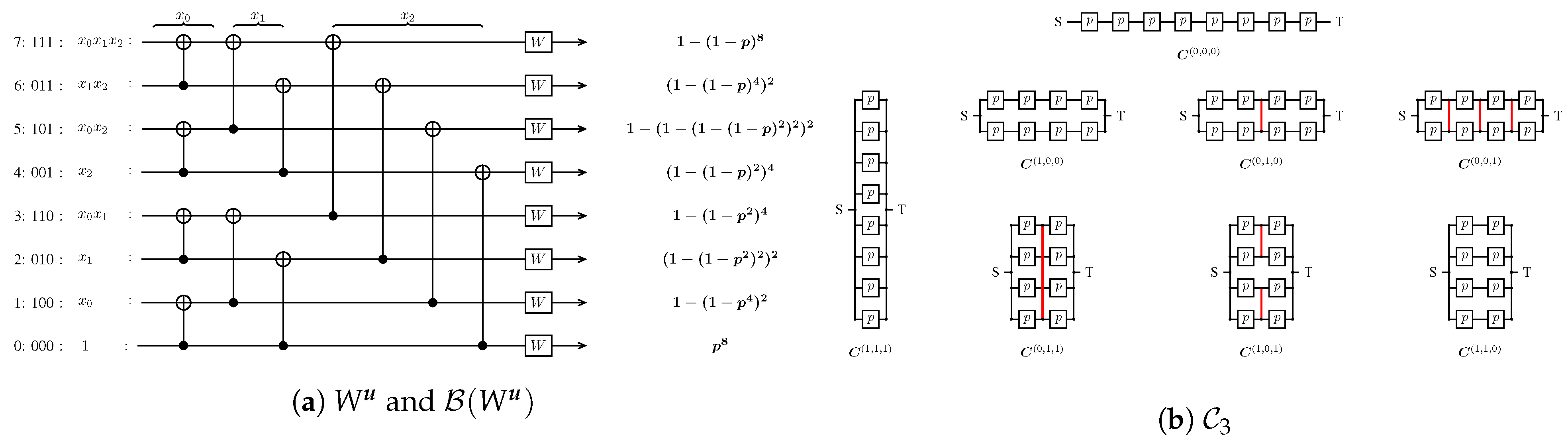Abstract
Monomial codes were recently equipped with partial order relations, a fact that allowed researchers to discover structural properties and efficient algorithm for constructing polar codes. Here, we refine the existing order relations in the particular case of the binary erasure channel. The new order relation takes us closer to the ultimate order relation induced by the pointwise evaluation of the Bhattacharyya parameter of the synthetic channels, which is still a partial order relation. To overcome this issue, we appeal to a related technique from network theory. Reliability network theory was recently used in the context of polar coding and more generally in connection with decreasing monomial codes. In this article, we investigate how the concept of average reliability is applied for polar codes designed for the binary erasure channel. Instead of minimizing the error probability of the synthetic channels, for a particular value of the erasure parameter p, our codes minimize the average error probability of the synthetic channels. By means of basic network theory results, we determine a closed formula for the average reliability of a particular synthetic channel, that recently gain the attention of researchers.
1. Introduction
One of the most striking developments in coding theory in the last two decades is probably the theory around polar codes. In his seminal article [1], Arikan demonstrated, for the first time, that one could achieve the capacity of binary discrete memoryless channels (BDMC), using both efficient encoding and efficient decoding algorithms. The so-called polar codes are now present in the fifth generation (5G) technology [2]. Indeed, polar code was elected as the standard coding technique for the control channel in support of the enhanced mobile broadband service, one of the major parts in 5G wireless network technology. Getting back to the three principal directions on which coding theory evolved, polar coding seemed to be unrelated to classical algebraic coding. Typically, the construction of polar codes does not come from any particular structure in the code, but rather from the process of channel polarization. However, polar codes are closely related to Reed–Muller codes, as pointed out even by Arikan [1]. Hence, polar and Reed-Muller code share a common algebraic description [3,4]. More precisely, they are sub-classes of a larger family of algebraic codes called decreasing monomial codes (DMC). The structure underlying DMCs and its algebraic formalism was applied in conjunction with other fields, e.g., in the context of quantum error correcting codes [5,6,7], post-quantum cryptography [8,9,10] and network reliability [11,12,13].
Several challenges regarding polar coding, among which the efficient construction of polar codes given a specific BDMC, were proposed. Arikan’s initial technique [1] was improved by several authors [14,15,16,17,18,19,20,21,22]. Let W denote a BDMC, m a fixed integer and a binary vector of length The main idea of the construction of polar codes is to estimate the reliability of the synthetic channels . For that, one might use the Bhattacharyya parameter , where p denotes the error probability of the channel W. The message parts of a polar code of length and dimension k are allocated to the k sub-channels having the smallest . Hence, one might classify the set of into “good” (reliable) or “bad” (non-reliable). For a fixed value of p, the values are put in order. In other words, when the parameter p is fixed, any distinct pair of channels satisfies either or In this case, we say that a channel is point-wise more reliable than a channel However, when considering the whole interval , ranking the synthetic channels becomes complicated. In this case, we say that is globally more reliable than , and write , if and only if
Estimating how reliable a synthetic channel is can be done in several ways, Monte Carlo simulations being among the most common ones. Arikan, in his seminal paper [1], proposed such a method for determining the error probability of each synthetic channel which yields a relatively efficient generating algorithm. It could be possible to employ recent development in Monte Carlo such as those in [23,24] in order to improve Arikan’s idea. However, the most efficient techniques for constructing polar codes are exploiting order relations between the synthetic channels. One of the most efficient techniques that orders the set of synthetic channels (with respect to the concept of globally more reliable), provides sub-linear complexity construction [14]. It exploits the existence of a partial order (denoted by ⪯) on the set of synthetic channels [4]. This partial order is compatible with the notion of being globally more reliable, i.e., Even though ⪯ provided a contribution to understanding polar codes, i.e., their structure and construction, simulations show that ⪯ is far from ordering optimally. Hence, in a recent article, ⪯ was refined [25]. Compared to Monte Carlo methods, the techniques based on order relations valid for polar codes require a small number of computations, only for a fraction of the synthetic channels, as they exploit the rules induced by the order relations.
In the analysis of the performance of several families of codes, among which are polar, Reed–Muller, cyclic and BCH codes, the communication channel that received a lot of attention is the binary erasure channel (). When polar codes are designed for (in this particular case, p denotes the erasure probability), all the synthetic channels are also . In this case, the erasure probability of is equal to the Bhattacharyya parameter of Here, we analyze this particular channel. Our choice is motivated by several results and methods. First of all, the simplicity of this channel makes the theoretical proofs significantly simpler and easier. Moreover, many of the properties that hold for the turn out to be valid for more general channel models. For example, the proof of Reed–Muller codes achieving the capacity of a communication channel started with the [26,27]. Codes that admit a doubly-transitive automorphism group or having large orbits under the action of their permutation group achieve the capacity of the [27,28]. In [29], the authors analyze threshold points for in the case of , a fact that allows them to propose sets of asymptotically “good” channels. Recently, in [30] the authors analyzed the Bhattacharyya parameter of polar codes for the using network reliability theory. They have proposed simple approximations of . These were used to determine sub-intervals of , where polar codes coincide with Reed–Muller codes. They have also managed to determine new sets of asymptotically “good” channels.
