Automatic Key Update Mechanism for Lightweight M2M Communication and Enhancement of IoT Security: A Case Study of CoAP Using Libcoap Library †
Abstract
:1. Introduction
2. Background
2.1. PSK
2.2. Key Exchange
2.3. Ciphering Methods
2.4. TLS
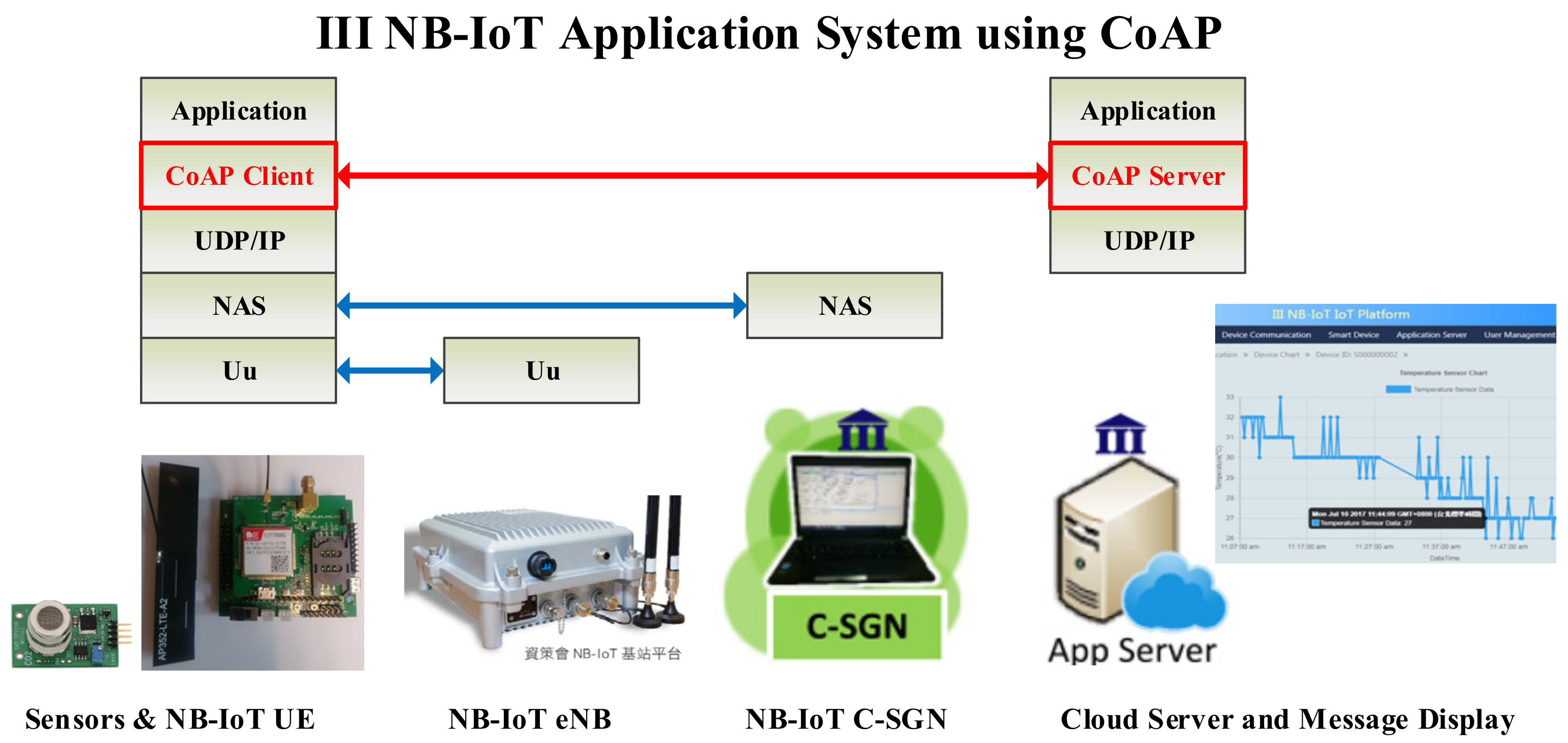
