Covert Information Mapped Spatial and Directional Modulation toward Secure Wireless Transmission
Abstract
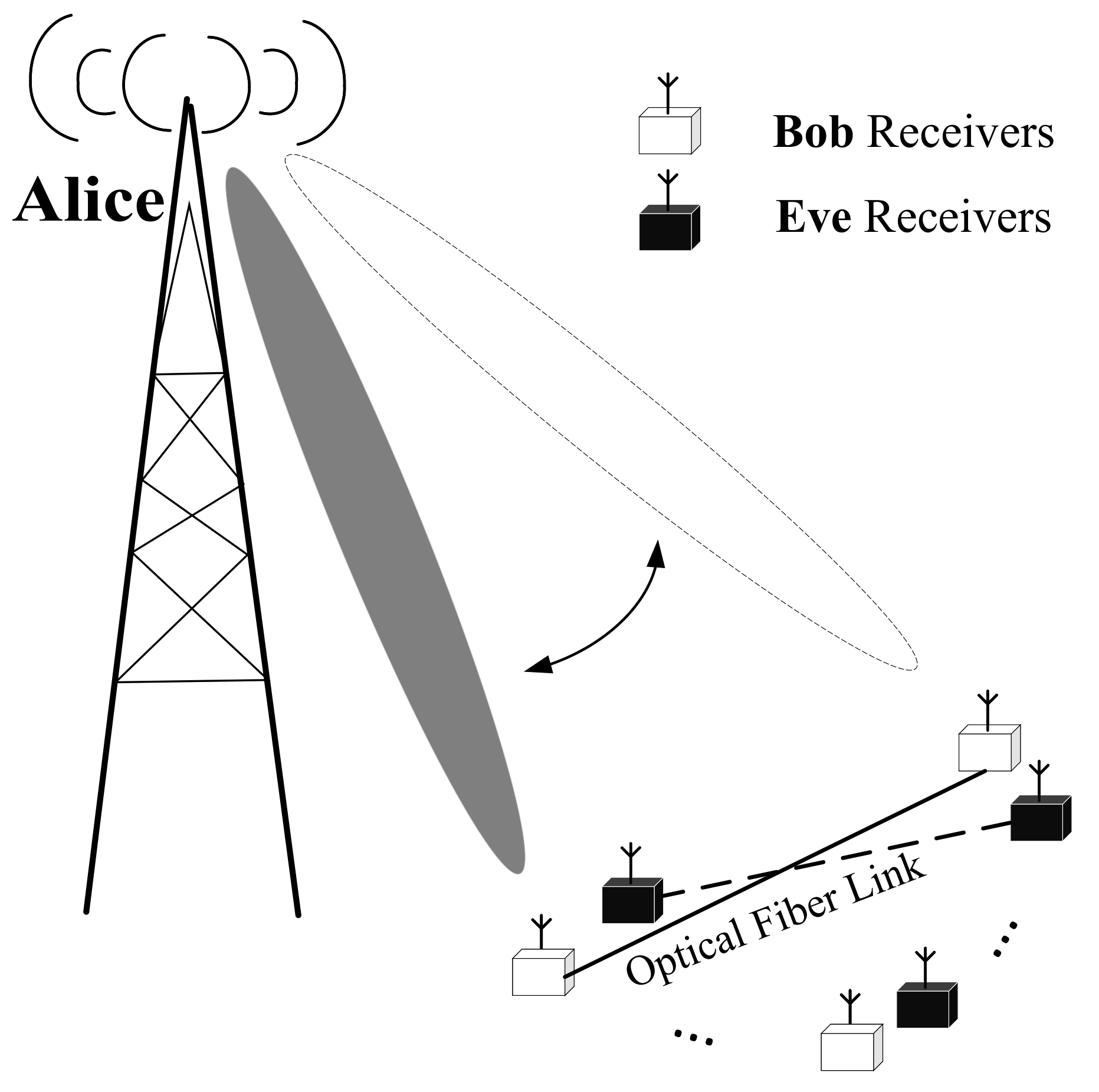
:1. Introduction
2. Convert Information Mapping for SDM
2.1. Traditional SDM System Model
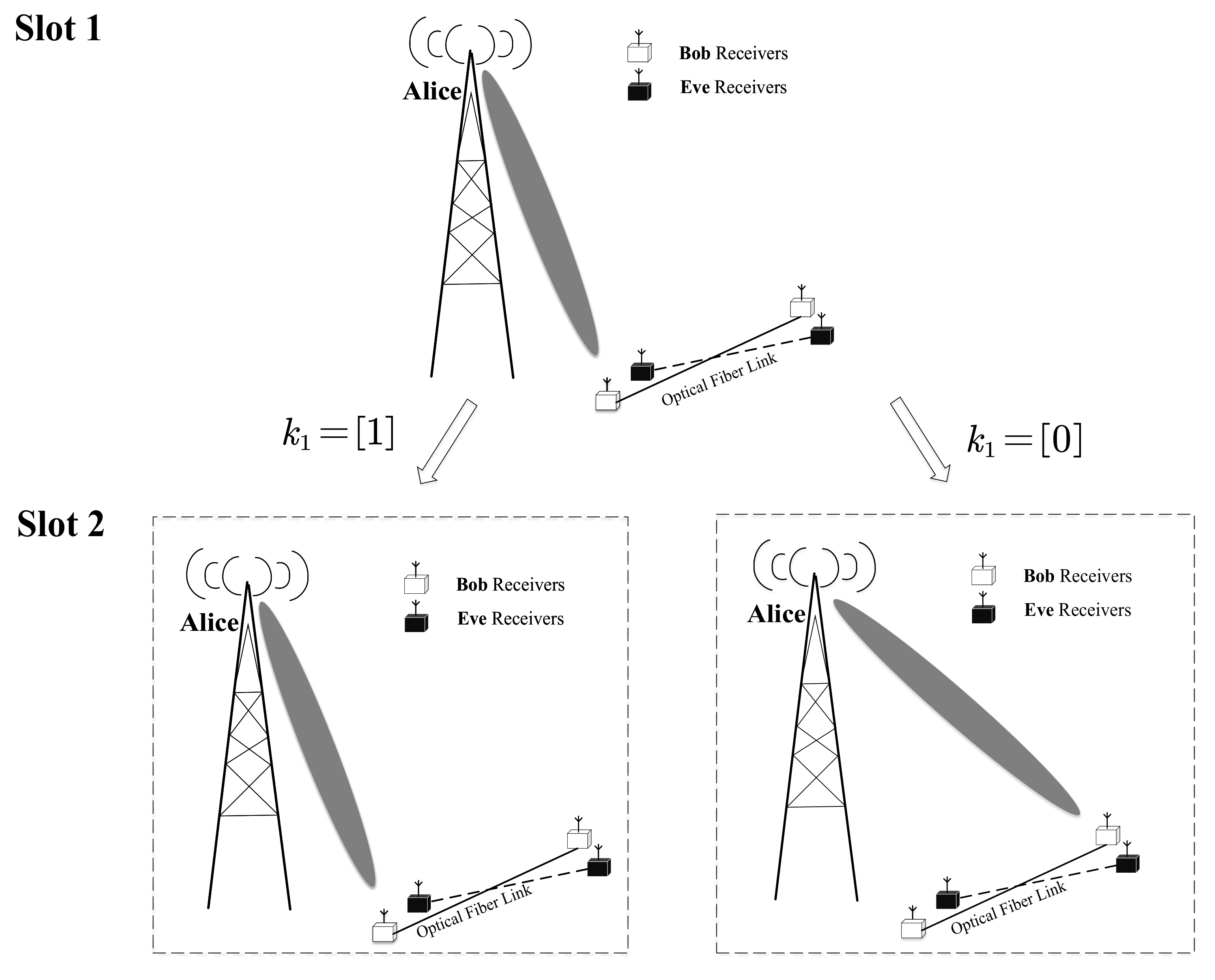
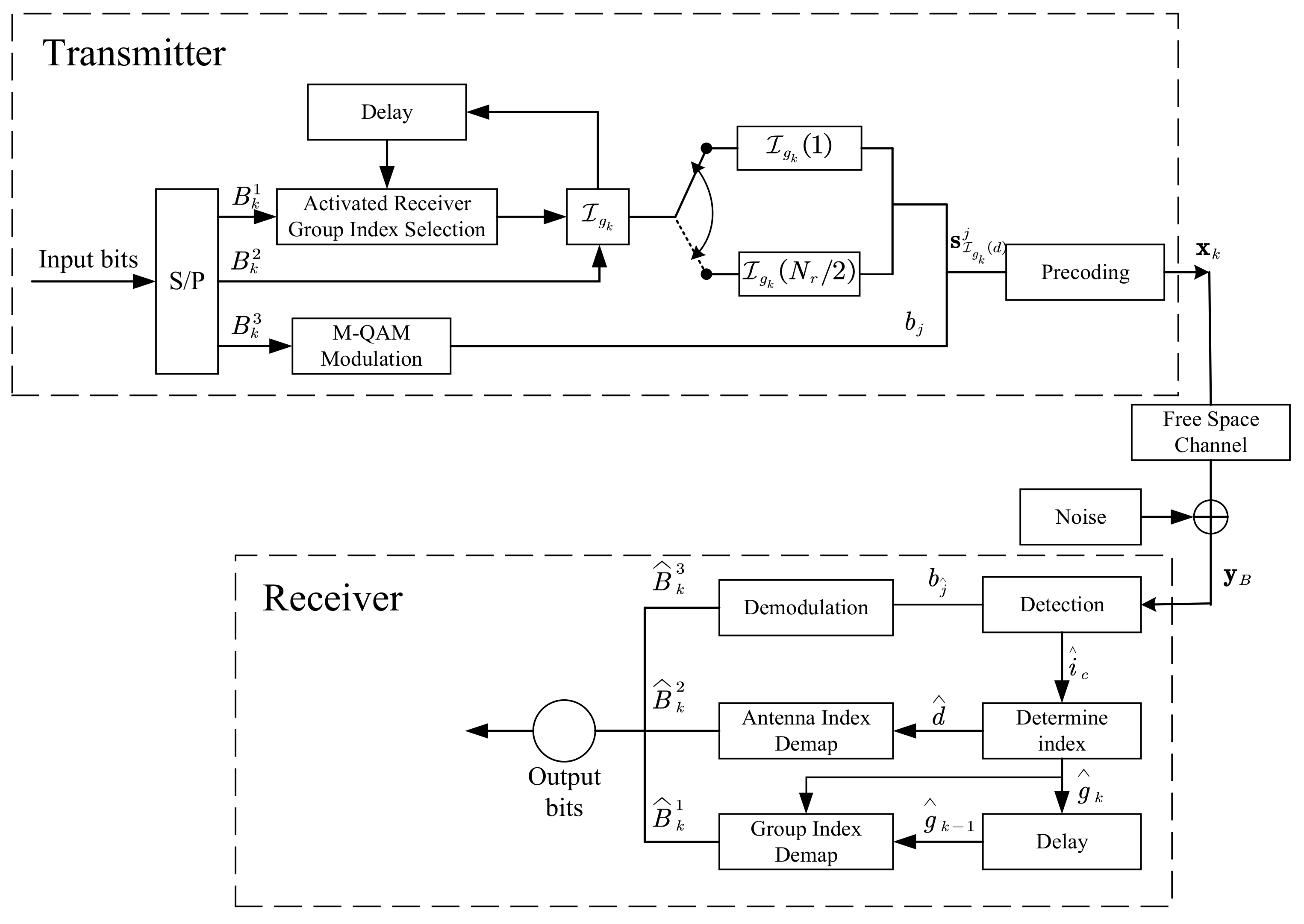
2.2. Proposed CIM-SDM Scheme
2.3. Detection Algorithm for the Proposed Scheme
3. Performance Analysis
3.1. Bob’s Average Bit Error Probability
3.2. Eve’s Average Bit Error Probability
4. Performance Evaluation
4.1. The Implementation of the Simulation Model
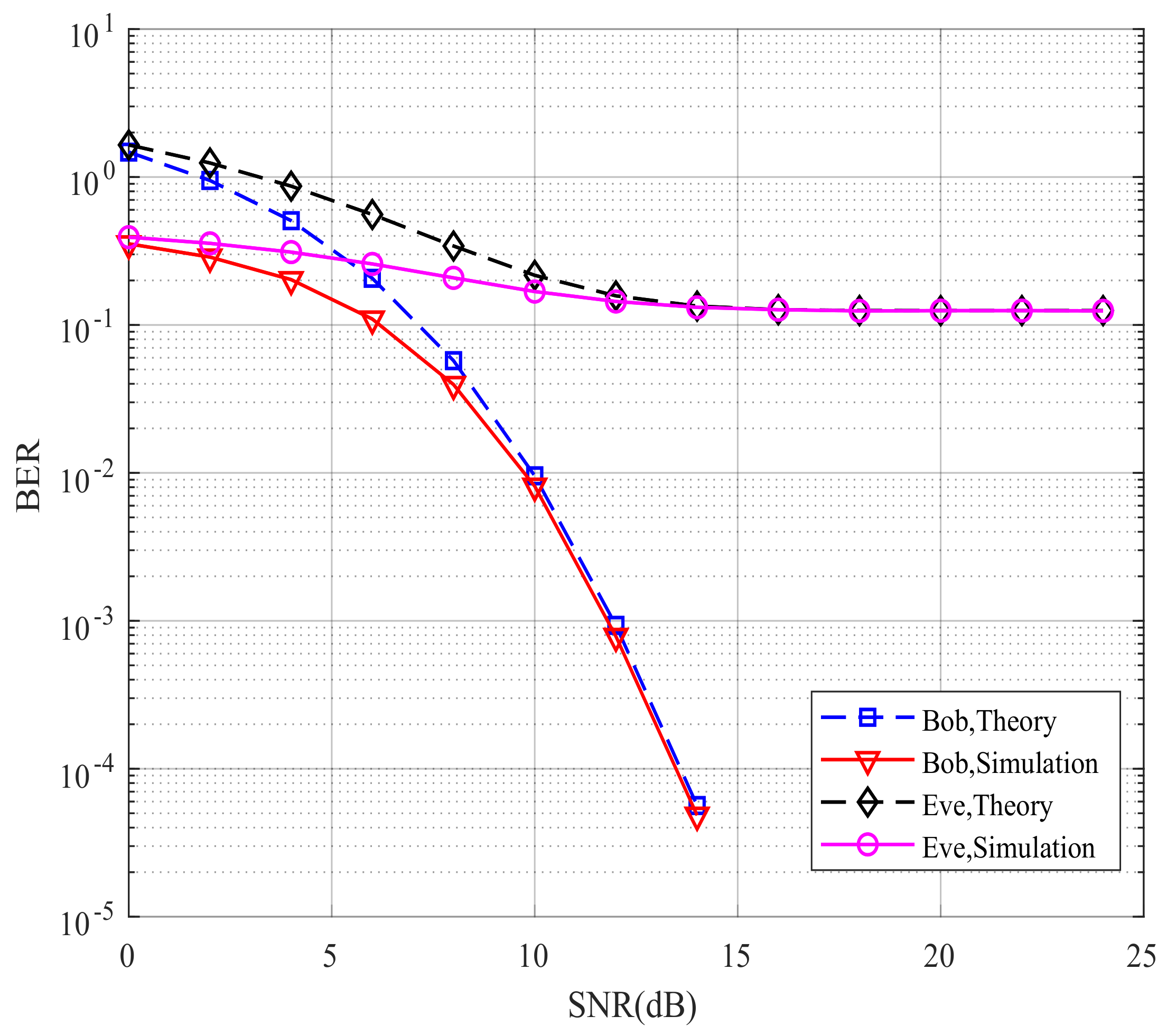
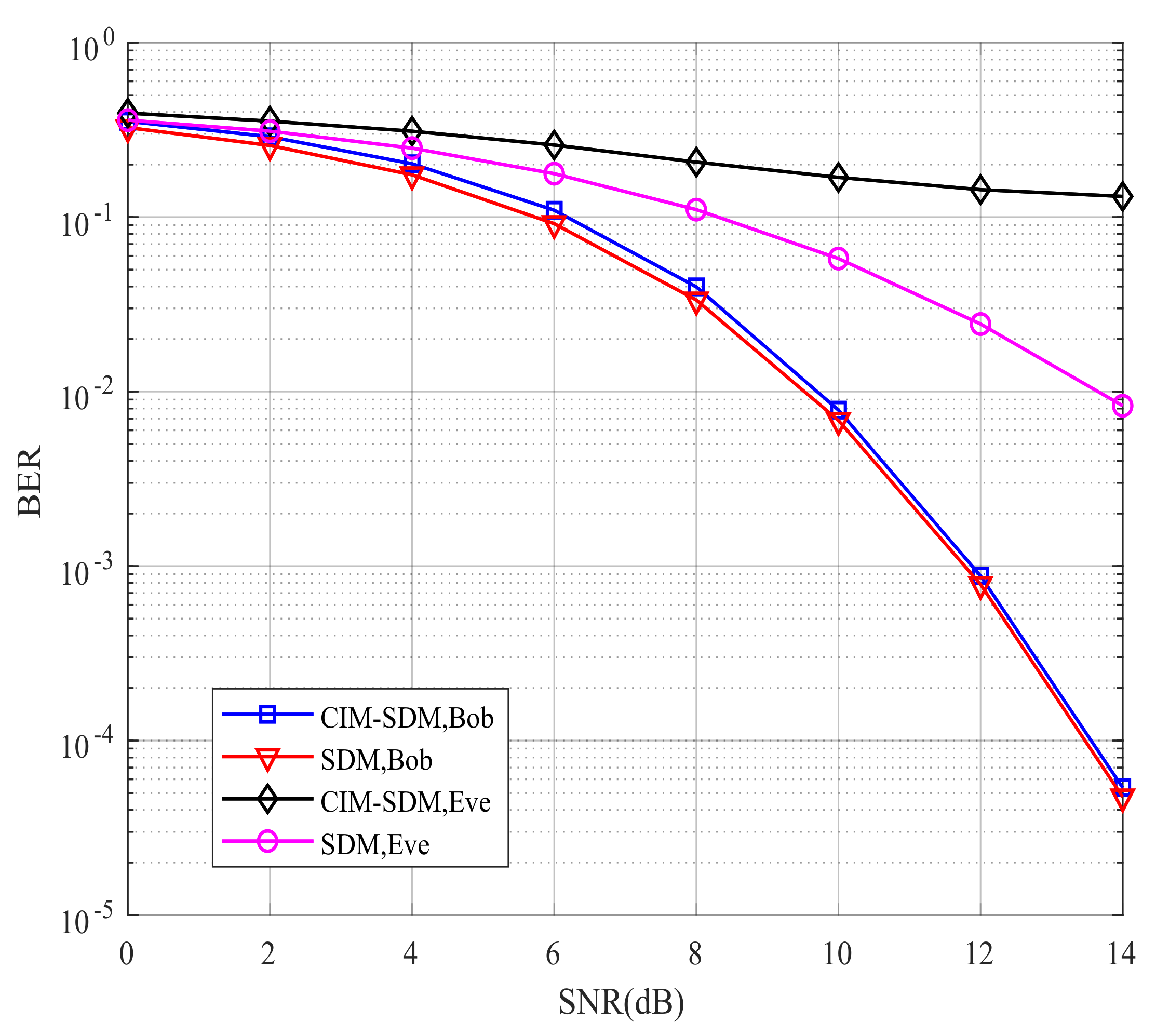
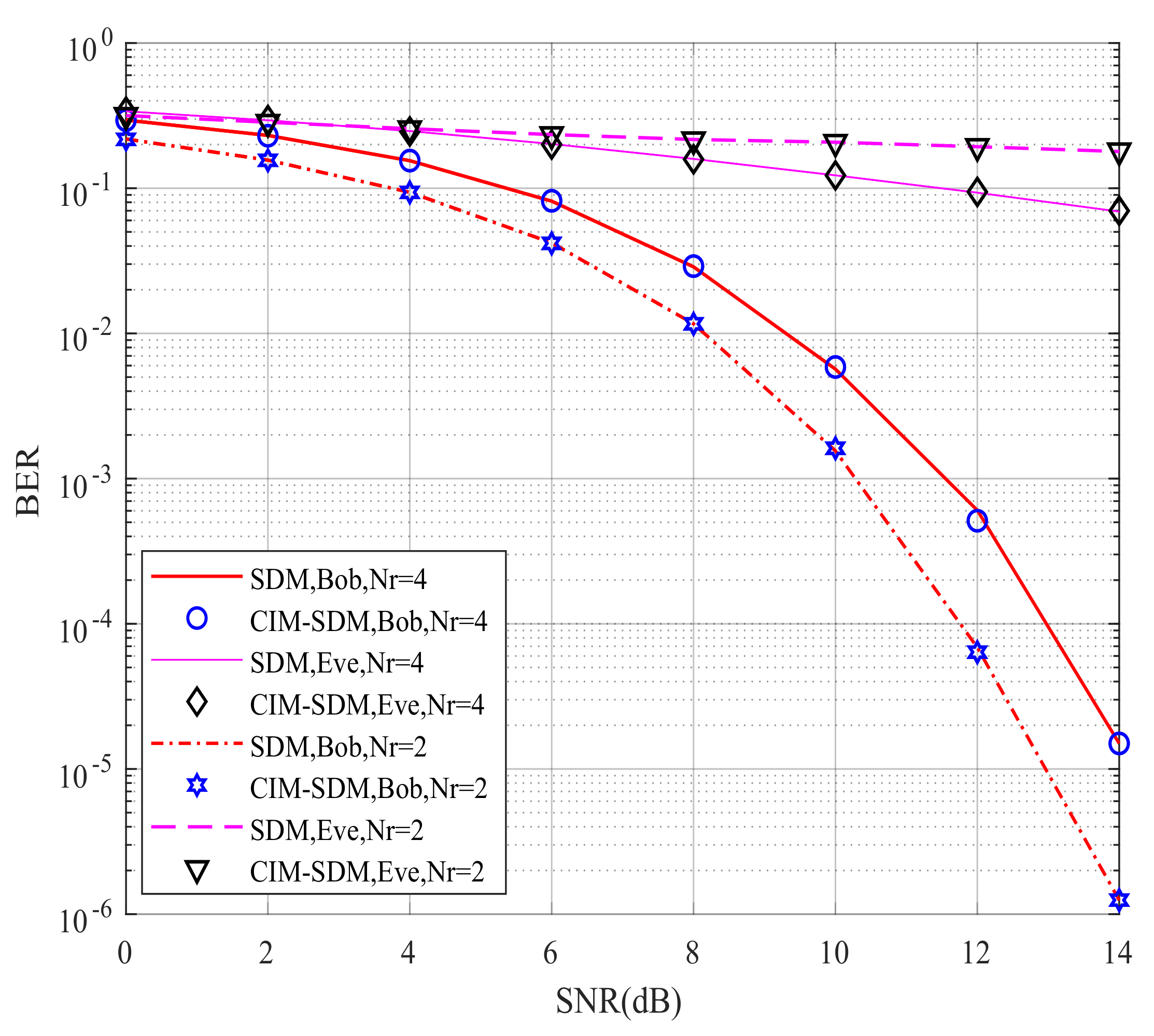
4.2. Simulation Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wu, C.; Xiao, Y.; Yang, P. Covert Information Embedded Spatial Modulation. IEEE Commun. Lett. 2020, 24, 2426–2430. [Google Scholar] [CrossRef]
- Corre, Y.; Gougeon, G.; Doré, J.B.; Bicaïs, S.; Miscopein, B.; Faussurier, E.; Saad, M.; Palicot, J.; Bader, F. Sub-THz Spectrum as Enabler for 6G Wireless Communications up to 1 Tbit/s. In Proceedings of the 6GWireless Summit, Levi, Finland, 24–26 March 2019. [Google Scholar]
