Z.; Hu, L.; Wu, C.; Ding, Y.; Zhao, J. A novel trajectory similarity–based approach for location prediction. Int. J. Distrib. Sens. Netw. 2016, 12, 1550147716678426. [Google Scholar] [CrossRef][Green Version]
- Cai, H.; Jia, X.; Feng, J.; Li, W.; Hsu, Y.M.; Lee, J. Gaussian Process Regression for numerical wind speed prediction enhancement. Renew. Energy 2020, 146, 2112–2123. [Google Scholar] [CrossRef]
- Cheng, C.; Jain, R.; van den Berg, E. Location prediction algorithms for mobile wireless systems. In Wireless Internet Handbook; CRC Press, Inc.: Boca Raton, FL, USA, 2003; pp. 245–263. [Google Scholar]
- Lefèvre, S.; Vasquez, D.; Laugier, C. A survey on motion prediction and risk assessment for intelligent vehicles. Robomech. J. 2014, 1, 1. [Google Scholar] [CrossRef]
- Lin, M.; Hsu, W.J. Mining GPS data for mobility patterns: A survey. Pervasive Mob. Comput. 2014, 12, 1–16. [Google Scholar] [CrossRef]
- Gao, H.; Tang, J.; Liu, H. Mobile location prediction in spatio-temporal context. In Proceedings of the Nokia Mobile Data Challenge Workshop, Newcastle, UK, 18–19 June 2012; Volume 41, pp. 1–4. [Google Scholar]
- Morris, B.T.; Trivedi, M.M. A survey of vision-based trajectory learning and analysis for surveillance. IEEE Trans. Circuits Syst. Video Technol. 2008, 18, 1114–1127. [Google Scholar] [CrossRef]
- Greenwade, G.D. The Comprehensive Tex Archive Network (CTAN). TUGBoat 1993, 14, 342–351. [Google Scholar]
- Stegmann, R.A.; Žliobaitė, I.; Tolvanen, T.; Hollmén, J.; Read, J. A survey of evaluation methods for personal route and destination prediction from mobility traces. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2018, 8, e1237. [Google Scholar] [CrossRef]
