Multi-Source Knowledge Reasoning for Data-Driven IoT Security
Abstract
:1. Introduction
- We extracted the relationship between the entries of the IoT security public knowledge bases for knowledge integration, and the relationship mapping link graph model is constructed to provide support for the assessment of threat elements that affect IoT security;
- An IoT security threat ontology framework is proposed to describe the correlation of threat objects. The framework expands the current knowledge domain of network security ontology modeling and can provide a wider sense of security status;
- This paper proposes a reasoning method based on the multi-source knowledge of IoT security, which can perceive highly vulnerable platforms in the IoT environment and automatically respond to threats.
2. Related Work
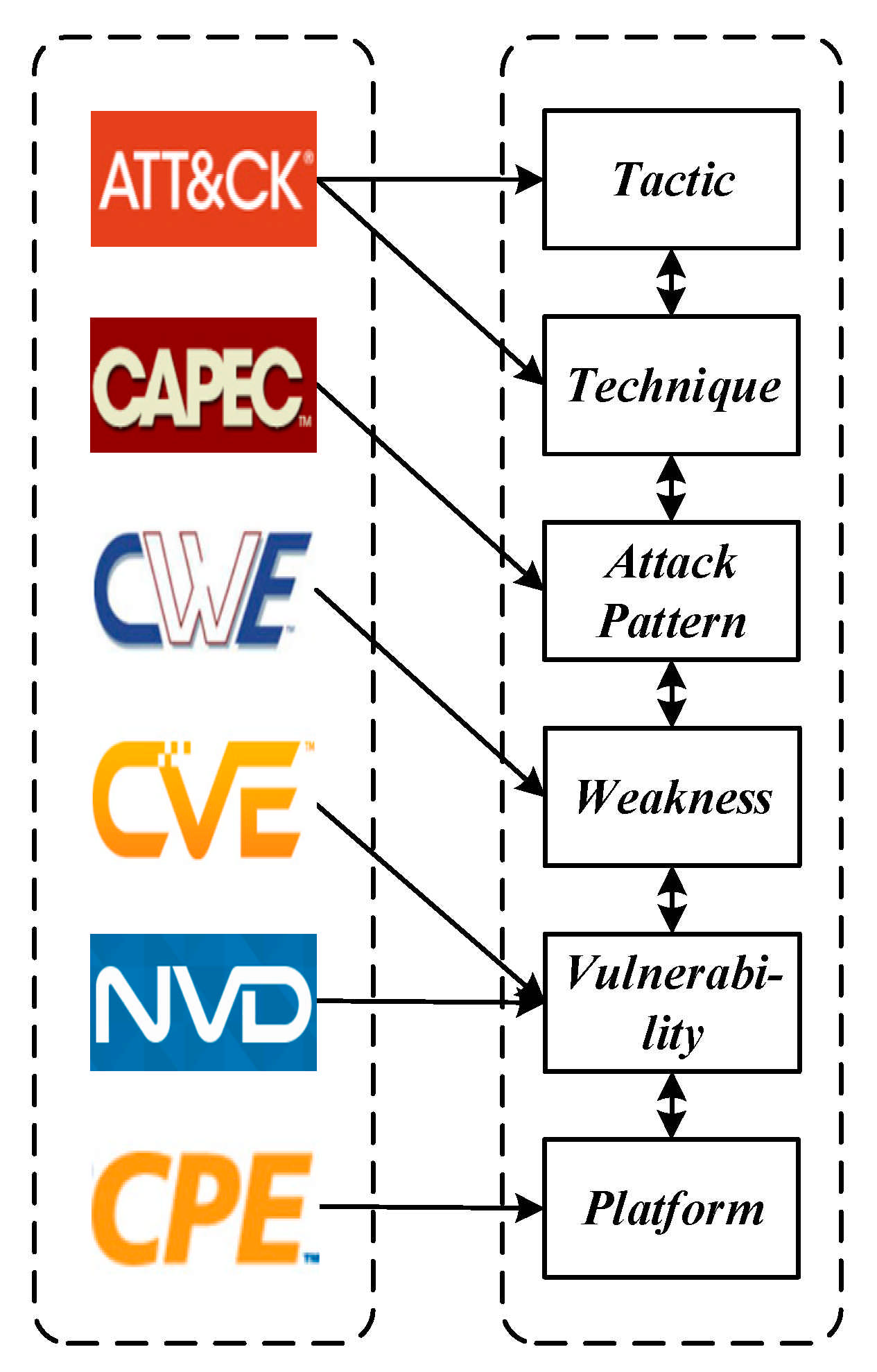
3. IoT Security Multi-Source Knowledge Base
- Common Vulnerabilities and Exposures (CVE) [25];
- National Vulnerability Database (NVD) [26];
- Common Weakness Enumeration (CWE) [27];
- Common Attack Pattern Enumeration and Classification (CAPEC) [28];
- Common Platform Enumeration (CPE) [29];
- Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) matrix [30].
