SPETS: Secure and Privacy-Preserving Energy Trading System in Microgrid
Abstract
:1. Introduction
Contributions
- It proposes a decentralized energy trading system that can be effectively integrated with HF. The proposed system enables authorized users to trade energy in a secure, reliable, and privacy-preserving manner without a third-party.
- It explores the capability of HF as a management information system to immutably store transactions, ensures secure energy transactions, and protect the participant’s sensitive information, employing channels and private data collections (PDC).
- It proposes a lightweight and efficient discrete-time double auction with an average mechanism to allocate energy and calculates energy price. A market reputation score method is adopted to guarantee reliability and trust.
- It provides theoretical security analysis and quantitative performance analysis to prove the effectiveness of our proposed system and how it resists against several security attacks.
- It provides a benchmark study on the designed HF energy network using the Hyperledger Caliper tool (V0.4.0) to measure transaction latency, throughput, resource consumption, and network utilization.
2. Background and Related Work
2.1. Blockchain-Enabled P2P Energy Trading in MG
2.2. P2P Energy Trading Design Approaches
3. Threat Model and Design Goals of P2P Energy Trading
3.1. Threat Model
3.1.1. Data Breaches
3.1.2. Sensitive Data Leakage
3.1.3. Security and Stability Breaches of Energy Market
3.1.4. Network Security Attacks
3.2. Design Goals
3.2.1. Preserving Privacy
3.2.2. Securing the Energy Market
3.2.3. Ensuring Stability of Energy Trading Market
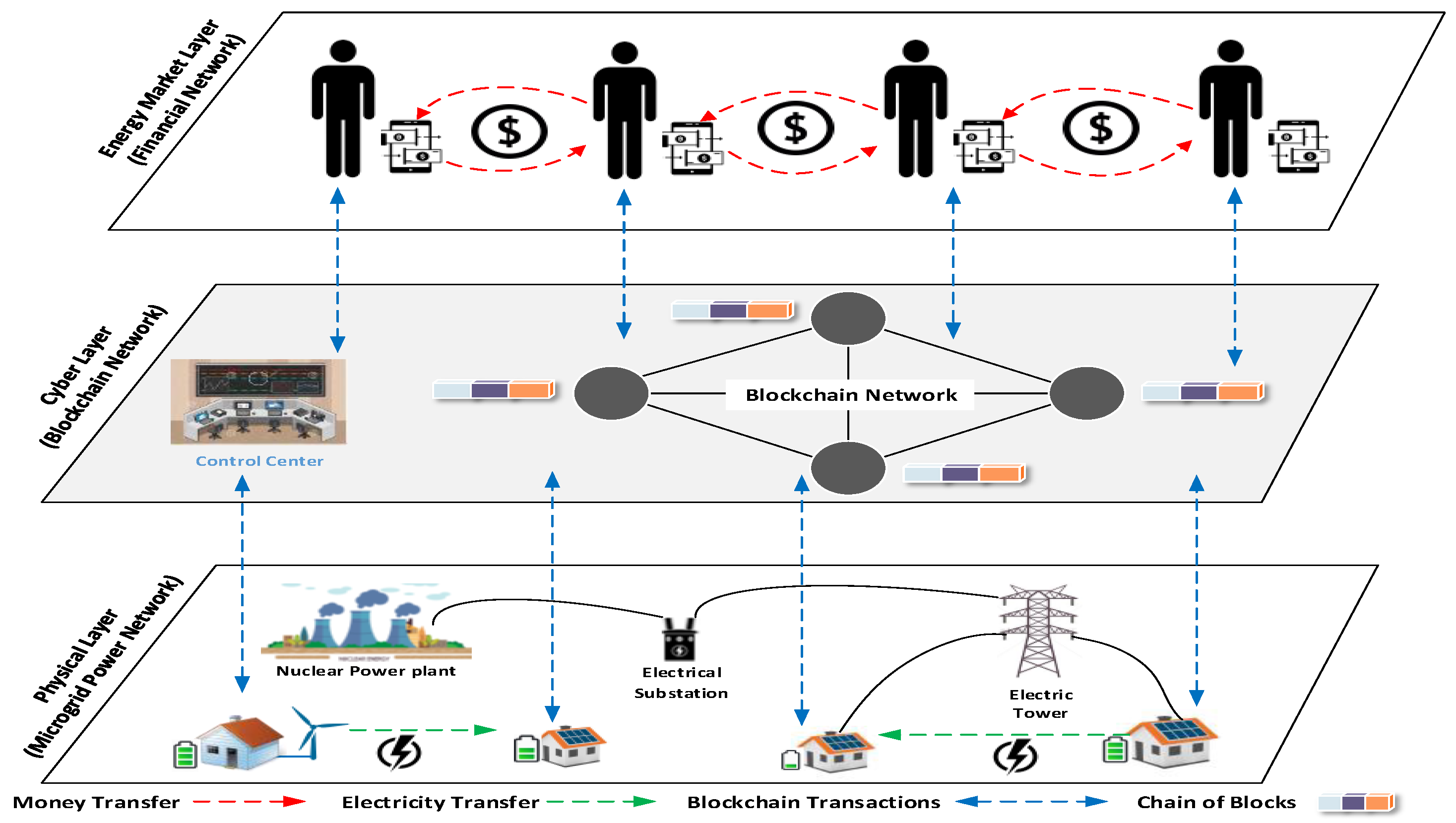
4. The Proposed HF-Enabled P2P Energy Trading System
4.1. Components of the Proposed System
- Microgrid: MG provides the physical communication between smart energy peers. MG with integrated control is responsible for providing utilities such as energy generation, energy storage, bi-directional energy transfer, and energy trading management.