- Xu, G.; Gao, S.; Daneshmand, M.; Wang, C.; Liu, Y. A survey for mobility big data analytics for geolocation prediction. IEEE Wirel. Commun. 2017, 24, 111–119. [Google Scholar] [CrossRef]
- Ashbrook, D.; Starner, T. Using GPS to learn significant locations and predict movement across multiple users. Pers. Ubiquitous Comput. 2003, 7, 275–286. [Google Scholar] [CrossRef]
- Matekenya, D.; Ito, M.; Shibasaki, R.; Sezaki, K. Enhancing location prediction with big data: Evidence from dhaka. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing: Adjunct, Heidelberg, Germany, 12–16 September 2016; pp. 753–762. [Google Scholar]
- Cho, S.B. Exploiting machine learning techniques for location recognition and prediction with smartphone logs. Neurocomputing 2016, 176, 98–106. [Google Scholar] [CrossRef]
- Gambs, S.; Killijian, M.O.; del Prado Cortez, M.N. Next place prediction using mobility markov chains. In Proceedings of the First Workshop on Measurement, Privacy, and Mobility, Bern, Switzerland, 10–13 April 2012; p. 3. [Google Scholar]
- Yavaş, G.; Katsaros, D.; Ulusoy, Ö.; Manolopoulos, Y. A data mining approach for location prediction in mobile environments. Data Knowl. Eng. 2005, 54, 121–146. [Google Scholar] [CrossRef]
- Tran, L.H.; Catasta, M.; McDowell, L.K.; Aberer, K. Next place prediction using mobile data. In Proceedings of the Mobile Data Challenge Workshop (MDC 2012), Newcastle, UK, 18–19 June 2012. No. EPFL-CONF-182131. [Google Scholar]