3.1. Data Sources
3.2. ATT&CK Matrix
3.3. Knowledge Integration and Relationship Mapping
4. Ontology-Based Multi-Source Knowledge Reasoning Framework for IoT Security
- The multi-source heterogeneous IoT security knowledge is obtained from crawlers embedded in several knowledge sources. The amount of knowledge is huge and the structure of the knowledge is different;
- The crawled multi-source heterogeneous knowledge is integrated into a unified graph database;
- The integrated data are mapped into the proposed ontology model through instance mapping, and the generated instances are integrated into the ontology repository;
- The inference engine perceives and separates the abnormalities based on the instances repository and the user-defined inference rules to achieve the goal of automatically responding to threats.
4.1. Classes and Attributes Analysis of IoTSTO
4.1.1. Ontology Description of the Platform
ProductPlatform ∩hasPlatformType.PT (Application∪Hardware∪OperatingSystem)hasSupplyChain. String ∩hasVendor. String ∩hasVersion. Version ∩hasStatus. Status (Normal Vulnerable∪Serious Vulnerable ∪ Critical Vulnerable)
4.1.2. Ontology Description of the Vulnerability
Vulnerability (CVE-2017-7921)∩hasSeverity. Severity(Critical) ∩hasAttackVector. AV (Network) ∩hasAttackComplexity. AC (Low) ∩hasPrivilegesRequired. PR (None) ∩hasUserInteraction. UI (None) ∩hasScope. S (Changed) ∩hasConfidentiality. C (High) ∩hasIntegrity. I (High) ∩hasAvailability. A (High) ∩exploitedBy. AttackPattern (Token Impersonation ∪ Session Hijacking)
4.1.3. Ontology Description of the Weakness
