A Hybrid Lightweight System for Early Attack Detection in the IoMT Fog
Abstract
:1. Introduction
- A fog-computing architecture for the IoMT system is proposed, representing moderate to large healthcare organizations.
- We propose a hybrid (for host and network) lightweight fog-based multi-attack detection system with early detection capability, due to adaptive learning techniques. These methods are novel Weighted Hoeffding Tree Ensemble (WHTE); Incremental Naïve Bayes (INB); Hoeffding Tree Majority Class (HTMC); Hoeffding Tree Naïve Bayes (HTNB), and Hoeffding Tree Naïve Bayes Adaptive (HTNBA). The model is unique because it was performed by an adaptive incremental setting, which does not impose any overhead on the devices. Consequently, the proposed model is suitable for real-world circumstances, with ever-increasing IoT-infected sensors and NetFlow data with multiple attacks arriving at the fog devices.
2. Materials and Methods
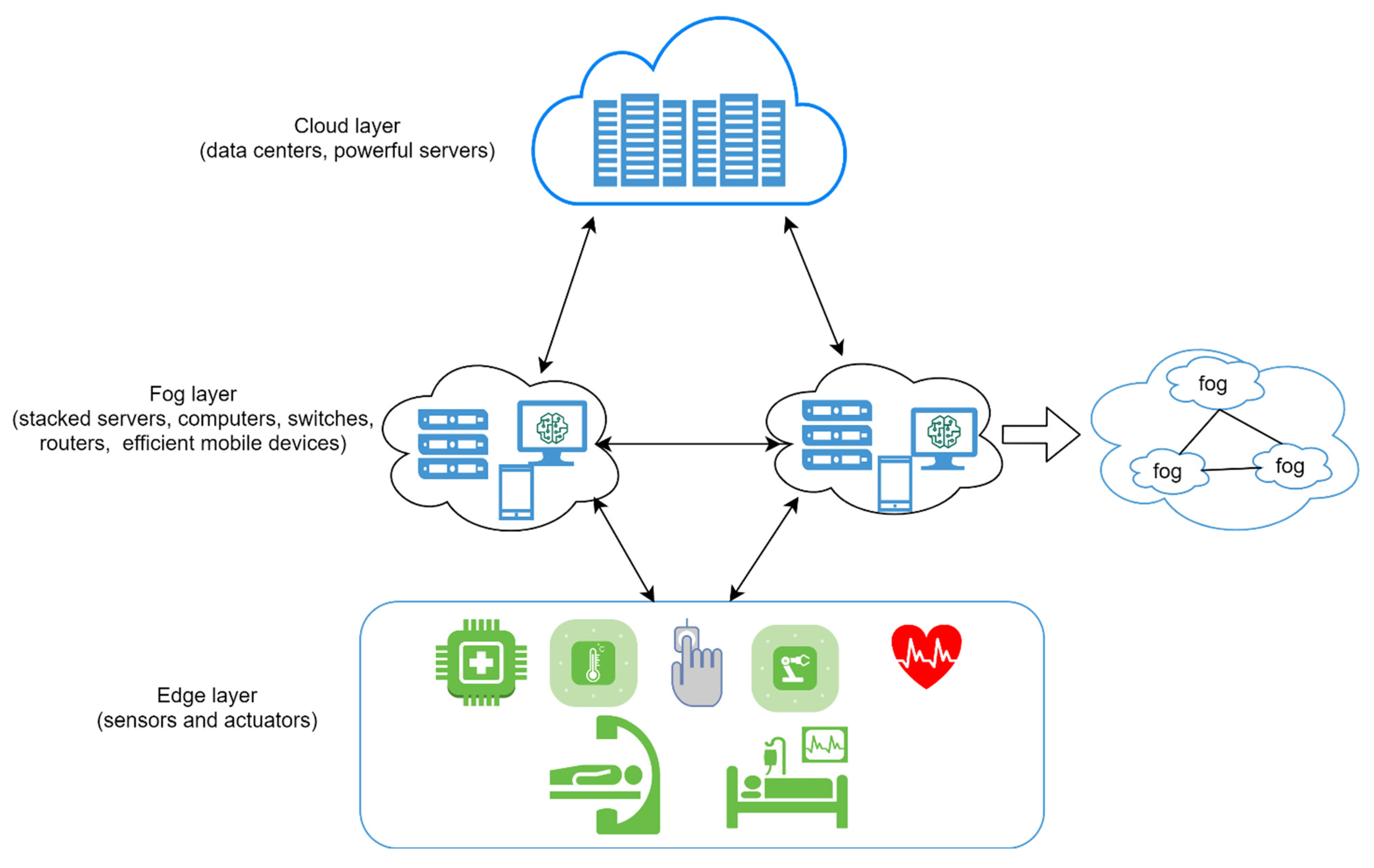
2.1. Proposed Fog-Based Hybrid Attack Detection System
- Collecting and extracting the sensor and network data at the edge of the IoMT system. The extracted datasets are explained in detail in Section 2.2.