- Smart Energy Sources: It is supposed that each participant has one or more renewable generation units such as PV panels or small wind turbine. In addition, participants must have SMs to monitor energy consumption and initiate and receive energy transactions to and from the blockchain.
- Participants: There are two types of participants, namely producers (sellers) and consumers (buyers). The producer is a person who has surplus energy and wants to sell it. The produced energy can be stored in local battery banks in his residence or in the energy buffer of the MG. The consumer is a person who has an energy shortage and wants to buy energy.
- Energy Management System (EMS): The EMS represented by the energy market, which is the interface between energy sellers and buyers, controls energy trading, performs energy allocation, calculates energy price, controls access to energy assets, monitors participants’ behaviors, and secures transactions. The EMS implementation is utilizing HF security, privacy, and performance features.
4.2. Problem Definition of Energy Trading in MG
4.3. Configuration Specification of HF in SPETS
4.3.1. Identity Generation and Management
4.3.2. Channel Creation
4.3.3. Genesis Block Generation
4.3.4. HF Network Initialization
4.3.5. Secure Energy Transactions Generation
5. The Working Mechanism of SPETS
5.1. The Proposed Energy Market
- Orders Manager (OM): It comprises two processes, namely orders handling and orders verification. The orders handling process is responsible for receiving orders, checking their format, and sending back the responses. If the order format is correct, it will be sent to the verification process. If not, it will be rejected, and the participant will be notified. If the process receives an order in the time before or after the submitting time, it will be buffered until the next submission time. The orders verification process examines if the orders meet the rules of the market in terms of order configuration, pricing, and participant reputation. Firstly, the order configuration includes the determination of energy source, unit price, and the number of energy units that will be produced or consumed. Secondly, the buying or selling prices must be within the price range pre-determined by the market. Finally, the reputation score of the seller must be greater than the pre-determined reputation threshold . Algorithm 1 shows orders validation and verification steps. The computational complexity for this algorithm is .
- The Market Manager (MM): It includes the time slot manager that is responsible for managing the time slot’s beginning and ending as well as order submitting time. All orders verified by the OM are assembled in the orders book to execute the allocation mechanism. We use a discrete-time double auction mechanism to allocate supply and demand of market participants in a specific time slot, as discussed in Algorithm 2. If there is a matching, the matching result is sent to the orders handling process to send notifications to the involved participants. The market allocation mechanism employs a maximum allocation threshold () to mitigate the collusion attack.
- The Reputation Manager (RM): It is used to initialize and calculate the market reputation scores of sellers to guarantee market reliability and trustfulness between buyers and sellers. The reputation score initialization used to set initial scores for sellers at the beginning of their participation. By the end of time slots, reputation scores are updated by the reputation score update process and the orders verification process is notified of the scores.
| Algorithm 1 Energy Orders Handling and Verification |
|
5.1.1. Market Reputation Score (MRS)
5.1.2. Discrete-Time Double Auction
| Algorithm 2 Discrete-Time Double Auction With Average Mechanism |
|
5.2. Participants Registration and Authentication
5.3. Secure and Privacy-Preserving Energy Transactions
Sensitive Data Protection in SPETS
- 1.
- HF Channels: HF channel is a way of private communication between channel members where transactions submitted to one channel are hidden from any other channel members. One channel may include different organizations, while one organization can participate in different channels. The transaction issuer must be authenticated (by means of X.509 certificate) and authorized (by MSP) to submit a transaction to the channel.
- 2.
- HF PDC: HF presents PDC to allow a group of organizations on one channel to keep private data from other organizations on the same channel. Therefore, a defined group of organizations can endorse, commit, and query private data without creating a new channel. The PDC contains private data, which is stored in a private state database called "Side-DB" that existed on peers of authorized organizations. The private data was distributed from peer-to-peer using gossip protocol instead of sending it as blocks. Furthermore, the PDC contains the hash of the private data, which is stored on all peers who joined the channel to prove the existence of the private data and used for validation and audition.
