Decision-Making under Uncertainty for the Deployment of Future Hyperconnected Networks: A Survey †
Abstract
1. Introduction
2. Information Extraction Methods
2.1. Semantic Data Mining
2.2. Information Economy MetaLanguage
3. Computational Methods for Decision-Making under Uncertainty
3.1. Multiple Criteria Decision-Making
- The Preference Ranking Organization Method for Enrichment of Evaluations (PROMETHEE) [53] builds an external classification for various alternatives based on a combination of mathematical and psychological methods developing its own understanding of the problem to help agents choose the option that best serves their purpose. This method has been evaluated by different domains such as infrastructure construction [38], the electric power sector [39,40], and engineering decision-making [41], among others.
- The Analytic Hierarchy Process (AHP) [54] combines conflicting physical and psychological elements based on appraisals and assessments to manage complex decisions. In [42,43], decision-making is handled under uncertainty, while in [44], it is based on subjective product recommendations from consumers.
- The Multicriteria Optimization and Compromise Solution (VIKOR) [55] aims at determining the best possible solution when dealing with conflicting options or with different methods of measurement. In [45], VIKOR is combined with other techniques to assess feelings in social media; in [46], group decision-making processes are implemented; and in [47], it is used in the evaluation of airline service quality.
- The Technique for Order of Preference by Similarity to Ideal Solution (TOPSIS) [56] aims at finding an alternative solution using the shortest and longest Euclidean distance from the optimal positive solution and the optimal negative solution, respectively. This method is usually enhanced by additional algorithms, as shown in [48,49,50].
3.2. Optimization Methods
3.2.1. Fuzzy Logic
3.2.2. Game Theory
3.2.3. Bayesian Networks
3.2.4. Stochastic Process
3.2.5. Support Vector Machine
3.3. Machine Learning
3.3.1. Supervised Learning
- Telecommunications. In this field, supervised learning has been used based on factors such as QoS and automatic configuration. For example, QoS has been used to create resource appraisal and classification models for IoT [87] or for any type of network [88]. It has also been used as a retroactive measure to tailor service selection [89] and for decreasing the time required by virtual machine migration processes through WAN links [90]. In addition, in terms of automatic configuration processes, some studies address 5G networks [7,92] and elastic cloud systems [91].
- Energy. Several types of problems of this field have been solved by applying the supervised learning method, such as preventive planning of uncertain operations in power systems [93]; by selecting the best maintenance route to minimize operational costs when power grid failures occur [94]; by predicting nuclear power system behavior [95]; and by selecting the best location for wind turbines based on economic, regulatory, and social factors [96].
- Transport. In this field, several studies focus on process improvement, such as speed and accuracy in lane changing maneuvers when driving on highways [97], driving terrestrial vehicles on rural roads [98], robots learning routes through linguistic decision trees [99], and methods used in biped robot walking processes [100,101].
- Enhanced decisions. These studies focus on improving the performance of decision-making results by choosing selection mechanisms in complex negotiation scenarios [102], by considering environmental awareness when dealing with critical complex systems processes under supervision [103], by assessing the advantages of combining the learning process with multiple agents and weighted strategies [104], and by suggesting two complementary stages that would exist between machine learning and support vector machines [105].
3.3.2. Unsupervised Learning
- Transport. When applying this method to this field, research is centered on obstacle management for autonomous driving from various approaches. For example, in terms of the epistemic uncertainty of images [115], semantic segmentation methods achieve high inference classification accuracy in object recognition within interior spaces [116] or in different other additional challenges, as listed in [117].
- Health. The works proposed in this field are aimed at improving unsupervised learning accuracy and solution times, as denoted in [118], which discusses liver fibrosis diagnoses. Furthermore, in [119], this method was used to customize patient therapy processes and, in [120], it was used to diagnose complex vision pathologies.
- Business decisions. In this field, research works focus on earning profits by selecting the best decisions, as described in [121], where feeling assessments are combined with share price volatility. In addition, an evaluation of industrial systems in terms of sustainability through hard-to-find indicators was presented in [83]. Another study discussed learning from previous decisions through comparative evaluation processes [122]. This method was also applied in the education sector to assign students to a company depending on their skills [123] and to improve manager actions at universities [124].
- Dealing with uncertainty. Studies seeking to solve unsupervised learning problems dealing with uncertainty use different approaches, such as in battleground decision-making [125]. In geology, it is used for water- and oil-flow systems [126]; in gambling, its is used for the Khun poker game [127]; and it can be used when merely facing the uncertainty of applying this method to any type of problem, such as in [128,129].
3.3.3. Reinforcement Learning
- Telecommunications. Based on this method, several topics have been addressed within this field, such as resource management, particularly regarding power consumption for large-scale IoT applications [130]. In [131], a framework was proposed based on reinforcement learning for the SDN control plane to intelligently manage uncertainty in 5G networks. In routing, as in [132], the authors planned to prevent gateway bottlenecks by identifying the best path for reaching the best gateway through reinforcement learning techniques.
- Energy. For energy companies, decision-making is complicated due to the high level of uncertainty that exists. For these purposes, there are proposals, as in [133], seeking to balance supply and demand in real time in Smart energy markets, or as in [134], which improves previous energy market negotiations by adapting techniques such as Q-learning.
3.3.4. Deep Learning
- Human Behavior. On this subject, different research approaches have been used. For example, as a first approach, human behavior prediction models have been developed, either when decision-making is affected by peer pressure or by the inference of human activities based on short videos [151]. The approach ranges from psychological perspectives to assessing decision-making abstraction in human beings, both in regular contexts [152] or with imperfect information [153].
- Uncertainty. Through deep learning, uncertainty challenges have been studied under different approaches. Some examples are uncertainty problems due to subjective opinions in heterogeneous networks [154]; in military scenarios, the uncertainty in unmanned aerial combat vehicle decisions [155]; uncertainty modeling in real time for the relocation of automatic visual systems [156,162]; issues when dealing with missing data due to the calculation of uncertainty based on the remaining training dataset [157]; and a random estimation method to calculate uncertainty in object detection for applications that require reliable decisions [163]. Another area is decision-making under uncertainty, such as whenever assessing complex structures [158] or emotions are expressed in texts [159]. Finally, the work associated with taking risks under uncertainty has been mentioned, either as analyzed from the perspective of video games, as in [160], or in financial forecasts for customers [161].
4. Internet of Things Application Domain
4.1. Mobile Wireless Sensor Network
4.2. Smart Spaces
4.3. Industry 4.0
5. Radical New Approach to Deal with Uncertainty in HCNs
- Text mining and semantic analysis techniques, towards semantically rich representations of exchanged user texts;
- Graph-based representations of user data and relevant network metrics (such as centrality), towards identifying key user behavior types and patterns;
- Markovian models (Hidden Markov chains, dynamic graphs processes, information spreading, etc.) [178] to capture inherent dynamics and complex impacts of user data and Partially Observable Markov Decision Process (POMDP) to cope with the inherent uncertainty due to unreliable and/or incomplete information [179];
- Non-Markovian models (to capture special dependency on the current state) such as Martingales [184];
- Key algorithmic methodologies (primarily machine learning and cognitive reasoning) to characterize the user data, their reliability level, and the associated discourse types; and
- Game theory methods, which can contribute to behavior prediction of rational individuals (and the society as a whole) [185,186,187,188]. It is worth noting that variants of game theory models (including penalties) can even address (and perhaps mitigate) “irrational” behavior, due to, e.g., to hidden, latent, or even unconscious mechanisms in one’s behavior and actions.
- User 1:
- User 2:
6. Discussion
- Concerns in network connectivity. Mobility is one of the main characteristics of modern networks. However, depending on the technology, mobility may face challenges, such as radio spectrum reservations and allocation, bandwidth allocation, transfers, and routings. If communications are between heterogeneous networks, these situations may become quite complicated. Therefore, standardized self-organization mechanisms are required for the infrastructure to adjust to the constant changes caused by mobility and user demands, regardless of technology. However, cloud computing support provides greater availability and possibility for distributed and online processes to be implemented. Remote processes may be managed and monitored in manufacturing, medical care, or surveillance, among others, through their interaction with IoT. Nevertheless, in applications wherein response times are critical, this technology must be correctly assessed to prevent proper operations from being disrupted. Moreover, in contrast to cloud computing, fog computing uses a decentralized infrastructure that adapts to the specific nature of HCNs since devices can be distributed in several regions. Consequently, with fog computing, the data produced by devices is processed closer to the places where they are generated, which means that they are not uploaded over long distances to any cloud, thus improving the performance of the services offered by HCNs while decreasing response and reaction times. However, as fog computing continues to face several new challenges, such as business models, security, privacy, and scalability, further research on these areas may be required [4].
- Concerns about security and privacy. Security risks can have economic, environmental, and organizational consequences that may be related to personal, social, or industrial environments. Even people’s lives may face some type of risk. Malware that impacts devices connected to networks may reduce DCN performance and may compromise package delivery to such an extent that the whole network may collapse, among other examples. Attacks from malware, such as Mirai, take control over IoT network devices, such as IP cameras, printers, routers, sensors, and others, to carry out a distributed denial of service attack. The Mirai attack was considered the most devastating in history because it affected around 164 countries and blocked Dyn, one of the most important domain name system service providers for worldwide companies. The attack affected application services provided by companies such as WhatsApp, Github, Twitter, PayPal, and Spotify. Another consequence may be the interception or modification of personal or business information. Issues related to cybersecurity, where the authorization and authentication of sensors, devices, and actuators, are critical for securing trust in HCN operations.
