1. Introduction
Recently, two evolving technologies, cloud computing and Wireless Sensor Networks (WSNs), have been integrated. Cloud computing is referred to as a pay-per-use model and has servers that are connected to the Internet. It is the core responsibility of the servers to respond to every request of the user at any time [
1,
2]. Furthermore, cloud networks permit access to its offered services via the Internet through any handheld device or fixed device located anywhere in the world. Wireless sensor networks have also performed a great role in the field of information technology by enabling cloud organizations to strengthen their monitoring systems. Wireless sensor networks provide uninterrupted and distributed operations that are important in the field of cloud computing and conventional networks. Both technologies are opposite and cover each other’s drawbacks. At present, much research has already been conducted regarding the integration of wireless sensor networks with cloud computing. Many organizations have also integrated both technologies based on their requirements [
2,
3,
4,
5,
6,
7,
8]. It is paramount to add here that still no information security standard exists with information security controls for wireless sensor networks. Therefore, the majority of organizations apply conventional network information security standards on WSNs. Hence, this study considered the same Information Security Controls (ISCs) for wireless sensor networks that are deployed for information security in cloud computing networks for evaluation and prioritization.
Information security is becoming more important day by day, and it is also the foundation for cloud networks integrated with the wireless sensor networks of an organization. The key aim of information security decision makers is to protect the cloud networks, WSNs, and the assets of the organization through information security risk assessment and the maintenance of the confidentiality, integrity, and availability of resources [
9,
10,
11]. There are many risk assessment frameworks that depend upon qualitative methods and proper guidelines. Therefore, testing of ISCs on the basis of these risk assessment frameworks requires more time and costs. The ultimate goal of the information system in an organization is to improve all operations and simplify the decision process. Information Security Risk Management (ISRM) always played a critical role in the assessment of security risks associated with business operations. Also, it determined the selection of the most relevant information security controls [
12,
13]. In the past, information security experts had a habit of selecting all types of ISCs without considering the risks, attacks, costs, effectiveness, mitigation time, exploitation time, and maintenance time [
14].
The risk assessment process has many steps such as identification of the ISCs to be tested, evaluation to check their efficiency, analysis of the test results, and improvement of the ISC on the basis of the test recommendations [
15]. Several types of risk management methods and techniques have been developed to solve these issues by applying qualitative and quantitative modeling. Quantitative techniques that depend upon decision-making criteria are still lacking [
16].
In the real world, every innovation has many obstacles. The challenge is to make the best decision among different alternatives and controls [
17]. These alternatives are sometimes clashing in nature and increase the complexity of decision making [
18]. To overcome all the limitations and choose a definitive solution to the problem is a really difficult task [
19,
20]. The difficulty in making decisions arises when the obstacles are not natural or are ambiguous, uncertain, and confusing. The proposed methods of this study can be used to solve actual problems that organizations face in real time with a series of restrictions that are classified into a Multi-Criteria Decision Making (MCDM) method [
21,
22].
The process of evaluating and selecting the most efficient information security controls for an integrated WSN–cloud network from existing information security standards can be seen as tricky and challenging. Baseline manuals provide very little guidance on how to select the best set of ISCs to provide required security against threats. Obviously, this set of ISCs should meet the security and privacy requirements of organizations. The selection of ISCs must be driven according to organizational requirements and the linked security needs. The information security policy of the organization must be composed of security requirements and a list of controls that have the capability to provide the required privacy and security protection. If a set of ISCs has been properly evaluated and testified to cater to an organization’s needs, then the trust needed for WSN–cloud networks can be created. Furthermore, during risk management processes, an organization needs to ensure that the best set of ISCs is identified, installed, and operated accurately.
Under many contradictory obstacles, the decisions made by humans are not reliable, because the human brain is only capable of evaluating and acting on a limited amount of information at any given moment [
17]. To help decision makers solve actual problems for organizations, Thomas Sati (1980) [
23] introduced the Analytical Hierarchy Process (AHP). This approach is based on the comparison of pairs between an alternative and a best possible alternative. The strength of the AHP lies in its neutral and logical classification and its flexibility to integrate various functions such as the deployment of quality functions, linear programming, and fuzzy. The benefit of the AHP methodology in conjunction with fuzzy logic is called fuzzy AHP which is the most important method of the multi-criteria decision-making methodology for various types of applications [
24]. The fuzzy AHP approach helps to make decisions with various inclinations, fuzziness, and vulnerability. Research has shown the fuzzy AHP philosophy and furthered the supreme utilization of it [
25]. It is practical for dealing with uncertainty, complexity, and decision making for complex issues of a controversial nature [
26].
The structure of the article is as follows:
Section 2 is related to the integration of wireless sensor networks with cloud computing.
Section 3 reviews previous approaches for the selection of ISCs in organizations.
Section 4 presents the AHP, and
Section 5 discusses fuzzy AHP along with the model.
Section 6 covers the fuzzy AHP methodology,
Section 7 elaborates on the application of fuzzy AHP for the selection of information security controls,
Section 8 regards sensitivity analysis, and
Section 9 compares the fuzzy AHP technique with other methodologies. Finally,
Section 10 summarizes and concludes the paper with a suggestion for further research.