- Preprocessing the collected data to remove noises, followed by utilizing a sliding window to set the ML classifiers. By this, the memory is updated whenever a new set of samples arrives, and set to the sliding window. The sliding window was set to one thousand records and the memory frequency was set to five thousand records at a time.
- Incremental K-Nearest Neighbour (IKNN): This is an incremental modified version of the original K-Nearest Neighbour, a supervised machine learning technique for classification and regression problems. It uses the concept of similarities (also known as distance), such as finding the distance between two points or two objects on a surface. The KNN technique assumes that the samples close to each other belong to the same class. The parameters to be fed to this technique are the K-value, and the number of nearest neighbours that decide whether an instance belongs to those nearest neighbors’ class. Another parameter is the mathematical method for calculating the distance. In this work, the value of N was set to 10, and the mathematical approach was a linear model. Figure 3 illustrates how IKNN predicts new samples when they arrive at the system. If we take a smaller circle, in which the K value is five, the labels of the five nearest samples are examined. Then, based on the most repeatable class, it will decide the class of the new sample. Therefore, when K is five in the smaller circle, the incoming sample will be considered a threat, because the nearest samples are at least three. However, if the K value is 11, as shown in the larger circle, the incoming new sample will be considered normal, because there are six near-normal samples.
- Incremental Naïve Bayes: Naïve Bayesian classification is a common classification system used to analyze large sizes of data. In this work, Naïve Bayes incremental learning is used to handle massive datasets on resource-limited fog devices. The method’s success is that it can be supplemented with updated data without storing the entire dataset in the memory. Because of its incremental feature, the algorithm is well suited for detecting and classifying attacks quickly and accurately [49]. The basic formula of Naïve Bayes is as follows:where, is the class, which takes values considering the type of attacks and normal class, and is the list of features, in which X can be a list of components identified as . If this list is replaced by the variable , the equation can be updated as follows:Since the denominator of the above equation remains static, we can remove it and proportionally inject it into the equation as follows:This is for binary classes; however, we have eight classes in our datasets. Hence, the class with the highest probability or likelihood should be chosen by:From Equation (4), we can predict the class value for a list of features.
- Hoeffding Tree-based classifiers: Different forms of the original Hoeffding Tree (HT) are implemented in this study. The details of these classifiers are explained below:
- Hoeffding Tree-Based Majority Class (HTMC): Conventional tree-based classifiers have a significantly restricted number of training instances, because they presume that the real data should be saved in memory at once [50]. Hoeffding Tree (HT) is an efficient and straightforward tree-based classifier, designed to stream big data. This tree-based classifier assumes a constant distribution of data. This method works based on Hoeffding Bound’s theory. The Hoeffding Tree has a theoretically appealing feature that other incremental tree-based learners do not have. It provides a solid efficiency guarantee. HT is initially designed for big data streams. Hoeffding Tree-based Majority Class (HTMC) is a form of HT that uses the majority class technique to decide about the classes of the tree branches [51].
- Hoeffding Tree Naïve Bayes: There are some efforts to improve the accuracy of this classifier by using other techniques at the HT leaves. Using Naïve Bayes classifiers rather than the majority class classifier improves the HT classification performance. Most of the class approach utilizes information on classes patterns, only to categorize a test sample without searching for feature values. This only makes use of a small portion of the information given, and it is a rough estimation of the pattern of instances. However, Naïve Bayes considers both the prior distributions of the classes and the likelihoods of a feature, given the class. This allows for far better utilization of the available information [51]. The sample is traversed from the root to the leaf, to classify new samples. It uses the splitting test and feature values to establish a correct path. When the sample reaches any leaf, it will classify the sample. Here, the classifier will be a Naïve Bayes classifier. It uses information gained during the classification process without adding overhead [51].
- Hoeffding Tree Naïve Bayes Adaptive (HTNBA): At the presence of noise in cyber-attack infected datasets, Naïve Bayes at leaves may not tolerate well, and its performance is not better than the HTMC. Therefore, a hybrid of majority class and Naïve Bayes is proposed to overcome both techniques’ shortcomings, called Hoeffding Tree Naïve Bayes Adaptive (HTNBA) [52]. The HTNBA method uses Naïve Bayes Adaptive to classify the instances based on their discriminative features. It also uses the Gain value to decide the class of the incoming instances (Holmes et al., 2005). After predicting the new instances by both Naïve Bayes and the majority class, the hybrid method chooses one of them based on their prediction value.