- Chen, X.; Ng, D.W.K.; Yu, W.; Larsson, E.G.; Al-Dhahir, N.; Schober, R. Massive Access for 5G and Beyond. IEEE J. Sel. Areas Commun. 2021, 39, 615–637. [Google Scholar] [CrossRef]
- Ma, Z.; Xiao, M.; Xiao, Y.; Pang, Z.; Poor, H.V.; Vucetic, B. High-Reliability and Low-Latency Wireless Communication for Internet of Things: Challenges, Fundamentals, and Enabling Technologies. IEEE Internet Things J. 2019, 6, 7946–7970. [Google Scholar] [CrossRef]
- Wu, C.; Wu, M.; Gao, Y.; You, X. Dynamic relay access for D2D-aided low-latency and high-reliability communications. Sci. China Inf. Sci. 2021, 64, 1–14. [Google Scholar] [CrossRef]
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.K.; Gao, X. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef] [Green Version]
- Li, M.; Kundu, S.; Pados, D.; Batalama, S. Waveform Design for Secure SISO Transmissions and Multicasting. IEEE J. Sel. Areas Commun. 2013, 31, 1864–1874. [Google Scholar] [CrossRef]
- Yang, Y.; Guizani, M. Mapping-Varied Spatial Modulation for Physical Layer Security: Transmission Strategy and Secrecy Rate. IEEE J. Sel. Areas Commun. 2018, 36, 877–889. [Google Scholar] [CrossRef] [Green Version]
- Niu, H.; Lei, X.; Xiao, Y.; Liu, D.; Li, Y.; Zhang, H. Power Minimization in Artificial Noise Aided Generalized Spatial Modulation. IEEE Commun. Lett. 2020, 24, 961–965. [Google Scholar] [CrossRef]