1.1. Polar Codes Are Strongly Decreasing Monomial Codes
Polar codes over the satisfy an order relation that is finer than . Hence, we define another order relation on the set of monomials on m variables , coming closer to the ≤ relation, i.e., we have
The relation allows one to compare monomials with equal degrees that were not comparable with respect to ⪯, e.g., The idea of came from the link between the set of monomials of degree d in and the set of partitions/Young diagrams inside the grid (see Proposition 3.7.8 in [3]). From that, looking at order relations on partitions came as a natural idea, and the most common one is the dominance order [31]. The order is exactly defined as the dominance order on partitions inside a fixed grid.
The main result in this section can be stated as follows
Theorem 1.
Polar codes over the binary erasure channel are strongly decreasing monomial codes.
In the proof of this theorem, we will need to demonstrate two useful properties of this new order
- given two monomials in such that , then, for any multiples with and we have where denotes the greatest common divisor of .
- two particular monomials are the key ingredients in the proof, We show that for all , and in general that any pair of monomials of degree 2 , satisfying that has the property for all
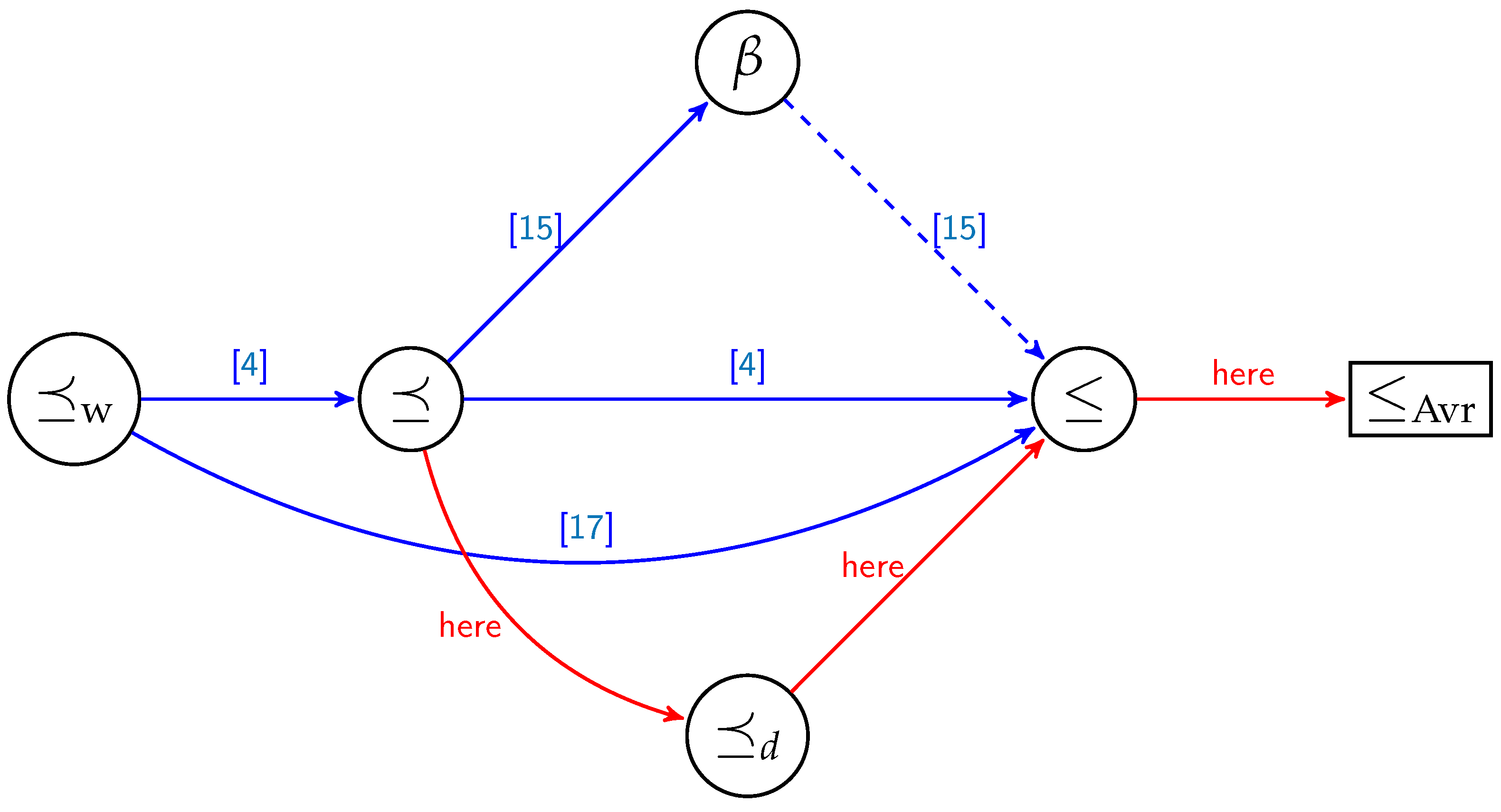
Even though gets us closer to the ultimate order relation ≤, we know that is a partial order relation. seems to perform as well as the order relation from [25], being much simpler to describe and analyze than the order in [25]. Furthermore, in [25] the authors determine new order relations based on some hypotheses which are not algebraically easy to express, and which are to be tested each time we change the parameters of the code. Figure 1 illustrates how our results fit into state-of-the-art order relations in conjunction with polar coding.
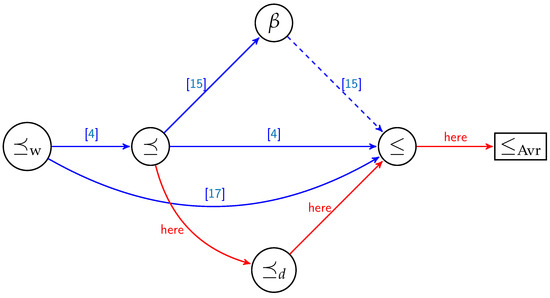
Figure 1.
Order () and preorder relations () for monomials codes over the . The connections in red are the results coming from this article. The dotted edge from to ≤ represents an order relation that is valid only for a sub-interval of
Now, as is thinner than ⪯, one could use it in order to determine new sets of comparable monomials and thus generate polar codes in a more efficient manner. Indeed, as more monomials are comparable with respect to , they induce new chains in the poset This enables us to reduce the number of non comparable elements and also the number of strongly decreasing monomial codes compared to decreasing monomial codes. These two ideas are being illustrated as possible methods for reducing the complexity of the construction algorithm, hence directing towards possible practical applications.