2. Integration of Wireless Sensor Networks with Cloud Computing
The goal of WSNs is to sense the environment in which it is installed and send data to the user. As the number of internet and cloud computing users is growing rapidly, there is a dire need to provide WSN services to this fast growing community [
27].
Cloud computing is an adaptable, incredible, and cost-effective framework that provides real-time information to its clients however and whenever it is required, at varying levels of desired quality. The cloud is composed of software, infrastructure, platforms, storage, systems, and interfaces that empower the conveyance of computing services. Likewise, it is very easy to transfer the information received from wireless sensor nodes to the internet/cloud networks through Simple Object Access Protocol (SOAP), emails, short message service, and blogs, etc. [
28]. By associating, assessing, and connecting these sensor systems, information can be concluded in real time, patterns can be anticipated, and unsafe circumstances can be avoided.
Wireless sensor networks (WSN) are a trendy domain of research due to the fact of their easy accessibility via the internet, any place and time. In WSNs, the sensors generate a large amount of data as input and appropriate action against the collected input is taken. Wireless sensor networks have generally been installed in various applications extending from smart industry, smart health, smart cities, smart environments, agriculture, habitat, indoor living, and greenhouses to climate and forest monitoring [
29]. In all these fields, the sensors generate data in huge amounts that need some protocols to be collected, stored, and processed. The design of a WSN is structured in a specially appointed manner and is not adaptable to adjustment to different applications or situations, while the central issue is the equivalent remote observing utilizing sensor systems [
30]. During the literature review, it was revealed that many researchers examined the way to connect the wireless sensor network to a cloud computing network [
1,
2,
5,
31,
32,
33,
34,
35]. In a WSN, the major issue with the deployment of sensors is the data storage, because sensors have temporary memory to store data and then send it to an end destination that can be a data repository [
36]. The combination of a WSN with a cloud facilitates the network to store data on the cloud [
37].
After an in-depth study of the literature, the authors of References [
1,
8,
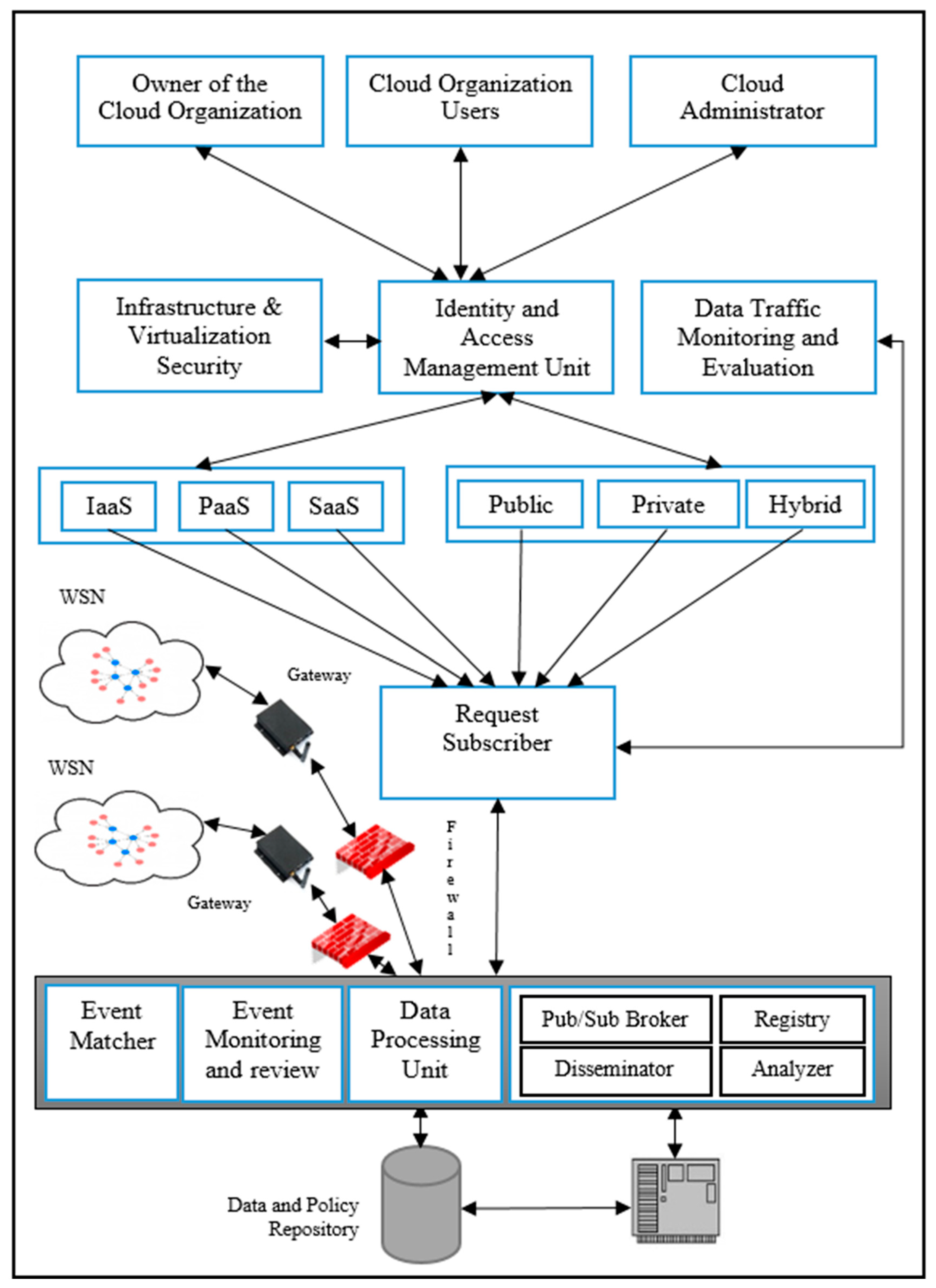
38] integrated a wireless sensor network with a cloud network. Their proposed framework has been updated, and the authors of this present article proposed their own WSN–cloud framework which is presented in
Figure 1.
