An Energy-Efficient Evolutionary Clustering Technique for Disaster Management in IoT Networks
Abstract
:1. Introduction
- Providing an energy-efficient method for clustering and routing in WSNs while considering the characteristics of disaster areas (with a non-uniform distribution of events).
- Proposing an improved hybrid PSO–HSA-based CH selection method with a novel fitness function including energy-efficiency, cluster closeness, and network coverage criteria.
- Utilizing the PSO to select relay nodes based on multi-hop routing with a fitness function including energy-efficiency and communication link quality criteria.
- Using the adaptive weighted sum (AWS) method as a mathematical model to solve the fitness function based on the multi-objective optimization problem (MOP) so that a lower optimization cost can be obtained.
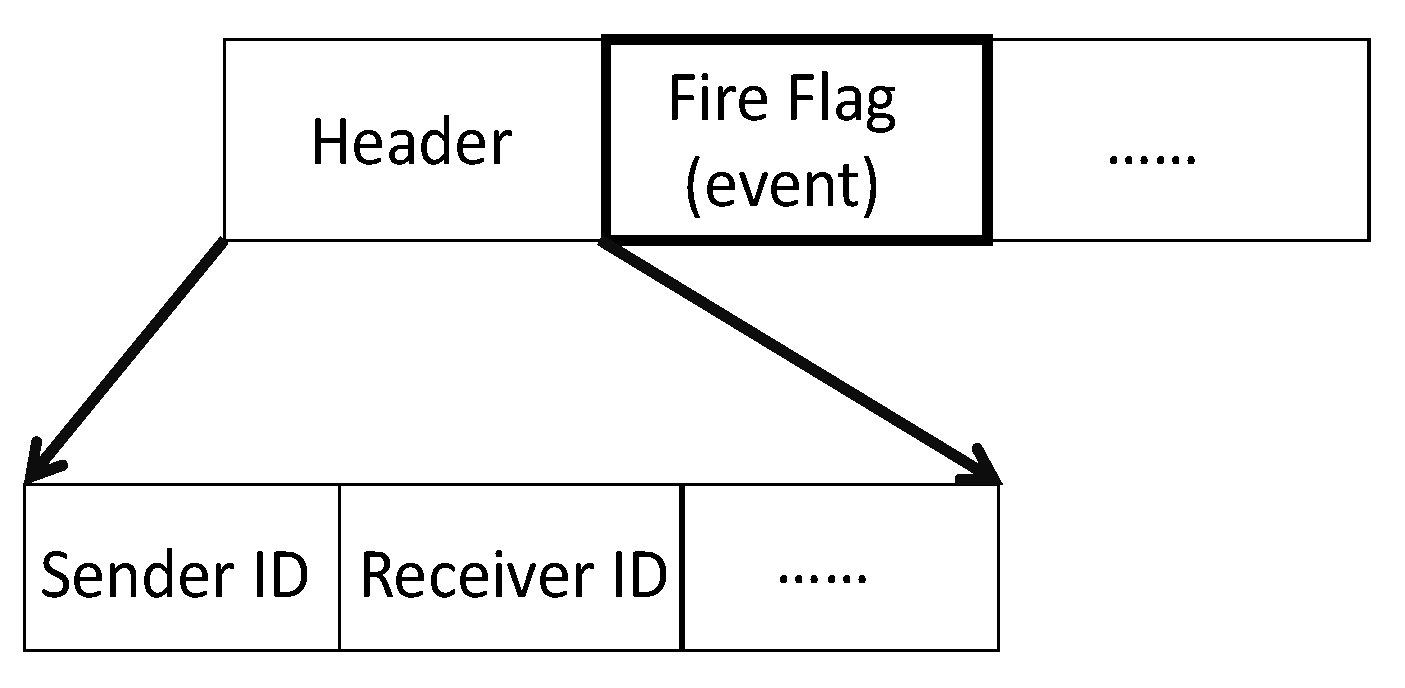
- Developing a new type of packet format which is adapted to use in disaster applications; furthermore, modifying the PSO encoding priority-based routing to build an optimal routing tree with non-uniform events.
- Overcoming the state-of-the-art approaches in terms of their average energy consumption, the number of live nodes, network coverage, and packet delivery ratio with various sink locations in disaster scenarios.
2. Related Works
3. Proposed Method
3.1. Network Model
- The nodes are fixed (stationary) in the network.
- Nodes are not location-aware, but the sink is aware of its position.
- All nodes have the same level of energy (E0) initially, and the network is homogeneous [7].
- The minimum RSSI with the value of −97 db is known as the worst received signal [27].
- The sink is responsible for clustering and routing. Therefore, the proposed method is centralized.
- The energy consumption of the nodes is estimated based on their distance from the sink or CH (by parameter d) [22].
3.2. AWS Method for LP Formula
Normalizing the LP Formula
3.3. Cluster Head Selection Phase
3.3.1. Improved Fitness Function for CH Selection
3.3.2. Cluster Closeness (CC)
3.3.3. Network Coverage (NC)
3.3.4. Clustering Steps
- Setting the Location and Velocity of the ParticlesThe location and velocity of the particles are placed randomly in the following intervals, respectively: and .The particle swarm size and harmony memory size (HMS) are initialized under the title of particle harmony memory (PHM). The initial PHM matrix [29], as shown in Equation (19), includes the number of random solutions generated to reach the optimal or near-optimal solution. Each row in the matrix is a random solution, and the fitness function for each vector is calculated by Equation (18).
- Improving Harmony Vectors for PHM and Updating the Hybrid MatrixAfter PHM is defined, new harmony vectors should be produced to improve the harmony vectors of the PHM. Each component of the new harmony vectors is generated by harmony memory considering the rate (HMCR), and eventually an optimal candidate vector of PHM is modified by the pitch adjusting rate (PAR). In this step, the state-of-the-art method [29] uses the simple structure of HSA, but attention must be paid to variations in different stages of the search process. Additionally, the study in [34] demonstrated that HSA suffers from a slow convergence speed to achieve a global optimum; however, in [31], the dynamic version of HSA exhibited fast convergence at the start of the algorithm, converging to the global optimum in the near-final stages of the search process. Therefore, in this paper, each harmony vector (HV) of the PHM is obtained dynamically. The procedure of improving the harmony vectors for PHM is described in Algorithm 1 [31].