- Elements related to decision-making. It is somewhat challenging to make decisions on cross-cutting issues such as HCN management due to the different types of resources used, such as heterogeneous networks, several types of sensors and devices, and the vast number of data collection sources, among others. Based on these reasons, reaching agreements on standards is a continuous improvement issue [199,200]. Furthermore, integrating decision-making and machine learning is an exciting matter due to the large amount of data, processing capacities, and the range of techniques that must adjust to needs under data uncertainty. In fact, this may even include exploring diverse possible potential integrations between MCDM methods and machine learning for each different phase of the decision-making process [94,201,202]. Another challenge faced is real-time decision-making processing because decisions are effective only if made in real time [203]. This involves several factors that require further research, such as data accuracy, low response times, distributed processing, and security methods [204].
- Challenges related to sensors and devices. Regarding electronic devices, they take samples and report the behavior of environment variables or of the individuals for whom these variables were created. In both instances, problems arise in terms of access conditions to power grids or communications networks [205,206], and especially for wireless sensors, which, in general, exhibit decreased processing resources, battery autonomy, wireless range or security [207]. These constraints contrast with the demands for resources needed when applying machine learning techniques, which implies that identifying computationally efficient strategies is an essential component. Various device manufacturers are another issue, since each has its own input and output data formats, protocols, and interfaces and this hinders interoperability and smooth operations.
- IoT massification and the deployment of the 5G network will cause high network densification, which brings about the need to examine new routing protocols that may support constant changes in user contexts. This means that these protocols may use context information whenever moment priorities change, employing the required resources to meet new objectives.
- The large level of ubiquity and information exchange among users and systems will facilitate security threats sustained by artificial intelligence. Therefore, there is an urgent need to set up policies and measures to protect personal information.
- HCNs can potentially generate large amounts of data due to the integration and interconnection of individuals and machines as part of their network infrastructure. The availability of data generated by people and machines brings about an opportunity to compile context awareness. In this light, a new information technology paradigm must be proposed to consider the rationality and irrationality of human behavior when managing the resources of underlying infrastructures. For instance, to suppress the data uncertainty that humans add to emerging networks, the structuralist nature of psychoanalysis can be researched to model human uncertainty.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Conti, M.; Passarella, A.; Das, S.K. The Internet of People (IoP): A new wave in pervasive mobile computing. Pervasive Mob. Comput. 2017, 41, 1–27. [Google Scholar] [CrossRef]
- Dix, A. Human-computer interaction, foundations and new paradigms. J. Vis. Lang. Comput. 2016, 42, 122–134. [Google Scholar] [CrossRef]
- Bellini, E.; Bellini, P.; Cenni, D.; Nesi, P.; Pantaleo, G.; Paoli, I.; Paolucci, M. An IoE and Big Multimedia Data Approach for Urban Transport System Resilience Management in Smart Cities. Sensors 2021, 21, 435. [Google Scholar] [CrossRef]
- Fei, X.; Shah, N.; Verba, N.; Chao, K.M.; Sanchez-Anguix, V.; Lewandowski, J.; James, A.; Usman, Z. CPS data streams analytics based on machine learning for Cloud and Fog Computing: A survey. Future Gener. Comput. Syst. 2019, 90, 435–450. [Google Scholar] [CrossRef]
- Lee, J.; Bagheri, B.; Kao, H.A. A Cyber-Physical Systems architecture for Industry 4.0-based manufacturing systems. Manuf. Lett. 2015, 3, 18–23. [Google Scholar] [CrossRef]
- Chahuara, P.; Portet, F.; Vacher, M. Context-aware decision making under uncertainty for voice-based control of smart home. Expert Syst. Appl. 2017, 75, 63–79. [Google Scholar] [CrossRef]
- Jiang, W.; Strufe, M.; Schotten, H.D. A SON decision-making framework for intelligent management in 5G mobile networks. In Proceedings of the 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2017; pp. 1158–1162. [Google Scholar]
- Kreutz, D.; Ramos, F.M.V.; Veríssimo, P.E.; Rothenberg, C.E.; Azodolmolky, S.; Uhlig, S. Software-Defined Networking: A Comprehensive Survey. Proc. IEEE 2015, 103, 14–76. [Google Scholar] [CrossRef]
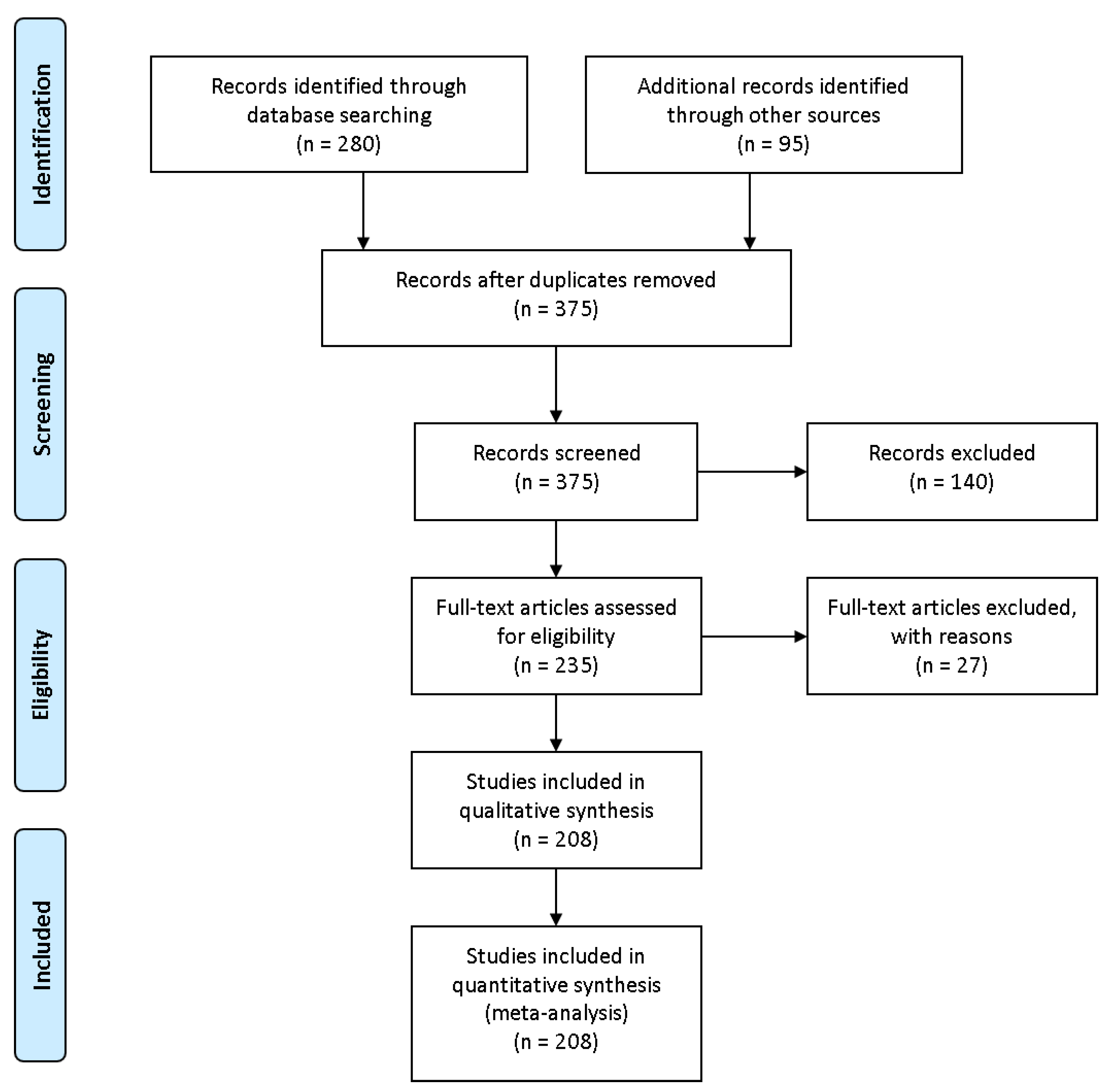
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372. [Google Scholar] [CrossRef]
- Zhou, Z.H. Three perspectives of data mining. Artif. Intell. 2003, 143, 139–146. [Google Scholar] [CrossRef]
- Saha, A.; Tasdid, M.N.; Rahman, M.R. Mining Semantic Web Based Ontological Data. In Proceedings of the 21st International Conference of Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 21–23 December 2018; pp. 1–5. [Google Scholar]
- Sheth, A. Internet of Things to Smart IoT Through Semantic, Cognitive, and Perceptual Computing. IEEE Intell. Syst. 2016, 31, 108–112. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context Aware Computing for The Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 414–454. [Google Scholar] [CrossRef]
- Ruta, M.; Scioscia, F.; Pinto, A.; Gramegna, F.; Ieva, S.; Loseto, G.; Sciascio, E.D. Cooperative semantic sensor networks for pervasive computing contexts. In Proceedings of the 7th IEEE International Workshop on Advances in Sensors and Interfaces (IWASI), Vieste, Italy, 15–16 June 2017; pp. 38–43. [Google Scholar]
- Alhakbani, N.; Hassan, M.M.; Ykhlef, M.; Fortino, G. An efficient event matching system for semantic smart data in the Internet of Things (IoT) environment. Future Gener. Comput. Syst. 2019, 95, 163–174. [Google Scholar] [CrossRef]
- Wang, R.; Ji, W.; Liu, M.; Wang, X.; Weng, J.; Deng, S.; Gao, S.; Yuan, C.A. Review on mining data from multiple data sources. Pattern Recognit. Lett. 2018, 109, 120–128. [Google Scholar] [CrossRef]
- Eichstadt, S.; Gruber, M.; Vedurmudi, A.P.; Seeger, B.; Bruns, T.; Kok, G. Toward Smart Traceability for Digital Sensors and the Industrial Internet of Things. Sensors 2021, 21, 19. [Google Scholar] [CrossRef] [PubMed]
- Dong, Y.; Wan, K.; Yue, Y. A Semantic-Based Belief Network Construction Approach in IoT. Sensors 2020, 20, 5747. [Google Scholar] [CrossRef] [PubMed]
- Cofta, P.; Karatzas, K.; Orłowski, C. A Conceptual Model of Measurement Uncertainty in IoT Sensor Networks. Sensors 2021, 21, 1827. [Google Scholar] [CrossRef]
- Kabir, S.; Ripon, S.; Rahman, M.; Rahman, T. Knowledge-based Data Mining Using Semantic Web. IERI Procedia 2014, 7, 113–119. [Google Scholar] [CrossRef]
- Shadroo, S.; Rahmani, A.M. Systematic survey of big data and data mining in internet of things. Comput. Netw. 2018, 139, 19–47. [Google Scholar] [CrossRef]
- Sharma, S.; Kumar, A.; Rana, V. Ontology Based Informational Retrieval System on the Semantic Web: Semantic Web Mining. In Proceedings of the International Conference on Next Generation Computing and Information Systems (ICNGCIS), Jammu, India, 11–12 December 2017; pp. 35–37. [Google Scholar]
