Cross-Layer-Aided Opportunistic Routing for Sparse Underwater Wireless Sensor Networks
Abstract
1. Introduction
2. Relate Works
3. System Model
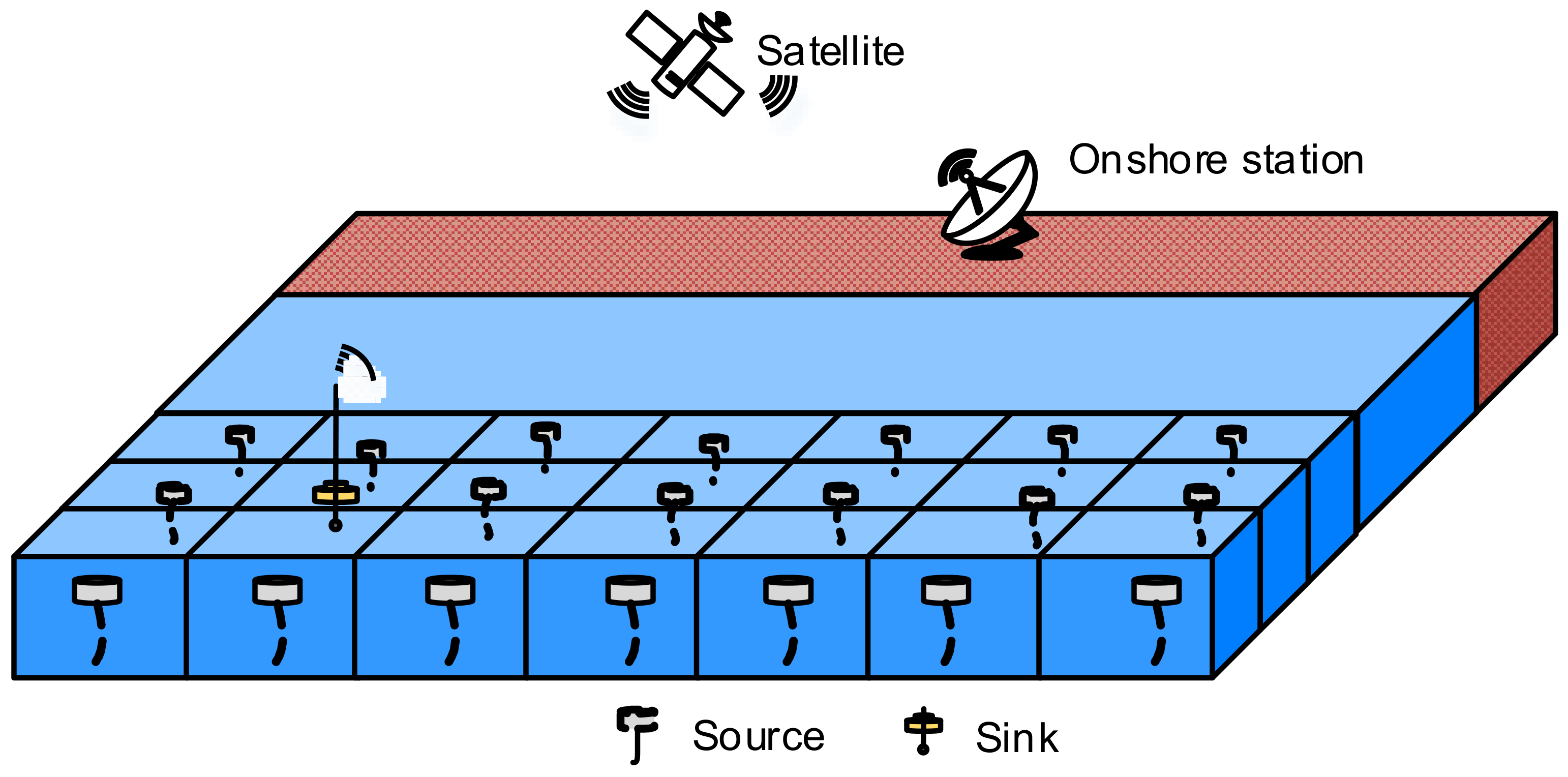
3.1. Network Architecture
3.2. Channel Model
3.2.1. Energy Propagation Model
3.2.2. Ambient Noise
3.2.3. Packet Error Rate
4. CLOR Protocol
4.1. Main Idea
4.1.1. Forwarder Selection Algorithm
4.1.2. Negotiation Strategy
4.1.3. Coding-Based Burst Transmission Mechanism
4.2. Process of CLOR
4.2.1. Network Initialization and Maintenance
4.2.2. Negotiation Process
| Algorithm 1 Upon receiving an RTF packet |
| 1: updates neighbor table and topological information. 2: if () then 3: if () then 4: back off according to (9) 5: end if 6: discard 7: else if () then 8: discard 9: else if () then 10: back off according to (9) 11: discard 12: else 13: set according to the burst information in ; 14: if () then 15: execute fuzzy logic 16: end if 17: create a CTF packet and send it to transmit queue. 18: end if |
4.2.3. Forwarder Selection Algorithm
Fuzzy Input
Fuzzy Rules
4.2.4. Adaptive Transmission Process
5. Protocol Analysis
5.1. Effectiveness of Negotiation
5.2. Effectiveness of Burst Transmission
5.3. Reliability of Network Coding
6. Performance Evaluation
6.1. Simulation Scenarios and Settings
6.2. Simulation Results
6.2.1. Impact of Various Parameters
Impact of Source Level
Impact of Burst Size
6.2.2. Comparison with Typical Protocols
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Sozer, E.M.; Stojanovic, M.; Proakis, J.G. Underwater acoustic networks. IEEE J. Oceanic Eng. 2000, 25, 72–83. [Google Scholar] [CrossRef]
- Heidemann, J.; Stojanovic, M.; Zorzi, M. Underwater sensor networks: Applications, advances and challenges. Philos. Trans. R. Soc. Lond. Ser. A 2012, 370, 158–175. [Google Scholar] [CrossRef] [PubMed]
- Basagni, S.; Valerio, V.D.; Gjanci, P.; Petrioli, C. MARLIN-Q: Multi-modal communications for reliable and low-latency underwater data delivery. Ad Hoc Netw. 2019, 82, 134–145. [Google Scholar] [CrossRef]
- Basagni, S.; Petrioli, C.; Petroccia, R.; Spaccini, D. CARP: A channel-aware routing protocol for underwater acoustic wireless networks. Ad Hoc Netw. 2015, 34, 92–104. [Google Scholar] [CrossRef]
- Misra, S.; Ojha, T.; Mondal, A. Game-Theoretic Topology Control for Opportunistic Localization in Sparse Underwater Sensor Networks. IEEE. Trans. Mob. Comput. 2015, 14, 990–1003. [Google Scholar] [CrossRef]
- Han, G.; Jiang, J.; Bao, N.; Wan, L.; Guizani, M. Routing protocols for underwater wireless sensor networks. IEEE Commun. Mag. 2015, 53, 72–78. [Google Scholar] [CrossRef]
