An Indexing Method of Continuous Spatiotemporal Queries for Stream Data Processing Rules of Detected Target Objects
Abstract
:1. Introduction
2. Spatiotemporal Continuous Query Rule Processing
2.1. Stream Processing Rules of Target Objects
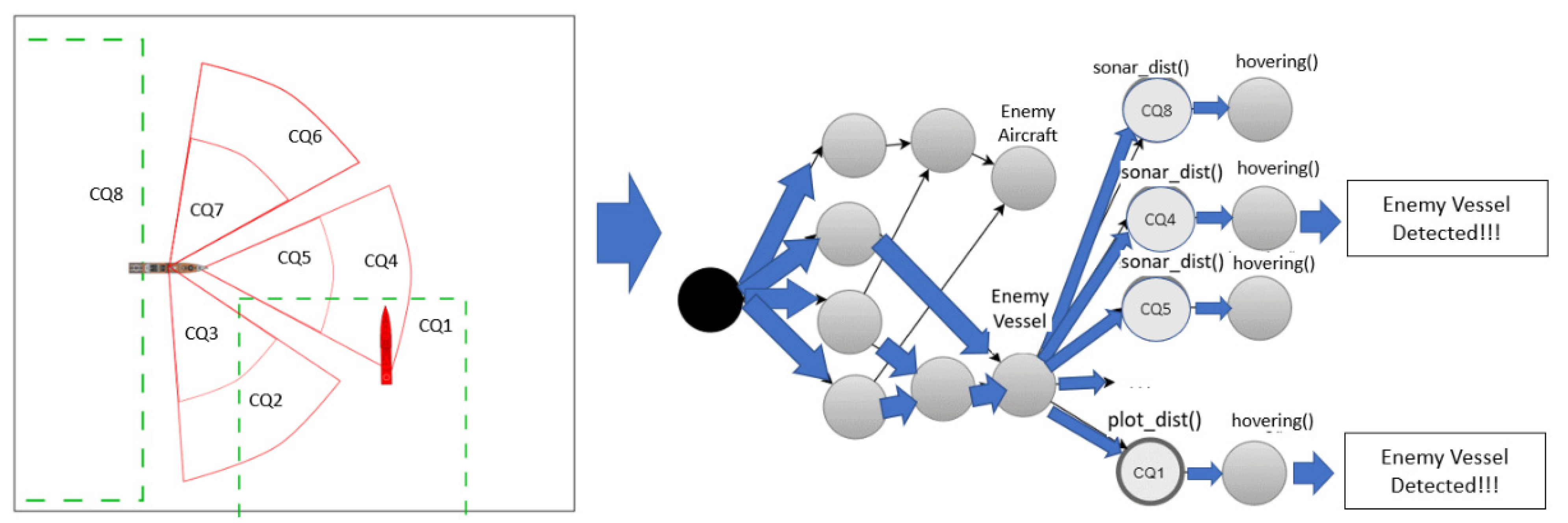
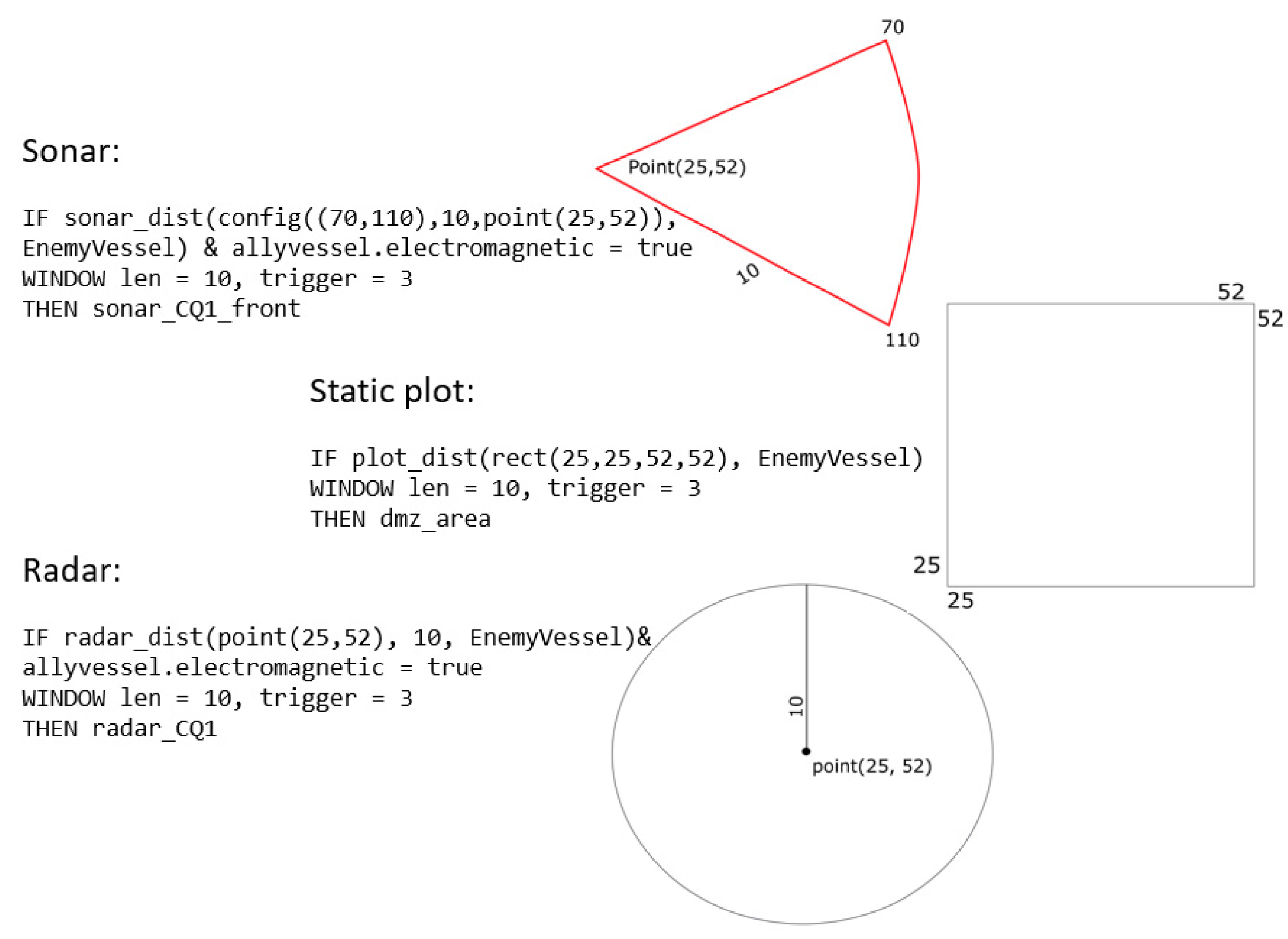
2.2. Spatiotemporal Continuous Query Rules
3. Rete Node Indexing and Stabbing Algorithms
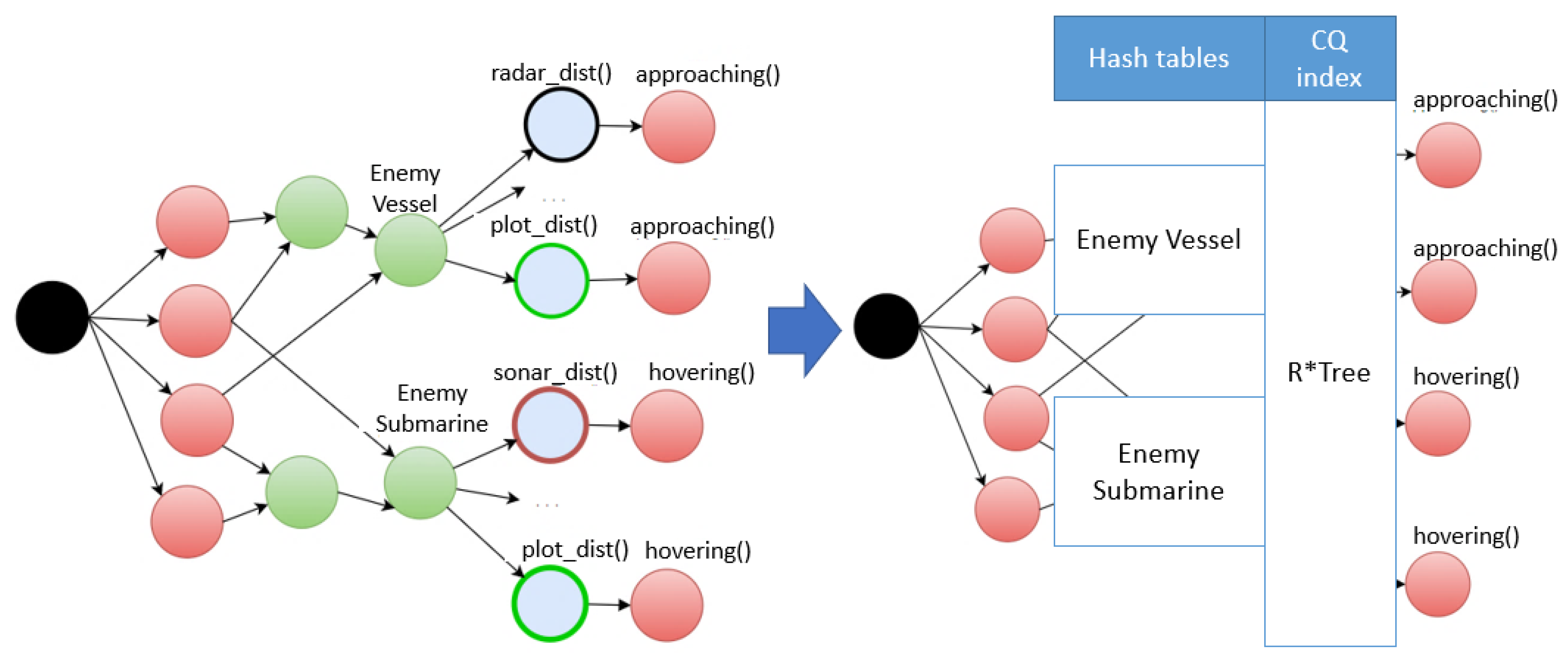
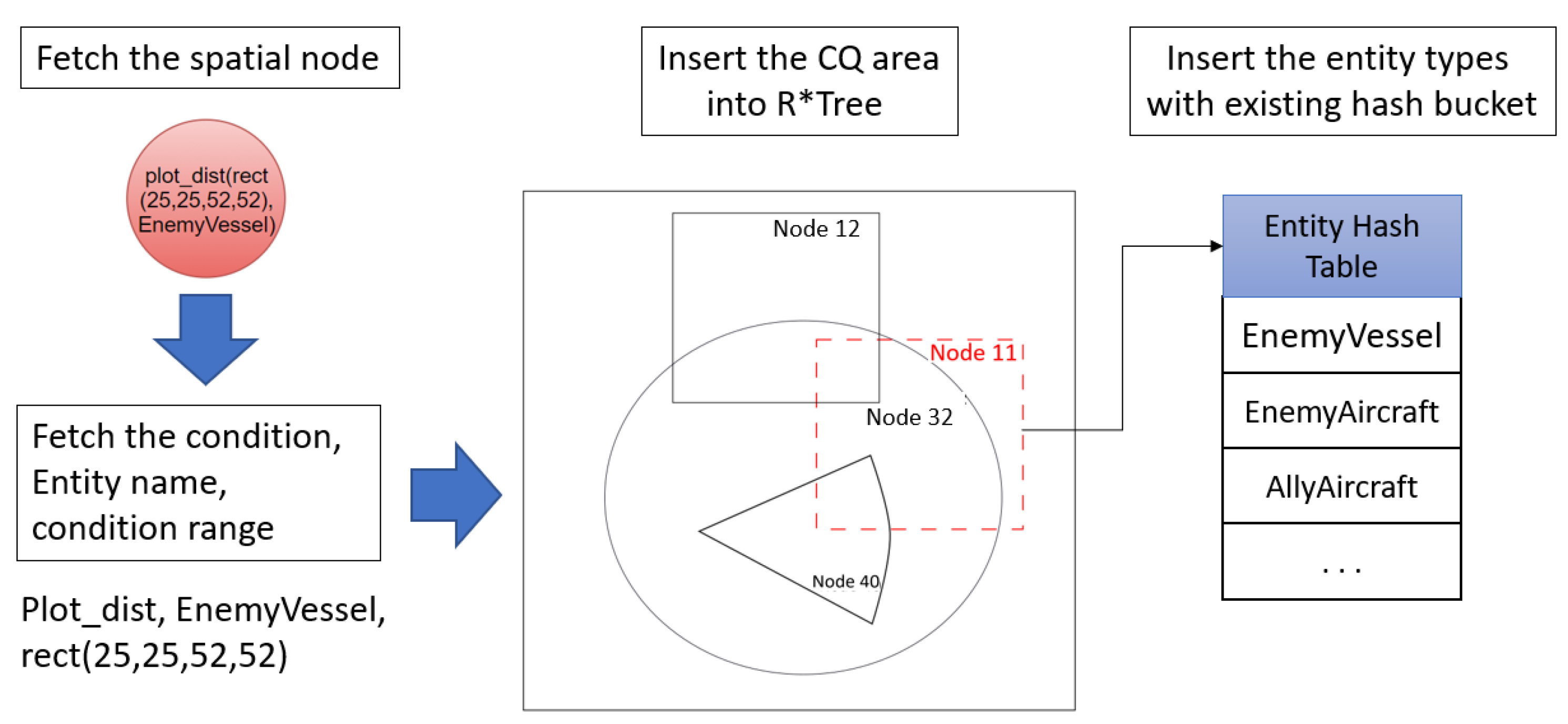
3.1. Hashing Index of Rete Node
| Algorithm 1 Rule Insertion (r) |
| 1 Input: vector<string> Input //string of rule input; 2 Output: RETE net and updated Node Indexing; /* Based on node identification, build each node*/ 3 expVec = new vector<pair<string,string>> //node type and rule input; 4 While (Input != end) { 5 extracted=DecomposeRule(Input[i]); 6 expVec.push(extracted); 7 } 8 nodeVec = new vector<Node*> //created node; 9 scalarVec = new vector<Node*> //created CQ node; 10 spatialVec = new vector<Node*> //created Spatial node; 11 While (expVec != NULL && nodeVec.size()—1){ 12 If (expVec.first == “Alpha”) { 13 tempAlphaNode = new AlphaNode(expVec.second); 14 nodeVec.push(tempAlphaNode); 15 scalarVec.push(tempAlphaNode); 16 expVec.pop(); 17 } 18 Else { /* check whether the previous node is an existing node */ 19 If (expVec.first == “spatial”) { 20 tempBetaNode = new BetaNode(expVec.second); 21 nodeVec.push(tempBetaNode); 22 spatialVec.push(tempBetaNode); 23 expVec.pop() 24 } 25 Else { 26 If (isExist(expVec.second)) { 27 nodeVec.push(findNode(expVec.second)); 28 } 29 Else { 30 tempBetaNode = new BetaNode(expVec.second); 31 nodeVec.push(tempBetaNode); 32 } 33 expVec.pop(); 34 } 35 } 36 tempBetaNode = newBetaNode(nodeVec.top(), nodeVec.top()-1); 37 connectNode(nodeVec.top, nodeVec.top()-1, tempBetaNode); 38 nodeVec.pop(); 39 nodeVec.pop(); 40 nodeVec.push(tempBetaNode); 