- Simmons, R.; Browning, B.; Zhang, Y.; Sadekar, V. Learning to predict driver route and destination intent. In Proceedings of the Intelligent Transportation Systems Conference (ITSC’06), Toronto, ON, Canada, 17–20 September 2006; pp. 127–132. [Google Scholar]
- Krumm, J.; Horvitz, E. Predestination: Inferring destinations from partial trajectories. In Proceedings of the UbiComp 2006: Ubiquitous Computing, Orange County, CA, USA, 17–21 September 2006; pp. 243–260. [Google Scholar]
- Ho, W.; Ho, G.T.; Ji, P.; Lau, H.C. A hybrid genetic algorithm for the multi-depot vehicle routing problem. Eng. Appl. Artif. Intell. 2008, 21, 548–557. [Google Scholar] [CrossRef]
- Froehlich, J.; Krumm, J. Route Prediction from Trip Observations; Technical Report; SAE Technical Paper: Warrendale, PA, USA, 2008. [Google Scholar]
- Tao, Y.; Faloutsos, C.; Papadias, D.; Liu, B. Prediction and indexing of moving objects with unknown motion patterns. In Proceedings of the 2004 ACM SIGMOD International Conference on Management of Data, Paris, France, 13–18 June 2004; pp. 611–622. [Google Scholar]
- Karbassi, A.; Barth, M. Vehicle route prediction and time of arrival estimation techniques for improved transportation system management. In Proceedings of the Intelligent Vehicles Symposium, Columbus, OH, USA, 9–11 June 2003; pp. 511–516. [Google Scholar]
- Guessoum, D.; Miraoui, M.; Tadj, C. Contextual location prediction using spatio-temporal clustering. Int. J. Pervasive Comput. Commun. 2016, 12, 290–309. [Google Scholar] [CrossRef]
