A Systematic Review on Recent Trends, Challenges, Privacy and Security Issues of Underwater Internet of Things
Abstract
:1. Introduction
2. Q1: What Are the Recent Trends of UIoT System?
2.1. Prior Research
2.2. Communication Technologies of UIoT
3. Q2: What Are the Challenges of the Current UIoT System
3.1. Channel Characteristics of UIoT
3.1.1. Underwater Channel
3.1.2. Energy Consumption and Storage
3.1.3. Environmental Condition
3.2. Technical Challenges of UIoT
3.2.1. Limited Resources
3.2.2. Unreliable Channel Condition
3.2.3. Insecure Environment
3.2.4. High Cost
3.2.5. Dynamic Topology
3.2.6. Physical Damages
3.2.7. Network Configuration
3.3. Security Challenges of UIoT
3.3.1. Complex Environment
3.3.2. Data Privacy
3.3.3. Network and Device Management
3.3.4. Localization Techniques
3.4. Security Goals, Attacks and Privacy of UIoT
3.4.1. Security Goals of UIoT
Confidentiality
Integrity
Availability
Privacy
Authenticity
Auditability
Others
3.4.2. Passive Attacks
3.4.3. Active Attacks
4. Q3: What Are the Methodologies Used to Overcome the Challenges in UIoT?
4.1. Methods to Overcome the Technical Challenges of UIoT
4.1.1. Low Battery Consumption Methods
4.1.2. Memory Management Methods
4.1.3. Unreliable Data Transmission Methods
4.1.4. Noise Modeling Methods
4.1.5. Localization Methods
4.1.6. Low-Cost Communication Methods
4.1.7. Device Management and Physical Damage Protection Methods
4.1.8. Connection and Reconfiguration Methods
4.2. Methods to Overcome the Security Challenges in UIoT
4.2.1. Methods to Prevent DoS Attacks
4.2.2. Methods to Prevent Jamming Attacks
4.2.3. Methods to Prevent Node Compromise Attacks
4.2.4. Methods to Prevent Sybil Attacks
4.2.5. Methods to Prevent Wormhole Attacks
4.2.6. Methods to Prevent Flooding Attacks
4.2.7. Methods to Prevent Black-Hole Attacks
5. Q4: What Are the Findings Based on the Existing Research Works?
6. Q5: Future Direction
6.1. Build Hybrid Communication Models for Future UIoT
6.2. Build Underwater Automatic Battery Recharging Module for Future UIoT
6.3. Build Standard Security Models for Future UIoT
6.4. Build Privacy Models for Future UIoT
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- NOAA, America’s Coastal & Ocean Agency. How Much Water Is in the Ocean? Available online: https://oceanservice.noaa.gov/facts/oceanwater.html (accessed on 28 October 2021).
- Awan, K.M.; Shah, P.A.; Iqbal, K.; Gillani, S.; Ahmad, W.; Nam, Y. Underwater Wireless Sensor Networks: A Review of Recent Issues and Challenges. Wirel. Commun. Mob. Comput. 2019, 2019, 6470359. [Google Scholar] [CrossRef]
- Yang, G.; Dai, L.; Si, G.; Wang, S.; Wang, S. Challenges and Security Issues in Underwater Wireless Sensor Networks. Procedia Comput. Sci. 2019, 147, 210–216. [Google Scholar] [CrossRef]
- Gussen, C.M.G.; Diniz, P.S.R.; Campos, M.L.R.; Martins, W.A.; Costa, F.M.; Gois, J.N. A Survey of Underwater Wireless Communication Technologies. J. Commun. Inf. Syst. 2016, 31, 242–255. [Google Scholar] [CrossRef]
- Zoksimovski, A.; Sexton, D.; Stojanovic, M.; Rappaport, C. Underwater electromagnetic communications using conduction—Channel characterization. Ad Hoc Netw. 2015, 34, 42–51. [Google Scholar] [CrossRef]
- Rhodes, M. Electromagnetic propagation in seawater and its value in military systems. In Proceedings of the Conference of System Engineering for Autonomous Systems from the Defense Technology Centre (SEAS DTC’07), Edinburgh, UK, 2007; pp. 1–6. [Google Scholar]
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Challenges for efficient communication in underwater acoustic sensor net-works. ACM Sigbed Rev. 2004, 1, 3–8. [Google Scholar] [CrossRef]
- Chitre, M.; Shahabudeen, S.; Freitag, L.; Stojanovic, M. Recent advances in underwater acoustic communications & networking. In Proceedings of the OCEANS 2008, Quebec City, QC, Canada, 15–18 September 2008; pp. 1–10. [Google Scholar]
- Kumar, P.; Trivedi, V.K.; Kumar, P. Recent trends in multicarrier underwater acoustic communications. In Proceedings of the Underwater Technology (UT), Chennai, India, 23–25 February 2015; pp. 1–8. [Google Scholar]
- Spagnolo, G.S.; Cozzella, L.; Leccese, F. Underwater Optical Wireless Communications: Overview. Sensors 2020, 20, 2261. [Google Scholar] [CrossRef] [PubMed]
- Zeng, Z.; Fu, S.; Zhang, H.; Dong, Y.; Cheng, J. A Survey of Underwater Optical Wireless Communications. IEEE Commun. Surv. Tutor. 2016, 19, 204–238. [Google Scholar] [CrossRef]
- Kaushal, H.; Kaddoum, G. Underwater Optical Wireless Communication. IEEE Access 2016, 4, 1518–1547. [Google Scholar] [CrossRef]
- Murgod, T.R.; Sundaram, S.M. Survey on underwater optical wireless communication: Perspectives and challenges. Indones. J. Electr. Eng. Comput. Sci. 2019, 13, 138–146. [Google Scholar] [CrossRef]
- Kumar, M.; Rani, M. A Design of Novel Hybrid Optoacoustic Modem for Underwater Communication. Int. J. Innov. Technol. Explor. Eng. (IJITEE) 2019, 8, 3383–3389. [Google Scholar]
- Farr, N.; Bowen, A.; Ware, J.; Pontbriand, C.; Tivey, M. An integrated, underwater optical /acoustic communications system. In Proceedings of the OCEANS’10 IEEE SYDNEY, Sydney, NSW, Australia, 24–27 May 2010; pp. 1–6. [Google Scholar] [CrossRef]
- Tennenbaum, A.; Dyakiw, M.; Cui, J.-H.; Peng, Z. Application of Low Cost Optical Communication Systems to Underwater Acoustic Networks. In Proceedings of the OCEANS’10 IEEE SYDNEY, Sydney, NSW, Australia, 24–27 May 2010; pp. 1–6. [Google Scholar] [CrossRef]
- Han, S.; Noh, Y.; Liang, R.; Chen, R.; Cheng, Y.-J.; Gerla, M. Evaluation of underwater optical-acoustic hybrid network. China Commun. 2014, 11, 49–59. [Google Scholar] [CrossRef]
- Johnson, L.J.; Green, R.J.; Leeson, M.S. Hybrid underwater optical/acoustic link design. In Proceedings of the 2014 16th International Conference on Transparent Optical Networks (ICTON), Graz, Austria, 6–10 July 2014; pp. 1–4. [Google Scholar] [CrossRef]
- Gauni, S.; Manimegalai, C.T.; Krishnan, K.M.; Shreeram, V.; Arvind, V.V.; Srinivas, T.V.N. Design and Analysis of Co-operative Acoustic and Optical Hybrid Communication for Underwater Communication. Wirel. Pers. Commun. 2021, 117, 561–575. [Google Scholar] [CrossRef]
- Delphin Raj, K.M.; Yum, S.-H.; Ko, E.; Shin, S.-Y.; Namgung, J.-I.; Park, S.-H. Multi-Media and Multi-Band Based Adaptation Layer Techniques for Underwater Sensor Networks. Appl. Sci. 2019, 9, 3187. [Google Scholar]
- Raj, M.K.; Yum, S.-H.; Lee, J.; Ko, E.; Shin, S.-Y.; Park, S.-H. Handover Mechanism Based on Underwater Hybrid Soft-ware-Defined Modem in Advanced Diver Networks. CMC-Comput. Mater. Contin. 2022, 70, 5721–5743. [Google Scholar]
- Kao, C.-C.; Lin, Y.-S.; Wu, G.-D.; Huang, C.-J. A Comprehensive Study on the Internet of Underwater Things: Applications, Challenges, and Channel Models. Sensors 2017, 17, 1477. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Felemban, E.; Shaikh, F.K.; Qureshi, U.M.; Sheikh, A.A.; Bin Qaisar, S. Underwater Sensor Network Applications: A Comprehensive Survey. Int. J. Distrib. Sens. Netw. 2015, 11, 1–14. [Google Scholar] [CrossRef] [Green Version]
- Hollinger, G.A.; Mitra, U.; Sukhatme, G.S. Active Classification: Theory and Application to Underwater Inspection. In Robotics Research; Springer Tracts in Advanced Robotics; Springer: Cham, Switzerland, 2016; Volume 100, pp. 95–110. [Google Scholar] [CrossRef] [Green Version]
- Delphin Raj, K.M.; Lee, J.; Yum, S.-H.; Ko, E.; Shin, S.-Y.; Namgung, J.-I.; Park, S.-H. Underwater Network Management System in Internet of Underwater Things: Open Challenges, Benefits, and Feasible Solution. Electronics 2020, 9, 1142. [Google Scholar] [CrossRef]
- Qiu, T.; Zhao, Z.; Zhang, T.; Chen, C.; Chen, C. Underwater Internet of Things in Smart Ocean: System Architecture and Open Issues. IEEE Trans. Ind. Inform. 2019, 16, 4297–4307. [Google Scholar] [CrossRef]
- Kong, J.; Ji, Z.; Wang, W.; Gerla, M.; Bagrodia, R.; Bhargava, B. Low-cost attacks against packet delivery, localization and time synchronization services in underwater sensor networks. In Proceedings of the 4th ACM Workshop on Wireless Security, Cologne, Germany, 2 September 2005. [Google Scholar]
- Das, A.; Thampi, S. Secure communication in mobile underwater wireless sensor networks. In Proceedings of the 2015 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Shenzhen, China, 10–13 August 2015. [Google Scholar]
- Ding, Y.; Li, N.; Song, B.; Yang, Y. The mobile node deployment algorithm for underwater wireless sensor networks. In Proceedings of the 2017 Chinese Automation Congress (CAC), Jinan, China, 20–22 October 2017; pp. 456–460. [Google Scholar] [CrossRef]
- Luo, J.; Yang, Y.; Wang, Z.; Chen, Y.; Wu, M. A Mobility-Assisted Localization Algorithm for Three-Dimensional Large-Scale UWSNs. Sensors 2020, 20, 4293. [Google Scholar] [CrossRef]
- Patel, K.K.; Patel, S.M. Internet of things (IoT): Definition, characteristics, architecture, enabling technologies, application and future challenges. Int. J. Eng. Sci. Comput. 2016, 6, 6122–6131. [Google Scholar]
- García, D.R.; Montiel-Nelson, J.; Bautista, T.; Sosa, J. A New Method for Gaining the Control of Standalone Underwater Sensor Nodes Based on Power Supply Sensing. Sensors 2021, 21, 4660. [Google Scholar] [CrossRef] [PubMed]
- Alazab, M.; Lakshmanna, K.; Reddy, G.T.; Pham, Q.-V.; Maddikunta, P.K.R. Multi-objective cluster head selection using fitness averaged rider optimization algorithm for IoT networks in smart cities. Sustain. Energy Technol. Assess. 2021, 43, 100973. [Google Scholar] [CrossRef]
- Bhattacharya, S.; Kumar, P.; Meenakshisundaram, I.; Gadekallu, T.R.; Sharma, S.; Alkahtani, M.; Abidi, M.H. Deep Neural Networks Based Approach for Battery Life Prediction. CMC-Comput. Mater. Contin. 2021, 69, 2599–2615. [Google Scholar] [CrossRef]
- Qadar, R.; Bin Qaim, W.; Nurmi, J.; Tan, B. Effects of Multipath Attenuation in the Optical Communication-Based Internet of Underwater Things. Sensors 2020, 20, 6201. [Google Scholar] [CrossRef] [PubMed]
- Hwang, H.Y. Analysis of Throughput and Delay for an Underwater Multi-DATA Train Protocol with Multi-RTS Reception and Block ACK. Sensors 2020, 20, 6473. [Google Scholar] [CrossRef]
- Kim, S.H.; Choi, B.K.; Kim, B.-N. Correlation between Underwater Noise and Sea Level at Ieodo Ocean Research Station. J. Mar. Sci. Eng. 2020, 9, 1. [Google Scholar] [CrossRef]
- Jiang, S. On Securing Underwater Acoustic Networks: A Survey. IEEE Commun. Surv. Tutor. 2018, 21, 729–752. [Google Scholar] [CrossRef]
- Misra, S.; Mondal, A.; Mondal, A. DATUM: Dynamic Topology Control for Underwater Wireless Multimedia Sensor Networks. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Ullah, I.; Chen, J.; Su, X.; Esposito, C.; Choi, C. Localization and Detection of Targets in Underwater Wireless Sensor Using Distance and Angle Based Algorithms. IEEE Access 2019, 7, 45693–45704. [Google Scholar] [CrossRef]
- Dini, G.; Duca, A.L. A Secure Communication Suite for Underwater Acoustic Sensor Networks. Sensors 2012, 12, 15133–15158. [Google Scholar] [CrossRef] [Green Version]
- Khanam, S.; Bin Ahmedy, I.; Idris, M.Y.I.; Jaward, M.H.; Sabri, A.Q.B.M. A Survey of Security Challenges, Attacks Taxonomy and Advanced Countermeasures in the Internet of Things. IEEE Access 2020, 8, 219709–219743. [Google Scholar] [CrossRef]
- Alsamani, B.; Lahza, H. A taxonomy of IoT: Security and privacy threats. In Proceedings of the 2018 International Conference on Information and Computer Technologies (ICICT), DeKalb, IL, USA, 23–25 March 2018; pp. 72–77. [Google Scholar] [CrossRef]
- Raymond, D.R.; Midkiff, S.F. Denial-of-service in wireless sensor networks: Attacks and defenses. IEEE Pervasive Comput. 2008, 7, 74–81. [Google Scholar] [CrossRef]
- Demirbas, M.; Song, Y. An RSSI-based Scheme for Sybil Attack Detection in Wireless Sensor Networks. In Proceedings of the 2006 International Symposium on a World of Wireless, Mobile and Multimedia Networks, Buffalo-Niagara Falls, NY, USA, 26–29 June 2006; pp. 564–570. [Google Scholar] [CrossRef] [Green Version]
- Du, W.; Deng, J.; Han, Y.S.; Varshney, P.K. A pairwise key predistribution scheme for wireless sensor networks. ACM Trans. Inf. Syst. Secur. 2005, 8, 228–258. [Google Scholar] [CrossRef] [Green Version]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The Sybil attack in sensor networks: Analysis & defences. In Proceedings of the Third International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 27 April 2004; pp. 259–268. [Google Scholar]
- Gorlatova, M.A.; Mason, P.C.; Wang, M.; Lamont, L.; Liscano, R. Detecting Wormhole Attacks in Mobile Ad Hoc Networks through Protocol Breaking and Packet Timing Analysis. In Proceedings of the MILCOM 2006—2006 IEEE Military Communications Conference, Washington, DC, USA, 23–25 October 2006; pp. 1–7. [Google Scholar] [CrossRef]
- Kong, J.; Ji, Z.; Wang, W.; Gerla, M.; Bagrodia, R. On Wormhole Attacks in Under-Water Sensor Networks: A Two-Tier Localization Approach; Technical Report; UCLA Computer Science Department: Los Angeles, CA, USA, 2004. [Google Scholar]
- Jen, S.-M.; Laih, C.-S.; Kuo, W.-C. A Hop-Count Analysis Scheme for Avoiding Wormhole Attacks in MANET. Sensors 2009, 9, 5022–5039. [Google Scholar] [CrossRef] [PubMed]
- Wang, W.; Kong, J.; Bhargava, B.; Gerla, M. Visualisation of wormholes in underwater sensor networks: A distributed approach. Int. J. Secur. Netw. 2008, 3, 10–23. [Google Scholar] [CrossRef]
- Kaur, P.; Gurm, J.S. Detect and prevent HELLO FLOOD Attack using Centralized technique in WSN. Int. J. Comput. Sci. Eng. Technol. 2016, 7, 379–381. [Google Scholar]
- Hyakudome, T.; Yoshida, H.; Ishibashi, S.; Sawa, T.; Nakamura, M. Development of advanced lithium-ion battery for underwater vehicle. In Proceedings of the 2011 IEEE Symposium on Underwater Technology and Workshop on Scientific Use of Submarine Cables and Related Technologies, Tokyo, Japan, 5–8 April 2011. [Google Scholar]
- Lin, M.; Li, D.; Yang, C. Design of an ICPT system for battery charging applied to underwater docking systems. Ocean. Eng. 2017, 145, 373–381. [Google Scholar] [CrossRef]
- Pendergast, D.R.; DeMauro, E.P.; Fletcher, M.; Stimson, E.; Mollendorf, J.C. A rechargeable lithium-ion battery module for underwater use. J. Power Sources 2011, 196, 793–800. [Google Scholar] [CrossRef]
- Jin, L.; (David) Huang, D. A slotted CSMA based reinforcement learning approach for extending the lifetime of underwater acoustic wireless sensor networks. Comput. Commun. 2013, 36, 1094–1099. [Google Scholar] [CrossRef]
- Guida, R.; Demirors, E.; Dave, N.; Melodia, T. Underwater Ultrasonic Wireless Power Transfer: A Battery-less Platform for the Internet of Underwater Things. IEEE Trans. Mob. Comput. 2020, 1–12. Available online: https://ieeexplore.ieee.org/document/9217956 (accessed on 6 December 2021). [CrossRef]
- Xing, G.; Chen, Y.; He, L.; Su, W.; Hou, R.; Li, W.; Zhang, C.; Chen, X. Energy Consumption in Relay Underwater Acoustic Sensor Networks for NDN. IEEE Access 2019, 7, 42694–42702. [Google Scholar] [CrossRef]
- Ahmed, G.; Zhao, X.; Fareed, M.M.S.; Fareed, M.Z. An Energy-Efficient Redundant Transmission Control Clustering Approach for Underwater Acoustic Networks. Sensors 2019, 19, 4241. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hou, R.; He, L.; Hu, S.; Luo, J. Energy-Balanced Unequal Layering Clustering in Underwater Acoustic Sensor Networks. IEEE Access 2018, 6, 39685–39691. [Google Scholar] [CrossRef]
- Raza, W.; Ma, X.; Ali, A.; Shah, Z.A.; Mehdi, G. An implementation of partial transmit sequences to design energy efficient underwater acoustic OFDM communication system. arXiv 2020, arXiv:2007.01273. [Google Scholar]
- Wang, C.; Zhao, X.; Zhao, Z.; Xu, W.; Cui, L. Software-Defined Multimodal Underwater Wireless Sensor Network Platform Powered by Seawater Battery. In Proceedings of the China Conference on Wireless Sensor Networks, Dunhuang, China, 18–21 September 2020; Springer: Singapore, 2020. [Google Scholar]