where Nd1 and Nd2 are normal distribution functions with (), ri1 and ri2 are random integers between [1, HMS], ri3, ri4 and ri5 are random mutually exclusive integers between [1, HMS], the function is a uniform random number in [0, 1], and parameter k is generated uniformly by a discreet random number in [1, K] [31]. After method 1 in Algorithm 1, if ≤ PAR, the harmony vector (HV) should be tuned or pitched (a term in music) according to the PAR. is defined as the closest node with more energy than current CH is the cluster. It is necessary to clarify that parameter best in update 2 as the index of the best HV inspired by the GHS method [45]. Next, updating the PHM is the last step in the HS algorithm [29]. To do this, if the fitness function of the new harmony vector () is better than the value of the fitness function of the worst harmony vector in PHM (), the new harmony is included in the matrix and the current worst harmony of the PHM is excluded. Thus, the PHM is updated with this condition, and this step is stopped If the iteration of HSA is bigger than the maximum iteration.Algorithm 1: Pseudo code of Improving Harmony Vectors for PHM - Updating the Location and Velocity of the ParticlesIn this step, to reach the optimal location of the CHs, the PSO algorithm updates the location and velocity of the particles [2]. The best particle location () is determined by the minimum cost of the fitness function in a swarm particle [29]. The , as the global best location, is determined by selecting the best solution of . In this paper, the nodes that harmonize with are taken, and the closest nodes to these harmonies form CHs. The velocity (V) and location (X) of the particles can be updated as follows [23,29]:where the index denotes the xth particles and dimension, and are acceleration constants, and are the random uniform amount in [0, 1], and factor is the inertia weight factor. Selecting a suitable value of creates a balance between exploration and