Convolutional Autoencoder-Based Flaw Detection for Steel Wire Ropes
Abstract
1. Introduction
2. Wire Rope Image Representation
2.1. Preliminaries of Denoising Autoencoder
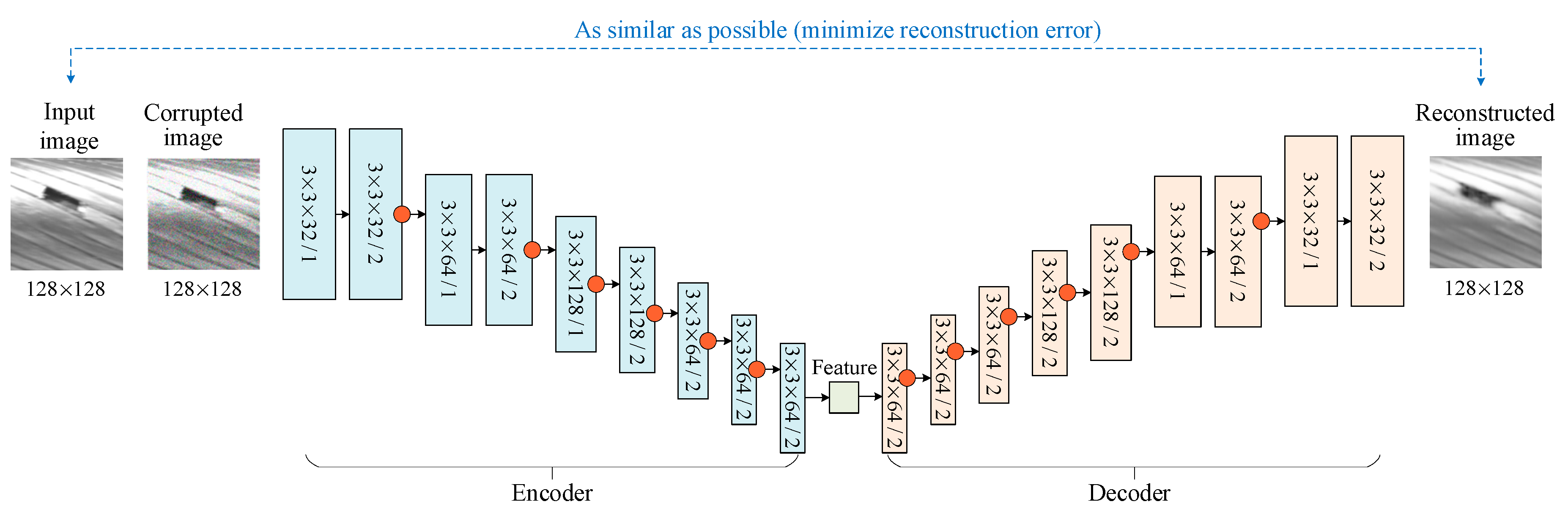
2.2. Convolutional Denoising Autoencoder-Based Feature Extraction
- Convolution layer: The convolution layer employs the learnable filter to slide with a prescribed stride and outputs feature maps. Each element in a feature map is the sum of the products of the filter and the input image (or the previous feature map) with which this filter overlaps. Let the k-th feature map of the l-th layer be , and the corresponding filter be . is calculated as follows:where is the number of channels in layer l − 1; i and j are the row and column indices, respectively; is a bias; and is an activation function. A Leaky ReLU with a negative slope of 0.2 is used in this study. The parameters related to the convolutional operation are the filter size, the stride, and the number of feature maps.
- Deconvolution layer: The deconvolutional layer also employs filters to slide with a prescribed stride. Similar to Equation (2), each element in a feature map is the sum of the products of the filter and the previous feature maps with which this filter overlaps. Different from convolutional layers, ReLU is used as the activation function. In addition, in order to increase the resolution of its input, extra zeros are padded to the input feature maps.
- Instance Normalization: Let be an input tensor containing a batch of T images. Let represent the tkij-th element, where t is the index of the t-th image in the batch, k is the channel index, and i and j are the row and column indices, respectively.