- Do, T.M.T.; Gatica-Perez, D. Contextual conditional models for smartphone-based human mobility prediction. In Proceedings of the 2012 ACM Conference on Ubiquitous Computing, Pittsburgh, PA, USA, 5–8 September 2012; pp. 163–172. [Google Scholar]
- Guo, Q.; Karimi, H.A. A novel methodology for prediction of spatial-temporal activities using latent features. Comput. Environ. Urban Syst. 2017, 62, 74–85. [Google Scholar] [CrossRef]
- Rudenko, A.; Palmieri, L.; Herman, M.; Kitani, K.M.; Gavrila, D.M.; Arras, K.O. Human motion trajectory prediction: A survey. Int. J. Robot. Res. 2020, 39, 895–935. [Google Scholar] [CrossRef]

| S No. | Paper | Dataset | Dataset Type | Link | Indoor/Outdoor |
|---|---|---|---|---|---|
| 1 | [9] | American Time Use Survey (ATUS) | Public | https://www.bls.gov/tus/data.htm | Both |
| 2 | [7] | GPS Cabspotting | Public | https://stamen.com/work/cabspotting/ | Both |
| 3 | [36] | GPS Dataset | Propriety | N/A | Outdoor |
| 4 | [25] | Mobile Data Challenge (MDC) Dataset | Propriety | https://www.idiap.ch/dataset/mdc | Outdoor |
| 5 | [12] | Vehicle GPS Dataset | Propriety | N/A | Outdoor |
| 6 | [8] | GPS Dataset | Propriety | N/A | Outdoor |
| 7 | [37] | Vehicle GPS Dataset | Propriety | N/A | Outdoor |
| 8 | [30] | GPS Dataset | Propriety | N/A | Outdoor |
| 9 | [14] | Movement data | Propriety | N/A | Outdoor |
| 10 | [15] | T.Brinkoff | Public | https://iapg.jade-hs.de/personen/brinkhoff/generator/ | Outdoor |
| 11 | [16] | Moving Objects Databases | Propriety | N/A | Outdoor |
| 12 | [38] | GPS Dataset | Propriety | N/A | Outdoor |