exploitation [46]. In [29], the linear reduction of factor has a positive effect on the efficiency of the application of WSNs, while in [46], the authors proposed a nonlinear time-varying inertia weight formula that led to a faster convergence than the linear inertia factor used in [29,45]. Therefore, to enhance efficacy, we use the following high-order (∝) nonlinear formula:where iter is the current of iteration and is the total number of iterations. Equation (22) [46] decreases nonlinearly from to and finds a suitable value at each round. The obtained results of [46] show that excellent performance is achieved when and the two constants and —as cognitive and social parameters—have the value 2. The location and velocity of the particles are calculated and updated at each round of the proposed method and for each row in PHM. As mentioned above, the closest nodes to will be the optimal CHs.
- Going Back to the First Step or Stopping the AlgorithmWhen all the rounds of the clustering phase come to an end, the algorithm stops and a total number of k optimal CHs are determined for the routing phase. Otherwise, the algorithm goes back to the second step and repeats until it finds optimal or near-optimal solutions. However, before the next round starts, the values of HMCR and PAR in Algorithm 1 are required to be updated as follows [31]:These dynamic updates in the search process enhance the exploration capacity of the first stages and lead to the improvement of the local search in the last stages [31] because the variation of the HMCR value affects the diversity and convergence of PHM, with similar results for the PAR value in terms of the local and global optimum [34,41,42]. Hence, the initial values of Equations (23) and (24) are adjusted according to [31].
3.4. Routing Phase
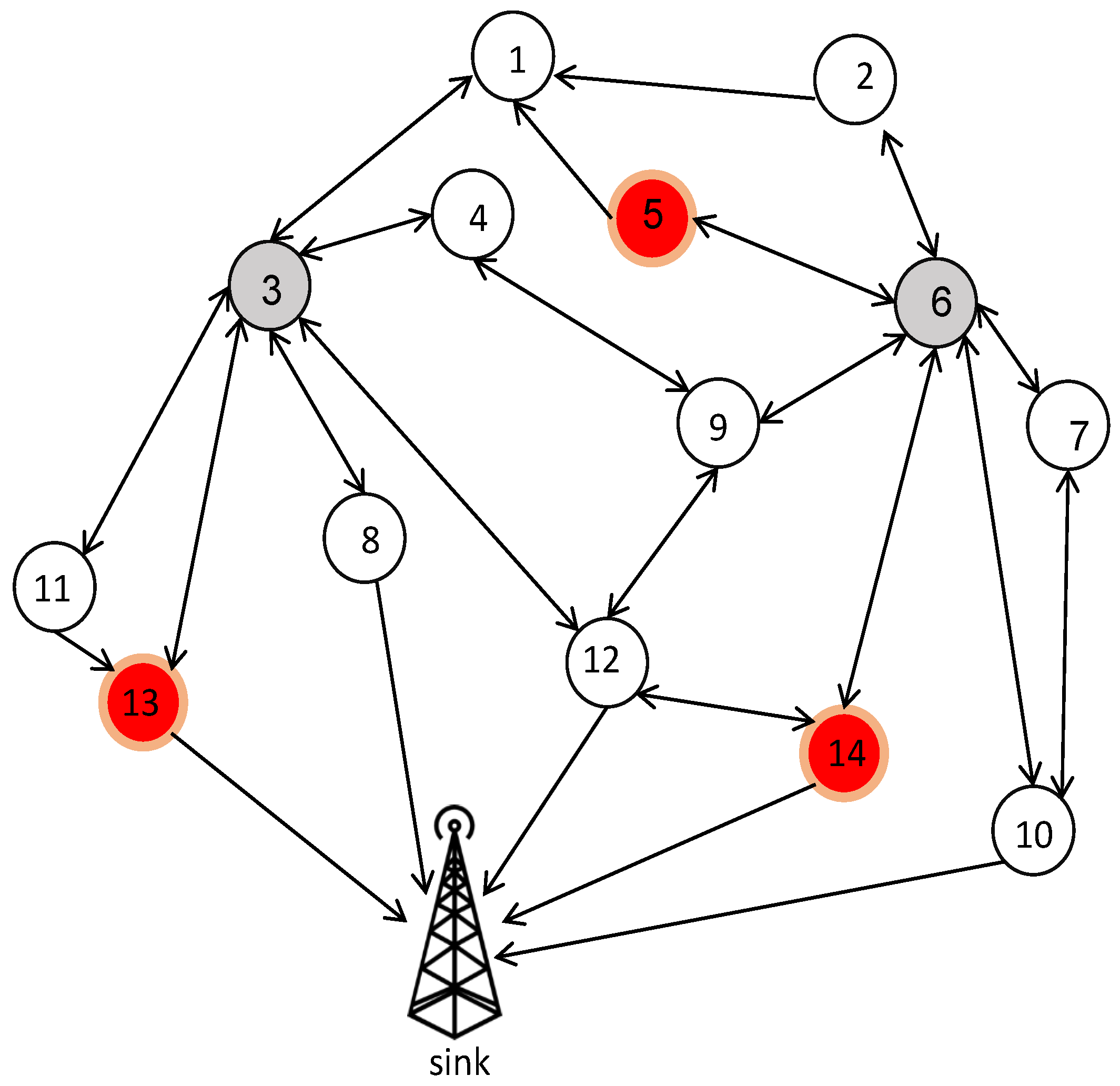
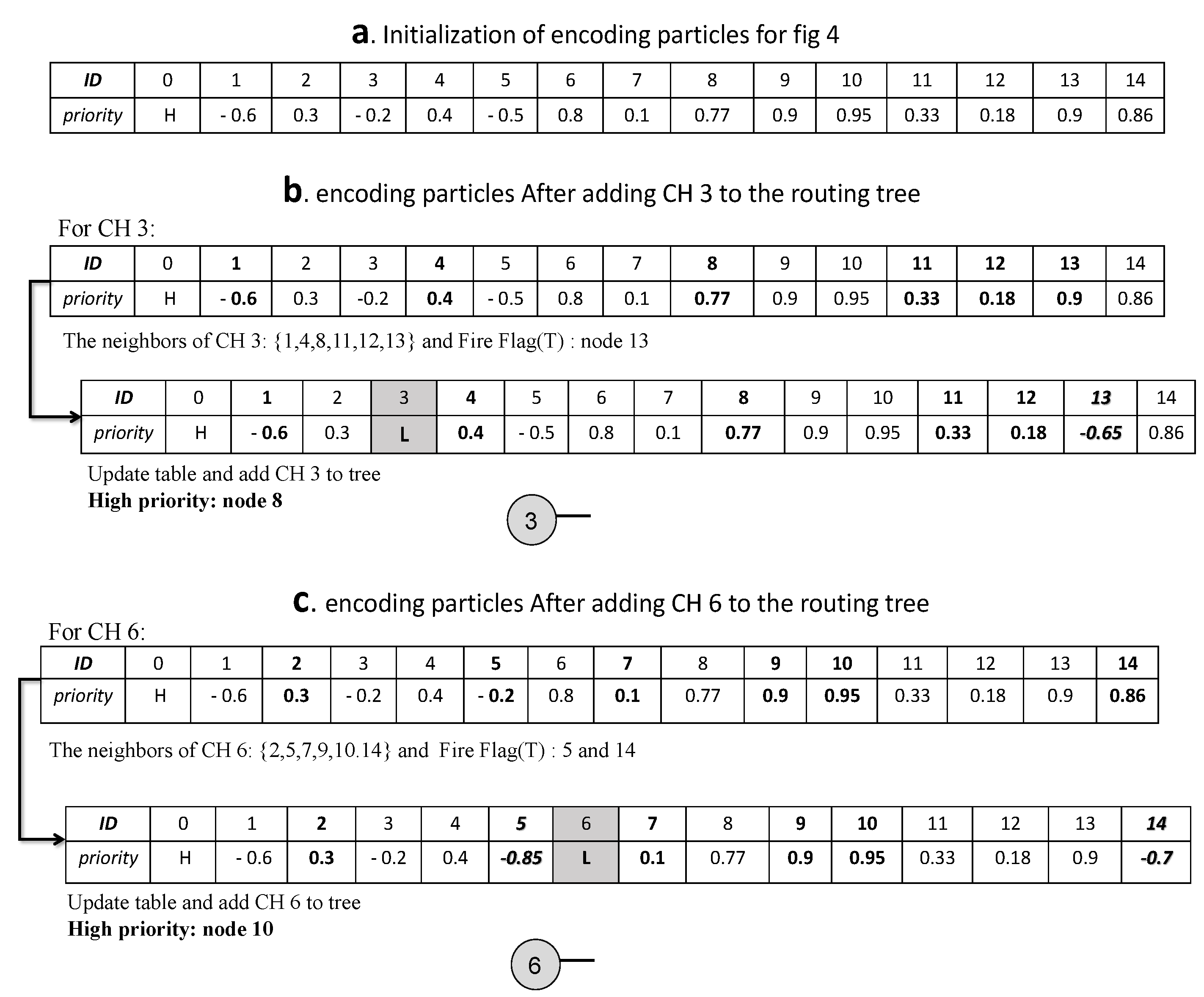
Enhanced Tree Encoding
3.5. Overall Proposed Algorithm
| Algorithm 2: Overall proposed pseudo-code (ECHSR) |