3. Flaw Detection with Deep Learning Features
3.1. Isolation Forest-Based Flaw Detection
| Algorithm 1. Isolation tree construction. |
| Isolation tree: Inputs:X- input data, e - current tree height, l - height limit Output: an iTree 1: if or then 2: return 3: else 4: let be a list of attributes in X 5: randomly select an attribute 6: randomly draw a split value from and value of 7: 8: 9: return 10: 11: 12: 13: end if |
- If the average path length of x is close to zero (), the flaw score will be close to one (), and hence x tends to be a flaw instance.
- If the average path length of x is close to the absolute maximum depth (), the flaw score will be close to zero (), and hence x tends to be a normal instance.
- If the average path length of x is close to the average path length of a random tree given ψ (), the flaw score will be close to 0.5 (). Then, there are no distinct flaws in the data.
3.2. Flaw Score-Based CDAE Finetuning
- Stage I: Offline construction
- Step 1: Get the sample set X under normal operating conditions and normalize it.
- Step 2: Initialize CDAE and pretrain its layers to be greedy to minimize a reconstruction loss between the inputs of the convolutional layer and its corresponding outputs in the deconvolutional layer.
- Step 3: Adjust the parameters of CDAE by minimizing the reconstruction loss between the input image and restored image.
- Step 4: Build the iForest model with CDAE features.
- Step 5: Finetune the parameters of CDAE to increase the gap between flaw scores of normal data and flaw data.
- Step 6: Calculate the flaw score of incoming data.
- Stage II: Online monitoring
- Step 1: Capture a new data and normalize it.
- Step 2: Calculate the CDAE image features of the new data.
- Step 3: Calculate the flaw score by feeding CDAE features to iForest model.
- Step 4: Determine whether the input data is flaw data or normal data.
- Step 5: If it is a flaw data, trigger the flaw alarm; otherwise, capture the next data.
4. Case Study: Application of Hauling Rope Flaw Detection on Mine Cableway
4.1. Description of Hauling Rope Flaw Detection
4.2. Evaluation Metrics
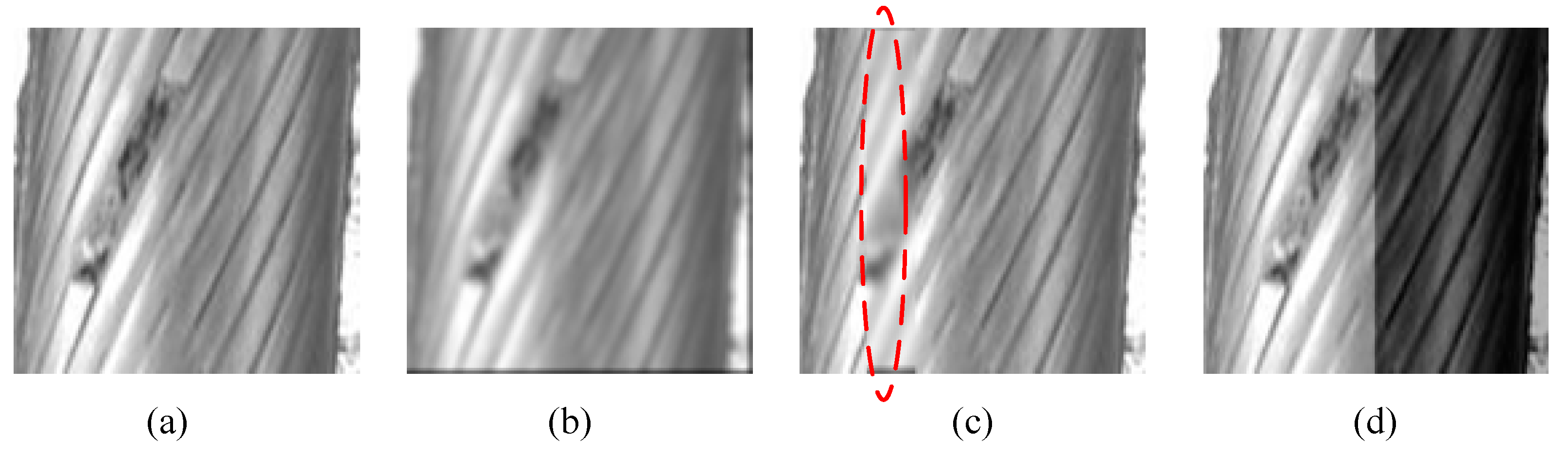
4.3. Experiments and Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Peng, K.; Zhang, K.; You, B.; Dong, J.; Wang, Z. A Quality-Based Nonlinear Fault Diagnosis Framework Focusing on Industrial Multimode Batch Processes. IEEE Trans. Ind. Electron. 2016, 63, 2615–2624. [Google Scholar] [CrossRef]