- Nguyen, C.T.; Nguyen, M.T.; Mai, V.V.; Nguyen, C.T. Reliable Transmission for Underwater Optical Wireless Communication Networks with Energy Harvesting. In Proceedings of the 2020 IEEE Eighth International Conference on Communications and Electronics (ICCE), Phu Quoc Island, Vietnam, 13–15 January 2021. [Google Scholar]
- Khan, Z.A.; Karim, O.A.; Abbas, S.; Javaid, N.; Bin Zikria, Y.; Tariq, U. Q-learning based energy-efficient and void avoidance routing protocol for underwater acoustic sensor networks. Comput. Netw. 2021, 197, 108309. [Google Scholar] [CrossRef]
- Urunov, K.; Shin, S.-Y.; Park, S.-H.; Lim, Y.K. Analysis of the network management system with constrained underwa-ter devices. In Proceedings of the Symposium of the Korean Institute of Communications and Information Sciences, Seoul, Korea, 21–23 June 2017. [Google Scholar]
- Urunov, K.; Shin, S.-Y.; Namgung, J.-I.; Park, S.-H. High-Level architectural design of management system for the in-ternet of underwater things. In Proceedings of the 2018 Tenth International Conference on Ubiquitous and Future Networks (ICUFN), Prague, Czech Republic, 3–6 July 2018; pp. 326–331. [Google Scholar]
- Li, N.; Martínez, J.-F.; Chaus, J.M.M.; Eckert, M. A Survey on Underwater Acoustic Sensor Network Routing Protocols. Sensors 2016, 16, 414. [Google Scholar] [CrossRef] [Green Version]
- Jiang, S. On Reliable Data Transfer in Underwater Acoustic Networks: A Survey From Networking Perspective. IEEE Commun. Surv. Tutor. 2018, 20, 1036–1055. [Google Scholar] [CrossRef]
- Fattah, S.; Gani, A.; Ahmedy, I.; Idris, M.Y.I.; Hashem, I.A.T. A Survey on Underwater Wireless Sensor Networks: Requirements, Taxonomy, Recent Advances, and Open Research Challenges. Sensors 2020, 20, 5393. [Google Scholar] [CrossRef] [PubMed]
- Lloyd, T.P.; Turnock, S.R.; Humphrey, V.F. Modelling techniques for underwater noise generated by tidal turbines in shallow waters. In Proceedings of the International Conference on Offshore Mechanics and Arctic Engineering, Rotterdam, The Netherlands, 19–24 June 2011; pp. 777–785. [Google Scholar] [CrossRef]
- Wang, C.; Yu, H.-Y.; Zhu, Y.-J.; Wang, T. Blind Detection for SPAD-Based Underwater VLC System Under P–G Mixed Noise Model. IEEE Commun. Lett. 2017, 21, 2602–2605. [Google Scholar] [CrossRef]
- Merchant, N.D.; Brookes, K.L.; Faulkner, R.; Bicknell, A.W.J.; Godley, B.J.; Witt, M. Underwater noise levels in UK waters. Sci. Rep. 2016, 6, 36942. [Google Scholar] [CrossRef]
- Bagočius, D.; Narščius, A. Simplistic underwater ambient noise modelling for shallow coastal areas: Lithuanian area of the Baltic Sea. Ocean. Eng. 2018, 164, 521–528. [Google Scholar] [CrossRef]
- Bagocious, D.; Aleksas, N. Underwater noise level predictions of ammunition explosions in the shal-low area of Lithuanian Baltic Sea. Environ. Pollut. 2019, 252, 1311–1317. [Google Scholar] [CrossRef]
- Kellett, P.; Turan, O.; Incecik, A. A study of numerical ship underwater noise prediction. Ocean. Eng. 2013, 66, 113–120. [Google Scholar] [CrossRef]
- Magnier, C.; Gervaise, C. Reciprocal modelling between the underwater ambient noise and the coastal maritime traffic density in the Calvi bay. Proc. Meet. Acoust. 2019, 37, 070006. [Google Scholar] [CrossRef]
- Pennucci, G.; Jiang, Y.-M. Extracting Acoustic Source Information of Shipping Noise for Dynamic Ambient Noise Modelling. J. Shipp. Ocean. Eng. 2018, 8, 10–20. [Google Scholar] [CrossRef]
- Jalkanen, J.-P.; Johansson, L.; Liefvendahl, M.; Bensow, R.; Sigray, P.; Östberg, M.; Karasalo, I.; Andersson, M.; Peltonen, H.; Pajala, J. Modelling of ships as a source of underwater noise. Ocean. Sci. 2018, 14, 1373–1383. [Google Scholar] [CrossRef] [Green Version]
- Pan, C.; Jia, L.; Cai, R.; Ding, Y. Modeling and simulation of channel for underwater communication network. Int. J. Innov. Comput. Inf. Control. 2012, 8, 2149–2156. [Google Scholar]
- Gholipour, A.; Zakeri, B.; Mafinezhad, K. Non-stationary additive noise modelling in direction-of-arrival estimation. IET Commun. 2016, 10, 2054–2059. [Google Scholar] [CrossRef]
- Roul, S.; Kumar, C.; Das, A. Ambient noise estimation in territorial waters using AIS data. Appl. Acoust. 2019, 148, 375–380. [Google Scholar] [CrossRef]
- Islam, T.; Park, S.-H. A Comprehensive Survey of the Recently Proposed Localization Protocols for Underwater Sensor Networks. IEEE Access 2020, 8, 179224–179243. [Google Scholar] [CrossRef]
- Liu, P.; Wang, B.; Deng, Z.; Fu, M. INS/DVL/PS Tightly Coupled Underwater Navigation Method With Limited DVL Measurements. IEEE Sens. J. 2018, 18, 2994–3002. [Google Scholar] [CrossRef]
- Carroll, P.; Mahmood, K.; Zhou, S.; Zhou, H.; Xu, X.; Cui, J.-H. On-Demand Asynchronous Localization for Underwater Sensor Networks. IEEE Trans. Signal. Process. 2014, 62, 3337–3348. [Google Scholar] [CrossRef]
- Das, A.P.; Thampi, S.M. Fault-resilient localization for underwater sensor networks. Ad Hoc Netw. 2017, 55, 132–142. [Google Scholar] [CrossRef]
- Benson, B.; Li, Y.; Faunce, B.; Domond, K.; Kimball, D.; Schurgers, C.; Kastner, R. Design of a Low-Cost Underwater Acoustic Modem. IEEE Embed. Syst. Lett. 2010, 2, 58–61. [Google Scholar] [CrossRef] [Green Version]
- Song, Y. Underwater Acoustic Sensor Networks with Cost Efficiency for Internet of Underwater Things. IEEE Trans. Ind. Electron. 2020, 68, 1707–1716. [Google Scholar] [CrossRef]
- Benson, B.; Li, Y.; Kastner, R.; Faunce, B.; Domond, K.; Kimball, D.; Schurgers, C. Design of a low-cost, underwater acoustic modem for short-range sensor networks. In Proceedings of the OCEANS′10 IEEE SYDNEY, Sydney, NSW, Australia, 24–27 May 2010. [Google Scholar]
- Cario, G.; Casavola, A.; Lupia, M.; Rosace, C. SeaModem: A low-cost underwater acoustic modem for shallow water communication. In Proceedings of the OCEANS 2015—Genova, Genova, Italy, 18–21 May 2015. [Google Scholar] [CrossRef]
- Mitchell, B.; Wilkening, E.; Mahmoudian, N. Low cost underwater gliders for littoral marine research. In Proceedings of the American Control Conference (ACC), Seattle, WA, USA, 17–19 June 2013; pp. 1412–1417. [Google Scholar]
- Fischell, E.M.; Kroo, A.R.; O’Neill, B.W. Single-hydrophone low-cost underwater vehicle swarming. IEEE Robot. Autom. Lett. 2019, 5, 354–361. [Google Scholar] [CrossRef]
- Sanchez, A.; Blanc, S.; Yuste, P.; Serrano, J.J. A low cost and high efficient acoustic modem for underwater sensor networks. In Proceedings of the OCEANS 2011 IEEE—Spain, Santander, Spain, 6–9 June 2011. [Google Scholar] [CrossRef]
- Zia, M.Y.I.; Otero, P.; Poncela, J. Design of a low-cost modem for short-range under-water acoustic communications. Wirel. Pers. Commun. 2018, 101, 375–390. [Google Scholar] [CrossRef]
- Pinto, D.; Viana, S.S.; Nacif, L.F.M.; Vieira, M.A.M.; Vieira, A.B.; Fernandes, A.O. HydroNode: A low cost, energy efficient, multi purpose node for underwater sensor networks. In Proceedings of the 37th Annual IEEE Conference on Local Computer Networks, Clearwater Beach, FL, USA, 22–25 October 2012. [Google Scholar]
- Siregar, S.; Sani, M.I.; Kurnia, M.M.; Hasbialloh, D. Low-cost communication system for explorer-class underwater remotely operated vehicle. TELKOMNIKA (Telecommun. Comput. Electron. Control.) 2019, 17, 593–600. [Google Scholar] [CrossRef]
- Ji, Z.; Fu, Y.; Li, J.; Zhao, Z.; Mai, W. Photoacoustic Communication from the Air to Underwater Based on Low-Cost Passive Relays. IEEE Commun. Mag. 2021, 59, 140–143. [Google Scholar] [CrossRef]
- Shang, G.-Y.; Feng, Z.-P.; Lian, L. A low-cost testbed of underwater mobile sensing network. J. Shanghai Jiaotong Univ. (Sci.) 2011, 16, 502–507. [Google Scholar] [CrossRef] [Green Version]
- Waseem, M.H.; Alamzeb, M.; Mustafa, B.; Malik, F.; Shakir, M.; Jhan, M.A. Design of a low-cost underwater wireless sensor network for water quality moni-toring. IETE J. Res. 2013, 59, 523–534. [Google Scholar] [CrossRef]
- Page, B.R.; Ziaeefard, S.; Pinar, A.J.; Mahmoudian, N. Highly Maneuverable Low-Cost Underwater Glider: Design and Development. IEEE Robot. Autom. Lett. 2016, 2, 344–349. [Google Scholar] [CrossRef]
- Abdillah, A.F.; Berlian, M.H.; Panduman, Y.Y.F.; Akbar, M.A.W.; Afifah, M.A.; Tjahjono, A.; Sukaridhoto, S.; Sasaki, S. Design and development of low cost coral monitoring system for shallow water based on internet of underwater things. J. Telecommun. Electron. Comput. Eng. (JTEC) 2017, 9, 97–101. [Google Scholar]
- ISO/IEC 30140-1. Information Technology—Underwater Acoustic Sensor Network (UWASN)—Part 1: Overview and Requirements. Available online: https://www.iso.org/standard/53260.html (accessed on 28 October 2021).
- ISO/IEC 30142. Internet of Things (IoT)—Underwater Acoustic Sensor Network (UWASN)—Network Management System Overview and Requirements. Available online: https://www.iso.org/standard/53262.html (accessed on 28 October 2021).
- Islam, J.; Ho, M.; Sattar, J. Dynamic Reconfiguration of Mission Parameters in Underwater Human-Robot Collaboration. In Proceedings of the 2018 IEEE International Conference on Robotics and Automation (ICRA), Brisbane, QLD, Australia, 21–25 May 2018; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Furno, L.; Blanke, M.; Galeazzi, R.; Christensen, D.J. Self-reconfiguration of modular underwater robots using an energy heuristic. In Proceedings of the 2017 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Vancouver, BC, Canada, 24–28 September 2017; pp. 6277–6284. [Google Scholar] [CrossRef] [Green Version]
- Qiao, G.; Liu, S.; Sun, Z.; Zhou, F. Full-duplex, multi-user and parameter reconfigurable under-water acoustic communication modem. In Proceedings of the 2013 OCEANS—San Diego, San Diego, CA, USA, 23–27 September 2013; pp. 1–8. [Google Scholar] [CrossRef]
- Martin, R.; Rajasekaran, S. Data centric approach to analyzing security threats in Underwater Sensor Networks. In Proceedings of the OCEANS 2016 MTS/IEEE Monterey, Monterey, CA, USA, 19–23 September 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Dong, Q.; Ai, X.; Cao, G.; Zhang, Y.; Wang, X. Study on risk assessment of water security of drought periods based on entropy weight methods. Kybernetes 2010, 39, 864–870. [Google Scholar] [CrossRef]
- Misra, S.; Dash, S.; Khatua, M.; Vasilakos, A.; Obaidat, M. Jamming in underwater sensor networks: Detection and mitigation. IET Commun. 2012, 6, 2178–2188. [Google Scholar] [CrossRef]
- Bagali, S.; Sundaraguru, R. Efficient channel access model for detecting reactive jamming for underwater wireless sensor net-work. In Proceedings of the 2019 International Conference on Wireless Communications Signal Processing and Networking (WiSPNET), Chennai, India, 21–23 March 2019. [Google Scholar]
- Xiao, L.; Li, Q.; Chen, T.; Cheng, E.; Dai, H. Jamming games in underwater sensor networks with reinforcement learning. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015. [Google Scholar]
- Osanaiye, O.; Alfa, A.S.; Hancke, G.P. A Statistical Approach to Detect Jamming Attacks in Wireless Sensor Networks. Sensors 2018, 18, 1691. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Coutinho, R.W.L.; Boukerche, A.; Vieira, L.F.M.; Loureiro, A.A.F. GEDAR: Geographic and opportunistic routing protocol with Depth Adjustment for mobile underwater sensor networks. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 251–256. [Google Scholar] [CrossRef]
- Raj, P.N.; Swadas, P.B. DPRAODV: A Dynamic Learning System against Black HoleAttack in AODV based MANET. IJCSI Int. J. Comput. Sci. Issues 2009, 2, 54–59. [Google Scholar]
- Tamilselvan, L.; Sankaranarayanan, V. Prevention of Co-operative Black Hole Attack in MANET. J. Netw. 2008, 3, 13–20. [Google Scholar] [CrossRef] [Green Version]
- Kalkha, H.; Satori, H.; Satori, K. Preventing Black Hole Attack in Wireless Sensor Network Using HMM. Procedia Comput. Sci. 2019, 148, 552–561. [Google Scholar] [CrossRef]
- Premkumardeepak, S.; Krishnan, M.M. Intelligent sensor based monitoring system for underwater pollution. In Proceedings of the 2017 International Conference on IoT and Application (ICIOT), Nagapattinam, India, 19–20 May 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Bayrakdar, M.E. Cost Effective Smart System for Water Pollution Control with Underwater Wireless Sensor Networks: A Simulation Study. Comput. Syst. Sci. Eng. 2020, 35, 283–292. [Google Scholar] [CrossRef]
- Hafeez, S.; Wong, M.S.; Abbas, S.; Kwok, C.Y.T.; Nichol, J.; Lee, K.H.; Tang, D.; Pun, L. Detection and Monitoring of Marine Pollution Using Remote Sensing Technologies. In Monitoring of Marine Pollution; 2019; Available online: https://doi.org/10.5772/intechopen.81657 (accessed on 6 December 2021).
- Cario, G.; Casavola, A.; Gjanci, P.; Lupia, M.; Petrioli, C.; Spaccini, D. Long lasting underwater wireless sensors network for water quality monitoring in fish farms. In Proceedings of the OCEANS 2017, Aberdeen, UK, 19–22 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Adu-Manu, K.S.; Tapparello, C.; Heinzelman, W.; Katsriku, F.A.; Abdulai, J. Water quality monitoring using wireless sensor networks: Current trends and future research directions. ACM Trans. Sens. Netw. (TOSN) 2017, 13, 1–41. [Google Scholar] [CrossRef] [Green Version]
- de Lima, R.L.P.; Boogaard, F.C.; de Graaf-van Dinther, R.E. Innovative water quality and ecology monitoring using underwater unmanned vehicles: Field applications, challenges and feedback from water managers. Water 2020, 12, 1196. [Google Scholar] [CrossRef] [Green Version]
- Chen, Y.; Han, D. Water quality monitoring in smart city: A pilot project. Autom. Constr. 2018, 89, 307–316. [Google Scholar] [CrossRef] [Green Version]
- Yunbing, H.U. Research on water quality monitoring by means of sensor network. J. Theor. Appl. Inf. Technol. 2013, 49, 126–130. [Google Scholar]
- Jindal, H.; Saxena, S.; Kasana, S.S. A sustainable multi-parametric sensors network topology for river water quality monitoring. Wirel. Netw. 2018, 24, 3241–3265. [Google Scholar] [CrossRef]
- Pappu, S.; Vudatha, P.; Niharika, A.V.; Karthick, T.; Sankaranarayannan, S. Intelligent IoT based water quality monitoring system. Int. J. Appl. Eng. Res. 2017, 12, 5447–5454. [Google Scholar]
- Li, D.; Liu, S. Water Quality Monitoring and Management: Basis, Technology and Case Studies; Academic Press: Cambridge, MA, USA, 2018. [Google Scholar]
- Jo, W.; Hoashi, Y.; Aguilar, L.L.P.; Postigo-Malaga, M.; Garcia-Bravo, J.M.; Min, B.-C. A low-cost and small USV platform for water quality monitoring. HardwareX 2019, 6, 1–13. [Google Scholar] [CrossRef]
- Xu, L.; Gu, H.; Li, C.; Shi, A.; Shen, J. System Design of Water Quality Monitoring Robot with Automatic Navigation and Self-test Capability. Int. J. Control. Autom. 2013, 6, 67–82. [Google Scholar] [CrossRef]
- Gupta, S.; Kohli, M.; Kumar, R.; Bandral, S. IoT Based Underwater Robot for Water Quality Monitoring. In Proceedings of the IOP Conference Series: Materials Science and Engineering, International Conference on Integrated Interdisciplinary Innovations in Engineering (ICIIIE 2020), Panjab University, Chandigarh, India, 28–30 August 2020; Volume 1033. [Google Scholar]
- Lu, H.; Zhang, Y.; Li, Y.; Zhou, Q.; Tadoh, R.; Uemura, T.; Kim, H.; Serikawa, S. Depth map reconstruction for underwater Kinect camera using inpainting and local image mode filtering. IEEE Access 2017, 5, 7115–7122. [Google Scholar] [CrossRef]
- Si, J.; Xiong, W.; Zhong, D.; Yan, A.; Wang, P.; Liu, Z. Piezoelectric-based damage-depth monitoring method for underwater energy-relief blasting technique. J. Civ. Struct. Health Monit. 2021, 11, 251–264. [Google Scholar] [CrossRef]
- Tanakitkorn, K.; Wilson, P.A.; Turnock, S.R.; Phillips, A.B. Depth control for an over-actuated, hover-capable autonomous underwater vehicle with experimental verification. Mechatronics 2017, 41, 67–81. [Google Scholar] [CrossRef] [Green Version]
- Yokogawa, Leading Provider of Industrial Automation, Developed Sea Water Surface Temperature Monitoring. 2021. Available online: https://www.yokogawa.com/library/resources/application-notes/sea-water-surface-temperature-monitoring/ (accessed on 28 October 2021).