Improper Authentication WeaknessType (Improper Access Control)Weakness ∩hasCWE_ID. CWE_ID (CWE-287) ∩hasApplicablePlatform. String ∩hasWeaknessMitigation. String ∩hasModesOfIntroduction. MOI (Phase ∩ Note) ∩hasLikelihoodOfExploit. LOE (High)
4.1.4. Ontology Description of the Attack Pattern
AttackMechanism (Session Hijacking) AttackPattern ∩hasCAPEC_ID. CAPEC_ID (CAPEC-593) ∩hasAttackLikelihood. AL (High) ∩hasAttackPatternMitigation. String ∩hasConsequence. C (Scope ∩ Impact) ∩hasPrerequisite. String ∩hasResourcesRequired. String
4.1.5. Ontology Description of the Campaign
Technique (Man-in-the-Middle) Campaign ∩belongToTactic. TA (Credential Access ∩ Collection) ∩hasSubTechnique. SubT (LLMNR/NBT-NS Poisoning and SMB Relay ∩ ARP CachePoisoning) ∩hasMitigation. String ∩hasSoftware. (Tool ∩ Malware) ∩hasThreatGroup. Group
4.2. Rule of Inference Design
5. Examples and Evaluation
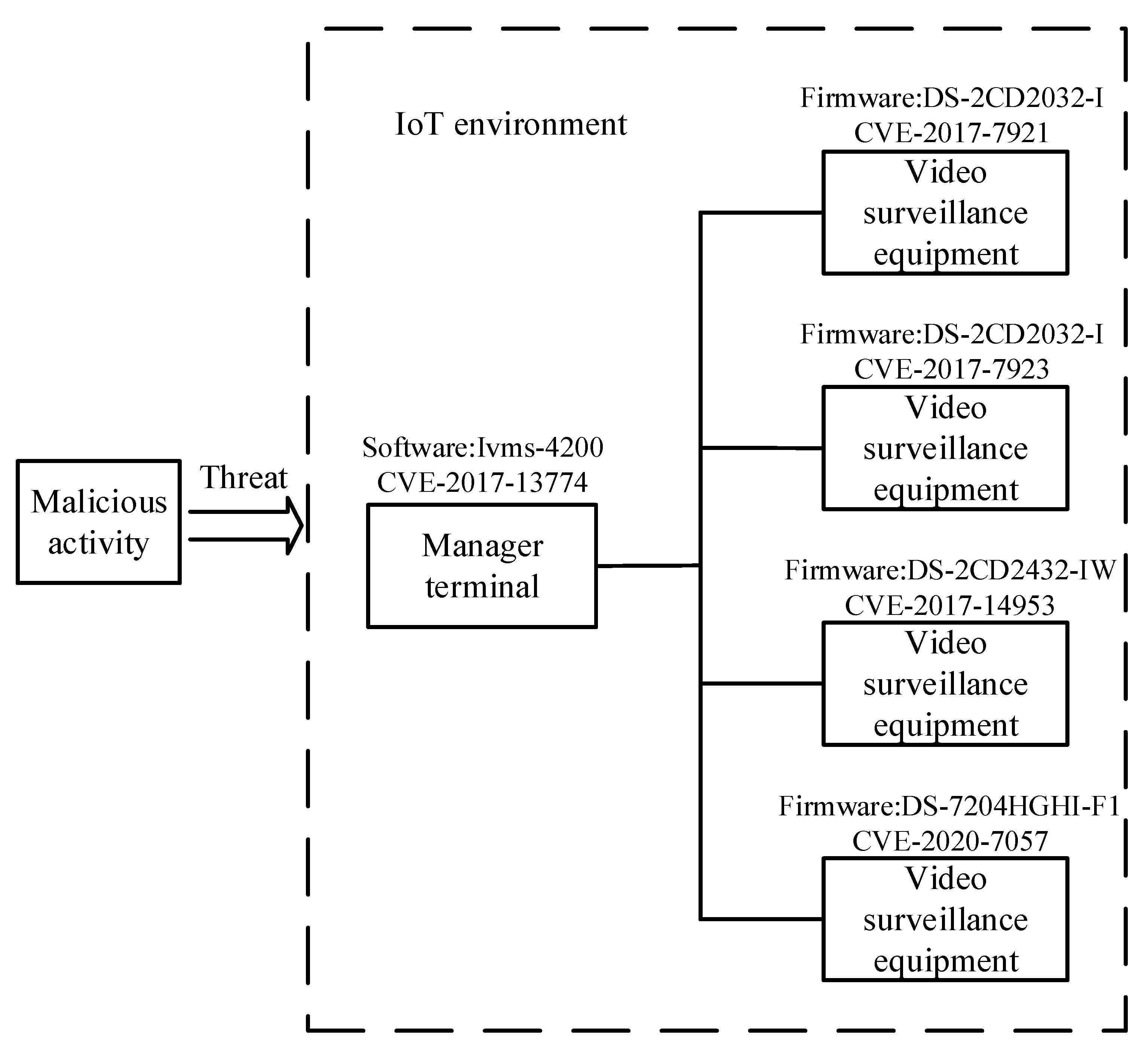
5.1. Linkage Example and Feasibility Analysis
- Tactic (TA0004) Privilege Escalation: This adversary is trying to gain higher-level permissions. Privilege Escalation consists of techniques that adversaries use to gain higher-level permissions in a system or network. Adversaries can often enter and explore a network with unprivileged access but require elevated permissions to follow through on their objectives. Obtaining an account that is necessary for attackers to achieve their goals of gaining access to a specific system or performing a specific authorized operation can also be considered a privilege escalation. Common approaches are taking advantage of system weaknesses, misconfigurations, and vulnerabilities.
