1. Introduction
Global navigation satellite systems (GNSSs) are some of the most important absolute positioning infrastructures, especially for unmanned air vehicles (UAVs) and other unmanned vehicles (UVs). GNSSs can provide precise position information for long periods of time, and the cost of the navigation receiver as a user-end device is low, which greatly expands the applications of GNSSs [
1].
Although the GNSS has incomparable advantage, its defects also should not be ignored. GNSS navigation relies on navigation signals transmitted by satellites from Earth orbits. The transmission power of the navigation signal is limited by the volume, mass, and payload of the satellite, and the signal attenuation after passing through the ionosphere, troposphere, and atmosphere is extremely serious. The receiver is vulnerable to interference or attack. The safety of GNSSs has attracted more and more concern in recent years. GPS spoofing is one of the most important threats affecting the positioning process in GPS receivers [
2].
There are two main types of GNSS interference: suppression (jamming) interference and spoofing interference. Compared with suppression interference, spoofing interference is more concealed and harmful, and anti-spoofing interference methods are more complicated. The purpose of spoofing interference is to deceive the receiver. The spoofing signals are usually created by imitation satellite navigation signals or delayed real navigation signals. The characteristics of the spoofing signals, like phase, frequency, Doppler frequency shift, and others, can be similar to the real signals when the spoofer has been synchronized with real signals. The signal-to-noise ratio (SNR) of the spoofing signal can be set slightly higher than that of the real one, so the receiver can easily lock the spoofing signals and output incorrect positioning solutions. Most UVs and UAVs utilize GNSSs as the only absolute positioning method, so spoofing attacks can damage the whole navigation system without the user being aware. To handle this kind of threat, the application of anti-spoofing technology in modern GNSSs is acquiring more and more attention [
3].
In December 2011, Iran announced the capture of a state-of-the-art US RQ-170 “Sentinel” stealth drone. According to an Iranian engineer who claimed to have participated in the capture mission [
4], they deployed a Global Positioning System (GPS) spoofing attack signal to induce the drone to use the coordinates set by Iran as the coordinates of the US Afghan base when undertaking the automatic return mission. The navigation data of the GPS were modified so that the estimated position of the drone was induced to the spoofer-specified one. In June 2012, Shepard et al. [
5] successfully demonstrated the spoofing of drones at the US Army’s White Sand Missile Range under the supervision of the US Department of Homeland Security. The drone was set to hover mode and spoofing signals were sent to the drone to mimic GPS signals, making the drone mistakenly think that it was moving upwards; as a result, the drone moved downwards to correct itself and finally touched ground. A research team at Austin’s Radio Navigation Laboratory led by Professor Todd Humphreys of the University of Texas has, using GPS spoofing, successfully deceived drones [
6] and the White Rose yacht [
7] and was invited to the US Congress discussion on drone safety.
Spoofing detection methods are generally divided into three categories according to the different detection principles. The first kind is based on detecting abnormal changes in signal characteristics, such the carrier-to-noise ratio [
8], signal power [
9], arrival directions [
10,
11], Doppler effect carrier frequency shift [
12], and so on. This kind of detection technology has the advantage of not requiring other auxiliary information and only utilizing the characteristics of the signal itself. However, the spoofing attacker may have the ability to acquire the receiver’s position and the speed to formulate an advanced spoofing strategy, in which a spoofing signal with similar characteristics to the real signals is generated.
The second kind of detection method is based on the encrypted information in the signal. Previous authors [
13,
14,
15] have discussed the application of signal encryption technology to civilian GNSS receivers. Two studies [
16,
17] introduced a form of spoofing detection technology using symmetrically encrypted GNSS signals, deploying correlation analysis with receivers known to be affected by spoofing interference. Another study [
18] used an encrypted spreading code, in which part of the spreading code is made public and the other part of the key is distributed to the receiver. This kind of method needs to modify the signal structure or navigation message structure, which is difficult to implement in the short term.