6. Experiment Methodology
- Organizations: In the proposed HF network, there are three organizations, sellers, buyers, and the energy supplier, that decide to employ the proposed HF network to manage, sell, and buy energy. The sellers’ organization is responsible for handling sellers’ asks, while the buyers’ organization processes the buyers’ bids. The energy supplier organization is responsible for managing the energy network and managing users accounts and organizations.
- Peers: They host instances of chaincode and the ledger. There are two types of peers: endorsing and committing peers. Each organization consists of two peer nodes for endorsing and committing transactions. One peer is selected as an anchor peer to enable communication between the three organizations.
- Orderer: It is responsible for concurrently receiving transaction proposal responses from different users’ applications and arranging them in a well-defined sequence and combining them into blocks. Orderer sends these blocks to committing peers to commit and add them to the ledger. A single orderer node is used for implementation simplicity; it is called SOLO ordering.
- Certificate Authority: Fabric-CA is responsible for generating X.509 digital certificates to manage identities and sign transactions. The MSP defines the trusted root CA and intermediate CAs. In our energy network, the Fabric-CA is employed as root CA.
- Channel: In the energy network, there are two channels: the application channel and the system channel. The application channel, called energy_channel, handles the transactions coming from user applications. The other channel handles transactions of the network configuration.
- Client Application: It is the program that users can use to interact with the energy network by generating transaction proposals to invoke specific chaincode function. In our proposed system, users are classified as energy sellers or buyers.
- Chaincode: It is a program that manipulates business logic approved by the members of the network. Chaincode can be packaged, installed, instantiated, and upgraded on the endorsing nodes by the administrator or authorized user. In our energy network, chaincode handles and verifies energy bids and asks, performs energy allocation, and determines energy price. Our chaincode is implemented in go language and called Energy_Trading_SC.
7. Security Analysis and Numerical Results
7.1. Security and Privacy Analysis
7.2. Case Study
7.2.1. Simulation Setup
- The first scenario is the base line in our experiment where all participants are connected to the grid without applying any market mechanism. Feed-in Tariff (FIT) is used when producers sell their surplus energy to the grid and Time of Use Tariff (ToU) is used when energy is transferred from the grid to consumers.
- In the second scenario, producers and consumers participate in the energy market as sellers and buyers to trade energy following the proposed energy trading system.
7.2.2. Result Analysis
7.3. Benchmark Analysis of the Proposed HF Network
- Memory Usage: This metric measures the maximum and average memory consumption for every node and chaincode. Figure 6 shows the average memory usage of peer nodes, orderer node, and chaincode. It can be seen that the average memory consumption of the peer node is low, where it starts with 129 MB in workload A to reach 245.9 MB in workload E. In addition, the orderer and the chaincode consume a very low memory level (35.2 and 9.3 MB, respectively) in workload E. The minimum level of memory is consumed by the chaincode (from 3.5 MB to 9.3 MB). This indicates that the implementation of the proposed energy network can be easily implemented on devices with limited capabilities, such as smart IoT devices.
- Disk Usage: It is used to evaluate the ledger performance in terms of size and determine whether or not the ledge needs pruning. During the invoke transactions, the HF does not have to make a read on the ledger. Similarly, during the query transaction, HF reads data from the world state database. Thus, invoke and query transactions are providing zero bytes on disk. All peer nodes are writing an equal number of bytes on the disk with a maximum of 8.5 MB. The orderer node writes a number of bytes equal to 15.3 MB on the disk.
- Traffic: The traffic In and traffic Out are the parameters employed to conduct the network utilization analysis. The convergence of this study with others will provide highly intuitive and detailed guidance on performance. The traffic In and Out values for orderer peer are 4.7 MB and 8.6 MB, respectively. The peer nodes traffic In is in the range of 0.65 MB to 5.7 MB, where the traffic Out is in the range 0.32 MB to 3.6 MB. The CA traffic In and Out values are 152 bytes and zero bytes, respectively.
- Performance Metrics: Transaction throughput, latency, and send rate are the metrics that represent the HF platform’s efficiency. Figure 7 shows the number of transactions per second for different SUTs where it is in the range (40 TPS to 90 TPS) in the query and (26 TPS to 41 TPS) in the Init transactions. The average latency of query transactions is approximately zero where the Init transactions consume average latency from between 0.72 s and 2.39 s. The send rate for Init transactions is in the range (26 TPS to 70 TPS) where the query transactions rate is in the range (42 TPS to 93 TPS).
