Diffusion Model of Preemptive-Resume Priority Systems and Its Application to Performance Evaluation of SDN Switches
Abstract
:1. Introduction and an Overview of Existing Results
2. Diffusion Single Station Models
2.1. First-In-First-Out G/G/1/N Station
2.2. Preemptive-Resume G/G/1/N/PRIOR Station
- : we consider the highest priority class alone and use the single class model presented in the previous section. The customers of lower classes are transparent for class; therefore, the solution is correct. .
- : we consider two classes, , determine , following (14), solve the diffusion equation with these parameters to obtain , which approximates the distribution of the joint number of customers of classes and ; we then compute .
- : we consider the system with three classes, to determine the parameters , following (14), solve the diffusion equation to obtain and , then, using of the previous step, compute , etc., until .
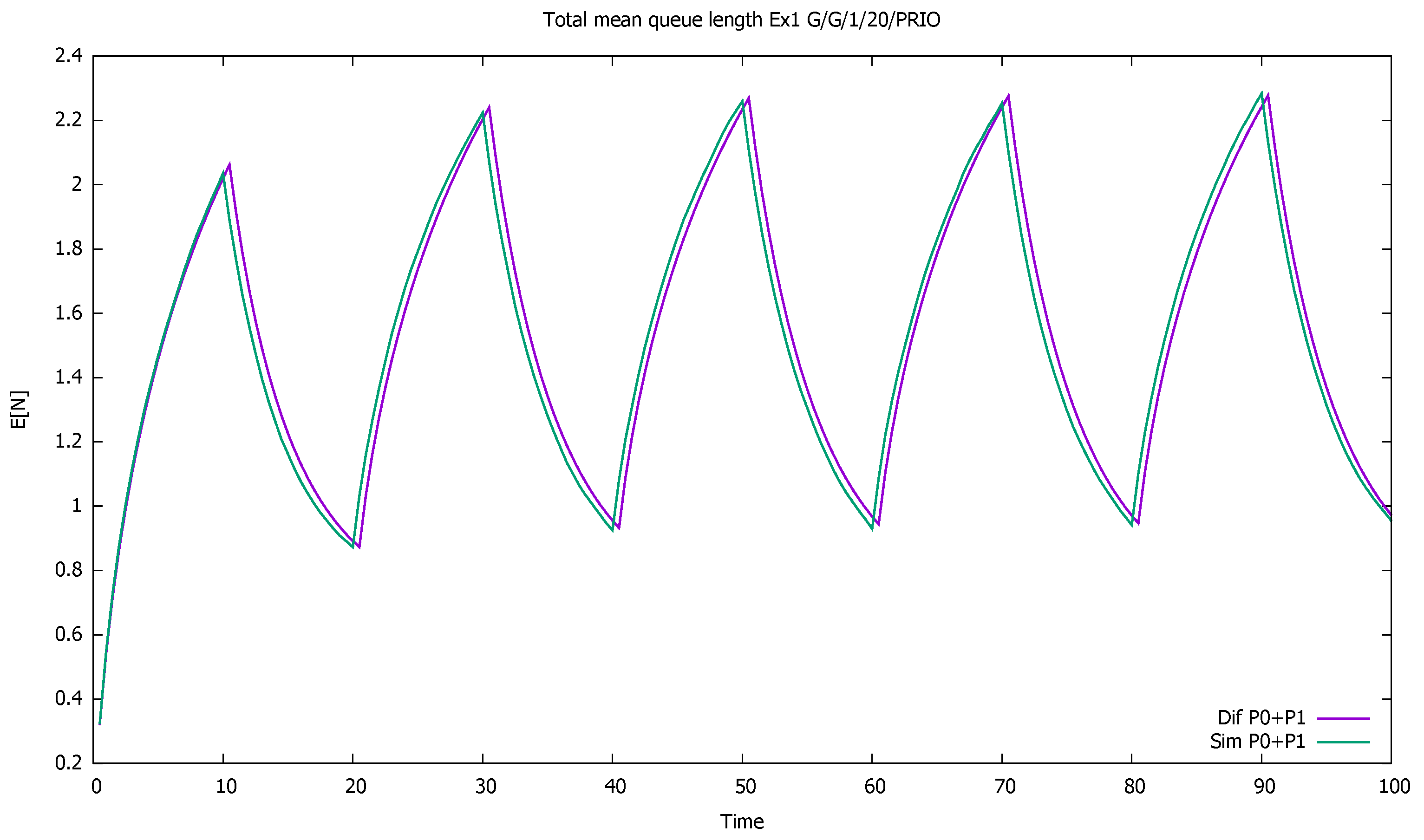
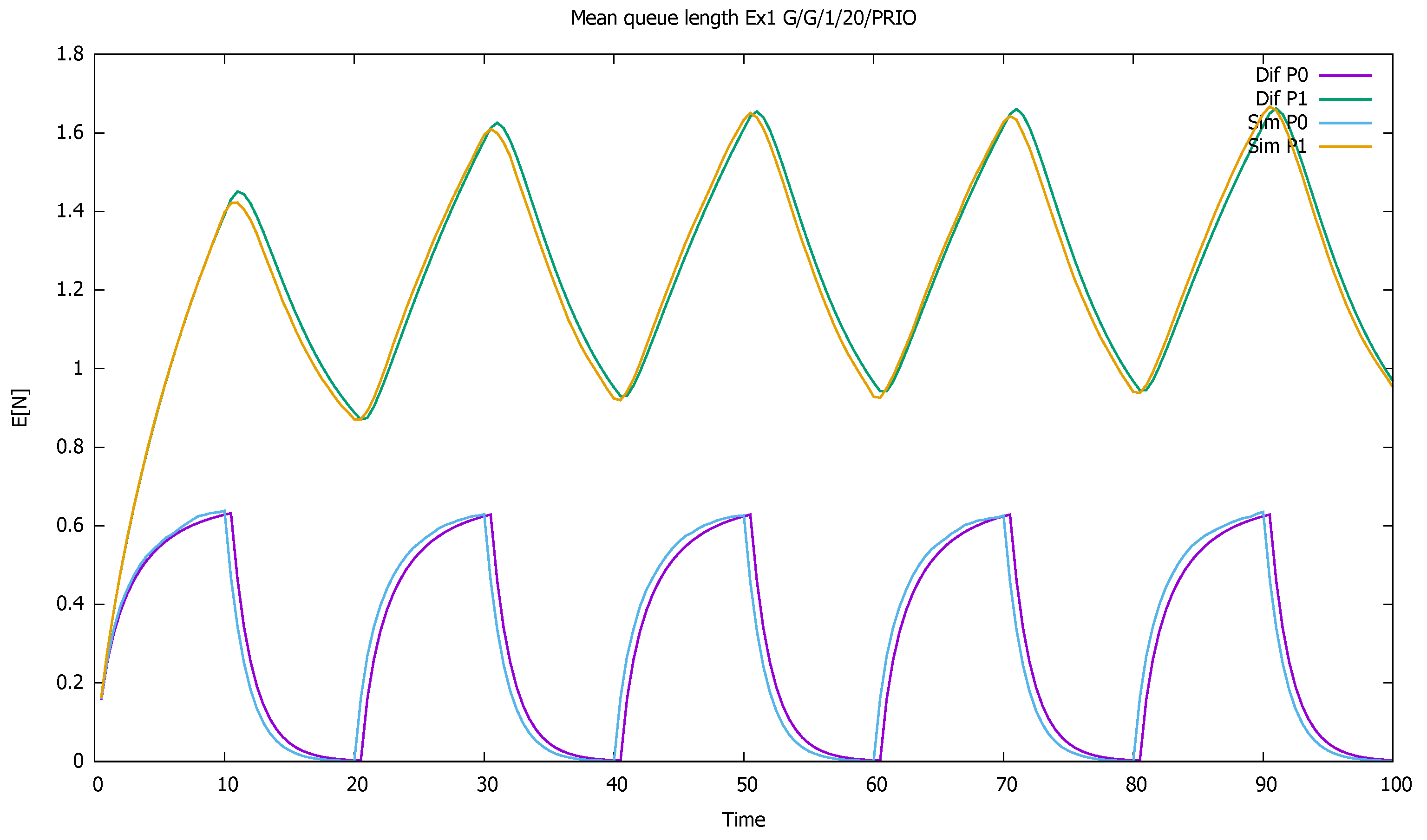
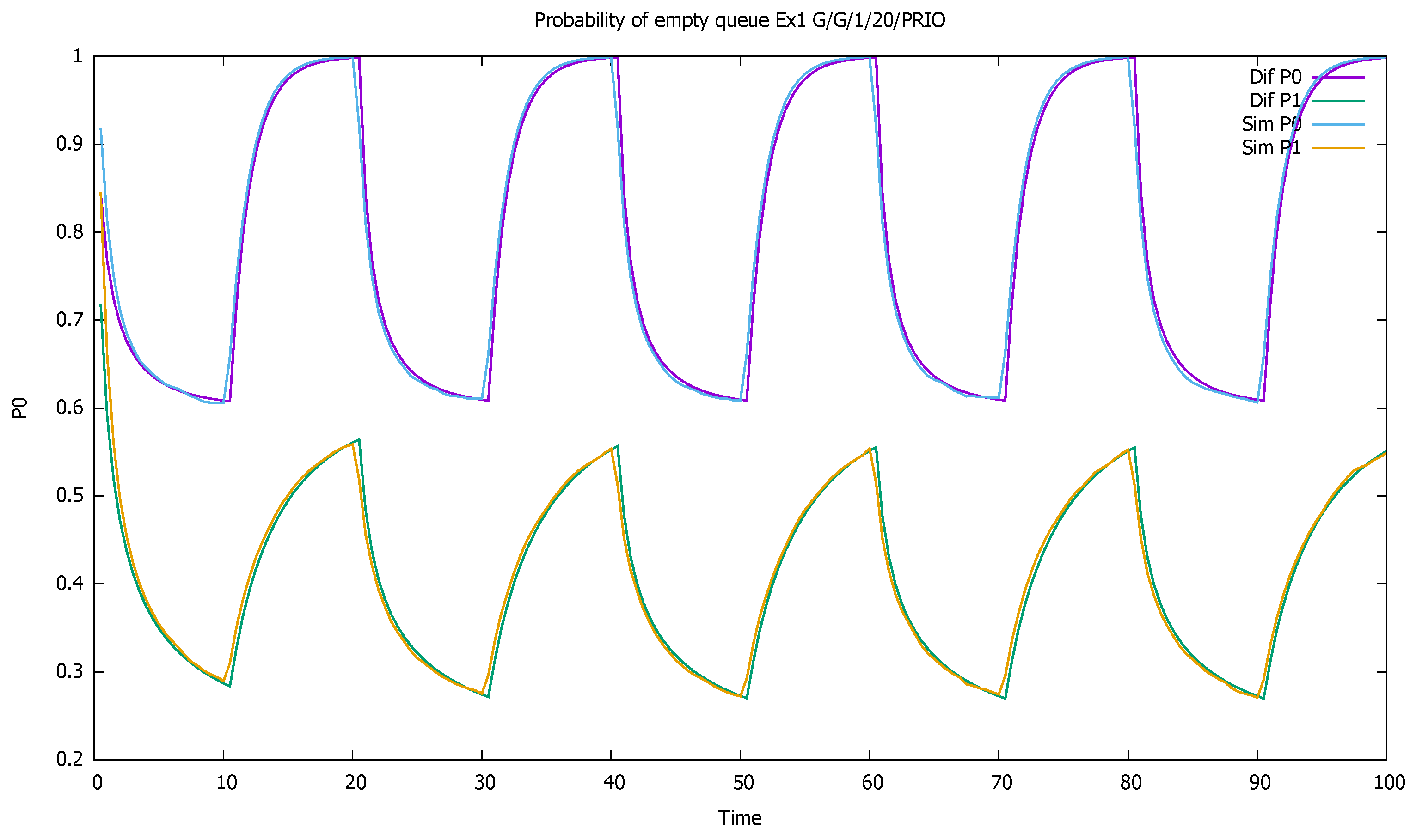
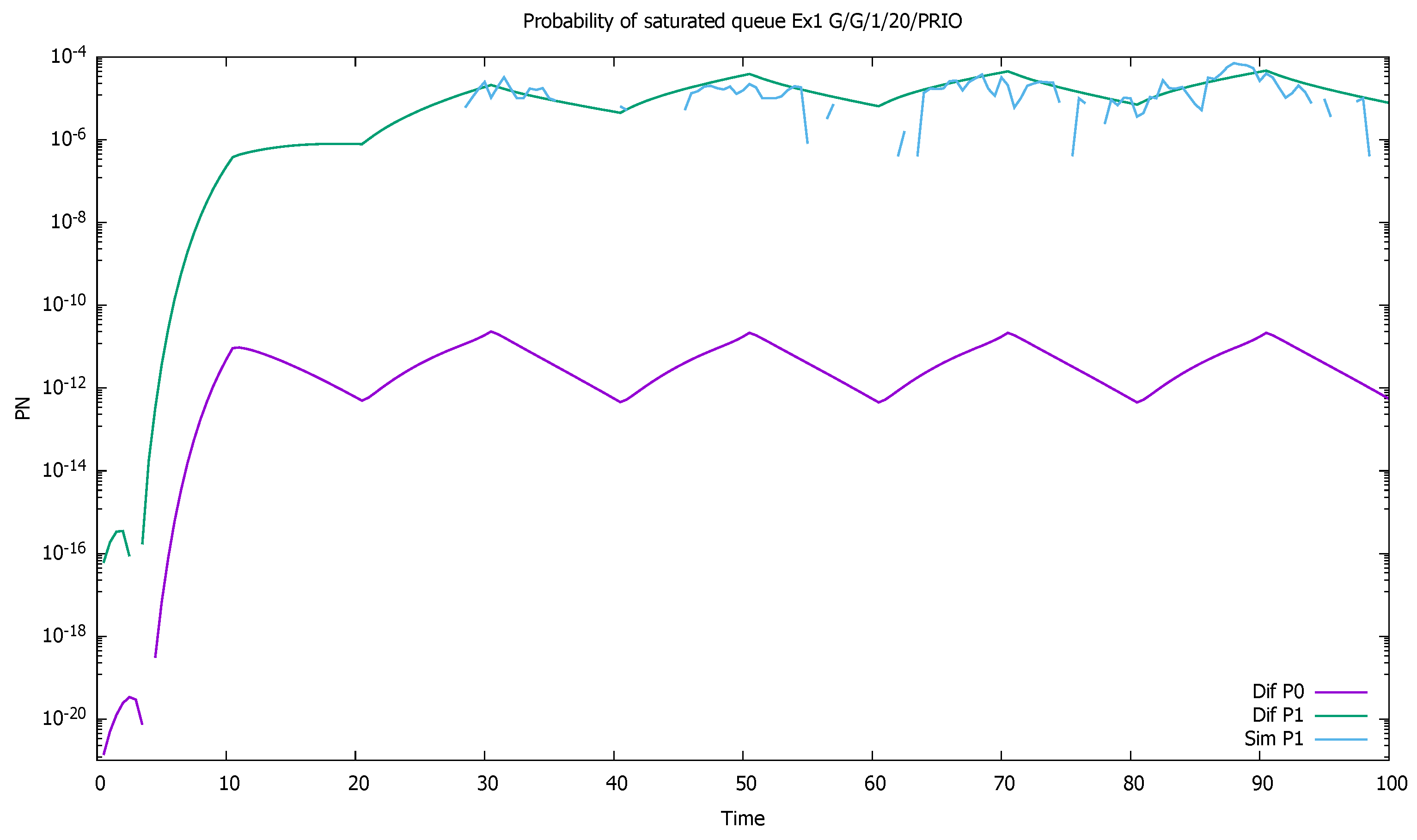
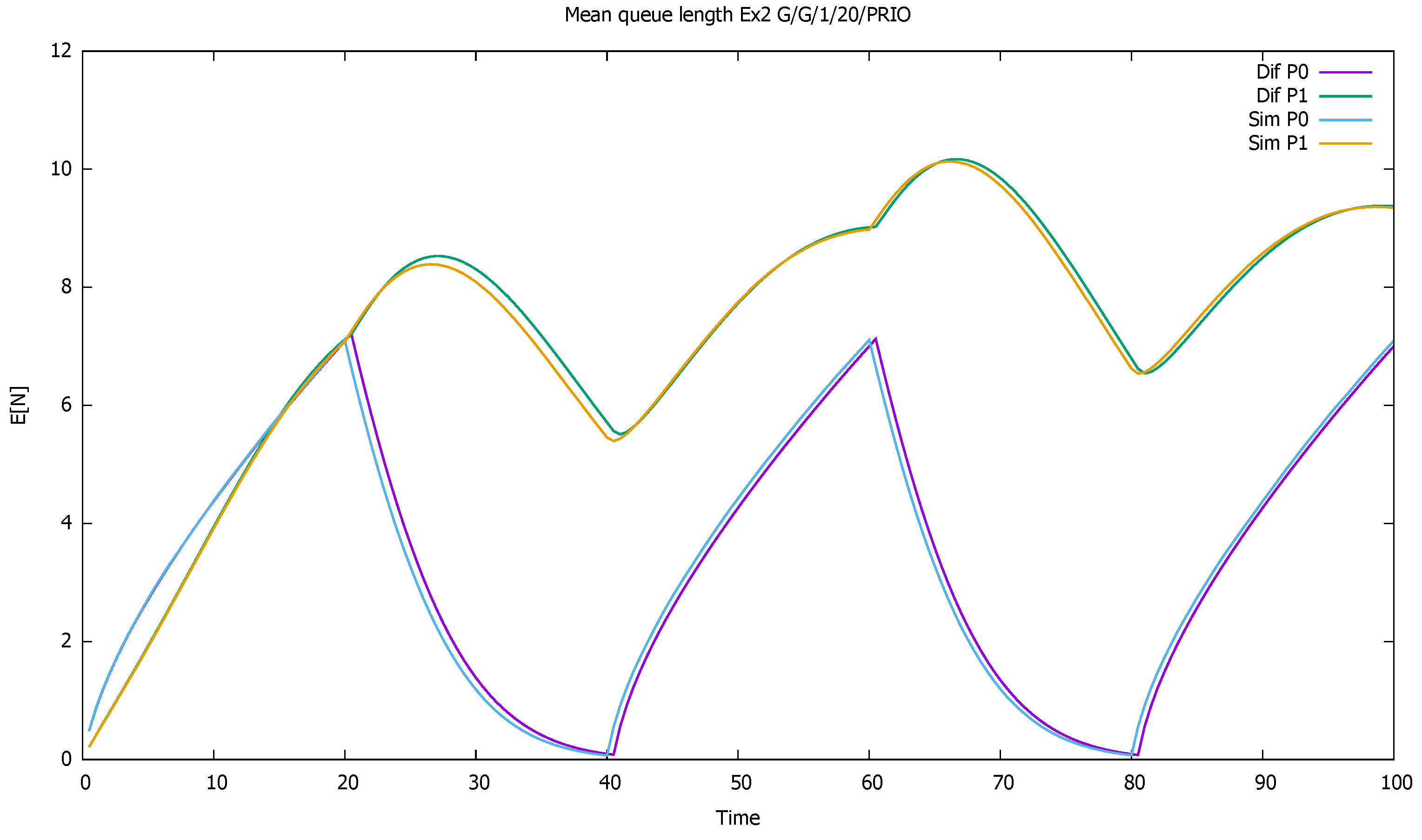
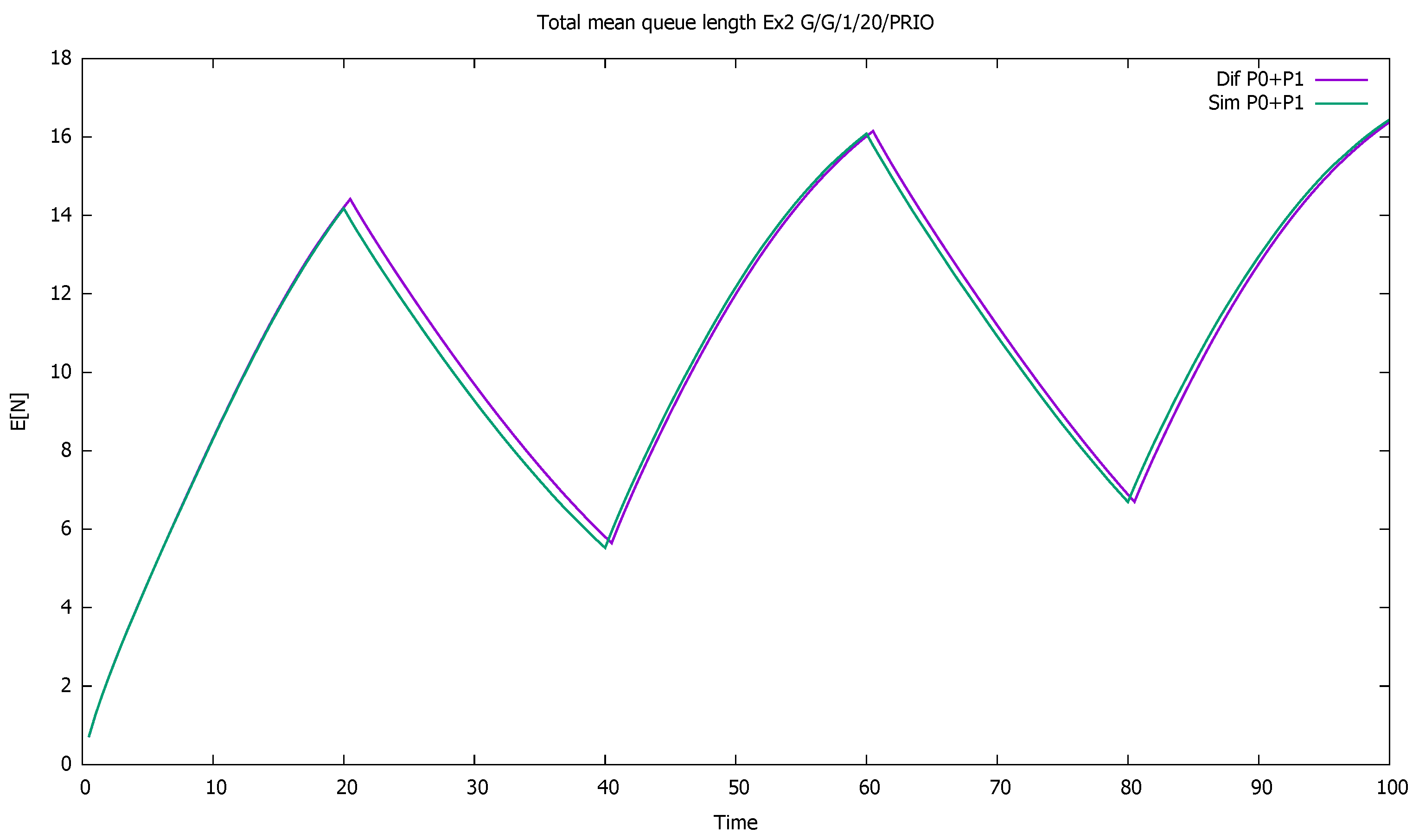
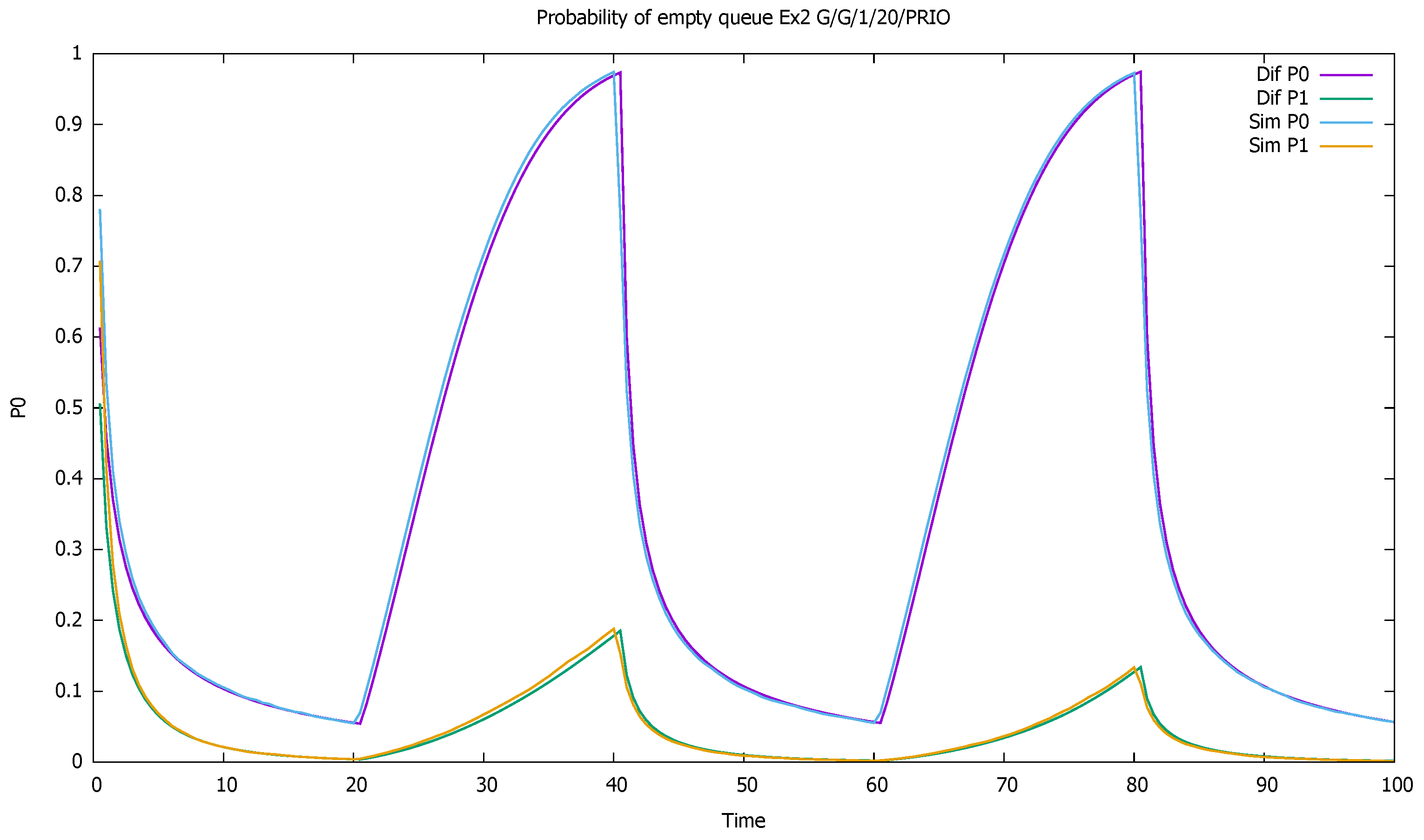
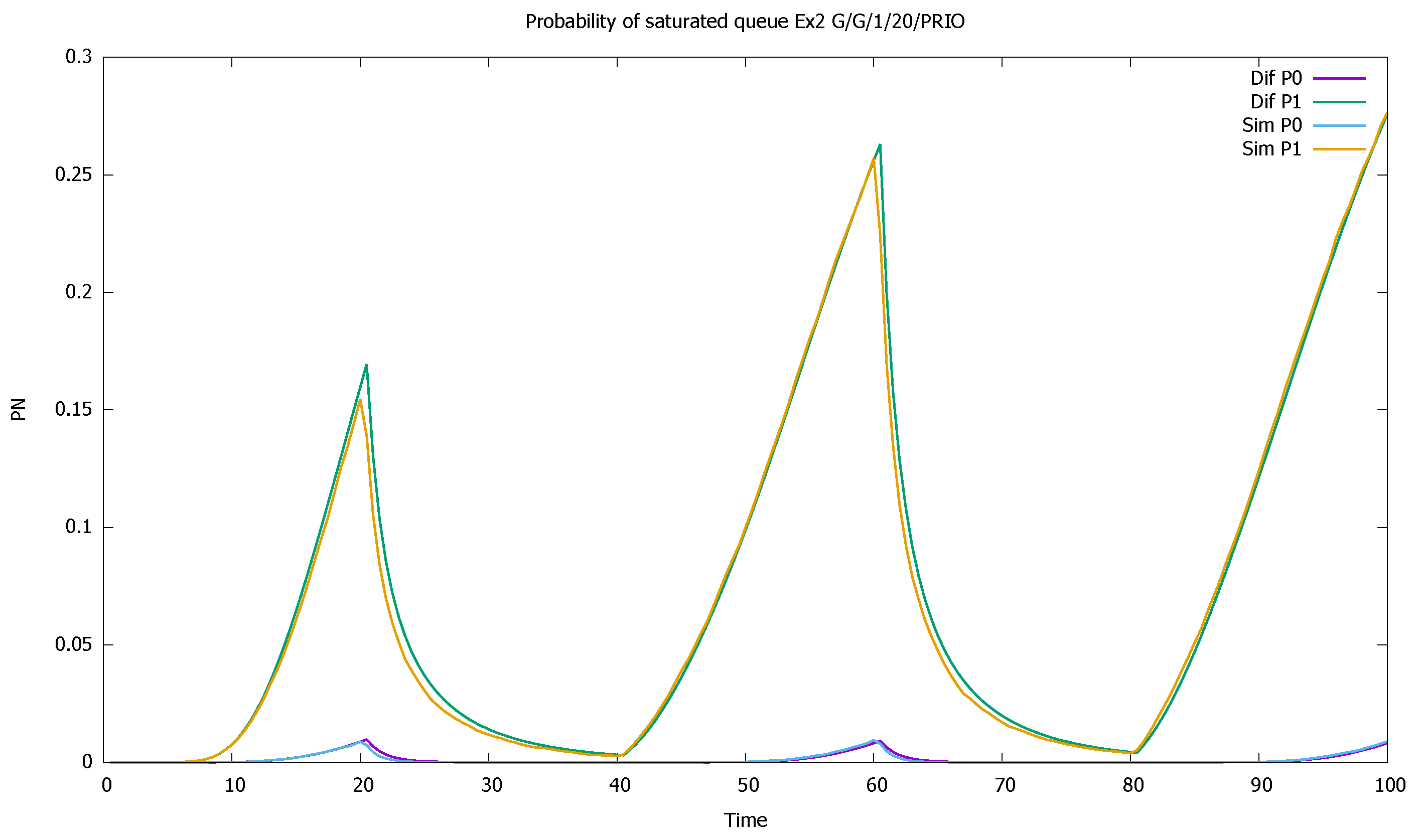
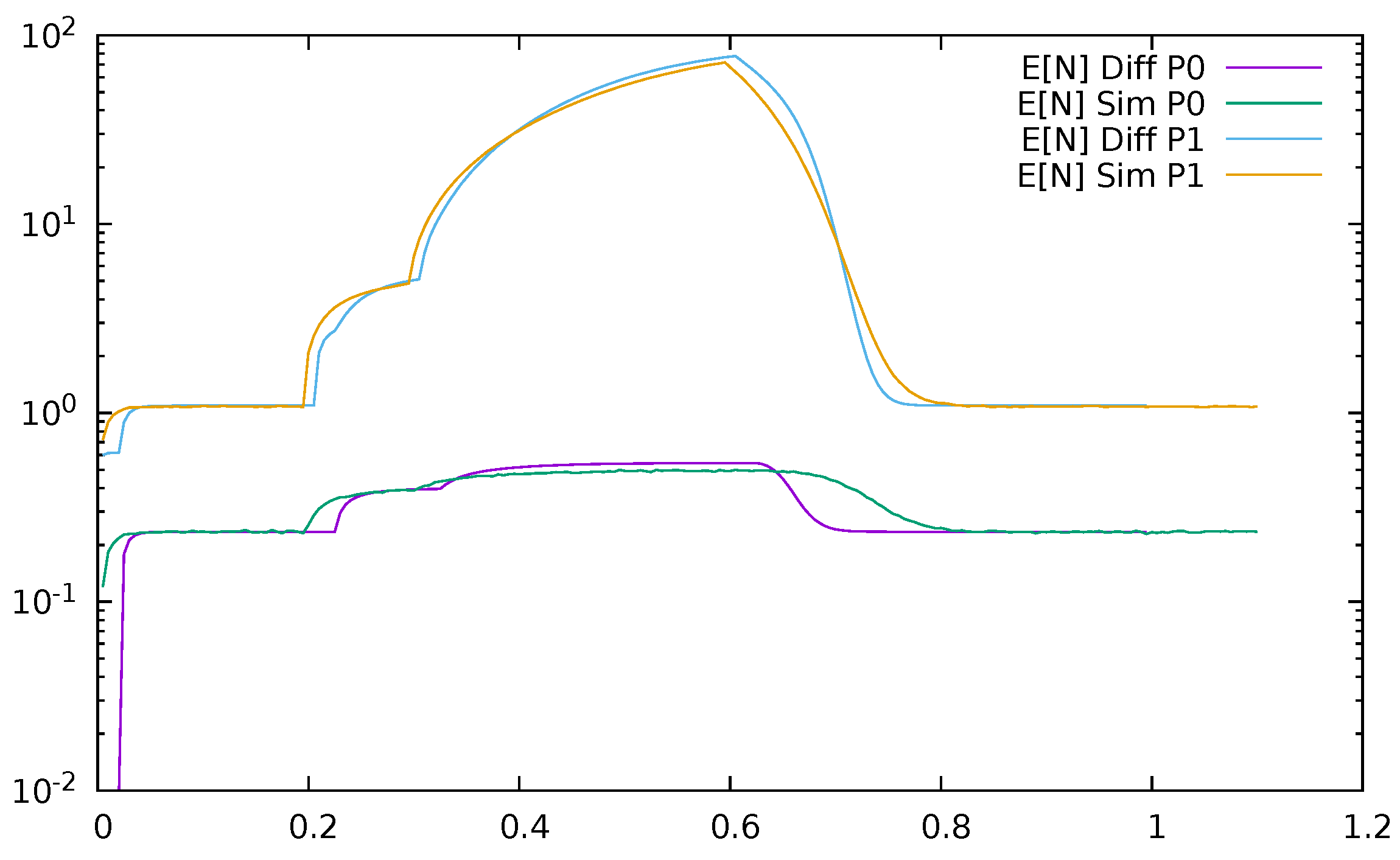
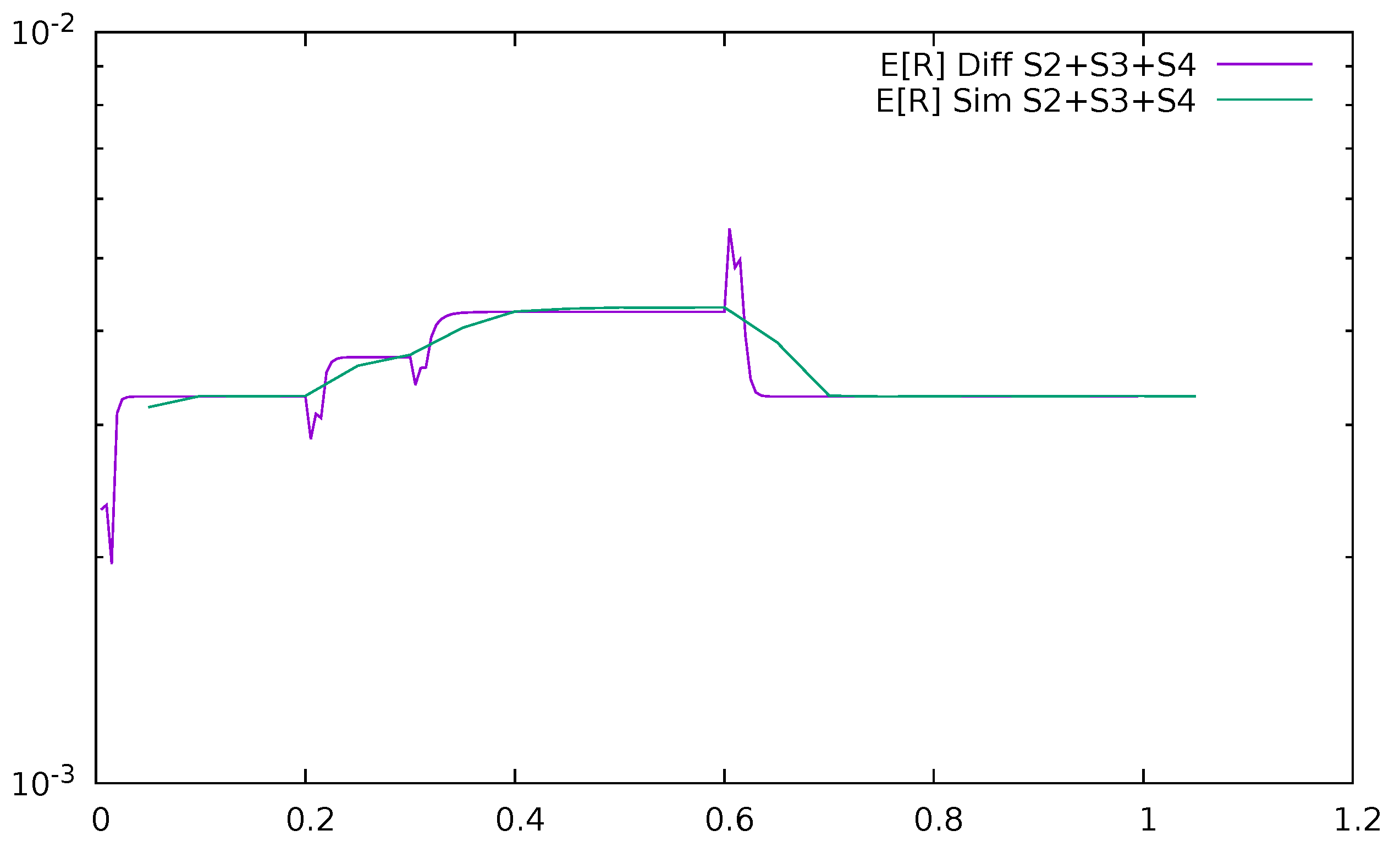