- Daly, M.P.; Bernhard, J.T. Directional Modulation Technique for Phased Arrays. IEEE Trans. Antennas Propag. 2009, 57, 2633–2640. [Google Scholar] [CrossRef]
- Ding, Y.; Fusco, V.F. A Vector Approach for the Analysis and Synthesis of Directional Modulation Transmitters. IEEE Trans. Antennas Propag. 2014, 62, 361–370. [Google Scholar] [CrossRef]
- Ding, Y.; Fusco, V. A review of directional modulation technology. Int. J. Microw. Wirel. Technol. 2016, 8, 981–993. [Google Scholar] [CrossRef] [Green Version]
- Ding, Y.; Fusco, V.; Zhang, J.; Wang, W.Q. Time-Modulated OFDM Directional Modulation Transmitters. IEEE Trans. Veh. Technol. 2019, 68, 8249–8253. [Google Scholar] [CrossRef]
- Zhang, Q.; Yang, Z.; Wang, W.; Ren, J.; Huang, W.; Zhang, N. A Dual-polarized Antennas Based Directional Modulation Scheme. In Proceedings of the 2019 26th International Conference on Telecommunications (ICT), Hanoi, Vietnam, 8–10 April 2019; pp. 468–473. [Google Scholar]
- Ding, Y.; Fusco, V. A Synthesis-Free Directional Modulation Transmitter Using Retrodirective Array. IEEE J. Sel. Top. Signal Process. 2017, 11, 428–441. [Google Scholar] [CrossRef]