The goals of the sensor–cloud integration framework are to assist the transfer of data/information received from a wireless sensor network to the cloud so that the events triggered by the sensors can be properly stored on cloud networks and to fully utilize the received data. The proposed integration of WSN–cloud framework components are an event matcher, data processing unit, event monitoring, review, publisher/subscriber broker, disseminator, registry, analyzer, request subscriber, identity and access management unit, policy repository, infrastructure and virtualization security, and data traffic monitoring and evaluation. In the first instance, all the users of the cloud will be connected to the sensor–cloud framework through a secured Identity and Access Management Unit (IAMU), and the users will be given access to the sensor–cloud network on the basis of the access policy stored in the IAMU against each account. After the successful granting permission, the users will be able to put their data access request; all such types of requests will be forwarded to the request subscriber component which will be further forwarded for subscription to the publisher and subscriber broker.
The proposed integrated WSN–cloud framework components are event matcher, data processing unit, event monitoring, review, publisher/subscriber broker, disseminator, registry, analyzer, request subscriber, identity and access management unit, policy repository, infrastructure and virtualization security, and data traffic monitoring and evaluation.
2.1. Identity and Access Management Unit (IAMU)
In the first instance, all the users of the cloud will connect to the sensor–cloud framework through a secured Identity and Access Management Unit (IAMU), and the users will give access to the sensor–cloud network on the basis of the access policy stored in the IAMU against each account.
Figure 2 shows the overall IAMU system consisting of two major components that are the access control decision unit and the access control implementation unit. Many authors have already used the Kerberos authentication mechanism by introducing the Edge Node (EN) which uses the Diffie–Hellman (DH) public key algorithm. The DH is used to securely exchange cryptographic keys in the public network.
The complete IAMU consists of Diffie–Hellman, Role-Based Access Control (RBAC), repository, service server, ticket granting server, authentication server, and Extensible Markup Language (XML). The IAMU has two primary purposes: the first is to ensure strong authentication between the user and cloud, and the second is to grant access to the cloud resources to the legitimate users using policy-based access [
1].
The users will initiate their login/registration communication with the cloud through the Access Control Implementation Unit (ACIU) which will facilitate the user in the authentication process and access control over the cloud resources.
2.1.1. Access Control Implementation Unit (ACIU)
The ACIU is composed of edge node, authentication server, ticket granting server, and service server. All the user requests will be directly sent to edge node and then the authentication server. The Kerberos server will help the user to gain authentication via the authentication server.
2.1.2. Access Control Decision Unit (ACDU)
The access control decision unit is a very important unit of IAMU which primarily has RBAC. It enables users to obtain access to only those resources that are required for them to perform their job and also restrict users’ access to resources which do not pertain to them. The role of the user is already defined in the RBAC through the Java language, and the policies are defined in Extensible Markup Language (XML). The ACDU communicates with the ACIU through the service server [
39].
2.2. Publisher/Subscriber Broker
After successfully being granting permission, users will be able to process their data access request, and all such types of requests will be forwarded to the request subscriber component which will further be forwarded for subscription to the publisher and subscriber broker. The framework is given in
Figure 1. The publisher/subscriber broker is an independent unit and is not directly linked to the gateway. All the collected data from sensors are directly stored in the repository for further processing by the Data Processing Unit (DPU). The stored sensor data are properly formatted by the DPU, and only relevant data are extracted and then sent back to the repository. The index of each datum stored in the repository is assigned to the publisher/subscriber broker. The subscription requests of the user will be fulfilled through the request subscriber (RS) and event matcher. The goal of the event matcher is to handle mapping related issues between the RS and published data. After successful mapping, the publisher/subscriber broker will initiate the fetching process of data from the data repository, and the user may access the data through a cloud interface.
2.3. Data Processing Unit (DPU)
The wireless sensor nodes generate data and send the data to the DPU through the General Packet Radio Service (GPRS) Gateway after filtration/security checking through the security firewall. The DPU processes the received data into a storage format and adds the data into the data and policy repository. The event monitoring and review component is responsible for continuously review and monitor of the quality of the received data and, in the case of any changes in the policy, review of the policy that is stored in the data and policy repository [
38]. Whenever a new event is published by the publisher broker, the event matcher evaluates the event and starts the event matching process. When an event match becomes available to the user, further processing of the matched event is carried out if needed [
1]. The function of the registry component is to store end-user subscriptions of the infrastructure, application, and platform service as well as the sensor data type. It also provides subscription details along with details of the applications to the disseminator component for the delivery of the event [
34]. The publisher/subscriber component is mainly responsible for monitoring all events triggered through the WSN, processing each triggered event, and sending the events to the registered users through the cloud. The functioning of the analyzer component starts when the data or events are received by the publisher and subscriber broker. It determines to which cloud service model and deployment model the event belongs. It also provides information on whether the events are periodic or emergent. Thereafter, the analyzed events are passed to the disseminator to send appropriate events to the concerned users through the cloud service [
34].