- Schuster, A.; Castagna, O.; Schmid, B.; Cibis, T.; Sieber, A.; GmbH, S. Underwater monitoring system for body temperature and ECG recordings. Underw. Technol. 2017, 34, 135–139. [Google Scholar] [CrossRef]
- Isaak, D.J.; Horan, D.L.; Wollrab, S.P. A simple protocol using underwater epoxy to install annual temperature monitoring sites in rivers and streams. Gen. Tech. Rep. 2013, 314, 1–28. [Google Scholar] [CrossRef] [Green Version]
- Puntsri, K.; Yindeemak, U.; Bubpawan, T. pH and temperature underwater monitoring with application using visible light communications. In Proceedings of the Fourth International Conference on Photonics Solutions (ICPS2019), Chiang Mai, Thailand, 20–22 November 2019. [Google Scholar] [CrossRef]
- Johansen, J.E. Underwater Optical Sensorbot for In Situ pH Monitoring. Master Thesis, Arizona State University, Tempe, AZ, USA, 2012. [Google Scholar]
- Mathias, R.; Ambalgi, A.P.; Upadhyaya, A.M. Grating based pressure monitoring system for subaquatic application. Int. J. Inf. Technol. 2018, 10, 551–557. [Google Scholar] [CrossRef]
- Costa, C.; Loy, A.; Cataudella, S.; Davis, D.; Scardi, M. Extracting fish size using dual underwater cameras. Aquac. Eng. 2006, 35, 218–227. [Google Scholar] [CrossRef]
- Yoo, S.-H.; Ju, Y.-T.; Kim, J.-S.; Kim, E.-K. Design and Development of Underwater Drone for Fish Farm Growth Environment Management. J. Korea Inst. Electron. Commun. Sci. 2020, 15, 959–966. [Google Scholar]
- Shortis, M.R.; Ravanbakskh, M.; Shaifat, F.; Harvey, E.S.; Mian, A.; Seager, J.W.; Culverhouse, P.F.; Cline, D.E.; Edigington, D.R. A review of techniques for the identification and measurement of fish in underwater stereo-video image sequences. In Proceedings of the Videometrics, Range Imaging, and Applications XII; and Automated Visual Inspection, Munich, Germany, 13–16 May 2013. [Google Scholar]
- Ohrem, S.J.; Kelasidi, E.; Bloecher, N. Analysis of a novel autonomous underwater robot for bio-fouling prevention and inspection in fish farms. In Proceedings of the 2020 28th Mediterranean Conference on Control and Automation (MED), Saint-Raphaël, France, 15–18 September 2020. [Google Scholar]
- Garcia, M.; Sendra, S.; Lloret, G.; Lloret, J. Monitoring and control sensor system for fish feeding in marine fish farms. IET Commun. 2011, 5, 1682–1690. [Google Scholar] [CrossRef]
- Magsumbol, J.-A.V.; Almero, V.J.; Rosales, M.; Bandala, A.A.; Dadios, E.P. A Fuzzy Logic Approach for Fish Growth Assessment. In Proceedings of the 2019 IEEE 11th International Conference on Humanoid, Nanotechnology, Information Technology, Communication and Control, Environment, and Management (HNICEM), Laoag, Philippines, 29 November–1 December 2019. [Google Scholar]
- Lloret, J.; Garcia-Pineda, M.; Sendra, S.; Lloret, G. An underwater wireless group-based sensor network for marine fish farms sustainability monitoring. Telecommun. Syst. 2015, 60, 67–84. [Google Scholar] [CrossRef]
- Delphin Raj, K.M.; Shin, S.-Y.; NAMGUNG, J.I.; Park, S.-H. The RIL based approach for predicting the growth of pearl spot fish using-UWAC. J. Inst. Electron. Inf. Eng. 2018, 55, 32–40. [Google Scholar]
- Marini, S.; Fanelli, E.; Sbragaglia, V.; Azzurro, E.; Fernandez, J.D.R.; Aguzzi, J. Tracking Fish Abundance by Underwater Image Recognition. Sci. Rep. 2018, 8, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Islam, N.Z.M.; Aziz, N.M.A.N.A.; Abu, N.; Shualdi, W.; Isha, K.M.; Kong, T.C.; Hai, T.C.; Mahat, M.M. Underwater Fish Attraction LED Lamp (UFAL) for Improving Aquaculture Productivity. J. Adv. Res. Appl. Mech. 2019, 53, 8–14. [Google Scholar]
- Ling, Y.J.; Lau, P.Y. Fish monitoring in complex environment. In Proceedings of the International Workshop on Advanced Image Technology (IWAIT), Singapore, 6–9 January 2019; Volume 11049. [Google Scholar]
- Dunn, M.; Dalland, K. Observing behaviour and growth using the Simrad FCM 160 fish cage monitoring system. In Fish Farming Technology; CRC Press: Boca Raton, FL, USA, 2020; pp. 269–274. [Google Scholar] [CrossRef]
- Almero, V.J.D.; Concepcion, R.S.; Sybingco, E.; Dadios, E.P. An Image Classifier for Underwater Fish Detection using Classification Tree-Artificial Neural Network Hybrid. In Proceedings of the 2020 RIVF International Conference on Computing and Communication Technologies (RIVF), Ho Chi Minh City, Vietnam, 14–15 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Boudhane, M.; Nsiri, B. Fish tracking using acoustical and optical data fusion in underwater environment. In Proceedings of the International Conference on Watermarking and Image Processing, Paris, France, 6–8 September 2017. [Google Scholar]
- Føre, M.; Frank, K.; Norton, T.; Svendsen, E.; Alfredsen, J.A.; Dempster, T.; Eguiraun, H.; Watson, W.; Stahl, A.; Sunde, L.M.; et al. Precision fish farming: A new framework to improve production in aquaculture. Biosyst. Eng. 2018, 173, 176–193. [Google Scholar] [CrossRef]
- Terayama, K.; Shin, K.; Mizuno, K.; Tsuda, K. Integration of sonar and optical camera images using deep neural network for fish monitoring. Aquac. Eng. 2019, 86. [Google Scholar] [CrossRef]
- Zhou, C.; Xu, D.; Lin, K.; Sun, C.; Yang, X. Intelligent feeding control methods in aquaculture with an emphasis on fish: A review. Rev. Aquac. 2017, 10, 975–993. [Google Scholar] [CrossRef]
- Karimanzira, D.; Jacobi, M.; Pfuetzenreuter, T.; Rauschenbach, T.; Eichhorn, M.; Taubert, R.; Ament, C. First testing of an AUV mission planning and guidance system for water quality monitoring and fish behavior observation in net cage fish farming. Inf. Process. Agric. 2014, 1, 131–140. [Google Scholar] [CrossRef]
- Torisawa, S.; Kadota, M.; Komeyama, K.; Suzuki, K.; Takagi, T. A digital stereo-video camera system for three-dimensional monitoring of free-swimming Pacific bluefin tuna, Thunnus orientalis, cultured in a net cage. Aquat. Living Resour. 2011, 24, 107–112. [Google Scholar] [CrossRef] [Green Version]
- Shi, C.; Wang, Q.; He, X.; Zhang, X.; Li, D. An automatic method of fish length estimation using underwater stereo system based on LabVIEW. Comput. Electron. Agric. 2020, 173, 105419. [Google Scholar] [CrossRef]
- da Silva Vale, R.T.; Ueda, E.K.; Takimoto, R.Y.; de Castro Martins, T. Fish Volume Monitoring Using Stereo Vision for Fish Farms. IFAC-Pap. 2020, 53, 15824–15828. [Google Scholar] [CrossRef]
- Harasti, D.; Lee, K.A.; Laird, R.; Bradford, R.; Bruce, B. Use of stereo baited remote underwater video systems to estimate the presence and size of white sharks (Carcharodon carcharias). Mar. Freshw. Res. 2017, 68, 1391. [Google Scholar] [CrossRef]
- Delgado, J.P.; Staniforth, M. Underwater archaeology. Archaeology 2010, I, 227. [Google Scholar]
- Castro, F. c Hunters, and the UNESCO Convention on the Protection of the Underwater Cultural Heritage: A Per-sonal Viewpoint. Odyssey Pap. 2010, 13, 7–9. [Google Scholar]
- Bass, G.F. The development of maritime archaeology. In The Oxford Handbook of Maritime Archaeology; Oxford University Press: Oxford, UK, 2011; pp. 3–22. [Google Scholar]
- Babits, L.E.; Van Tilburg, H. (Eds.) Maritime Archaeology: A Reader of Substantive and Theoretical Contributions; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Teixeira, F.C.; Pascoal, A. Magnetic navigation and tracking of underwater vehicles. IFAC Proc. Vol. 2013, 46, 239–244. [Google Scholar] [CrossRef] [Green Version]
- Ghafoor, H.; Noh, Y. An Overview of Next-Generation Underwater Target Detection and Tracking: An Integrated Underwater Architecture. IEEE Access 2019, 7, 98841–98853. [Google Scholar] [CrossRef]
- Yao, F.; Yang, C.; Zhang, M.; Wang, Y. Optimization of the Energy Consumption of Depth Tracking Control Based on Model Predictive Control for Autonomous Underwater Vehicles. Sensors 2019, 19, 162. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sheng, M.; Tang, S.; Qin, H.; Wan, L. Clustering Cloud-Like Model-Based Targets Underwater Tracking for AUVs. Sensors 2019, 19, 370. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bechlioulis, C.P.; Karras, G.C.; Heshmati-Alamdari, S.; Kyriakopoulos, K.J. Trajectory tracking with prescribed performance for underactuated underwater vehicles under model uncertainties and external disturbances. IEEE Trans. Control. Syst. Technol. 2016, 25, 429–440. [Google Scholar] [CrossRef]
- Wang, Z.; Wang, J.; Fan, R. An Underwater Single Target Tracking Method Using SiamRPN++ Based on Inverted Residual Bottleneck Block. IEEE Access 2021, 9, 25148–25157. [Google Scholar] [CrossRef]
- Isbitiren, G.; Akan, O.B. Three-Dimensional Underwater Target Tracking With Acoustic Sensor Networks. IEEE Trans. Veh. Technol. 2011, 60, 3897–3906. [Google Scholar] [CrossRef]
- Kim, J.H.; Yoo, S.J. Adaptive Event-Triggered Control Strategy for Ensuring Predefined Three-Dimensional Tracking Performance of Uncertain Nonlinear Underactuated Underwater Vehicles. Mathematics 2021, 9, 137. [Google Scholar] [CrossRef]
- Myint, M.; Yonemori, K.; Yanou, A.; Minami, M.; Ishiyama, S. Visual-servo-based autonomous docking system for underwater vehicle using dual-eyes camera 3D-pose tracking. In Proceedings of the 2015 IEEE/SICE International Symposium on System Integration (SII), Nagoya, Japan, 11–13 December 2015. [Google Scholar] [CrossRef]
- Sawa, T.; Kassaya, T.; Hyakudome, T.; Yoshida, H. Natural resource exploration with sonar on underwater vehicle. In International Conference on Off-Shore Mechanics and Arctic Engineering; American Society of Mechanical Engineers: New York, NY, USA, 2012; Volume 44946. [Google Scholar]
- Moskwa, E.C. Exploring Place Attachment: An Underwater Perspective. Tour. Mar. Environ. 2012, 8, 33–46. [Google Scholar] [CrossRef]
- Katzschmann, R.K.; DelPreto, J.; MacCurdy, R.; Rus, D. Exploration of underwater life with an acoustically controlled soft robotic fish. Sci. Robot. 2018, 3. [Google Scholar] [CrossRef] [Green Version]
- Manderson, T.; Higuera, J.C.G.; Cheng, R.; Dudek, G. Vision-Based Autonomous Underwater Swimming in Dense Coral for Combined Collision Avoidance and Target Selection. In Proceedings of the 2018 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Madrid, Spain, 1–5 October 2018. [Google Scholar] [CrossRef]
- Girdhar, Y.; Dudek, G. Exploring underwater environments with curiosity. In Proceedings of the 2014 Canadian Conference on Computer and Robot Vision, Montreal, QC, Canada, 6–9 May 2014. [Google Scholar]
- Carrasco, S.A.; Bravo, M.; Avilés, E.; Ruiz, P.A.R.; Yori, A.; Hinojosa, I.A. Exploring overlooked components of remote South-east Pacific oceanic islands: Larval and macrobenthic assemblages in reef habitats with distinct underwater soundscapes. Aquat. Conserv. Mar. Freshw. Ecosyst. 2020, 31, 273–289. [Google Scholar] [CrossRef]
- Nocerino, E.; Neyer, F.; Gruen, A.; Troyer, M.; Menna, F.; Brooks, A.; Capra, A.; Castagnetti, C.; Rossi, P. Comparison of diver-operated underwater photogrammetric systems for coral reef monitoring. ISPRS—Int. Arch. Photogramm. Remote. Sens. Spat. Inf. Sci. 2019, XLII-2/W10, 143–150. [Google Scholar] [CrossRef] [Green Version]
- Armstrong, R.A.; Pizarro, O.; Roman, C. Underwater Robotic Technology for Imaging Mesophotic Coral Ecosystems. In Mesophotic Coral Ecosystems; Springer: Cham, Switzerland, 2019; pp. 973–988. [Google Scholar] [CrossRef]
- Yoshida, H.; Hyakudome, T.; Ishibashi, S.; Sawa, T.; Nakano, Y.; Ochi, H.; Watanabe, Y.; Nakatani, T.; Ota, Y.; Sugesawa, M. An autonomous underwater vehicle with a canard rudder for underwater minerals exploration. In Proceedings of the 2013 IEEE International Conference on Mechatronics and Automation, Takamatsu, Japan, 4–7 August 2013. [Google Scholar]
- Wakita, N.; Hirokawa, K.; Ichikawa, T.; Yamauchi, Y. Development of autonomous underwater vehicle (AUV) for exploring deep sea marine mineral resources. Mitsubishi Heavy Ind. Tech. Rev. 2010, 47, 73–80. [Google Scholar]
- Di Vito, D.; De Palma, D.; Simetti, E.; Indiveri, G.; Antonelli, G. Experimental validation of the modeling and control of a multibody underwater vehicle manipulator system for sea mining exploration. J. Field Robot. 2021, 38, 171–191. [Google Scholar] [CrossRef]
- Lopes, L.; Zajzon, N.; Bodo, B.; Henley, S.; Žibret, G.; Dizdarevic, T. UNEXMIN: Developing an autonomous underwater explorer for flooded mines. Energy Procedia 2017, 125, 41–49. [Google Scholar] [CrossRef]
- Ulvrova, M.; Paris, R.; Kelfoun, K.; Nomikou, P. Numerical simulations of tsunamis generated by underwater volcanic explosions at Karymskoye lake (Kamchatka, Russia) and Kolumbo volcano (Aegean Sea, Greece). Nat. Hazards Earth Syst. Sci. 2014, 14, 401–412. [Google Scholar] [CrossRef] [Green Version]
- Koba, M.; Yamamoto, A.; Ueno, T.; Yuhi, M. A numerical study on the influence of variation of underwater landslide shape on tsunami generation. In Proceedings of the 28th International Ocean and Polar Engineering Conference, Sapporo, Japan, 10–15 June 2018. [Google Scholar]
- Karan, P.P.; Suganuma, U. (Eds.) Japan after 3/11: Global Perspectives on the Earthquake, Tsunami, and Fukushima Meltdown; University Press of Kentucky: Lexington, KY, USA, 2016. [Google Scholar]
- Kumar, P.; Kumar, P.; Priyadarshini, P. Srija Underwater acoustic sensor network for early warning generation. In Proceedings of the 2012 Oceans, Hampton Roads, VA, USA, 14–19 October 2012. [Google Scholar] [CrossRef]
- Kim, D.S.; Hong, S.J.; Park, H.S. Analysis of evacuation system on tsunami disaster prevention in Korea. J. Coast. Res. 2013, 65, 974–979. [Google Scholar] [CrossRef]
- Karambas, T.V.; Hasiotis, T. A Study of Tsunamis Generated by Underwater Landslides in the Aegean Sea. In Proceedings of the Twenty-second International Offshore and Polar Engineering Conference, Rhodes, Greece, 17–22 June 2012. [Google Scholar]
- Hanzawa, M.; Matsumoto, A.; Tanaka, H. Stability of wave-dissipating concrete blocks of detached breakwaters against tsunami. Coast. Eng. Proc. 2012, 1. [Google Scholar] [CrossRef] [Green Version]
- Liao, B.; Zhang, W. Research on landslide stability under water level fluctuation of reservoir: Case of Hushantan landslide of a hydropower station on Yalong River. Yangtze River 2013, 44, 37–40. [Google Scholar]
- Wang, S.-x.; Chen, D.-b.; Shi, L.U.O. Research on engineering effect evaluation of landslide prevention system. Shanxi Archit. 2012, 2012, 23. [Google Scholar]
- 196. Zahari, M.N.B.M.; Nazif, M. Structural Landslide Mitigation Technique. 2010. Available online: http://www.malrep.uum.edu.my/rep/Record/my-utp-utpedia.1022/Description#tabnav (accessed on 6 December 2021).