1.2. Average Reliability of Synthetic Channels
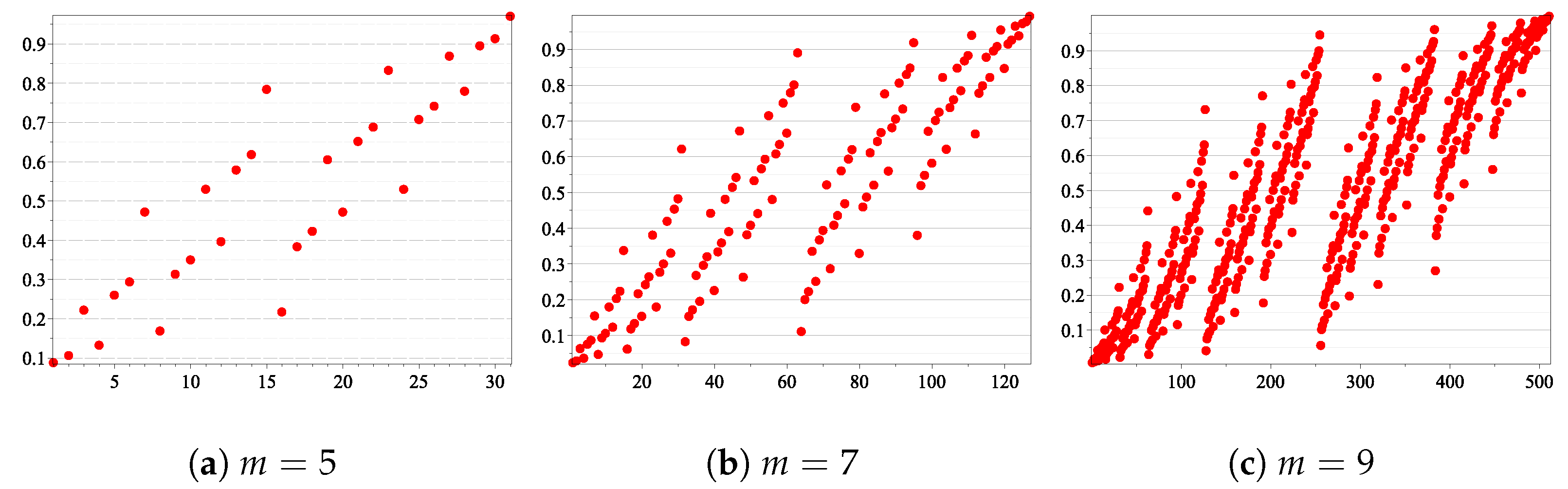
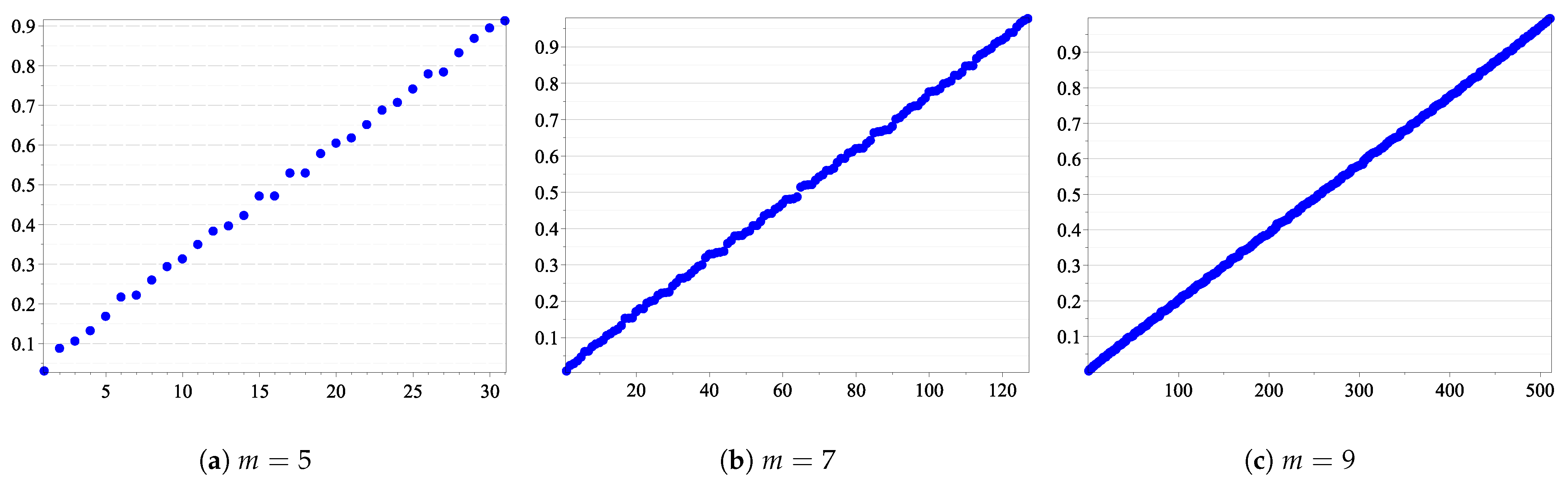
Hence, we are still left with elements that are not comparable and for which we need to compute In order to overcome this issue, we propose an alternative solution. Suppose that the erasure probability of the channel p changes with respect to the uniform distribution over the closed interval Instead of constructing, for each p, the corresponding polar code, we propose to construct the best polar code in average. More exactly, we consider the average reliability of the synthetic channels , , and choose those that minimize this quantity. As the average reliability induces a total order relation (see Figure 2), there is only one polar code for a given dimension and length. It is the linear code that minimizes the average error probability for all Hence, it might be less efficient than polar codes designed for a particular value of p, but it has the best performance on average.
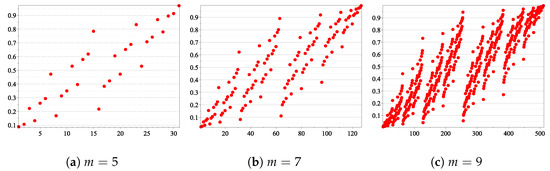
Figure 2.
Average Bhattacharyya parameter. On the x-axis are the integer values of the binary vectors , and on the y-axis are the values Avr().
The preorder induces a complementarity property with respect to the integral operator over , as defined in [32,33] in the case of two-terminal networks. We retrieve a similar property, i.e., where is the bit-wise complement of , in the context of monomial codes. Our simulations have shown that, considering the relation in the set of the synthetic channels, in each sub-interval , for , we have a rough proportion of binary vectors So, roughly speaking, a uniform distribution could be used to approximate the number of inside each sub-interval, with respect to However, our result is not constructive, in the sense that it does not fully characterize exactly the that belong to a specific interval. An answer to this question might provide an extremely efficient method for constructing polar codes and give much more insight into the synthetic channels
Threshold Points for Sharp Transitions
Determining the threshold point of is in general a difficult task [29,34]. In [29], the authors analyze a particular synthetic channel , for which asymptotic threshold points were determined. The conditions on i and m were further improved in [25]. Based on some basic notions and facts from network theory, we determine an exact formula for the average reliability of . The main result is
Theorem 2.
Let Then
This allows us to determine the exact threshold point of this particular channel. Moreover, we demonstrate that for any , the channel has an average Bhattacharyya parameter that tends to zero when m goes to infinity, i.e., is asymptotically “good” on average. Another consequence of our formula is that for any monomial with is such that tends to zero when m goes to infinity.
Another significant implication of our result is that any synthetic channel in the is asymptotically “good” on average, for any
1.3. Outline of the Article
The main concepts, notations and properties that are used all over the paper are introduced in Section 2. We introduce the background on coding, referring to the monomial codes in Section 2.1, the polar codes in Section 2.2 and to various manners of comparing them in Section 2.3. The two-terminal networks and their reliability are discussed in Section 2.4. The similarity between the behavior of the Bhattacharyya parameters and the reliability polynomial in assessing the monomial codes is emphasized in Section 2.5. The relationship between the order relations and the corresponding order structures over the set of polar codes over the binary erasure channel is studied in Section 3. The main result in this section proves that the polar codes over the binary erasure channel are strongly decreasing monomial codes. In the same section, two ideas pointing to possible practical applications of the order relation are developed. The concept of average reliability of a synthetic channel is introduced in Section 4. The properties of this operator are studied in Section 4.1 and the relation to the -expansion is presented in Section 4.2. Finally, the threshold points of the binary erasure polarization sub-channels are determined in Section 4.3. Simulations and numerical examples are included to illustrate all the new results. We conclude our article in Section 5.
2. Background and Preliminary Results
Let us begin by listing some of the usual notations from coding theory that are going to be used in this article. will denote the finite field with two elements Let be two strictly positive integers and A code of length n and dimension k is a vector sub-space of of dimension In this article, we focus out attention on a particular family or linear codes, namely monomial codes. W will be used to denote a communication channel with binary input and output from an alphabet In particular, we will focus on , where the output is , ? denoting an erasure and p being the erasure probability. For a more detailed reading of the subject, we recommend [35,36].