Data traffic monitoring and evaluation component of the framework keeps track of the utilization of the resources of cloud and request subscriber so that adequate resources can be distributed to a certain user. The function of the infrastructure and virtualization security component is to maintain privacy and security between the host operating system and guest operating systems as well as between wireless sensor network and cloud.
2.4. Request Subscriber
The purpose of the requesting subscriber is to deal with the requests of users. The RS module verifies the request of users regarding access to sensor data stored in the data repository. All service requests of the users are passed to the request subscriber module which after verification of the request, sends it to the publisher/subscriber for further mapping of the index data.
2.5. Flow of Data Among Framework Components
The sequence diagram of the proposed framework is presented in
Figure 3. It shows the interaction among the main relevant components for the proposed framework.
The steps of the sequence diagram are given as:
A new user arrives in the system and attempts to communicate with the cloud network of the organization. Its requests will go to the cloud threat wherein the edge node will first deal with the request. It is pertinent to add here that both the user and edge node will generate a common secret key by using the DF algorithm. The user sends its details (i.e., registration, username, and password) duly encrypted through a common secret key. The user’s registration details will be stored in the authentication server that is part of the ACIU.
Acknowledgment regarding successful registration of the user based upon information stored in the authentication server of ACIU will be sent to the edge node and then sent to the user. Thereafter, the user will generate a public/private key pair for the cloud. The ACIU decrypts the message and saves the public key in the authentication server against username. The encrypted message received from the cloud can be decrypted using the cloud’s public key.
The existing user will send a login request to the cloud thread wherein the edge node will deal with it. The user will provide encrypted usernames and passwords after establishing a connection through the Diffie–Hellman algorithm. User details will be going to the authentication server of the ACIU. User details will go to the authentication server of the ACIU.
Successful authentication Acknowledgement is sent to the user. Thereafter, the complete encryption process will be completed, as given above, to secure the communication between the user and the cloud.
After a successful login with the cloud network, the user will initiate a service request to the cloud network.
Thereafter, the cloud network will find the appropriate service type.
The cloud network will generate a corresponding request message.
After finding a suitable service type and generating a request message, the request of the user will be sent to the request subscriber.
The requesting subscriber will combine the request and create a new subscription on the basis of information received from the cloud network.
The subscription request will be sent to the publisher/subscriber broker.
The WSN gateway continuously sends sensor data to the data repository and the DPU quickly obtains sensor data for processing and then again stores the data in the data repository. The entire process is not time dependent in the proposed framework and can occur at any time. Therefore, a loop sign is used in the sequence diagram. The DPU will uninterruptedly send the prepared index of the data to the publisher/subscriber broker.
The index of the data will be stored in the registry of the publisher/subscriber broker.
Thereafter, the publisher and subscriber broker will initiate the event matcher to trace the same published data for received subscription requests.
If the publisher/subscriber broker finds relevant subscriptions related to the request, then the process of retrieving data from the DPU will be initiated.
The retrieved data from the DPU will be forwarded to the user through the request subscriber and the cloud network.
It is an entirely new idea to connect wireless sensor networks with cloud computing and, still, it is an area of research for organizations. It is impossible for organizations to connect each node of a WSN to the internet/cloud network.
The purpose of integrating a WSN with cloud is primarily to provide a storage service, recovery mechanism, and backup service to the sensed data/information. This can be achieved by sending all the sensed data and events to the cloud network through the internet. In this way, the user can access the sensed data from anywhere in the world, and the cloud network will also provide processing services to the sensed data for rapid and distributed processing. The integration of a WSN with a cloud also enables short-range hop networks to communicate with long-range networks and also enable WSNs to distribute their sensed data across the world.
In the following, the authors of this article propose the architecture of a sensor–cloud framework and explain why we integrated a WSN with a cloud network, the purpose of the integration, and how the sensor–cloud framework works.
3. Previous Approaches in the Selection of ISCs in Organizations
Based on Reference [
40], previously, the process of identifying the most effective information security controls in an organizations has been a challenge, and many attempts have been made to formulate effective methods to meet this challenge. Risk Analysis and Management (RAM) is one such example. Risk analysis and management has widely been used as an effective approach to identify ISCs. Risk analysis and management conducts business analyses and risk assessments which help to identify information security requirements. Subsequently, RAM enlists the information security requirements and the proposed ISCs that can be implemented to mitigate the specific risks after conducting risk analysis and evaluation. However, RAM does not take specific constraints of the organization into consideration while selecting ISCs [
41].
For example, when using RAM, organizations can identify 60 information security risks. However, it may be possible that management is unable to select and implement all the ISCs needed to address the identified risks due to the cost and budget constraints. Furthermore, there may not have enough resources within the organization to implement the ISCs. In this case, management must list all identified risks and determine the importance and severity level of each individual risk to the organization, taking into account cost/benefit analyses. The management of the organization must then explore new ways to determine/measure the relevance of these ISCs, taking into account the limitations.