 |
| Algorithm 3: The pseudo-code of CH-selection() |
 |
| Algorithm 4: The pseudo-code of Routing() |
 |
4. Simulation Results and Evaluations
4.1. Simulation Setup
4.2. Simulation Results
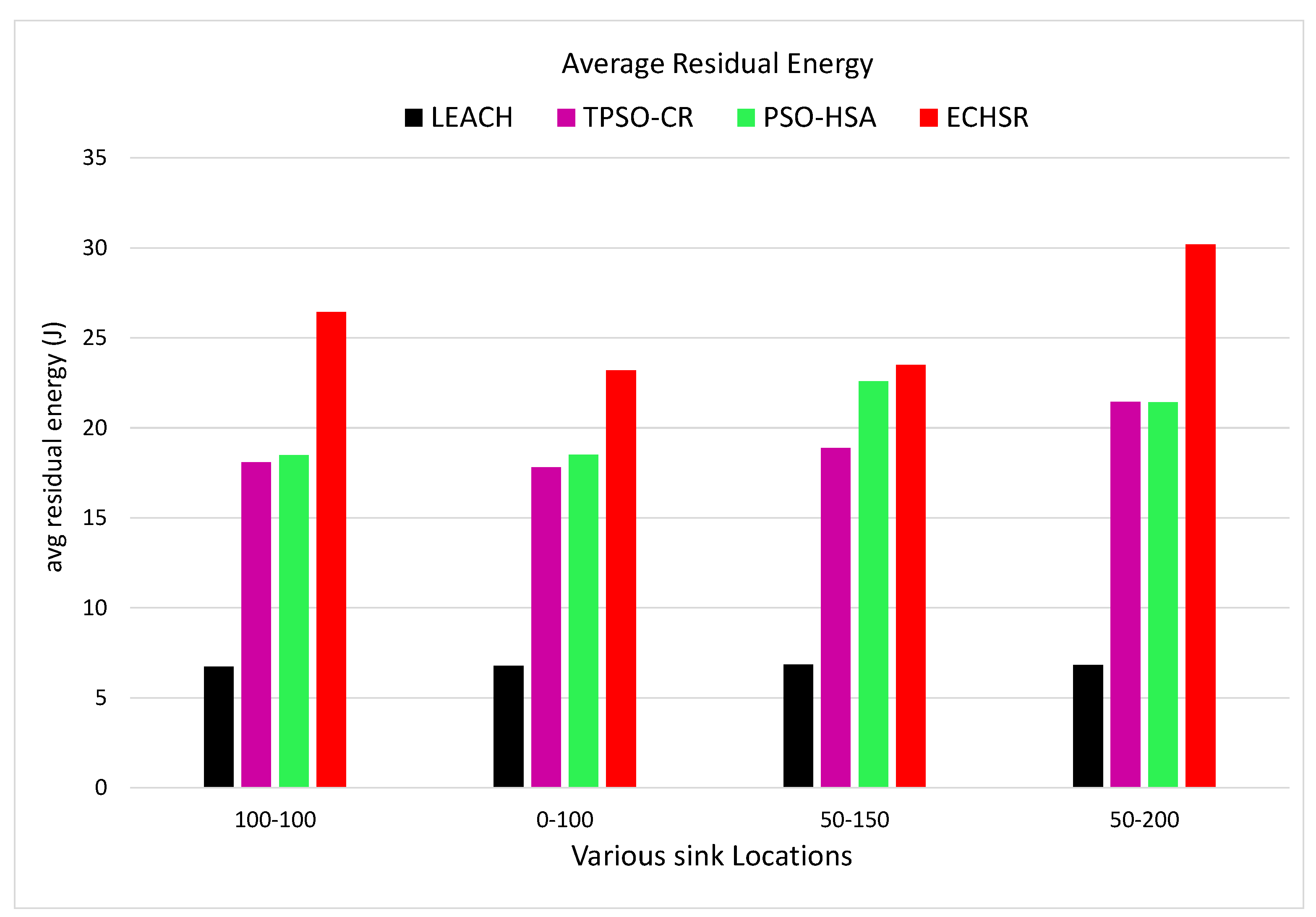
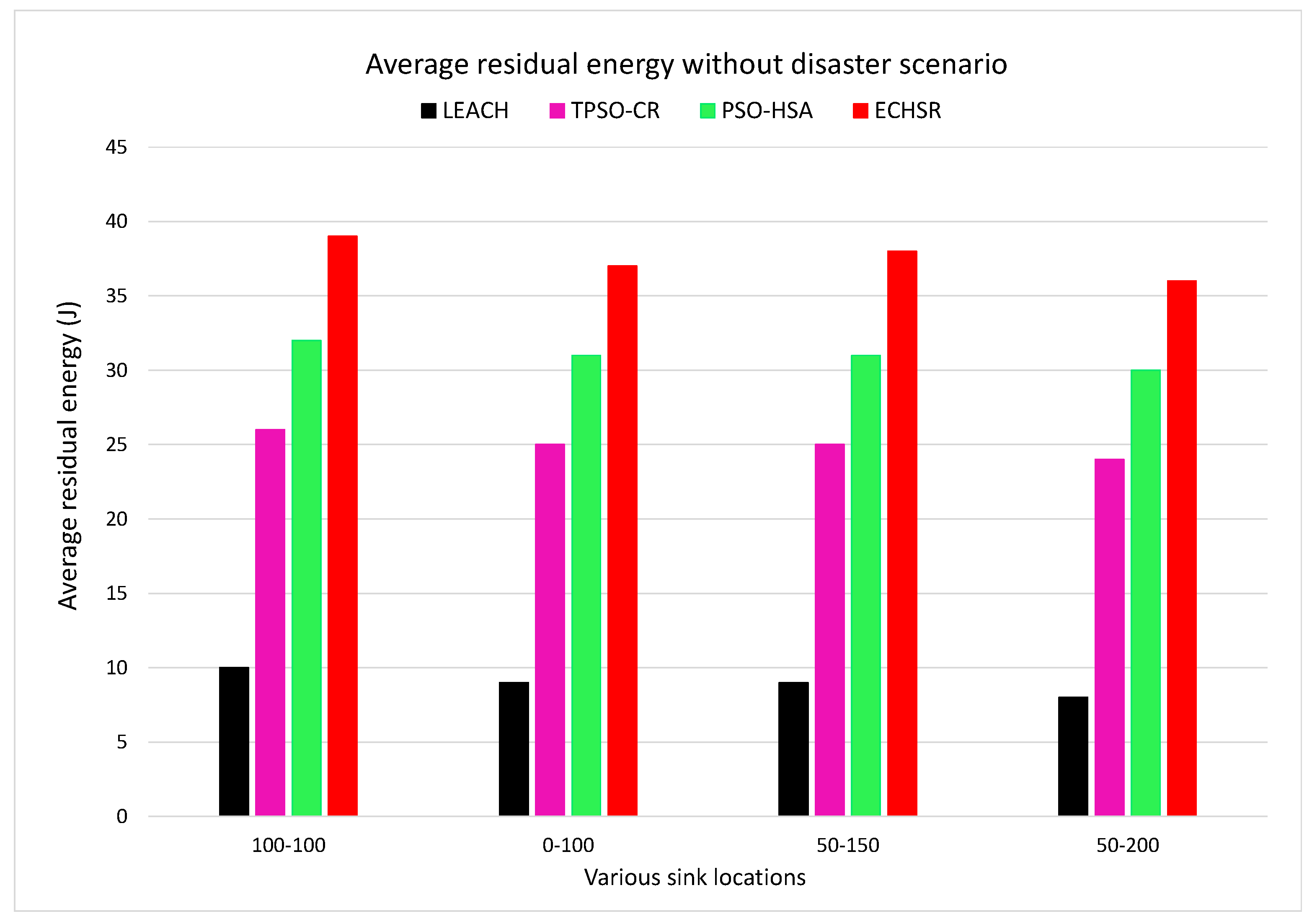
4.2.1. Overall Residual Energy
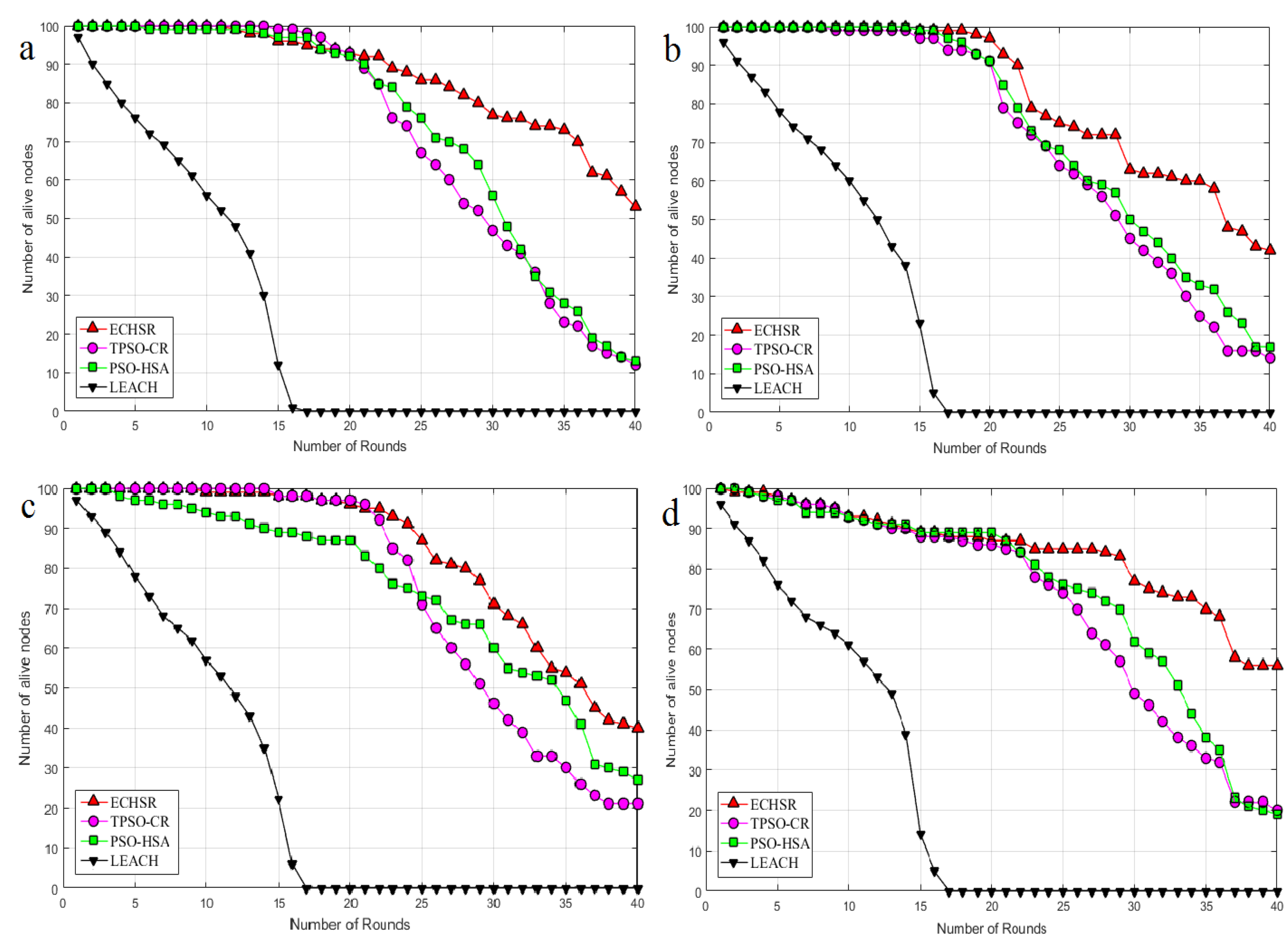
4.2.2. Active Nodes
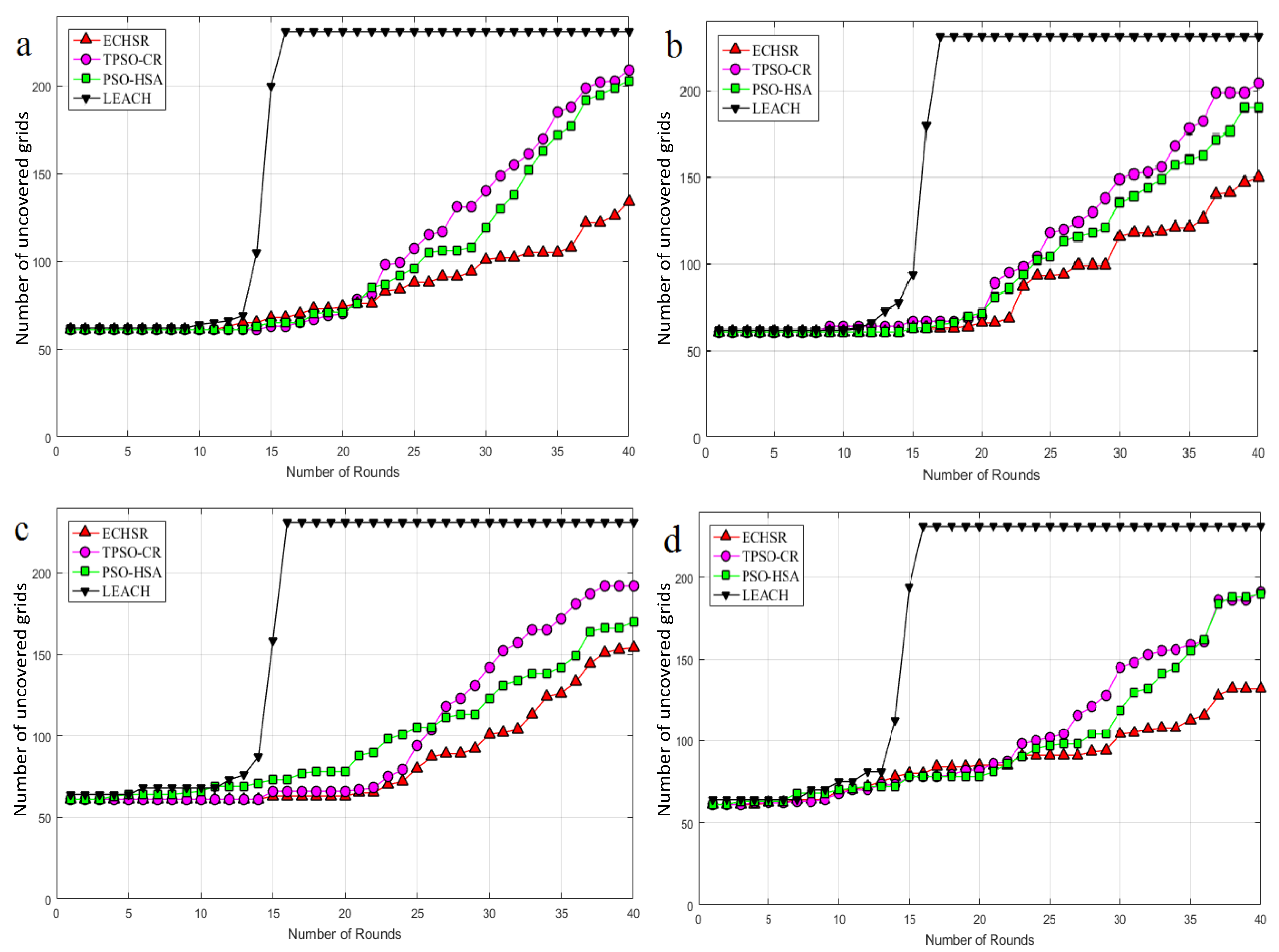
4.2.3. Network Coverage
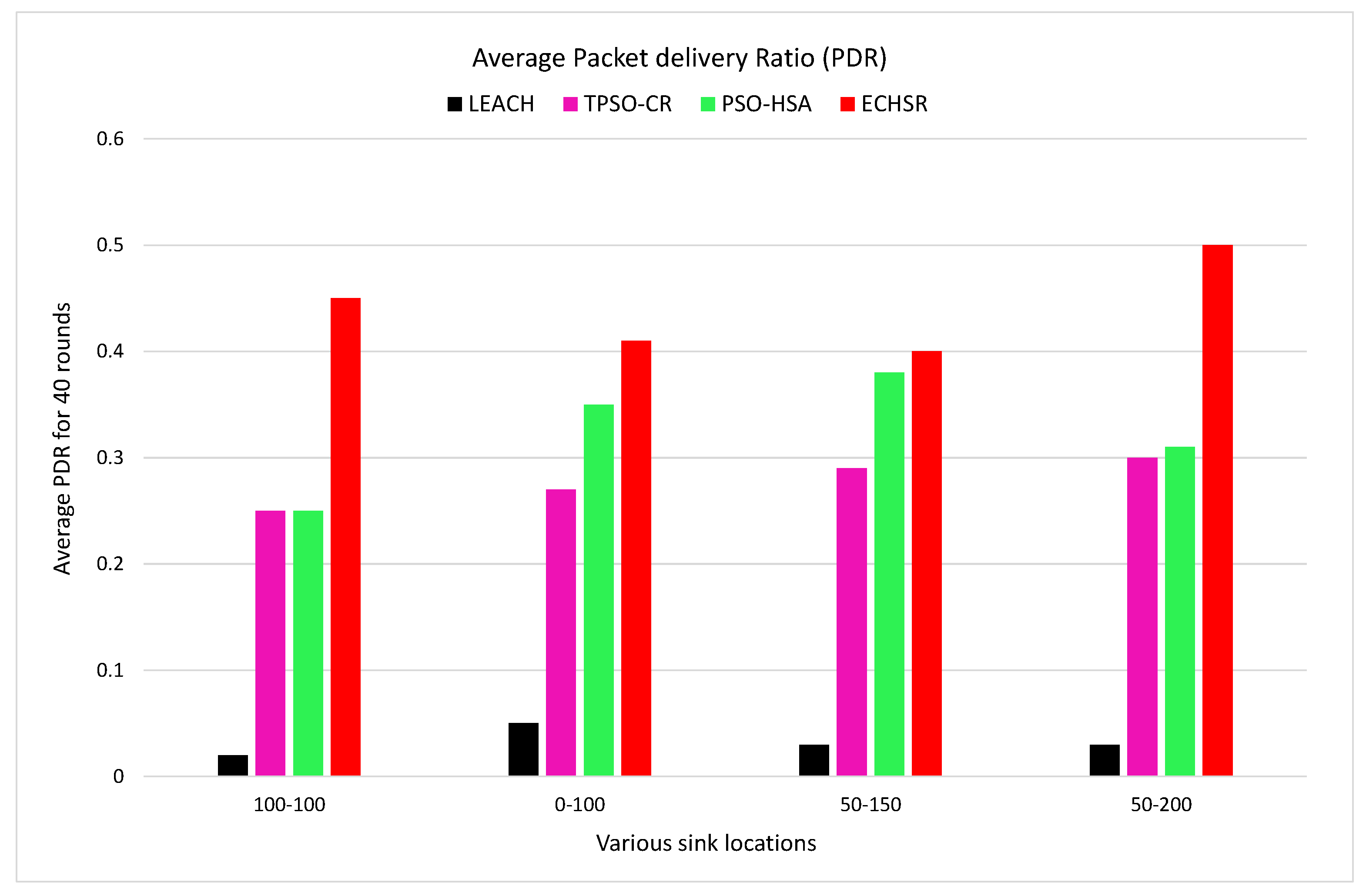
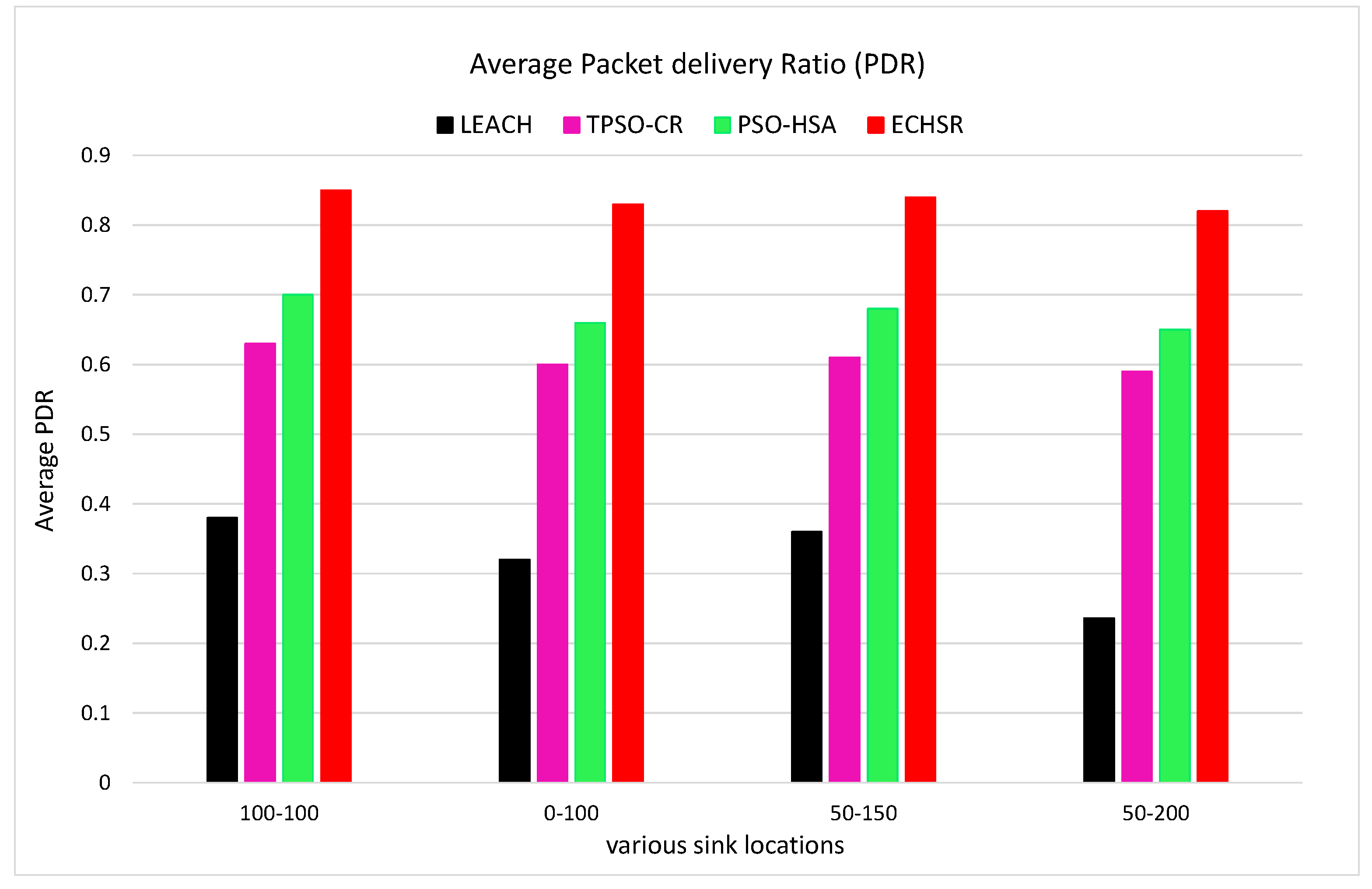
4.2.4. Packet Delivery Ratio
4.3. Uniform Distribution of Events
5. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Dhanvijay, M.M.; Patil, S.C. Internet of Things: A survey of enabling technologies in healthcare and its applications. Comput. Netw. 2019, 153, 113–131. [Google Scholar] [CrossRef]
- Qiu, T.; Li, B.; Zhou, X.; Song, H.; Lee, I.; Lloret, J. A Novel Shortcut Addition Algorithm with Particle Swarm for Multi-sink Internet of Things. IEEE Trans. Ind. Inform. 2019, 16, 3566–3577. [Google Scholar] [CrossRef]
- Cai, S.; Zhu, Y.; Wang, T.; Xu, G.; Liu, A.; Liu, X. Data collection in underwater sensor networks based on mobile edge computing. IEEE Access 2019, 7, 65357–65367. [Google Scholar] [CrossRef]
- Hao, Y.; Chen, M.; Hu, L.; Hossain, M.S.; Ghoneim, A. Energy efficient task caching and offloading for mobile edge computing. IEEE Access 2018, 6, 11365–11373. [Google Scholar] [CrossRef]
- Akkaya, K.; Younis, M. A survey on routing protocols for wireless sensor networks. Ad Hoc Netw. 2005, 3, 325–349. [Google Scholar] [CrossRef] [Green Version]
- Hussain, I.; Ullah, M.; Ullah, I.; Bibi, A.; Naeem, M.; Singh, M. Optimizing Energy Consumption in the Home Energy Management System via a Bio-Inspired Dragonfly Algorithm and the Genetic Algorithm. Electronics 2020, 9, 406. [Google Scholar] [CrossRef]
- Khan, I.; Singh, D. Energy-balance node-selection algorithm for heterogeneous wireless sensor networks. ETRI J. 2018, 40, 604–612. [Google Scholar] [CrossRef]