- Yang, J.; Jian, W.; Yang, H.; Zhang, J. Dynamic variation rule of phreatic line in Huangtupo landslide in Three Gorges reservoir area. Rock Soil Mech. 2012, 33, 853–858. [Google Scholar]
- Kozlova, T.V.; Cherkez, E.A.; Medinets, V.I.; Gazyetov, Y.I.; Snihirov, S.M.; Medinets, S.V. Study of structural-tectonic discreteness of abrasion-landslide bench in a segment of Odesa coastline. In Geoinformatics: Theoretical and Applied Aspects 2020; European Association of Geoscientists & Engineers: Houten, The Netherlands, 2020; Volume 2020, pp. 1–5. [Google Scholar] [CrossRef]
- Chuanzhi, W.; Lixin, W. Forming Mechanism and Stability Analysis of Diaozhon Dam Landslides in Zhong County of Chongqing. Urban. Roads Bridges Flood Control. 2015, 8. Available online: https://en.cnki.com.cn/Article_en/CJFDTotal-CSDQ201508111.htm (accessed on 6 December 2021).
- Zhang, Y.; Shi, S.-W.; Song, J.; Cheng, Y.-J. Evaluation on Effect for the Prevention and Control Against the Landslide Disasters in the Three Gorges Reservoir Area. In Landslide Science for a Safer Geoenvironment; Springer: Cham, Switzerland, 2014; pp. 407–414. [Google Scholar] [CrossRef]
- Marra, G.; Clivati, C.; Luckett, R.; Tampellini, A.; Kronjäger, J.; Wright, L.; Mura, A.; Levi, F.; Robinson, S.; Xuereb, A.; et al. Ultrastable laser interferometry for earthquake detection with terrestrial and submarine cables. Science 2018, 361, 486–490. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lior, I.; Sladen, A.; Rivet, D.; Ampuero, J.; Hello, Y.; Becerril, C.; Martins, H.F.; Lamare, P.; Jestin, C.; Tsagkli, S.; et al. On the Detection Capabilities of Underwater Distributed Acoustic Sensing. J. Geophys. Res. Solid Earth 2021, 126. [Google Scholar] [CrossRef]
- Shakila, R.; Paramasivan, B. Performance Analysis of Submarine Detection in Underwater Wireless Sensor Networks for Naval Application. Microprocess. Microsyst. 2020, 103293. [Google Scholar] [CrossRef]
- Chen, B.; Li, R.; Bai, W.; Li, J.; Zhou, Y.; Guo, R. Application analysis of autonomous underwater vehicle in submarine cable detection operation. In Proceedings of the 2018 International Conference on Robotics, Control and Automation Engineering, Beijing, China, 26–28 December 2018. [Google Scholar]
- Williams, D.P. On optimal AUV track-spacing for underwater mine detection. In Proceedings of the 2010 IEEE International Conference on Robotics and Automation, Anchorage, AK, USA, 3–7 May 2010. [Google Scholar]
- Khaledi, S.; Mann, H.; Perkovich, J.; Zayed, S. Design of an underwater mine detection system. In Proceedings of the 2014 Systems and Information Engineering Design Symposium (SIEDS), Charlottesville, VA, USA, 25 April 2014. [Google Scholar]
- Vinutha, K.V.; Vinutha, K.; Yuvaraja, T. Under water mine detection using SONAR. J. Comput. Theor. Nanosci. 2018, 15, 2150–2152. [Google Scholar] [CrossRef]
- Sawas, J.; Petillot, Y.; Pailhas, Y. Cascade of boosted classifiers for rapid detection of underwater objects. In Proceedings of the European Conference on Underwater Acoustics, Istambul, Turkey, 5–9 July 2010; Volume 164. [Google Scholar]
- Artusi, E.; Chaillan, F. Automatic recognition of underwater acoustic signature for naval applications. In Proceedings of the 1st Maritime Situational Awareness Workshop MSAW 2019, Lerici, Italy, October 2019. [Google Scholar]
- Ferri, G.; Munafò, A.; Tesei, A.; Braca, P.; Meyer, F.; Pelekanakis, K.; Petroccia, R.; Alves, J.; Strode, C.; LePage, K. Cooperative robotic networks for underwater surveillance: An overview. IET Radar Sonar Navig. 2017, 11, 1740–1761. [Google Scholar] [CrossRef]
- Macias, E.; Suarez, A.; Chiti, F.; Sacco, A.; Fantacci, R. A Hierarchical Communication Architecture for Oceanic Surveillance Applications. Sensors 2011, 11, 11343–11356. [Google Scholar] [CrossRef] [Green Version]
- Aversa, M.; Lapinsky, S.E. Lung physiology at play: Hemoptysis due to underwater hockey. Respir. Med. Case Rep. 2014, 11, 16–17. [Google Scholar] [CrossRef] [Green Version]
- Vladimirovna, R.E.; Anatolevich, T.I.; Nikolaevna, L.A.; Nikolaevna, B.G. The study of the heart rate ib athleters engaged in underwater sports, depending on the specialization. Eur. J. Mol. Clin. Med. 2021, 8, 1492–1498. [Google Scholar]
- Battal, O.; Balcioglu, T.; Duru, A.D. Analysis of gaze characteristics with eye tracking system during repeated breath holding exercises in underwater hockey elite athletes. In Proceedings of the 2016 20th National Biomedical Engineering Meeting (BIYOMUT), Izmir, Turkey, 3–5 November 2016. [Google Scholar] [CrossRef]
- Ozen, S. Correlation between Agility and Speed in Elite Underwater Hockey Players. Int. J. Appl. Exerc. Physiol. 2020, 9, 86–91. [Google Scholar]
- Musa, G.; Seng, W.T.; Thirumoorthi, T.; Abessi, M. The influence of scuba divers’ personality, experience, and demographic profile on their under-water behavior. Tour. Mar. Environ. 2011, 7, 1–14. [Google Scholar] [CrossRef] [Green Version]
- Ong, T.F.; Musa, G. Examining the influences of experience, personality and attitude on SCUBA divers’ underwater behaviour: A structural equation model. Tour. Manag. 2012, 33, 1521–1534. [Google Scholar] [CrossRef]
- Hegrenaes, Ø.; Hallingstad, O. Model-Aided INS with Sea Current Estimation for Robust Underwater Navigation. IEEE J. Ocean. Eng. 2011, 36, 316–337. [Google Scholar] [CrossRef]
- Qin, H.-D.; Yu, X.; Zhu, Z.-B.; Deng, Z.-C. An expectation-maximization based single-beacon underwater navigation method with unknown ESV. Neurocomputing 2019, 378, 295–303. [Google Scholar] [CrossRef]
- Boyer, F.; Lebastard, V.; Chevallereau, C.; Mintchev, S.; Stefanini, C. Underwater navigation based on passive electric sense: New perspectives for underwater docking. Int. J. Robot. Res. 2015, 34, 1228–1250. [Google Scholar] [CrossRef] [Green Version]
- Hernández, J.D.; Istenič, K.; Gracias, N.; Palomeras, N.; Campos, R.; Vidal, E.; García, R.; Carreras, M. Autonomous underwater navigation and optical mapping in unknown natural environments. Sensors 2016, 16, 1174. [Google Scholar] [CrossRef] [Green Version]
- Kim, T.; Kim, J.; Byun, S.-W. A Comparison of Nonlinear Filter Algorithms for Terrain-referenced Underwater Navigation. Int. J. Control. Autom. Syst. 2018, 16, 2977–2989. [Google Scholar] [CrossRef]
- Yuan, X.; Martínez-Ortega, J.-F.; Fernández, J.A.S.; Eckert, M. AEKF-SLAM: A New Algorithm for Robotic Underwater Navigation. Sensors 2017, 17, 1174. [Google Scholar] [CrossRef] [Green Version]
- Davari, N.; Gholami, A. An asynchronous adaptive direct Kalman filter algorithm to improve underwa-ter navigation system performance. IEEE Sens. J. 2016, 17, 1061–1068. [Google Scholar] [CrossRef]
- Manderson, T.; Higuera, J.C.G.; Wapnick, S.; Tremblay, J.; Shkurti, F.; Meger, D.; Dudek, G. Vision-based goal-conditioned policies for underwater navigation in the presence of obstacles. arXiv 2020, arXiv:2006.16235. [Google Scholar]
- Bahr, A.; Leonard, J.J.; Martinoli, A. Dynamic positioning of beacon vehicles for cooperative underwater navigation. In Proceedings of the 2012 IEEE/RSJ International Conference on Intelligent Robots and Systems, Vilamoura-Algarve, Portugal, 7–12 October 2012. [Google Scholar]
- Ullah, I.; Liu, Y.; Su, X.; Kim, P. Efficient and Accurate Target Localization in Underwater Environment. IEEE Access 2019, 7, 101415–101426. [Google Scholar] [CrossRef]
- Waldmeyer, M.; Tan, H.-P.; Seah, W.K.G. Multi-stage AUV-aided localization for underwater wireless sensor networks. In Proceedings of the 2011 IEEE Workshops of International Conference on Advanced Information Networking and Applications, Biopolis, Singapore, 22–25 March 2011. [Google Scholar]
- Callmer, J.; Skoglund, M.; Gustafsson, F. Silent localization of underwater sensors using magnetometers. Eurasip J. Adv. Signal Process. 2010, 2010, 1–8. [Google Scholar] [CrossRef] [Green Version]
- Li, Z.; Dosso, S.E.; Sun, D. Motion-Compensated Acoustic Localization for Underwater Vehicles. IEEE J. Ocean. Eng. 2016, 41, 840–851. [Google Scholar] [CrossRef]
- Pinheiro, B.C.; Moreno, U.F.; de Sousa, J.T.B.; Rodriguez, O.C. Kernel-Function-Based Models for Acoustic Localization of Underwater Vehicles. IEEE J. Ocean. Eng. 2016, 42, 603–618. [Google Scholar] [CrossRef]
- Zheng, C.; Sun, D.; Cai, L.; Li, X. Mobile Node Localization in Underwater Wireless Networks. IEEE Access 2018, 6, 17232–17244. [Google Scholar] [CrossRef]
- Yan, J.; Xu, Z.; Wan, Y.; Chen, C.; Luo, X. Consensus estimation-based target localization in underwater acoustic sensor networks. Int. J. Robust Nonlinear Control. 2016, 27, 1607–1627. [Google Scholar] [CrossRef]
- Chang, S.; Li, Y.; He, Y.; Wang, H. Target Localization in Underwater Acoustic Sensor Networks Using RSS Measurements. Appl. Sci. 2018, 8, 225. [Google Scholar] [CrossRef] [Green Version]
- Gong, Z.; Li, C.; Jiang, F.; Zheng, J. AUV-Aided Localization of Underwater Acoustic Devices Based on Doppler Shift Measurements. IEEE Trans. Wirel. Commun. 2020, 19, 2226–2239. [Google Scholar] [CrossRef]
- Zhang, B.; Wang, H.; Zheng, L.; Wu, J.; Zhuang, Z. Joint synchronization and localization for underwater sensor networks considering stratification effect. IEEE Access 2017, 5, 26932–26943. [Google Scholar] [CrossRef]
- Burguera, A.; Bonin-Font, F.; Oliver, G. Trajectory-based visual localization in underwater surveying missions. Sensors 2015, 15, 1708–1735. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, T.L.N.; Shin, Y. An efficient RSS localization for underwater wireless sensor networks. Sensors 2019, 19, 3105. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yan, J.; Xu, Z.; Luo, X.; Chen, C.; Guan, X. Feedback-Based Target Localization in Underwater Sensor Networks: A Multisensor Fusion Approach. IEEE Trans. Signal. Inf. Process. Over Netw. 2018, 5, 168–180. [Google Scholar] [CrossRef]
- Tang, L.; Liu, M.; Wang, K.-C.; Huang, Y.; Yang, F.; Zhang, D. Study of path loss and data transmission error of IEEE 802.15.4 compliant wireless sensors in small-scale manufacturing environments. Int. J. Adv. Manuf. Technol. 2012, 63, 659–669. [Google Scholar] [CrossRef]
- Zhang, Y.; Negahdaripour, S.; Li, Q. Error-resilient coding for underwater video transmission. In Proceedings of the OCEANS 2016 MTS/IEEE Monterey, Monterey, CA, USA, 19–23 September 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Esmaiel, H.; Qasem, Z.A.H.; Sun, H.; Wang, J.; Junejo, N.U.R. Underwater Image Transmission Using Spatial Modulation Unequal Error Protection for Internet of Underwater Things. Sensors 2019, 19, 5271. [Google Scholar] [CrossRef] [Green Version]
- Esmaiel, H.; Jiang, D. Optimum Bit Rate for Image Transmission over Underwater Acoustic Channel. J. Electr. Electron. Eng. 2014, 2, 64. [Google Scholar] [CrossRef] [Green Version]
- El-Banna, A.A.A.; Wu, K.; ElHalawany, B.M. Opportunistic cooperative transmission for un-derwater communication based on the Water’s key physical variables. IEEE Sens. J. 2019, 20, 2792–2802. [Google Scholar] [CrossRef]
- Diamant, R.; Lampe, L. Adaptive Error-Correction Coding Scheme for Underwater Acoustic Communication Networks. IEEE J. Ocean. Eng. 2014, 40, 104–114. [Google Scholar] [CrossRef]
- Ilyas, N.; Alghamdi, T.A.; Farooq, M.N.; Mehboob, B.; Sadiq, A.H.; Qasim, U.; Khan, Z.A.; Javaid, N. AEDG: AUV-aided efficient data gathering routing protocol for underwater wireless sensor networks. Procedia Comput. Sci. 2015, 52, 568–575. [Google Scholar] [CrossRef] [Green Version]
- Wei, X.; Liu, Y.; Gao, S.; Wang, X.; Yue, H. An RNN-Based Delay-Guaranteed Monitoring Framework in Underwater Wireless Sensor Networks. IEEE Access 2019, 7, 25959–25971. [Google Scholar] [CrossRef]
- Domingo, M.C. A Distributed Energy-Aware Routing Protocol for Underwater Wireless Sensor Networks. Wirel. Pers. Commun. 2009, 57, 607–627. [Google Scholar] [CrossRef] [Green Version]
- Sher, A.; Khan, A.; Javaid, N.; Ahmed, S.H.; Aalsalem, M.Y.; Khan, W.Z. Void hole avoidance for reliable data delivery in IoT enabled underwater wireless sensor networks. Sensors 2018, 18, 3271. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ilyas, N.; Akbar, M.; Ullah, R.; Khalid, M.; Arif, A.; Hafeez, A.; Qasim, U.; Khan, Z.A.; Javaid, N. SEDG: Scalable and Efficient Data Gathering Routing Protocol for Underwater WSNs. Procedia Comput. Sci. 2015, 52, 584–591. [Google Scholar] [CrossRef] [Green Version]
- Ruby, D.; Jeyachidra, J. Semaphore based data aggregation and similarity findings for underwater wireless sensor networks. Int. J. Grid High. Perform. Comput. (IJGHPC) 2019, 11, 59–76. [Google Scholar] [CrossRef]
- Akbar, M.; Javaid, N.; Khan, A.H.; Imran, M.; Shoaib, M.; Vasilakos, A. Efficient Data Gathering in 3D Linear Underwater Wireless Sensor Networks Using Sink Mobility. Sensors 2016, 16, 404. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Nasir, H.; Javaid, N.; Ashraf, H.; Manzoor, S.; Khan, Z.; Qasim, U.; Sher, M. CoDBR: Cooperative Depth Based Routing for Underwater Wireless Sensor Networks. In Proceedings of the 2014 Ninth International Conference on Broadband and Wireless Computing, Communication and Applications, Guangdong, China, 8–10 November 2014; pp. 52–57. [Google Scholar] [CrossRef]
- Ali, M.; Khan, A.; Aurangzeb, K.; Ali, I.; Mahmood, H.; Halider, S.I.; Bhatti, N. CoSIM-RPO: Cooperative routing with sink mobility for reliable and persistent operation in underwater acoustic wireless sensor networks. Sensors 2019, 19, 1101. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Javaid, N.; Ahmad, Z.; Sher, A.; Wadud, Z.; Khan, Z.A.; Ahmed, S.H. Fair energy management with void hole avoidance in intelligent heterogeneous underwater WSNs. J. Ambient. Intell. Humaniz. Comput. 2018, 10, 4225–4241. [Google Scholar] [CrossRef]
- Javaid, N.; Jafri, M.R.; Khan, Z.A.; Qasim, U.; Alghamdi, T.A.; Ali, M. iAMCTD: Improved Adaptive Mobility of Courier Nodes in Threshold-Optimized DBR Protocol for Underwater Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2014, 10. [Google Scholar] [CrossRef]
- Jiang, J.; Han, G.; Shu, L.; Chan, S.; Wang, K. A Trust Model Based on Cloud Theory in Underwater Acoustic Sensor Networks. IEEE Trans. Ind. Inform. 2015, 13, 342–350. [Google Scholar] [CrossRef]
- Tran-Dang, H.; Kim, D.-S. Channel-aware cooperative routing in underwater acoustic sensor networks. J. Commun. Netw. 2019, 21, 33–44. [Google Scholar] [CrossRef]
- Hsu, C.-C.; Liu, H.-H.; Gomez, J.L.G.; Chou, C.-F. Delay-Sensitive Opportunistic Routing for Underwater Sensor Networks. IEEE Sens. J. 2015, 15, 6584–6591. [Google Scholar] [CrossRef]
- Li, C.; Xu, Y.; Xu, C.; An, Z.; Diao, B.; Li, X. DTMAC: A Delay Tolerant MAC Protocol for Underwater Wireless Sensor Networks. IEEE Sens. J. 2015, 16, 4137–4146. [Google Scholar] [CrossRef]