Basic manuals or best practices are other approaches widely used by organizations to introduce minimum security controls in organizations. In Reference [
42], best practice frameworks assist organizations in identifying appropriate ISCs. Furthermore, Reference [
43] mentioned other best practice frameworks that contributed to the identification and selection of ISCs.
The procedure of picking the most efficient ISCs from available best practice frameworks can be a challenge. According to Reference [
41], best practice frameworks do not guide users toward the selection of effective ISCs. In addition, the available frameworks also do not consider the specific constraints of the organization such as cost, budget, effectiveness, suitability, scheduling, and resource limits. Other formal methods used in the past, such as ad hoc or randomized approaches, can lead to the inclusion of unnecessary controls and/or the exclusion of necessary controls.
The random approach is a less formalized method. The use of this method leads to the inclusion of unnecessary controls and the non-inclusion of necessary controls. Regarding the importance of selecting effective controls for information security, most organizations choose the most recent approaches and structures. For example, Reference [
44] used the control information security checks. However, they used hypothetical variables to show a numerical example in their case study. Therefore, there is a lack of these information security checks.
The identification and selection of ISCs in light of the above clearly states that organizations are not able to protect the Confidentiality, Integrity and availability of their information [
42]. In order to increase the effectiveness of the selection process and prioritization for ISCs, new methods are required to be developed that save time by considering the main factors (e.g., cost, budget, effeteness, and suitability) which undoubtedly influence the selection of ISCs.
In the literature review, it was clear that ISC selection is mainly based on costs, effectiveness, suitability, budget, and resource availability. In other words, ISC in organizations are selected by the administration when the benefits of its implementation are within budgetary limitation. Equally important, cost and budget can influence the possible selection of ISCs.
The implementation of ISCs can require specific methods, time, and costs. Finally, staff availability often determines whether ISCs can be selected or not. The effective implementation of the security in an organization may require the identification and adoption of the most appropriate and effective ISCs, taking into account the problems presented above.
The problems of evaluating and selecting information security controls require attention in practice. To address this problem, a number of approaches have been proposed by researchers using Multi Criteria Decision Making which deals with the selection of the best solutions amongst different alternatives/substitutes according to their attributes and objects. Multi-Objective Optimization by Ratio Analysis (MOORA) was introduced in Reference [
45]. The Multi Criteria Decision Making (MCDM) presents different techniques such as the analytical hierarchy process (AHP). The AHP, developed in Reference [
46], deals with how to define the relative significance of a set of activities. The AHP method consists of three principles: (1) developing the structure of the proposed model; (2) conducting a comparative analysis of the alternatives and criteria; and (3) preparing a synthesis of the priorities.
The Decision-Making Trial and Evaluation Laboratory (DEMATEL) method was developed to find the weights of each inter-dependence value against each criterion. Briefly speaking, it was developed in the years 1972 and 1976, and the Science and Human Affairs Program funded this project. The DEMATEL method is basically based upon the causes and effects of the criteria and converts causes and effects criteria into an intelligible model [
47].
The Analytic Network Process (ANP) is a general form of AHP, and it is used in MCDM. It is a multi-criteria theory used to obtain relative priority scales of numbers from discrete decisions. The ANP does not make an assumption about the higher and lower levels of elements [
48].
A Technique for Order Preference by Similarity to Ideal Solution (TOPSIS) was established in Reference [
49]. The basic idea of this technique is that the nominated alternative must have the shortest distance from the ideal positive and negative solutions [
50]. The TOPSIS method supposes that each criterion inclines towards a monotonically increasing or decreasing utility [
51]. Therefore, it is the easiest way to describe ideal positive and negative solutions. The Euclidean distance approach is used to proximate the ideal solution. Therefore, the series of comparisons in light of relative distances are made to order the preference amongst the alternatives [
50].
The Preference Ranking Organization Method for the Enrichment of Evaluations (PROMETHEE) is an outranking method and is used for different kinds of ISCs. It can be simply modified for use as a group judgment aid, for example, by introducing diverse weighting schemes [
52]. Thus, PROMETHEE is clear and easier to use, even by decision makers (DMs) who are not familiar with Multi Attribute Decision Making (MADM).
Vlse kriterijumska optimizacija I kompromisno resenje (VIKOR) is a multi-criteria technique that generates optimized solutions, and it has preference over other MCDM approaches. The VIKOR was developed by Opricovic [
53] in 1998, and in 2002 Opricovic and Tzeng [
54] introduced criteria to deal with complex systems [
55]. The VIKOR governs the ranking list, its solution, and intervals of weight stability. Similar to the other methods, this method has also been used to rank and select the best candidate amongst alternatives in light of conflicting criteria. The VIKOR introduced a ranking index technique for multi-criteria to measure the closeness of the ideal solution [
54,
55].
During the literature review, different methods were found to compare and prioritize the alternatives to select the best one; however, in this dissertation, different methodologies can be used such as fuzzy TOPSIS [
56,
57], fuzzy AHP [
56], fuzzy ANP [
58], and fuzzy VIKOR [
59]. There are a number of studies that discuss ISC selection and mathematical methods that have been used to rank the ISCs as shown in
Table 1. After comparing these techniques, fuzzy AHP was chosen as the most convenient, best, and easy to use method, as it facilitates prioritizing the alternatives based on the rating of the individual decision makers, supports a hierarchy process as well as a huge number of criteria, and deals with ambiguities.