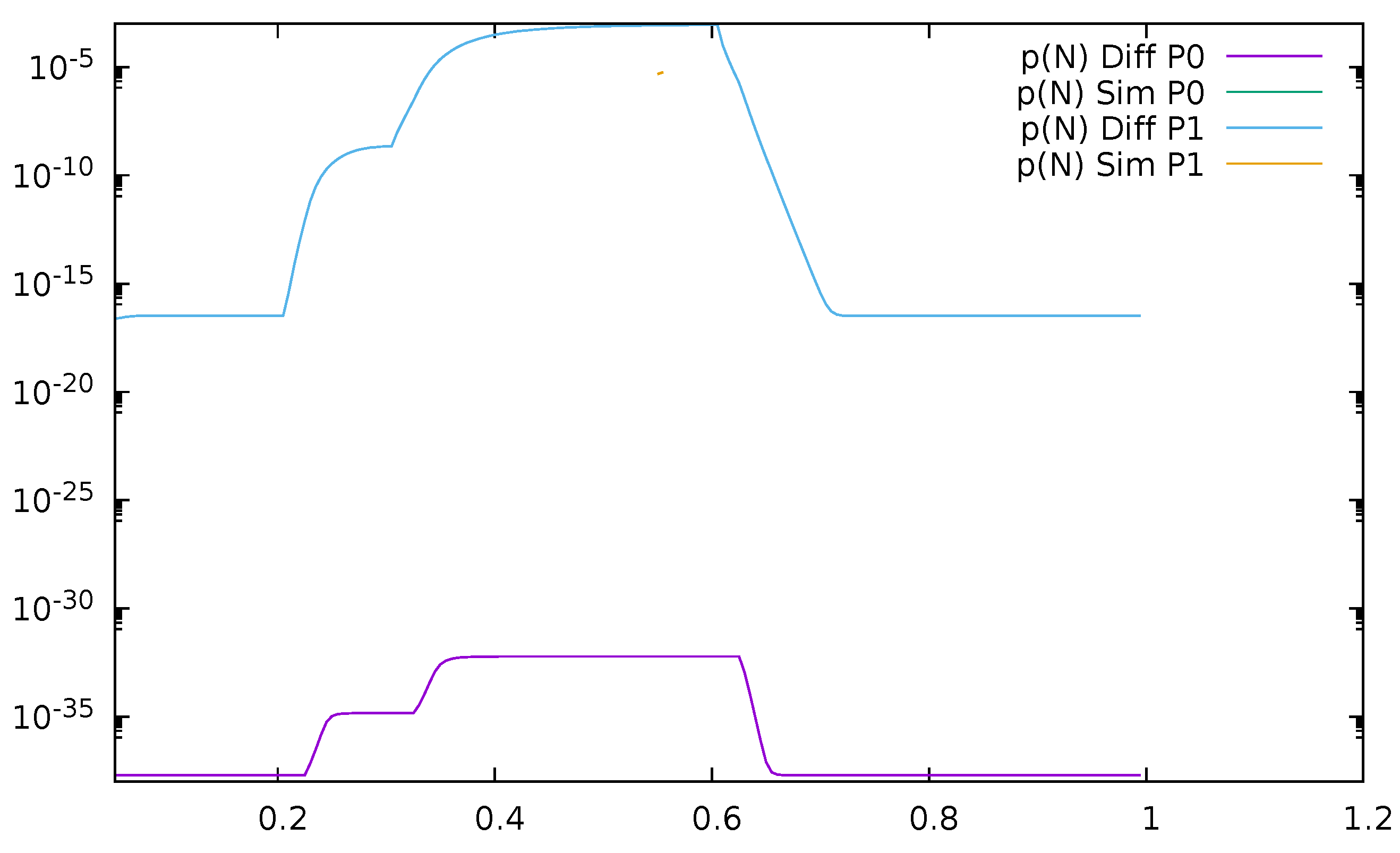
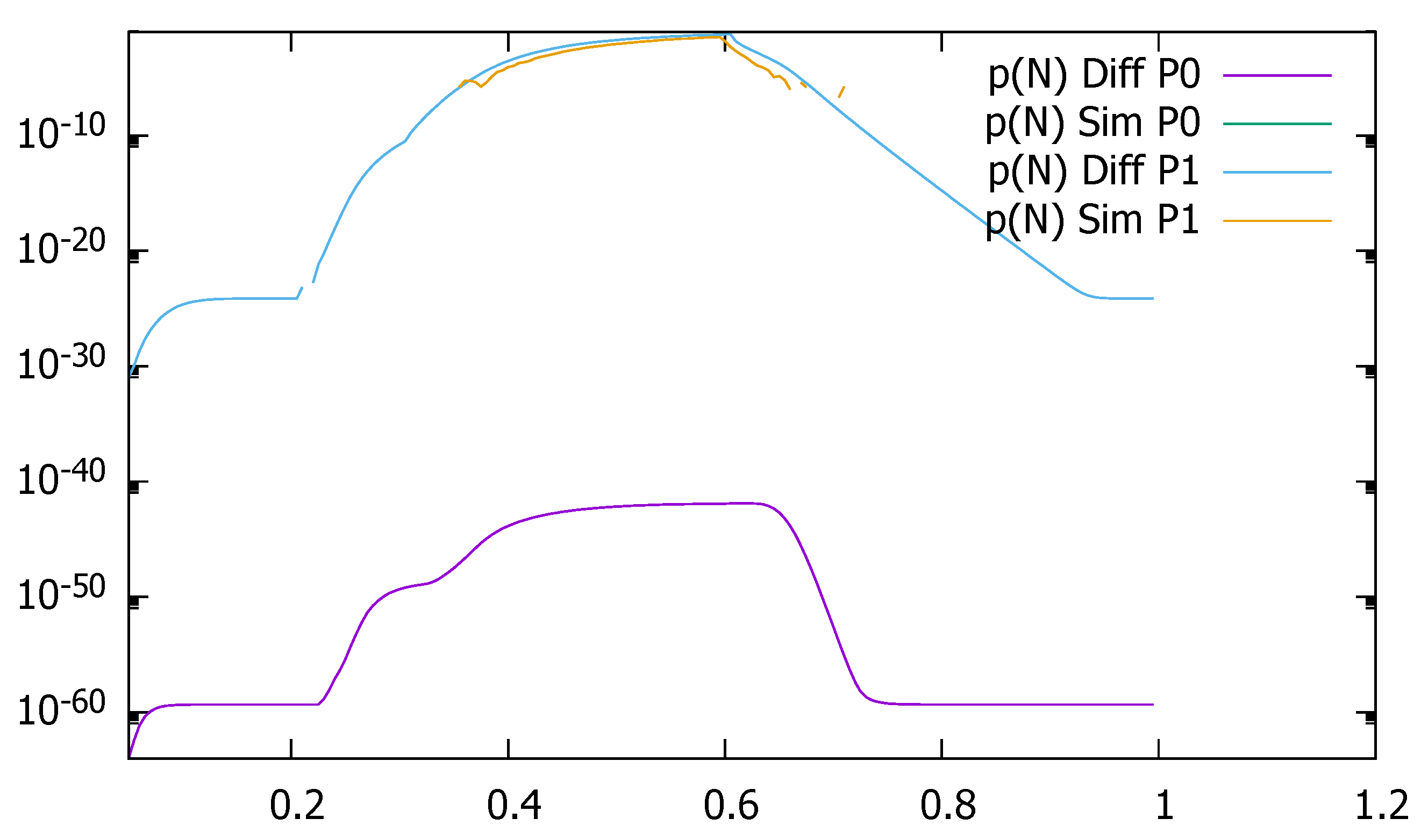
3. Validation of the Priority Model
3.1. Two Priorities, Low Input Intensities
3.2. Two Priorities, Medium Input Intensities
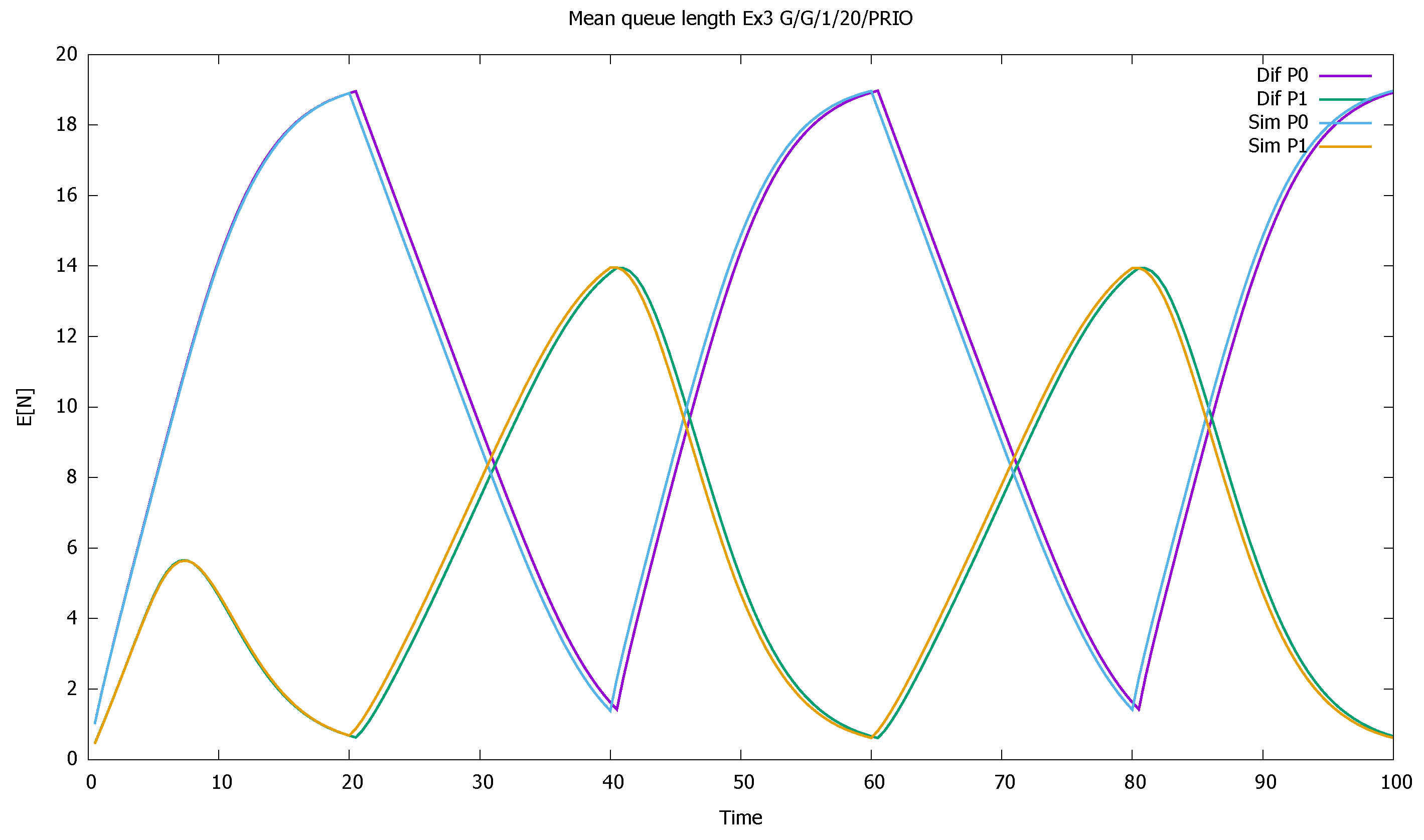
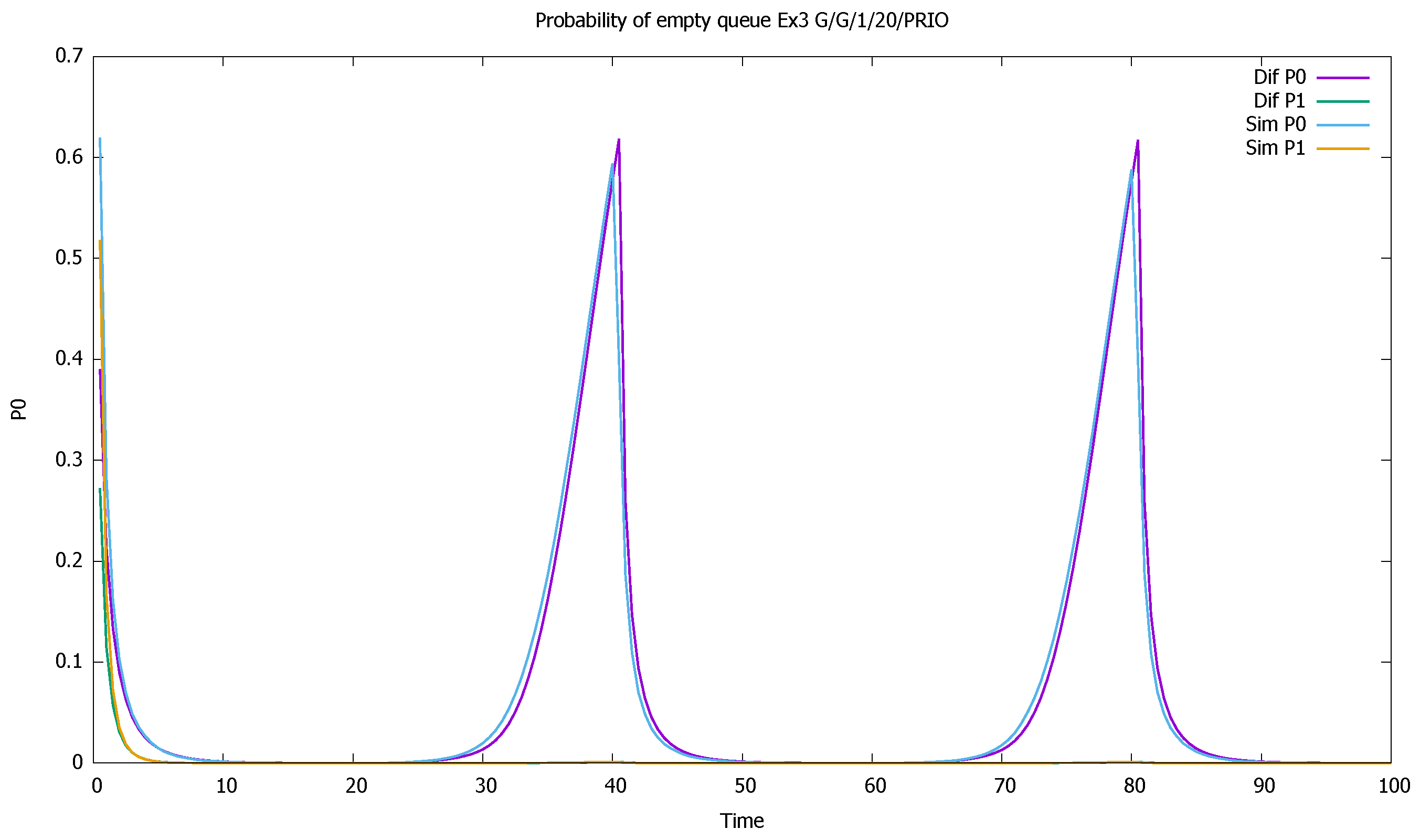
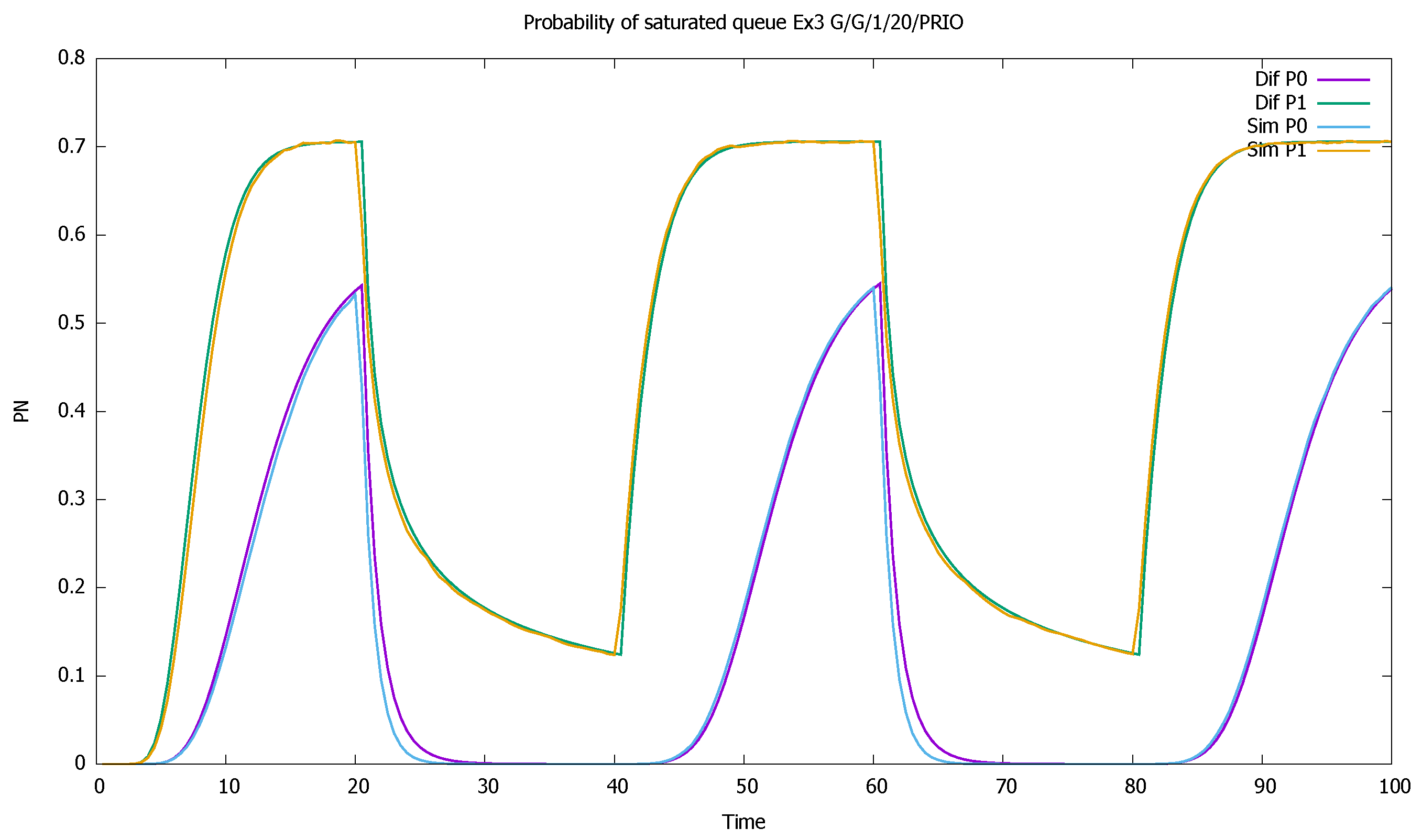
3.3. Two Priorities, High Input Intensities
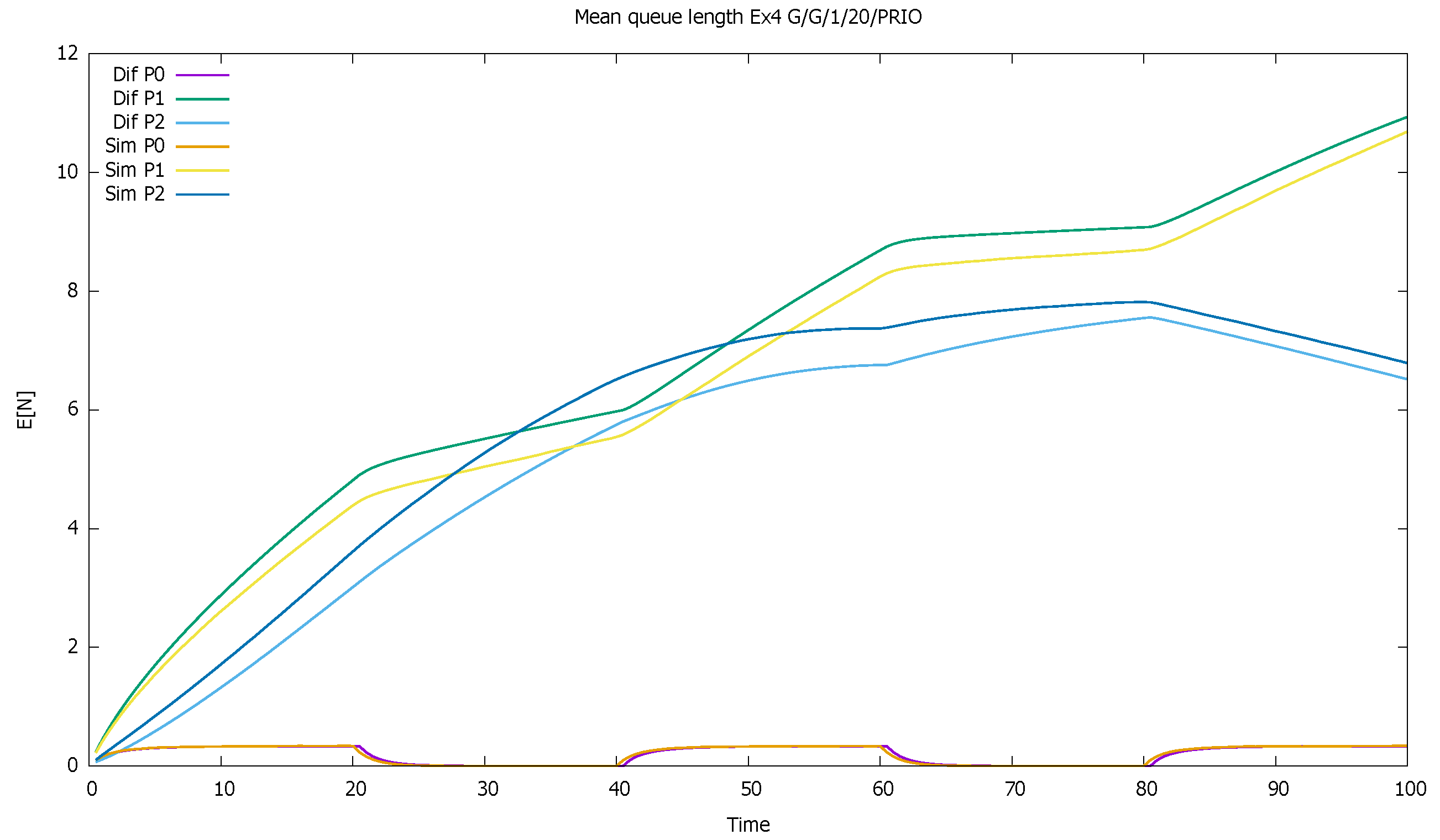