- Darehshoorzadeh, A.; Boukerche, A. Underwater sensor networks: A new challenge for opportunistic routing protocols. IEEE Commun. Mag. 2015, 53, 98–107. [Google Scholar] [CrossRef]
- Chakchouk, N. A Survey on Opportunistic Routing in Wireless Communication Networks. IEEE Commun. Surv. Tutor. 2015, 17, 2214–2241. [Google Scholar] [CrossRef]
- Xu, X.; Yuan, M.; Liu, X.; Liu, A.; Xiong, N.; Cai, Z.; Wang, T. A Cross-Layer Optimized Opportunistic Routing Scheme for Loss-and-Delay Sensitive WSNs. Sensors 2018, 18, 1422. [Google Scholar] [CrossRef]
- Jornet, J.M.; Stojanovic, M.; Zorzi, M. Focused beam routing protocol for underwater acoustic networks. In Proceedings of the Third ACM International Workshop on Underwater Networks, San Francisco, CA, USA, 14–19 September 2008; pp. 75–82. [Google Scholar]
- Ng, H.-H.; Soh, W.-S.; Motani, M. A bidirectional-concurrent MAC protocol with packet bursting for underwater acoustic networks. IEEE J. Oceanic Eng. 2013, 38, 547–565. [Google Scholar] [CrossRef]
- Anjangi, P.; Chitre, M. Experimental demonstration of super-TDMA: A MAC protocol exploiting large propagation delays in underwater acoustic networks. In Proceedings of the IEEE Third Underwater Communications and Networking Conference (UComms), Lerici, Italy, 30 August–1 September 2016; pp. 1–5. [Google Scholar]
- Zeng, H.C.; Hou, Y.T.; Shi, Y.; Lou, W.J.; Kompella, S.; Midkiff, S.F. A Distributed Scheduling Algorithm for Underwater Acoustic Networks With Large Propagation Delays. IEEE Trans. Commun. 2017, 65, 1131–1145. [Google Scholar] [CrossRef]
- Ahmed, R.; Stojanovic, M. Grouped Packet Coding: A Method for Reliable Communication Over Fading Channels With Long Delays. IEEE J. Oceanic Eng. 2018, 44, 1253–1263. [Google Scholar] [CrossRef]
- Coutinho, R.W.L.; Boukerche, A.; Vieira, L.F.M.; Loureiro, A.A.F. Geographic and Opportunistic Routing for Underwater Sensor Networks. IEEE Trans. Comput. 2016, 65, 548–561. [Google Scholar] [CrossRef]
- Coutinho, R.W.L.; Boukerche, A.; Vieira, L.F.M.; Loureiro, A.A.F. Design Guidelines for Opportunistic Routing in Underwater Networks. IEEE Commun. Mag. 2016, 54, 40–48. [Google Scholar] [CrossRef]
- Xie, P.; Cui, J.-H.; Lao, L. VBF: Vector-based forwarding protocol for underwater sensor networks. In Proceedings of the International Conference on Research in Networking, Coimbra, Portugal, 15–19 May 2006; pp. 1216–1221. [Google Scholar]
- Nicolaou, N.; See, A.; Xie, P.; Cui, J.H.; Maggiorini, D. Improving the Robustness of Location-Based Routing for Underwater Sensor Networks. In Proceedings of the OCEANS 2007, Europe, Aberdeen, UK, 18–21 June 2007; pp. 1–6. [Google Scholar]