Furthermore, to acquire and manage the human assessment of ambiguity, vagueness, and subjectivity, the linguistic variables in fuzzy sets were integrated into the assessment and selection process of the ISCs. This widespread opted hybrid MCDM technique was applied to evaluate and select the information security control. The AHP approach was used which was based on the weights obtained with the entropy method in a fuzzy decision-making environment. The linguistic variables were converted into fuzzy values; to make the criteria more important, fuzzy values were utilized to calculate fuzzy entropy weights. To obtain a comprehensive performance evaluation of the ISCs problem, these weights were used in the fuzzy AHP approach. Thereafter, the total score of each control against each criterion was obtained for the selection of best control and to make a decision. The proposed method is more effective and easier to apply and provides the best decision-making quality.
4. Analytical Hierarchy Process (AHP)
Analytical hierarchy process is a technique to solve the complex, unstructured problems by breaking them down into small components, reorganizing these components into hierarchic positioning, synthesizing the final judgment to evaluate which alternative have the highest-ranking, and also to influence the output of the situation. It utilizes a hierarchical structure to extract, deteriorate, compose, and control the complexity of the decision including numerous attributes, and it utilizes judgment or the decision maker’s opinion to gauge the relative worth or commitment of these characteristics.
The AHP was developed by Thomas Saaty [
23], and it is the most efficient method to make very complicated decisions, and it also helps the decision maker to decide the priorities and make the best decision among the alternatives [
17]. In AHP, pairwise comparisons are developed to reduce complicated decisions, and synthetization of the results are also taken. Furthermore, the AHP also assists in taking subjective and objective types of the decision. In the AHP model, weights are given to the decision makers. During the decision-making process, the alternatives are compared with each other by assigning that weight. The AHP is currently used in many different areas such as computer programming, information investigation, and fuzzy set theory [
90].
Furthermore, the AHP has a very helpful methodology to examine the reliability of evaluators/decision makers and, therefore, the biases of decision makers can be reduced through this process [
91].
Through the AHP, many assessment criteria and alternatives are discussed, and this helps in the selection of the best choice [
17,
92,
93].
Figure 4 represents a hierarchy structure for the evaluation of ISCs utilizing the AHP method.
Figure 4 explains the processes of the AHP and all main criteria in a graphical format. In the AHP, the first process is to define the goals of the model which is the evaluation and best selection of the information security controls. After defining the goals, it is required to formulate the criteria of the evaluation. Here, in
Figure 4, we defined six criteria in consultation with decision makers/experts. Every criterion was also assigned a certain weight which indicates its importance. The proposed criteria are applied to the alternatives to select the best candidate among all alternatives and also to prioritize the alternatives.
Figure 4 shows five information security controls as alternatives. The best information security control and ranking of the information security controls must be done according to the six criteria.
The AHP gives weight to each criterion. Extra importance is given to the object that has a higher weight. Next, for a fixed paradigm, the AHP doles out a score to every alternative as indicated by the evaluator’s pairwise examinations of the choices dependent on that rule [
13]. The better performance of the criteria is examined on the basis of the higher score with respect to each criterion. At last, the AHP combines the weights and the scores of the alternatives; in this manner, the score of each alternative is evaluated out of a total score it obtained against each criterion [
25].
The primary goal of the AHP is to select an alternative that best satisfies a given set of criteria out of a set of alternatives or to determine the weights of criteria in any application. The AHP scales the weights of attributes at each level of the hierarchy with respect to a goal using the decision maker’s (experts’) experience and knowledge in a matrix of pairwise comparison of attributes. The usual application of AHP is to select the best alternative from a discrete set of alternatives.
The main objective of the AHP is to choose an alternative that best fulfills a given arrangement of criteria out of many alternatives or to decide the weight of the criteria. The second objective of the AHP is to weights of sub-criteria at each degree of the hierarchy order regarding an objective utilizing the specialists’ experience. The AHP is the best methodology to select the best alternative from a set of different types of alternatives.
6. Fuzzy AHP Methodology
In the FAHP, alternatives are evaluated by using triangular fuzzy (TFN) and for the prioritization of alternatives and then to cope with the problems of the AHP. It was extended and a synthetic pairwise evaluation function was introduced [
98]. The triangular fuzzy number denoted with M is shown in
Figure 5.
Most of the researchers and academicians represented triangular fuzzy numbers by
M =
(l, m, u). The
l is used to express the smallest possible value,
m is used to express the closest value, and
u is accordingly used to express the largest possible value. The membership function is described as:
There are many operations that can be performed on triangular fuzzy numbers, but the main operations that have been used in this study are illustrated below. Let us assume two triangular fuzzy numbers
M1 =
(l1, m1, u1) and
M2 =
(l2, m2, u2) then:
Suppose
is an object set and the goal setting is supposed as
. Next, according to Chang’s [
19] method, each object is taken from the list of the objects and an extended analysis of each goal is performed on each object. After the implementation of the extent analysis, the m extent analysis value for each object can be obtained using the following triangular fuzzy numbers:
We may represent the fuzzy synthetic extent value in respect of
ith object as:
To get
, a fuzzy addition operation is required to be performed on
m above the extent analysis values for a specific matrix using Equation (6):
Furthermore, in order to get the
, first, the fuzzy addition operation must be performed by considering Equation (7), and then the inverse of the vector on the basis of Equation (8) must be taken.