- Tactic (TA0005) Defense Evasion: This adversary is trying to avoid being detected. Defense Evasion consists of techniques that adversaries use to avoid detection throughout their compromise. Adversaries also leverage and abuse trusted processes to hide and masquerade their malware.
- Technique (T1134) Access Token Manipulation: Adversaries may modify access tokens to operate under a different user or system security context to perform actions and bypass access controls. The operation system, such as Windows, uses access tokens to determine the ownership of a running process. A user can manipulate access tokens to make a running process appear as though it is the child of a different process or belongs to someone other than the user that started the process.
- Attack Pattern (CAPEC-633) Token Impersonation: An adversary exploits a weakness in authentication to create an access token that impersonates a different entity, and then associates a process to that that impersonated token. Attackers can use this operation to use tokens to verify identity and take actions based on that identity.
- Weakness (CWE-287) Improper Authentication: When an actor claims to have a given identity, the platform does not prove or insufficiently proves that the claim is correct.
- Vulnerability: CVE-2017-7921. The improper authentication vulnerability occurs when an application does not adequately or correctly authenticate users. This may allow a malicious user to escalate his or her privileges on the system and gain access to sensitive information.
- Affected platform and CPE: “cpe:2.3:o: hikvision:ds-2cd2032-i_firmware:-:*:*:*:*:*:*:*’,” According to the CPE entry, the affected platforms are Hikvision video surveillance devices with firmware version DS-2CD2032-I.
5.2. Inference Rules Based on Multi-Source Knowledge of IoT Security
- A video surveillance device with firmware DS-2CD2032-I is deployed in the IoT. According to the explicit knowledge in the knowledge bases CVE and NVD, this video surveillance device has a CVE-2017-7921 vulnerability, and the Severity is CriticalSeverity;
- System classifies the Status describing the vulnerability of the devices as CriticalVulnerable, which is based on the Severity of the Vulnerability associated with the video surveillance device
- According to the explicit knowledge in the knowledge base CAPEC and the ATT&CK matrix, the Attack Pattern Token Impersonation is mapped to Technique T1134. System analyzes related threat events, which can infer appropriate Mitigations to mitigate threat activities that may be generated by adversaries.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Borgia, E. The internet of things vision: Key features, applications and open issues. Comput. Commun. 2014, 1, 1–31. [Google Scholar] [CrossRef]
- Mohammad, S.J.; Jessica, P.K.; Michael, S.; Stuart, M. The internet of things promises new benefits and risks: A systematic analysis of adoption dynamics of IoT products. IEEE Secur. Priv. 2019, 17, 39–48. [Google Scholar]
- CISA: Advanced Persistent Threat Compromise of Government Agencies, Critical Infrastructure, and Private Sector Organizations. Available online: https://us-cert.cisa.gov/ncas/alerts/aa20-352a (accessed on 27 October 2021).
- SECURELIST by Kaspersky: Popular Server Management Software Hit in Supply Chain Attack. Available online: https://securelist.com/shadowpad-in-corporate-networks/81432/ (accessed on 27 October 2021).