- Dou, D.; Wang, H.; Liu, H. Semantic data mining: A survey of ontology-based approaches. In Proceedings of the 9th International Conference on Semantic Computing (ICSC), Anaheim, CA, USA, 7–9 February 2015; pp. 244–251. [Google Scholar]
- Ristoski, P.; Paulheim, H. Semantic Web in data mining and knowledge discovery: A comprehensive survey. J. Web Semant. 2016, 36, 1–22. [Google Scholar] [CrossRef]
- Safwat, H.; Gruzitis, N.; Davis, B.; Enache, R. Extracting Semantic Knowledge from Unstructured Text Using Embedded Controlled Language. In Proceedings of the IEEE Tenth International Conference on Semantic Computing (ICSC), Laguna Hills, CA, USA, 4–6 February 2016; pp. 87–90. [Google Scholar]
- Nagorny, K.; Scholze, S.; Ruhl, M.; Colombo, A.W. Semantical support for a CPS data marketplace to prepare Big Data analytics in smart manufacturing environments. In Proceedings of the IEEE Industrial Cyber-Physical Systems (ICPS), St. Petersburg, Russia, 15–18 May 2018; pp. 206–211. [Google Scholar]
- Wang, Y.; Bai, X.; Ou, H. Design and Development of Intelligent Logistics System Based on Semantic Web and Data Mining Technology. In Proceedings of the International Conference on Computer Network, Electronic and Automation (ICCNEA), Xi’an, China, 23–25 September 2017; pp. 231–235. [Google Scholar]
- Shadbolt, N.; Berners-Lee, T.; Hall, W. The Semantic Web Revisited. IEEE Intell. Syst. 2006, 21, 96–101. [Google Scholar] [CrossRef]
- IEML. Le Métalangage de Léconomie de Línformation. LIVRE BLANC. 2019. Available online: https://www.dropbox.com/s/875vsj0atbcts43/0-00-IEML-Manifesto-2019-fr.pdf?dl=0 (accessed on 18 February 2021). [CrossRef]
- Lévy, P. The Semantic Sphere; Addison-Wesley: Reading, MA, USA, 2011. [Google Scholar]
- Kochenderfer, M.J.; Amato, C.; Chowdhary, G.; How, J.P.; Reynolds, H.J.D.; Thornton, J.R.; Torres-Carrasquillo, P.A.; Üre, N.K.; Vian, J. Decision Making under Uncertainty: Theory and Application; MIT Lincoln Laboratory Series; The MIT Press: Cambridge, MA, USA, 2015; p. 352. [Google Scholar]
- Cables, E.; Lamata, M.; Verdegay, J. RIM-reference ideal method in multicriteria decision making. Inf. Sci. 2016, 337, 1–10. [Google Scholar] [CrossRef]
- Asadabadi, M.R. The stratified multi-criteria decision-making method. Knowl. Based Syst. 2018, 162, 115–123. [Google Scholar] [CrossRef]
- Ferrara, M.; Rasouli, S.; Khademi, M.; Salimi, M. A robust optimization model for a decision-making problem: An application for stock market. Oper. Res. Perspect. 2017, 4, 136–141. [Google Scholar] [CrossRef]
- Chen, S.; Liu, J.; Wang, H.; Augusto, J.C. An evidential reasoning based approach for decision making with partially ordered preference under uncertainty. In Proceedings of the International Conference on Machine Learning and Cybernetics, Tianjin, China, 14–17 July 2013; pp. 1712–1717. [Google Scholar]
- Zhang, P.; Yao, H.; Qiu, C.; Liu, Y. Virtual Network Embedding Using Node Multiple Metrics Based on Simplified ELECTRE Method. IEEE Access 2018, 6, 37314–37327. [Google Scholar] [CrossRef]
- Dammak, F.; Baccour, L.; Ayed, A.B.; Alimi, A.M. ELECTRE method using interval-valued intuitionistic fuzzy sets and possibility theory for multi-criteria decision making problem resolution. In Proceedings of the IEEE International Conference on Fuzzy Systems, Naples, Italy, 9–12 July 2017; pp. 1–6. [Google Scholar]
- Gervasio, H.; Simoes Da Silva, L. A probabilistic decision-making approach for the sustainable assessment of infrastructures. Expert Syst. Appl. 2012, 39, 7121–7131. [Google Scholar] [CrossRef]
- Wei, L.; Yuan, Z.; Yan, Y.; Hou, J.; Qin, T. Evaluation of energy saving and emission reduction effect in thermal power plants based on entropy weight and PROMETHEE method. In Proceedings of the Chinese Control and Decision Conference (CCDC), Yinchuan, China, 28–30 May 2016; pp. 143–146. [Google Scholar]
- Almeida, A.T.d.; Morais, D.C.; Alencar, L.H.; Clemente, T.R.N.; Krym, E.M.; Barboza, C.Z. A multicriteria decision model for technology readiness assessment for energy based on PROMETHEE method with surrogate weights. In Proceedings of the IEEE International Conference on Industrial Engineering and Engineering Management, Selangor, Malaysia, 9–12 December 2014; pp. 64–68. [Google Scholar]
- Smet, Y.D. About the computation of robust PROMETHEE II rankings: Empirical evidence. In Proceedings of the IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Bali, Indonesia, 4–7 December 2016; pp. 1116–1120. [Google Scholar]
- Zavadskas, E.K.; Turskis, Z.; Bagočius, V. Multi-criteria selection of a deep-water port in the Eastern Baltic Sea. Appl. Soft Comput. 2015, 26, 180–192. [Google Scholar] [CrossRef]
- Mousavi, S.M.; Gitinavard, H.; Siadat, A. A new hesitant fuzzy analytical hierarchy process method for decision-making problems under uncertainty. In Proceedings of the IEEE International Conference on Industrial Engineering and Engineering Management, Selangor, Malaysia, 9–12 December 2014; pp. 622–626. [Google Scholar]
- Kumar, G. A multi-criteria decision making approach for recommending a product using sentiment analysis. In Proceedings of the 12th International Conference on Research Challenges in Information Science (RCIS), Nantes, France, 29–31 May 2018; pp. 1–6. [Google Scholar]
- Qin, J.; Liu, X.; Pedrycz, W. An extended VIKOR method based on prospect theory for multiple attribute decision making under interval type-2 fuzzy environment. Knowl. Based Syst. 2015, 86, 116–130. [Google Scholar] [CrossRef]
- Morente-Molinera, J.A.; Kou, G.; Samuylov, K.; Ureña, R.; Herrera-Viedma, E. Carrying out consensual Group Decision Making processes under social networks using sentiment analysis over comparative expressions. Knowl. Based Syst. 2019, 165, 335–345. [Google Scholar] [CrossRef]
- Perçin, S. Evaluating airline service quality using a combined fuzzy decision-making approach. J. Air Transp. Manag. 2018, 68, 48–60. [Google Scholar] [CrossRef]
- Yu, B.; Cai, M.; Li, Q. A λ-rough set model and its applications with TOPSIS method to decision making. Knowl. Based Syst. 2019, 165, 420–431. [Google Scholar] [CrossRef]
- Chen, S.M.; Cheng, S.H.; Lan, T.C. A new multicriteria decision making method based on the topsis method and similarity measures between intuitionistic fuzzy sets. In Proceedings of the International Conference on Machine Learning and Cybernetics (ICMLC), Jeju, Korea, 10–13 July 2016; pp. 692–696. [Google Scholar]
- Cables, E.H.; Lamata, M.T.; Verdegay, J.L. Ideal Reference Method with Linguistic Labels: A Comparison with LTOPSIS. In Uncertainty Management with Fuzzy and Rough Sets: Recent Advances and Applications; Springer International Publishing: Cham, Switzerland, 2019; pp. 115–126. [Google Scholar]
- Khezrimotlagh, D.; Chen, Y. Data envelopment analysis. In International Series in Operations Research and Management Science; Springer: Dordrecht, The Netherlands, 2018; Volume 269, pp. 217–234. [Google Scholar]
- Roy, B. Classement et choix en présence de points de vue multiples. Rev. Française d’Informatique Rech. Opérationnelle 1968, 2, 57–75. [Google Scholar] [CrossRef]
- Mareschal, B.; Brans, J.P.; Vincke, P. PROMETHEE: A new family of outranking methods in multicriteria analysis. Oper. Res. ORIJ 1984, 84. Available online: https://ideas.repec.org/p/ulb/ulbeco/2013-9305.html (accessed on 18 February 2021).