| 13 | [33] | Phonetic, GeoLife | Public | http://www.clres.com/phonetic.htmlhttps://www.microsoft.com/en-us/download/details.aspx?id=52367 | Outdoor |
| 14 | [39] | GPS driving data | Propriety | N/A | Outdoor |
| 15 | [17] | MIT Reality Dataset | Public | http://realitycommons.media.mit.edurealitymining.html | Outdoor |
| 16 | [18] | Synthetic data | Propriety | N/A | Outdoor |
| 17 | [40] | TIGER | Public | http://spatialhadoop.cs.umn.edu/datasets.html | Outdoor |
| 18 | [34] | Mobility Data | Propriety | N/A | Both |
| 19 | [41] | Automatic Vehicle Location (AVL) System | Public | http://ieeexplore.ieee.org/document/5174540/?reload=true | Outdoor |
| 20 | [31] | CDR dataset | Propriety | N/A | Both |
| 21 | [35] | Nokia Real life Dataset | Public | https://www.idiap.ch/dataset/mdc | Both |
| 22 | [42] | GPS Sensors Data | Public | N/A | Outdoor |
| 23 | [43] | Smartphones Mobility Data | Propriety | N/A | Both |
| 24 | [32] | Smartphone logs | Propriety | N/A | Both |
| 25 | [6] | Augsburg Indoor Location Tracking Benchmarks | Public | https://www.informatik.uni-augsburg.de/en/chairs/sik/research/finished/ailtbenchmarks/ | Indoor |
| 26 | [19] | Augsburg Indoor Location Tracking Benchmarks | Public | https://www.informatik.uni-augsburg.de/en/chairs/sik/research/finished/ailtbenchmarks/ | Indoor |
| 27 | [44] | Mobility Dataset | Propriety | N/A | Both |
| 28 | [20] | MIT Reality Dataset | Public | http://realitycommons.media.mit.edu/realitymining.html | Both |
| S No. | Year | Algorithms | Author | Accuracy | Dataset | Indoor/Outdoor | Citations |
|---|---|---|---|---|---|---|---|
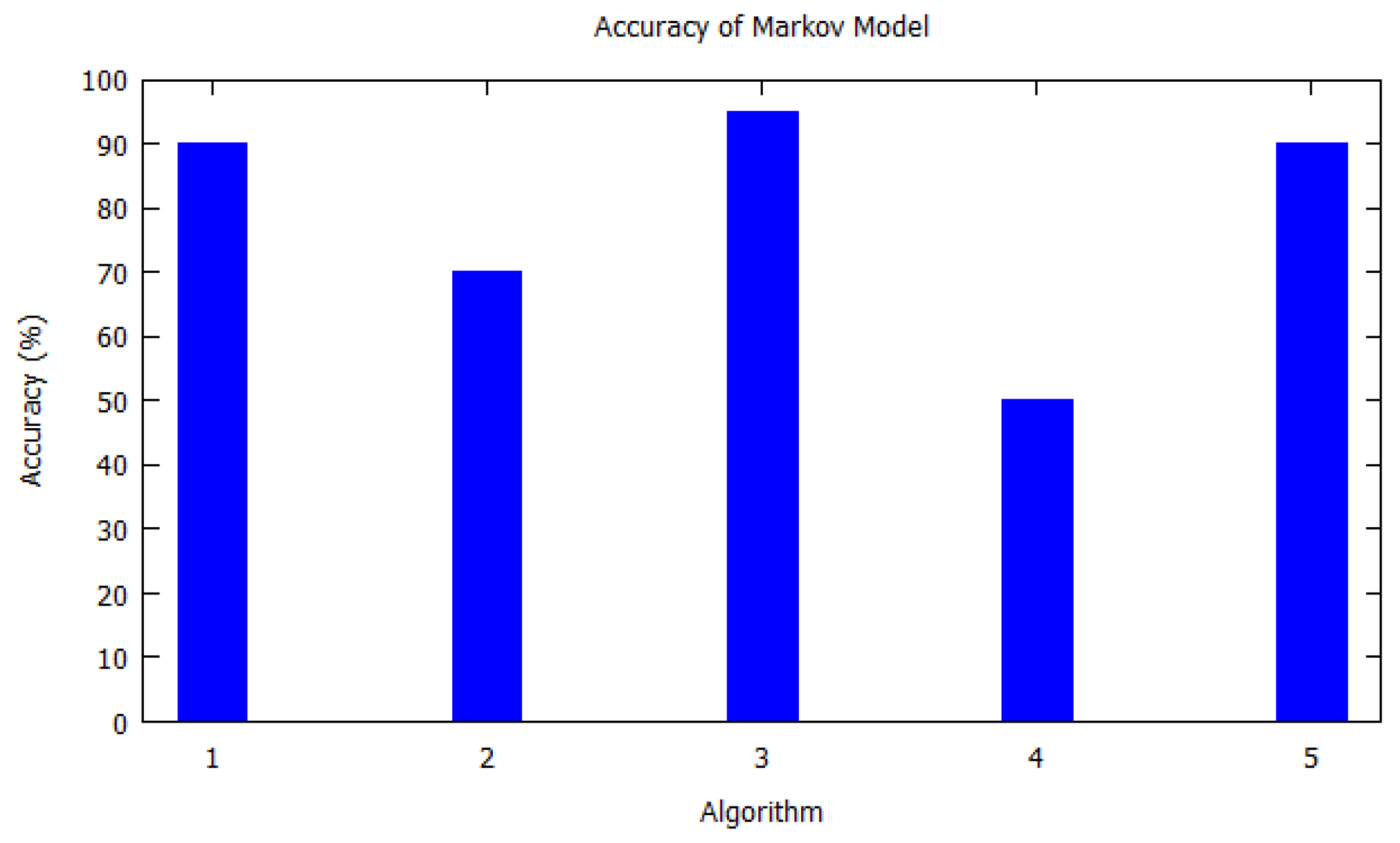