- Rawat, P.; Singh, K.D.; Chaouchi, H.; Bonnin, J.M. Wireless sensor networks: A survey on recent developments and potential synergies. J. Supercomput. 2014, 68, 1–48. [Google Scholar] [CrossRef]
- Araghizadeh, M.A.; Teymoori, P.; Yazdani, N.; Safari, S. An efficient medium access control protocol for WSN-UAV. Ad Hoc Netw. 2016, 52, 146–159. [Google Scholar] [CrossRef]
- Johnson, D.B.; Maltz, D.A. Dynamic source routing in ad hoc wireless networks. In Mobile Computing; Springer: Boston, MA, USA, 1996; pp. 153–181. [Google Scholar]
- Shen, H.; Bai, G. Routing in wireless multimedia sensor networks: A survey and challenges ahead. J. Netw. Comput. Appl. 2016, 71, 30–49. [Google Scholar] [CrossRef]
- Jha, R.; Singh, A.; Tewari, A.; Shrivastava, P. Performance analysis of disaster management using WSN technology. Procedia Comput. Sci. 2015, 49, 162–169. [Google Scholar] [CrossRef] [Green Version]
- Hefeeda, M.; Bagheri, M. Forest fire modeling and early detection using wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2009, 7, 169–224. [Google Scholar]
- Avesani, P.; Perini, A.; Ricci, F. Interactive case-based planning for forest fire management. Appl. Intell. 2000, 13, 41–57. [Google Scholar] [CrossRef]
- Priyadarsini, P.U.; Sriramya, P. Disaster management using evidence-based interactive trust management system for wireless sensor networks by Internet of Things. Comput. Electr. Eng. 2019, 75, 164–174. [Google Scholar] [CrossRef]
- Yu, L.; Wang, N.; Meng, X. Real-time forest fire detection with wireless sensor networks. In Proceedings of the 2005 International Conference on Wireless Communications, Networking and Mobile Computing, Wuhan, China, 26 September 2005; Volume 2, pp. 1214–1217. [Google Scholar]
- Molina-Pico, A.; Cuesta-Frau, D.; Araujo, A.; Alejandre, J.; Rozas, A. Forest monitoring and wildland early fire detection by a hierarchical wireless sensor network. J. Sens. 2016, 2016, 8325845. [Google Scholar] [CrossRef] [Green Version]