- Shu, F.; Wu, X.; Hu, J.; Li, J.; Chen, R.; Wang, J. Secure and Precise Wireless Transmission for Random-Subcarrier-Selection-Based Directional Modulation Transmit Antenna Array. IEEE J. Sel. Areas Commun. 2018, 36, 890–904. [Google Scholar] [CrossRef]
- Qiu, B.; Tao, M.; Wang, L.; Xie, J.; Wang, Y. Multi-Beam Directional Modulation Synthesis Scheme Based on Frequency Diverse Array. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2593–2606. [Google Scholar] [CrossRef]
- Cheng, Q.; Zhu, J.; Xie, T.; Luo, J.; Xu, Z. Time-Invariant Angle-Range Dependent Directional Modulation Based on Time-Modulated Frequency Diverse Arrays. IEEE Access 2017, 5, 26279–26290. [Google Scholar] [CrossRef]
- Mesleh, R.Y.; Haas, H.; Sinanovic, S.; Ahn, C.W.; Yun, S. Spatial Modulation. IEEE Trans. Veh. Technol. 2008, 57, 2228–2241. [Google Scholar] [CrossRef]
- Di Renzo, M.; Haas, H.; Ghrayeb, A.; Sugiura, S.; Hanzo, L. Spatial Modulation for Generalized MIMO: Challenges, Opportunities, and Implementation. Proc. IEEE 2014, 102, 56–103. [Google Scholar] [CrossRef]
- Yang, P.; Di Renzo, M.; Xiao, Y.; Li, S.; Hanzo, L. Design Guidelines for Spatial Modulation. IEEE Commun. Surv. Tutor. 2015, 17, 6–26. [Google Scholar] [CrossRef] [Green Version]