- CPU Utilization: This metric measures the CPU utilization of different peer nodes that help to analyze the chaincode operations using CPU utilization. Furthermore, it can be used to detect abnormal behavior of the HF network entities. Figure 8 shows the CPU utilization of endorsing peer nodes, which is in the range of (9% to 26%) in Init transactions, while it nears zero in the query transaction. The average and maximum CPU utilization of the chaincode and CA is approximately zero because the ordering service and the certificate generation are not run at the same time as the transaction proposal processing. However, the orderer node consumes a maximum of 15% of the CPU utilization because one orderer node is used (SOLO ordering).
8. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Acronym | Description |
|---|---|
| G | Set of Microgrids |
| Set of Energy Sellers | |
| Set of Energy Buyers | |
| Energy Seller | |
| Energy Buyer | |
| Minimum Energy Requirement for | |
| Minimum Energy Requirement for | |
| Maximum Energy Requirement for | |
| Maximum Energy Requirement for | |
| Total Energy Demand in MG | |
| Energy State of | |
| Energy State of | |
| Supplied Energy by | |
| Total Supplied Energy by | |
| Anticipated Energy of | |
| Total Anticipated Energy of | |
| s | Slot Time |
| Slot Time Beginning | |
| Slot time Ending | |
| Ask of | |
| Bid of | |
| Submission Time of Asks and Bids | |
| Selling Price of | |
| Maximum Energy Units to be Trade by | |
| Purchasing Price of | |
| Maximum Energy Units Required by | |
| Maximum Energy Selling Price | |
| Minimum Energy Purchasing Price | |
| Total Energy Sell Prices | |
| Total Energy Purchase Prices | |
| Orders Book in Time Slot s | |
| Reputation Threshold of Energy Sellers | |
| Maximum Energy Allocation Threshold | |
| RMS Value in Time Slot s | |
| Offered Quantity of Energy Units by | |
| Actual Quantity of Energy Units Generated by | |
| Digital Certificate of | |
| Public and Private Key Pair | |
| Transaction Number n | |
| Clearing price of transferred Energy from to | |
| Welfare of | |
| Welfare of |
| Acronym | Definition |
|---|---|
| CA | Certificate Authority |
| CoCB | Consortium Blockchain |
| DER | Distributed Energy Resources |
| DDoS | Distributed Denial of Service |
| DoS | Denial of Service |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| EMS | Energy Management System |
| FIT | Feed-in Tariff |
| GW | Gigawatt |
| HF | Hyperledger Fabric |
| MG | Microgrid |
| MITM | Man in the Middle |
| MM | Market Manager |
| MRS | Market Reputation Score |
| MSP | Membership Service Provider |
| NREL | National Renewable Energy Laboratory |
| P2P | Peer-to-Peer |
| PDC | Private Data Collections |
| PM | Orders Manager |
| PV | Photovoltaic |
| RES | Renewable Energy Resources |
| RM | Reputation Manager |
| SM | Smart Meter |
| SPETS | Secure and Privacy-Preserving Energy Trading System |
| SUT | System Under Test |
| TLS | Transport layer Security |
| ToU | Time of Use Tariff |
| TPS | Transactions Per Second |
References
- Mengelkamp, E.; Gärttner, J.; Rock, K.; Kessler, S.; Orsini, L.; Weinhardt, C. Designing microgrid energy markets: A case study: The Brooklyn Microgrid. Appl. Energy 2018, 210, 870–880. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-Preserving Energy Trading Using Consortium Blockchain in Smart Grid. IEEE Trans. Ind. Informatics 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Come Zebra, E.I.; van der Windt, H.J.; Nhumaio, G.; Faaij, A.P. A review of hybrid renewable energy systems in mini-grids for off-grid electrification in developing countries. Renew. Sustain. Energy Rev. 2021, 144, 111036. [Google Scholar] [CrossRef]
- U.S. Solar Market Insight. 2019. Available online: https://www.seia.org/us-solar-market-insight (accessed on 15 January 2021).