- Yan, H.; Shi, Z.J.; Cui, J.-H. DBR: Depth-based routing for underwater sensor networks. In Proceedings of the International Conference on Research in Networking, Singapore, 5–9 May 2008; pp. 72–86. [Google Scholar]
- Rahman, M.A.; Lee, Y.; Koo, I. EECOR: An energy-efficient cooperative opportunistic routing protocol for Underwater acoustic sensor networks. IEEE Access 2017, 5, 14119–14132. [Google Scholar] [CrossRef]
- Khan, A.; Ali, I.; Rahman, A.U.; Imran, M.; Mahmood, H. Co-EEORS: Cooperative Energy Efficient Optimal Relay Selection Protocol for Underwater Wireless Sensor Networks. IEEE Access 2018, 6, 28777–28789. [Google Scholar] [CrossRef]
- Zhao, D.; Lun, G.; Xue, R. Coding-Aware Opportunistic Routing for Sparse Underwater Wireless Sensor Networks. IEEE Access 2021, 9, 50170–50187. [Google Scholar]
- Noh, Y.; Lee, U.; Lee, S.; Wang, P.; Vieira, L.F.M.; Cui, J.H.; Gerla, M.; Kim, K. HydroCast: Pressure Routing for Underwater Sensor Networks. IEEE Trans. Veh. Technol. 2016, 65, 333–347. [Google Scholar] [CrossRef]
- Noh, Y.; Lee, U.; Wang, P.; Choi, B.S.C.; Gerla, M. VAPR: Void-Aware Pressure Routing for Underwater Sensor Networks. IEEE. Trans. Mob. Comput. 2013, 12, 895–908. [Google Scholar] [CrossRef]
- Di Valerio, V.; Lo Presti, F.; Petrioli, C.; Picari, L.; Spaccini, D.; Basagni, S. CARMA: Channel-Aware Reinforcement Learning-Based Multi-Path Adaptive Routing for Underwater Wireless Sensor Networks. IEEE J. Sel. Areas Commun. 2019, 37, 2634–2647. [Google Scholar] [CrossRef]
- Yu, H.; Yao, N.; Liu, J. An adaptive routing protocol in underwater sparse acoustic sensor networks. Ad Hoc Netw. 2015, 34, 121–143. [Google Scholar] [CrossRef]
- Yu, H.T.; Yao, N.M.; Wang, T.; Li, G.S.; Gao, Z.G.; Tan, G.Z. WDFAD-DBR: Weighting depth and forwarding area division DBR routing protocol for UASNs. Ad Hoc Netw. 2016, 37, 256–282. [Google Scholar] [CrossRef]
- Basagni, S.; Petrioli, C.; Petroccia, R.; Spaccini, D. Channel-aware routing for underwater wireless networks. In Proceedings of the 2012 Oceans – Yeosu, Yeosu, Korea, 21–24 May 2012; pp. 1–9. [Google Scholar]
- Pompili, D.; Melodia, T. An architecture for ocean bottom underwater acoustic sensor networks (UWASN). In Proceedings of the Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), Bodrum, Turkey, 27–30 June 2004. [Google Scholar]
- Heidemann, J.; Li, Y.; Syed, A.; Wills, J.; Ye, W. Underwater Sensor Networking: Research Challenges and Potential Applications; Technical Report ISI-TR-2005-603; USC/Information Sciences Institute: Arlington, VA, USA, 2005. [Google Scholar]
- Porter, M. Bellhop Code. Available online: http://oalib.hlsresearch.com/Rays/index.html (accessed on 25 April 2021).