41 } /*Spatial Node Index Construction */ 42 While (spatialVec.size() > 0) { 43 pointVec = Utilities::decomposeNode(spatialVec.top); /*Get the entity name from the CQ node */ 44 observedEntityName = getEntityName(spatialVec.top); /*from the existing node indexing tree, insert the CQ area */ 45 *(spatialIndex[observedEntityName]).insert(pointVec); /*remove the node from the vector */ 46 spatialVec.pop(); 47 } |
3.2. Stabbing Algorithm for Continuous Query Events
| Algorithm 2 Event Stabbing (e) |
| 1 Input: Event //Tested event with its attributes; 2 Output: List<String> //Result of Event evaluation; /* Copy the input into Working Memory queue */ 3 mainWM.pushEvent(Event); /* stab the event */ 4 If (IsNotEmpty(mainWM)) { /* Define the entity hash */ 5 List<Node*> stabbed; 6 While (ScalarNode != NULL) { 7 If (ScalarNode[i].test(Event)) { 8 stabbed.push(ScalarNode-i); 9 } 10 } 11 EntityHash = EntityNodeList[stabbed]; 12 EntityNode.pushEvent(Event); /* spatial node stabbing */ 13 *SpatialTree = SpatialIndex[EntityHash]; 14 *root = *SpatialTree; 15 EventLocation<int, int> = {Event.Latitude, Event.Longitude}; 16 List<Node*> stabbedCQ; 17 While (*root != NULL) { 18 If (IsALeaf(*root)) { 19 stabbedCQ.push(*root); 20 *root = NULL; 21 } 22 Else { 23 For (auto *leaf in *root.leaf) { 24 If (Intersects(EventLocation, *leaf) == true) { 25 *root = *leaf; 26 break; 27 } 28 } 29 } /* collect the result in a list of string */ 30 List<string> res; 31 For (auto s in stabbedCQ) { 32 s.push(Event); 33 res.Append(Node.evaluate()); 34 } 35 return res; 36 } 37 } 38 Else { 39 continue; 40 } |
4. Performance Evaluation
4.1. Hashing Index of Rete Node
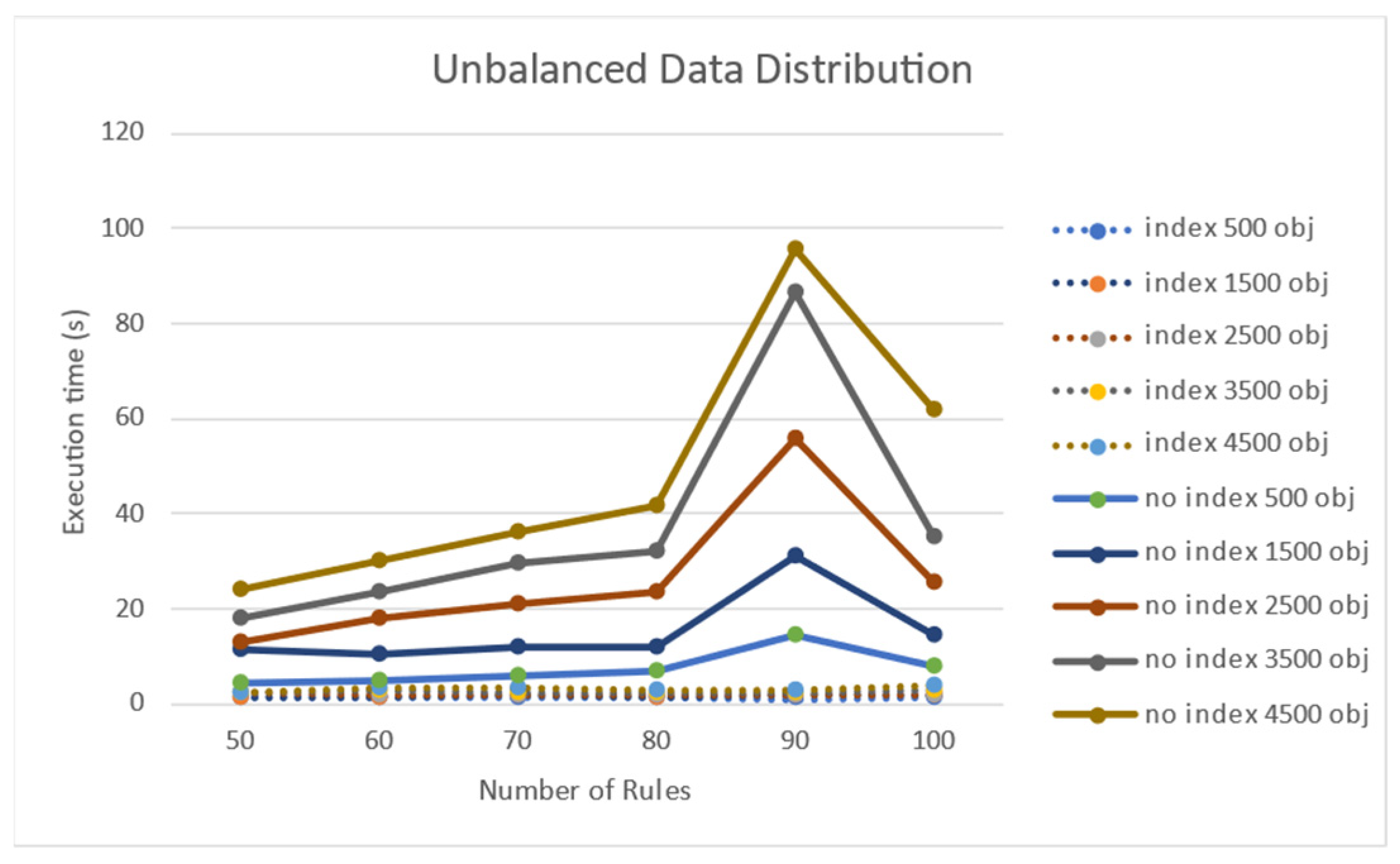
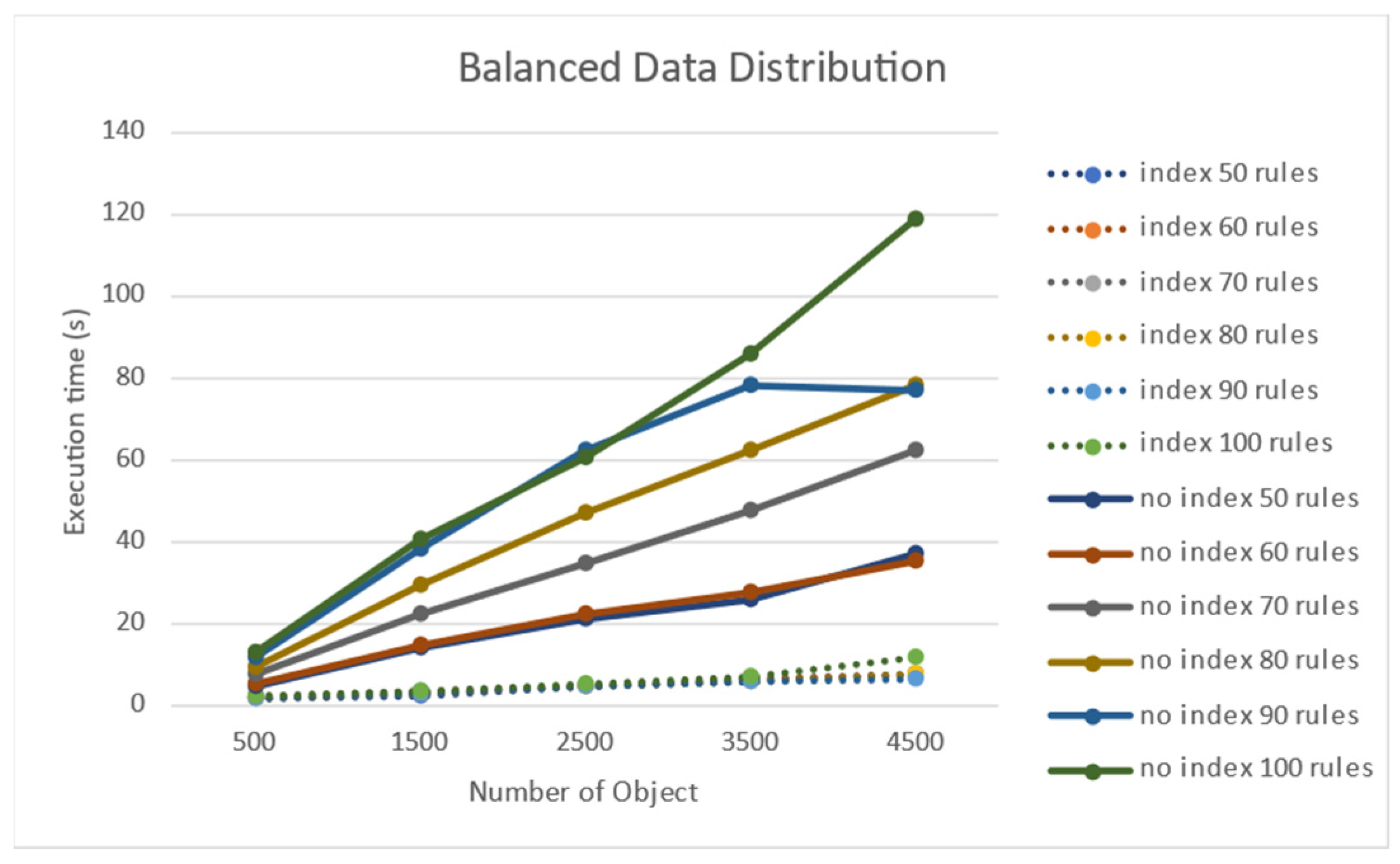
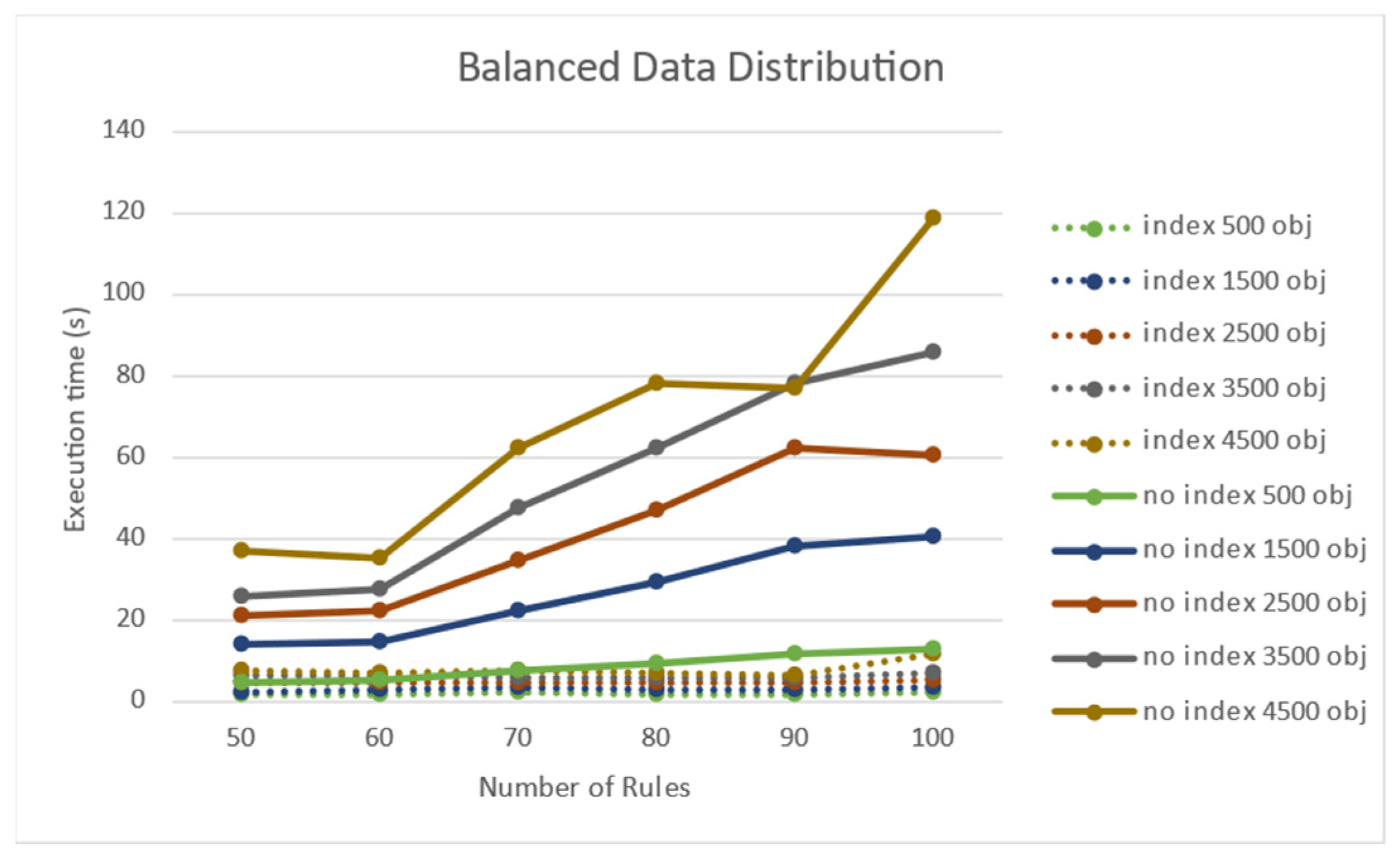
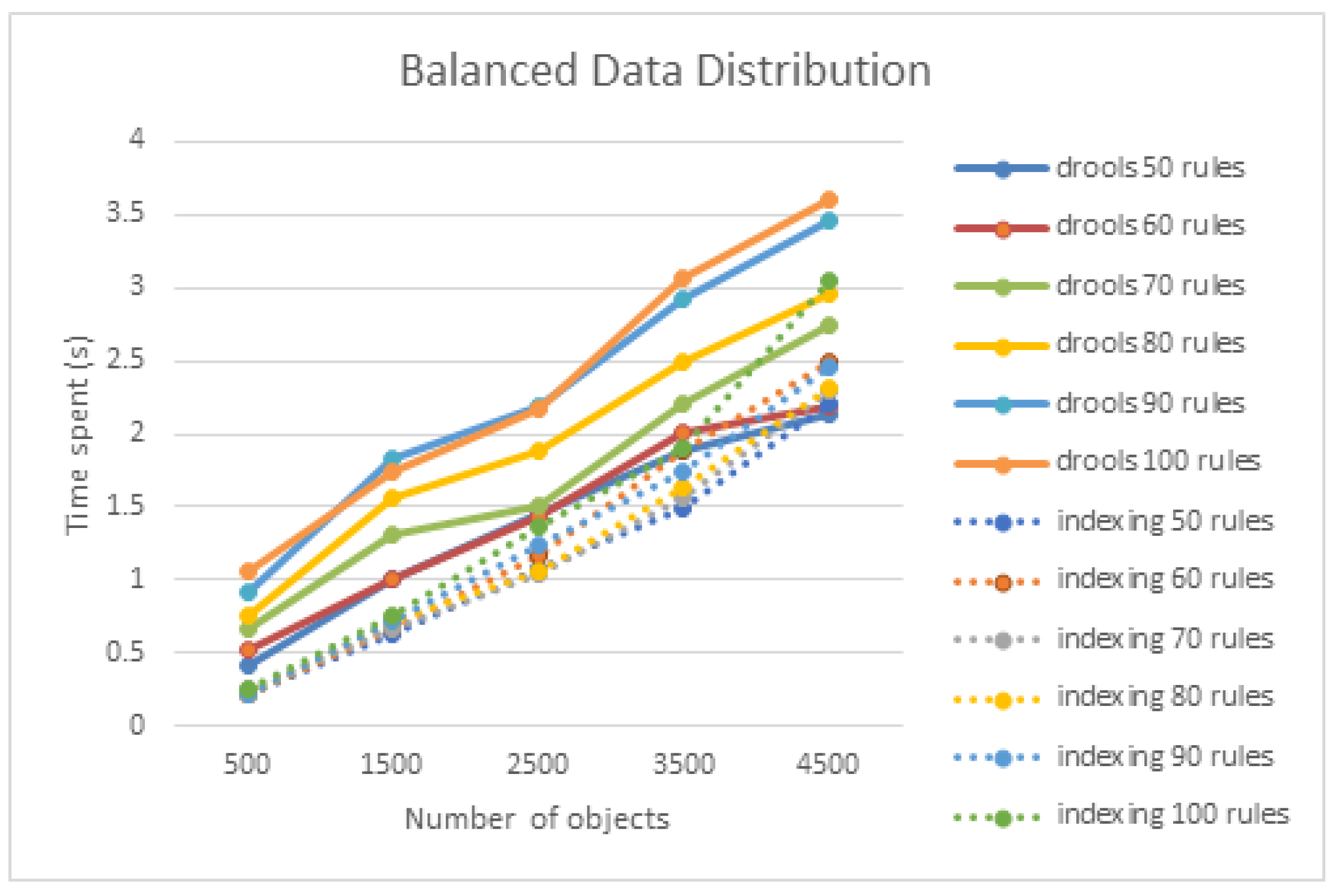
4.2. Performance Testing on the Number of Rules and the Number of Target Objects