2.1. Monomial Codes
Monomial codes are a special class of structured codes. Informally, any code that admits a basis, in which each vector is the evaluation of a monomial, is called a monomial code. In general, monomial codes have a predefined length, i.e., Many of the notations, definitions, properties, and results presented in this section are taken from [3].
In this article, binary vectors of length m will be denoted using bold small letters, e.g., , with the convention that bits are ordered from left to right, being the least significant bit. We also define the bit-wise complement of by (as in [4]), where is the all-ones vector. The set will be ordered in a natural manner, using the mapping
and the natural order on the integers. Notice that we compute the value u regardless of the fact that Notice that the relation between and induces .
We consider multivariate polynomials and monomials defined over the polynomial ring The usual operators will be employed, i.e., for , we denote by the degree of f, the greatest common divisor of f and g. denotes the quotient of f and g.
Notation 1.
Let m be a strictly positive integer. We denote
- monomials: where
- support of a monomial: , where and
- a subset of the support of a monomial:
- the set of monomials:
Proposition 1
([37]). Let and order the elements in with respect to the decreasing index order. Define the evaluation function
Then, is a bijection defining an isomorphism between the vector spaces and
Now, we are ready to define the concept of monomial codes.
Definition 1
(Monomial code). Let be a finite set of monomials in m variables. The linear code defined by I is the vector subspace generated by that is called monomial code.
Proposition 2
([3]). For all , the dimension of the monomial code is equal to .
Remark 1.
The order Reed–Muller code is a monomial code with dimension
2.2. Polar Codes
In order to define polar codes, we have to introduce the concept of synthetic channels. Consider the channel transformation defined in the following manner.
Definition 2
(Synthetic channels). Let W be a BDMC with output alphabet and be the inputs and be the outputs of two copies of Define two new channels
For any , we define as in [4]. Moreover, we extend the notation to monomials, by where We are using the index m in to precisely identify the number of variables on which f is expressed. For example, if , we have
Definition 3.
Let W be a BDMC with output alphabet Then, the Bhattacharyya parameter of the channel W is
Remark 2.
Let W be a , then, we have that and
Definition 4.
The polar code of length and dimension k devised for the channel W is the linear code obtained by selecting the set of k synthetic channels with the smallest values among all .
Moreover, we define the relation
The relation (3) is called universal, i.e., two monomials satisfying are always comparable for any p and any This property can be used when constructing polar codes by storing a table with all such monomials. However, there might be several monomials bigger than f which are not comparable pairwise (see, for example, [4,14]). Indeed, one can easily verify that ≤ is a well-defined order relation (reflexive, anti-symmetric, and transitive), and thus, induces a poset on the set of monomials. In some particular cases, the order ≤ becomes total (all elements are ordered in a chain), e.g., when and . However, in general, ≤ is a partial order, even in the case of (starting from ), as pointed out in [3,11,30].
Proposition 3.
Let be an integer and Then, is a poset.
For simplification, when we refer to ordering the Bhattacharyya parameters, we will just write
2.3. Weakly Decreasing and Decreasing Monomial Codes
Definition 5.
Let f and g be two monomials in
- The order between f and g is defined as
- The ⪯ order between f and g is defined as
- -
- when and , we have
- -
- when we have
The two order relations and ⪯ are well defined. was already used in the case of polar codes, but in a completely different context by Mori and Tanaka in [17]. In their case, the purpose was to tighten the bounds of the error block probability of a polar code designed for the family.
Notice that is weaker than ⪯, meaning that The inverse is not always true: taking, for example, and it follows by definition that but 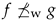 . We also remark that is the smallest element both for ⪯ and for , and we have
. We also remark that is the smallest element both for ⪯ and for , and we have
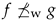 . We also remark that is the smallest element both for ⪯ and for , and we have
. We also remark that is the smallest element both for ⪯ and for , and we have
Definition 6.
Let f and g be two monomials in such that and
- We define the closed interval
- is called a decreasing set if and only if ( and ) implies .
- Let be a decreasing set. Then, is called a decreasing monomial code.
Polar codes were recently related to network theory. In [30], the authors make a connection between the Bhattacharyya parameter of a synthetic channel and the reliability polynomial of a two-terminal network. Following the same path, we introduce in the next subsection all the required preliminaries in reliability and network theory.
2.4. Two-Terminal Networks
Definition 7.
Let n be a strictly positive integer. We say that is a two-terminal network (2TN) of size n if is a network made of n identical devices, that has two distinct terminals: an input S, and an output T.
To any network, made of n devices we associate two parameters: width (w) and length (l), where w is the cardinal of a “minimal cut” separating S from T, and l is the cardinal of a “minimal path” from S to T, that satisfy
(see Theorem 3 in [38]). The number of devices n is known in the literature as the size of the network. When , we say that is a minimal 2TN [38].
The composition of and can be defined as in [38]. The resulting network is obtained by replacing each device in by a copy of . We will denote a composition by , the simplest possible being two devices in series , and two devices in parallel . The composition of with is , where . The set of all -size compositions will be denoted by , and the set of all compositions of width and length by (see Figure 3b).
Figure 3.
Combined circuit as defined by Arikan [1], the Bhattacharyya parameter of the corresponding synthetic channels and the compositions in .
Proposition 4
([39]). Let and Then, is a minimal 2TN of size length and width We also have
Theorem 3
([11]). There is a natural bijection between and the set of all , for any fixed positive integer
In Figure 3, we illustrate the bijection between the two aforementioned sets. More significant is the equality between the reliability polynomial of a composition and the Bhattacharyya parameter of , a fact that is visible from Figure 3b and proven in the next paragraph.
Reliability Polynomial
The reliability of is defined as the probability that S and T are connected (also known as -connectivity) [40]. One of the most common hypotheses considered in network theory is that devices are uniformly and identically supposed to close with a probability Hence, the reliability of , denoted by , can be expressed as a polynomial
The coefficients represent the number of paths from S to T of length i. Several properties regarding the coefficients , as well as complementarity relations between a 2TN and its dual , are detailed in [32,41] in the case of hammock networks.
2.5. Bhattacharyya Parameters and Reliability Polynomials
Theorem 4
([11]). Let , , and
where and .
Proposition 5
([25]). Let and Then
This condition expresses the duality of the two corresponding networks, namely , the dual of (see [11,32]). Notice that by (7), one has to analyze only with .
3. Polar Codes Are Strongly Decreasing Monomial Code Over the BEC
3.1. Definitions and Results
Definition 8.
The order between f and g is defined as
- when and , we have
- when we have
Definition 9.
Let f and g be two monomials in , such that and
- We define the closed interval
- is called a strongly decreasing set if, and only if, ( and ) implies .
- Let be a strongly decreasing set. Then, is called strongly decreasing monomial code.
Lemma 1.
The order is a well-defined order relation and forms a Poset.
The proof of this lemma comes directly from the definition of .
Remark 3.
Notice that implies that The converse is no longer true, take for example, the monomials and
Proposition 6.
Let f and g be two monomials with the same degree and be such that  and
and  . Then, we have
. Then, we have
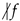 and
and 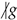 . Then, we have
. Then, we haveThe proof of Proposition 6 can be found in Appendix A. In particular, notice that if are co-prime, i.e., , then
Remark that when the condition on variable is not satisfied, the result does not hold, e.g., , but and are not comparable with respect to Before we get to our main theorem of this section, the following lemma is required.