- Stojanovic, M. On the relationship between capacity and distance in an underwater acoustic communication channel. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2007, 11, 34–43. [Google Scholar] [CrossRef]
- Pompili, D.; Melodia, T.; Akyildiz, I.F. Distributed Routing Algorithms for Underwater Acoustic Sensor Networks. IEEE Trans. Wireless Commun. 2010, 9, 2934–2944. [Google Scholar] [CrossRef]
- Qarabaqi, P.; Stojanovic, M. Statistical Characterization and Computationally Efficient Modeling of a Class of Underwater Acoustic Communication Channels. IEEE J. Oceanic Eng. 2013, 38, 701–717. [Google Scholar] [CrossRef]
- Hollinger, G.A.; Choudhary, S.; Qarabaqi, P.; Murphy, C.; Mitra, U.; Sukhatme, G.S.; Stojanovic, M.; Singh, H.; Hover, F. Underwater Data Collection Using Robotic Sensor Networks. IEEE J. Sel. Areas Commun. 2012, 30, 899–911. [Google Scholar] [CrossRef]
- Guerra, F.; Casari, P.; Zorzi, M. World Ocean Simulation System (WOSS): A simulation tool for underwater networks with realistic propagation modeling. In Proceedings of the Fourth ACM International Workshop on Under Water Networks, Berkeley, CA, USA, 3 November 2009. [Google Scholar]
- World Ocean Atlas. Available online: https://www.nodc.noaa.gov/OC5/SELECT/woaselect/woaselect.html (accessed on 25 April 2021).
- General Bathymetric Chart of the Oceans. Available online: www.gebco.net (accessed on 25 April 2021).
- National Geophysical Data Center. Seafloor Surficial Sediment Descriptions. Available online: https://www.ngdc.noaa.gov/mgg/geology/geology.html (accessed on 25 April 2021).
- Tapparello, C.; Casari, P.; Toso, G.; Calabrese, I.; Otnes, R.; Walree, P.v.; Goetz, M.; Nissen, I.; Zorzi, M. Performance evaluation of forwarding protocols for the RACUN network. In Proceedings of the Eighth ACM International Conference on Underwater Networks and Systems, Kaohsiung, Taiwan, 11–13 November 2013; pp. 1–8. [Google Scholar]
- Parissidis, G.; Karaliopoulos, M.; Spyropoulos, T.; Plattner, B. Interference-Aware Routing in Wireless Multihop Networks. IEEE. Trans. Mob. Comput. 2011, 10, 716–733. [Google Scholar] [CrossRef]
- Zhang, H.; Arora, A.; Sinha, P. Link Estimation and Routing in Sensor Network Backbones: Beacon-Based or Data-Driven? IEEE. Trans. Mob. Comput. 2009, 8, 653–667. [Google Scholar]
- Baccour, N.; Koubâa, A.; Youssef, H.; Alves, M.J.A.H.N. Reliable link quality estimation in low-power wireless networks and its impact on tree-routing. Ad Hoc Netw. 2015, 27, 1–25. [Google Scholar]
- Nimbalkar, A.A.; Pompili, D. Reliability in underwater inter-vehicle communications. In Proceedings of the third ACM international workshop on Underwater Networks, San Francisco, CA, USA, 2008, 15 September 2008; pp. 19–26. [Google Scholar]
- Wang, C.; Li, B.; Sohraby, K.; Daneshmand, M.; Hu, Y. Upstream congestion control in wireless sensor networks through cross-layer optimization. IEEE J. Sel. Areas Commun. 2007, 25, 786–795. [Google Scholar] [CrossRef]
- Bharghavan, V.; Demers, A.; Shenker, S.; Zhang, L. MACAW: A media access protocol for wireless LAN’s. ACM SIGCOMM Comput. Commun. Rev. 1994, 24, 212–225. [Google Scholar] [CrossRef]
- Zhou, Z.; Mo, H.; Zhu, Y.; Peng, Z.; Huang, J.; Cui, J.H. Fountain code based Adaptive multi-hop Reliable data transfer for underwater acoustic networks. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 6396–6400. [Google Scholar]
- Ahmed, R.; Stojanovic, M. Joint Power and Rate Control for Packet Coding Over Fading Channels. IEEE J. Oceanic Eng. 2017, 42, 697–710. [Google Scholar] [CrossRef]