- Laszka, A.; Dubey, A.; Walker, M.; Schmidt, D. Providing Privacy, Safety, and Security in IoT-Based Transactive Energy Systems Using Distributed Ledgers. In Proceedings of the Seventh International Conference on the Internet of Things, Linz, Austria, 22 October 2017; Association for Computing Machinery: New York, NY, USA, 2017. [Google Scholar] [CrossRef] [Green Version]
- Park, D.H.; Park, Y.G.; Roh, J.H.; Lee, K.Y.; Park, J.B. A Hierarchical Peer-to-Peer Energy Transaction Model Considering Prosumer’s Green Energy Preference. Int. J. Control. Autom. Syst. 2021, 19, 311–317. [Google Scholar] [CrossRef]
- Dogan, E.; Altinoz, B.; Madaleno, M.; Taskin, D. The impact of renewable energy consumption to economic growth: A replication and extension of Inglesi-Lotz (2016). Energy Econ. 2020, 90. [Google Scholar] [CrossRef]
- Kermani, M.; Adelmanesh, B.; Shirdare, E.; Sima, C.A.; Carnì, D.L.; Martirano, L. Intelligent energy management based on SCADA system in a real Microgrid for smart building applications. Renew. Energy 2021, 171, 1115–1127. [Google Scholar] [CrossRef]
- Bullich-Massagué, E.; Díaz-González, F.; Aragüés-Peñalba, M.; Girbau-Llistuella, F.; Olivella-Rosell, P.; Sumper, A. Microgrid clustering architectures. Appl. Energy 2018, 212, 340–361. [Google Scholar] [CrossRef]
- Abdella, J.; Shuaib, K. Peer to Peer Distributed Energy Trading in Smart Grids: A Survey. Energies 2018, 11, 1560. [Google Scholar] [CrossRef] [Green Version]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Luecking, M. The convergence of IoT and distributed ledger technologies (DLT): Opportunities, challenges, and solutions. J. Netw. Comput. Appl. 2021, 177, 102936. [Google Scholar] [CrossRef]
- Tushar, W.; Saha, T.K.; Yuen, C.; Smith, D.; Poor, H.V. Peer-to-Peer Trading in Electricity Networks: An Overview. IEEE Trans. Smart Grid 2020, 4, 3185–3200. [Google Scholar] [CrossRef] [Green Version]
- Lohachab, A.; Garg, S.; Kang, B.H.; Amin, M.B. Performance evaluation of Hyperledger Fabric-enabled framework for pervasive peer-to-peer energy trading in smart Cyber–Physical Systems. Future Gener. Comput. Syst. 2021, 118, 392–416. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Maharjan, S.; Zhang, Y.; Hossain, E. Enabling Localized Peer-to-Peer Electricity Trading Among Plug-in Hybrid Electric Vehicles Using Consortium Blockchains. IEEE Trans. Ind. Informatics 2017, 13, 3154–3164. [Google Scholar] [CrossRef]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Informatics 2018, 14, 3690–3700. [Google Scholar] [CrossRef] [Green Version]
- Wang, S.; Taha, A.F.; Wang, J.; Kvaternik, K.; Hahn, A. Energy Crowdsourcing and Peer-to-Peer Energy Trading in Blockchain-Enabled Smart Grids. 2019. Available online: http://xxx.lanl.gov/abs/1901.02390 (accessed on 1 April 2021).
- Yang, X.; Wang, G.; He, H.; Lu, J.; Zhang, Y. Automated Demand Response Framework in ELNs: Decentralized Scheduling and Smart Contract. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 58–72. [Google Scholar] [CrossRef]
- Kim, H.M.; Turesson, H.; Laskowski, M.; Bahreini, A.F. Permissionless and Permissioned, Technology-Focused and Business Needs-Driven: Understanding the Hybrid Opportunity in Blockchain Through a Case Study of Insolar. IEEE Trans. Eng. Manag. 2020, 1–16. [Google Scholar] [CrossRef]
- Li, Z.; Bahramirad, S.; Paaso, A.; Yan, M.; Shahidehpour, M. Blockchain for decentralized transactive energy management system in networked microgrids. Electr. J. 2019, 32, 58–72. [Google Scholar] [CrossRef]
- Brooklyn Microgrid. 2016. Available online: https://www.brooklyn.energy/ (accessed on 12 August 2020).
- Olympic Peninsula GridWise. 2006. Available online: https://bgintegration.pnnl.gov/olypendemo.asp (accessed on 24 August 2020).
- SolarCoin. 2014. Available online: https://solarcoin.org/ (accessed on 24 August 2020).
- Mihaylov, M.; Razo-Zapata, I.; Nowé, A. Chapter 9 - NRGcoin—A Blockchain-based Reward Mechanism for Both Production and Consumption of Renewable Energy. In Transforming Climate Finance and Green Investment with Blockchains; Marke, A., Ed.; Academic Press: Cambridge, MA, USA, 2018; pp. 111–131. [Google Scholar] [CrossRef]
- Energy Blockchain Labs Inc. 2006. Available online: https://www.ibm.com/case-studies/energy-blockchain-labs-inc (accessed on 12 August 2020).