- Tran-Dang, H.; Kim, D.-S. Channel-aware energy-efficient two-hop cooperative routing protocol for underwater acoustic sensor networks. IEEE Access 2019, 7, 63181–63194. [Google Scholar] [CrossRef]
- Li, J.; Toulgoat, M.; Zhou, Y.; Lamont, L. Logical Link Control and Channel Scheduling for Multichannel Underwater Sensor Networks. ICST Trans. Mob. Commun. Appl. 2012, 12. [Google Scholar] [CrossRef] [Green Version]
- Rahman, R.; Frater, M. Delay-tolerant networks (DTNs) for underwater communications. In Advances in Delay-Tolerant Networks (DTNs); Woodhead Publishing: Sawston, UK, 2015; pp. 81–103. [Google Scholar] [CrossRef]
- Behrje, U.; Isokeit, C.; Meyer, B.; Maehle, E. A Robust Acoustic-Based Communication Principle for the Navigation of an Underwater Robot Swarm. In Proceedings of the 2018 OCEANS-MTS/IEEE Kobe Techno-Oceans (OTO), Kobe, Japan, 28–31 May 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Rodríguez-Molina, J.; Bilbao, S.; Martínez, B.; Frasheri, M.; Cürüklü, B. An Optimized, Data Distribution Service-Based Solution for Reliable Data Exchange Among Autonomous Underwater Vehicles. Sensors 2017, 17, 1802. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chen, M.-T.; Shen, Y.-C.; Luis, J.; Chou, C.-F. Energy-efficient OR-based MAC protocol for underwater sensor networks. In Proceedings of the SENSORS, 2014 IEEE, Valencia, Spain, 2–5 November 2014; pp. 118–121. [Google Scholar] [CrossRef]
- Kim, Y.; Varzi, A.; Mariani, A.; Kim, G.; Kim, Y.; Passerini, S. Redox-Mediated Red-Phosphorous Semi-Liquid Anode Enabling Metal-Free Rechargeable Na-Seawater Batteries with High Energy Density. Adv. Energy Mater. 2021, 11, 2102061. [Google Scholar] [CrossRef]
- Cho, J.; Kim, M.W.; Kim, Y.; Park, J.-S.; Lee, D.-H.; Kim, Y.; Kim, J.J. Seawater Battery-Based Wireless Marine Buoy System With Battery Degradation Prediction and Multiple Power Optimization Capabilities. IEEE Access 2021, 9, 104104–104114. [Google Scholar] [CrossRef]
- Son, M.; Park, S.; Kim, N.; Angeles, A.T.; Kim, Y.; Cho, K.H. Simultaneous Energy Storage and Seawater Desalination using Rechargeable Seawater Battery: Feasibility and Future Directions. Adv. Sci. 2021, 8, 2101289. [Google Scholar] [CrossRef]
- Ateniese, G.; Capossele, A.; Gjanci, P.; Petrioli, C.; Spaccini, D. SecFUN: Security framework for underwater acoustic sensor networks. In Proceedings of the OCEANS 2015—Genova, Genova, Italy, 18–21 May 2015; pp. 1–9. [Google Scholar] [CrossRef]
- Li, H.; He, Y.; Cheng, X.; Zhu, H.; Sun, L. Security and privacy in localization for underwater sensor networks. IEEE Commun. Mag. 2015, 53, 56–62. [Google Scholar] [CrossRef]
- Han, G.; Jiang, J.; Shu, L.; Guizani, M. An Attack-Resistant Trust Model Based on Multidimensional Trust Metrics in Underwater Acoustic Sensor Network. IEEE Trans. Mob. Comput. 2015, 14, 2447–2459. [Google Scholar] [CrossRef]
- Su, Y.; Ma, S.; Zhang, H.; Jin, Z.; Fu, X. A Redeemable SVM-DS Fusion-Based Trust Management Mechanism for Underwater Acoustic Sensor Networks. IEEE Sens. J. 2021, 21, 26161–26174. [Google Scholar] [CrossRef]
- Dargahi, T.; Javadi, H.H.S.; Shafiei, H. Securing underwater sensor networks against routing attacks. Wirel. Pers. Commun. 2017, 96, 2585–2602. [Google Scholar] [CrossRef]
- Han, G.; He, Y.; Jiang, J.; Wang, N.; Guizani, M.; Ansere, J.A. A Synergetic Trust Model Based on SVM in Underwater Acoustic Sensor Networks. IEEE Trans. Veh. Technol. 2019, 68, 11239–11247. [Google Scholar] [CrossRef]
- Jiang, J.; Han, G.; Zhu, C.; Chan, S.; Rodrigues, J.J.P.C. A Trust Cloud Model for Underwater Wireless Sensor Networks. IEEE Commun. Mag. 2017, 55, 110–116. [Google Scholar] [CrossRef]
- Nie, D.; Sun, Z.; Qiao, G.; Liu, S.; Yin, Y. Kite-type passive acoustic detection system for underwater small targets. In Proceedings of the 2014 Oceans—St. John’s, St. John’s, NL, Canada, 14–19 September 2014. [Google Scholar] [CrossRef]
- Kozhaeva, K.V.; Mustafin, F.M.; Yakupova, D.E. Methods for calculating the longitudinal stability of the pipeline and security measures in the area of underwater crossing (Russian). Neftyanoe Khozyaystvo-Oil Ind. 2016, 2016, 102–104. [Google Scholar]
- Kim, H.; Lee, J.; Yi, O. Proposal of Piecewise Key Management Design Considering Capability of Underwater Communication Nodes. Adv. Sci. Lett. 2017, 23, 12729–12733. [Google Scholar] [CrossRef]
- Shuvo, M.D.; Firdaus, M.T. A Model for Underwater Security in Communication Using Secret Key Algorithm and Node Value; Department of Computer Science and Engineering, Diss. Brac University: Dhaka, Bangladesh, 2021. [Google Scholar]
- Lal, C.; Petroccia, R.; Pelekanakis, K.; Conti, M.; Alves, J. Toward the Development of Secure Underwater Acoustic Networks. IEEE J. Ocean. Eng. 2017, 42, 1075–1087. [Google Scholar] [CrossRef]
- Silarski, M.; Hunik, D.; Smolis, M.; Tadeja, S.; Moskal, P. Design of the SABAT System for Underwater Detection of Dangerous Substances. Acta Phys. Pol. B 2016, 47, 497. [Google Scholar] [CrossRef] [Green Version]
- Li, C.; Marzani, F.; Yang, F. Demodulation of Chaos Phase Modulation Spread Spectrum Signals Using Machine Learning Methods and Its Evaluation for Underwater Acoustic Communication. Sensors 2018, 18, 4217. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chen, Q. Application of the Vibration Fiber Optic Perimeter Alarm System Based on the GPRS in the Underwater Security. Electron. Sci. Technol. 2013, 7. Available online: https://en.cnki.com.cn/Article_en/CJFDTotal-DZKK201307011.htm (accessed on 6 December 2021).
- Arifeen, M.M.; Mamun, A.A.; Ahmed, T.; Kaiser, M.S.; Mahmud, M. A Blockchain-Based Scheme for Sybil Attack Detection in Underwater Wireless Sensor Networks. In Proceedings of International Conference on Trends in Computational and Cognitive Engineering; Springer: Singapore, 2021. [Google Scholar]
- Huynh, T.; Khatib, M.; Haick, H. Self-Healable Materials for Underwater Applications. Adv. Mater. Technol. 2019, 4, 1900081. [Google Scholar] [CrossRef]
- Elhanafi, A.; Macfarlane, G.; Fleming, A.; Leong, Z. Experimental and numerical investigations on the intact and damage survivability of a floating–moored oscillating water column device. Appl. Ocean. Res. 2017, 68, 276–292. [Google Scholar] [CrossRef]
- Xu, L.; Huang, Z.; Deng, Z.; Du, Z.; Sun, T.L.; Guo, Z.; Yue, K. A Transparent, Highly Stretchable, Solvent-Resistant, Recyclable Multifunctional Ionogel with Underwater Self-Healing and Adhesion for Reliable Strain Sensors. Adv. Mater. 2021, 2105306. [Google Scholar] [CrossRef]
- von Bleichert, P. Port Security: The Terrorist Naval Mine/Underwater Improvised Explosive Device Threat. Ph.D. Thesis, Public Policy and Administration, Walden University, Washington, DC, USA, 2015. [Google Scholar]
- Khatib, M.; Zohar, O.; Haick, H. Self-healing soft sensors: From material design to implementation. Adv. Mater. 2021, 11, 2004190. [Google Scholar] [CrossRef] [PubMed]
- Khatib, M.; Zohar, O.; Saliba, W.; Haick, H. A Multifunctional Electronic Skin Empowered with Damage Mapping and Autonomic Acceleration of Self-Healing in Designated Locations. Adv. Mater. 2020, 32, 2000246. [Google Scholar] [CrossRef]
- Lopez, A.B.; Vatanparvar, K.; Nath, A.P.D.; Yang, S.; Bhunia, S.; Al Faruque, M.A. A Security Perspective on Battery Systems of the Internet of Things. J. Hardw. Syst. Secur. 2017, 1, 188–199. [Google Scholar] [CrossRef]
- Yang, G.; Dai, L.; Wei, Z. Challenges, Threats, Security Issues and New Trends of Underwater Wireless Sensor Networks. Sensors 2018, 18, 3907. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Cong, Y.; Yang, G.; Wei, Z.; Zhou, W. Security in underwater sensor network. In Proceedings of the 2010 International Conference on Communications and Mobile Computing, Shenzhen, China, 12–14 April 2010; Volume 1. [Google Scholar]
- Lal, C.; Petroccia, R.; Conti, M.; Alves, J. Secure underwater acoustic networks: Current and future research directions. In Proceedings of the 2016 IEEE third underwater communications and networking conference (UComms), Lerici, Italy, 30 August–1 September 2016. [Google Scholar]
- Wang, Q.; Dai, H.-N.; Li, X.; Wang, H.; Xiao, H. On Modeling Eavesdropping Attacks in Underwater Acoustic Sensor Networks †. Sensors 2016, 16, 721. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Zuba, M.; Shi, Z.; Peng, Z.; Cui, J. Launching denial-of-service jamming attacks in underwater sensor networks. In Proceedings of the Sixth ACM International Workshop on Underwater Networks, Seattle, WA, USA, 1–2 December 2011. [Google Scholar]
- Domingo, M.C. Securing underwater wireless communication networks. IEEE Wirel. Commun. 2011, 18, 22–28. [Google Scholar] [CrossRef]
- Vasudevan, A.R. Security Challenges in NDN Based Underwater Wireless Sensor Networks: An Overview. In Proceedings of the 2nd International Conference on IoT, Social, Mobile, Analytics & Cloud in Computational Vision & Bio-Engineering (ISMAC-CVB 2020), Tirunelveli, India, 29–30 October 2020. [Google Scholar]
- Mohsan, S.A.H.; Naqvi, S.S.A.; Banoori, F.; Siddique, M.I.; Mehdi, M.M.; Bruce, F.N.O.; Mazinani, A. A Systematic Review Study on Research Challenges, Opportunities, Threats and Limitations in Underwater Wireless Sensor Networks (UWSNs). In Proceedings of the International Conference on Intelligent and Interactive Systems and Applications, Shanghai, China, 25–27 September 2020; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Jiang, H.F.; Xu, Y. Research Advances on Security Problems of Underwater Sensor Networks. Adv. Mater. Res. 2011, 317–319, 1002–1006. [Google Scholar] [CrossRef]
- Diamant, R.; Casari, P.; Tomasin, S. Cooperative authentication in underwater acoustic sensor networks. IEEE Trans. Wirel. Commun. 2018, 18, 954–968. [Google Scholar] [CrossRef] [Green Version]
- Xiao, L.; Sheng, G.; Wan, X.; Su, W.; Cheng, P. Learning-Based PHY-Layer Authentication for Underwater Sensor Networks. IEEE Commun. Lett. 2018, 23, 60–63. [Google Scholar] [CrossRef]
- Ibragimov, M.; Lee, J.-H.; Kalyani, M.; Namgung, J.-I.; Park, S.-H.; Yi, O.; Kim, C.H.; Lim, Y.-K. CCM-UW Security Modes for Low-band Underwater Acoustic Sensor Networks. Wirel. Pers. Commun. 2016, 89, 479–499. [Google Scholar] [CrossRef]
- Souza, E.; Wong, H.C.; Cunha, I.; Vieira, L.F.M.; Oliveira, L.B. End-to-end authentication in under-water sensor networks. In Proceedings of the 2013 IEEE Symposium on Computers and Communications (ISCC), Split, Croatia, 7–10 July 2013. [Google Scholar]
- Yun, C.-W.; Lee, J.-H.; Yi, O.Y.; Park, S.-H.; Shin, S.-Y. Design the Secured Message Authentication Code Protocol for Underwater Wireless Sensor Networks. Adv. Sci. Lett. 2016, 22, 2491–2495. [Google Scholar] [CrossRef]
- Shanthi, M.B.; Anvekar, D.K. Secure localization for underwater wireless sensor networks based on probabilistic approach. In Proceedings of the 2018 Second International Conference on Advances in Electronics, Computers and Communications (ICAECC), Bangalore, India, 9–10 February 2018. [Google Scholar]
- Yan, J.; Meng, Y.; Yang, X.; Luo, X.; Guan, X. Privacy-Preserving Localization for Underwater Sensor Networks via Deep Reinforcement Learning. IEEE Trans. Inf. Forensics Secur. 2020, 16, 1880–1895. [Google Scholar] [CrossRef]
- Zhao, H.; Yan, J.; Luo, X.; Guan, X. Privacy preserving solution for the asynchronous localization of underwater sensor networks. IEEE/CAA J. Autom. Sin. 2020, 7, 1511–1527. [Google Scholar] [CrossRef]
- Ansari, Z.; Ghazizadeh, R.; Shokhmzan, Z. Gradient descent approach to secure localization for underwater wireless sensor networks. In Proceedings of the 2016 24th Iranian Conference on Electrical Engineering (ICEE), Shiraz, Iran, 10–12 May 2016. [Google Scholar]
- Cai, W.; Yang, J.; Zhang, M.; Peng, S.; Yang, J. Robust and Cooperative Localization for Underwater Sensor Networks in the Existence of Malicious Anchors. Sensors 2019, 19, 4519. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Misra, S.; Ojha, T. SecRET: Secure range-based localization with evidence theory for underwater sensor networks. ACM Trans. Auton. Adapt. Syst. (TAAS) 2021, 15, 1–26. [Google Scholar] [CrossRef]
- Chandavarkar, B.R.; Gadagkar, A.V. Mitigating Localization and Neighbour Spoofing Attacks in Under-water Sensor Networks. In Proceedings of the 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India, 1–3 July 2020. [Google Scholar]
- Zhang, Y.; Jin, Z.; Luo, Y.; Du, X. Node secure localization algorithm in underwater sensor network based on trust mechanism. J. Comput. Appl. 2013, 33, 1208–1211. [Google Scholar] [CrossRef]
- Verma, S.; Prachi, A. Cluster based Key Management Scheme for Underwater Wireless Sensor Networks. Int. J. Comput. Netw. Inf. Secur. 2015, 7, 54–63. [Google Scholar] [CrossRef]
- Petrioli, C.; Saturni, G.; Spaccini, D. Feasibility Study for Authenticated Key Exchange Protocols on Underwater Acoustic Sensor Networks. In Proceedings of the International Conference on Underwater Networks & Systems, Atlanta, GA, USA, 23–25 October 2019. [Google Scholar] [CrossRef]
- Zhao, Y.; Chen, Z.; Ding, J.; Tian, B.; Liu, Y. An Energy-Efficient Key Agreement Mechanism for Underwater Sensor Networks. In IT Convergence and Security 2017; Springer: Singapore, 2017; Volume 450, pp. 146–158. [Google Scholar] [CrossRef]
- Kim, H.; Lee, J.; Yi, O. Key managements of Underwater Acoustic Communication Environments. In Proceedings of the International Workshop on Information Security Applications, Jeju Island, Korea, 24–26 August 2017; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Pelekanakis, K.; Gussen, C.M.G.; Petroccia, R.; Alves, J. Robust Channel Parameters for Crypto Key Generation in Underwater Acoustic Systems. In Proceedings of the OCEANS 2019 MTS/IEEE SEATTLE, Seattle, WA, USA, 27–31 October 2019. [Google Scholar]
- Capossele, A.; Petrioli, C.; Saturni, G.; Spaccini, D.; Venturi, D. Securing underwater communications: Key agreement based on fully hashed MQV. In Proceedings of the International Conference on Underwater Networks & Systems, Halifax, NS, Canada, 6–8 November 2017. [Google Scholar]
- Gopinath, M.P.; Tamizharasi, G.S.; Kavisankar, L.; Sathyaraj, R. A secure cloud-based solution for real-time monitoring and management of Internet of under-water things (IOUT). Neural. Comput. Appl. 2019, 31, 293–308. [Google Scholar] [CrossRef]
- Nissen, I.V.O.R. Burst communication—a solution for the underwater information management. Hydroacoustics 2015, 18, 113–126. [Google Scholar]
- Yang, G.; Wei, Z.-Q.; Cong, Y.-P. Hierarchical Trust Management in Underwater Wireless Communication Networks. Period. Ocean. Univ. China 2013, 6. Available online: https://en.cnki.com.cn/Article_en/CJFDTotal-QDHY201306019.htm (accessed on 6 December 2021).