Lemma 2.
Let , such that Then,
Corollary 1.
Let and s.t. Then, for any monomial satisfying , we have and
Theorem 5.
Polar codes over the binary erasure channel are strongly decreasing monomial codes.
The proof of Theorem 5 is given in Appendix A.
Theorem 6.
Reed–Muller codes are strongly decreasing monomial codes, i.e.,
Proof.
The proof follows from and (see Proposition 3.3.12 in [3]). □
3.2. Perspectives of Application of in the Construction of Polar Codes
State-of-the-art algorithms for constructing polar codes [14] are using the structure induced by the existing partial order relations on the set of monomials. As explained in [14], the complexity of the algorithm for construction of polar codes is dominated by the cardinality of the largest set of non comparable monomials with respect to Hence, a finer order relation than ⪯ could potentially decrease the complexity of such an algorithm. As is thinner than ⪯, we will seek, through examples, how many non-comparable monomials with respect to ⪯ are comparable with respect to Typically, our procedure can be used for a more efficient enumeration of sets of non-comparable elements in the new poset The longest antichain in the poset gives a direct intuition on how efficient the construction algorithm can be. Indeed, when estimating the reliability of the synthetic channels in order to construct a polar code, one need to estimate the reliability of the non comparable elements. Hence, having a finner poset, where the maximum length antichain becomes smaller, induces a more efficient construction algorithm. In order to make things clear, we will explain, in view of two distinct perspectives (reducing the number of non comparable elements and reducing the number of codes of fixed dimension), how induces more efficient construction rules for the polar code.
3.2.1. Reducing the Number of Non-Comparable Monomials
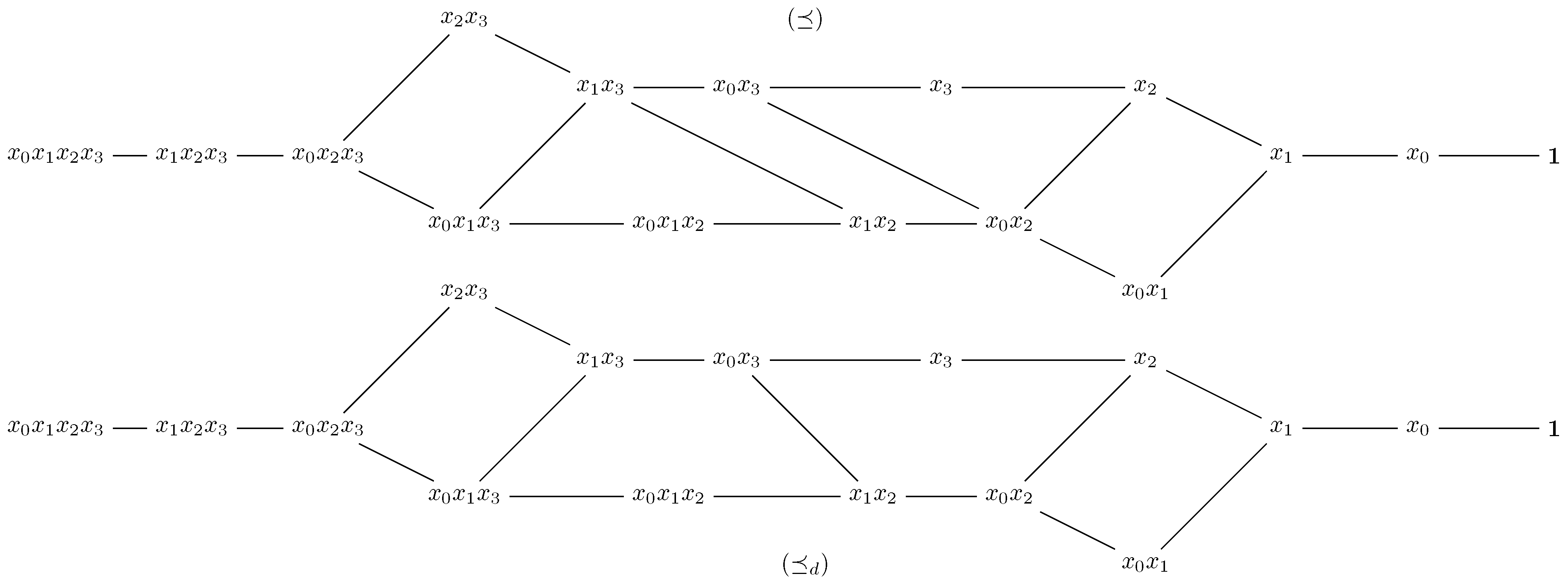
For , the middle of the poset is also a maximum length antichain. Let us explain the concept of middle of A monomial g is situated in the middle of the poset if any chain from g to (the infimum of the poset) has length equal to any chain from g to (the supremum of the poset). Clearly, two distinct monomial that are in the middle of the poset are non-comparable. Moreover, notice that not every poset admits a middle, with respect to our definition. For example, has a middle, since it is a graded poset (see [11,14,31] for more details). However, is not graded and it does not admit a middle. When (see Figure 4), the middle of is the set As is thinner than ⪯, it could be possible to reduce the number of non-comparable elements from the middle of Indeed, this fact can be validated through simulations, as we point out in Table 1.
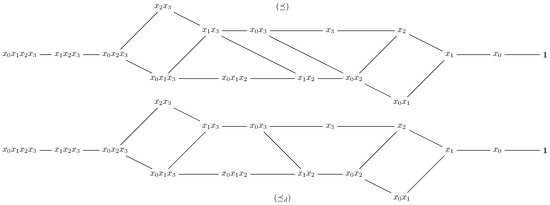
Figure 4.
The two-order relations ⪯ and for

Table 1.
Non comparable elements in the middle of .
Simulations
We have implemented an algorithm for generating all elements in the middle of For each value of m in , the elements in the set are displayed in Table 1. We choose to display the instead of g, where for , The main reason for this convention is that the elements in the middle of are the answers of a well-known problem in computer science, i.e., perfect subset sum problem. Indeed, if we carefully check the elements for each value of m, we discover that for any g in the middle of the poset
As one can notice from Table 1, the number of non comparable elements from the middle of decreases rapidly when the order relation is used. For example, when , we have decreased this number from 14 non comparable monomials, with respect to ⪯, to 3 distinct non comparable chains, with respect to
3.2.2. Reducing the Number of Codes
Another pertaining aspect when we deal with decreasing and strongly decreasing monomial codes is the estimation of codes for a fixed length and dimension It seems quite natural, in view of the relation between ⪯ and , to state that there are fewer strongly decreasing monomial codes of fixed length and dimension than decreasing monomial codes. Formally, we have
Lemma 3.
Let m be a strictly positive integer and Then the number of decreasing monomial code with and greater than or equal to the number of strongly decreasing monomial codes with and
The proof of this lemma is obvious and comes directly from the fact that any strongly decreasing monomial set I is necessarily a decreasing monomial set. However, the inverse is not always true.
Simulations
We have written an algorithm that computes the number of decreasing monomial codes for a fixed length and dimension. Our algorithm works recursively, by adding new monomials from to the previous sets of monomials of cardinality , in such a manner that the cardinality of the new sets does not exceed The algorithm outputs all possible decreasing monomials sets of cardinality k and then it checks which of them are also strongly decreasing monomial sets.
For small values of k, i.e., when , there are almost no differences between strongly decreasing and decreasing sets. However, for bigger values of k, we observe a significant reduction of the number of strongly decreasing monomial codes compared to decreasing monomial codes. In Table 2, we illustrate on a small example and the difference between the two sets. We choose to represent each monomial set I by

Table 2.