- Aitzhan, N.Z.; Svetinovic, D. Security and Privacy in Decentralized Energy Trading Through Multi-Signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2018, 15, 840–852. [Google Scholar] [CrossRef]
- Zhang, C.; Wu, J.; Zhou, Y.; Cheng, M.; Long, C. Peer-to-Peer energy trading in a Microgrid. Appl. Energy 2018, 220, 1–12. [Google Scholar] [CrossRef]
- Han, D.; Zhang, C.; Ping, J.; Yan, Z. Smart contract architecture for decentralized energy trading and management based on blockchains. Energy 2020, 199, 117417. [Google Scholar] [CrossRef]
- Paudel, A.; Chaudhari, K.; Long, C.; Gooi, H.B. Peer-to-Peer Energy Trading in a Prosumer-Based Community Microgrid: A Game-Theoretic Model. IEEE Trans. Ind. Electron. 2019, 66, 6087–6097. [Google Scholar] [CrossRef]
- Zhou, Z.; Wang, B.; Dong, M.; Ota, K. Secure and Efficient Vehicle-to-Grid Energy Trading in Cyber Physical Systems: Integration of Blockchain and Edge Computing. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 43–57. [Google Scholar] [CrossRef]
- Li, M.; Hu, D.; Lal, C.; Conti, M.; Zhang, Z. Blockchain-enabled Secure Energy Trading with Verifiable Fairness in Industrial Internet of Things. IEEE Trans. Ind. Informatics 2020, 16, 6564–6574. [Google Scholar]
- Zhong, W.; Xie, K.; Liu, Y.; Yang, C.; Xie, S. Auction Mechanisms for Energy Trading in Multi-Energy Systems. IEEE Trans. Ind. Informatics 2018, 14, 1511–1521. [Google Scholar] [CrossRef]
- Thakur, S.; Hayes, B.P.; Breslin, J.G. Distributed Double Auction for Peer to Peer Energy Trade using Blockchains. In Proceedings of the 5th International Symposium on Environment-Friendly Energies and Applications (EFEA), Rome, Italy, 24–26 September 2018; pp. 1–8. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2009, 21260. [Google Scholar]
- Sun, L.; Yang, Q.; Chen, X.; Chen, Z. RC-chain: Reputation-based crowdsourcing blockchain for vehicular networks. J. Netw. Comput. Appl. 2021, 176, 102956. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; Caro, A.D.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. arXiv 2018, arXiv:1801.10228. [Google Scholar]
- Hyperledger Fabric Tutorials. 2020. Available online: https://hyperledger-fabric.readthedocs.io/en/latest/getting_started.html (accessed on 15 January 2020).
- Sabounchi, M.; Wei, J. Towards resilient networked microgrids: Blockchain-enabled peer-to-peer electricity trading mechanism. In Proceedings of the IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–5. [Google Scholar]
- Andoni, M.; Robu, V.; Flynn, D.; Abram, S.; Geach, D.; Jenkins, D.; McCallum, P.; Peacock, A. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 2019, 100, 143–174. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Parsons, S.; Marcinkiewicz, M. Everything You Wanted to Know About Double Auctions, but Were Afraid to (Bid or) Ask; City University of New York: New York, NY, USA, 2006. [Google Scholar]
- Yuan, P.; Xiong, X.; Lei, L.; Zheng, K. Design and Implementation on Hyperledger-Based Emission Trading System. IEEE Access 2019, 7, 6109–6116. [Google Scholar] [CrossRef]
- Park, I.H.; Moon, S.J.; Lee, B.S.; Jang, J.W. A P2P Surplus Energy Trade Among Neighbors Based on Hyperledger Fabric Blockchain. In Information Science and Applications; Kim, K.J., Kim, H.Y., Eds.; Springer: Singapore, 2020; pp. 65–72. [Google Scholar]
- Khattak, H.A.; Tehreem, K.; Almogren, A.; Ameer, Z.; Din, I.U.; Adnan, M. Dynamic pricing in industrial internet of things: Blockchain application for energy management in smart cities. J. Inf. Secur. Appl. 2020, 55, 102615. [Google Scholar] [CrossRef]
- Wang, L.; Jiao, S.; Xie, Y.; Mubaarak, S.; Zhang, D.; Liu, J.; Jiang, S.; Zhang, Y.; Li, M. A Permissioned Blockchain-Based Energy Management System for Renewable Energy Microgrids. Sustainability 2021, 13, 1317. [Google Scholar] [CrossRef]
- Saha, S.; Ravi, N.; Hreinsson, K.; Baek, J.; Scaglione, A.; Johnson, N.G. A secure distributed ledger for transactive energy: The Electron Volt Exchange (EVE) blockchain. Appl. Energy 2021, 282, 116208. [Google Scholar] [CrossRef]
- PVWatts® Calculator. 2016. Available online: https://pvwatts.nrel.gov/pvwatts.php (accessed on 1 October 2020).
- Electricity Rates by State. 2020. Available online: https://www.electricchoice.com/electricity-prices-by-state/ (accessed on 1 October 2020).