The third kind of spoofing detection method is based on utilizing supplementary measurements from other navigation or positioning sensors of the system. One previous study [
19] mentioned the use of the receiver’s clock to monitor the abnormal changes in satellite time information. Others [
9,
17,
20] concentrate on utilizing the auxiliary measurement information obtained by the inertial measurement unit (IMU). For integrated IMU/GNSSs, a Kalman filter (KF) or extended Kalman filter (EKF) is generally used for information fusion. The spoofing detection method based on the IMU always monitors the residuals of the KF or EKF measurements. A previous study [
21] introduced a method of providing auxiliary measurement information by means of a land-based Roland system.
The purpose of a spoofing attack is to mislead the navigation system by inducing the system to estimate an incorrect positioning result. The supplementary measurement methods focus on monitoring the abnormal deviation and the credibility of positioning solutions, highlighting the most important point of the spoofing detection problem. Although the IMU method is used most extensively, it also has some disadvantages restricting its detection performance in some spoofing scenarios. Due to the serious cumulative error, the IMU only has good short-term accuracy. Over time, the positioning solution output of the IMU develops a large deviation. This restricts performance in the detection of induced spoofing signals [
22], which deviate from real signals slowly.
The IMU and cameras are two of the most widely used sensors for UVs and UAVs. Spoofing detection methods based on visual measurements have also been introduced. Qiao [
23] proposed a GPS spoofing detection method based on cameras for small drones. In this study, the speed of the camera, calculated from adjacent frame images using the pyramid Lucas–Kanade (LK) optical flow method, and the speed obtained from the IMU are coupled as the reference speed of the system. The deviation between the reference speed and the instantaneous speed calculated by the GPS receiver is used for spoofing detection. The visual measurement information used in the GNSS spoofing detection is separated from the positioning system and does not fuse with the visual/GNSS information to improve the robustness of the navigation system. Furthermore, the existing coupled visual/inertial/GNSS positioning algorithm does not consider the adverse effect of GNSS spoofing. When the GNSS receiver locks the spoofing signal, the integrated navigation system is deceived and induced to the wrong position.
In order to improve the performance of the aided spoofing detection method using supplementary measurements and protect visual/inertial/GNSS integrated systems from GNSS spoofing, a novel spoofing detection method based on a coupled visual/inertial/GNSS algorithm for UVs/UAVs is proposed in this paper. The coupled visual/inertial/GNSS positioning algorithm has been widely discussed in simultaneous localization and mapping (SLAM) and other fields. In this paper, a well-known, open-source, optimization-based coupled VIO/GNSS positioning algorithm VINS-Fusion is referred to. The KITTI dataset [
24] is used to verify the vulnerability of VINS-Fusion to spoofing attacks. Then, a spoofing detection algorithm based on Chi-square detection is proposed to identify the presence of a spoofing attack, in which a test statistic is calculated based on the residuals and error covariance matrix. A GNSS confidence factor is defined to modify the coupled positioning algorithm and to prevent false spoofing alarms. To evaluate the proposed spoofing detection method, a visual/inertial/GNSS integrated system was established. The experiments were conducted both for the KITTI dataset and the real GNSS spoofing scenarios. The framework structure of the spoofing detection and coupled positioning algorithm proposed in this paper is illustrated in
Figure 1.
The main contributions of this paper can be summarized as follows:
A novel spoofing detection method using visual/inertial estimations as supplementary measurements is proposed, with the spoofing detection factor calculated by residuals and the error covariance matrix;
The spoofing detection and the coupled visual/inertial/GNSS positioning estimation are both considered as part of the coupled positioning system. The vulnerability of the coupled visual/inertial/GNSS algorithms under spoofing attacks is discussed;
The least squares solution for GNSS measurement under spoofing interference is analyzed in order to represent the mechanism of spoofing errors. Suddenly changed and induced spoofing are discussed and modeled;
The experiments for the proposed spoofing detection method and the modified coupled positioning algorithm were conducted both with a dataset and real GNSS spoofing scenarios. The effectiveness of the detection and the superiority of the modified coupled positioning algorithm under GNSS spoofing attacks are shown.