- Tang, Q.; Xiao, Y.; Yang, P.; Yu, Q.; Li, S. A New Low-Complexity Near-ML Detection Algorithm for Spatial Modulation. IEEE Wirel. Commun. Lett. 2013, 2, 90–93. [Google Scholar] [CrossRef]
- Zhang, H.; Xiao, Y.; Xiao, Y.; Xiang, W. Impact of Imperfect Angle Estimation on Spatial and Directional Modulation. IEEE Access 2020, 8, 7081–7092. [Google Scholar] [CrossRef]
- Basar, E.; Wen, M.; Mesleh, R.; Di Renzo, M.; Xiao, Y.; Haas, H. Index Modulation Techniques for Next-Generation Wireless Networks. IEEE Access 2017, 5, 16693–16746. [Google Scholar] [CrossRef]
- Xiao, Y.; Tang, W.; Xiao, Y.; Zhang, H.; Wu, G.; Xiang, W. Directional Modulation with Cooperative Receivers. IEEE Access 2018, 6, 34992–35000. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, M. Secrecy Enhancement for Media-Based Modulation via Probabilistic Optimization. IEEE Commun. Lett. 2019, 23, 1149–1152. [Google Scholar] [CrossRef]
- Gao, Z.; Bai, S.; Liao, X.; Leung, V.C.M. Secure Quadrature Channel Modulation. IEEE Trans. Veh. Technol. 2019, 68, 9974–9987. [Google Scholar] [CrossRef]
- Wu, F.; Yang, L.L.; Wang, W.; Kong, Z. Secret Precoding-Aided Spatial Modulation. IEEE Commun. Lett. 2015, 19, 1544–1547. [Google Scholar] [CrossRef]