- Ahmed, R.; Stojanovic, M. Reliable communication using packet coding for underwater acoustic channels. In Proceedings of the 2016 IEEE 17th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Edinburgh, UK, 3–6 July 2016; pp. 1–5. [Google Scholar]
- Lindgren, A.; Doria, A.; Schelén, O. Probabilistic routing in intermittently connected networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2003, 7, 19–20. [Google Scholar] [CrossRef]
- Yager, R.R. On ordered weighted averaging aggregation operators in multicriteria decisionmaking. IEEE Trans. Syst. Man Cybern. 1988, 18, 183–190. [Google Scholar] [CrossRef]
- Keller, L.; Atsan, E.; Argyraki, K.; Fragouli, C. SenseCode: Network coding for reliable sensor networks. ACM Trans. Sen. Netw. 2013, 9, 1–20. [Google Scholar] [CrossRef]
- MacKay, D.J.C. Fountain codes. IEE Proc. Commun. 2005, 152, 1062–1068. [Google Scholar] [CrossRef]
- Bioglio, V.; Grangetto, M.; Gaeta, R.; Sereno, M. On the fly gaussian elimination for LT codes. IEEE Commun. Lett. 2009, 13, 953–955. [Google Scholar] [CrossRef]
- Partan, J.; Kurose, J.; Levine, B.N.; Preisig, J. Low spreading loss in underwater acoustic networks reduces RTS/CTS effectiveness. In Proceedings of the Sixth ACM International Workshop on Underwater Networks, Seattle, WA, USA, 1–2 December 2011; pp. 1–8. [Google Scholar]
- Partan, J.; Kurose, J.; Levine, B.N.; Preisig, J. Spatial Reuse in Underwater Acoustic Networks Using Rts/Cts Mac Protocols; UM-CS-2010-045; University of Massachusetts Department of Computer Science: Amherst, MA, USA, 2010. [Google Scholar]
- Ye, F.; Yi, S.; Sikdar, B. Improving spatial reuse of IEEE 802.11 based ad hoc networks. In Proceedings of the GLOBECOM ‘03. IEEE Global Telecommunications Conference (IEEE Cat. No.03CH37489), San Francisco, CA, USA, 1–5 December 2003; pp. 1013–1017. [Google Scholar]
- Zhao, D.; Lun, G. Effectiveness of handshake strategy in 3D underwater acoustic networks. J. Phys. Conf. Ser. 2021, 1748, 032044. [Google Scholar] [CrossRef]
- Liva, G.; Paolini, E.; Chiani, M. Performance versus overhead for fountain codes over Fq. IEEE Commun. Lett. 2010, 14, 178–180. [Google Scholar] [CrossRef]
- Llor, J.; Malumbres, M.P.; Garrido, P. Performance evaluation of underwater wireless sensor networks with OPNET. In Proceedings of the 4th International ICST Conference on Simulation Tools and Techniques, ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering), Barcelona, Spain, 21–25 March 2011; pp. 19–26. [Google Scholar]
- Gallimore, E.; Partan, J.; Vaughn, I.; Singh, S.; Shusta, J.; Freitag, L. The WHOI micromodem-2: A scalable system for acoustic communications and networking. In Proceedings of the OCEANS 2010, Seattle, WA, USA, 20–23 September 2010; pp. 1–7. [Google Scholar]














Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, D.; Lun, G.; Xue, R.; Sun, Y. Cross-Layer-Aided Opportunistic Routing for Sparse Underwater Wireless Sensor Networks. Sensors 2021, 21, 3205. https://doi.org/10.3390/s21093205
Zhao D, Lun G, Xue R, Sun Y. Cross-Layer-Aided Opportunistic Routing for Sparse Underwater Wireless Sensor Networks. Sensors. 2021; 21(9):3205. https://doi.org/10.3390/s21093205
Chicago/Turabian StyleZhao, Danfeng, Guiyang Lun, Rui Xue, and Yanbo Sun. 2021. "Cross-Layer-Aided Opportunistic Routing for Sparse Underwater Wireless Sensor Networks" Sensors 21, no. 9: 3205. https://doi.org/10.3390/s21093205
APA StyleZhao, D., Lun, G., Xue, R., & Sun, Y. (2021). Cross-Layer-Aided Opportunistic Routing for Sparse Underwater Wireless Sensor Networks. Sensors, 21(9), 3205. https://doi.org/10.3390/s21093205