The rest of the paper is organized as follows. In
Section 2, the GNSS model under spoofing attack and the coupled VIO/GNSS algorithm are introduced. Then, the proposed GNSS spoofing detection method is presented in
Section 3. In
Section 4, the performances of the spoofing detection method and the coupled positioning algorithm are evaluated both through dataset experiments and real spoofing experiments.
Section 5 concludes the paper.
3. GNSS Spoofing Detection Method
The GNSS spoofing detection method proposed in this paper is of the same type as the supplementary measurement methods introduced in
Section 1. A novel spoofing detection method based on a coupled visual/inertial/GNSS positioning algorithm is proposed, which is different from the IMU-based method and utilizes VIO estimations as supplementary measurements.
Chi-square () detection is a widely used system-anomaly detection method based on residual analysis. If presents a series of independent random variables following a Gaussian distribution with a mean value of 0 (that is, independent and identically distributed in a Gaussian distribution with a mean value of 0), then the random variables formed by the sum of the squares of random variables will follow the chi-square distribution.
After aligning the time series of the GNSS measurements and VIO estimations, the real location corresponding to the
th GNSS measurement can be expressed as
, which the system is unable to acquire. The final location estimation of the coupled navigation system
in
Section 2 is the optimal estimation of real location
.
The residual of the GNSS measurement and the residual of the VIO estimation can be expressed as:
Without considering the influence of spoofing interference, every GNSS measurement can be analyzed as a variable following a Gaussian distribution with a mean value of the real location . So the residual of the GNSS measurement will follow a Gaussian distribution with a mean value of 0 and an error covariance matrix of . Although the VIO estimation acquires a cumulative error over time, the error in each estimation is independent and will follow a Gaussian distribution. It is reasonable to make approximations at several frames between the two successive optimizations of Equation (16) that assume that the VIO estimation follows a Gaussian distribution with a mean value of the real location . In another words, the residual of the VIO estimation , in a short period, approximately follows a Gaussian distribution with an error covariance matrix of . Between the two successive optimizations of Equation (14), the calculation processes of the GNSS measurements and VIO estimations are totally independent. In this short term perspective, the distributions of and are independently and identically distributed in a Gaussian distribution.
The nature of a Gaussian distribution entails that adding and subtracting the independent Gaussian distributions still results in a Gaussian distribution. The residual between the GNSS measurement and the VIO estimation is calculated as follows:
in which
still approximately follows a Gaussian distribution with an error covariance matrix of
.
To execute the Chi-square detection test, a Chi-square detection factor can be constructed from normalized residuals as follows:
in which
is the normalized residual at the testing moment
, and
is the sum of all normalized residuals in a testing window with a length of
, which means there will be
GNSS VIO residuals in the testing window up to the testing moment. Under normal circumstances,
follows a Gaussian distribution, so
is a Chi-square random variable and follows the Chi-square distribution. The value of the degrees of freedom in this Chi-square distribution is determined by the dimensions of the residual
and the length of the testing window
.
The last procedure in Chi-square detection is hypothesis verification. Based on the degrees of freedom and the selected false detection rate
, a Chi-square threshold
from the table of the Chi-square distribution can be set up to test the Chi-square factor
. Considering the tendency for error accumulation of VIO estimations and the non-Gaussian nature of the VIO residuals, spoofing detection must make some modifications to the Chi-square detection. The spoofing detection threshold should be considered as an amplification of the Chi-square detection threshold by multiplying by a non-Gaussian factor
(
). The hypothesis verification is as follows:
where the result of the hypothesis verification being 1 means that
likely follows a Chi-square distribution with a probability of
, and the result of the hypothesis verification being 0 means that
is likely to not follow a Chi-square distribution.
Under spoofing circumstances, if the GNSS receiver locks the spoofing signals and spoofing deviation
from Equation (10) has been involved in the output
, the spoofing deviation will also be involved in the residual as follows:
in which the residual
has the form of a Gaussian distribution plus spoofing deviation. In these circumstances, the Chi-square detection factor can be described as:
The Chi-square detection factor under spoofing interference in Equation (20) includes two separated parts. represents the real factor without the influence of spoofing, and is from the spoofing interference. The numerical relationship between and can be analyzed from different spoofing patterns and different laws of change for the spoofing deviation .