- Weighted Majority Hoeffding Tree Ensemble (WHTE): single classifiers which were explained previously may not work similarly well on different types of input data. Therefore, their ensemble can be used to maximize their performance and minimize their weaknesses. Since sensor and network data change in their features and sample statistics, applying one type of classifier may not always bring the best result. Therefore, we propose a new ensemble approach, combining a group of single classifiers; specifically, the different types of Hoeffding Tree classifiers (HTMC, HTNB, HTNBA). The ensemble approach uses the weighted majority approach, which initially considers all the classifier’s decisions [53]. However, it will punish a classifier once they make a wrong decision, by not considering their decisions to be as important as they were [54]. All experts (classifiers) will have a vote, and initially these will be equally weighted. Then, if one of those experts (classifiers) makes a mistake, their votes will be cut down in proportional value, and weighting will be used for the overall performance. Then, the final performance is optimal because the mistakes made by the entire algorithm will be close to the constant mistake made by the best technique. When the expert makes a mistake in the original weighted majority algorithm, the weighted value will be multiplied by ½. Hence, the error bound equation is as follows:where is the number of mistakes made by the best classifier, is the number of errors made by the ensemble, and is the number of classifiers in the pool.One can see that the minimum constant factor (coefficient of the right-hand side of Equation (5)) is greater than two. However, this can be reduced by performing the randomized form of weighted majority algorithm in which Beta (β) is used as a penalty value to minimize the constant value to be close to one. Therefore, in our WHTE algorithm, the error will be counted as follows:In our study, we have set the value of to be 0.5. Hence, the value of for each iteration or a sample at a time will be counted by:A simplified flowchart of our ensemble method is presented in Figure 4, whereas the pseudo code of the entire system is shown in Algorithm 1.
| Algorithm 1. Hybrid Lightweight Attack Detection System |
| Input as a set of single sensor datasets, as NetFlow dataset, as set of single incremental classifiers (INB, IKNN, HTMC, HTNB, HTNBA), and as ensemble WHTE |
| Output set of performance metrics (average accuracy, average memory, average CPU time, kappa statistic, precision, recall, concept drift sensitivity) |
| Begin At fog devices close to the edge in framework 1 Collect infected sensor data in Collect infected NetFlow for and each in while there is data record in and Do Pre-process the data Set the sliding window to 1K records Set the maximum memory to 5K records Set the initial parameters of each classifier in Set the parameters of each in for each record in S and N Do Prequential train and test using and each Compute each in return average Update parameters of and each in end for end while for each in and for each in Compute one-way ANOVA Assume that all population means are equal Initialise p value if (p < 0.05). then reject else accept return statistical metrics end if end for end for end for End |
2.2. Sensor and Network Datasets for IoMT Fog
- ToN-IoT: The first form of the dataset was a collection of sensors datasets gathered from the seven different sensors. It held data of about seven IoT cyber-attacks with legitimate device data. Each dataset had different features on the devices. The total samples of all datasets were 401,119 (fridge: 59,944, Garage door: 59,587, GPS: 58,960, Modbus: 51,106, Motion light: 59,488, Thermostat: 52,774, Weather: 59,260). The attacks in this dataset were (backdoor, distributed denial of service (DDoS), injection, password, ransomware, scanning, and cross-site scripting (XSS)) [55]. Figure 5a shows the number of attack samples among all the sensor datasets.
- NetFlow_ToN-IoT: The second form of dataset was the network traffic of the IoT system, in which network traffic packets were transformed to NetFlow files [56]. NetFlow format network traffic was less heavy than its payloads (packets) because it used the traffic features, rather than the content of the packets. This dataset consisted of 14 features and 1,379,274 samples. This big data included all the attacks which existed in its sensor telemetry datasets, such as injection, DDoS, scanning, password, XSS, backdoor, and ransomware, with another two attacks of denial of service (DoS), and man in the middle (MiM), which mainly target the network layer. Additionally, the attacks at NetFlow had a different number of samples, compared with those in the sensor dataset. Figure 5b shows the number of attack samples in the NetFlow dataset.
2.3. Evaluation Metrics
- Average accuracy: This is the average of all the sliding windows’ accuracies at the end of the analysis. In incremental learning, accuracy is not calculated in this way in batch learning, because there is a high possibility for the samples to fall within a single class in one sliding window.
- Average time (s): The average CPU time taken by the incremental learning method for each sliding window dataset’s training and evaluation process.
- Precision: Is the ratio of true positive over predicted positive samples.
- Recall: This is the ratio of true positive over total positives in the dataset.
- Kappa Static: It measures how well the samples identified by the classifier resembled the data labeled as ground truth, while adjusting for the performance of a randomized classifier as evaluated by anticipated accuracy. It will add more information to the accuracy of a model, especially when the incoming samples are more skewed (imbalanced).
- ANOVA test: To evaluate the significant differences among the performances of the used classifiers, one-way ANOVA is used.