After the determination of the synthetic extent, the next step is to determine the degree of possibility in the case of
. It can be calculated as follows:
The ordinate of the highest intersection point is denoted as d and is lying between
and
.
The term is the height of fuzzy numbers on the intersection of and .
Figure 6 shows that the intersection of both triangular fuzzy numbers is denoted as (d) as ordinate, and it is the highest intersection point
D between two fuzzy membership functions.
To compute the smallest degree of possibility
, all fuzzy values
are required to be compared using the following equation:
Let us suppose,
; for
, the weights can be calculated under:
The next step is to normalize the vector,
. The final priority weights vector of each alternative are calculated as follows:
The consistency index (CI) is the next step, and the following equation is used to calculate it.
Finally, the consistency ratio (CR) is calculated as follows:
Here RI means Random Index table which is available on the Internet.
The specific steps of the FAHP and the step-by-step procedure adopted in this study to calculate the weights of the criteria are shown in
Figure 7.
7. Application of the Fuzzy AHP for the Selection of Information Security Controls
An organization having a WSN–cloud-integrated network needs evaluation and prioritization of the information security controls to effectively implement security and privacy. In this situation with inadequate resources, the organization wants to use as much effort as possible to evaluate ISCs which are very important for risk management. The best selection of information security controls is a serious and very important task for organizations. The objective of this section is to choose the best ISCs among alternatives. The organization desires to take all essential possible criteria which are vital in the process of security control selection. For ISC selection and evaluation, there are seven main criteria determined by the decision makers’ team: implementation time (C1), effectiveness (C2), risk (C3), budgetary constraints (C4), exploitation time (C5), maintenance cost (C6), and mitigation time (C7). Secondly, we assigned them the weights of the criteria. The information security control that has the highest priority weight will be selected as the best information security control. The problem hierarchy determines how every alternative (information security control) is assessed through the predefined criteria. The preferences are determined using the triangular fuzzy scale (0 to 11). In this way, there is a very small chance of mistake and error as compared to the AHP.
Figure 8 shows the fuzzy AHP model used in this study.
The linguistic scale was prepared after an in-depth literature review to develop a pairwise comparison matrix, as shown in
Table 2.
In the next step, the values of the linguistic scale were transformed into TFNs as shown in
Table 3. A pairwise comparison matrix was required to be developed in light of the opinions/preferences of the decision makers against each criterion.
After the formalization of the above fuzzy pairwise comparison matrix, the next step was to calculate the weights of all the criteria with the support of the FAHP. Therefore, keeping in view the FAHP method, the synthesis values of the criteria were required to be calculated based on Equation (5).
SC1 = (6.33, 6.33, 6.33) * (0.010, 0.014, 0.022) = (0.063, 0.090, 0.142)
SC2 = (11, 21, 31) * (0.010, 0.014, 0.022) = (0.109, 0.3, 0.695)
SC3 = (6.20, 14.33, 23) * (0.010, 0.014, 0.022) = (0.061, 0.205, 0.505)
SC4 = (7.40, 11.67, 17) * (0.010, 0.014, 0.022) = (0.073, 0.167, 0.381)
SC5 = (5.40, 7.67, 11) * (0.010, 0.014, 0.022) = (0.053, 0.109, 0.247)
SC6 = (3.69, 4.07, 5.67) * (0.010, 0.014, 0.022) = (0.036, 0.058, 0.127)
SC7 = (4.60, 5, 7) * (0.010, 0.014, 0.022) = (0.046, 0.071, 0.157)
The next step is to calculate the degree of possibility by using Equation (10).
V (SC1≥SC2) = 0.136, V (SC1≥SC3) = 0.414, V (SC1≥SC4) = 0.474, V (SC1≥SC5) = 0.823, V (SC1≥SC6) = 1,
V (SC1≥SC7) = 1
V (SC2≥SC1) = 1, V (SC2≥SC3) = 1, V (SC2≥SC4) = 1, V (SC2≥SC5) = 1, V (SC2≥SC6) = 1, V (SC2≥SC7) = 1
V (SC3≥SC1) = 1, V (SC3≥SC2) = 0.810, V (SC3≥SC4) = 1, V (SC3≥SC5) = 1, V (SC3≥SC6) = 1, V (SC3≥SC7) = 1
V (SC4≥SC1) = 1, V (SC4≥SC2) = 0.671, V (SC4≥SC3) = 0.894, V (SC4≥SC5) = 1, V (SC4≥SC6) = 1,
V (SC4≥SC7) = 1
V (SC5≥SC1) = 1, V (SC5≥SC2) = 0.420, V (SC5≥SC3) = 0.661, V (SC5≥SC4) = 0.752, V (SC5≥SC6) = 1,
V (SC5≥SC7) = 1
V (SC6≥SC1) = 0.665, V (SC6≥SC2) = 0.070, V (SC6≥SC3) = 0.309, V (SC6≥SC4) = 0.331, V (SC6≥SC5) = 0.589,
V (SC6≥SC7) = 0.859
V (SC7≥SC1) = 0.832, V (SC7≥SC2) = 0.174, V (SC7≥SC3) = 0.418, V (SC7≥SC4) = 0.468, V (SC7≥SC5) = 0.731,
V (SC7≥SC6) = 1.