- Yuan, C.; Zhang, Y.; Liu, Z. A survey on technologies for automatic forest fire monitoring, detection, and fighting using unmanned aerial vehicles and remote sensing techniques. Can. J. For. Res. 2015, 45, 783–792. [Google Scholar] [CrossRef]
- Aslan, Y.E.; Korpeoglu, I.; Ulusoy, Ö. A framework for use of wireless sensor networks in forest fire detection and monitoring. Comput. Environ. Urban Syst. 2012, 36, 614–625. [Google Scholar] [CrossRef]
- Karafyllidis, I. Design of a dedicated parallel processor for the prediction of forest fire spreading using cellular automata and genetic algorithms. Eng. Appl. Artif. Intell. 2004, 17, 19–36. [Google Scholar] [CrossRef]
- Alkhatib, A.A. A review on forest fire detection techniques. IInt. J. Distrib. Sens. Netw. 2014, 10, 597368. [Google Scholar] [CrossRef] [Green Version]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000; p. 10. [Google Scholar]
- Singh, B.; Lobiyal, D.K. A novel energy-aware cluster head selection based on particle swarm optimization for wireless sensor networks. Hum. Cent. Comput. Inf. Sci. 2012, 2, 13. [Google Scholar] [CrossRef] [Green Version]
- Zungeru, A.M.; Ang, L.M.; Seng, K.P. Classical and swarm intelligence based routing protocols for wireless sensor networks: A survey and comparison. J. Netw. Comput. Appl. 2012, 35, 1508–1536. [Google Scholar] [CrossRef]
- Krishnan, M.; Yun, S.; Jung, Y.M. Dynamic clustering approach with ACO-based mobile sink for data collection in WSNs. Wirel. Netw. 2019, 25, 4859–4871. [Google Scholar] [CrossRef]
- Han, T.; Zhang, L.; Pirbhulal, S.; Wu, W.; de Albuquerque, V.H.C. A novel cluster head selection technique for edge-computing based IoMT systems. Comput. Netw. 2019, 158, 114–122. [Google Scholar] [CrossRef]
- Elhabyan, R.S.; Yagoub, M.C. Two-tier particle swarm optimization protocol for clustering and routing in wireless sensor network. J. Netw. Comput. Appl. 2015, 52, 116–128. [Google Scholar] [CrossRef]