- Song, F.; Ai, Z.; Zhou, Y.; You, I.; Zhang, H. Smart collaborative automation for receive buffer control in multipath industrial networks. IEEE Trans. Ind. Inform. 2020, 16, 1385–1394. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Schinagl, S.; Schoon, K.; Paans, R. A framework for designing a security operations centre (SOC). In Proceedings of the 2015 48th Hawaii International Conference on System Sciences (HICSS), Washington, DC, USA, 5–8 January 2015; pp. 2253–2262. [Google Scholar]
- Antonio, L.M.; Fabio, M.; Francesco, M.; Andrea, S.; Mina, S. D-BRIDEMAID: A distributed framework for collaborative and dynamic analysis of android malware. JoWUA 2020, 11, 1–28. [Google Scholar]
- Zeshan, F.; Ahmad, A.; Abdel-Aty, A.-H.; Algarni, F.; Mahmoud, E.E.; Ahmad, A. A hybrid semantic knowledge integration and sharing approach for distributed smart environments. Sensors 2020, 20, 5918. [Google Scholar] [CrossRef]
- Clayton, J.; Bishal, K.; Ram, B.B.; Tenzin, D. Towards detecting and classifying malicious URLs using deep learning. JoWUA 2020, 11, 31–48. [Google Scholar]
- Davide, C.; Luca, V.; Andrea, R.; Alessio, M.; Luca, C. Fine-hearing Google Home: Why silence will not protect your privacy. JoWUA 2020, 11, 35–53. [Google Scholar]
- Syed, Z.; Padia, A.; Finin, T.; Mathews, L.; Joshi, A. UCO: A unified cybersecurity ontology. In Proceedings of the 2016 AAAI Workshop on Artificial Intelligence for Cyber Security, Menlo Park, CA, USA, 12 February 2016. [Google Scholar]
- Abbas, S.G.; Vaccari, I.; Hussain, F.; Zahid, S.; Fayyaz, U.U.; Shah, G.A.; Bakhshi, T.; Cambiaso, E. Identifying and mitigating phishing attack threats in IoT use cases using a threat modelling approach. Sensors 2021, 21, 4816. [Google Scholar] [CrossRef]
- Huang, K.; Lian, Y.; Feng, D.; Zhang, H.; Liu, Y.; Ma, X. Cyber security threat intelligence sharing model based on blockchain. J. Comput. Res. Dev. 2020, 57, 836–846. [Google Scholar]
- Kiesling, E.; Ekelhart, A.; Kurniawan, K.; Ekaputra, F. The SEPSES knowledge graph: An integrated resource for cybersecurity. In Proceedings of the Semantic Web—ISWC 2019, Auckland, New Zealand, 26–30 October 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 198–214. [Google Scholar]
- Tian, J.; Tian, Z.; Qi, W.; Hao, H.; Li, R.; Li, X.; Qiao, H.; Xue, H. Threat propagation based security situation quantitative assessment in multi-node network. J. Comput. Res. Dev. 2017, 54, 731–741. [Google Scholar]
- Jia, Y.; Qi, Y.L.; Shang, H.J.; Li, A. A practical approach to constructing a knowledge graph for cybersecurity. Engineering 2018, 4, 53–60. [Google Scholar] [CrossRef]
- Rastogi, N.; Dutta, S.; Zaki, M.J.; Gittens, A.; Aggarwal, C. MALOnt: An ontology for malware threat intelligence. arXiv 2020, arXiv:2006.11446. [Google Scholar]
- Mozzaquatro, B.; Goncalves, R.J.; Agostinho, C. Towards a reference ontology for security in the internet of things. In Proceedings of the 2015 IEEE International Workshop on Measurements & Networking, Coimbra, Portugal, 12–13 October 2015; pp. 1–6. [Google Scholar]
- Choi, C.; Choi, J. Ontology-based security context reasoning for power IoT-cloud security service. IEEE Access 2019, 7, 110510–110517. [Google Scholar] [CrossRef]
- Si, C.; Zhang, H.Q.; Wang, Y.W.; Yang, Y. Research on network security situational elements knowledge base model based on ontology. Comput. Sci. 2015, 42, 173–177. [Google Scholar]
- Li, T.; Lin, J.C.; Hu, A.Q. Ontology model based on security parameters capturing process for network systems. Chin. J. Netw. Inf. Secur. 2017, 3, 39–45. [Google Scholar]
- Mozzaquatro, B.; Agostinho, C.; Goncalves, D.; Martins, J.; Goncalves, R.J. An ontology-based cybersecurity framework for the internet of things. Sensors 2018, 18, 3053. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Igor, T.; Petra, G. Towards the open ontology for IoT ecosystem’s security. In Proceedings of the 2020 43rd International Convention on Information, Communication and Electronic Technology (MIPRO), Opatija, Croatia, 28 September 2020. [Google Scholar]
- MITRE. Common Vulnerabilities and Exposure. Available online: https://cve.mitre.org/ (accessed on 15 December 2020).