- Zhang, R.; Tao, H.; Wu, L.; Guan, Y. Transfer Learning with Neural Networks for Bearing Fault Diagnosis in Changing Working Conditions. IEEE Access 2017, 5, 14347–14357. [Google Scholar] [CrossRef]
- Li, C.; Zhang, W.; Peng, G.; Liu, S. Bearing Fault Diagnosis Using Fully-Connected Winner-Take-All Autoencoder. IEEE Access 2017, 6, 6103–6115. [Google Scholar] [CrossRef]
- Zhang, J.; Tang, Z.; Xie, Y.; Ai, M.; Gui, W. Visual perception-based fault diagnosis in froth flotation using statistical approaches. Tsinghua Sci. Technol. 2020, 26, 172–184. [Google Scholar] [CrossRef]
- Zhou, P.; Zhou, G.; He, Z.; Tang, C.; Zhu, Z.; Li, W. A novel texture-based damage detection method for wire ropes. Measurement 2019, 148, 106954. [Google Scholar] [CrossRef]
- Zhou, P.; Zhou, G.; Zhu, Z.; He, Z.; Ding, X.; Tang, C. A Review of Non-Destructive Damage Detection Methods for Steel Wire Ropes. Appl. Sci. 2019, 9, 2771. [Google Scholar] [CrossRef]
- Zhou, P.; Zhou, G.; Li, Y.; He, Z.; Liu, Y. A Hybrid Data-Driven Method for Wire Rope Surface Defect Detection. IEEE Sens. J. 2020, 20, 8297–8306. [Google Scholar] [CrossRef]
- Chang, Y.-W.; Wang, Y.-C.; Liu, T.; Wang, Z.-J. Fault diagnosis of a mine hoist using PCA and SVM techniques. J. China Univ. Min. Technol. 2008, 18, 327–331. [Google Scholar] [CrossRef]
- Zhang, Z.; Jiang, T.; Li, S.; Yang, Y. Automated feature learning for nonlinear process monitoring—An approach using stacked denoising autoencoder and k-nearest neighbor rule. J. Process. Control 2018, 64, 49–61. [Google Scholar] [CrossRef]
- Vallan, A.; Molinari, F. A Vision-Based Technique for Lay Length Measurement of Metallic Wire Ropes. IEEE Trans. Instrum. Meas. 2009, 58, 1756–1762. [Google Scholar] [CrossRef]
- Janssens, O.; Slavkovikj, V.; Vervisch, B.; Stockman, K.; Loccufier, M.; Verstockt, S.; Van De Walle, R.; Van Hoecke, S. Convolutional Neural Network Based Fault Detection for Rotating Machinery. J. Sound Vib. 2016, 377, 331–345. [Google Scholar] [CrossRef]
- Lu, C.; Wang, Z.-Y.; Qin, W.-L.; Ma, J. Fault diagnosis of rotary machinery components using a stacked denoising autoencoder-based health state identification. Signal Process. 2017, 130, 377–388. [Google Scholar] [CrossRef]