- Saaty, T.L. The Analytic Hierarchy Process: Planning, Priority Setting, Resource Allocation; McGraw-Hill: New York, USA, 1980; p. 287. [Google Scholar]
- Duckstein, L.; Opricovic, S. Multiobjective optimization in river basin development. Water Resour. Res. 1980, 16, 14–20. [Google Scholar] [CrossRef]
- Hwang, C.L.; Yoon, K. Methods for Multiple Attribute Decision Making. In Multiple Attribute Decision Making: Methods and Applications A State-of-the-Art Survey; Springer: Berlin/Heidelberg, Germany, 1981; pp. 58–191. [Google Scholar] [CrossRef]
- Charnes, A.; Cooper, W.; Rhodes, E. Measuring the efficiency of decision making units. Eur. J. Oper. Res. 1978, 2, 429–444. [Google Scholar] [CrossRef]
- Peng, X.; Garg, H. Algorithms for interval-valued fuzzy soft sets in emergency decision making based on WDBA and CODAS with new information measure. Comput. Ind. Eng. 2018, 119, 439–452. [Google Scholar] [CrossRef]
- Mokhtarian, M.N.; Sadi-Nezhad, S.; Makui, A. A new flexible and reliable IVF-TOPSIS method based on uncertainty risk reduction in decision making process. Appl. Soft Comput. J. 2014, 23, 509–520. [Google Scholar] [CrossRef]
- Madi, E.N.; Garibaldi, J.M.; Wagner, C. Exploring the use of type-2 fuzzy sets in multi-criteria decision making based on TOPSIS. In Proceedings of the IEEE International Conference on Fuzzy Systems (FUZZ-IEEE), Naples, Italy, 9–12 July 2017; pp. 1–6. [Google Scholar]
- Yue, Z.; Jia, Y. An application of soft computing technique in group decision making under interval-valued intuitionistic fuzzy environment. Appl. Soft Comput. J. 2013, 13, 2490–2503. [Google Scholar] [CrossRef]
- Shen, L.; Wang, H.; Feng, X. Ranking Methods of Intuitionistic Fuzzy Numbers in Multicriteria Decision Making. In Proceedings of the 3rd International Conference on Information Management, Innovation Management and Industrial Engineering, Kunming, China, 26–28 November 2010; pp. 143–146. [Google Scholar]
- Yan, R.; Zheng, J.; Wang, X. Vague set methods of multi-criteria fuzzy decision-making. In Proceedings of the Chinese Control and Decision Conference, Xuzhou, China, 26–28 May 2010; pp. 658–661. [Google Scholar]
- Gao, C.; Lai, Z.; Zhou, J.; Zhao, C.; Miao, D. Maximum decision entropy-based attribute reduction in decision-theoretic rough set model. Knowl. Based Syst. 2018, 143, 179–191. [Google Scholar] [CrossRef]
- Remesh, K.M.; Nair, L.R. Rough set theory and three way decisions: Refinement of boundary region in the decision making process. In Proceedings of the International Conference on Information Science (ICIS), Kochi, India, 12–13 August 2016; pp. 156–159. [Google Scholar]
- Yao, J.; Azam, N. Web-Based Medical Decision Support Systems for Three-Way Medical Decision Making With Game-Theoretic Rough Sets. IEEE Trans. Fuzzy Syst. 2015, 23, 3–15. [Google Scholar] [CrossRef]
- Kondratenko, Y.; Kondratenko, G.; Sidenko, I. Multi-criteria Decision Making and Soft Computing for the Selection of Specialized IoT Platform. In Recent Developments in Data Science and Intelligent Analysis of Information; Chertov, O., Mylovanov, T., Kondratenko, Y., Kacprzyk, J., Kreinovich, V., Stefanuk, V., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 71–80. [Google Scholar]
- Lamata, M.T.; Pelta, D.A.; Rosete, A.; Verdegay, J.L. Context-Based Decision and Optimization: The Case of the Maximal Coverage Location Problem. In Information Processing and Management of Uncertainty in Knowledge-Based Systems; Medina, J., Ojeda-Aciego, M., Verdegay, J.L., Perfilieva, I., Bouchon-Meunier, B., Yager, R.R., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 330–341. [Google Scholar]
- Mendel, J.M. Type-1 Fuzzy Sets and Fuzzy Logic. In Uncertain Rule-Based Fuzzy Systems: Introduction and New Directions, 2nd ed.; Springer International Publishing: Cham, Switzerland, 2017; pp. 25–99. [Google Scholar] [CrossRef]
- Keshavarz Ghorabaee, M.; Amiri, M.; Zavadskas, E.K.; Turskis, Z.; Antucheviciene, J. A new multi-criteria model based on interval type-2 fuzzy sets and EDAS method for supplier evaluation and order allocation with environmental considerations. Comput. Ind. Eng. 2017, 112, 156–174. [Google Scholar] [CrossRef]
- Matía, F.; Jiménez, V.; Alvarado, B.P.; Haber, R. The fuzzy Kalman filter: Improving its implementation by reformulating uncertainty representation. Fuzzy Sets Syst. 2021, 402, 78–104. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, S.; Deng, X.; Jiang, W. An improved approach for adversarial decision making under uncertainty based on simultaneous game. In Proceedings of the Chinese Control And Decision Conference (CCDC), Shenyang, China, 9–11 June 2018; pp. 2499–2503. [Google Scholar]
- Giraldo, F.A.; Gomez, J. The evolution of neural networks for decision making in non-cooperative repetitive games. In Proceedings of the 8th Computing Colombian Conference (8CCC), Armenia, Colombia, 21–23 August 2013; pp. 1–6. [Google Scholar]
- Chen, Y.; Jiang, C.; Wang, C.Y.; Gao, Y.; Liu, K.R. Decision Learning: Data analytic learning with strategic decision making. IEEE Signal Process. Mag. 2016, 33, 37–56. [Google Scholar] [CrossRef]
- Vamvakas, P.; Tsiropoulou, E.E.; Papavassiliou, S. Risk-Aware Resource Management in Public Safety Networks. Sensors 2019, 19, 3853. [Google Scholar] [CrossRef]
- Bin, Z.; Ming-jun, L.; Kai-ying, W.; Lin, W. Hybrid interval uncertain multi-attribute decision making based on set pair analysis. In Proceedings of the International Conference on Mechatronic Science, Electric Engineering and Computer (MEC), Jilin, China, 19–22 August 2011; pp. 938–941. [Google Scholar]
- Du, P.; Liu, H. Study on air combat tactics decision-making based on bayesian networks. In Proceedings of the 2nd IEEE International Conference on Information Management and Engineering, Chengdu, China, 16–18 April 2010; pp. 252–256. [Google Scholar]
- Mushtaq, S.A.; Sajjadand, A.; Razzaq, S. Decision making framework with stochastic dynamicity: A step forward towards SDN. Procedia Comput. Sci. 2014, 34, 188–195. [Google Scholar] [CrossRef][Green Version]
- Belzner, L.; Gabor, T. Bayesian Verification under Model Uncertainty. In Proceedings of the IEEE/ACM 3rd International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS), Buenos Aires, Argentina, 21 May 2017; pp. 10–13. [Google Scholar]
- Carrera, A.; Alonso, E.; Iglesias, C.A. A Bayesian Argumentation Framework for Distributed Fault Diagnosis in Telecommunication Networks. Sensors 2019, 19, 3408. [Google Scholar] [CrossRef] [PubMed]
- Kim, Y.J.; Ahn, K.U.; Park, C.S. Decision making of HVAC system using Bayesian Markov chain Monte Carlo method. Energy Build. 2014, 72, 112–121. [Google Scholar] [CrossRef]
- Cámara, J.; Peng, W.; Garlan, D.; Schmerl, B. Reasoning about sensing uncertainty and its reduction in decision-making for self-adaptation. Sci. Comput. Program. 2018, 167, 51–69. [Google Scholar] [CrossRef]
- Mukherjee, R. Selection of Sustainable Process and Essential Indicators for Decision Making Using Machine Learning Algorithms. Process Integr. Optim. Sustain. 2017, 1, 153–163. [Google Scholar] [CrossRef]
- de Medeiros, T.H.; Rocha, H.P.; Torres, F.S.; Takahashi, R.H.C.; Braga, A.P. Multi-objective Decision in Machine Learning. J. Control. Autom. Electr. Syst. 2017, 28, 217–227. [Google Scholar] [CrossRef]
- Kondratenko, Y.P.; Kozlov, O.V.; Korobko, O.V. Two Modifications of the Automatic Rule Base Synthesis for Fuzzy Control and Decision Making Systems. In Information Processing and Management of Uncertainty in Knowledge-Based Systems. Theory and Foundations; Medina, J., Ojeda-Aciego, M., Verdegay, J.L., Pelta, D.A., Cabrera, I.P., Bouchon-Meunier, B., Yager, R.R., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 570–582. [Google Scholar]
- Pynadath, D.V.; Barnes, M.J.; Wang, N.; Chen, J.Y.C. Transparency Communication for Machine Learning in Human-Automation Interaction. In Human and Machine Learning: Visible, Explainable, Trustworthy and Transparent; Springer International Publishing: Cham, Switzerland, 2018; pp. 75–90. [Google Scholar]