- Hyperledger Caliper. Available online: https://www.hyperledger.org/use/caliper (accessed on 10 January 2020).







| Reference | Parameters | |||||
|---|---|---|---|---|---|---|
| Scenario | Market Design | Security Analysis | Privacy Consideration | Infrastructure Management | Performance Analysis | |
| [2] | Smart Grid | ⊗ | ⊗ | √ | CoCB | ⊙ |
| [5] | Microgrid | ⊙ | √ | √ | HF | ⊗ |
| [15] | Electric vehicles | ⊙ | √ | √ | CoBC | ⊙ |
| [17] | Smart Grid | ⊙ | ⊗ | ⊗ | HF | ⊙ |
| [26] | Smart Grid | √ | √ | √ | PBC | ⊙ |
| [27] | Microgrid | ⊙ | ⊗ | ⊗ | GT | ⊙ |
| [28] | Microgrid | √ | ⊗ | ⊗ | Eth | ⊙ |
| [29] | Microgrid | √ | ⊗ | ⊗ | GT | ⊙ |
| [30] | V2G | ⊙ | √ | ⊗ | CoBC | ⊙ |
| [31] | IIoT | ⊙ | √ | ⊙ | CoBC | ⊙ |
| [32] | Multi Energy System | ⊙ | ⊗ | ⊗ | Auction | ⊙ |
| [33] | Smart Grid | ⊙ | ⊗ | ⊗ | distributed Auction | ⊙ |
| Proposed Work | Microgrid | √ | √ | √ | HF | √ |
| Attacks | Definition | Defense | Resistant to Attack |
|---|---|---|---|
| Appending Attack | Attacker compromises a peer node to generate blocks with fake transactions. | The MSP manages the identity of all peer nodes using digital signatures generated from trusted certificate authority and defines permissions of nodes over network resources. | High. |
| Device Injection Attack | Malicious user tries to join the energy trading system with fake or compromised SM to provide incorrect transactions to cheat other users and make the system unstable. | SPETS validates the identity of the SM from the DSO company database and ensures the data that comes from the SM is encrypted and not altered. | High. |
| Linking Attack | Attacker uses the information in the transactions to link data in the ledger with the same ID to conclude the energy consumption history, leak user sensitive data, or reveal the identity of a participant. | SPETS uses the channels and private data collection to make hashes of the private data of participants and store it in a side-DB that is only accessible for authorized nodes from authorized organizations. | Beyond High. |
| Distributed DoS (DDoS) Attack. | Attacker tries to make a service unavailable to users by sending a huge number of requests to overwhelm the HF peers and becomes unable to handle them. Attackers flood the endorsing peers with a huge number of transactions to overwhelm the network. | HF mitigates DDoS attacks using redundant architecture such as using Raft and Kafka instead of single orderer. Separating transaction execution functionalities in HF helps to increase efficiency and accelerate delivery of transactions to ordering services. Determining fixed time slots for receiving traders’ bids/asks reduced the number of transactions possibly received by the endorsing peers. | Beyond High. |
| Man-in-the-Middle (MITM) Attack | An adversary intercepting user data to control the communication channel between the seller/buyer and the energy market. Then, the adversary can hijack the network stream and tamper with data transmitted on the compromised channel | HF secures communication between peers using transport layer security (TLS), where any peer can work as a TLS client or server. Furthermore, hashing algorithms such as SHA-256 are used to ensure data integrity and authentication. | High. |
| Collusion Attack | Prosumers can collude with others to maximize their profit. | SPETS determines a maximum allocation of energy per time slot for participants to mitigate a collusion attack. Moreover, prosumers and consumers can participate once every time slot. | Beyond High. |
| First Preimage Attack | The attacker obtains the victim’s original seed and performs a collision search using an elliptic curve to find a seed message that gives the same hash as the victim’s private key. | All transactions are encrypted and signed using private key, and hence only the receiver could decrypt the transaction. Consequently, a minor change in any transaction will break the integrity and signature of the transaction | High. |