- Vincent, P.; Larochelle, H.; Lajoie, I.; Bengio, Y.; Manzagol, P. Stacked Denoising Autoencoders: Learning Useful Representations in a Deep Network with a Local Denoising Criterion. J. Mach. Learn. Res. 2010, 11, 3371–3408. [Google Scholar]
- Zhang, J.; Tang, Z.; Xie, Y.; Ai, M.; Zhang, G.; Gui, W. Data-driven adaptive modeling method for industrial processes and its application in flotation reagent control. ISA Trans. 2020. [Google Scholar] [CrossRef]
- Adetola, V.; DeHaan, D.; Guay, M. Adaptive model predictive control for constrained nonlinear systems. Syst. Control Lett. 2009, 58, 320–326. [Google Scholar] [CrossRef]
- Liu, F.T.; Ting, K.M.; Zhou, Z.-H. Isolation forest. In Proceedings of the IEEE International Conference on Data Mining, Pisa, Italy, 15–19 December 2008; pp. 413–422. [Google Scholar]
- Liu, F.T.; Ting, K.M.; Zhou, Z.-H. Isolation-Based Anomaly Detection. ACM Trans. Knowl. Discov. Data 2012, 6, 1–39. [Google Scholar] [CrossRef]
- Yin, S.; Ding, S.X.; Xie, X.; Luo, H. A Review on Basic Data-Driven Approaches for Industrial Process Monitoring. IEEE Trans. Ind. Electron. 2014, 61, 6418–6428. [Google Scholar] [CrossRef]
- Zhang, J.; Tang, Z.; Zhang, J.; Tan, Z.; Xu, P. Recognition of flotation working conditions through froth image statistical modeling for performance monitoring. Miner. Eng. 2016, 86, 116–129. [Google Scholar] [CrossRef]
- Zhu, R.; Fang, J.-W.; Xu, H.; Xue, J. Progressive Temporal-Spatial-Semantic Analysis of Driving Anomaly Detection and Recounting. Sensors 2019, 19, 5098. [Google Scholar] [CrossRef]
- Stripling, E.; Baesens, B.; Chizi, B.; Broucke, S.V. Isolation-based conditional anomaly detection on mixed-attribute data to uncover workers’ compensation fraud. Decis. Support Syst. 2018, 111, 13–26. [Google Scholar] [CrossRef]
- Kramer, M.A. Nonlinear principal component analysis using autoassociative neural networks. AIChE J. 1991, 37, 233–243. [Google Scholar] [CrossRef]
- Hinton, G.E.; Zemel, R.S. Autoencoders, minimum description length and helmholtz free energy. In Proceedings of the Advances in Neural Information Processing Systems, Denver, CO, USA, 28 November–1 December 1994; pp. 3–10. [Google Scholar]