- Dilli, R.; Argou, A.; Reiser, R.; Yamin, A. IoT Resources Ranking: Decision Making Under Uncertainty Combining Machine Learning and Fuzzy Logic. In Communications in Computer and Information Science; Springer: Cham, Switzerland, 2018; Volume 831, pp. 119–131. [Google Scholar]
- Cao, K.; Wang, G.; Han, D.; Ning, J.; Zhang, X. Classification of Uncertain Data Streams Based on Extreme Learning Machine. Cogn. Comput. 2015, 7, 150–160. [Google Scholar] [CrossRef]
- Saleem, M.S.; Ding, C.; Liu, X.; Chi, C.H. Personalized Decision Making for QoS-Based Service Selection. In Proceedings of the IEEE International Conference on Web Services, Anchorage, AK, USA, 27 June–2 July 2014; pp. 17–24. [Google Scholar]
- Arif, M.; Kiani, A.K.; Qadir, J. Machine learning based optimized live virtual machine migration over WAN links. Telecommun. Syst. 2017, 64, 245–257. [Google Scholar] [CrossRef]
- Jamshidi, P.; Pahl, C.; Mendonca, N.C. Managing Uncertainty in Autonomic Cloud Elasticity Controllers. IEEE Cloud Comput. 2016, 3, 50–60. [Google Scholar] [CrossRef]
- Klus, R.; Klus, L.; Solomitckii, D.; Talvitie, J.; Valkama, M. Deep Learning-Based Cell-Level and Beam-Level Mobility Management System. Sensors 2020, 20, 7124. [Google Scholar] [CrossRef] [PubMed]
- Duchesne, L.; Karangelos, E.; Wehenkel, L. Machine learning of real-time power systems reliability management response. In Proceedings of the IEEE Manchester PowerTech, Manchester, UK, 18–22 June 2017; pp. 1–6. [Google Scholar]
- Tulabandhula, T.; Rudin, C. On combining machine learning with decision making. Mach. Learn. 2014, 97, 33–64. [Google Scholar] [CrossRef]
- Gomez Fernandez, M.; Tokuhiro, A.; Welter, K.; Wu, Q. Nuclear energy systems behavior and decision making using machine learning. Nucl. Eng. Des. 2017, 324, 27–34. [Google Scholar] [CrossRef]
- Luck, L.; Moser, A. Combining Machine Learning and Multi Criteria Decision Analysis Modeling Regulatory, Economic and Social Influences on Wind Turbine Allocation. In Proceedings of the 15th International Conference on the European Energy Market (EEM), Lodz, Poland, 27–29 June 2018; pp. 1–5. [Google Scholar]
- Cheng, S.; Xu, Y.; Zong, R.; Wang, C. A fast decision making method for mandatory lane change using kernel extreme learning machine. Int. J. Mach. Learn. Cybern. 2019, 10, 3363–3369. [Google Scholar] [CrossRef]
- Wu, X.; Xu, X.; Li, X.; Li, K.; Jiang, B. A kernel-based extreme learning modeling method for speed decision making of autonomous land vehicles. In Proceedings of the 6th Data Driven Control and Learning Systems (DDCLS), Chongqing, China, 26–27 May 2017; pp. 769–775. [Google Scholar]
- Hongmei, H.; McGinnity, T.M.; Coleman, S.; Gardiner, B. Linguistic Decision Making for Robot Route Learning. IEEE Trans. Neural Networks Learn. Syst. 2014, 25, 203–215. [Google Scholar]
- Kouppas, C.; Meng, Q.; King, M.; Majoe, D. Machine learning comparison for step decision making of a bipedal robot. In Proceedings of the 3rd International Conference on Control and Robotics Engineering (ICCRE), Nagoya, Japan, 20–23 April 2018; pp. 21–25. [Google Scholar]
- Samadi Gharajeh, M.; Jond, H.B. Speed Control for Leader-Follower Robot Formation Using Fuzzy System and Supervised Machine Learning. Sensors 2021, 21, 3433. [Google Scholar] [CrossRef]
- Aydoğan, R.; Marsa-Maestre, I.; Klein, M.; Jonker, C.M. A Machine Learning Approach for Mechanism Selection in Complex Negotiations. J. Syst. Sci. Syst. Eng. 2018, 27, 134–155. [Google Scholar] [CrossRef]
- Gross, K.C.; Baclawski, K.; Chan, E.S.; Gawlick, D.; Ghoneimy, A.; Liu, Z.H. A supervisory control loop with Prognostics for human-in-the-loop decision support and control applications. In Proceedings of the IEEE Conference on Cognitive and Computational Aspects of Situation Management (CogSIMA), Savannah, GA, USA, 27–31 March 2017; pp. 1–7. [Google Scholar]
- Vidhate, D.A.; Kulkarni, P. Improved decision making in multiagent system for diagnostic application using cooperative learning algorithms. Int. J. Inf. Technol. 2018, 10, 201–209. [Google Scholar] [CrossRef]
- Bhat, M.; Shumaiev, K.; Biesdorf, A.; Hohenstein, U.; Matthes, F. Automatic extraction of design decisions from issue management systems: A machine learning based approach. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2017; Volume 10475, pp. 138–154. [Google Scholar]
- Lombardi, M.; Milano, M.; Bartolini, A. Empirical decision model learning. Artif. Intell. 2017, 244, 343–367. [Google Scholar] [CrossRef]
- Ramchandani, P.; Paich, M.; Rao, A. Incorporating Learning into Decision Making in Agent Based Models. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2017; Volume 10423, pp. 789–800. [Google Scholar]
- Vidhate, D.A.; Kulkarni, P. Performance enhancement of cooperative learning algorithms by improved decision making for context based application. In Proceedings of the International Conference on Automatic Control and Dynamic Optimization Techniques (ICACDOT), Pune, India, 9–10 September 2016; pp. 246–252. [Google Scholar]
- Di Capua, M.; Petrosino, A. A Deep Learning Approach to Deal with Data Uncertainty in Sentiment Analysis. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2017; Volume 10147, pp. 172–184. [Google Scholar]
- Es-Soufi, W.; Yahia, E.; Roucoules, L. On the Use of Process Mining and Machine Learning to Support Decision Making in Systems Design. In IFIP Advances in Information and Communication Technology; Springer: Cham, Switzerland, 2016; Volume 492, pp. 56–66. [Google Scholar]
- Cook, A.; Wu, P.; Mengersen, K. Machine Learning and Visual Analytics for Consulting Business Decision Support. In Proceedings of the Big Data Visual Analytics (BDVA), Hobart, TAS, Australia, 22–25 September 2015; pp. 1–2. [Google Scholar]
- Lyubchyk, L.; Grinberg, G. Pairwise kernel-based preference learning for multiple criteria decision making. In Proceedings of the IEEE First Ukraine Conference on Electrical and Computer Engineering (UKRCON), Kyiv, UKraine, 29 May–2 June 2017; pp. 818–821. [Google Scholar]
- Spychalski, P.; Arendt, R. Machine Learning in Multi-Agent Systems using Associative Arrays. Parallel Comput. 2018, 75, 88–99. [Google Scholar] [CrossRef]
- Czarnecki, W.M.; Podolak, I.T. Machine Learning with Known Input Data Uncertainty Measure. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2013; Volume 8104, pp. 379–388. [Google Scholar]
- Feng, D.; Rosenbaum, L.; Dietmayer, K. Towards Safe Autonomous Driving: Capture Uncertainty in the Deep Neural Network For Lidar 3D Vehicle Detection. In Proceedings of the 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 3266–3273. [Google Scholar]
- Isobe, S.; Arai, S. Inference with model uncertainty on indoor scene for semantic segmentation. In Proceedings of the IEEE Global Conference on Signal and Information Processing (GlobalSIP), Montreal, QC, Canada, 14–16 November 2017; pp. 1170–1174. [Google Scholar]
- Shafaei, S.; Kugele, S.; Osman, M.H.; Knoll, A. Uncertainty in machine learning: A safety perspective on autonomous driving. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2018; Volume 11094, pp. 458–464. [Google Scholar]
- Ayeldeen, H.; Shaker, O.; Ayeldeen, G.; Anwar, K.M. Prediction of liver fibrosis stages by machine learning model: A decision tree approach. In Proceedings of the Third World Conference on Complex Systems (WCCS), Marrakech, Morocco, 23–25 November 2015; pp. 1–6. [Google Scholar]
- Donsa, K.; Spat, S.; Beck, P.; Pieber, T.R.; Holzinger, A. Towards Personalization of Diabetes Therapy Using Computerized Decision Support and Machine Learning: Some Open Problems and Challenges. In Smart Health: Open Problems and Future Challenges; Springer International Publishing: Cham, Switzerland, 2015; pp. 237–260. [Google Scholar]
- Eremeev, A.; Ivliev, S.; Vagin, V. Using Nosql Databases and Machine Learning for Implementation of Intelligent Decision System in Complex Vision Patalogies. In Proceedings of the 3rd Russian-Pacific Conference on Computer Technology and Applications (RPC), Vladivostok, Russia, 18–25 August 2018; pp. 1–4. [Google Scholar]