- Arifeen, M.; Bhakta, D.; Remu, S.R.H.; Islam, M.; Mahmud, M.; Kaiser, M.S. Hidden Markov Model based Trust Management Model for Underwater Wireless Sensor Networks. In Proceedings of the International Conference on Computing Advancements, Dhaka, Bangladesh, 10–12 January 2020. [Google Scholar] [CrossRef]
- Arifeen, M.M.; Islam, A.A.; Rahman, M.M.; Taher, K.A.; Islam, M.M.; Kaiser, M.S. Anfis based trust management model to enhance location privacy in underwater wireless sensor networks. In Proceedings of the 2019 International Conference on Electrical, Computer and Communication Engineering (ECCE), Cox’sBazar, Bangladesh, 7–9 February 2019. [Google Scholar]
- Bolster, A.; Marshall, A. Single and Multi-metric Trust Management Frameworks for Use in Underwater Autonomous Networks. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 185–693. [Google Scholar] [CrossRef] [Green Version]
- Han, G.; Du, J.; Lin, C.; Wu, H.; Guizani, M. An Energy-Balanced Trust Cloud Migration Scheme for Underwater Acoustic Sensor Networks. IEEE Trans. Wirel. Commun. 2019, 19, 1636–1649. [Google Scholar] [CrossRef]
- Jiang, J.; Zhu, X.; Han, G.; Guizani, M.; Shu, L. A dynamic trust evaluation and update mechanism based on C4.5 decision tree in underwater wireless sensor networks. IEEE Trans. Veh. Technol. 2020, 69, 9031–9040. [Google Scholar] [CrossRef]
- Goyal, N.; Dave, M.; Verma, A.K. Trust model for cluster head validation in underwater wireless sensor networks. Underw. Technol. 2017, 34, 106–113. [Google Scholar] [CrossRef]
- Han, G.; Liu, L.; Jiang, J.; Shu, L.; Rodrigues, J.J. A Collaborative Secure Localization Algorithm Based on Trust Model in Underwater Wireless Sensor Networks. Sensors 2016, 16, 229. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- He, Y.; Han, G.; Jiang, J.; Wang, H.; Martinez-Garcia, M. A Trust Update Mechanism Based on Reinforcement Learning in Underwater Acoustic Sensor Networks. IEEE Trans. Mob. Comput. 2020, 1. [Google Scholar] [CrossRef]
- Cong, Y.P.; Wei, Z.Q.; Yang, G. Trust Management for One-Hop Cluster-Based Underwater Wireless Sensor Networks. Adv. Mater. Res. 2012, 488–489, 1163–1167. [Google Scholar] [CrossRef]
- Mazdin, P.; Arbanas, B.; Haus, T.; Bogdan, S.; Petrovic, T.; Miskovic, N. Trust Consensus Protocol for Heterogeneous Underwater Robotic Systems. IFAC-Pap. 2016, 49, 341–346. [Google Scholar] [CrossRef]
- Buddesab, T.; Thriveni, J.; Venugopal, K.R. Trust model genetic node recovery based on cloud theory for underwater acoustic sensor network. Int. J. Electr. Comput. Eng. 2019, 9, 3759. [Google Scholar]
- Han, G.; He, Y.; Jiang, J.; Wang, H.; Peng, Y.; Fan, K. Fault-Tolerant Trust Model for Hybrid Attack Mode in Underwater Acoustic Sensor Networks. IEEE Netw. 2020, 34, 330–336. [Google Scholar] [CrossRef]
- Du, J.; Han, G.; Lin, C.; Martinez-Garcia, M. ITrust: An Anomaly-resilient Trust Model Based on Isolation Forest for Underwater Acoustic Sensor Networks. IEEE Trans. Mob. Comput. 2020, 1. [Google Scholar] [CrossRef]
- Liang, K.; Huang, H.; Huang, X.; Yang, Q. CS-Based Homomorphism Encryption and Trust Scheme for Underwater Acoustic Sensor Networks. In Proceedings of the International Conference on Machine Learning and Big Data Analytics for IoT Security and Privacy, Shanghai, China, 6–8 November 2020; Springer: Cham, Switzerland, 2020. [Google Scholar]
- MIT, Massachusetts Institute of Technology. A Battery-Free Sensor for Underwater Exploration. 2021. Available online: https://news.mit.edu/2019/battery-free-sensor-underwater-exploration-0820 (accessed on 28 October 2021).
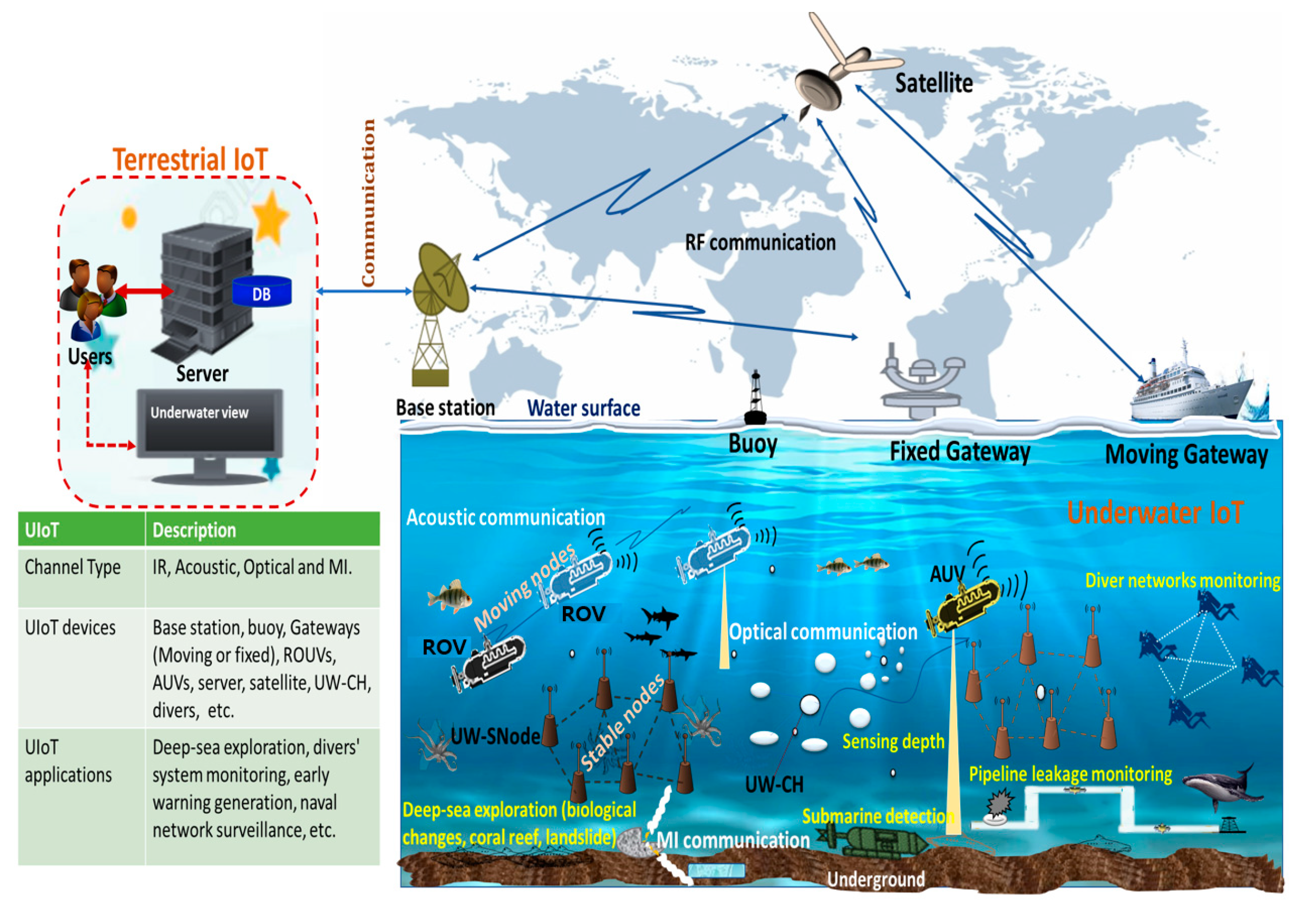
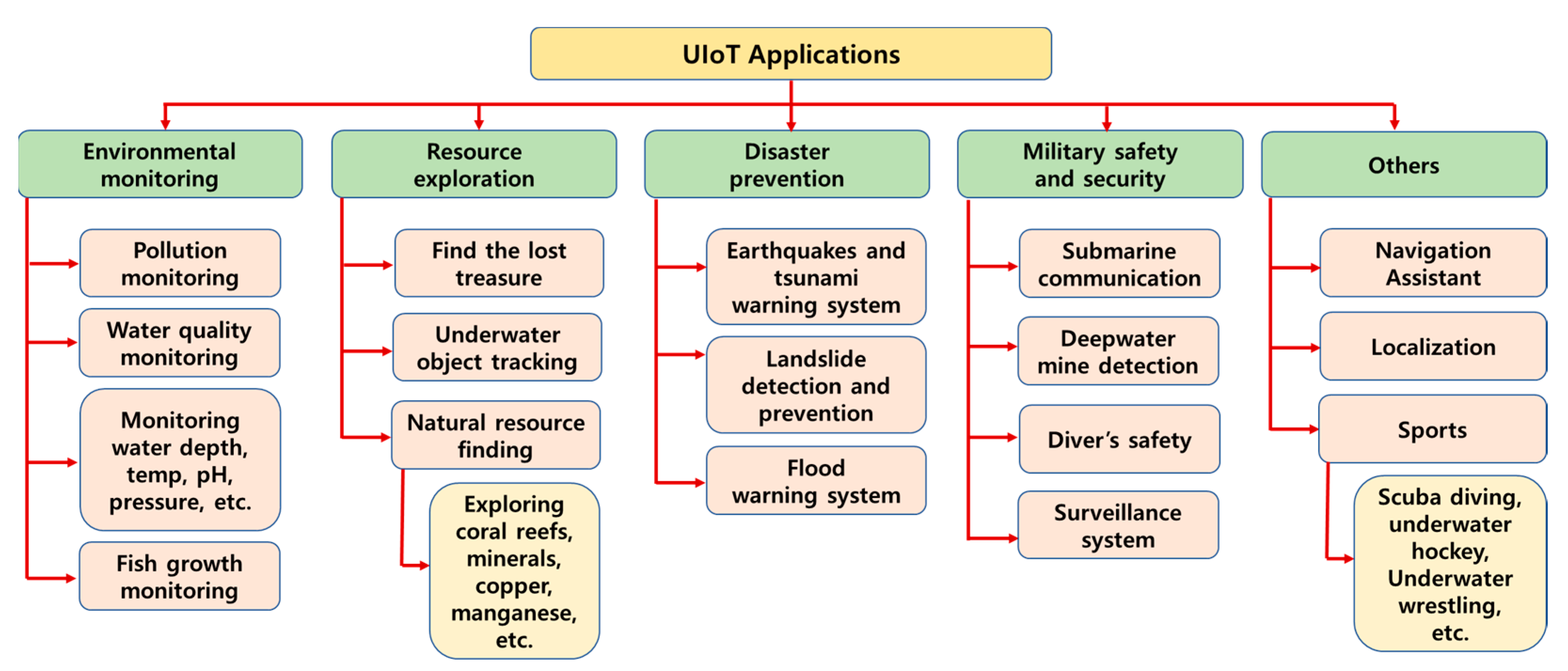
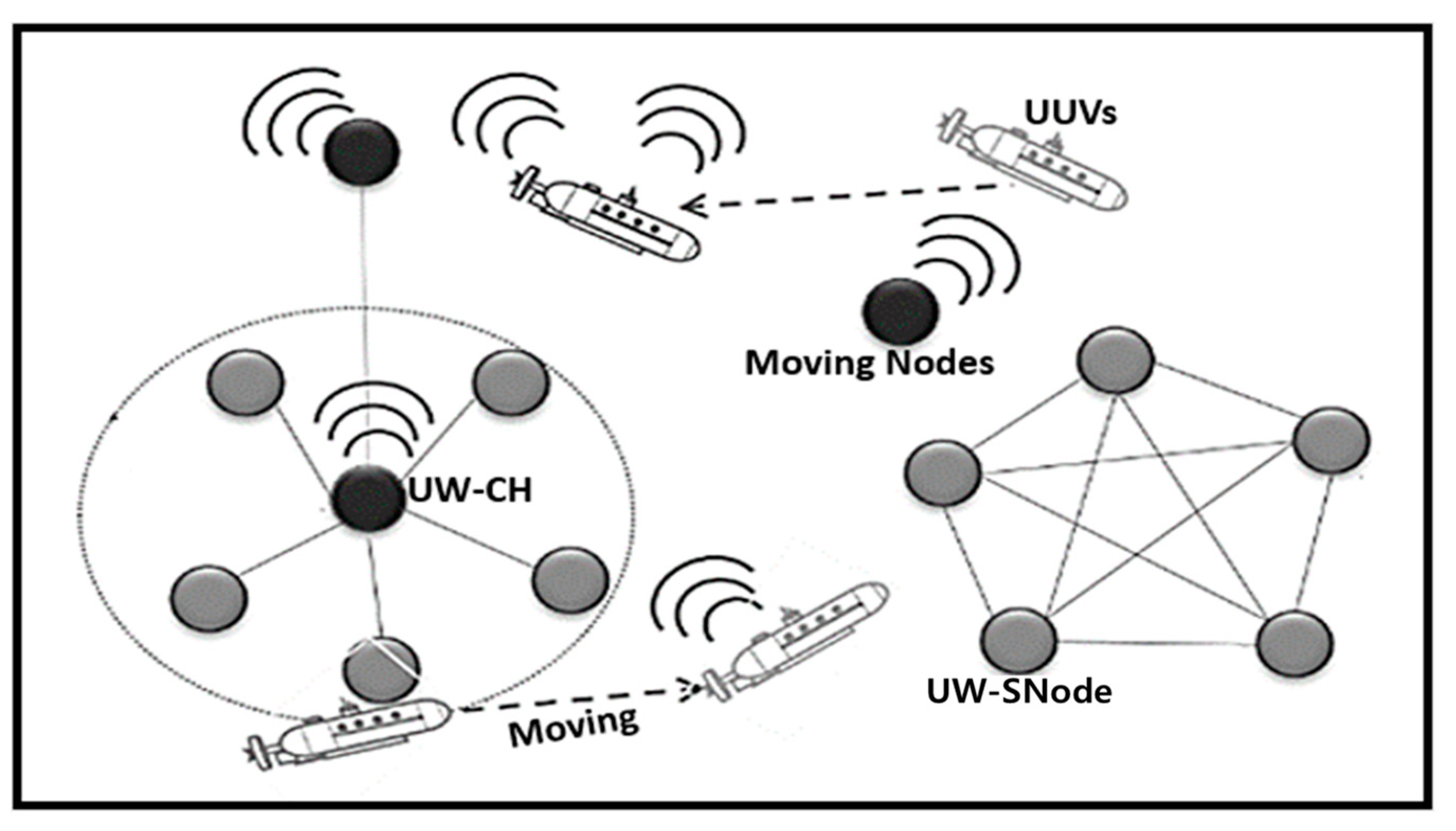
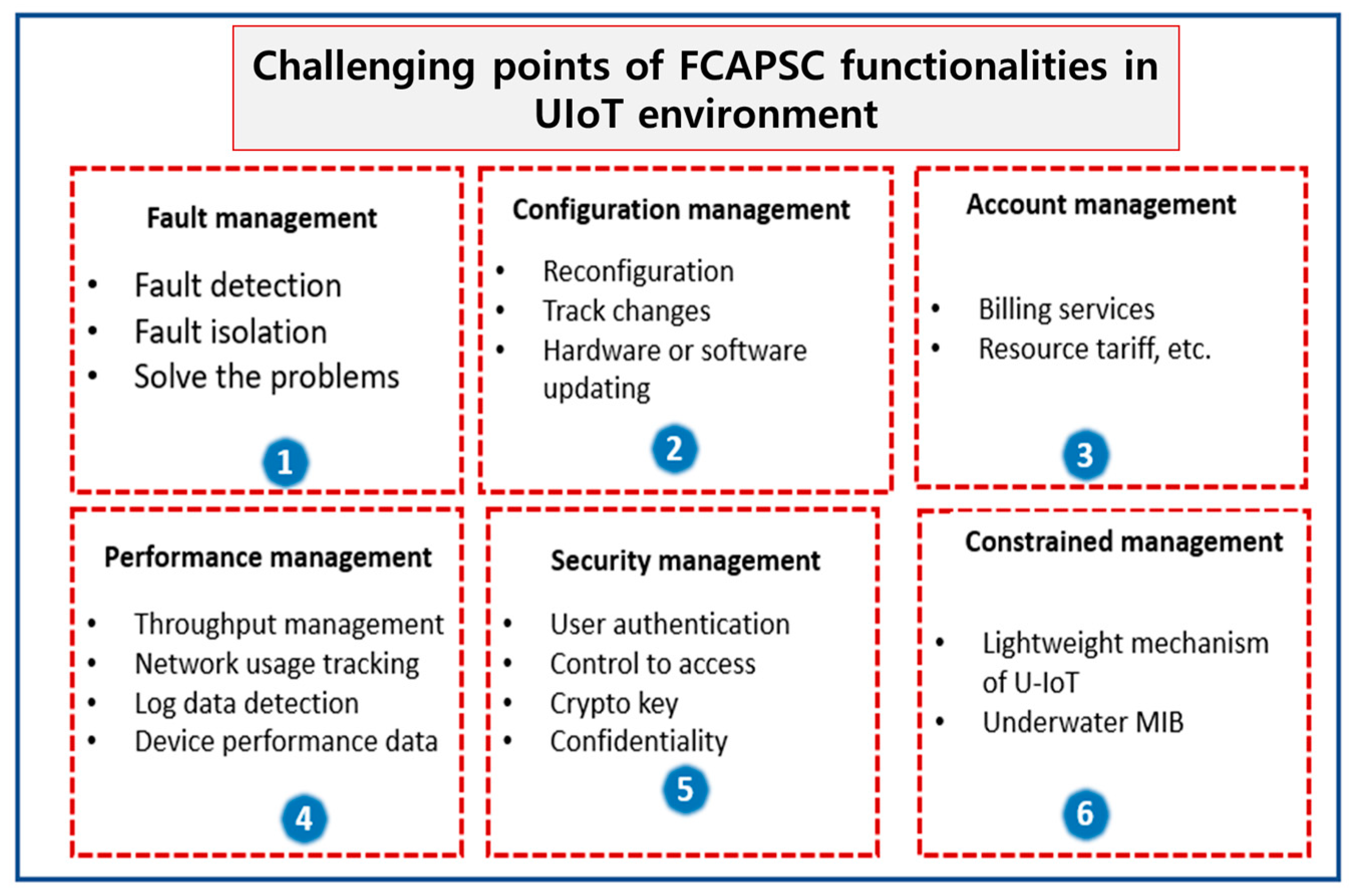


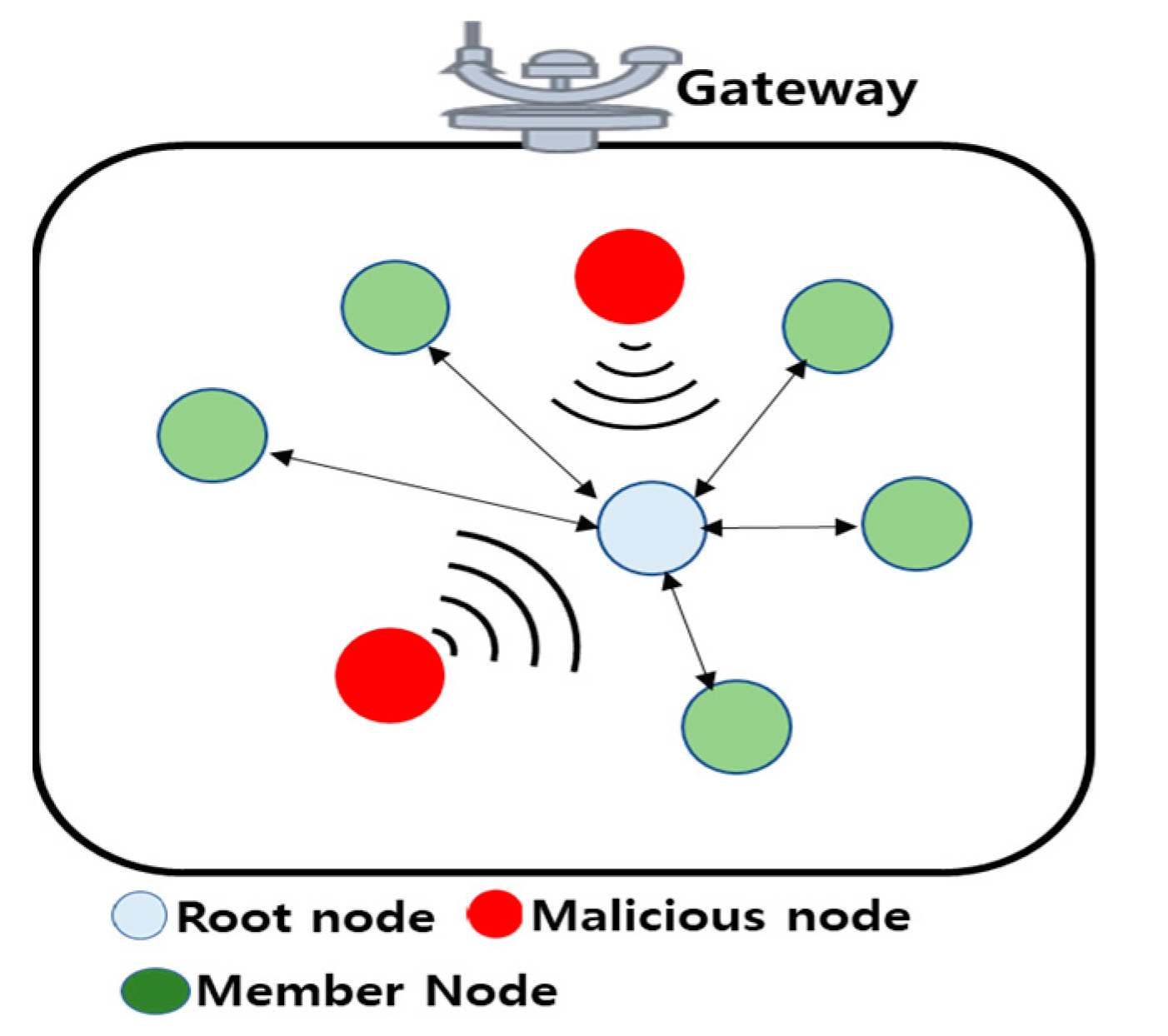
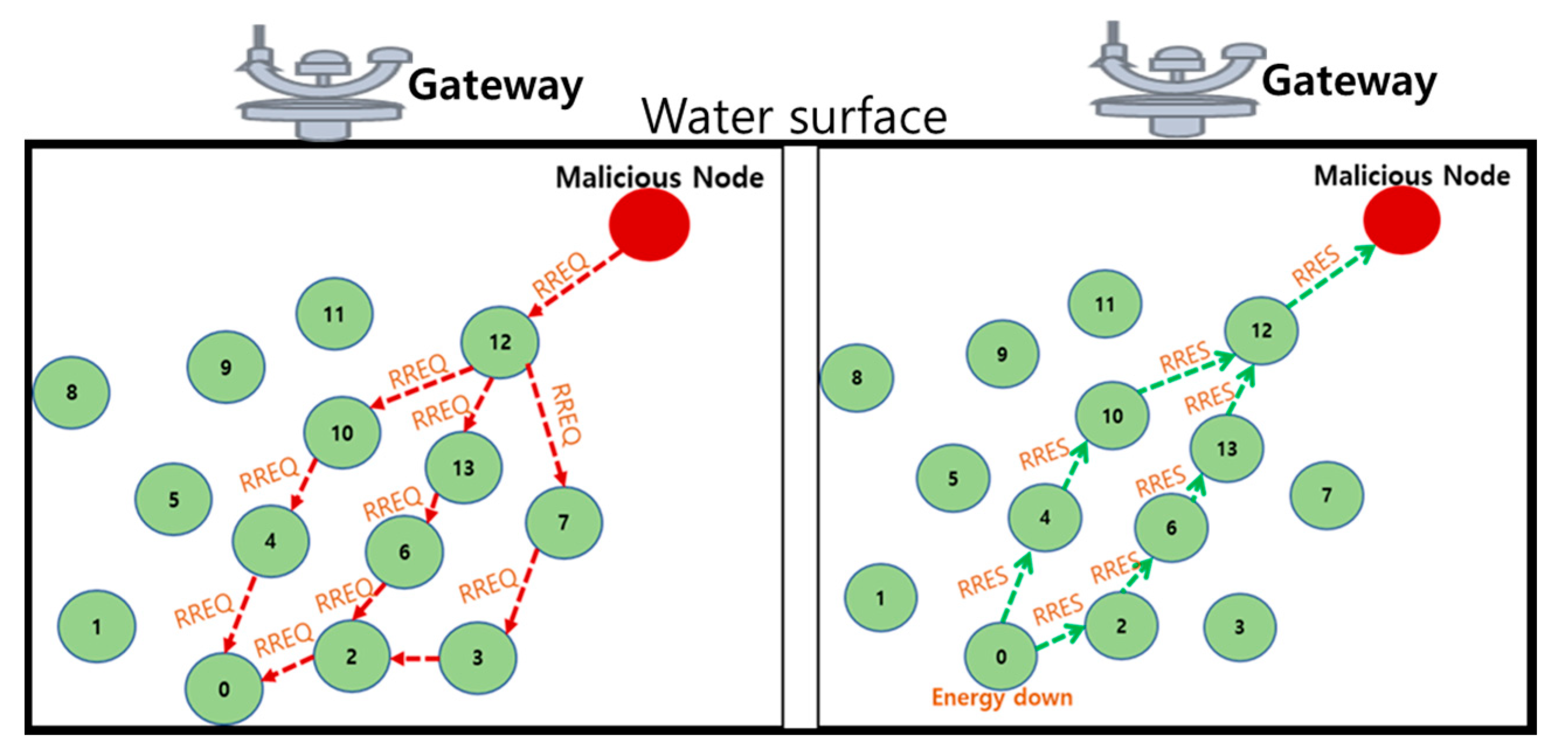