The residual between the GNSS measurement and the VIO estimation has the magnitude of a meter and is constrained by the accuracy of the GNSS receiver and the VIO estimator. The error covariance matrix and also indicate this character of . The quantity of is decided by the relation between the magnitude of the spoofing deviation and the residual .
In
Section 2.1, suddenly changed spoofing and inducing spoofing were introduced. The spoofing deviation
in suddenly changed spoofing interference has a significant value from the point that the deviation begins. To fulfill the purpose of spoofing the GNSS receiver into the wrong place, the deviation has to be obvious enough. The magnitude of the spoofing deviation
can be tens or hundreds of meters, which is much larger than the residual
.
The spoofing deviation in inducing spoofing is much more complicated. If the spoofing deviation accumulates very quickly and becomes enormous during the testing window, it can be similar to suddenly changed spoofing. Only when the deviation injection rate in Equation (10) is small enough can the spoofing deviation infect the positioning result smoothly and progressively.
By providing an evaluation of GNSS quality from spoofing detection, the GNSS confidence factor
in Equation (16) is varied for the different results of hypothesis verification as follows:
When the result of hypothesis verification is 0, it indicates that the GNSS data is normal and the optimal estimation of GNSS and VIO can be operated normally. However, if the result of hypothesis verification is 1, there is a high probability that the GNSS has been spoofed and the GNSS confidence factor becomes . The constant factor 4 in the denominator ensures that even if the is slightly higher than the threshold, can reduce the weight of the GNSS factor from 1 to under 0.25 to avoid the damage of the questionable GNSS positioning results. The is a quadratic inverse proportion of , and therefore suddenly changed or inducing spoofing can both make rapidly reductions of to 0.01. When is less than 0.01, the GNSS factor drops away to lessen the calculative burden. The benefit of this form of , rather than dropping the GNSS positioning results directly when becomes 1, is that if the detection factor has become slightly higher than the threshold and triggered a false alarm, there is still a chance to fix it after several optimal estimations.
5. Conclusions
GNSS spoofing has been proven to be one of the most dangerous threats to navigation systems. If they are unaware of the existence of GNSS spoofing interference, coupled navigation systems will be corrupted by the damage caused by spoofed GNSS data. In this paper, a spoofing detection method based on a coupled visual/inertial/GNSS positioning algorithm to alert the integrated system of spoofing attack was proposed. The least squares solution of the GNSS measurement under spoofing interference was analyzed to represent the mechanism of the spoofing error. To achieve high-level positioning accuracy, an open-source, optimization-based, coupled VIO/GNSS positioning algorithm was introduced. Then, the damage caused by the spoofed GNSS measurements to the coupled positioning algorithm was analyzed. A modification through the addition of a GNSS confidence factor was made to adapt to the spoofing scenario.
The spoofing detection method proposed in this paper was based on Chi-square detection. The residuals between the GNSS measurements, VIO estimations, and real position were analyzed separately. Spoofing detection statistics were constructed from the residuals and error covariance matrixes.
The KITTI dataset was introduced and modified to simulate a spoofing scenario in this paper. The operating results of the coupled positioning algorithm with the spoofed GPS positioning results indicated that the positioning estimation had been deceived about the authentic location with a spoofed location. The experiment involving the coupled positioning algorithm with spoofing detection indicated that, even with a deviation injection rate in inducing spoofing as small as 1 m/s, the spoofing detection program worked and prevented the positioning result from being induced to a deceptive position. Similar results were found when the deviation injection rate was increased. The positioning errors were compared in two conditions, with and without spoofing detection, and it was found that the former was constrained and at least an order of magnitude smaller than the latter.