- Wu, D.D.; Zheng, L.; Olson, D.L. A Decision Support Approach for Online Stock Forum Sentiment Analysis. IEEE Trans. Syst. Man, Cybern. Syst. 2014, 44, 1077–1087. [Google Scholar] [CrossRef]
- Swierczyska, D.; Stach, T.; Pelc, M. Toward a Framework for Evaluation of Cache-Based Decision Making Process. In Proceedings of the 23rd International Conference on Methods & Models in Automation & Robotics (MMAR), Miedzyzdroje, Poland, 27–30 August 2018; pp. 855–858. [Google Scholar]
- Thangavel, S.K.; Bkaratki, P.D.; Sankar, A. Student placement analyzer: A recommendation system using machine learning. In Proceedings of the 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017; pp. 1–5. [Google Scholar]
- Nieto, Y.; García-Díaz, V.; Montenegro, C.; Crespo, R.G. Supporting academic decision making at higher educational institutions using machine learning-based algorithms. Soft Comput. 2018, 23, 4145–4153. [Google Scholar] [CrossRef]
- Jin, X. Research on Command Decision Support System AI Problem Decomposition. In Proceedings of the 10th International Conference on Intelligent Human-Machine Systems and Cybernetics (IHMSC), Hangzhou, China, 25–26 August 2018; Volume 2, pp. 96–100. [Google Scholar]
- Trehan, S.; Durlofsky, L.J. Machine-learning-based modeling of coarse-scale error, with application to uncertainty quantification. Comput. Geosci. 2018, 22, 1093–1113. [Google Scholar] [CrossRef]
- Shi, L.; Liu, S.; Hao, J.; Koh, J.Y.; Hou, Z.; Dong, J.S. Towards Solving Decision Making Problems Using Probabilistic Model Checking. In Proceedings of the 22nd International Conference on Engineering of Complex Computer Systems (ICECCS), Fukuoka, Japan, 5–8 November 2017; pp. 150–153. [Google Scholar]
- Zhou, Q.; Huang, Z. A Decision-Making Method Using Knowledge-Based Machine Learning. In Proceedings of the International Conference on Computer Science and Electronics Engineering (ICCSEE), Hangzhou, China, 23–25 March 2012; Volume 3, pp. 616–620. [Google Scholar]
- Haldenwang, N.; Ihler, K.; Kniephoff, J.; Vornberger, O. A comparative study of uncertainty based active learning strategies for general purpose twitter sentiment analysis with deep neural networks. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2018; Volume 10713, pp. 208–215. [Google Scholar]
- Chowdhury, A.; Raut, S.A.; Narman, H.S. DA-DRLS: Drift adaptive deep reinforcement learning based scheduling for IoT resource management. J. Netw. Comput. Appl. 2019, 138, 51–65. [Google Scholar] [CrossRef]
- Mazied, E.A.; ElNainay, M.Y.; Abdel-Rahman, M.J.; Midkiff, S.F.; Rizk, M.R.M.; Rakha, H.A.; MacKenzie, A.B. The wireless control plane: An overview and directions for future research. J. Netw. Comput. Appl. 2019, 126, 104–122. [Google Scholar] [CrossRef]
- Boushaba, M.; Hafid, A.; Gendreau, M. Node stability-based routing in Wireless Mesh Networks. J. Netw. Comput. Appl. 2017, 93, 1–12. [Google Scholar] [CrossRef]
- Peters, M.; Ketter, W.; Saar-Tsechansky, M.; Collins, J. A reinforcement learning approach to autonomous decision-making in smart electricity markets. Mach. Learn. 2013, 92, 5–39. [Google Scholar] [CrossRef]
- Rodriguez-Fernandez, J.; Pinto, T.; Silva, F.; Praça, I.; Vale, Z.; Corchado, J. Context aware Q-Learning-based model for decision support in the negotiation of energy contracts. Int. J. Electr. Power Energy Syst. 2019, 104, 489–501. [Google Scholar] [CrossRef]
- Zheng, R.; Liu, C.; Guo, Q. A decision-making method for autonomous vehicles based on simulation and reinforcement learning. In Proceedings of the International Conference on Machine Learning and Cybernetics, Tianjin, China, 14–17 July 2013; pp. 362–369. [Google Scholar]
- Mirchevska, B.; Pek, C.; Werling, M.; Althoff, M.; Boedecker, J. High-level Decision Making for Safe and Reasonable Autonomous Lane Changing using Reinforcement Learning. In Proceedings of the 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 2156–2162. [Google Scholar]
- Leonetti, M.; Iocchi, L.; Stone, P. A synthesis of automated planning and reinforcement learning for efficient, robust decision-making. Artif. Intell. 2016, 241, 103–130. [Google Scholar] [CrossRef]
- Liang, H.; Yang, L.; Cheng, H.; Tu, W.; Xu, M. Human-in-the-loop reinforcement learning. In Proceedings of the Chinese Automation Congress (CAC), Jinan, China, 20–22 October 2017; pp. 4511–4518. [Google Scholar]
- Khayut, B.; Fabri, L.; Avikhana, M. Modeling of computational perception of reality, situational awareness, cognition and machine learning under uncertainty. In Proceedings of the Intelligent Systems Conference (IntelliSys), London, UK, 7–8 September 2017; pp. 331–340. [Google Scholar]
- Castaño, F.; Strzelczak, S.; Villalonga, A.; Haber, R.E.; Kossakowska, J. Sensor Reliability in Cyber-Physical Systems Using Internet-of-Things Data: A Review and Case Study. Remote Sens. 2019, 11, 2252. [Google Scholar] [CrossRef]
- Gavirangaswamy, V.B.; Gupta, A.A.; Gupta, A.A. A parallel implementation of reinforced learning model used in analyzing risky decision making. In Proceedings of the International Conference on High Performance Computing & Simulation (HPCS), Innsbruck, Austria, 18–22 July 2016; pp. 940–946. [Google Scholar]
- Doltsinis, S.; Ferreira, P.; Lohse, N. A Symbiotic Human-Machine Learning Approach for Production Ramp-up. IEEE Trans. Hum. Mach. Syst. 2018, 48, 229–240. [Google Scholar] [CrossRef]
- Shin, J.; Lee, J.H. Multi-timescale, multi-period decision-making model development by combining reinforcement learning and mathematical programming. Comput. Chem. Eng. 2019, 121, 556–573. [Google Scholar] [CrossRef]
- Akiyama, H.; Tsuji, M.; Aramaki, S. Learning Evaluation Function for Decision Making of Soccer Agents Using Learning to Rank. In Proceedings of the Joint 8th International Conference on Soft Computing and Intelligent Systems (SCIS) and 17th International Symposium on Advanced Intelligent Systems (ISIS), Sapporo, Japan, 25–28 August 2016; pp. 239–242. [Google Scholar]
- Villalonga, A.; Beruvides, G.; Castaño, F.; Haber, R.E. Cloud-Based Industrial Cyber–Physical System for Data-Driven Reasoning: A Review and Use Case on an Industry 4.0 Pilot Line. IEEE Trans. Ind. Inform. 2020, 16, 5975–5984. [Google Scholar] [CrossRef]
- Ravì, D.; Wong, C.; Lo, B.; Yang, G. A Deep Learning Approach to on-Node Sensor Data Analytics for Mobile or Wearable Devices. IEEE J. Biomed. Health Inform. 2017, 21, 56–64. [Google Scholar] [CrossRef]
- Sun, H.; Chen, X.; Shi, Q.; Hong, M.; Fu, X.; Sidiropoulos, N.D. Learning to optimize: Training deep neural networks for wireless resource management. In Proceedings of the IEEE 18th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Sapporo, Japan, 3–6 July 2017; pp. 1–6. [Google Scholar]
- Ravi, D.; Wong, C.; Lo, B.; Yang, G. Deep learning for human activity recognition: A resource efficient implementation on low-power devices. In Proceedings of the IEEE 13th International Conference on Wearable and Implantable Body Sensor Networks (BSN), San Francisco, CA, USA, 14–17 June 2016; pp. 71–76. [Google Scholar]
- Liu, M.; Song, T.; Hu, J.; Yang, J.; Gui, G. Deep Learning-Inspired Message Passing Algorithm for Efficient Resource Allocation in Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2019, 68, 641–653. [Google Scholar] [CrossRef]
- He, Y.; Yu, F.R.; Zhao, N.; Leung, V.C.M.; Yin, H. Software-Defined Networks with Mobile Edge Computing and Caching for Smart Cities: A Big Data Deep Reinforcement Learning Approach. IEEE Commun. Mag. 2017, 55, 31–37. [Google Scholar] [CrossRef]
- Ziaeefard, M.; Bergevin, R.; Lalonde, J.F. Deep Uncertainty Interpretation in Dyadic Human Activity Prediction. In Proceedings of the 16th IEEE International Conference on Machine Learning and Applications (ICMLA), Cancun, Mexico, 18–21 December 2017; pp. 822–825. [Google Scholar]
- Zheng, R.; Greenberg, K. Effective Design in Human and Machine Learning: A Cognitive Perspective. In Human and Machine Learning: Visible, Explainable, Trustworthy and Transparent; Springer: Cham, Switzerland, 2018; pp. 55–74. [Google Scholar]