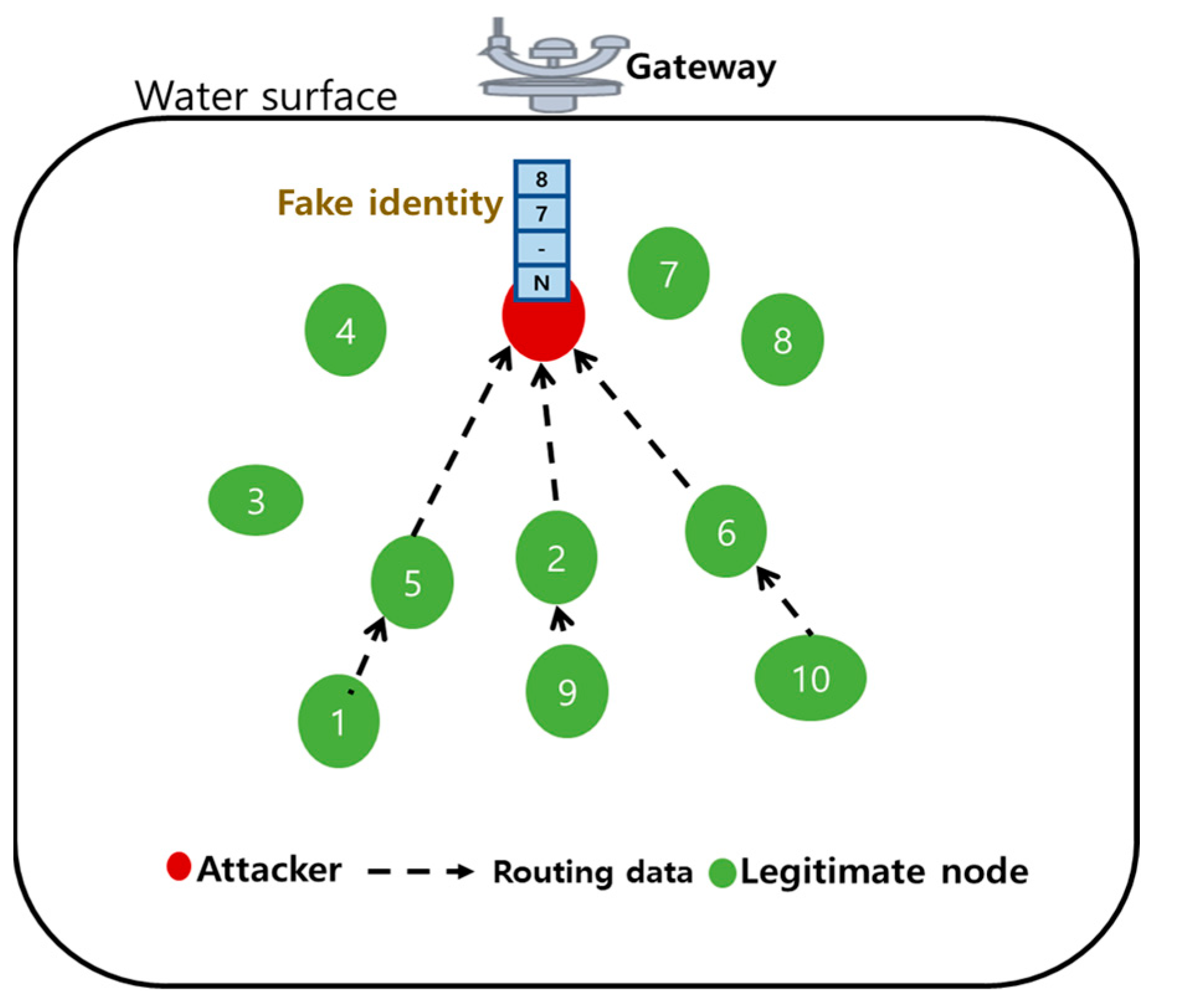
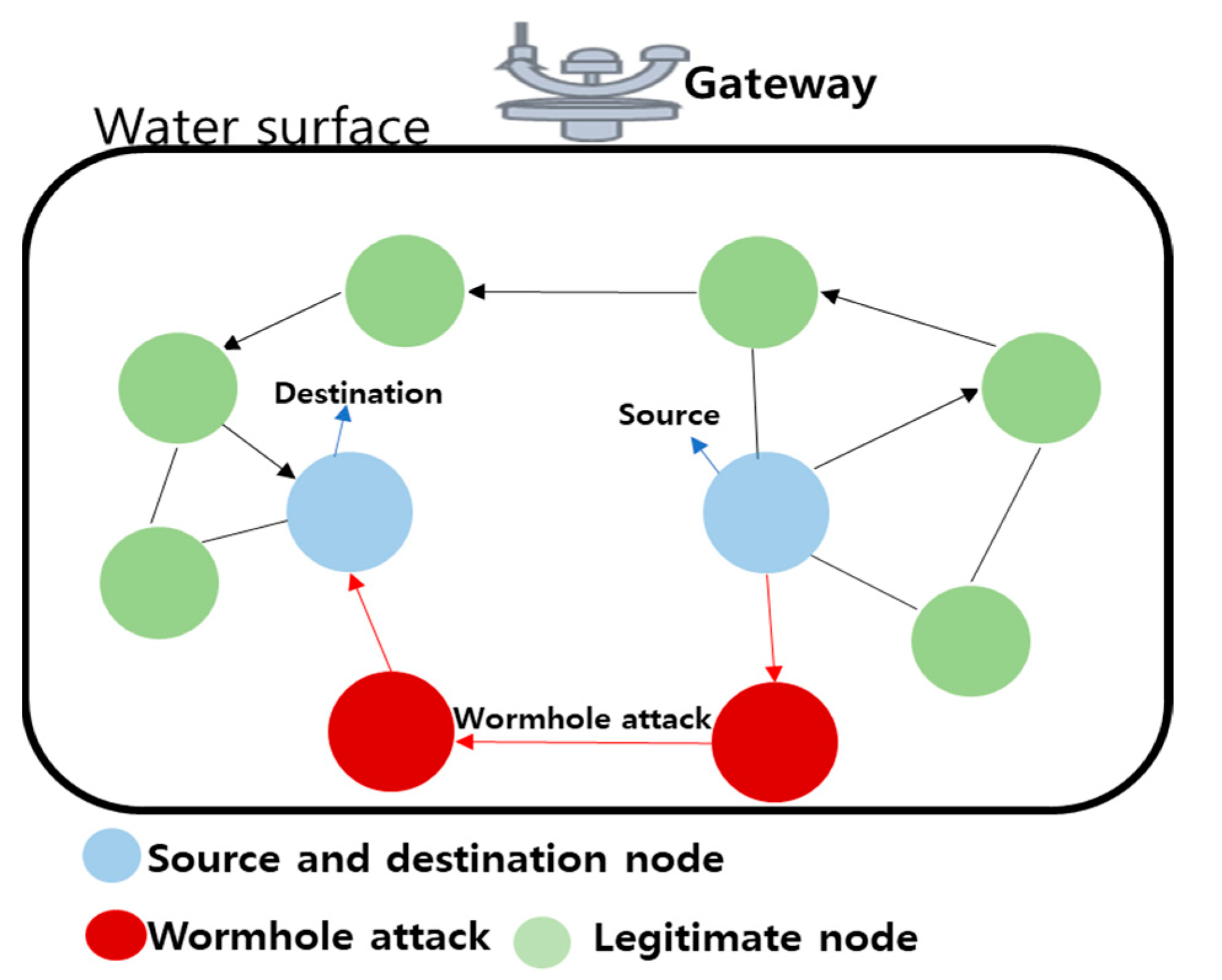
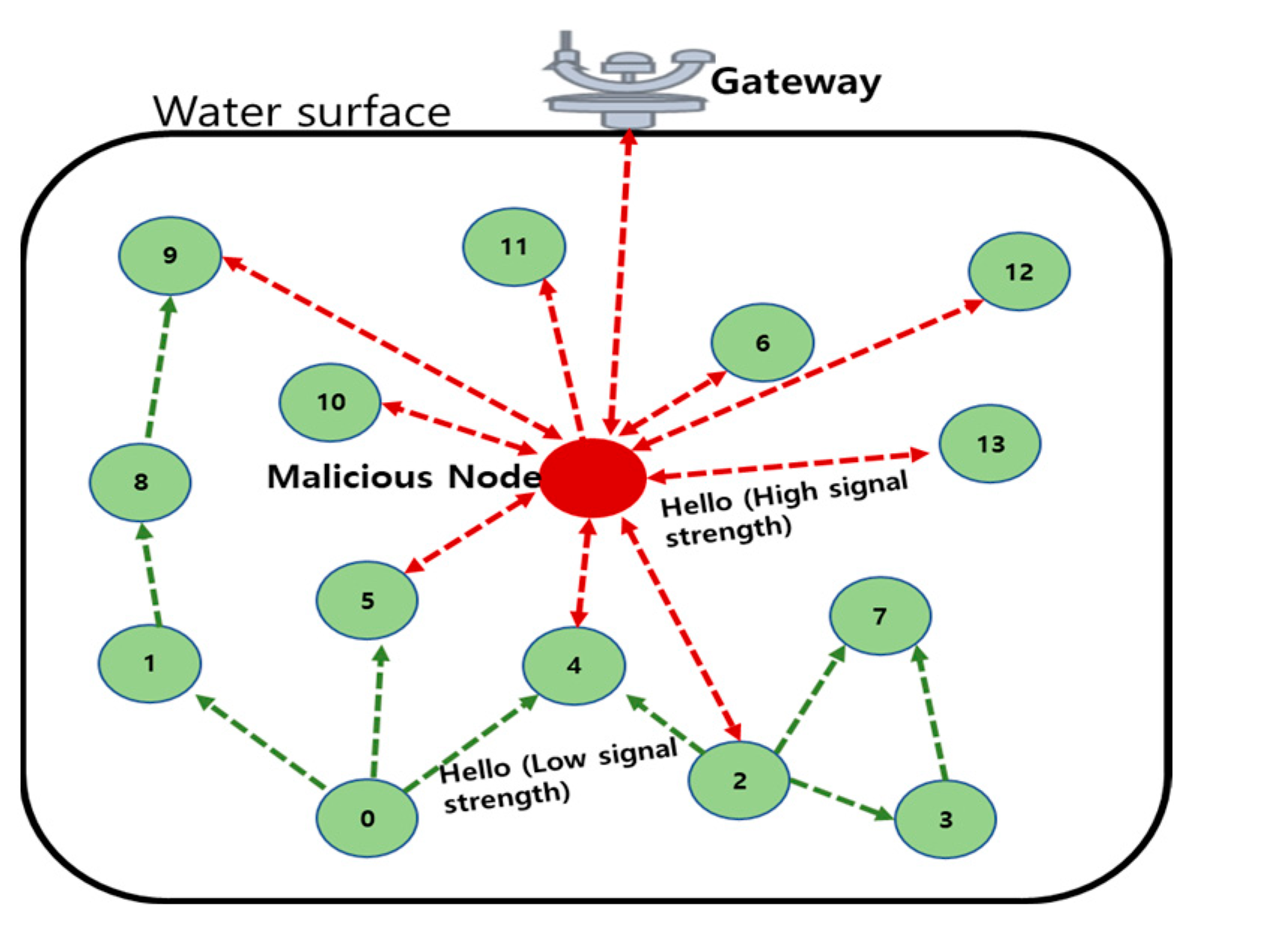

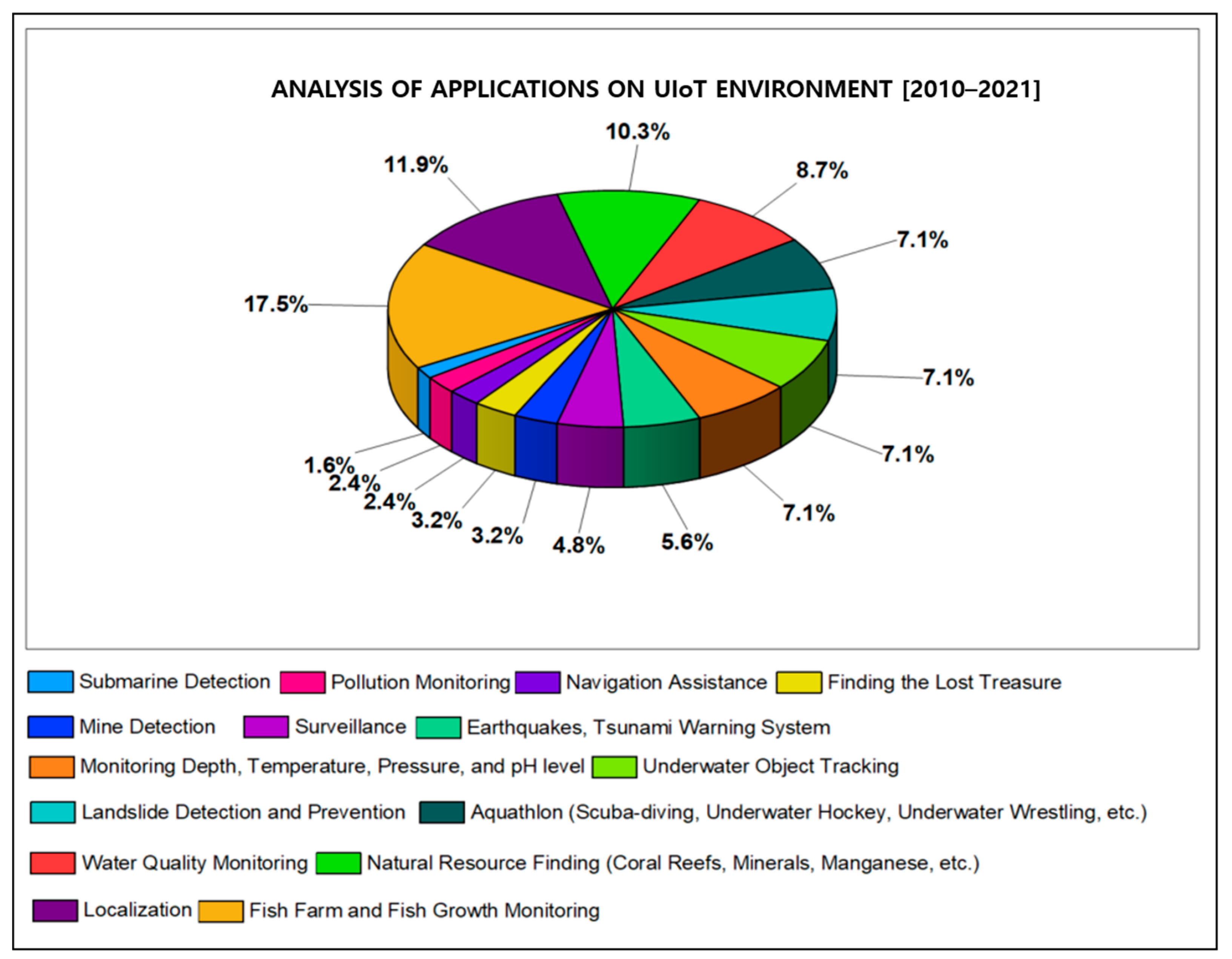
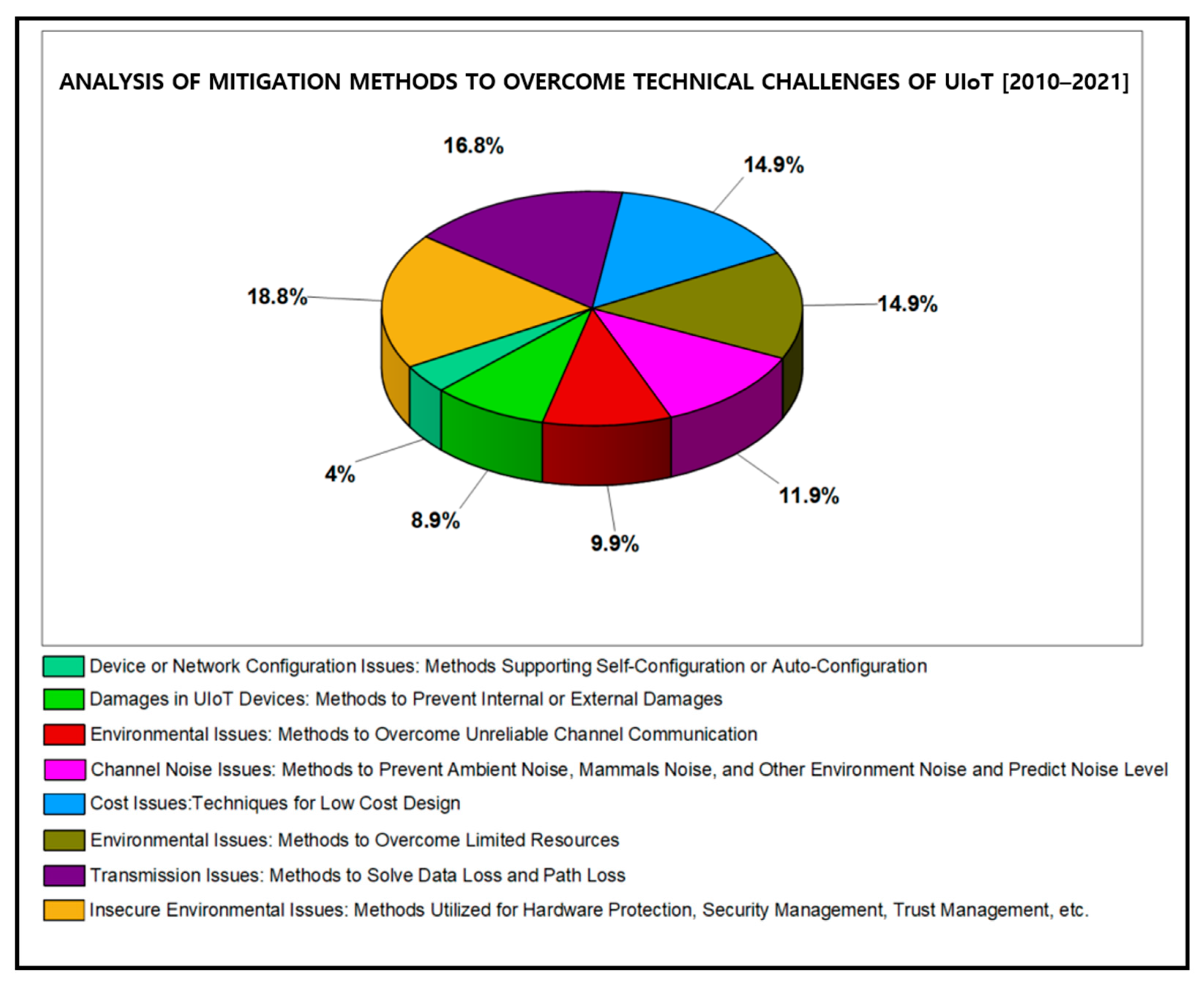
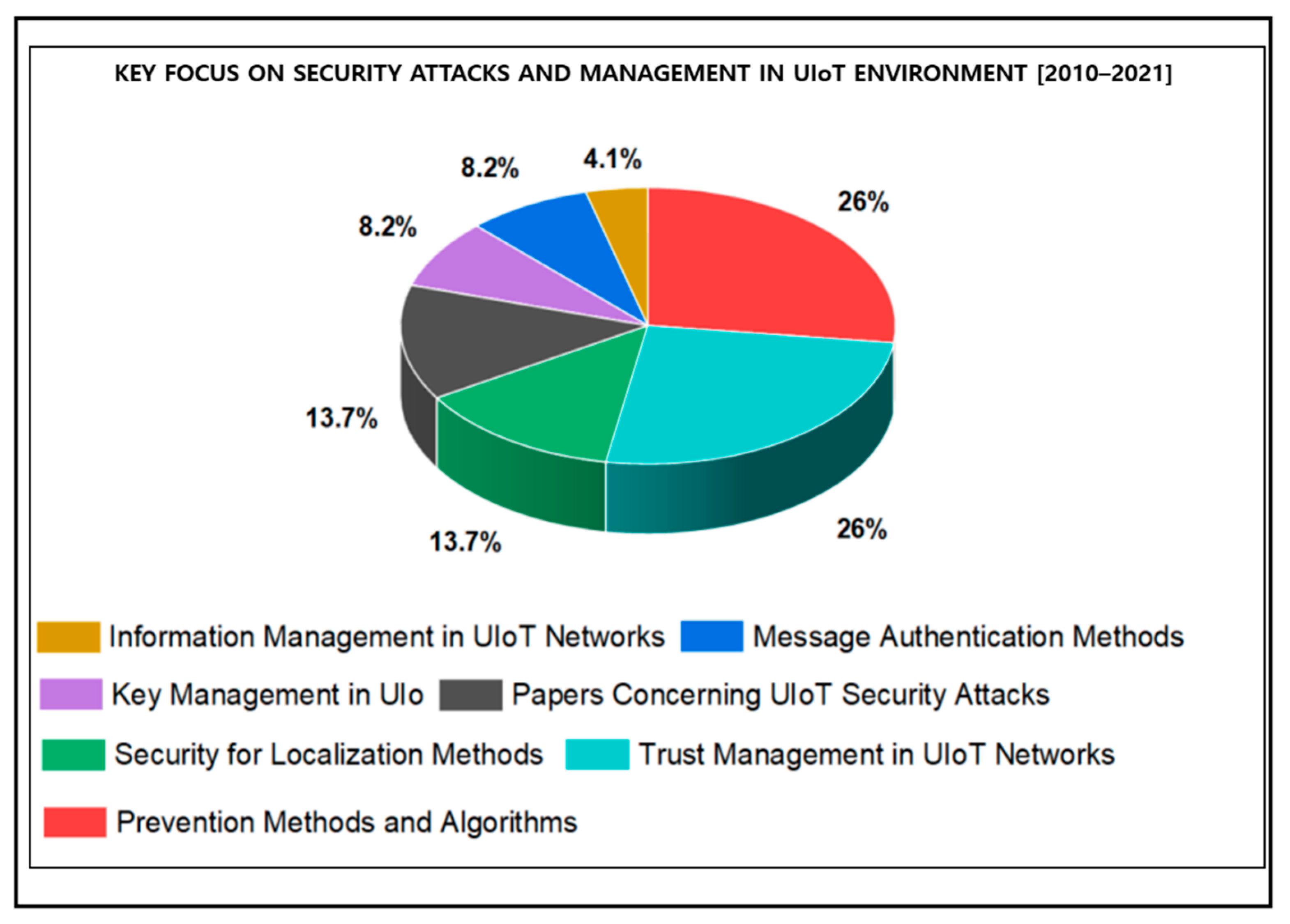
| Queries (Qs) | Discussion |
|---|---|
| Q1: What are the current trends of the UIoT system? | UIoT is the growing trend in the current IoT system. Recently, numerous UIoT applications have been developed for the industries. Therefore, Q1 provides the survey based on the latest article and the recently developed UIoT applications. Furthermore, the communication technologies of UIoT are discussed, which includes the pros and cons of UIoT channels such as RF, acoustic, optical and MI. |
| Q2: What are the challenges of the current UIoT system? | Challenges include technical challenges, security attacks and privacy issues. Therefore, Q2 discusses the technical challenges based on UIoT channel characteristics and the possible security challenges and privacy issues in UIoT. |
| Q3: What are the possible methods to overcome the challenges, security attacks and privacy issues in the UIoT system? | In the UIoT system, most of the challenges and security issues are still of concern. Likewise, privacy methodologies are not yet considered for the current UIoT system. Therefore, Q3 highlights the countermeasures taken to overcome the challenges, security attacks and privacy issues of the current UIoT system. |
| Q4 and Q5: What are the findings and future directions? | Q4 discusses the findings based on the systematic review and Q5 highlights the future direction of this paper. |
| Attributes | Acoustic | RF | Optical | MI |
|---|---|---|---|---|
| Channel speed | ≈1500 m/s | ≈3.33 × 108 m/s | ≈3.33 × 108 m/s | ≈3.33 × 108 m/s |
| Communication range | ≈kilometer (km) | ≈10 m | ≈10–100 m | ≈10–100 m |
| Data rate | ≈kbps | ≈Mbps | ≈Gbps | ≈Mbps |
| Signal operation | Audible | Non-visible and non-audible | Visible | Non-visible and non-audible |
| Frequency band | 10−15 kHz | 30−300 Hz | ≈5 × 1014 Hz | - |
| Size of the Antena | ≈0.1 s | ≈0.5 s | ≈0.1 s | ≈0.1 s |
| Channel characteristics dependency | Undersea noise, temperature, pressure, Doppler spread, salinity, etc. | Conductivity | Undersea noise, attenuation, turbidity, scattering, etc. | Conductivity |
| Bandwidth | ≈1–100 Kilohertz (kHz) | ≈Megahertz (MHz) | ≤150 Megahertz (MHz) | ≈Megahertz (MHz) |
| Purpose of each channel | Long-range communication | Surface water communication | Short-range communication | Underground communication in deep sea |
| Transmission power | >10 watts (W) | megawatts (MW)−watts(W) | megawatts (MW)−watts(W) | 10−8 watts (W) |
| Power loss dependency | ≈0.1 dB per meter (m) or per hertz (Hz) | ≈28 dB per kilometer (km) or one million hertz (HZ) | Depending on the turbulence of water | Depending on the permeability of undersea soils |
| Main Clause | Subclause | Paper Count | References Number |
|---|---|---|---|
| Environmental monitoring | Pollution monitoring | 3 | [117,118,119] |
| Water quality monitoring | 11 | [120,121,122,123,124,125,126,127,128,129,130] | |
| Monitoring depth, temperature, pressure, and pH level. | 9 | [131,132,133,134,135,136,137,138,139] | |
| Fish farm and fish growth monitoring | 22 | [140,141,142,143,144,145,146,147,148,149,150,151,152,153,154,155,156,157,158,159,160,161] | |
| Resource exploration | Finding the lost treasure | 4 | [162,163,164,165] |
| Underwater object tracking | 9 | [166,167,168,169,170,171,172,173,174] | |
| Natural resource finding (Coral reefs, minerals, manganese, etc.) | 13 | [175,176,177,178,179,180,181,182,183,184,185,186] | |
| Disaster prevention | Earthquakes, Tsunami warning system | 7 | [187,188,189,190,191,192,193] |
| Landslide detection and prevention | 9 | [194,195,196,197,198,199,200,201,202] | |