- Xiao, Y.; Wang, S.; Dan, L.; Lei, X.; Yang, P.; Xiang, W. OFDM with Interleaved Subcarrier-Index Modulation. IEEE Commun. Lett. 2014, 18, 1447–1450. [Google Scholar] [CrossRef]
- Datta, T.; Eshwaraiah, H.S.; Chockalingam, A. Generalized Space-and-Frequency Index Modulation. IEEE Trans. Veh. Technol. 2016, 65, 4911–4924. [Google Scholar] [CrossRef] [Green Version]
- Simon, M.K.; Alouini, M.S. Digital Communication over Fading Channels, 2nd ed.; Wiley: Newark, NJ, USA, 2005. [Google Scholar]
- Mailloux, R. Phased Array Antenna Handbook, 3rd ed.; Artech House Boston: Norwood, MA, USA, 2017. [Google Scholar]
- Trees, H.L.V. Optimum Array Processing: Part IV of Detection, Estimation, and Modulation Theory; Wiley: New York, NY, USA, 2003. [Google Scholar]
- Hansen, R. Phased Array Antennas; Wiley Series in Microwave and Optical Engineering; Wiley: New York, NY, USA, 2009. [Google Scholar]
- Wang, L.; Wu, H.; Stüber, G.L. Cooperative Jamming-Aided Secrecy Enhancement in P2P Communications with Social Interaction Constraints. IEEE Trans. Veh. Technol. 2017, 66, 1144–1158. [Google Scholar] [CrossRef]
- Wang, W.; Teh, K.C.; Li, K.H. Enhanced Physical Layer Security in D2D Spectrum Sharing Networks. IEEE Wirel. Commun. Lett. 2017, 6, 106–109. [Google Scholar] [CrossRef]