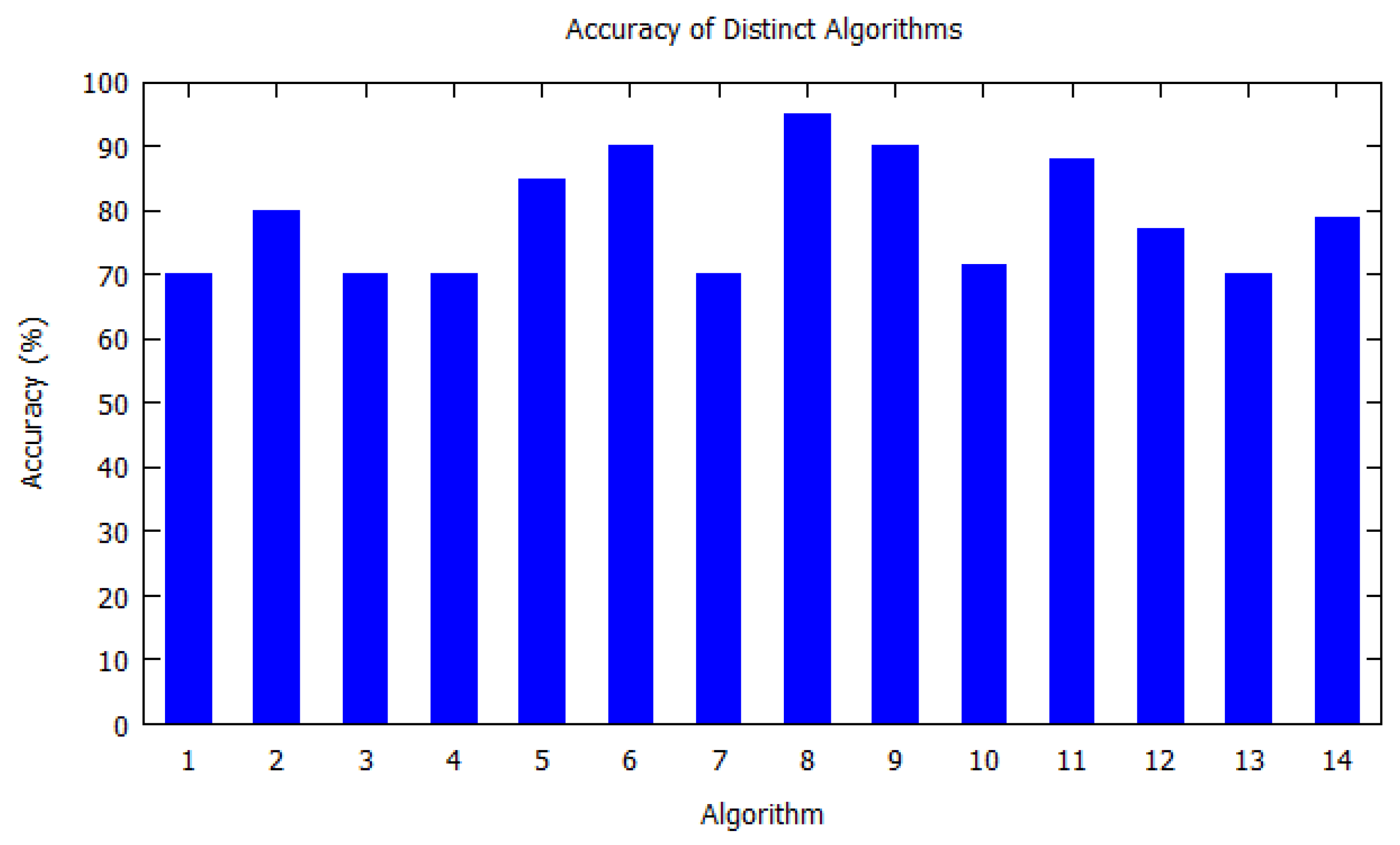
| 1 | 2016 | Markov model | [8] | 90% | GPS data from volunteer drivers in Microsoft Multiperson Location Survey (MSMLS) | Outdoors | 171 |
| 2 | 2003 | Markov model | [30] | 70% | Automatic clusters GPS data taken over an extended period of time | Outdoors | 1383 |
| 3 | 2012 | Markov model | [33] | 95% | Three datasets: Phonetic, Geolife, synthetic dataset | Outdoors | 396 |
| 4 | 2012 | Nine different baseline models | [25] | 50% | Mobile dataset provided by Nokia Mobile Data Challenge which contains 80 users over one year of time | Outdoors | 135 |
| 5 | 2011 | NextPlace, derived from Markov model | [7] | 90% | Four datasets: two GPS-based (CenceMe) and two registration patterns of Wi-Fi access points | Both | 340 |
| S No. | Year | Algorithms | Author | Accuracy | Dataset | Indoor/Outdoor | Citations |
|---|---|---|---|---|---|---|---|
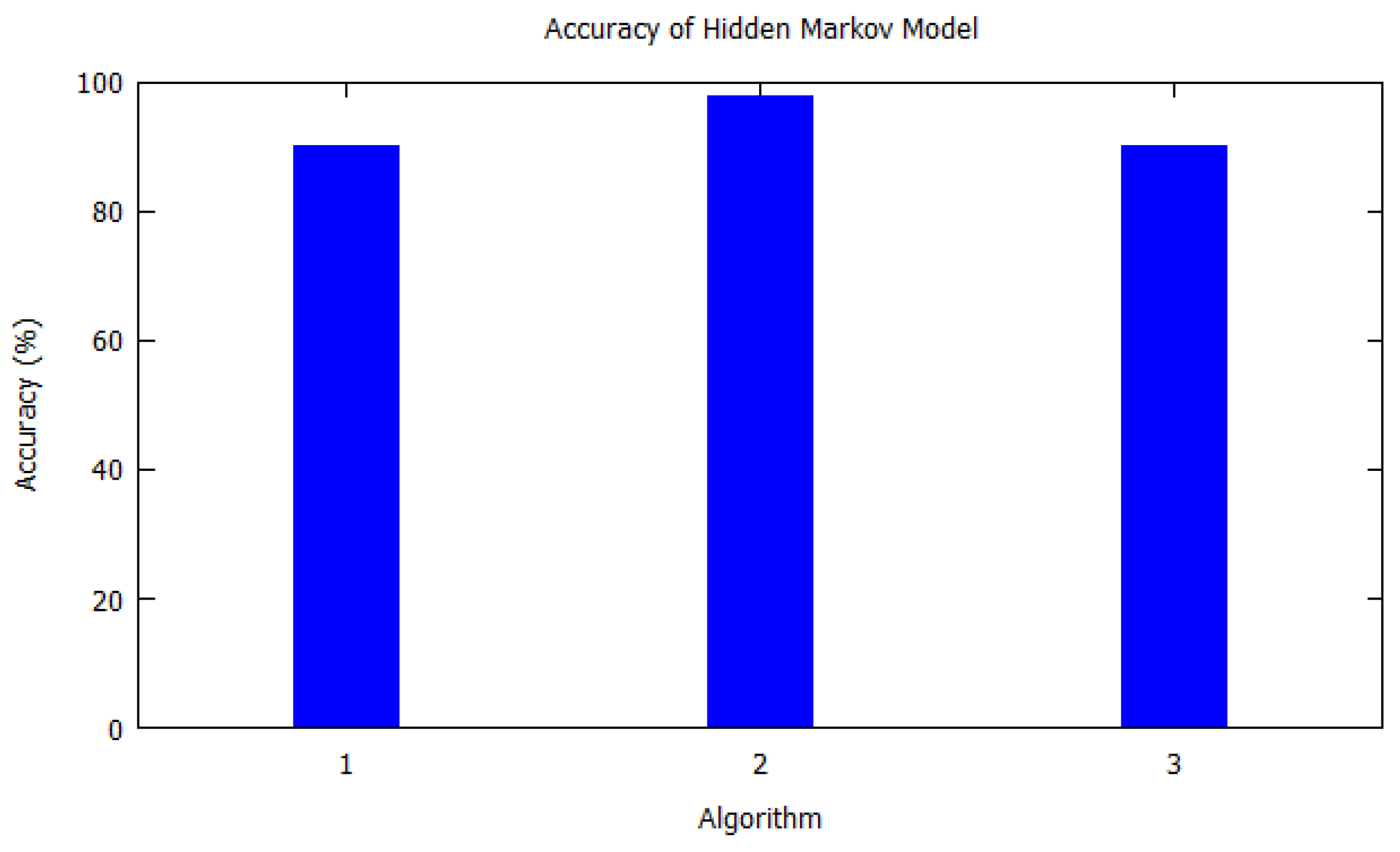
| 1. | 2015 | HMM | [9] | 90% | American Time-Use Survey (ATUS) dataset | Both | 5 |
| 2. | 2006 | HMM | [36] | 98% | Low-cost GPS unit | Outdoor | 227 |
| 3. | 2016 | HMM | [32] | 90% | Real everyday life datasets collected from 10 persons for six months | Both | 50 |
| S No. | Year | Algorithms | Author | Accuracy | Dataset | Indoor/Outdoor | Citations |
|---|---|---|---|---|---|---|---|
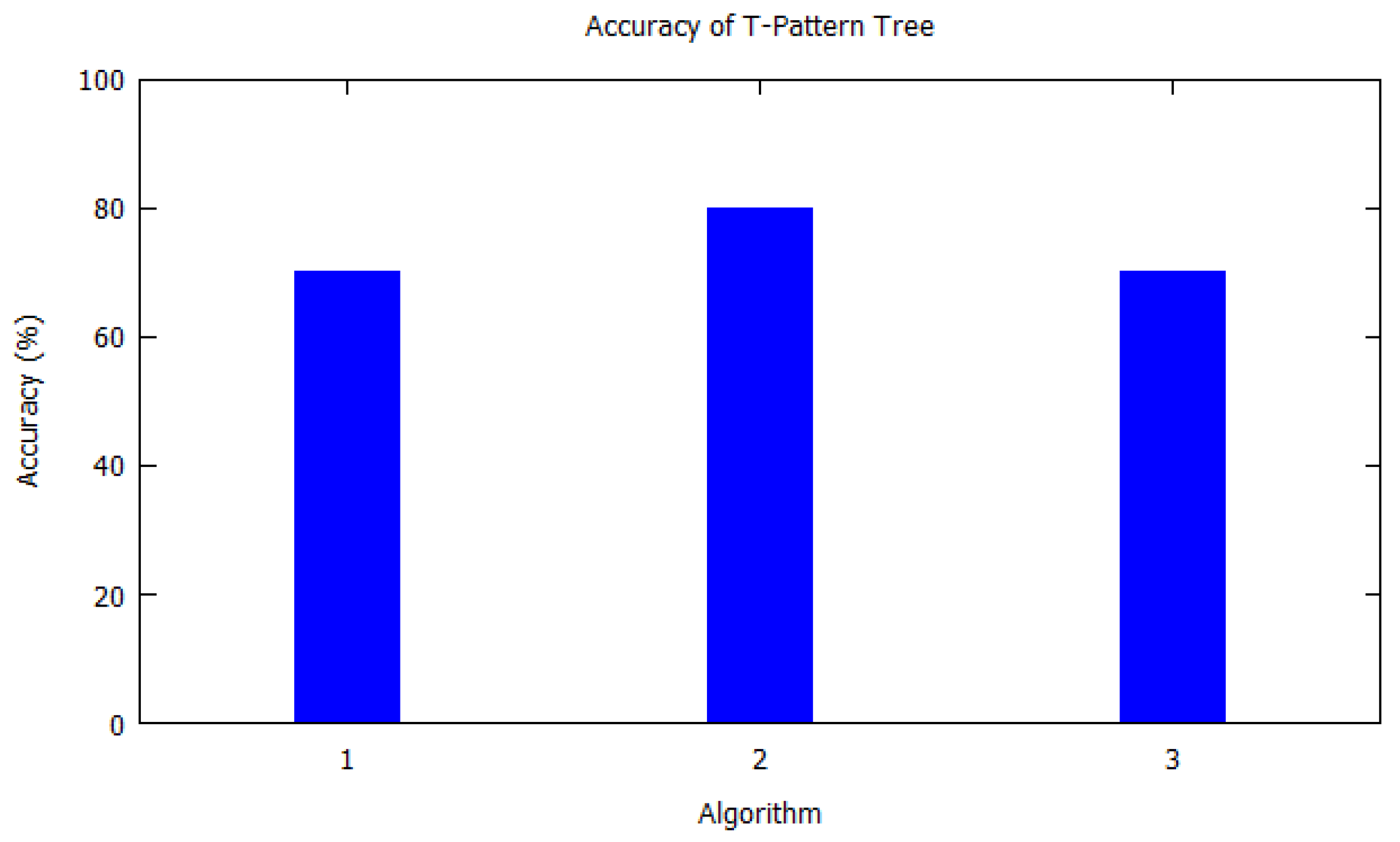
| 1 | 2009 | T-pattern tree | [12] | 70% | Dataset of 17,000 cars equipped with GPS | Outdoors | 617 |
| 2 | 2012 | Decision tree | [35] | 80% | Real-life dataset provided by Nokia | Both | 31 |