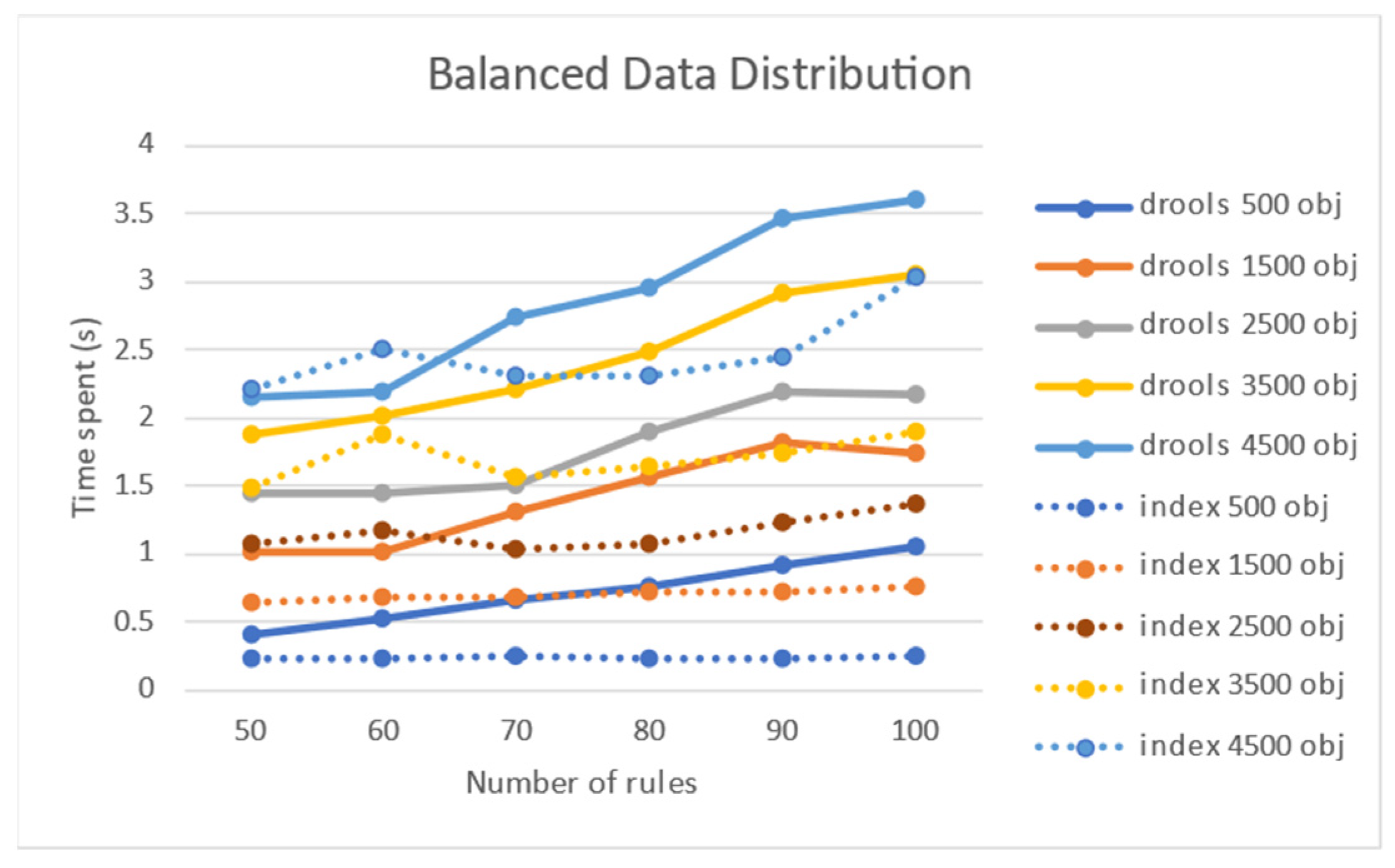
4.3. Performance Comparison Test with Drool
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Merilinna, J. A mechanism to enable spatial reasoning in jboss drools. In Proceedings of the 2014 International Conference on Industrial Automation, Information and Communications Technology, Bali, Indonesia, 28–30 August 2014; pp. 135–140. [Google Scholar]
- Beckmann, N.; Kriegel, H.P.; Schneider, R.; Seeger, B. The R*-tree: An efficient and robust access method for points and rectangles. In Proceedings of the 1990 ACM SIGMOD International Conference on Management of Data (SIGMOD ‘90), Atlantic City, NJ, USA, 23–25 May 1990; Association for Computing Machinery: New York, NY, USA, 1990; pp. 322–331. [Google Scholar]
- Dong, T.; Shi, J.; Fan, J.; Zhang, L. An Improved Rete algorithm Based on Double Hash Filter and Node Indexing for Distributed Rule Engine. IEICE Trans. Inf. Syst. 2013, 96, 2635–2644. [Google Scholar] [CrossRef] [Green Version]
- Ship Self Defense System. Available online: https://man.fas.org/dod-101/sys/ship/weaps/mk-1.htm (accessed on 9 October 2021).
- Roy, J. Rule-based expert system for maritime anomaly detection. In Proceedings of the Sensors, and Command, Control, Communications, and Intelligence (C3I) Technologies for Homeland Security and Homeland Defense IX, Orlando, FL, USA, 5 May 2010; Volume 7666, p. 76662N. [Google Scholar]
- Friedlander, G.D. World War II: Electronics and the US Navy Radar, sonar, loran, and infrared techniques. IEEE Spectr. 1967, 4, 56–70. [Google Scholar] [CrossRef]
- Data Distribution Service. Available online: https://www.omg.org/omg-dds-portal (accessed on 9 October 2021).
- Oracle Continuous Query Language. Available online: https://docs.oracle.com/middleware/12212/osa/cql-reference/toc.htm (accessed on 9 October 2021).