- Rahimi, S.; Abdollahpouri, A.; Moradi, P. A multi-objective particle swarm optimization algorithm for community detection in complex networks. Swarm Evol. Comput. 2018, 39, 297–309. [Google Scholar] [CrossRef]
- Shankar, T.; Shanmugavel, S.; Rajesh, A. Hybrid HSA and PSO algorithm for energy efficient cluster head selection in wireless sensor networks. Swarm Evol. Comput. 2016, 30, 1–10. [Google Scholar] [CrossRef]
- Guleria, K.; Verma, A.K. Comprehensive review for energy efficient hierarchical routing protocols on wireless sensor networks. Wirel. Netw. 2019, 25, 1159–1183. [Google Scholar] [CrossRef]
- Wang, L.; Hu, H.; Liu, R.; Zhou, X. An improved differential harmony search algorithm for function optimization problems. Soft Comput. 2019, 23, 4827–4852. [Google Scholar] [CrossRef]
- Gumaida, B.F.; Luo, J. A hybrid particle swarm optimization with a variable neighborhood search for the localization enhancement in wireless sensor networks. Appl. Intell. 2019, 49, 3539–3557. [Google Scholar] [CrossRef]
- Bongale, A.M.; Nirmala, C.; Bongale, A.M. Hybrid Cluster Head Election for WSN Based on Firefly and Harmony Search Algorithms. Wirel. Pers. Commun. 2019, 106, 275–306. [Google Scholar] [CrossRef]
- Sarkhel, R.; Das, N.; Saha, A.K.; Nasipuri, M. An improved harmony search algorithm embedded with a novel piecewise opposition based learning algorithm. Eng. Appl. Artif. Intell. 2018, 67, 317–330. [Google Scholar] [CrossRef]
- Khalesian, M.; Delavar, M.R. Wireless sensors deployment optimization using a constrained Pareto-based multi-objective evolutionary approach. Eng. Appl. Artif. Intell. 2016, 53, 126–139. [Google Scholar] [CrossRef]
- Handl, J.; Knowles, J. An evolutionary approach to multiobjective clustering. IEEE Trans. Evol. Comput. 2007, 11, 56–76. [Google Scholar] [CrossRef]
- Grodzevich, O.; Romanko, O. Normalization and Other Topics in Multi-Objective Optimization 2006. Available online: http://www.maths-in-industry.org/miis/233/1/fmipw1-6.pdf (accessed on 2 May 2020).