- NIST. National Vulnerability Databased. Available online: https://nvd.nist.gov (accessed on 15 December 2020).
- MITRE. Common Weakness Enumeration. Available online: https://cwe.mitre.org/ (accessed on 15 December 2020).
- MITRE. Common Attack Pattern Enumeration and Classification. Available online: https://capec.mitre.org/ (accessed on 15 December 2020).
- NIST. Common Platform Enumeration. Available online: https://nvd.nist.gov/Products/CPE (accessed on 15 December 2020).
- MITRE. ATT&CK Matrix for Enterprise. Available online: https://attack.mitre.org/ (accessed on 15 December 2020).
- FIRST. Common Vulnerability Scoring System. Available online: https://www.first.org/cvss/ (accessed on 15 December 2020).
- MITRE. Common Weakness Enumeration. Available online: https://cwe.mitre.org/about/index.html (accessed on 15 December 2020).
- Cheng, X.; Zhang, J.; Chen, B. Cyber situation comprehension for IoT systems based on APT alerts and logs correlation. Sensors 2019, 19, 4045. [Google Scholar] [CrossRef] [Green Version]
- Dong, C.; Jiang, B.; Lu, Z.G.; Liu, B.; Li, N.; Ma, P. Knowledge graph for cyberspace security intelligence: A survey. J. Cyber Secur. 2020, 5, 56–76. [Google Scholar]
- Abhishta, A.; Wouter, V.H.; Marianne, J.; Lambert, J.M.N.; Reinoud, J. Why would we get attacked? An analysis of attacker’s aims behind DDoS attacks. JoWUA 2020, 11, 3–22. [Google Scholar]
- Yang, Z.M.; Li, Q.; Liu, J.R. Research of threat intelligence sharing and using for cyber attack attribution. J. Inf. Secur. Res. 2015, 1, 37–42. [Google Scholar]
- Song, F.; Zhu, M.; Zhou, Y.; You, I.; Zhang, H. Smart collaborative tracking for ubiquitous power IoT in edge-cloud interplay domain. IEEE Internet Things J. 2020, 7, 6046–6055. [Google Scholar] [CrossRef]
- Kasturi, G.S.; Jain, A.; Singh, J. Detection and classification of radio frequency jamming attacks using machine learning. JoWUA 2020, 11, 49–62. [Google Scholar]
- Xu, G.Q.; Cao, Y.; Ren, Y.Y.; Li, X.; Feng, Z. Network security situation awareness based on semantic ontology and user-defined rules for internet of things. IEEE Access 2017, 5, 21046–21056. [Google Scholar] [CrossRef]
- Lee, O.J.; Nguyen, H.L.; Jung, J.E.; Um, T.; Lee, H. Towards ontological approach on trust-aware ambient services. IEEE Access 2017, 5, 1589–1599. [Google Scholar] [CrossRef]
- Li, J.; Li, X.L.; Yang, B.; Sun, X. Segmentation-based image copy-move forgery detection scheme. IEEE Trans. Inf. Forensics Secur. 2017, 10, 507–518. [Google Scholar]
- W3C Semantic Web. Available online: https://www.w3.org/OWL/ (accessed on 17 March 2021).
- Qin, S.Z.; Chow, K.P. Automatic analysis and reasoning based on vulnerability knowledge graph. In Cyberspace Data and Intelligence, and Cyber-Living, Syndrome, and Health; Springer: Berlin/Heidelberg, Germany, 2019; pp. 3–19. [Google Scholar]
- Ian, H.; Peter, F.P.; Harold, B.; Said, T.; Benjamin, G.; Mike, D. SWRL: A Semantic Web Rule Language Combining OWL and RuleML. Available online: http://www.daml.org/rules/proposal/ (accessed on 15 April 2021).