| 51% Attack | If the attacker can control more than 51% of peer nodes in the network, the 51% attack can occur. The controlling nodes can prevent new transactions being confirmed and help accept fake blocks. | The modular architecture of HF and severity of consensus protocols make it suitable for different business needs. The 51% attack is very unlikely to happen if the HF network is correctly set up and configured. | Moderate. |
| Ref. | Year | Paper Summary | Scope | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Utilized Blockchain | Energy Trading Framework | Benchmark Analysis | Application Designing | System Security | Sensitive Data Protection | Market Designing | |||
| [5] | 2017 | Energy transactions enabled in a privacy-preserving manner in microgrid. | HF | ⊙ | ⊗ | ⊗ | √ | √ | ⊙ |
| [17] | 2019 | HF-enabled energy trading for crowd- sourced energy systems in smart grids. | HF | ⊙ | ⊗ | √ | ⊗ | ⊗ | ⊙ |
| [42] | 2018 | Hyperledger-enabled emission trading system to provide credible trading service for legal polluters. | HF | ⊙ | ⊙ | √ | ⊗ | ⊗ | ⊙ |
| [43] | 2020 | Reliable and scalable surplus energy trading among neighbors using HF. | HF | ⊙ | ⊗ | ⊗ | ⊗ | ⊗ | ⊙ |
| [44] | 2020 | Adopting smart contract to control energy bidding process to enable dynamic pricing of energy trading in smart cities. | HF | ⊙ | ⊗ | √ | ⊙ | ⊗ | ⊙ |
| [45] | 2020 | P2P energy management system based on permissioned blockchain with privacy protection. | HF | ⊙ | ⊗ | √ | √ | √ | ⊙ |
| [46] | 2021 | Secure energy transaction based on distributed pricing, scheduling, and theft mitigation. | HF | ⊙ | ⊗ | ⊗ | √ | ⊗ | √ |
| Proposed work | Utilizing HF to implement energy trading system with secure energy market, sensitive information protection, reputation management, and allocation control. | HF | √ | √ | √ | √ | √ | √ | |
| Sellers’ Asks | Buyers’ Bids | ||||
|---|---|---|---|---|---|
| Seller No. | (kWh) | (¢/kWh) | Buyer No. | (kWh) | (¢/kWh) |
| 1 | 18 | 20.20 | 1 | 15 | 21.10 |
| 2 | 17 | 19.00 | 2 | 9 | 21.30 |
| 3 | 19 | 18.50 | 3 | 15 | 19.50 |
| 4 | 12 | 22.00 | 4 | 14 | 22.00 |
| 5 | 10 | 17.90 | 5 | 18 | 22.25 |
| 6 | 16 | 20.50 | 6 | 7 | 21.20 |
| 7 | 18 | 21.00 | 7 | 11 | 21.00 |
| 8 | 4 | 21.50 | 8 | 8 | 21.50 |
| 9 | 14 | 23.00 | 9 | 16 | 22.50 |
| 10 | 29 | 20.90 | 10 | 22 | 23.00 |
| - | - | - | - | - | - | 8 | 21.10 | 10 | 21.23 | - | - | - | - | - | - | - | - | - | - | |
| - | - | - | - | - | - | - | - | 8 | 20.62 | - | - | - | - | - | - | 9 | 20.75 | - | - | |
| - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | 7 | 20.50 | 12 | 20.75 | |
| - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | |
| - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | 10 | 20.45 | |
| - | - | 2 | 20.90 | - | - | 6 | 21.25 | - | - | - | - | - | - | 8 | 21.00 | - | - | - | - | |
| - | - | - | - | - | - | - | - | - | - | - | 11 | 21.00 | - | - | - | - | - | - | ||
| - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | |
| - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | |
| 15 | 21.00 | 7 | 21.10 | - | - | - | - | - | - | 7 | 21.05 | - | - | - | - | - | - | - | - | |
| Attributes | Number of Clients | Number of Transactions | Transaction Arrival Rate | Batch Timeout (ms) | Max Message Count | |
|---|---|---|---|---|---|---|
| SUT | A | 10 | 100 | 60 | 200 | 50 |
| B | 20 | 200 | 120 | 350 | 100 | |
| C | 30 | 300 | 180 | 500 | 150 | |
| D | 40 | 400 | 240 | 650 | 200 | |
| E | 50 | 500 | 300 | 700 | 250 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Samy, A.; Yu, H.; Zhang, H.; Zhang, G. SPETS: Secure and Privacy-Preserving Energy Trading System in Microgrid. Sensors 2021, 21, 8121. https://doi.org/10.3390/s21238121
Samy A, Yu H, Zhang H, Zhang G. SPETS: Secure and Privacy-Preserving Energy Trading System in Microgrid. Sensors. 2021; 21(23):8121. https://doi.org/10.3390/s21238121
Chicago/Turabian StyleSamy, Ahmed, Haining Yu, Hongli Zhang, and Guangyao Zhang. 2021. "SPETS: Secure and Privacy-Preserving Energy Trading System in Microgrid" Sensors 21, no. 23: 8121. https://doi.org/10.3390/s21238121
APA StyleSamy, A., Yu, H., Zhang, H., & Zhang, G. (2021). SPETS: Secure and Privacy-Preserving Energy Trading System in Microgrid. Sensors, 21(23), 8121. https://doi.org/10.3390/s21238121