2.4. Experimental Environment
3. Results and Discussion
3.1. Host-Based Attack Detection
3.2. Network-Based Attack Detection
4. Limitations and Future Work
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Gatouillat, A.; Badr, Y.; Massot, B.; Sejdic, E. Internet of Medical Things: A Review of Recent Contributions Dealing with Cyber-Physical Systems in Medicine. IEEE Internet Things J. 2018, 5, 3810–3822. [Google Scholar] [CrossRef] [Green Version]
- Pandey, P.; Litoriya, R. Elderly care through unusual behavior detection: A disaster management approach using IoT and intelligence. IBM J. Res. Dev. 2020, 64, 15:1–15:11. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. Continuous Patient Monitoring with a Patient–Centric Agent: A Block Architecture. IEEE Access 2018, 6, 32700–32726. [Google Scholar] [CrossRef]
- Hameed, S.S.; Hassan, W.H.; Latiff, L.A.; Ghabban, F. A systematic review of security and privacy issues in the internet of medical things; the role of machine learning approaches. PeerJ Comput. Sci. 2021, 7, e414. [Google Scholar] [CrossRef] [PubMed]
- Nanayakkara, N.; Halgamuge, M.; Syed, A. Security and Privacy of Internet of Medical Things (IoMT) Based Healthcare Applications: A Review. In Proceedings of the International Conference on Advances in Business Management and Information Technology, Istanbul, Turkey, 11 June–11 July 2019. [Google Scholar]
- Dang, L.M.; Piran, M.; Han, D.; Min, K.; Moon, H. A survey on internet of things and cloud computing for healthcare. Electronics 2019, 8, 768. [Google Scholar] [CrossRef] [Green Version]
- Newaz, A.; Sikder, A.K.; Rahman, M.A.; Uluagac, A.S. A Survey on Security and Privacy Issues in Modern Healthcare Systems: Attacks and Defenses. ACM Trans. Comput. Healthc. 2021, 2, 27. [Google Scholar] [CrossRef]
- Firouzi, F.; Rahmani, A.M.; Mankodiya, K.; Badaroglu, M.; Merrett, G.V.; Wong, P.; Farahani, B. Internet-of-Things and big data for smarter healthcare: From device to architecture, applications and analytics. Future Gener. Comput. Syst. 2018, 78, 583–586. [Google Scholar] [CrossRef] [Green Version]
- Rahmani, A.M.; Gia, T.N.; Negash, B.; Anzanpour, A.; Azimi, I.; Jiang, M.; Liljeberg, P. Exploiting smart e-Health gateways at the edge of healthcare Internet-of-Things: A fog computing approach. Future Gener. Comput. Syst. 2018, 78, 641–658. [Google Scholar] [CrossRef]
- Wei, K.; Zhang, L.; Guo, Y.; Jiang, X. Health Monitoring Based on Internet of Medical Things: Architecture, Enabling Technologies, and Applications. IEEE Access 2020, 8, 27468–27478. [Google Scholar] [CrossRef]
- Gupta, S.; Venugopal, V.; Mahajan, V.; Gaur, S.; Barnwal, M.; Mahajan, H. HIPAA, GDPR and Best Practice Guidelines for preserving data security and privacy-What Radiologists should know. In Proceedings of the European Congress of Radiology-ECR 2020, Vienna, Austria, 26 February–1 March 2020. Poster Number C-13220. [Google Scholar]
- Jaigirdar, F.T.; Rudolph, C.; Bain, C. Can I Trust the Data I See? A Physician’s Concern on Medical Data in IoT Health Architectures. In Proceedings of the Australasian Computer Science Week Multiconference, Sydney, Australia, 29–31 January 2019; pp. 1–10. [Google Scholar]
- Goud, N. Malware and Ransomware Attack on Medical Devices. Available online: https://www.cybersecurity-insiders.com/malware-and-ransomware-attack-on-medical-devices/ (accessed on 28 April 2021).
- Sun, Y.; Lo, F.P.-W.; Lo, B. Security and Privacy for the Internet of Medical Things Enabled Healthcare Systems: A Survey. IEEE Access 2019, 7, 183339–183355. [Google Scholar] [CrossRef]
- Landau, O.; Cohen, A.; Gordon, S.; Nissim, N. Mind your privacy: Privacy leakage through BCI applications using machine learning methods. Knowl.-Based Syst. 2020, 198, 105932. [Google Scholar] [CrossRef]
- Bolton, T.; Dargahi, T.; Belguith, S.; Al-Rakhami, M.S.; Sodhro, A.H. On the security and privacy challenges of virtual assistants. Sensors 2021, 21, 2312. [Google Scholar] [CrossRef]