- Chen, J.; DeWitt, D.J.; Tian, F.; Wang, Y. NiagaraCQ: A scalable continuous query system for Internet databases. In Proceedings of the 2000 ACM SIGMOD International Conference on Management of Data (SIGMOD ‘00), Dallas, TX, USA, 16–18 May 2000; Association for Computing Machinery: New York, NY, USA, 2000; pp. 379–390. [Google Scholar]
- Lim, H.-S.; Lee, J.-G.; Lee, M.-J.; Song, I.-Y. Continuous query processing in data streams using duality of data and queries. In Proceedings of the 2006 ACM SIGMOD International Conference on Management of Data (SIGMOD ‘06), Chicago, IL, USA, 27–29 June 2006; Association for Computing Machinery: New York, NY, USA, 2006; pp. 313–324. [Google Scholar]
- Prabhakar, S.; Xia, Y.; Kalashnikov, D.V.; Aref, W.G.; Hambrusch, S.E. Query indexing and velocity constrained indexing: Scalable techniques for continuous queries on moving objects. In IEEE Trans. Comput. 2002, 51, 1124–1140. [Google Scholar] [CrossRef]
- Gyllstrom, D.; Wu, E.; Chae, H.J.; Diao, Y.; Stahlberg, P.; Anderson, G. SASE: Complex event processing over streams. arXiv 2006, arXiv:cs/0612128. [Google Scholar]
- Wu, E.; Diao, Y.; Rizvi, S. High-performance complex event processing over streams. In Proceedings of the 2006 ACM SIGMOD International Conference on Management of Data (SIGMOD ‘06), Chicago, IL, USA, 27–29 June 2006; Association for Computing Machinery: New York, NY, USA, 2006; pp. 407–418. [Google Scholar]
- Mozafari, B.; Zeng, K.; Zaniolo, C. High-performance complex event processing over XML streams. In Proceedings of the 2012 ACM SIGMOD International Conference on Management of Data (SIGMOD ‘12), Scottsdale, AZ, USA, 20–24 May 2012; Association for Computing Machinery: New York, NY, USA, 2012; pp. 253–264. [Google Scholar]
- Schultz-Møller, N.P.; Migliavacca, M.; Pietzuch, P. Distributed complex event processing with query rewriting. In Proceedings of the Third ACM International Conference on Distributed Event-Based Systems (DEBS ‘09), Nashville, TN, USA, 6–9 July 2009; Association for Computing Machinery: New York, NY, USA, 2009. Article 4. pp. 1–12. [Google Scholar]
- Akdere, M.; Çetintemel, U.; Tatbul, N. Plan-based complex event detection across distributed sources. In Proceedings of the VLDB ‘08, Auckland, New Zealand, 24–30 August 2008; pp. 66–77. [Google Scholar]
- Xiao, F. CaFtR: A Fuzzy Complex Event Processing Method. Int. J. Fuzzy Syst. 2021, 1–14. [Google Scholar] [CrossRef]
- Ray, C.; Grancher, A.; Thibaud, R.; Etienne, L. Spatio-Temporal Rule-based Analysis of Maritime Traffic. In Proceedings of the Third Conference on Ocean & Coastal Observation: Sensors and Observing Systems, Numerical Models and Information (OCOSS), Nice, France, 28–31 October 2013. [Google Scholar]
- Drools Complex Event Processing. Available online: https://docs.jboss.org/drools/release/6.2.0.CR3/drools-docs/html/DroolsComplexEventProcessingChapter.html (accessed on 11 November 2021).
- Liu, D.; Gu, T.; Xue, J.P. Rule Engine based on improvement Rete algorithm. In Proceedings of the 2010 International Conference on Apperceiving Computing and Intelligence Analysis Proceeding, Chengdu, China, 17–19 December 2010; pp. 346–349. [Google Scholar]
- Yu, M.; Bambacus, M.; Cervone, G.; Clarke, K.; Duffy, D.; Huang, Q.; Li, J.; Li, W.; Li, Z.; Liu, Q.; et al. Spatiotemporal event detection: A review. Int. J. Digital Earth 2020, 13, 1339–1365. [Google Scholar] [CrossRef] [Green Version]
- Oracle Complex Event Processing Visualizer. Available online: https://docs.oracle.com/cd/E28280_01/doc.1111/e14302.pdf (accessed on 11 November 2021).
- Liang, Y.; Lee, J.; Hong, B.; Kim, W. Rule-based Complex Event Processing on Tactical Moving Objects. In Proceedings of the 2018 IEEE 4th International Conference on Computer and Communications (ICCC), Chengdu, China, 7–10 December 2018. [Google Scholar]
- Liang, Y.; Hong, B.; Lee, J.; Kim, W. A Framework of Spatio-Temporal Continuous Query Rule-based Complex Event Processing for RealTime Risk Analysis and Decision Making. Database Res. KIISE 2020, 36, 74–92. [Google Scholar]
- Bhargavi, R.; Pathak, R.; Vaidehi, V. Dynamic complex event processing—adaptive rule engine. In Proceedings of the 2013 International Conference on Recent Trends in Information Technology (ICRTIT), Chennai, India, 25–27 July 2013; pp. 189–194. [Google Scholar]
- Buchmann, A.; Koldehofe, B. Complex Event Processing. It-Inf. Technol. 2009, 51, 241. [Google Scholar] [CrossRef]
- Jun, C.; Chi, C. Design of complex event-processing IDS in internet of things. In Proceedings of the 2014 Sixth International Conference on Measuring Technology and Mechatronics Automation, Zhangjiajie, China, 10–11 January 2014; pp. 226–229. [Google Scholar]
- Complex Event Processing. Available online: https://en.wikipedia.org/wiki/Complex_event_processing (accessed on 11 November 2021).