- Cepheli, O.; Karabulut Kurt, G. Physical layer security in cognitive radio networks: A beamforming approach. In Proceedings of the 2013 First International Black Sea Conference on Communications and Networking (BlackSeaCom), Batumi, Georgia, 3–5 July 2013; pp. 233–237. [Google Scholar]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A Comprehensive Survey on Cooperative Relaying and Jamming Strategies for Physical Layer Security. IEEE Commun. Surv. Tutor. 2019, 21, 2734–2771. [Google Scholar] [CrossRef] [Green Version]
- Wang, T.; Jing, W.; Song, W. Hybrid prefix OFDM with spatial modulation toward terahertz broadband transmission. Sci. China Inf. Sci. 2020, 63, 1–3. [Google Scholar] [CrossRef]
- You, Q.; Xiao, Y. Spatial and directional modulation with scrambling. Phys. Commun. 2019, 35, 100694. [Google Scholar] [CrossRef]





| Figure | Scheme | M | |||||
|---|---|---|---|---|---|---|---|
| 1 | CIM-SDM | 8 | 2 | 4 | {15°, 85°} | 2 | {20°, 60°} |
| 2 | CIM-SDM | 8 | 4 | 4 | {15°, 85°, 120°, 210°} | 4 | {20°, 60°, 110°, 230°} |
| 3 | CIM-SDM | 8 | 2 | 4 | {15°, 85°} | 2 | {20°, 60°} |
| SDM | 8 | 2 | 4 | {15°, 85°} | 2 | {20°, 60°} | |
| 4 | CIM-SDM | 8 | 4 | 4 | {15°, 85°, 120°, 210°} | 4 | {20°, 60°, 110°, 230°} |