Decreasing and strongly decreasing monomial sets for .
4. Average Reliability of the Synthetic Channels
The geometric approach of the properties of a function by means of its subgraph and/or epigraph generated useful mathematical tools from the very beginning of the theory of functions. Measure, intersection, support and shape properties lead to applications in various domains: optimization, shape description and recognition, etc. Here, we propose a geometric approach in the field of polar coding. Recently, the concept of average reliability was introduced and analyzed in the context of all terminal reliability [42]. In view of Theorem 4, the Bhattacharyya parameter of a synthetic channel can be mapped into the reliability polynomial of a minimal two-terminal network. As a consequence, almost all constructive and efficient methods from network reliability can be applied to polar codes over BEC, by means of the Bhattacharyya parameter.
As the set of the synthetic channels cannot be totally ordered [4,25], we propose a different method to define the optimality of a synthetic channel. For that, we will check how reliable a channel is on average, i.e., we define
Definition 10.
Let m be a strictly positive integer and . The average reliability of is
Moreover, we define the relation
This notion of optimality has a meaning in the following context. Imagine that the communication channel is a with variable erasure probability, coming from different physical reasons. This means that either we choose a different polar code in function of the variations of p and in this case we obtain the best performance for each instance, or we choose a polar code and hope that on average it performs in an optimal way. The former strategy comes with the cost of computing for each value of p the corresponding polar code; as for the latter, the cost is minimal, since we construct only one polar code.
4.1. Properties
Lemma 4.
The relation is reflexive and transitive. In other words, is a preorder relation.
Our simulations have shown that up to , is also antisymmetric. However, this property might not be true in general. Indeed, one can easily find two distinct polynomials with integer coefficients defined over with values in , such that their integrals are equal.
Conjecture 1.
The relation is a preorder relation on the set of all synthetic channels.
All the same, we can overcome this by applying the following procedure.
Remark 4.
Let if, and only if, Let us extend the relation to the factor set naturally, using the relation between class representatives. Then, is a total order relation over Indeed, one can easily check that is antisymmetric over
Lemma 5.
Let m be a strictly positive integer, , and Then,
Proposition 7.
Let m be a strictly positive integer and be two binary vectors of length m, such that . Then,
In Table 3, we compute the of all the binary vectors for Notice that in this case, Proposition 7 applies, since we know that up to , the synthetic channels can be totally ordered over the [3,25]. Starting from , this property is no longer true. When and are no longer comparable, i.e., there is such that , we can still decide whether on average is optimal compared with The set of non-comparable pairs for is Notice that half of the pairs are coming from duality, i.e., if are not comparable, then are also non-comparable. However, these are ordered with respect to average reliability. The average reliability for the first 4 non-comparable pairs are . Hence, for the ordering with respect to the average reliability is 0,1,2,4,8,16,3,5,6,9, 10,17,12,18,20,7,24, and the rest can be completed by symmetry.

Table 3.
Average reliability of the synthetic channels.
Example 1.
The ordering induced by the average reliability.
Our simulations have shown that, considering the relation in the set of the synthetic channels, in each sub-interval , for , we have a rough proportion of binary vectors So, roughly speaking, a uniform distribution could be used to approximate the number of inside each sub-interval (illustrated in Figure 5), with respect to (see Table 4 for )
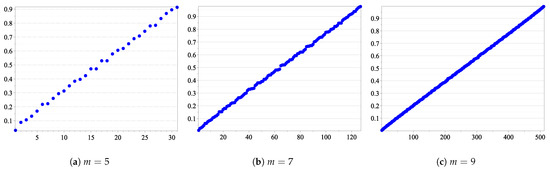
Figure 5.
Sorted for all u ∈ {0, 1}m.

Table 4.
Number of that satisfy , for ,
4.2. Relation to -Expansion
-expansion [15] is a well-known method for an efficient construction of polar codes. Hence, it is with no surprise that our results on average reliability determine possibly more refined choices of the variable Let us begin by defining the method.
In [15], the authors proved that for any , the order induced by on the sequence of synthetic channels respects the order relation In particular, this means that if then and this for any value of Some values of are of high interest, in particular , when W is designed for additive white Gaussian noise (AWGN). In the case of AWGN, the authors in [15] proposed a procedure in which an interval for is determined, an interval that converges to a value close to Notice that in [15], the order induced by is not valid for any signal to noise ratio value, but it tries to cover as much as possible the interval A natural question that one could raise is whether there is a -expansion for the average reliability, i.e., is there a real value such that and are identical over the set of binary vectors of length There is a significant difference between the two relations. In our case, not only that W is a BEC, but also the preorder induced by the average reliability is total over and holds for the entire interval
Remark 5.
By computer simulations, one can easily prove that for there is , such that the order induced by and the preorder induced by the average reliability coincide. It can be done by simply tacking .
Conjecture 2.

For , we did not find a value of β for which the two aforementioned relations are equal. Moreover, for , the number of elements with similar mutual relations with respect to the two relations is minimized (see Table 5).

Table 5.
Number of pairs satisfying for which 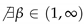 s.t.
s.t.
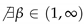 s.t.
s.t.
4.3. Threshold Points of the Binary Erasure Polarization Sub-Channels
The fact that when m goes to infinity the Bhattacharyya polynomial has a sharp transition from zero to one when m goes to infinity has already been proven ([34]). More exactly, for any , there exists a point for which in its vicinity passes from very small values (close to zero) to very high values (close to one). Formally speaking, we have
Lemma 6
([34]).
However, finding the point where this transition holds is not trivial (see [15,29]). Here, we will use the average reliability to determine this point for some specific channels.
Lemma 7.
A particular interesting channel analyzed in [25,29] is the synthetic channel More exactly, the authors analyze the sharp transition of from 0 to 1 when m tends to infinity, in function of the limit Here, we will give an exact formula for the average reliability of . This result combined with Lemma 7 will allow us to obtain a finer approximation of To achieve our goal, we will look at the corresponding 2TN, namely at . For simplification, we use and Notice that
Theorem 7.
Proof.
In order to prove our result, we need to demonstrate that
The proof is based on an inclusion-exclusion argument. Denote by the set of paths of length i from S to T for the . This leads to
Any path of length i with is composed of at least one path of length l, hence we have w choices for fixing a path of length l and choices for the remaining positions. However, in the choices, we might count other l length paths. Hence, we need to subtract the over-counting, which is all the combinations of two length l paths, i.e., , times the number of choices for the remaining positions, i.e., Now, we need to add all the paths that are composed of at least 3 l paths which equals and so on till we reached the last level, i.e., □
Theorem 8.
Proof.
□
Basically, we have
Corollary 2.
Based on Theorem 8, we can establish new classes of asymptotically “good” channels. For that, we will need the following result.
Lemma 8.
Theorem 8, Lemma 8 and Lemma 7 imply the following result.
Corollary 3.
Let m be a strictly positive integer and Then,
- for any we have and
- for any we have and
Another direct consequence of our results is that for any , the monomial is highly reliable on average. Hence, all the monomials are also highly reliable in average, as their average reliability tends to zero when m goes to infinity. Moreover, f becomes unreliable on average for The values are to be considered in more detail.
Corollary 4.
Let m be a strictly positive integer and Then, for any with , we have that when In other words, any synthetic channel in the is asymptotically “good” on average.