- Peng, C.; Goswami, P. Meaningful integration of data from heterogeneous health services and home environment based on ontology. Sensors 2019, 19, 1747. [Google Scholar] [CrossRef] [Green Version]
- Song, F.; Li, L.; You, I.; Zhang, H. Enabling heterogeneous deterministic networks with smart collaborative theory. IEEE Netw. 2021, 35, 64–71. [Google Scholar] [CrossRef]
- Song, F.; Ai, Z.; Zhang, H.; You, I.; Li, S. Smart collaborative balancing for dependable network components in cyber-physical systems. IEEE Trans. Industr. Inform. 2021, 17, 6916–6924. [Google Scholar] [CrossRef]
- Song, F.; Zhou, Y.; Wang, Y.; Zhao, T.; You, I.; Zhang, H. Smart collaborative distribution for privacy enhancement in moving target defense. Inform. Sci. 2019, 479, 593–606. [Google Scholar] [CrossRef]
- Shang, H.J.; Rong, J.; Li, A.P.; Wei, W. A framework to construct knowledge base for cyber security. In Proceedings of the 2017 IEEE Second International Conference on Data Science in Cyberspace, Shenzhen, China, 26–29 June 2017; pp. 242–248. [Google Scholar]
- Zhu, L.N.; Zhang, Z.C.; Xia, G.E.; Jiang, C. Research on vulnerability ontology model. In Proceedings of the 2019 IEEE 8th Joint International Information Technology and Artificial Intelligence Conference (ITAIC), Chongqing, China, 24–26 May 2019; pp. 657–661. [Google Scholar]
- Qi, Y.L.; Jiang, R.; Jia, Y.; Li, A. Attack analysis framework for cyber-attack and defense test platform. Electronics 2020, 9, 1413. [Google Scholar] [CrossRef]










| Level | Class | Level | Class |
|---|---|---|---|
| 2 | Platform | 3 | Status, Platform_Type, Product, Supply_Chain, Vendor, Version |
| 2 | Vulnerability | 3 | CVSS, Impact, Severity |
| 2 | Weakness | 3 | CWE_ID, Modes_Of_Introduction, Weakness_Type, Applicable_Platform, Weakness_Mitigation, Likelihood_Of_Exploit |
| 2 | Attack Pattern | 3 | CAPEC_ID, Attack_Likelihood, Attack_Mechanism, Attack_Pattern_Mitigation, Consequence, Prerequisite, Resources_Required |
| 2 | Campaign | 3 | Malware, Mitigation, Tactic, Technique, Threat_Group, Tool, Sub-Technique |
| IoT Platform | Vulnerability | CVSS V3 | Severity |
|---|---|---|---|
| DS-2CD2032-I | CVE-2017-7921 | 10.0 | Critical |
| DS-2CD2032-I | CVE-2017-7923 | 8.8 | High |
| Ivms-4200 | CVE-2017-13774 | 7.8 | High |
| DS-2CD2432-IW | CVE-2017-14953 | 6.5 | Medium |
| DS-7204HGHI-F1 | CVE-2020-7057 | 5.3 | Medium |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, S.; Bai, G.; Li, H.; Liu, P.; Zhang, M.; Li, S. Multi-Source Knowledge Reasoning for Data-Driven IoT Security. Sensors 2021, 21, 7579. https://doi.org/10.3390/s21227579
Zhang S, Bai G, Li H, Liu P, Zhang M, Li S. Multi-Source Knowledge Reasoning for Data-Driven IoT Security. Sensors. 2021; 21(22):7579. https://doi.org/10.3390/s21227579
Chicago/Turabian StyleZhang, Shuqin, Guangyao Bai, Hong Li, Peipei Liu, Minzhi Zhang, and Shujun Li. 2021. "Multi-Source Knowledge Reasoning for Data-Driven IoT Security" Sensors 21, no. 22: 7579. https://doi.org/10.3390/s21227579
APA StyleZhang, S., Bai, G., Li, H., Liu, P., Zhang, M., & Li, S. (2021). Multi-Source Knowledge Reasoning for Data-Driven IoT Security. Sensors, 21(22), 7579. https://doi.org/10.3390/s21227579