- Vincent, P.; LaRochelle, H.; Bengio, Y.; Manzagol, P.-A. Extracting and composing robust features with denoising autoencoders. In Proceedings of the International Conference on Machine Learning, Helsinki Finland, 5–9 July 2008; pp. 1096–1103. [Google Scholar]
- Tian, S.; Lin, Y.; Gao, W.; Zhang, H.; Wang, C. A Multi-Scale U-Shaped Convolution Auto-Encoder Based on Pyramid Pooling Module for Object Recognition in Synthetic Aperture Radar Images. Sensors 2020, 20, 1533. [Google Scholar] [CrossRef]
- Ioffe, S.; Szegedy, C. Batch normalization: Accelerating deep network training by reducing internal covariate shift. In Proceedings of the International Conference on Machine Learning, Lille, France, 7–9 July 2015; pp. 448–456. [Google Scholar]
- Simonyan, K.; Zisserman, A. Very deep convolutional networks for large-scale image recognition. In Proceedings of the International Conference on Learning Representations, San Diego, CA, USA, 7–9 May 2015. [Google Scholar]


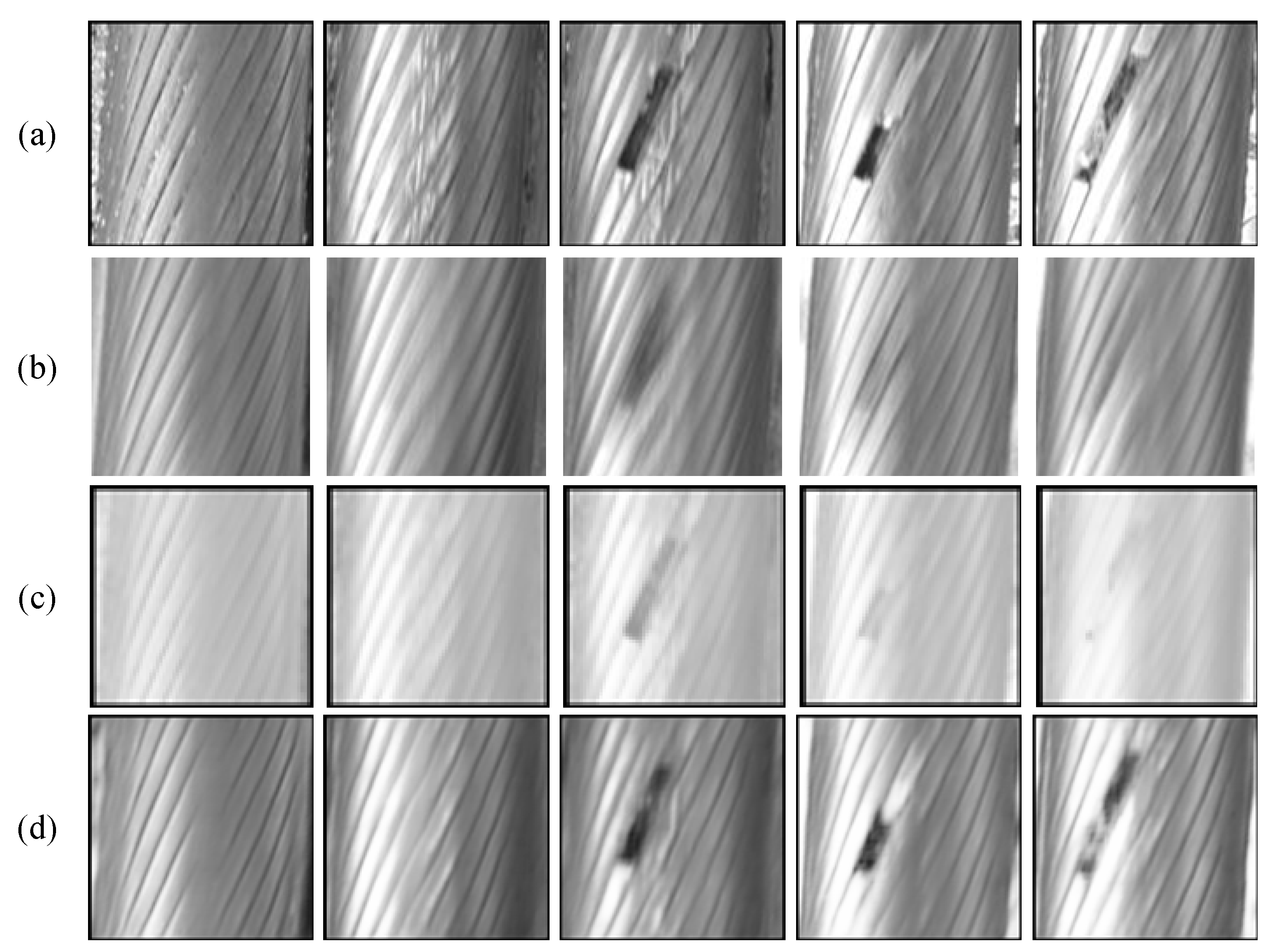
| Method | |||
|---|---|---|---|
| PCA | SAE | Proposed | |
| SNR | 6.5656 | 1.0592 | 8.4465 |
| RMSE | 7.3944 | 14.1201 | 6.0218 |
| Method | Feature | Isolation Model | Metric | |||
|---|---|---|---|---|---|---|
| Accuracy | Precision | Recall | F1-Score | |||
| Algorithm I [8] | PCA | SVM | 0.775 | 0.784 | 0.76 | 0.772 |
| Algorithm II [7] | LBP + GLCM | SVM | 0.805 | 0.814 | 0.79 | 0.802 |
| Algorithm III | SAE | SVM | 0.865 | 0.884 | 0.84 | 0.861 |
| Algorithm IV | CDAE | SVM | 0.885 | 0.905 | 0.86 | 0.882 |
| Algorithm V | CNN | iForest | 0.835 | 0.876 | 0.78 | 0.823 |
| Proposed | CDAE | iForest | 0.93 | 0.948 | 0.91 | 0.929 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, G.; Tang, Z.; Zhang, J.; Gui, W. Convolutional Autoencoder-Based Flaw Detection for Steel Wire Ropes. Sensors 2020, 20, 6612. https://doi.org/10.3390/s20226612
Zhang G, Tang Z, Zhang J, Gui W. Convolutional Autoencoder-Based Flaw Detection for Steel Wire Ropes. Sensors. 2020; 20(22):6612. https://doi.org/10.3390/s20226612
Chicago/Turabian StyleZhang, Guoyong, Zhaohui Tang, Jin Zhang, and Weihua Gui. 2020. "Convolutional Autoencoder-Based Flaw Detection for Steel Wire Ropes" Sensors 20, no. 22: 6612. https://doi.org/10.3390/s20226612
APA StyleZhang, G., Tang, Z., Zhang, J., & Gui, W. (2020). Convolutional Autoencoder-Based Flaw Detection for Steel Wire Ropes. Sensors, 20(22), 6612. https://doi.org/10.3390/s20226612