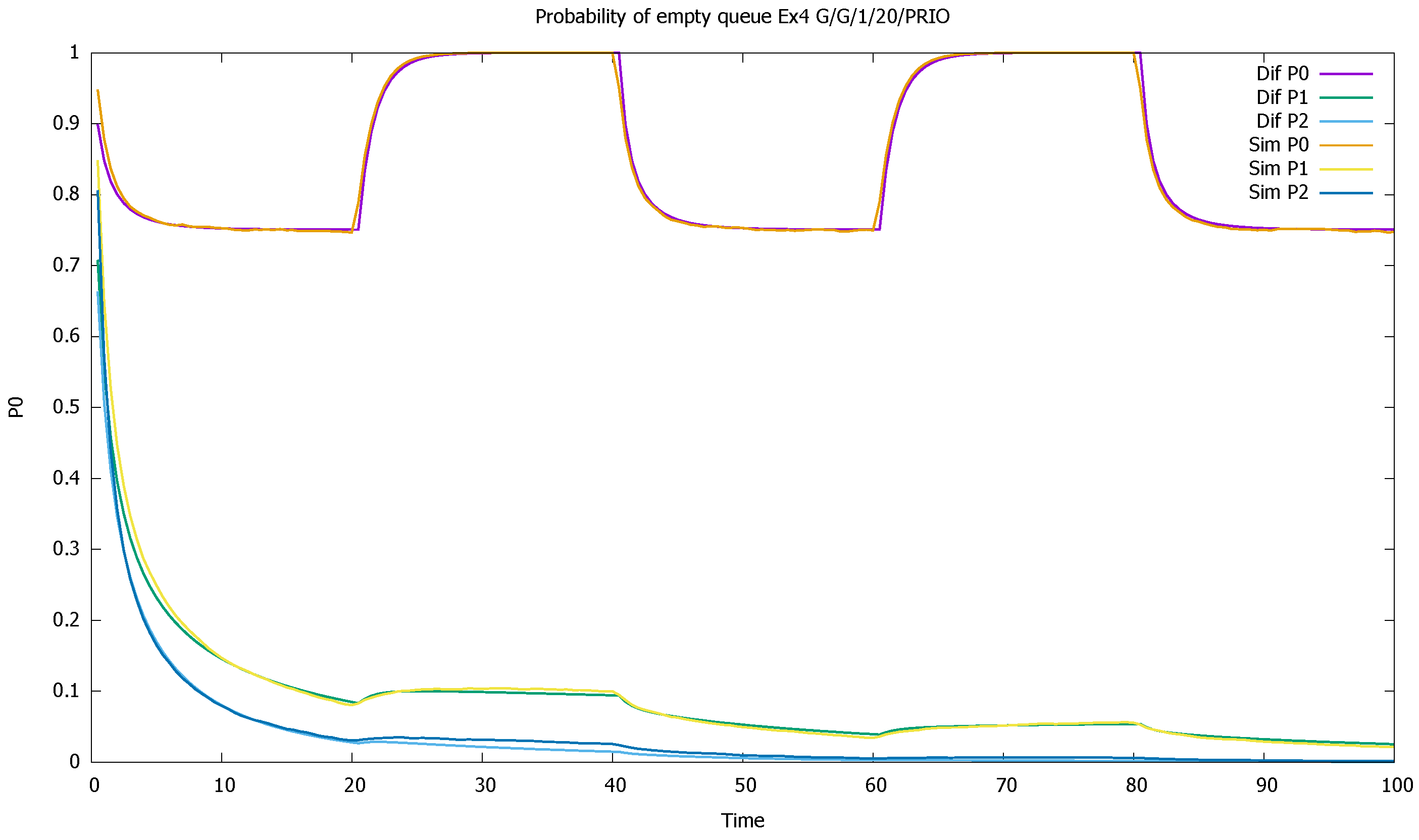
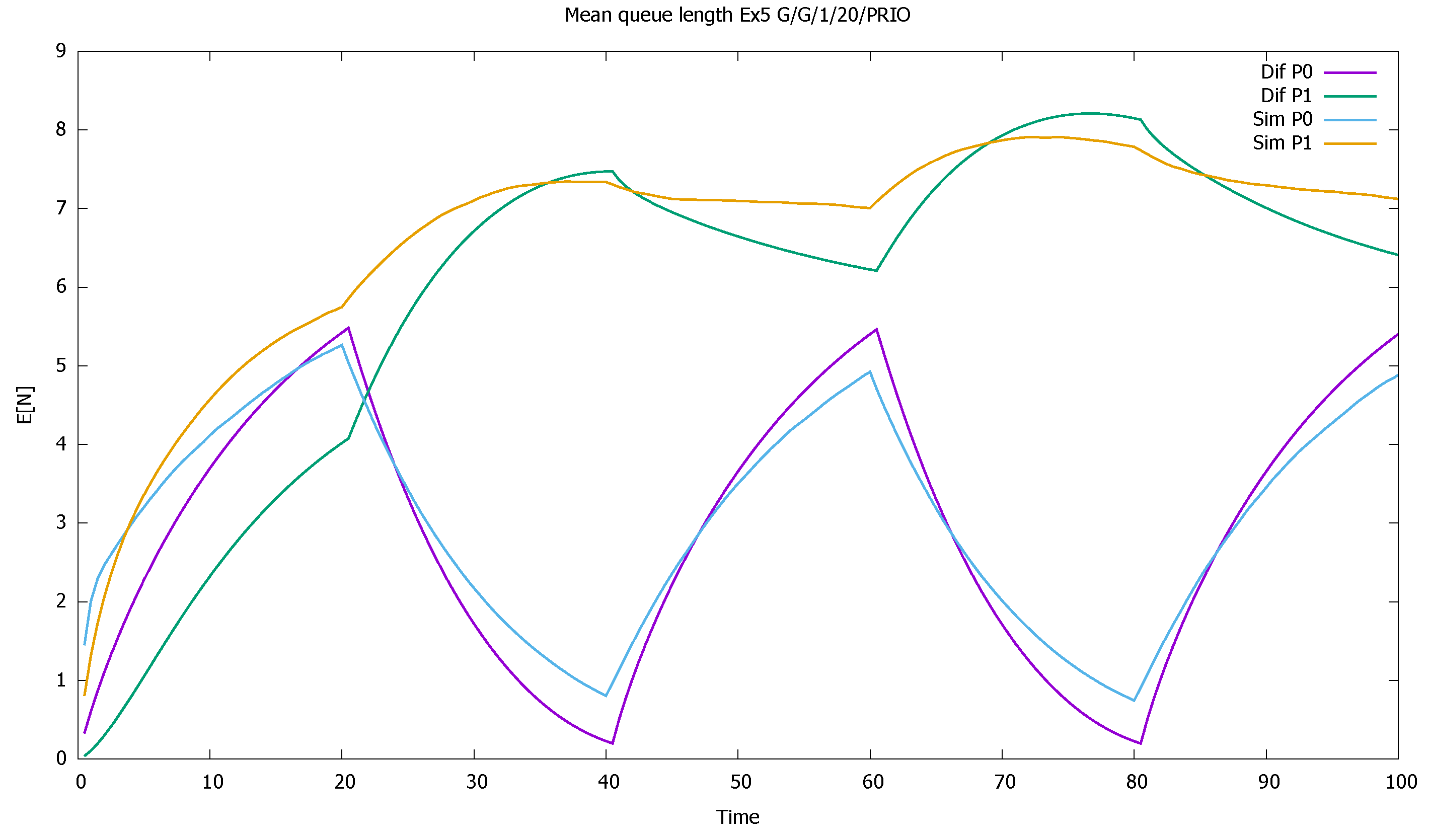
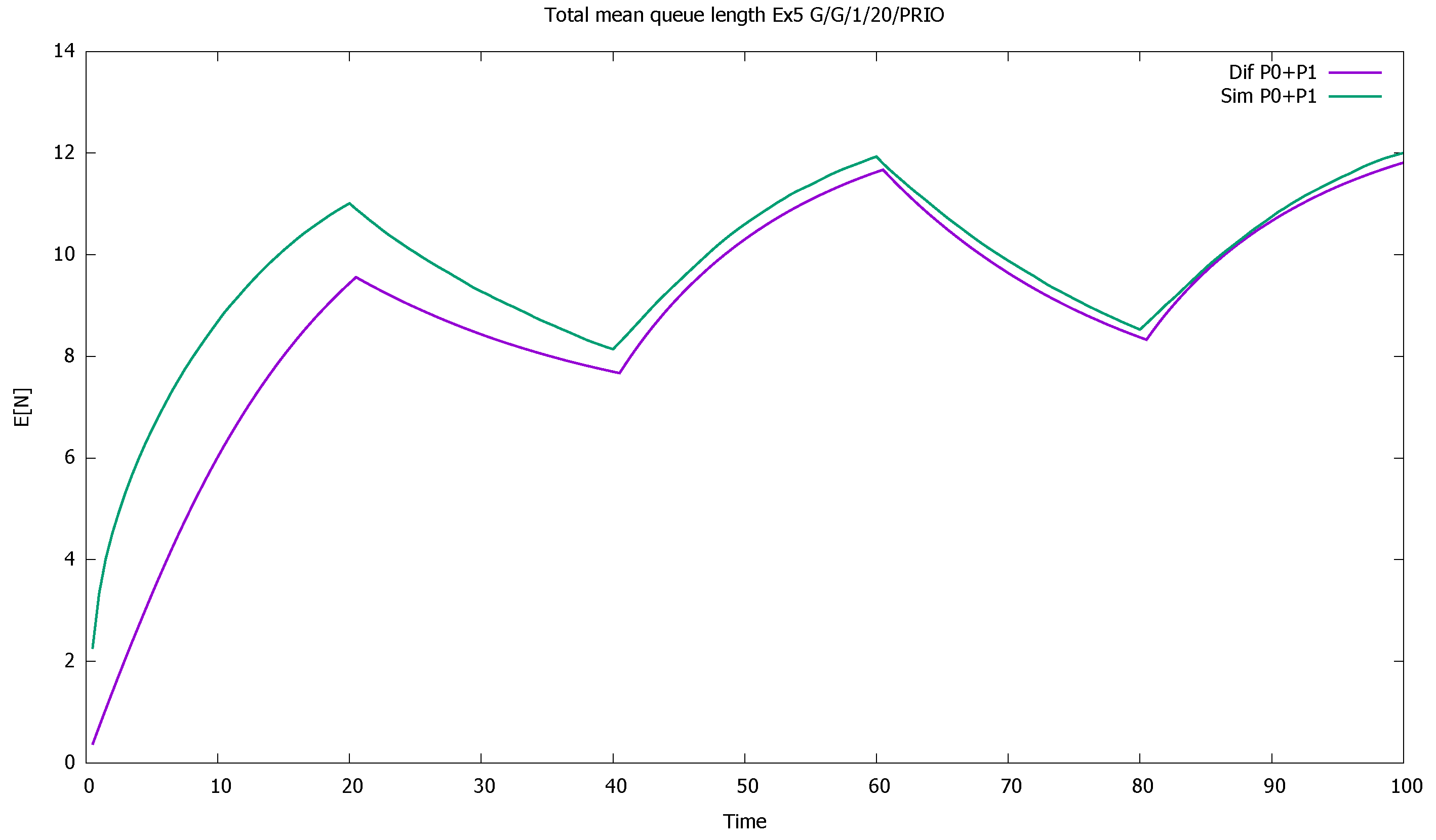
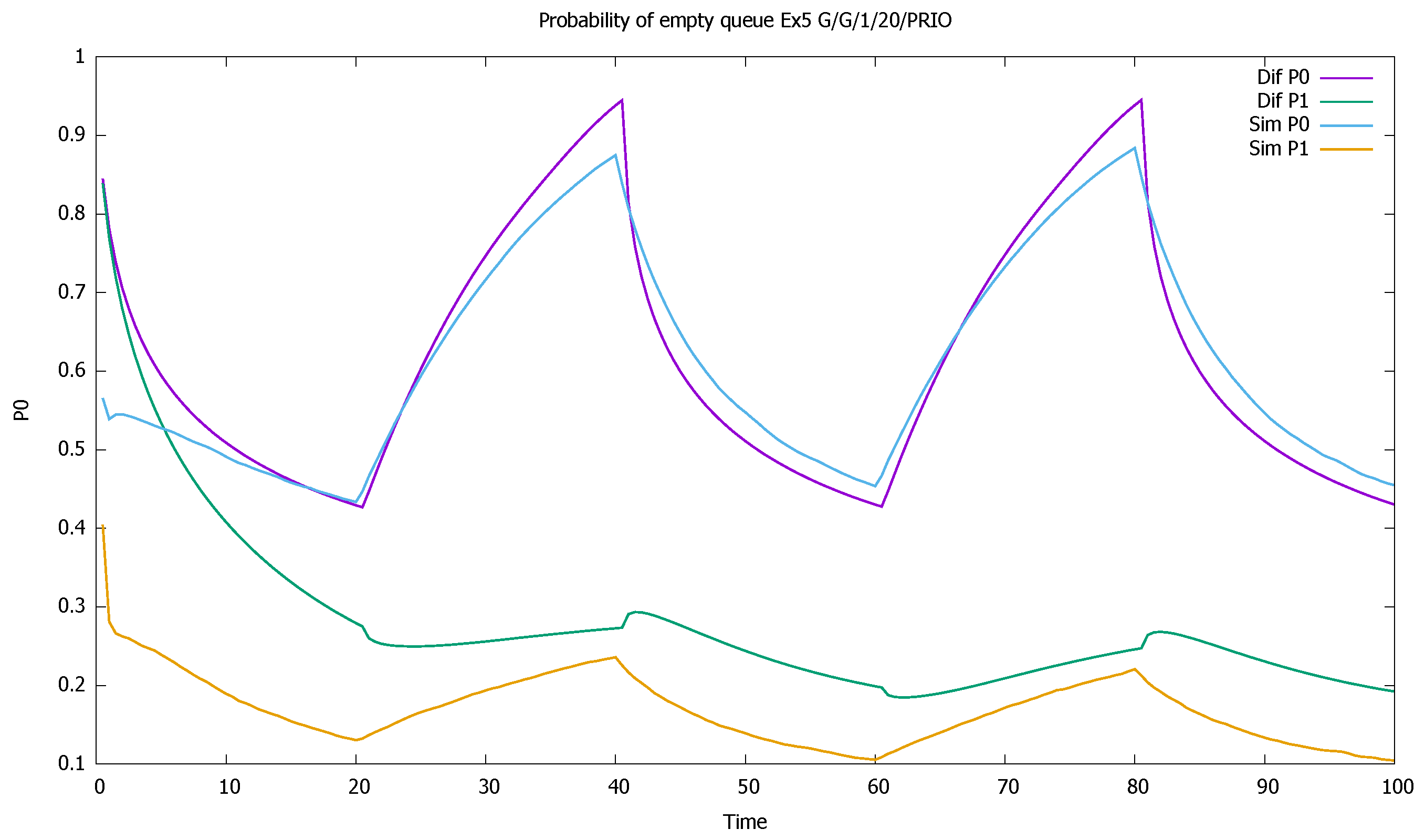
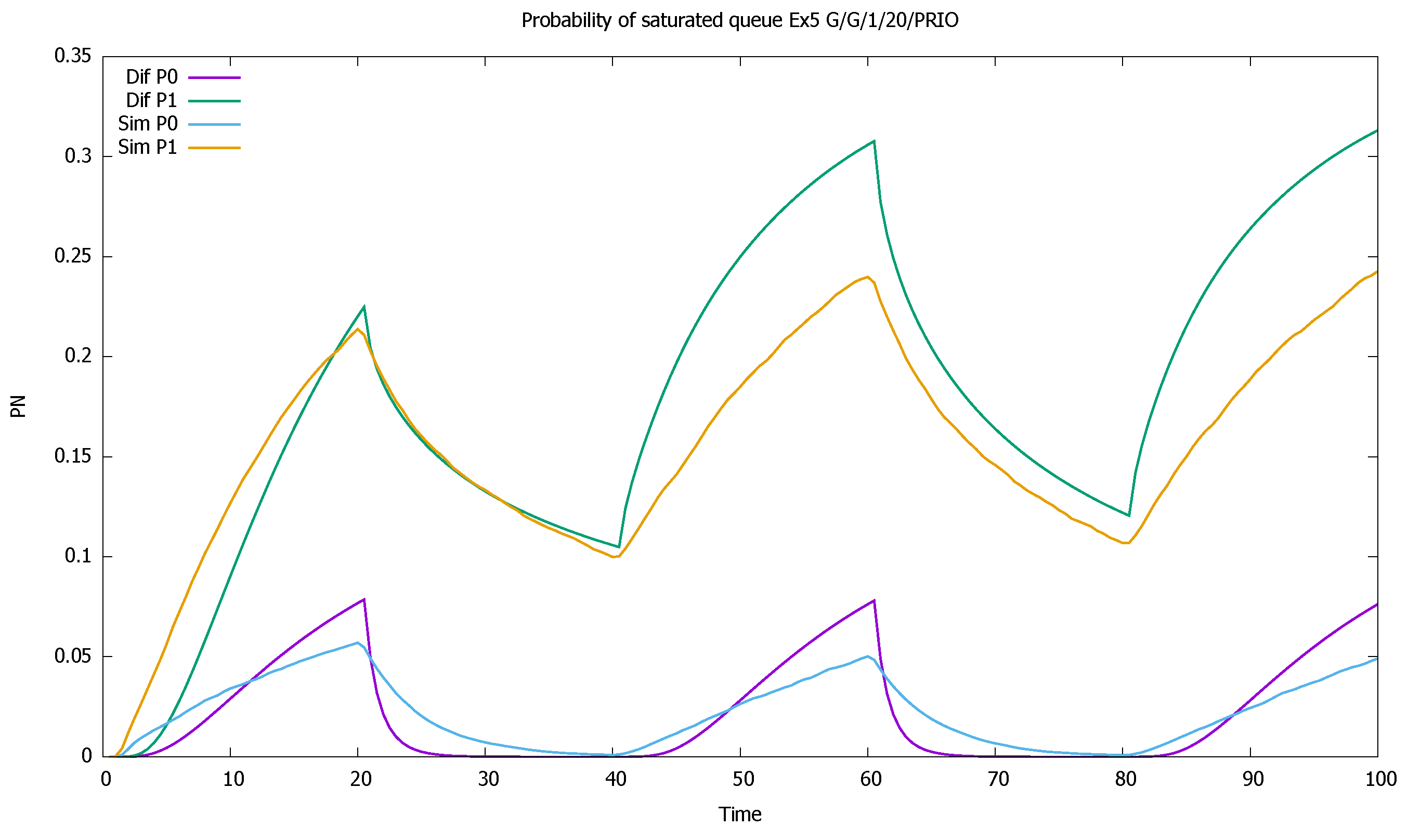
3.4. Three Priorities; Mean Service Time Depends on Priority
3.5. Two Priorities; General Interarrival and Service Time Distributions
4. Network of Priority and Non-Priority Queues
4.1. The Output Stream at the FIFO Station
4.2. The Output Stream at the Priority Station
- –
- The next customer in the class k is in the system (this occurs with probability ) and will leave it after its completion time;
- –
- There are no customers of this class in the system, and we shall wait for the time described by until it appears and enters the server;
- –
- No customer of class k is present in the system, and a customer of higher class comes before him, so the busy period must first be terminated.