| Naval applications | Submarine detection | 2 | [203,204] |
| Mine detection | 4 | [205,206,207,208] | |
| Surveillance | 3 | [209,210,211] | |
| Others | Aquathlon (Scuba-diving, underwater hockey, underwater wrestling, etc.) | 6 | [212,213,214,215,216,217] |
| Navigation assistance | 9 | [218,219,220,221,222,223,224,225,226] | |
| Localization | 15 | [85,86,227,228,229,230,231,232,233,234,235,236,237,238,239] |
| Problems | Solutions and Effective Methods | Paper Count | References Number |
|---|---|---|---|
| Transmission issues | Methods to preventing path loss and data loss in UIoT networks. | 17 | [240,241,242,243,244,245,246,247,248,249,250,251,252,253,254,255,256] |
| Environmental issues | Methods to solve unreliable channel conditions in UIoT networks. | 10 | [257,258,259,260,261,262,263,264,265,266] |
| Methods to solve limited resources in UIoT networks. | 15 | [26,54,55,56,57,58,59,60,61,62,63,64,267,268,269] | |
| Insecure environment issues | Methods used to support trust management, security management, hardware protection, etc., in UIoT networks. | 19 | [42,107,113,270,271,272,273,274,275,276,277,278,279,280,281,282,283,284,285] |
| Cost issues | Lost cost design approaches for UIoT networks | 15 | [87,88,89,90,91,92,93,94,95,96,97,98,99,100,101] |
| Channel noise issues | Methods to prevent ambient noise, mammals noise, other environmental noise in UIoT networks. Methods to predict noise level in UIoT networks. | 12 | [71,72,73,74,75,76,77,78,79,80,81,82] |
| Damages in UIoT devices | Methods to prevent internal or external damages of UIoT devices. | 9 | [26,286,287,288,289,290,291,292] |
| Device or network configuration issues | Methods supporting self-configuration or auto-configuration mechanism for devices in UIoT networks. | 4 | [26,104,105,106] |
| Main Clause | Subclause | Paper Count | References Number |
|---|---|---|---|
| Key focus on security attacks and management | Papers discussing privacy and security attacks on UIoT networks. | 10 | [271,293,294,295,296,297,298,299,300,301] |
| Papers discussing attack prevention methods and management in UIoT networks. | 19 | [42,107,113,270,271,272,273,274,275,276,277,278,279,280,281,282,283,284,285] | |
| Papers discussing message authentication techniques in UIoT networks. | 6 | [42,302,303,304,305,306] | |
| Papers discussing localization security in UIoT networks. | 10 | [42,271,307,308,309,310,311,312,313,314] | |
| Papers discussing key management in UIoT networks. | 6 | [315,316,317,318,319,320] | |
| Papers discussing information management in UIoT networks. | 3 | [78,321,322] | |
| Papers discussing trust management in UIoT networks. | 19 | [273,275,276,314,323,324,325,326,327,328,329,330,331,332,333,334,335,336,337] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mary, D.R.K.; Ko, E.; Kim, S.-G.; Yum, S.-H.; Shin, S.-Y.; Park, S.-H. A Systematic Review on Recent Trends, Challenges, Privacy and Security Issues of Underwater Internet of Things. Sensors 2021, 21, 8262. https://doi.org/10.3390/s21248262
Mary DRK, Ko E, Kim S-G, Yum S-H, Shin S-Y, Park S-H. A Systematic Review on Recent Trends, Challenges, Privacy and Security Issues of Underwater Internet of Things. Sensors. 2021; 21(24):8262. https://doi.org/10.3390/s21248262
Chicago/Turabian StyleMary, Delphin Raj Kesari, Eunbi Ko, Seung-Geun Kim, Sun-Ho Yum, Soo-Young Shin, and Soo-Hyun Park. 2021. "A Systematic Review on Recent Trends, Challenges, Privacy and Security Issues of Underwater Internet of Things" Sensors 21, no. 24: 8262. https://doi.org/10.3390/s21248262
APA StyleMary, D. R. K., Ko, E., Kim, S.-G., Yum, S.-H., Shin, S.-Y., & Park, S.-H. (2021). A Systematic Review on Recent Trends, Challenges, Privacy and Security Issues of Underwater Internet of Things. Sensors, 21(24), 8262. https://doi.org/10.3390/s21248262