| 3 | 2004 | Spatiotemporal prediction tree | [40] | 70% | Real point dataset (Tiger) | Outdoors | 354 |
| S No. | Year | Algorithms | Author | Accuracy | Dataset | Indoor/Outdoor | Citations |
|---|---|---|---|---|---|---|---|
| 1 | 2006 | Predestination | [37] | 70% | Microsoft Multiperson Location Survey (MSMLS) | Outdoors | 586 |
| 2 | 2016 | Enhanced Bayes predictor | [31] | 70% | CDR dataset with more than 3.5 billion calls | Both | 3 |
| 3 | 2005 | Transition matrix (TM) | [34] | 90% | Personal Communication Systems | Both | 394 |
| S No. | Year | Algorithms | Author | Accuracy | Dataset | Indoor/Outdoor | Citations |
|---|---|---|---|---|---|---|---|
| 1 | 2006 | Apriori-Traj Algorithm | [14] | 70% | Network-based generator of moving objects | Outdoors | 96 |
| 2 | 2007 | Traj-Prefix-Span Algorithm | [15] | 80% | Synthetic datasets by T.Brinkhoff | Outdoor | 209 |
| 3 | 2003 | Query-Triggered Revision with Query Relaxation | [16] | 70% | Moving objects database | Outdoor | 58 |
| 4 | 2008 | Hybrid Genetic Algorithm | [38] | 70% | GPS dataset | Outdoors | 363 |
| 5 | 2008 | Route Prediction | [39] | 85% | GPS data from 252 drivers | Outdoor | 278 |
| 6. | 2011 | Seman Predict | [17] | 90% | MIT Reality Dataset | Outdoor | 304 |
| 7. | 2008 | The Hybrid Prediction Model | [18] | 70% | 4 synthetic datasets | Outdoor | 327 |
| 8. | 2003 | Time of Arrival Prediction | [41] | 95% | Automatic vehicle location (AVL) systems | Outdoors | 122 |
| 9. | 2004 | State Predictor Method | [19] | 90% | Augsburg Indoor Location Tracking Benchmarks | Indoors | 15 |