| SDM | 8 | 4 | 4 | {15°, 85°, 120°, 210°} | 4 | {20°, 60°, 110°, 230°} | |
| 5, 6 | CIM-SDM | 10 | 2,4 | 4 | {15°, 85°}, {15°, 85°, 120°, 210°} | 2,4 | {20°, 60°}, {20°, 60°, 110°, 230°} |
| SDM | 10 | 2,4 | 4 | {15°, 85°}, {15°, 85°, 120°, 210°} | 2,4 | {20°, 60°}, {20°, 60°, 110°, 230°} |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, J.; Chen, H.; Wang, Z.; Shi, X.; Ji, Z.; Li, X. Covert Information Mapped Spatial and Directional Modulation toward Secure Wireless Transmission. Sensors 2021, 21, 7646. https://doi.org/10.3390/s21227646
Tian J, Chen H, Wang Z, Shi X, Ji Z, Li X. Covert Information Mapped Spatial and Directional Modulation toward Secure Wireless Transmission. Sensors. 2021; 21(22):7646. https://doi.org/10.3390/s21227646
Chicago/Turabian StyleTian, Jie, Hao Chen, Zhigang Wang, Xianhua Shi, Zhengyu Ji, and Xianglu Li. 2021. "Covert Information Mapped Spatial and Directional Modulation toward Secure Wireless Transmission" Sensors 21, no. 22: 7646. https://doi.org/10.3390/s21227646
APA StyleTian, J., Chen, H., Wang, Z., Shi, X., Ji, Z., & Li, X. (2021). Covert Information Mapped Spatial and Directional Modulation toward Secure Wireless Transmission. Sensors, 21(22), 7646. https://doi.org/10.3390/s21227646