- Wakatsuki, M.; Fujimura, M.; Nishino, T. A Decision Making Method Based on Society of Mind Theory in Multi-player Imperfect Information Games. In Proceedings of the 3rd International Conference on Applied Computing and Information Technology/2nd International Conference on Computational Science and Intelligence, Okayama, Japan, 12–16 July 2015; pp. 67–72. [Google Scholar]
- Zhao, X.; Chen, F.; Cho, J.H. Deep Learning Based Scalable Inference of Uncertain Opinions. In Proceedings of the IEEE International Conference on Data Mining (ICDM), Singapore, 17–20 November 2018; pp. 807–816. [Google Scholar]
- Zhang, Y.; Zu, W.; Gao, Y.; Chang, H. Research on autonomous maneuvering decision of UCAV based on deep reinforcement learning. In Proceedings of the Chinese Control And Decision Conference (CCDC), Shenyang, China, 9–11 June 2018; pp. 230–235. [Google Scholar]
- Kendall, A.; Cipolla, R. Modelling uncertainty in deep learning for camera relocalization. In Proceedings of the IEEE International Conference on Robotics and Automation (ICRA), Stockholm, Sweden, 16–21 May 2016; pp. 4762–4769. [Google Scholar]
- Hoblitzell, A.; Babbar-Sebens, M.; Mukhopadhyay, S. Uncertainty-Based Deep Learning Networks for Limited Data Wetland User Models. In Proceedings of the IEEE International Conference on Artificial Intelligence and Virtual Reality (AIVR), Taichung, Taiwan, 10–12 December 2018; pp. 19–26. [Google Scholar]
- Pan, H.; Gui, G.; Lin, Z.; Yan, C. Deep BBN Learning for Health Assessment toward Decision-Making on Structures under Uncertainties. KSCE J. Civ. Eng. 2018, 22, 928–940. [Google Scholar] [CrossRef]
- Kratzwald, B.; Ilić, S.; Kraus, M.; Feuerriegel, S.; Prendinger, H. Deep learning for affective computing: Text-based emotion recognition in decision support. Decis. Support Syst. 2018, 115, 24–35. [Google Scholar] [CrossRef]
- Dilokthanakul, N.; Shanahan, M. Deep Reinforcement Learning with Risk-Seeking Exploration. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2018; Volume 10994, pp. 201–211. [Google Scholar]
- Brando, A.; Rodríguez-Serrano, J.A.; Ciprian, M.; Maestre, R.; Vitrià, J. Uncertainty Modelling in Deep Networks: Forecasting Short and Noisy Series. In Machine Learning and Knowledge Discovery in Databases; Springer International Publishing: Cham, Switzerland, 2019; pp. 325–340. [Google Scholar]
- Cho, C.; Choi, W.; Kim, T. Leveraging Uncertainties in Softmax Decision-Making Models for Low-Power IoT Devices. Sensors 2020, 20, 4603. [Google Scholar] [CrossRef]
- Le, M.T.; Diehl, F.; Brunner, T.; Knol, A. Uncertainty Estimation for Deep Neural Object Detectors in Safety-Critical Applications. In Proceedings of the 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 3873–3878. [Google Scholar]
- Ashton, K. That ’Internet of Things’ thing in the real world, things matter more than ideas. RFID J. 2009, 22, 97–114. [Google Scholar]
- Ken, S.A.F.; Eldor, S.R.M.; Guillemin, W.C.H.; Paul, Y.W.K.; Armstrong, C.D.; Smith, I.G.; Kim, Y.-W.; Chartier, C.P.; Armstrong, L.D. RFID and the Inclusive Model for the Internet of Things. Available online: https://docbox.etsi.org/zArchive/TISPAN/Open/IoT/low%20resolution/www.rfidglobal.eu%20CASAGRAS%20IoT%20Final%20Report%20low%20resolution.pdf (accessed on 6 January 2021).
- Cearley, D.; Burke, B.; Furlonger, D.; Kandaswamy, R.; Litan, A. Top 10 Strategic Technology Trends for 2019; Technical Report March 2019; Gartner: Stamford, USA, 2019. [Google Scholar]
- Gorecky, D.; Schmitt, M.; Loskyll, M.; Zuhlke, D. Human-machine-interaction in the industry 4.0 era. In Proceedings of the 12th IEEE International Conference on Industrial Informatics (INDIN), Porto Alegre, Brazil, 27–30 July 2014; pp. 289–294. [Google Scholar]
- Ma, Y.W.; Chen, Y.C.; Chen, J.L. SDN-enabled network virtualization for industry 4.0 based on IoTs and cloud computing. In Proceedings of the 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, South Korea, 19–22 February 2017; pp. 199–202. [Google Scholar]
- Zeng, P.; Wang, Z.; Jia, Z.; Kong, L.; Li, D.; Jin, X. Time-slotted software-defined Industrial Ethernet for real-time Quality of Service in Industry 4.0. Future Gener. Comput. Syst. 2019, 99, 1–10. [Google Scholar] [CrossRef]
- Thames, L.; Schaefer, D. Software-defined Cloud Manufacturing for Industry 4.0. Procedia CIRP 2016, 52, 12–17. [Google Scholar] [CrossRef]
- Fraile, F.; Flores, J.L.; Poler, R.; Saiz, E. Software-Defined Networking to Improve Cybersecurity in Manufacturing Oriented Interoperability Ecosystems. In Enterprise Interoperability VIII; Springer: Berlin, Germany, 19–23 March 2018; pp. 31–41. [Google Scholar]
- Wan, J.; Tang, S.; Shu, Z.; Li, D.; Wang, S.; Imran, M.; Vasilakos, A. Software-Defined Industrial Internet of Things in the Context of Industry 4.0. IEEE Sens. J. 2016, 16, 7373–7380. [Google Scholar] [CrossRef]
- Villalonga, A.; Negri, E.; Biscardo, G.; Castano, F.; Haber, R.E.; Fumagalli, L.; Macchi, M. A decision-making framework for dynamic scheduling of cyber-physical production systems based on digital twins. Annu. Rev. Control. 2021. [Google Scholar] [CrossRef]
- Lacan, J. Seminaire 20: Encore. 1972–1973. Available online: http://staferla.free.fr/S20/S20/20ENCORE.pdf (accessed on 22 April 2021).
- Lacan, J. Seminaire 22: R. S. I. 1974–1975. Available online: http://staferla.free.fr/S22/S22/20R.S.I..pdf (accessed on 24 April 2021).
- Bailly, L. Lacan: A Beginner’s Guide; Oneworld Publications: London, UK, 2009. [Google Scholar]
- Contri, G.B. (Ed.) Lacan in Italia 1953–1978; Chapter Du Discours Psychanalytique; Available online: https://www.praxislacaniana.it/wordpress/download/lacan_in_italia.pdf (accessed on 25 April 2021).
- Norris, J.R. Markov Chains; Cambridge Series on Statistical & Probabilistic Mathematics; Cambridge University Press: Cambridge, UK, 1997. [Google Scholar]
- Krishnamurthy, V. Partially Observed Markov Decision Processes; Cambridge University Press: Cambridge, UK, 2016. [Google Scholar]
- Harsanyi, J. Games with Incomplete Information Played by Bayesian Players—Part I. Manag. Sci. 1967, 14, 159–183. [Google Scholar] [CrossRef]
- Harsanyi, J. Games with Incomplete Information Played by Bayesian Players—Part II. Manag. Sci. 1968, 14, 320–334. [Google Scholar] [CrossRef]
- Harsanyi, J. Games with Incomplete Information Played by Bayesian Players—Part III. Manag. Sci. 1968, 14, 486–502. [Google Scholar] [CrossRef]
- Osborne, M.J.; Rubinstein, A. A Course in Game Theory; MIT Press: Cambridge, MA, USA, 1994; ISBN 0-262-65040-1. [Google Scholar]
- Williams, D. Probability with Martingales; Cambridge University Press: Cambridge, UK, 1991. [Google Scholar]
- Deligkas, A.; Fearnley, J.; Savani, R.; Spirakis, P. Computing Approximate Nash Equilibria in Polymatrix Games. Algorithmica 2017, 72, 487–514. [Google Scholar] [CrossRef]
- Fotakis, D.; Gkatzelis, V.; Kaporis, A.; Spirakis, P. The Impact of Social Ignorance on Weighted Congestion Games. In Theory of Computing Systems; Springer: Berlin, Germany, 2012; pp. 559–578. [Google Scholar]
- Fotakis, D.; Kaporis, A.C.; Lianeas, T.; Spirakis, P.G. Resolving Braess’s Paradox in Random Networks. Algorithmica 2017, 78, 788–818. [Google Scholar] [CrossRef]
- Nikoletseas, S.; Panagopoulou, P.; Raptopoulos, C.; Spirakis, P. On the Structure of Equilibria in Basic Network Formation. Theor. Comput. Sci. 2015, 590, 96–105. [Google Scholar] [CrossRef]
- Freud, S. The Moses of Michelangelo. In The Standard Edition of the Complete Psychological Works of Sigmund Freud; Strachey, J., Ed.; Hogarth Press: London, UK, 1914; Volume XIV, pp. 211–238. [Google Scholar]
- Freud, S. Group Psychology and the Analysis of the Ego. In The Standard Edition of the Complete Psychological Works of Sigmund Freud; Strachey, J., Ed.; Hogarth Press: London, UK, 1921; Volume XVIII, pp. 67–143. [Google Scholar]
- Freud, S. Why War? In The Standard Edition of the Complete Psychological Works of Sigmund Freud; Strachey, J., Ed.; Hogarth Press: London, UK, 1933; Volume XXII, pp. 197–215. [Google Scholar]