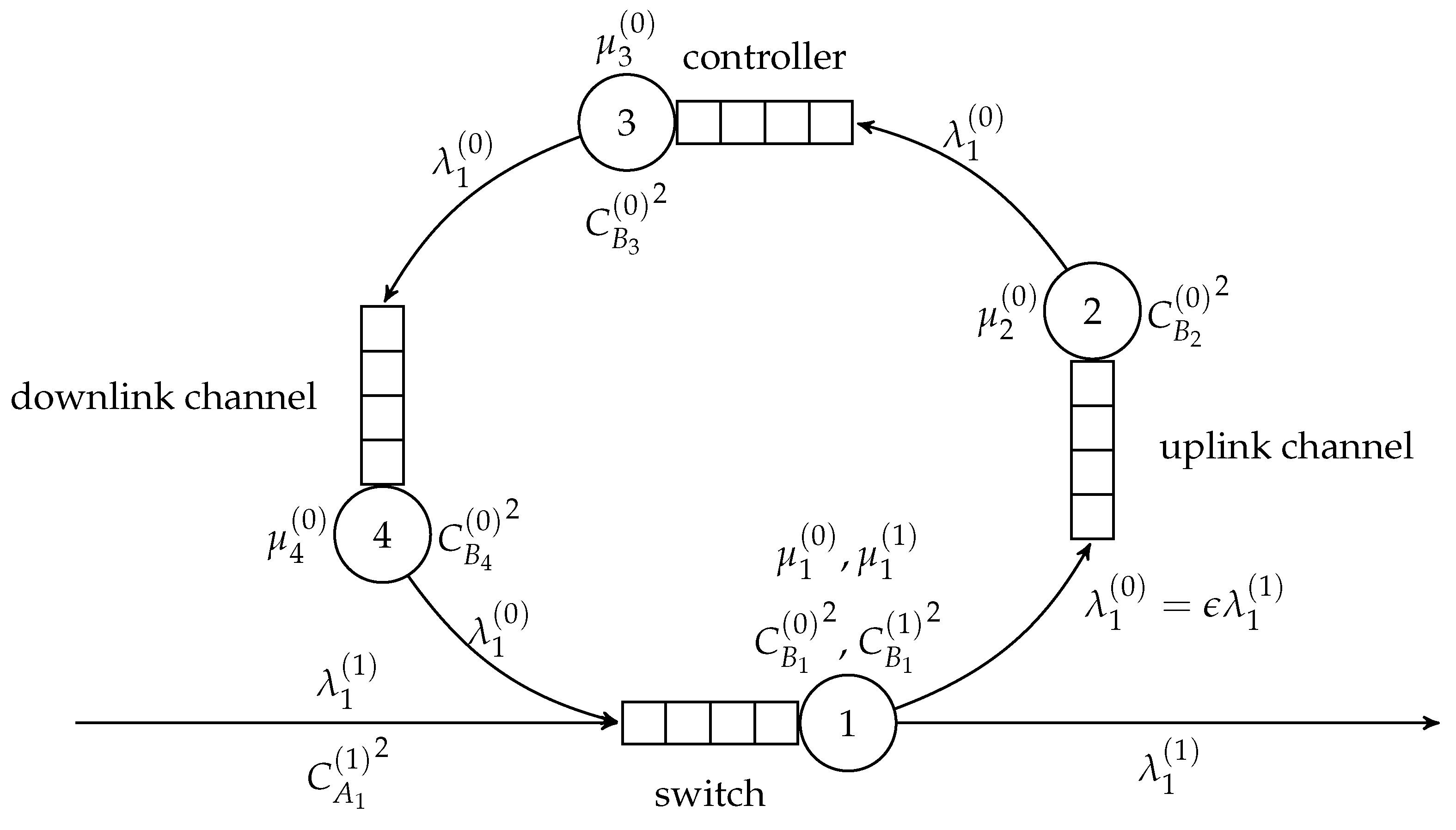
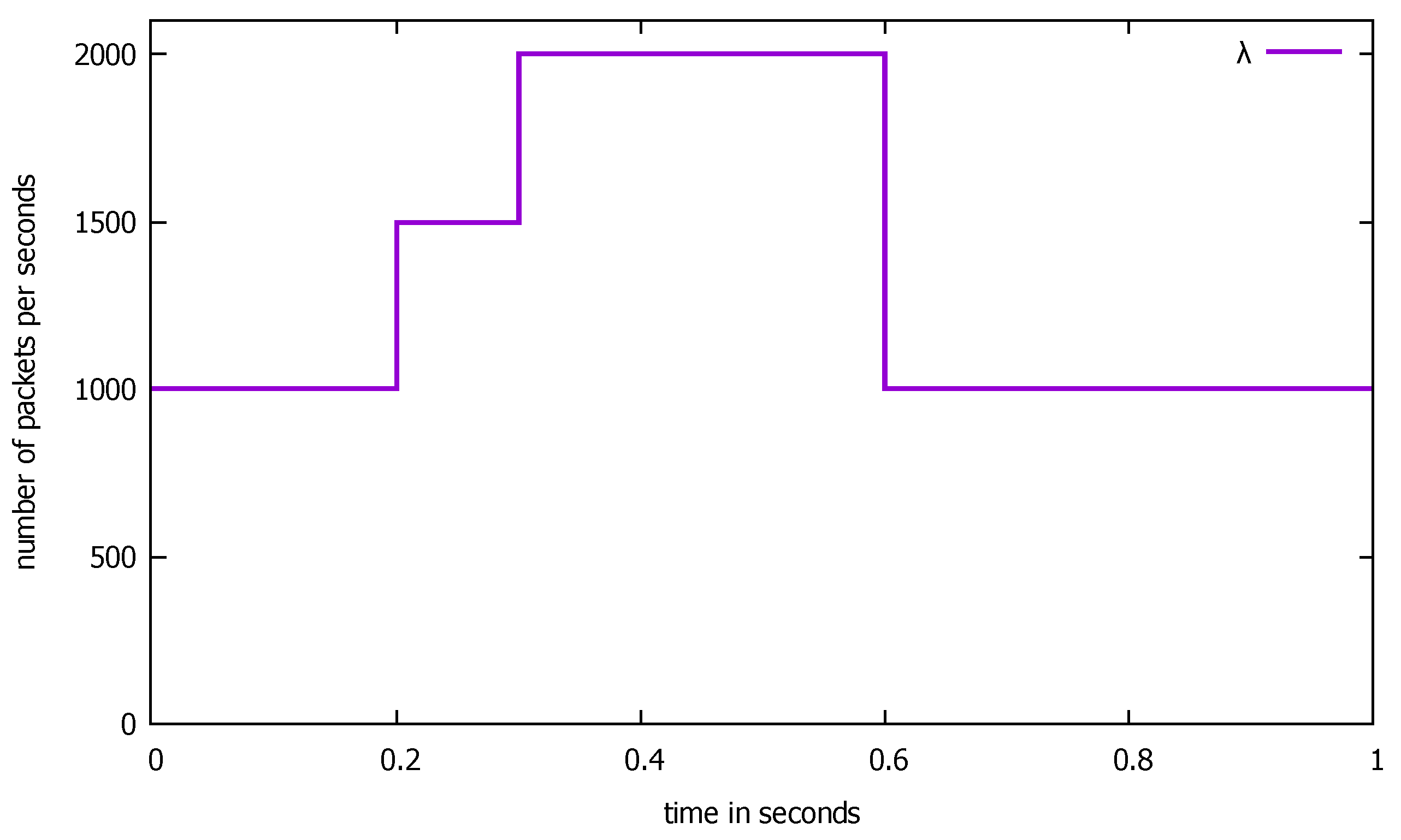
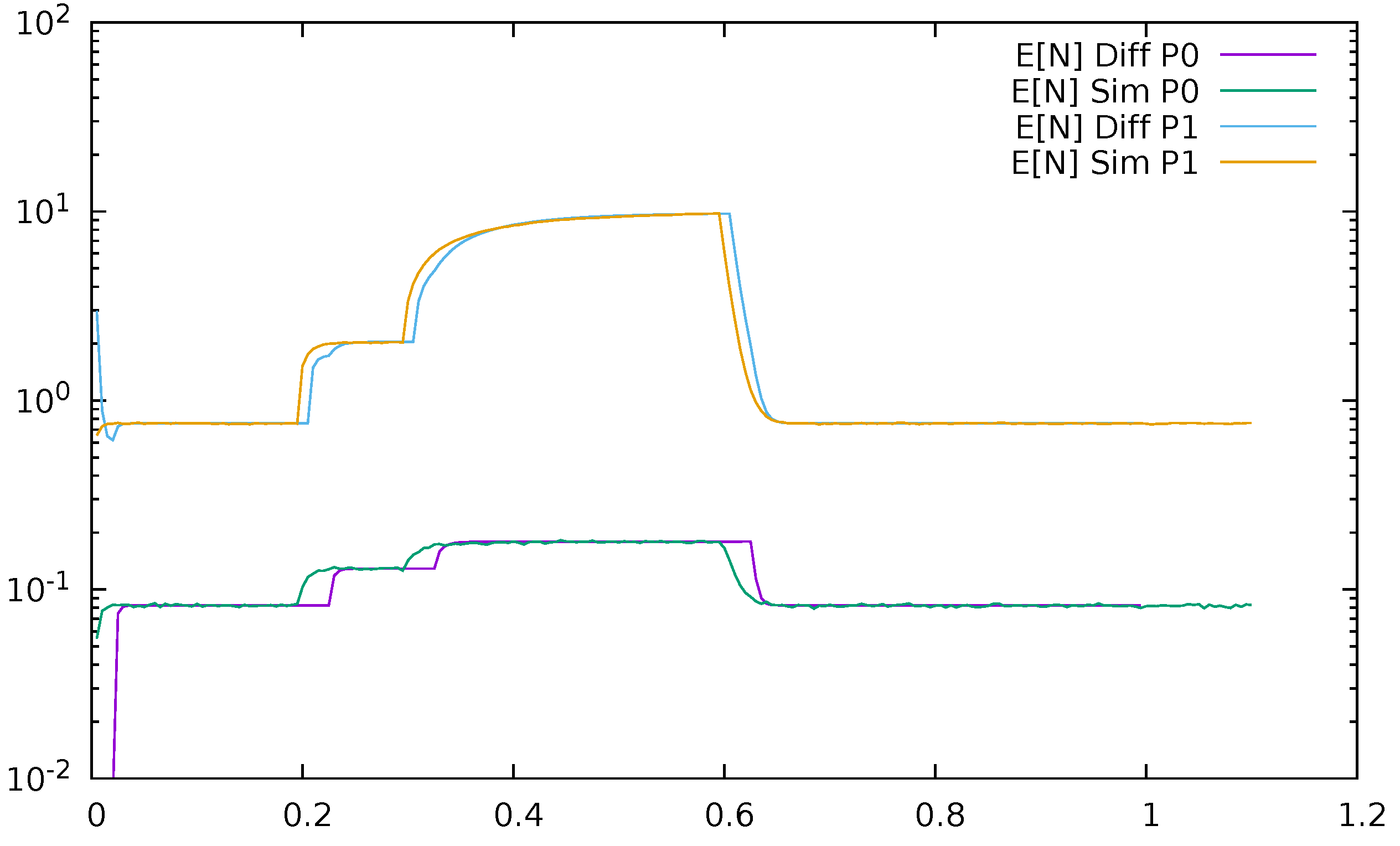
5. The SDN Switch
- Proposing the diffusion model of a multiclass G/G/1/N/Priority station, i.e., a station with general interarrival and service time distributions, limited buffer, and with preemptive-resume priority queues. Each class of customers has its specified priority level and its own parameters of the interarrival and service time distribution. Within one priority class, the scheduling is based on the FIFO algorithm. The model covers transient and steady-state analysis.