Using Equation (12), priority weights were calculated.
0.136, 0.414, 0.474, 0.823, 1, 1) = 0.136
, 1, 1, 1, 1, 1) = 1
, 0.810, 1, 1, 1, 1) = 0.810
, 0.671, 0.894, 0.1, 1, 1) = 0.671
, 0.420, 0.661, 0.752, 1, 1) = 0.420
0.665, 0.070, 0.309, 0.331, 0.589, 0.859) = 0.070
0.832, 0.174, 0.418, 0.468, 0.731, 1) = 0.174
The priority weights were
, and the next step was normalizing the priority weights by using Equation (13) and
using Equation (14). The final weights of each criteria are given in
Table 4.
The value of , and the value of the CI was calculated using Equation (15), and it was 0.117. Similarly, the value of CR was calculated using Equation (16), and it was 0.089 which is less than 0.1.
Evaluation of Alternatives with Respect to Each Criterion
The next step was to evaluate the alternatives. The ISO/IEC 27002:2013 has 114 information security controls, and it is not possible to demonstrate the detailed steps of 114 information security controls. Therefore, the authors decided to pick one domain of information security controls as alternatives and demonstrate a step-by-step calculation so that other information security controls could be evaluated using the same pattern. To accomplish this, we used the fuzzy AHP geometric means approach for synthetic pairwise comparison matrix as suggested by Buckley [
99].
Step 1: Similar to the evaluation of the main criteria, the first step is to develop a pairwise comparison matrix, keeping in view the first criterion using Equation (17).
Here, demonstrates the liking of i criterion over j, by the k evaluators.
The pairwise comparison matrix for implementation time criteria is given in
Table 5.
Step 2: The next step was to calculate the fuzzy geometric means of the pairwise comparison matrix using the Equation (18).
Similarly, geometric means values of the fuzzy comparison matrix were calculated for the remaining alternatives.
Table 6 shows the complete geometric means of
Table 5. In the last 03 lines of the given table, a total of the alternatives is also given. Their reverse values are also shown and, according to the requirements of fuzzy triangular numbers, the order of the numbers should be sequential.
Step 3: The next step is to calculate the fuzzy weights,
of each alternative by using Equation (19).
The following steps are required to be performed first before calculating
. First, calculate the summation of each
calculated in
Table 6 under the “Total” heading; then, calculate the (-1) power of the total
value as shown in the “Reverse” heading of
Table 6; finally, calculate
by multiplying each
with the reverse values.
.
The fuzzy weights
of each alternative in respect to the implementation time criteria are presented in
Table 7.
Step 4: In the fourth step, the relative weights of the non-fuzzy numbers of the alternatives were calculated using Equation (20).
Step 5: The fifth step was to normalize the non-fuzzy numbers using Equation (21).
The results of the
are shown in
Table 8.
Step 6: The next step was to check the consistency index and the fuzzy pairwise comparison matrix. The value of and the value of the C) was calculated using Equation (15), and it was 0.045. Similarly, the value of CR = 0.050, calculated using Equation (16), which is less than 0.10.
Step: 7: Here, we repeated steps 1 to 6 for the evaluation of each remaining alternative by using the equations given above.
The pairwise comparison matrix for the effectiveness (C
2) criteria is given in
Table 9.
The results of the
is calculated in respect to C
2 and presented in
Table 10.
The CI = 0.046 and CR = 0.051.
The pairwise comparison matrix for the risk (C
3) criteria is given in
Table 11.
The results of the
was calculated in respect to the risk (C
3) and is presented in
Table 12.
The CI = 0.055 and CR = 0.061.
The pairwise comparison matrix for the budgetary constraints (C
4) criteria is given in
Table 13.
The results of the
was calculated in respect to the budgetary constraints (C
4) and is presented
Table 14.
The CI = 0.073 and CR = 0.082.
The pairwise comparison matrix for the exploitation time (C
5) criteria is given in
Table 15.
The results of the
is calculated in respect to the exploitation time (C
5) and is presented in
Table 16.
The CI = 0.081 and CR = 0.090.
The pairwise comparison matrix for the maintenance cost (C
6) criteria is given in
Table 17.
The results of the
is calculated in respect to the maintenance cost (C
6) and presented in
Table 18.
The CI = 0.035 and CR = 0.039.
The pairwise comparison matrix for the mitigation time (C
7) criteria is given in
Table 19.
The results of the
is calculated in respect to the mitigation time (C
7) and is presented in
Table 20.
The CI = 0.012 and CR = 0.013.
Step 8: This is the last step to calculate the final weights of all the alternatives by multiplying the matrix of the normalized weights of each alternative with the matrix of the criteria weights while evaluating in respect to each criterion. The final weights of each alternative are calculated and shown in
Table 21 and depicted in
Figure 9.
The complete steps for the weighting of criterion through the fuzzy analytical hierarchy process using the extended analysis method and prioritization of the alternatives/information security controls were conducted. The FAHP using geometric means was used. The details are given above and in light of these steps, all the information security controls of ISO / IEC 27002:2013 were evaluated and prioritized. The results are shown in
Table 22.
The above results show that the controls have different ranks but fall in the same preference band. This is because similar preference band controls had almost the same results. The information security controls of a higher preference band must be given higher priority while implementing these controls, etc.