- Xing, K.; Srinivasan, S.S.R.; Jose, M.; Li, J.; Cheng, X. Attacks and countermeasures in sensor networks: A survey. In Network Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 251–272. [Google Scholar]
- Bostami, B.; Ahmed, M.; Choudhury, S. False Data Injection Attacks in Internet of Things. In Performability in Internet of Things; Springer: Berlin/Heidelberg, Germany, 2019; pp. 47–58. [Google Scholar]
- Rahman, M.A.; Mohsenian-Rad, H. False data injection attacks with incomplete information against smart power grids. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 3153–3158. [Google Scholar]
- Hei, X.; Du, X.; Wu, J.; Hu, F. Defending resource depletion attacks on implantable medical devices. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM 2010, Miami, FL, USA, 6–10 December 2010; pp. 1–5. [Google Scholar]
- Zhang, M.; Raghunathan, A.; Jha, N.K. MedMon: Securing medical devices through wireless monitoring and anomaly detection. IEEE Trans. Biomed. Circuits Syst. 2013, 7, 871–881. [Google Scholar] [CrossRef]
- Qu, G.; Yuan, L. Design THINGS for the Internet of Things—An EDA perspective. In Proceedings of the 2014 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 3–6 November 2014; pp. 411–416. [Google Scholar]
- Mosenia, A.; Jha, N.K. A comprehensive study of security of internet-of-things. IEEE Trans. Emerg. Top. Comput. 2016, 5, 586–602. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Tyagi, S.; Kumar, N. Machine learning models for secure data analytics: A taxonomy and threat model. Comput. Commun. 2020, 153, 406–440. [Google Scholar] [CrossRef]
- Zuhair, H.; Selamat, A.; Krejcar, O. A Multi-Tier Streaming Analytics Model of 0-Day Ransomware Detection Using Machine Learning. Appl. Sci. 2020, 10, 3210. [Google Scholar] [CrossRef]
- Fernandez Maimo, L.; Huertas Celdran, A.; Perales Gomez, A.L.; Garcia Clemente, F.J.; Weimer, J.; Lee, I. Intelligent and dynamic ransomware spread detection and mitigation in integrated clinical environments. Sensors 2019, 19, 1114. [Google Scholar] [CrossRef] [Green Version]
- Yaacoub, J.-P.A.; Noura, M.; Noura, H.N.; Salman, O.; Yaacoub, E.; Couturier, R.; Chehab, A. Securing internet of medical things systems: Limitations, issues and recommendations. Future Gener. Comput. Syst. 2020, 105, 581–606. [Google Scholar] [CrossRef]
- Spiekermann, S. Ethical IT Innovation: A Value-Based System Design Approach; CRC Press: Boca Raton, FL, USA, 2015. [Google Scholar]
- Bahşi, H.; Nõmm, S.; La Torre, F.B. Dimensionality reduction for machine learning based iot botnet detection. In Proceedings of the 2018 15th International Conference on Control, Automation, Robotics and Vision (ICARCV), Singapore, 18–21 November 2018; pp. 1857–1862. [Google Scholar]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. IoT malicious traffic identification using wrapper-based feature selection mechanisms. Comput. Secur. 2020, 94, 101863. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT security techniques based on machine learning: How do IoT devices use AI to enhance security? IEEE Signal Process. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]
- Sehatbakhsh, N.; Alam, M.; Nazari, A.; Zajic, A.; Prvulovic, M. Syndrome: Spectral analysis for anomaly detection on medical iot and embedded devices. In Proceedings of the 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 30 April–4 May 2018; pp. 1–8. [Google Scholar]
- Abdaoui, A.; Al-Ali, A.; Riahi, A.; Mohamed, A.; Du, X.; Guizani, M. Secure medical treatment with deep learning on embedded board. In Energy Efficiency of Medical Devices and Healthcare Applications; Elsevier: Amsterdam, The Netherlands, 2020; pp. 131–151. [Google Scholar]
- Rathore, H.; Wenzel, L.; Al-Ali, A.K.; Mohamed, A.; Du, X.; Guizani, M. Multi-layer perceptron model on chip for secure diabetic treatment. IEEE Access 2018, 6, 44718–44730. [Google Scholar] [CrossRef]
- Ben Amor, L.; Lahyani, I.; Jmaiel, M. AUDIT: Anomalous data detection and Isolation approach for mobile healThcare systems. Expert Syst. 2020, 37, e12390. [Google Scholar] [CrossRef]