- Validation of this model by comparison with discrete-event simulation for various loads and interarrival and service time distributions, and discussion of errors;
- The model of an open network with any topology integrationg priority and FIFO service stations;
- A model of SDN switch exchanging packets with undetermined routing with SDN controller and validation of this model.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Anerousis, N.; Chemouil, P.; Lazar, A.A.; Mihai, N.; Weinstein, S.B. The Origin and Evolution of Open Programmable Networks and SDN. IEEE Commun. Surv. Tutor. 2021. [Google Scholar] [CrossRef]
- Benzekki, K.; Fergougui, A.E.; Elalaoui, A.E. Software-defined networking (SDN): A survey. Secur. Commun. Netw. 2016, 9, 5803–5833. [Google Scholar] [CrossRef]
- Shirmarz, A.; Ghaffari, A. Performance issues and solutions in SDN-based data center: A survey. J. Supercomput. 2020, 76, 7545–7593. [Google Scholar] [CrossRef]
- Thirupathi, V.; Sandeep, C.; Kumar, S.N.; Kumar, P.P. A Comprehensive Review on SDN Architecture, Applications And Major Benifits of SDN. Int. J. Adv. Sci. Technol. 2019, 28, 607–614. [Google Scholar]
- Agg, P.; Johanyák, Z.C.; Szilveszter, K. Survey on SDN Programming Languages. In Proceedings of the 8th International Scientific and Expert Conference TEAM 2016, Rome, Italy, 24–26 February 2016; pp. 64–70. [Google Scholar]
- Mahmood, W.; Nasir, S.D.; Waqas, I. A Research Survey on Software Defined Networking (SDN). In Proceedings of the Ninth International Conference on Advances in Computing, Control and Networking (ACCN 2019), London, UK, 21 July 2019; pp. 127–132. [Google Scholar] [CrossRef]
- Yu, T.; Hong, Y.; Cui, H.; Jiang, H. A survey of Multi-controllers Consistency on SDN. In Proceedings of the 2018 4th International Conference on Universal Village (UV), Boston, MA, USA, 21–24 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Stevens, M.; Ng, B.; Streader, D.; Welch, I. Global and local knowledge in SDN. In Proceedings of the 2015 International Telecommunication Networks and Applications Conference (ITNAC), Sydney, NSW, Australia, 18–20 November 2015; pp. 237–243. [Google Scholar] [CrossRef]
- Paliwal, M.; Shrimankar, D.; Tembhurne, O. Controllers in SDN: A Review Report. IEEE Access 2018, 6, 36256–36270. [Google Scholar] [CrossRef]
- Michel, O.; Keller, E. SDN in wide-area networks: A survey. In Proceedings of the 2017 Fourth International Conference on Software Defined Systems (SDS), Valencia, Spain, 8–11 May 2017; pp. 37–42. [Google Scholar] [CrossRef]
- Das, T.; Sridharan, V.; Gurusamy, M. A Survey on Controller Placement in SDN. IEEE Commun. Surv. Tutor. 2020, 22, 472–503. [Google Scholar] [CrossRef]
- Isong, B.; Molose, R.R.S.; Abu-Mahfouz, A.M.; Dladlu, N. Comprehensive Review of SDN Controller Placement Strategies. IEEE Access 2020, 8, 170070–170092. [Google Scholar] [CrossRef]
- Mbodila, M.; Isong, B.; Gasela, N. A Review of SDN-Based Controller Placement Problem. In Proceedings of the 2020 2nd International Multidisciplinary Information Technology and Engineering Conference (IMITEC), Kimberley, South Africa, 25–27 November 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Yan, B.; Liu, Q.; Shen, J.; Liang, D.; Zhao, B.; Ouyang, L. A survey of low-latency transmission strategies in software defined networking. Comput. Sci. Rev. 2021, 40, 100386. [Google Scholar] [CrossRef]
- Yang, L.; Ng, B.; Seah, W.K.; Groves, L.; Singh, D. A survey on network forwarding in Software-Defined Networking. J. Netw. Comput. Appl. 2021, 176, 102947. [Google Scholar] [CrossRef]
- Hemanth, D.J. A Survey on Traffic Prediction and Classification in SDN. Intell. Syst. Comput. Technol. 2020, 37, 367–370. [Google Scholar] [CrossRef]
- Priyadarsini, M.; Bera, P. Software defined networking architecture, traffic management, security, and placement: A survey. Comput. Netw. 2021, 192, 108047. [Google Scholar] [CrossRef]
- Moin, S.; Karim, A.; Safdar, K.; Iqbal, I.; Safdar, Z.; Vijayakumar, V.; Ahmed, K.T.; Abid, S.A. GREEN SDN—An enhanced paradigm of SDN: Review, taxonomy, and future directions. Concurr. Comput. Pract. Exp. 2018, 32, 1–21. [Google Scholar] [CrossRef]
- Rasool, Z.I.; Ali, R.S.A.; Abdulzahra, M.M. Network Management in Software-Defined Network: A Survey. IOP Conf. Ser. Mater. Sci. Eng. 2020, 1094, 1–6. [Google Scholar] [CrossRef]
- Ahmad, S.; Mir, A.H. Scalability, Consistency, Reliability and Security in SDN Controllers: A Survey of Diverse SDN Controllers. J. Netw. Syst. Manag. 2021, 29. [Google Scholar] [CrossRef]
- Sandhya; Sinha, Y.; Haribabu, K. A survey: Hybrid SDN. J. Netw. Comput. Appl. 2017, 100, 35–55. [Google Scholar] [CrossRef]
- Khorsandroo, S.; Sánchez, A.G.; Tosun, A.S.; Arco, J.; Doriguzzi-Corin, R. Hybrid SDN evolution: A comprehensive survey of the state-of-the-art. Comput. Netw. 2021, 192, 107981. [Google Scholar] [CrossRef]
- Keshari, S.K.; Kansal, V.; Kumar, S. A Systematic Review of Quality of Services (QoS) in Software Defined Networking (SDN). Wirel. Pers. Commun. 2021, 116, 2593–2614. [Google Scholar] [CrossRef]
- Mahmood, K.; Chilwan, A.; Østerbø, O.; Jarschel, M. Modelling of OpenFlow-based software-defined networks: The multiple node case. IET Netw. 2015, 4, 278–284. [Google Scholar] [CrossRef]
- Ansell, J.; Seah, W.K.G.; Ng, B.; Marshall, S. Making Queueing Theory More Palatable to SDN/OpenFlow-based Network Practitioners. In Proceedings of the 2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; IEEE: Istanbul, Turkey, 2016; pp. 1119–1124. [Google Scholar] [CrossRef]
- Sood, K.; Yi, S.; Xiang, Y. Performance Analysis of Software-Defined Network router using M/Geo/1. IEEE Commun. Lett. 2016, 20, 27–51. [Google Scholar] [CrossRef]
- Miao, W.; Min, G.; Wu, Y.; Wang, H. Performance Modelling of Preemption-Based Packet Scheduling for Data Plane in Software Defined Networks. In Proceedings of the 2015 IEEE International Conference on Smart City/SocialCom/SustainCom (SmartCity), Chengdu, China, 19–21 December 2015; pp. 60–65. [Google Scholar] [CrossRef]
- Miao, W.; Min, G.; Wu, Y.; Wang, H.; Hu, J. Performance Modelling and Analysis of Software-Defined Networking under Bursty Multimedia Traffic. ACM Trans. Multimed. Comput. Commun. Appl. 2016, 12, 24–36. [Google Scholar] [CrossRef] [Green Version]
- Singh, D.; Ng, B.; Lai, Y.C.; Lin, Y.D.; Seah, W.K.G. Modelling Software-Defined Networking: Software and Hardware Switches. J. Comput. Netw. Comput. Appl. 2018, 122, 24–36. [Google Scholar] [CrossRef]
- Goto, Y.; Ng, B.; Seah, W.K.G.; Takahashi, Y. Queueing analysis of software defined network with realistic OpenFlow-based switch model. Comput. Netw. 2019, 164, 106892. [Google Scholar] [CrossRef]
- Mochalov, V.P.; Linets, G.I.; Palkanov, I. The Erlang Model for a Fragment of SDN Architecture. In Advances in Automation II, Proceedings of the RusAutoConf 2020, Sochi, Russia, 6–12 September 2020; Lecture Notes in Electrical Engineering; Springer International Publishing: Cham, Switzerland, 2021; Volume 729, pp. 424–437. [Google Scholar] [CrossRef]
- Azodolmolky, S.; Wieder, P.; Yahyapour, R. Performance evaluation of a scalable software-defined networking deployment. In Proceedings of the 2013 Second European Workshop on Software Defined Networks, Berlin, Germany, 10–11 October 2013; IEEE: Berlin, Germany, 2013; pp. 68–74. [Google Scholar] [CrossRef]
- Azodolmolky, S.; Nejabati, R.; Pazouki, M.; Wieder, P.; Yahyapour, R.; Simeonidou, D. An analytical model for software defined networking: A network calculus-based approach. In Proceedings of the IEEE Global Communications Conference, Atlanta, GA, USA, 9–13 December 2013; IEEE: Atlanta, GA, USA, 2013; pp. 1397–1402. [Google Scholar] [CrossRef]
- Bozakov, Z.; Rizk, A. Taming SDN controllers in heterogeneous hardware environments. In Proceedings of the 2013 Second European Workshop on Software Defined Networks, Berlin, Germany, 10–11 October 2013; IEEE: Berlin, Germany, 2013; pp. 50–55. [Google Scholar] [CrossRef]
- Champernowne, D.C. An elementary method of solution of the queueing problem with a single server and constant parameters. J. R. Statist. Soc. 2000, 3, 263–266. [Google Scholar] [CrossRef]
- Takâcs, L. Introduction to the Theory of Queues; Oxford University Press: Oxford, UK, 1960. [Google Scholar]
- Tarabia, A.M.K. Transient Analysis of M/M/1/N Queue—An Alternative Approach. Tamkang J. Sci. Eng. 2000, 3, 263–266. [Google Scholar]
- Parthasarathy, P.; Selvaraju, N. Transient analysis of a queue where potential customers are discouraged by queue length. Math. Probl. Eng. 2001, 7, 433–454. [Google Scholar] [CrossRef] [Green Version]
- Parthasarathy, P.; Sudhesh, R. Exact transient solution of a discrete time queue with state-dependent rates. Am. J. Math. Manag. Sci. 2006, 26, 253–276. [Google Scholar] [CrossRef]
- Sudhesh, R. Transient analysis of a queue with system disasters and customer impatience. Queueing Syst. 2010, 66, 95–105. [Google Scholar] [CrossRef]
- Vuppalapati, N.; Venkatesh, T.G. Modeling & analysis of software defined networks under non-stationary conditions. Peer Netw. Appl. 2021, 14, 1174–1189. [Google Scholar] [CrossRef]
- Tipper, D.; Sundareshan, M. Numerical methods for modeling computer networks under nonstationary conditions. IEEE J. Sel. Areas Commun. 1990, 8, 1682–1695. [Google Scholar] [CrossRef]
- Misra, V.; Gongnad, W.B.; Towsley, D. A Fluid-based Analysis of a Network of AQM Routers Supporting TCP Flows with an Application to RED. In Proceedings of the Conference on Applications, Technologies, Architectures and Protocols for Computer Communication (SIGCOMM 2000), Stockholm, Sweden, 28 August–1 September 2000; ACM: New York, NY, USA, 2000; pp. 152–160. [Google Scholar] [CrossRef]
- Gelenbe, E. On Approximate Computer Systems Models. J. ACM 1975, 22, 261–269. [Google Scholar] [CrossRef]
- Reinecke, P.; Krauß, T.; Wolter, K. HyperStar: Phase-Type Fitting Made Easy. In Proceedings of the 9th International Conference on the Quantitative Evaluation of Systems (QEST 2012), London, UK, 17–20 September 2012; pp. 201–202. [Google Scholar]
- Czachórski, T.; Nycz, M.; Nycz, T. Modelling transient states in queueing models of computer networks: A few practical Issues. In Distributed Computer and Communication Networks; Vishnevsky, V., Ed.; Springer: Moscow, Russia, 2013; Volume 279, pp. 58–72. [Google Scholar] [CrossRef]
- Czachórski, T.; Gelenbe, E.; Suila, K.; Marek, D. Transient behaviour of a network router. In Proceedings of the 43th International Conference on Telecommunications and Signal Processing (TSP), Milan, Italy, 7–9 July 2020; pp. 246–252. [Google Scholar] [CrossRef]
- Czachórski, T.; Gelenbe, E.; Kuaban, G.S.; Marek, D. Time-Dependent Performance of a Multi-Hop Software Defined Network. Appl. Sci. 2021, 11, 2469. [Google Scholar] [CrossRef]
- Czachórski, T.; Nycz, T.; Pekergin, F. Transient States of Priority Queues—A Diffusion Approximation Study. In Proceedings of the Fifth Advanced International Conference on Telecommunications, AICT 2009, Venice/Mestre, Italy, 24–28 May 2009; pp. 44–51. [Google Scholar] [CrossRef]
- Czachórski, T. A method to solve diffusion equation with instantaneous return processes acting as boundary conditions. Bull. Pol. Acad. Sci. Tech. Sci. 1993, 41, 417–451. [Google Scholar]
- Czachórski, T. Queuing models for performance evaluation of computer networks: Transient state analysis. In Analytic Methods in Interdisciplinary Applications; Mityushev, V., Ruzhansky, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 116, pp. 51–80. [Google Scholar] [CrossRef]
- Cox, R.P.; Miller, H.D. The Theory of Stochastic Processes; Chapman and Hall: London, UK, 1965. [Google Scholar]
- Gelenbe, E.; Pujolle, G. The behaviour of a single queue in a general queueing network. Acta Inform. 1976, 7, 123–136. [Google Scholar] [CrossRef]
- Jaiswal, N.K. Priority Queues, 1st ed.; Academic Press: New York, NY, USA, 1968. [Google Scholar]
- OMNET++ Community Site. Available online: http://www.omnetpp.org/ (accessed on 27 May 2021).
- Czachórski, T.; Pekergin, F. Diffusion approximation as a modelling tool. In Network Performance Engineering; Kouvatsos, D.D., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; Volume 5233, pp. 447–476. [Google Scholar] [CrossRef]
- Czachórski, T.; Gelenbe, E.; Kuaban, G.S.; Marek, D. Time Dependent Diffusion Model for Security Driven Software Defined Networks. In Proceedings of the Second International Workshop on Stochastic Modeling and Applied Research of Technology (SMARTY 2020), CEUR-WS, Petrozavodsk, Russia, 16–20 August 2020; Volume 2792, pp. 38–56. [Google Scholar]
- Burke, P.J. The Output of a Queuing System. Oper. Res. 1956, 4, 699–704. [Google Scholar] [CrossRef] [Green Version]
- Wijeratne, S.; Ekanayake, A.; Jayaweera, S.; Ravishan, D.; Pasqual, A. Scalable High Performance router Architecture on FPGA for Core Networks. In Proceedings of the 2019 ACM/SIGDA International Symposium, Seaside, CA, USA, 24–26 February 2019; ACM: New York, NY, USA, 2019. [Google Scholar] [CrossRef] [Green Version]






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nycz, T.; Czachórski, T.; Nycz, M. Diffusion Model of Preemptive-Resume Priority Systems and Its Application to Performance Evaluation of SDN Switches. Sensors 2021, 21, 5042. https://doi.org/10.3390/s21155042
Nycz T, Czachórski T, Nycz M. Diffusion Model of Preemptive-Resume Priority Systems and Its Application to Performance Evaluation of SDN Switches. Sensors. 2021; 21(15):5042. https://doi.org/10.3390/s21155042
Chicago/Turabian StyleNycz, Tomasz, Tadeusz Czachórski, and Monika Nycz. 2021. "Diffusion Model of Preemptive-Resume Priority Systems and Its Application to Performance Evaluation of SDN Switches" Sensors 21, no. 15: 5042. https://doi.org/10.3390/s21155042
APA StyleNycz, T., Czachórski, T., & Nycz, M. (2021). Diffusion Model of Preemptive-Resume Priority Systems and Its Application to Performance Evaluation of SDN Switches. Sensors, 21(15), 5042. https://doi.org/10.3390/s21155042