- Zhang, H.; Wang, R.; Liu, H.; Luo, H.; Liu, Y. MCDMSR: Multicriteria decision making selection/replacement based on agility strategy for real optimization problems. Appl. Intell. 2019, 49, 2918–2941. [Google Scholar] [CrossRef]
- Mohemmed, A.W.; Sahoo, N.C.; Geok, T.K. Solving shortest path problem using particle swarm optimization. Appl. Soft Comput. 2008, 8, 1643–1653. [Google Scholar] [CrossRef]
- Manjeshwar, A.; Agrawal, D.P. TEEN: ARouting Protocol for Enhanced Efficiency in Wireless Sensor Networks. Available online: http://www.nhu.edu.tw/~cmwu/Lab/TEEN.pdf (accessed on 2 May 2020).
- Hoang, D.; Yadav, P.; Kumar, R.; Panda, S. A robust harmony search algorithm based clustering protocol for wireless sensor networks. In Proceedings of the 2010 IEEE international conference on communications workshops, Capetown, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar]
- Gupta, G.P.; Jha, S. Integrated clustering and routing protocol for wireless sensor networks using Cuckoo and Harmony Search based metaheuristic techniques. Eng. Appl. Artif. Intell. 2018, 68, 101–109. [Google Scholar] [CrossRef]
- Khatarkar, S.; Kamble, R. Wireless sensor network MAC protocol: SMAC & TMAC. Indian J. Comput. Sci. Eng. 2013, 4, 304–310. [Google Scholar]
- Armano, G.; Farmani, M.R. Multiobjective clustering analysis using particle swarm optimization. Expert Syst. Appl. 2016, 55, 184–193. [Google Scholar] [CrossRef]
- Shi, Y.; Eberhart, R.C. Empirical study of particle swarm optimization. In Proceedings of the 1999 Congress on Evolutionary Computation-CEC99 (Cat. No. 99TH8406), Washington, DC, USA, 6–9 July 1999; Volume 3, pp. 1945–1950. [Google Scholar]
- Yang, C.; Gao, W.; Liu, N.; Song, C. Low-discrepancy sequence initialized particle swarm optimization algorithm with high-order nonlinear time-varying inertia weight. Appl. Soft Comput. 2015, 29, 386–394. [Google Scholar] [CrossRef]
- Wilensky, U. Netlogo. (Center for Connected Learning and Computer-Based Modeling.) 1999. Available online: http://ccl.northwestern.edu/netlogo/ (accessed on 2 May 2020).






| Reference | Clustering Schema | Converge | Energy-Efficient | Cluster Stability | Event Awareness | Routing | Clustering Objective |
|---|---|---|---|---|---|---|---|
| LEACH [22] | Random Distributed | No | Low | Low | No | single-hop | Changing CH based Prob./Random |
| TEEN [40] | Probability Centralized | No | Medium | Low | No | single-hop | Changing CH based Threshold |
| [23] | PSO-based Centralized | Low balanced | Moderate | High | No | single-hop | Energy Efficiency + Min Distance + Node Hop count |
| [41] | HSA-based Centralized | Low balanced | Medium | Low | No | single-hop | Energy Efficiency + Min Distance |
| TPSO-CR [27] | PSO-based Centralized | Moderate balanced | Moderate | High | No | multi-hop | Energy Efficiency + link Quality + Coverage |
| PSO-HSA [29] | PSO and HSA Centralized | Moderate balanced | High | High | No | single-hop | Energy Efficiency + Min Distance |
| iCSHS [42] | Cuckoo-based Distributed | Moderate balanced | Moderate | Low | No | multi-hop | Energy Efficiency + Node degree + Intra Distance + Coverage |
| This Paper | PSO and HSA Centralized | High balanced | very High | High | Yes | multi-hop | Energy Efficiency + Cluster Closeness + Coverage |
| N | AN | MR |
|---|---|---|
| N | Number of nodes | 100 |
| Sensor field region | 100 m × 200 m | |
| E0 | Initial energy of a nodes | 0.5 (j) |
| K | Number of CHs | 5 |
| DP | Data packet length | 4096 (bits) |
| DA | Energy data aggregation | 5 (nJ) |
| [Xmin, Xmax] | Particle position | [0, 200] |
| [Vmin, Vmax] | Particle velocity | [0, 200] (m/s) |
| [c1min, c1max] and [c2min, c2max] | Acceleration constants | 2 |
| Eamp | Multipath fading transmitter amplifier energy | 130 (pJ/bit/m2) |
| Eelec | Transmission and receiving energy | 50 (nJ/bit) |
| Efs | Free space transmitter amplifier energy | 10 (pJ/bit/m2) |
| Max Round | Maximum number of rounds | 40 rounds |
| Sw | Swarm size | 15 |
| Iter | Number of iterations | 5 |
| HMCRmin and HMCRmax | Harmonic memory considering rate | 0.8 and 0.9 |
| PARmin and PARmax | Pitch adjustment rate | 0.1 and 0.9 |
| Maximum values of inertia weight | 0.9 | |
| Minimum values of inertia weight | 0.4 | |
| Base Station (BS) | Various sink locations | (0, 100), (100, 100), (50, 150), (50, 200) |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Biabani, M.; Fotouhi, H.; Yazdani, N. An Energy-Efficient Evolutionary Clustering Technique for Disaster Management in IoT Networks. Sensors 2020, 20, 2647. https://doi.org/10.3390/s20092647
Biabani M, Fotouhi H, Yazdani N. An Energy-Efficient Evolutionary Clustering Technique for Disaster Management in IoT Networks. Sensors. 2020; 20(9):2647. https://doi.org/10.3390/s20092647
Chicago/Turabian StyleBiabani, Morteza, Hossein Fotouhi, and Nasser Yazdani. 2020. "An Energy-Efficient Evolutionary Clustering Technique for Disaster Management in IoT Networks" Sensors 20, no. 9: 2647. https://doi.org/10.3390/s20092647
APA StyleBiabani, M., Fotouhi, H., & Yazdani, N. (2020). An Energy-Efficient Evolutionary Clustering Technique for Disaster Management in IoT Networks. Sensors, 20(9), 2647. https://doi.org/10.3390/s20092647