- Khan, F.A.; Haldar, N.A.H.; Ali, A.; Iftikhar, M.; Zia, T.A.; Zomaya, A.Y. A continuous change detection mechanism to identify anomalies in ECG signals for WBAN-based healthcare environments. IEEE Access 2017, 5, 13531–13544. [Google Scholar] [CrossRef]
- Kintzlinger, M.; Cohen, A.; Nissim, N.; Rav-Acha, M.; Khalameizer, V.; Elovici, Y.; Shahar, Y.; Katz, A. CardiWall: A Trusted Firewall for the Detection of Malicious Clinical Programming of Cardiac Implantable Electronic Devices. IEEE Access 2020, 8, 48123–48140. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Djallel, H.; Choo, K.-K.R. Deep Learning-Based Intrusion Detection for Distributed Denial of Service Attack in Agriculture 4.0. Electronics 2021, 10, 1257. [Google Scholar] [CrossRef]
- NG, B.A.; Selvakumar, S. Anomaly detection framework for Internet of things traffic using vector convolutional deep learning approach in fog environment. Future Gener. Comput. Syst. 2020, 113, 255–265. [Google Scholar]
- Priyadarshini, R.; Barik, R.K. A deep learning based intelligent framework to mitigate DDoS attack in fog environment. J. King Saud Univ.-Comput. Inf. Sci. 2019, in press. [Google Scholar] [CrossRef]
- Sudqi Khater, B.; Wahab, A.; Bin, A.W.; Idris, M.Y.I.B.; Abdulla Hussain, M.; Ahmed Ibrahim, A. A lightweight perceptron-based intrusion detection system for fog computing. Appl. Sci. 2019, 9, 178. [Google Scholar] [CrossRef] [Green Version]
- Fantacci, R.; Nizzi, F.; Pecorella, T.; Pierucci, L.; Roveri, M. False data detection for fog and internet of things networks. Sensors 2019, 19, 4235. [Google Scholar] [CrossRef] [Green Version]
- De Donno, M.; Donaire Felipe, J.M.; Dragoni, N. ANTIBIOTIC 2.0: A Fog-based Anti-Malware for Internet of Things. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Stockholm, Sweden, 17–19 June 2019; pp. 11–20. [Google Scholar]
- Alrashdi, I.; Alqazzaz, A.; Alharthi, R.; Aloufi, E.; Zohdy, M.A.; Ming, H. FBAD: Fog-based attack detection for IoT healthcare in smart cities. In Proceedings of the 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 10–12 October 2019; pp. 515–522. [Google Scholar]
- Kumar, P.; Gupta, G.P.; Tripathi, R. An ensemble learning and fog-cloud architecture-driven cyber-attack detection framework for IoMT networks. Comput. Commun. 2021, 166, 110–124. [Google Scholar] [CrossRef]
- Hameed, S.S.; Hassan, W.H.; Latiff, L.A. An Efficient Fog-Based Attack Detection Using Ensemble of MOA-WMA for Internet of Medical Things. In Innovative Systems for Intelligent Health Informatics; Springer: Cham, Switzerland, 2021; pp. 774–785. [Google Scholar]
- Cisco, C. Fog Computing and the Internet of Things: Extend the Cloud to Where the Things Are. Электронный Ресурс. 2015. Available online: https://www.cisco.com/c/dam/en_us/solutions/trends/iot/docs/computing-overview.pdf (accessed on 10 March 2019).
- OpenFog Consortium Architecture Working Group. OpenFog reference architecture for fog computing. OPFRA001 2017, 162, 20817. [Google Scholar]
- Alaei, P.; Noorbehbahani, F. Incremental anomaly-based intrusion detection system using limited labeled data. In Proceedings of the 2017 3th International Conference on Web Research (ICWR), Tehran, Iran, 19–20 April 2017; pp. 178–184. [Google Scholar]
- Muallem, A.; Shetty, S.; Pan, J.W.; Zhao, J.; Biswal, B. Hoeffding tree algorithms for anomaly detection in streaming datasets: A survey. J. Inf. Secur. 2017, 8, 339–361. [Google Scholar] [CrossRef] [Green Version]
- Gama, J.; Medas, P.; Rodrigues, P. Learning decision trees from dynamic data streams. In Proceedings of the 2005 ACM Symposium on Applied computing, New York, NY, USA, 13–17 March 2005; pp. 573–577. [Google Scholar]
- Holmes, G.; Kirkby, R.; Pfahringer, B. Stress-testing hoeffding trees. In Proceedings of the European Conference on Principles of Data Mining and Knowledge Discovery, Porto, Portugal, 3–7 October 2005; pp. 495–502. [Google Scholar]