| 10. | 2016 | TLP (Trajectory similarity-based approach for location prediction) | [20] | 71.60% | MIT Reality Mining Dataset | Both | 68 |
| 11. | 2016 | Contextual Location Prediction | [42] | 88% | GPS, GSM and Wi-Fi data | Outdoors | 6 |
| 12. | 2012 | Smartphone-based Mobility Prediction | [43] | 77% | 153 mobile users data | Both | 130 |
| 13. | 2017 | Gaussian Process Regression | [44] | 70% | Large-scale mobility datasets at a city level | Both | 12 |
| 14. | 2005 | Elman Net, MLP, Bayesian Network, State Predictor, Markov Predictor | [6] | 79% | Augsburg Indoor Location Tracking Benchmarks | Indoors | 70 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Daud Kamal, M.; Tahir, A.; Babar Kamal, M.; Moeen, F.; Naeem, M.A. A Survey for the Ranking of Trajectory Prediction Algorithms on Ubiquitous Wireless Sensors. Sensors 2020, 20, 6495. https://doi.org/10.3390/s20226495
Daud Kamal M, Tahir A, Babar Kamal M, Moeen F, Naeem MA. A Survey for the Ranking of Trajectory Prediction Algorithms on Ubiquitous Wireless Sensors. Sensors. 2020; 20(22):6495. https://doi.org/10.3390/s20226495
Chicago/Turabian StyleDaud Kamal, Muhammad, Ali Tahir, Muhammad Babar Kamal, Faisal Moeen, and M. Asif Naeem. 2020. "A Survey for the Ranking of Trajectory Prediction Algorithms on Ubiquitous Wireless Sensors" Sensors 20, no. 22: 6495. https://doi.org/10.3390/s20226495
APA StyleDaud Kamal, M., Tahir, A., Babar Kamal, M., Moeen, F., & Naeem, M. A. (2020). A Survey for the Ranking of Trajectory Prediction Algorithms on Ubiquitous Wireless Sensors. Sensors, 20(22), 6495. https://doi.org/10.3390/s20226495