- Freud, S. The Future of an Illusion. In The Standard Edition of the Complete Psychological Works of Sigmund Freud; Strachey, J., Ed.; Hogarth Press: London, UK, 1927; Volume XXI, pp. 3–56. [Google Scholar]
- Freud, S. Civilization and its Discontents. In The Standard Edition of the Complete Psychological Works of Sigmund Freud; Strachey, J., Ed.; Hogarth Press: London, UK, 1930; Volume XXI, pp. 59–145. [Google Scholar]
- Castro, J.C.L.D. Applications of the Lacanian theory of discourses in the field of Communication. Intercom Rev. Bras. Cienc. Comun. 2016, 39, 99–113. [Google Scholar] [CrossRef][Green Version]
- Bion, W.R. Elements of Psychoanalysis; Maresfield Library, Ed.; Karnac: London, UK, 1984. [Google Scholar]
- Bion, W.R. Learning from Experience; Maresfield Library, Ed.; Karnac: London, UK, 1994. [Google Scholar]
- Amazonas, J.R.A. From Thinking the Thought Towards Teach the Teaching. In Proceedings of the World Congress on Engineering and Technology Education, Guarujá and Santos, Brazil, 14–17 March 2004; pp. 121–123. [Google Scholar]
- Amazonas, J.R.A. Alpha-elements generation modelling in Web learning environments. In Proceedings of the GCETE’2005—Global Congress on Engineering and Technology Education, São Paulo, Brazil, 13–16 March 2005; pp. 100–103. [Google Scholar]
- Reddy, R.R.G.; Mamatha, C.; Reddy, R.R.G. A Review on Machine Learning Trends, Application and Challenges in Internet of Things. In Proceedings of the International Conference on Advances in Computing, Communications and Informatics (ICACCI), Bangalore, India, 19–22 September 2018; pp. 2389–2397. [Google Scholar]
- Djorgovski, S.G.; Mahabal, A.; Donalek, C.; Graham, M.; Drake, A.; Turmon, M.; Fuchs, T. Automated Real-Time Classification and Decision Making in Massive Data Streams from Synoptic Sky Surveys. In Proceedings of the IEEE 10th International Conference on e-Science, Sao Paulo, Brazil, 20–24 October 2014; pp. 204–211. [Google Scholar]
- Kartal, H.; Oztekin, A.; Gunasekaran, A.; Cebi, F. An integrated decision analytic framework of machine learning with multi-criteria decision making for multi-attribute inventory classification. Comput. Ind. Eng. 2016, 101, 599–613. [Google Scholar] [CrossRef]
- Lamata, M.T.; Pelta, D.A.; Verdegay, J.L. Fuzzy Information and Contexts for Designing Automatic Decision-Making Systems. In Advances in Artificial Intelligence; Springer International Publishing: Cham, Switzerland, 2018; pp. 174–183. [Google Scholar]
- Eremeev, A.P.; Kozhukhov, A.A. About the Integration of Learning and Decision-Making Models in Intelligent Systems of Real-Time. In Proceedings of the Third International Scientific Conference “Intelligent Information Technologies for Industry” (IITI’18), Cham, Switzerland, 17–21 September 2018; pp. 181–189. [Google Scholar]
- Tien, J.M. Internet of Things, Real-Time Decision Making, and Artificial Intelligence. Ann. Data Sci. 2017, 4, 149–178. [Google Scholar] [CrossRef]
- Cui, L.; Yang, S.; Chen, F.; Ming, Z.; Lu, N.; Qin, J. A survey on application of machine learning for Internet of Things. Int. J. Mach. Learn. Cybern. 2018, 9, 1399–1417. [Google Scholar] [CrossRef]
- Mahdavinejad, M.S.; Rezvan, M.; Barekatain, M.; Adibi, P.; Barnaghi, P.; Sheth, A.P. Machine learning for internet of things data analysis: A survey. Digit. Commun. Netw. 2018, 4, 161–175. [Google Scholar] [CrossRef]
- Shaukat, H.R.; Hashim, F.; Shaukat, M.A.; Ali Alezabi, K. Hybrid Multi-Level Detection and Mitigation of Clone Attacks in Mobile Wireless Sensor Network (MWSN). Sensors 2020, 20, 2283. [Google Scholar] [CrossRef]








| Work Area | Related Work | Key Points |
|---|---|---|
| IoT | [12,13,14,15,16,17,18,19] | Interoperability Data sources |
| Semantic Web | [11,20,21,22,23,24,25] | Association rules mining Ontological data Recommender systems Knowledge extraction |
| Industry 4.0 | [26,27] | Data marketplace Logistics infrastructure |
| Method | Related Work | Key Points |
|---|---|---|
| ELECTRE | [35,36,37] | Execution time optimization |
| PROMETHEE | [38,39,40,41] | Infrastructure construction Energy sector Engineering decision problems |
| AHP | [42,43,44] | Decision-making under uncertainty Recommendation systems |
| VIKOR | [45,46,47] | Sentiment analysis in social networks Performance evaluations |
| TOPSIS | [48,49,50] | Several combinations of methods |
| DEA | [51] | Evaluate relative efficiency |
| Method | Related Work | Key Points |
|---|---|---|
| Fuzzy logic | [38,45,58,59,60,61,62,63,64,65,66,67,68,69,70,71] | They handle diverse types of uncertainties |
| Game theory | [72,73,74,75] | Decision learning Decision-making |
| Bayesian networks | [76,77,78,79,80] | Decision-making under uncertainty |
| Stochastic process | [6,81,82] | Adaptive systems Context-aware decision process |
| Support vector machine | [83,84] | Sustainability indicators |
| Work Area | Related Work | Key Points |
|---|---|---|
| Telecommunications | [7,87,88,89,90,91,92] | Self-Organizing Network Improve QoS Virtual machine migration over WAN links 5G auto-configuration |
| Energy | [93,94,95,96] | Operations planning Behaviors nuclear energy system Power grid |
| Transport | [97,98,99,100,101] | Lane change Driving on rough terrains Robot mobility |
| Enhance decisions | [102,103,104,105] | Complex negotiations Combination of techniques Support for human decisions |
| Complex systems | [106,107,108,109] | Human behavior |
| Optimization problems | [84,110,111,112,113,114] | Deal with uncertainty |
| Work Area | Related Work | Key Points |
|---|---|---|
| Transport | [115,116,117] | Overcoming obstacles |
| Health | [118,119,120] | Improve diagnostic accuracy Decrease diagnostic times |
| Business decisions | [83,121,122,123,124] | Improve profits |
| Deal with uncertainty | [125,126,127,128,129] | Battlefield decision-making Geology decisions Gambling |
| Work Area | Realted Work | Key Points |
|---|---|---|
| Telecommunications | [130,131,132] | Resource management 5G Routing |
| Energy | [133,134] | Supply and demand balance |
| Transport | [135,136,137,138,139,140] | Autonomous driving Driving experience |
| Optimization problems | [141,142,143,144,145] | Noisy data Scalable solutions Data fitting Computational costs |
| Work Area | Realted Work | Key Points |
|---|---|---|
| Telecommunications | [146,147,148,149,150] | Resource allocation SDN |
| Human behavior | [151,152,153] | Behavior modeling Decision-making from psychology |
| Uncertainty | [154,155,156,157,158,159,160,161,162] | Noisy or incomplete data Decision-making under uncertainty |
| User 1 | User 2 |
|---|---|
|
|
| User 1 | User 2 | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Piece of user data | ||||||||||||
| 1 | 0.5 | 0.0 | 0.5 | 0.0 | 1 | 0 | 0.0 | 0.5 | 0.5 | 0.0 | 1 | 0 |
| 2 | 0.1 | 0.0 | 0.9 | 0.0 | 0 | 1 | 0.0 | 0.3 | 0.7 | 0.0 | 1 | 0 |
| 3 | 0.0 | 0.0 | 1.0 | 0.0 | 0 | 1 | 0.0 | 0.5 | 0.5 | 0.0 | 1 | 0 |
| 4 | 0.0 | 0.0 | 1.0 | 0.0 | 0 | 1 | 0.0 | 0.2 | 0.8 | 0.0 | 1 | 0 |
| mean E | 0.15 | 0.0 | 0.85 | 0.0 | 0.25 | 0.75 | 0.0 | 0.375 | 0.625 | 0.0 | 1 | 0 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alzate-Mejía, N.; Santos-Boada, G.; de Almeida-Amazonas, J.R. Decision-Making under Uncertainty for the Deployment of Future Hyperconnected Networks: A Survey. Sensors 2021, 21, 3791. https://doi.org/10.3390/s21113791
Alzate-Mejía N, Santos-Boada G, de Almeida-Amazonas JR. Decision-Making under Uncertainty for the Deployment of Future Hyperconnected Networks: A Survey. Sensors. 2021; 21(11):3791. https://doi.org/10.3390/s21113791
Chicago/Turabian StyleAlzate-Mejía, Néstor, Germán Santos-Boada, and José Roberto de Almeida-Amazonas. 2021. "Decision-Making under Uncertainty for the Deployment of Future Hyperconnected Networks: A Survey" Sensors 21, no. 11: 3791. https://doi.org/10.3390/s21113791
APA StyleAlzate-Mejía, N., Santos-Boada, G., & de Almeida-Amazonas, J. R. (2021). Decision-Making under Uncertainty for the Deployment of Future Hyperconnected Networks: A Survey. Sensors, 21(11), 3791. https://doi.org/10.3390/s21113791