- Kolter, J.Z.; Maloof, M.A. Dynamic weighted majority: An ensemble method for drifting concepts. J. Mach. Learn. Res. 2007, 8, 2755–2790. [Google Scholar]
- Littlestone, N.; Warmuth, M.K. The weighted majority algorithm. Inf. Comput. 1994, 108, 212–261. [Google Scholar] [CrossRef] [Green Version]
- Moustafa, N. New Generations of Internet of Things Datasets for Cybersecurity Applications based Machine Learning: Ton_iot datasets. In Proceedings of the eResearch Australasia Conference, Brisbane, Australia, 21–25 October 2019. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Portmann, M. Netflow datasets for machine learning-based network intrusion detection systems. arXiv 2020, arXiv:2011.09144. [Google Scholar]
- Bhatia, N. Survey of nearest neighbor techniques. arXiv 2010, arXiv:1007.0085. [Google Scholar]












| Type | Description | Examples |
|---|---|---|
Implantable  | They are implanted in human organs. | Hip implants, cardiac pacemakers, implanted insulin pumps, and hearing implanted devices. |
Wearable | Humans wear these devices. | Smartwatch, fitness devices, etc. |
Ambient | These devices are for monitoring human behaviors. | Telemetry devices for patient and remote elderly monitoring. |
Stationary | These devices are used inside hospitals. | Imaging devices with connectivity, such as X-rays and lab devices. |
| Layer | Attacks | References |
|---|---|---|
| Device | Physical sensor/node tampering | [17] |
| False data injection | [18,19] | |
| Resource depletion attacks (battery drain, sleep deprivation, buffer overflow) | [20] | |
| Side-channel | [7,21] | |
| Hardware Trojan | [22,23] | |
| Eavesdropping | [24] | |
| Ransomware | [25,26] | |
| Network | Denial of Service (DoS) and distributed DoS (DDoS) | [24,27] |
| Man in the middle (MIM) | [27] | |
| Eavesdropping attack | [24] | |
| Replay | [27,28] | |
| Botnet | [29] | |
| Jamming | [14] | |
| Flooding | [24,30] |
| Individual Sensor Dataset | Method | Average Accuracy (%) | Average Time (s) | Average Memory (MiB) |
|---|---|---|---|---|
| IoT-fridge | IKNN | 99.72 | 8.96 | 2.8 |
| INB | 99.93 | 3.16 | 1.80 | |
| HTMC | 99.42 | 1.97 | 0.61 | |
| HTNB | 99.92 | 2.08 | 0.61 | |
| HTNBA | 99.92 | 2.04 | 0.61 | |
| WHTE | 99.95 | 5.58 | 2.90 | |
| Garage door | IKNN | 99.80 | 9.08 | 2.51 |
| INB | 99.98 | 2.78 | 2.30 | |
| HTMC | 98.19 | 2.37 | 0.71 | |
| HTNB | 99.98 | 3.30 | 0.71 | |
| HTNBA | 99.96 | 2.28 | 0.71 | |
| WHTE | 99.99 | 8.68 | 3.99 | |
| GPS tracker | IKNN | 99.79 | 9.32 | 2.46 |
| INB | 99.34 | 3.25 | 2.53 | |
| HTMC | 90.34 | 32.32 | 0.79 | |
| HTNB | 99.73 | 42.13 | 0.79 | |
| HTNBA | 99.76 | 25.96 | 0.79 | |
| WHTE | 99.80 | 80.15 | 4.19 | |
| Modbus | IKNN | 100.00 | 9.85 | 3.16 |
| INB | 100.00 | 2.70 | 2.82 | |
| HTMC | 100.00 | 0.67 | 0.48 | |
| HTNB | 100.00 | 1.15 | 0.48 | |
| HTNBA | 100.00 | 1.05 | 0.48 | |
| WHTE | 100.00 | 3.74 | 3.87 | |
| Motion light | IKNN | 99.80 | 10.59 | 3.04 |
| INB | 98.42 | 3.92 | 3.23 | |
| HTMC | 96.55 | 13.60 | 0.95 | |
| HTNB | 96.55 | 13.55 | 0.95 | |
| HTNBA | 99.87 | 11.78 | 0.95 | |
| WHTE | 99.90 | 40.46 | 5.25 | |
| Thermostat | IKNN | 99.90 | 8.38 | 3.00 |
| INB | 100.00 | 2.96 | 2.94 | |
| HTMC | 100.00 | 1.52 | 0.72 | |
| HTNB | 100.00 | 2.05 | 0.72 | |
| HTNBA | 100.00 | 1.90 | 0.72 | |
| WHTE | 100.00 | 5.67 | 4.45 | |
| Weather sensor | IKNN | 99.82 | 9.51 | 2.75 |
| INB | 99.95 | 2.83 | 1.81 | |
| HTMC | 99.98 | 1.24 | 0.54 | |
| HTNB | 99.95 | 1.75 | 0.54 | |
| HTNBA | 99.97 | 1.58 | 0.54 | |
| WHTE | 100.0 | 5.83 | 3.68 |
| Classifiers | ||||||
|---|---|---|---|---|---|---|
| IKNN | INB | HTMC | HTNB | HTNBA | WHTE | |
| Number of Datasets | 7 | 7 | 7 | 7 | 7 | 7 |
| Sum | 698.83 | 697.62 | 684.48 | 696.13 | 699.48 | 699.62 |
| Average | 99.83 | 99.66 | 97.78 | 99.45 | 99.93 | 99.95 |
| Details of Result | ||||||
| Source | SS | df | MS | F | p-value | |
| Between classifiers | 24.08 | 5 | 4.82 | 2.00 | 0.10 | |
| Within classifiers | 86.52 | 36 | 2.40 | - | - | |
| Total | 110.61 | 41 | - | - | - | |
| Classifiers | ||||||