- Rahman, M.H.; Hong, B.; Kim, W. Hash indexing on RETE nodes for fast executing of spatiotemporal continuous query processing rules. Database Res. KIISE 2021, 37, 21–36. [Google Scholar]
- Teymourian, K.; Rohde, M.; Paschke, A. Knowledge-based processing of complex stock market events. In Proceedings of the 15th International Conference on Extending Database Technology (EDBT ‘12), Berlin, Germany, 27–30 March 2012; Association for Computing Machinery: New York, NY, USA, 2012; pp. 594–597. [Google Scholar]
- Komazec, S.; Cerri, D.; Fensel, D. Sparkwave: Continuous schema-enhanced pattern matching over RDF data streams. In Proceedings of the 6th ACM International Conference on Distributed Event-Based Systems (DEBS ‘12), Hamilton New Zealand, 25–29 June 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 58–68. [Google Scholar]
- Forgy, C.L. Rete: A fast algorithm for the many patterns/many object pattern match. Readings in Artificial Intelligence and Databases. Morgan Kaufmann 1989, 547–559. [Google Scholar] [CrossRef]
- Xiao, F. CEQD: A Complex Mass Function to Predict Interference Effects. IEEE Trans. Cybern. 2021, 1–13. [Google Scholar] [CrossRef]


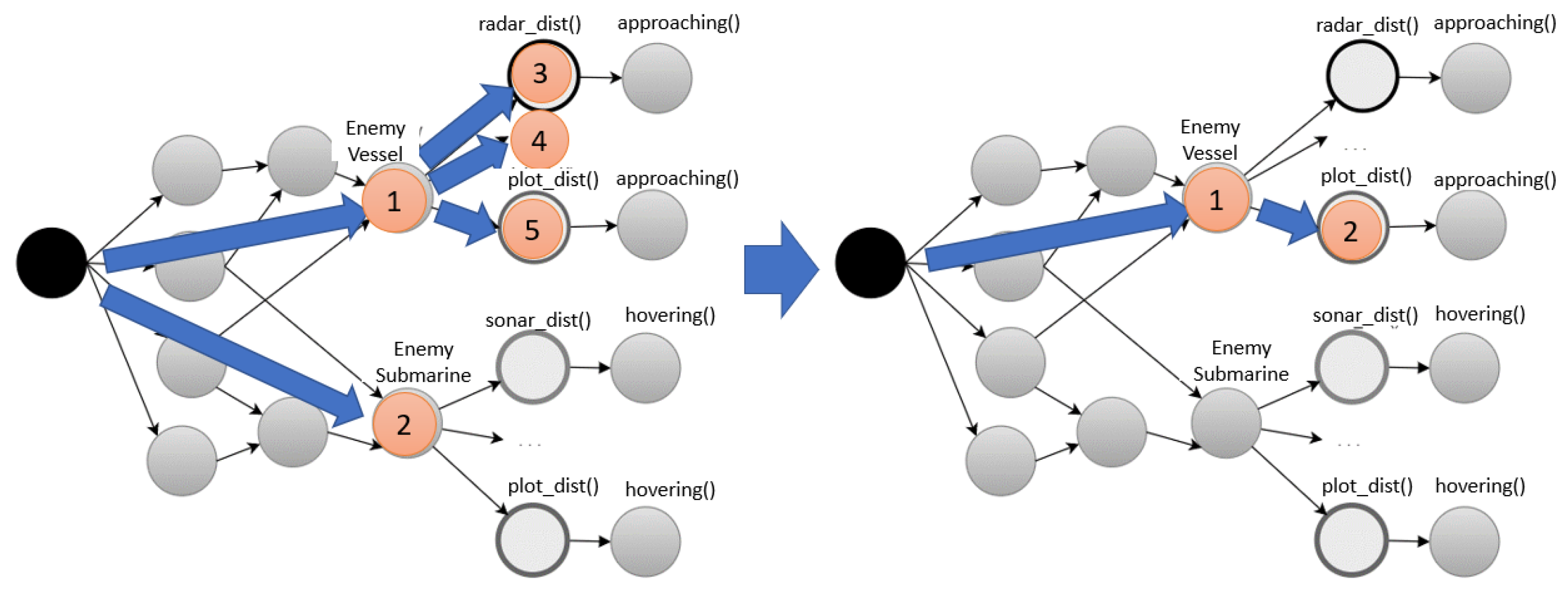


| No. | Attribute | Data Type | Value | Meaning |
|---|---|---|---|---|
| 1 | Event Id | Integer | 1–∞ | Event id |
| 2 | Time | Long Long | 0–∞ | Event time |
| 3 | Speed | Float | −30–200 | Object speed (m/s) |
| 4 | Elevation | Float | 0–10 | Object elevation (10 m) |
| 5 | IFF | Boolean | True, False | Friend or Foe |
| 6 | Latitude | Float | 115–136 | Latitude location |
| 7 | Longitude | Float | 15–46 | Longitude location |
| 8 | Object Type | String | fighter, destroyer, etc. | Object type or mode |
| 9 | Object Id | Integer | ∞ | Object id of current event |
| No. | Rules | Radar | Sonar | Plot Dist |
|---|---|---|---|---|
| 1 | 50 | 34% | 32% | 34% |
| 2 | 60 | 41% | 28% | 30% |
| 3 | 70 | 44% | 27% | 28% |
| 4 | 80 | 43% | 25% | 31% |
| 5 | 90 | 42% | 24% | 33% |
| 6 | 100 | 25% | 25% | 50% |
| No. | Entity Type | Speed (m/s) | Elevation (m) | IFF |
|---|---|---|---|---|
| 1 | Enemy Aircraft | 10–100 | 10–100 | FALSE |
| 2 | Ally Aircraft | 10–100 | 10–100 | TRUE |
| 3 | Enemy Vessel | 3–100 | 0–10 | FALSE |
| 4 | Ally Vessel | 3–100 | 0–10 | TRUE |
| 6 | Enemy Submarine | 0–100 | −10–0 | FALSE |
| 7 | Ally Submarine | 0–100 | −10–0 | TRUE |
| Number of Rule Nodes | Objects | Average Time (ms) | Improvement Rate | |
|---|---|---|---|---|
| Indexed Rete | Original | |||
| 50 | 500 | 220 | 409 | 85% |
| 2500 | 1.071 | 1.448 | 35% | |
| 4500 | 2.143 | 2.211 | 3% | |
| 60 | 500 | 226 | 521 | 130% |
| 2500 | 1.163 | 1.444 | 24% | |
| 4500 | 2.183 | 2.500 | 14% | |
| 70 | 500 | 245 | 662 | 170% |
| 2500 | 1.041 | 1.512 | 45% | |
| 4500 | 2.303 | 2.736 | 18% | |
| 80 | 500 | 222 | 762 | 243% |
| 2500 | 1.061 | 1.893 | 78% | |
| 4500 | 1.631 | 2.958 | 81% | |
| 90 | 500 | 226 | 913 | 303% |
| 2500 | 1.237 | 2.183 | 76% | |
| 4500 | 2.450 | 3.463 | 45% | |
| 100 | 500 | 246 | 1.057 | 329% |
| 2500 | 1356 | 2.169 | 59% | |
| 4500 | 3.042 | 3.599 | 18% | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rahman, M.H.; Hong, B.; Setiawan, H.; Lee, S.; Lim, D.; Kim, W. An Indexing Method of Continuous Spatiotemporal Queries for Stream Data Processing Rules of Detected Target Objects. Sensors 2021, 21, 8013. https://doi.org/10.3390/s21238013
Rahman MH, Hong B, Setiawan H, Lee S, Lim D, Kim W. An Indexing Method of Continuous Spatiotemporal Queries for Stream Data Processing Rules of Detected Target Objects. Sensors. 2021; 21(23):8013. https://doi.org/10.3390/s21238013
Chicago/Turabian StyleRahman, Muhammad Habibur, Bonghee Hong, Hari Setiawan, Sanghyun Lee, Dongjun Lim, and Woochan Kim. 2021. "An Indexing Method of Continuous Spatiotemporal Queries for Stream Data Processing Rules of Detected Target Objects" Sensors 21, no. 23: 8013. https://doi.org/10.3390/s21238013
APA StyleRahman, M. H., Hong, B., Setiawan, H., Lee, S., Lim, D., & Kim, W. (2021). An Indexing Method of Continuous Spatiotemporal Queries for Stream Data Processing Rules of Detected Target Objects. Sensors, 21(23), 8013. https://doi.org/10.3390/s21238013