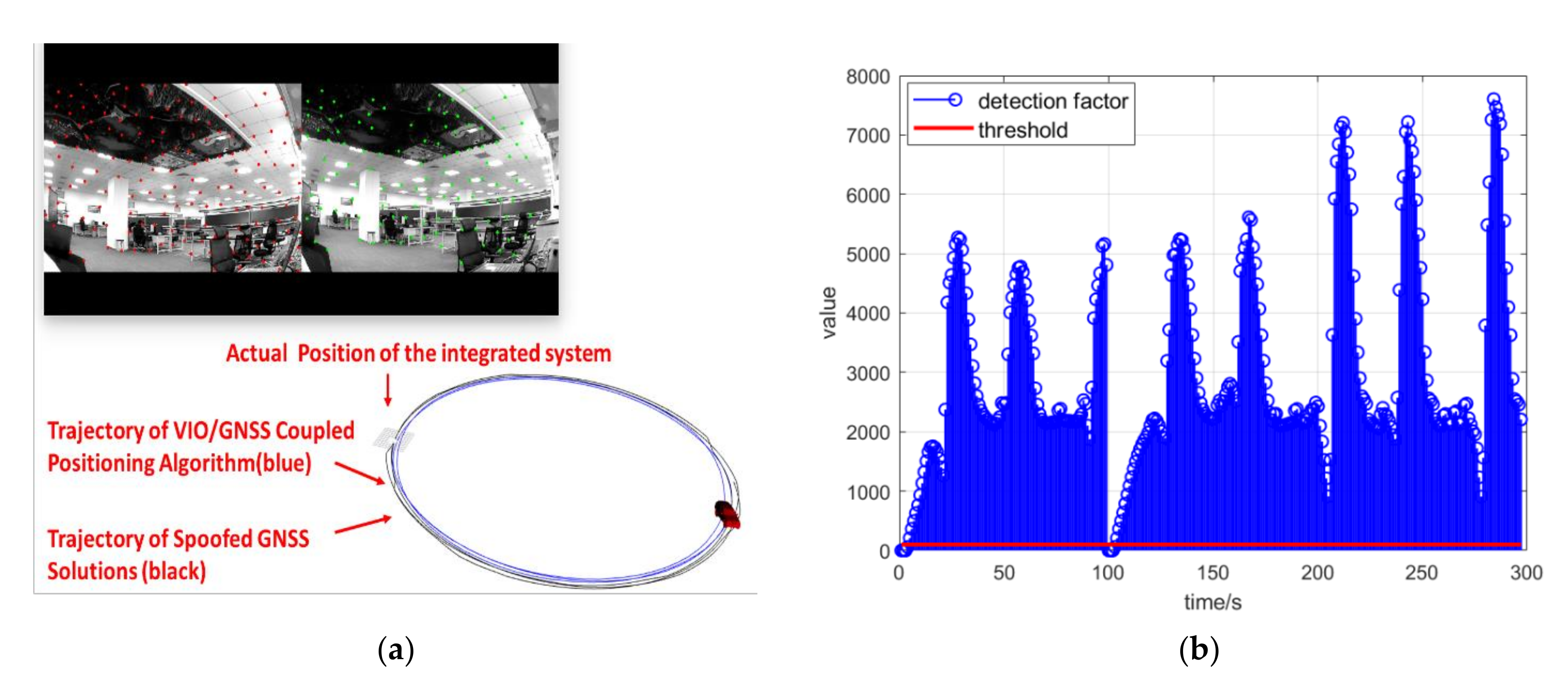
The real spoofing experiment was undertaken using a GNSS spoofer. A spoofing attack was executed after the GNSS receiver of the integrated positioning platform had already locked real GNSS signals. The positioning results of the coupled algorithm were induced to a certain deceptive position or moved following the spoofing trajectory. The spoofing detection algorithm and spoofing detection module were verified to be good supplements to the coupled positioning algorithm against spoofing attacks.
In the results from this paper, the vulnerability of the coupled visual/inertial/GNSS system under inducing spoofing interference was apparent. The spoofing detection method and the modification made to the coupled positioning algorithm proposed in this paper were able settle this problem up to a point. This system could potentially be used in any coupled navigation system that is equipped with a camera, IMU, and GNSS receiver, such as most UVs and UAVs.