|---|---|---|---|---|---|---|
| IKNN | INB | HTMC | HTNB | HTNBA | WHTE | |
| Datasets # | 7 | 7 | 7 | 7 | 7 | 7 |
| Sum | 65.69 | 21.60 | 53.69 | 66.01 | 46.59 | 150.11 |
| Average | 9.38 | 3.09 | 7.67 | 9.43 | 6.66 | 21.44 |
| Details of Result | ||||||
| Source | SS | df | MS | F | p-value | |
| Between classifiers | 1366.34 | 5 | 273.27 | 1.27 | 0.30 | |
| Within classifiers | 7743.23 | 36 | 215.09 | - | - | |
| Total | 9109.57 | 41 | - | - | - | |
| Classifiers | ||||||
|---|---|---|---|---|---|---|
| IKNN | INB | HTMC | HTNB | HTNBA | WHTE | |
| Datasets # | 7 | 7 | 7 | 7 | 7 | 7 |
| Sum | 19.72 | 17.43 | 4.80 | 4.80 | 4.80 | 28.33 |
| Average | 2.82 | 2.49 | 0.69 | 0.69 | 0.69 | 4.05 |
| Details of Result | ||||||
| Source | SS | df | MS | F | p-value | |
| Between classifiers | 71.56 | 5 | 14.31 | 88.33 | 2.5 × 10−19 | |
| Within classifiers | 5.83 | 36 | 0.16 | - | - | |
| Total | 77.39 | 41 | - | - | - | |
| Dataset | Method | Average Accuracy (%) | Average Time (s) | Average Memory (MiB) | Average Precision (Normal) | Average Precision (Attack) | Average Recall (Normal) | Average Recall (Attack) |
|---|---|---|---|---|---|---|---|---|
| NetFlow-ToNIoT | IKNN | 98.79 | 184.69 | 1.15 | 98.8 | 98.9 | 98.82 | 88.22 |
| INB | 97.62 | 8.47 | 0.22 | 96.7 | 95.3 | 94.4 | 98.7 | |
| HTMC | 99.01 | 3.90 | 0.08 | 99.6 | 99.6 | 99.6 | 99.6 | |
| HTNB | 98.94 | 5.75 | 0.08 | 99.5 | 98.2 | 98.91 | 99.7 | |
| HTNBA | 99.01 | 5.02 | 0.08 | 99.7 | 99.7 | 98.99 | 99.1 | |
| WHTE | 100.00 | 12.89 | 0.37 | 100.00 | 100.00 | 100.00 | 100.00 |
| Ref. | Domain | Architecture | Lightweight | Device Specs | Detection | Best Testing Accuracy (%) | Type/Name of Dataset | Classification Type | Type of Learning | Details on IoMT System and Fog Architecture | Complexity Metrics | Statistical Comparison | Splitting Method |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [45] | IoMT | Cloud-Fog | No | CPU 2.20 GHz (10 cores, 13.75 MB L3 Cache), and 128 GB RAM | Network-based | 96.35 | Network packet/ToNIoT | Binary | Batch | No | Not considered | No | Holdout Train-test (80:20) |
| [44] | IoMT | Fog | No | Intel core i7 CPU processor and 16 GB RAM. | Network-based | 98.19 | Network packet/NSL-KDD | Binary | Batch | No | Not considered | No | Holdout Train-test (80:20) |
| [38] | Agriculture 4.0 | Fog | No | Google Collaboratory supplied by GPU | Network-based | 98.00 | Network packet (CIC-DDoS2019 TON_IoT) | Multiclass | Batch | No | Not considered | No | Holdout Train-test (80:20) |
| [39] | IoT | Fog | No | Core (TM) i7- 6700 processor with 16 GB RAM | Network-based | 93.44 | Network packet (Bot-IoT) | Multiclass | Batch | No | Not considered | No | Holdout Train-test |
| [40] | IoT | Fog | No | - | Network-based | 98.88 | Network packet (Hogzilla Dataset) | Binary | Batch | No | Not considered | No | Holdout Train-test |
| This work | IoMT | Edge-Fog | Yes | CPUs ≈ 2.2 GHz (4 cores, 3 MB L3 Cache), and 8 GB RAM | Hybrid (Host and Network-based) | 100.00 | NetFlow and Sensors datasets (ToNIoT sensors and NetFlowToNIoT) | Multiclass for sensors and binary for NetFlow | Incremental | yes | Considered | Yes | Windowing (test-train) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hameed, S.S.; Selamat, A.; Abdul Latiff, L.; Razak, S.A.; Krejcar, O.; Fujita, H.; Ahmad Sharif, M.N.; Omatu, S. A Hybrid Lightweight System for Early Attack Detection in the IoMT Fog. Sensors 2021, 21, 8289. https://doi.org/10.3390/s21248289
Hameed SS, Selamat A, Abdul Latiff L, Razak SA, Krejcar O, Fujita H, Ahmad Sharif MN, Omatu S. A Hybrid Lightweight System for Early Attack Detection in the IoMT Fog. Sensors. 2021; 21(24):8289. https://doi.org/10.3390/s21248289
Chicago/Turabian StyleHameed, Shilan S., Ali Selamat, Liza Abdul Latiff, Shukor A. Razak, Ondrej Krejcar, Hamido Fujita, Mohammad Nazir Ahmad Sharif, and Sigeru Omatu. 2021. "A Hybrid Lightweight System for Early Attack Detection in the IoMT Fog" Sensors 21, no. 24: 8289. https://doi.org/10.3390/s21248289