5. Conclusions and Perspectives
A complete characterization of the Bhattacharyya parameter of synthetic channels of a monomial code is an open problem that has attracted a lot of attention in the last decade. Even for the particular case of binary erasure channel, the question remains unanswered. However, the implications of such a result are of high importance in coding theory, especially in polar coding. In this article, we make a step forward by proposing an order relation that decreases the gap between state-of-the-art and the ultimate partial order relation for the Bhattacharyya parameter of synthetic channels. The advantage of this approach is that our algebraic description is rather easy to implement and analyze, compared to other order relations such as [25]. Simulations show that is a valid order relation on binary symmetric channel, and a deeper inspection of [25], and our work could potentially determine an algebraic description that fits the latest results.
The order relation proposed here could be employed as a new construction rule for polar codes. As is thinner than ⪯, it enables two reductions:
- the number of non-comparable monomials in the middle of is significantly reduced by means of ,
- the number of strongly decreasing monomial codes is less than the number of decreasing monomial codes for fixed length and dimension.
Hence, these two properties open the perspectives of a more efficient construction algorithm for strongly decreasing monomial codes, and hence for polar codes.
As the relations on the Bhattacharyya parameter are all partial orders, we have proposed an alternative solution for ordering the synthetic channels. For that, we have used the concept of average reliability, borrowed from network theory. Instead of the local evaluation of the Bhattacharyya parameter, we propose a global one, by evaluating the integral, i.e., by measuring its global average behavior. Hence, we rank the synthetic channels using a preorder relation , given by the value of the integral. Our result is not constructive, in the sense that it does not fully characterize the channels that belong to a specific interval. An answer to this question might provide an extremely efficient method for constructing polar codes and give much more insight into the synthetic channels
Author Contributions
Conceptualization, V.-F.D. and G.C.; methodology, V.-F.D.; software, V.-F.D.; validation, V.-F.D. and G.C.; formal analysis, V.-F.D. and G.C.; investigation, V.-F.D.; resources, V.-F.D. and G.C.; writing—original draft preparation, V.-F.D. and G.C. All authors have read and agreed to the published version of the manuscript.
Funding
V-F. Dragoi is supported by a grant of the Romanian Ministry of Education and Research, CNCS- UEFISCDI, project number PN-III-P1-1.1-PD-2019-0285, within PNCDI III.
Data Availability Statement
The data presented in this study are available within the article.
Acknowledgments
The authors are thankful to anonymous reviewers for their valuable suggestions and comments to improve the quality of the article.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Proofs of Results from Section 3
Appendix A.1. Proof of Proposition 6
Proposition
(6). Let f and g be two monomial having the same degree and be such that 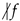 and
and 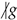 . Then we have
. Then we have
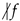 and
and 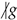 . Then we have
. Then we haveProof.
Let and with Also, let and There are several cases to be examined here:
- If or then the relation can easily be verified by using the definition of
- If there is an integer s.t. and then the relation can easily be verified as in the previous step.
- If there are two distinct integers s.t. and then two cases have to be considered.
- -
- If then we have and , which implies the following orderingCombining Equation (A2) with the definition of we obtain the desired result, i.e.,
- -
- then we have and which implies the following orderingNow, since it might be possible to have , which implies a violation of the partial sum conditions in the definition of If the next partial sum changes the sign, i.e., , by setting we have the following inequalitiesThis impliesHowever, since the Equation A6) becomes impossible, which completes the proof.
□
Appendix A.2. Proof of Lemma 2
Lemma
(2). Let , such that Then
Proof.
Let and If then , which implies
Now suppose , and let Denote By definition of and ⪯ we have
If we prove the proof is finished. By definition, one can easily notice that Hence we are left to prove that We have that and
By writing the two polynomials in the Bernstein basis, and using Theorem 4 we have and with
As for all we conclude the proof. □
Appendix A.3. Proof of Theorem 5
Theorem
(5). Polar codes over the Binary Erasure Channel are strongly decreasing monomial codes.
Proof.
The proof is based on two induction steps. First the parameter m is fixed and we prove that the result holds for any . Secondly we use induction on m.
Firstly, fix m and use an induction argument on the degree of monomial, namely on We also suppose that For we have that so the result is obvious. For use Lemma 2.
Now suppose that for any with we have that Let and such that with the usual convention and . Then we have two cases. Either if or if then we have . Indeed, in the first case we have that
In the second case when the proof works in the same way. If we are not in the previous case it means that and We know that there is for which First we treat the two extreme cases or If this implies that for all . Let Then
In this case, either or Hence, by Lemma 2 and using the order relation ⪯ we obtain
If , by putting and taking into account that we obtain
When suppose that and denote by Using the definition of we have
Notice that Next, we prove that Since , we can use Lemma 6 and demonstrate , i.e., As,
we obtain , simply by verifying
The next partial sums inequalities,
are verified from the relation So we check the partial sums step by step:
- and thus
- and thus
- ⋯
- and thus
- by definition of and thus
- ⋯
Hence we have that which implies, using the induction hypothesis, that from which we deduce Also,
Secondly, we use induction on the number of variables For the first values of m, i.e., it is straightforward to check the result.
Let and such that with the usual convention and . The following cases are possible
- If then we have and Since we have by the induction hypothesis
- Else, by the definition of the order we necessary have We also have thatWhich implies that In the same time notice that and Therefore we obtain
□
References
- Arıkan, E. Channel polarization: A method for constructing capacity-achieving codes for symmetric binary-input memoryless channels. IEEE Trans. Inform. Theory 2009, 55, 3051–3073. [Google Scholar] [CrossRef]
- Bioglio, V.; Condo, C.; Land, I. Design of Polar Codes in 5G New Radio. IEEE Commun. Surv. Tutor. 2020, 23, 29–40. [Google Scholar] [CrossRef]
- Dragoi, V. Algebraic Approach for the Study of Algorithmic Problems Coming from Cryptography and the Theory of Error Correcting Codes. Ph.D. Thesis, Université de Rouen, Normandie, France, 2017. [Google Scholar]
- Bardet, M.; Dragoi, V.; Otmani, A.; Tillich, J. Algebraic properties of polar codes from a new polynomial formalism. In Proceedings of the 2016 IEEE International Symposium on Information Theory (ISIT), Barcelona, Spain, 10–15 July 2016; pp. 230–234. [Google Scholar] [CrossRef]
- Rengaswamy, N.; Calderbank, R.; Newman, M.; Pfister, H.D. Classical Coding Problem from Transversal T Gates, 2020. In Proceedings of the 2020 IEEE International Symposium on Information Theory (ISIT), Los Angeles, CA, USA, 21–26 June 2020; pp. 1891–1896. [Google Scholar] [CrossRef]
- Rengaswamy, N. Classical Coding Approaches to Quantum Applications. arXiv 2020, arXiv:2004.06834. [Google Scholar]
- Krishna, A.; Tillich, J.P. Magic state distillation with punctured polar codes. arXiv 2019, arXiv:1811.03112. [Google Scholar]
- Bardet, M.; Chaulet, J.; Dragoi, V.; Otmani, A.; Tillich, J.P. Cryptanalysis of the McEliece Public Key Cryptosystem Based on Polar Codes. In Post-Quantum Cryptography, PQCrypto 2016; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2016; Volume 9606, pp. 118–143. [Google Scholar] [CrossRef]
- Drăgoi, V.; Beiu, V.; Bucerzan, D. Vulnerabilities of the McEliece Variants Based on Polar Codes. In Innovative Security Solutions for Information Technology and Communications, SecITC 2018; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2018; Volume 11359, pp. 376–390. [Google Scholar] [CrossRef]
- Bucerzan, D.; Dragoi, V.; Kalachi, H.T. Evolution of the McEliece Public Key Encryption Scheme. In Innovative Security Solutions for Information Technology and Communications, SecITC 2017; Lecture Notes in Computer Science; Springer: Cham, Switzerland; Volume 10543, pp. 129–149. [CrossRef]
- Drăgoi, V.F.; Beiu, V. Fast Reliability Ranking of Matchstick Minimal Networks. arXiv 2019, arXiv:1911.01153. [Google Scholar]
- Dragoi, V.; Cowell, S.; Beiu, V. Ordering series and parallel compositions. In Proceedings of the 2018 IEEE 18th International Conference on Nanotechnology (IEEE-NANO), Cork, Ireland, 23–26 July 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Beiu, V.; Cowell, S.R.; Drăgoi, V.F. On Posets for Reliability: How Fine Can They Be? In Soft Computing Applications SOFA 2018, Advances in Intelligent Systems and Computing; Springer: Cham, Switzerland, 2021; Volume 1221, pp. 115–129. [Google Scholar] [CrossRef]
- Mondelli, M.; Hassani, S.H.; Urbanke, R. Construction of polar codes with sublinear complexity. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 1853–1857. [Google Scholar] [CrossRef]
- He, G.; Belfiore, J.; Land, I.; Yang, G.; Liu, X.; Chen, Y.; Li, R.; Wang, J.; Ge, Y.; Zhang, R.; et al. Beta-Expansion: A Theoretical Framework for Fast and Recursive Construction of Polar Codes. In Proceedings of the GLOBECOM 2017-2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Tal, I.; Vardy, A. How to Construct Polar Codes. IEEE Trans. Inform. Theory 2013, 59, 6562–6582. [Google Scholar] [CrossRef]
- Mori, R.; Tanaka, T. Performance and construction of polar codes on symmetric binary-input memoryless channels. In Proceedings of the 2009 IEEE International Symposium on information theory, Seoul, Korea, 28 June–3 July 2009; pp. 1496–1500. [Google Scholar] [CrossRef]
- Mahdavifar, H.; El-Khamy, M.; Lee, J.; Kang, I. On the construction and decoding of concatenated polar codes. In Proceedings of the 2013 IEEE International Symposium on Information Theory, Istanbul, Turkey, 7–12 July 2013; pp. 952–956. [Google Scholar] [CrossRef]
- Korada, S.B.; Sasoglu, E.; Urbanke, R.L. Polar Codes: Characterization of Exponent, Bounds, and Constructions. IEEE Trans. Inform. Theory 2010, 56, 6253–6264. [Google Scholar] [CrossRef]
- Afşer, H.; Deliç, H. On the Channel-Specific Construction of Polar Codes. IEEE Commun. Lett. 2015, 19, 1480–1483. [Google Scholar] [CrossRef]
- Trifonov, P.; Trofimiuk, G. A randomized construction of polar subcodes. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 1863–1867. [Google Scholar] [CrossRef]
- Huang, L.; Zhang, H.; Li, R.; Ge, Y.; Wang, J. AI Coding: Learning to Construct Error Correction Codes. IEEE Trans. Commun. 2020, 68, 26–39. [Google Scholar] [CrossRef]
- Romano, G.; Ciuonzo, D. Minimum-Variance Importance-Sampling Bernoulli Estimator for Fast Simulation of Linear Block Codes over Binary Symmetric Channels. IEEE Trans. Wirel. Commun. 2014, 13, 486–496. [Google Scholar] [CrossRef]
- Minja, A.; Šenk, V. Quasi-Analytical Simulation Method for Estimating the Error Probability of Star Domain Decoders. IEEE Trans. Commun. 2019, 67, 3101–3113. [Google Scholar] [CrossRef]
- Wu, W.; Siegel, P.H. Generalized Partial Orders for Polar Code Bit-Channels. IEEE Trans. Inf. Theory 2019, 65, 7114–7130. [Google Scholar] [CrossRef]
- Saptharishi, R.; Shpilka, A.; Volk, B.L. Efficiently Decoding Reed–Muller Codes From Random Errors. IEEE Trans. Inf. Theory 2017, 63, 1954–1960. [Google Scholar] [CrossRef]
- Kudekar, S.; Kumar, S.; Mondelli, M.; Pfister, H.D.; Sasoglu, E.; Urbanke, R. Reed-Muller Codes Achieve Capacity on Erasure Channels. IEEE Trans. Inf. Theory 2017, 63, 4298–4316. [Google Scholar] [CrossRef]
- Kumar, S.; Calderbank, R.; Pfister, H.D. Beyond double transitivity: Capacity-achieving cyclic codes on erasure channels. In Proceedings of the 2016 IEEE Information Theory Workshop (ITW), Cambridge, UK, 11–14 September 2016; pp. 241–245. [Google Scholar] [CrossRef]
- Ordentlich, E.; Roth, R.M. On the Pointwise Threshold Behavior of the Binary Erasure Polarization Subchannels. IEEE Trans. Inf. Theory 2019, 65, 6044–6055. [Google Scholar] [CrossRef]
- Drăgoi, V.F.; Beiu, V. Studying the Binary Erasure Polarization Subchannels Using Network Reliability. IEEE Commun. Lett. 2020, 24, 62–66. [Google Scholar] [CrossRef]
- Stanley, R.P. Enumerative Combinatorics; Cambridge University Press: Cambridge, NY, USA, 2012. [Google Scholar]
- Cristescu, G.; Drăgoi, V.F. Cubic Spline Approximation of the Reliability Polynomials of Two Dual Hammock Networks. Transylv. J. Math. Mech. 2019, 11, 77–90. [Google Scholar]
- Cristescu, G.; Drăgoi, V.F. Efficient approximation of two-terminal networks reliability polynomials using cubic splines. IEEE Trans. Reliab. 2021, 1–11. [Google Scholar] [CrossRef]
- Mondelli, M. From Polar to Reed-Muller Codes: Unified Scaling, Non-standard Channels, and a Proven Conjecture. Ph.D. Thesis, Ecole Polytechnique Fédérale de Lausanne, Lausanne, Switzerland, 2016. [Google Scholar]
- Richardson, T.; Urbanke, R. Modern Coding Theory; Cambridge University Press: New York, NY, USA, 2008. [Google Scholar]
- Roth, R.M. Introduction to Coding Theory; Cambridge University Press: New York, NY, USA, 2006. [Google Scholar]
- Carlet, C. Boolean functions for cryptography and error correcting codes. In Boolean Models and Methods in Mathematics, Computer Science, and Engineering; Cambridge University Press: Cambridge, NY, USA, 2010; Chapter 8; pp. 257–397. [Google Scholar]
- Moore, E.F.; Shannon, C.E. Reliable circuits using less reliable relays - Part I. J. Frankl. Inst. 1956, 262, 191–208. [Google Scholar] [CrossRef]
- Drăgoi, V.; Cowell, S.R.; Beiu, V.; Hoară, S.; Gaşpar, P. How Reliable are Compositions of Series and Parallel Networks Compared with Hammocks? Int. J. Comput. Commun. Control 2018, 13, 772–791. [Google Scholar] [CrossRef]
- Colbourn, C.J. The Combinatorics of Network Reliability; Oxford University Press: New York, NY, USA, 1987. [Google Scholar]
- Dăuş, L.; Jianu, M. The shape of the reliability polynomial of a hammock network. In Intelligent Methods in Computing, Communication and Control. ICCC 2020, Advances in Intelligent Systems and Computing; Springer: Berlin/Heidelberg, Germany, 2021; Volume 1243, pp. 93–105. [Google Scholar] [CrossRef]
- Brown, J.; Cox, D.; Ehrenborg, R. The average reliability of a graph. Discret. Appl. Math. 2014, 177, 19–33. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).