2.5. CoAP and Secure IoT Transmission
2.6. CoAP Library of Libcoap
2.7. Nonrepeating PRNG
3. Design Methodology
3.1. OTP and One-Time Pad
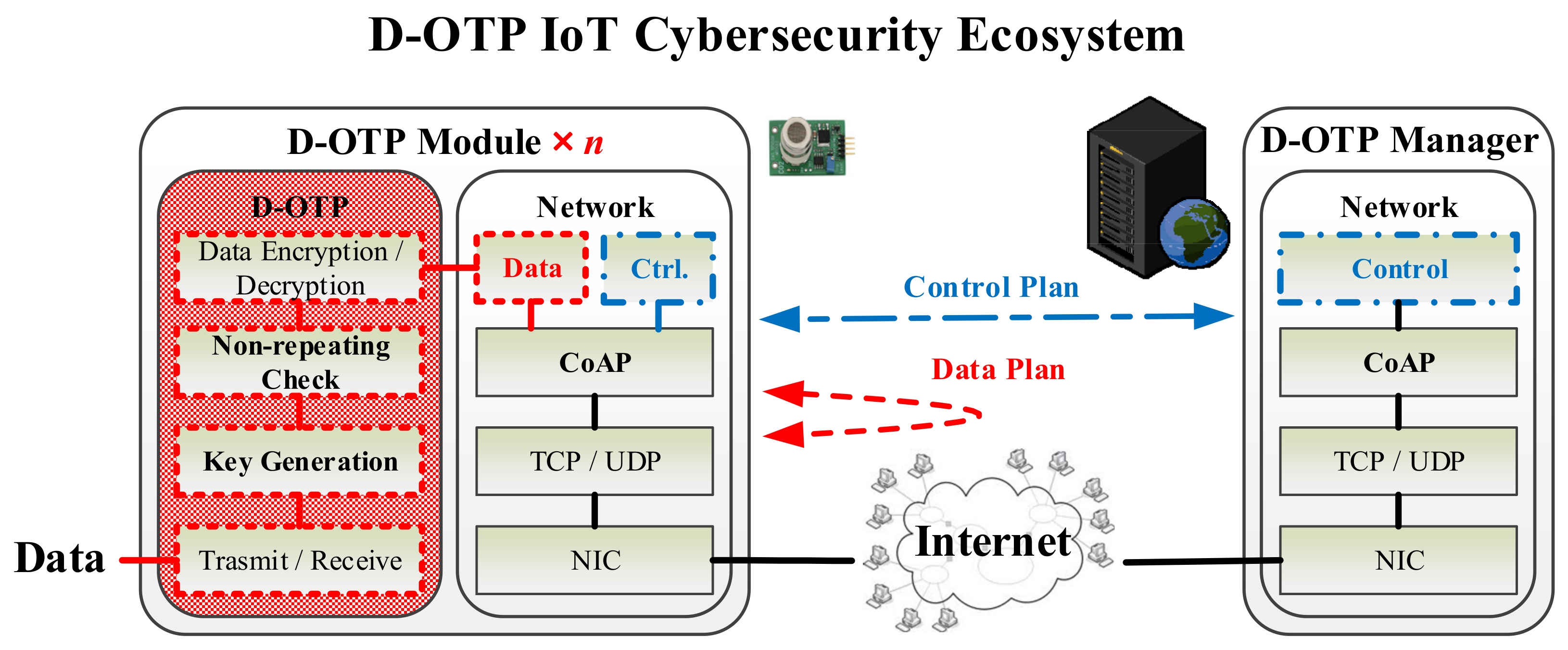
3.2. D-OTP Secure Transmission Ecosystem
- Setup Plane
- 2.
- Control Plane
- 3.
- Data Plane
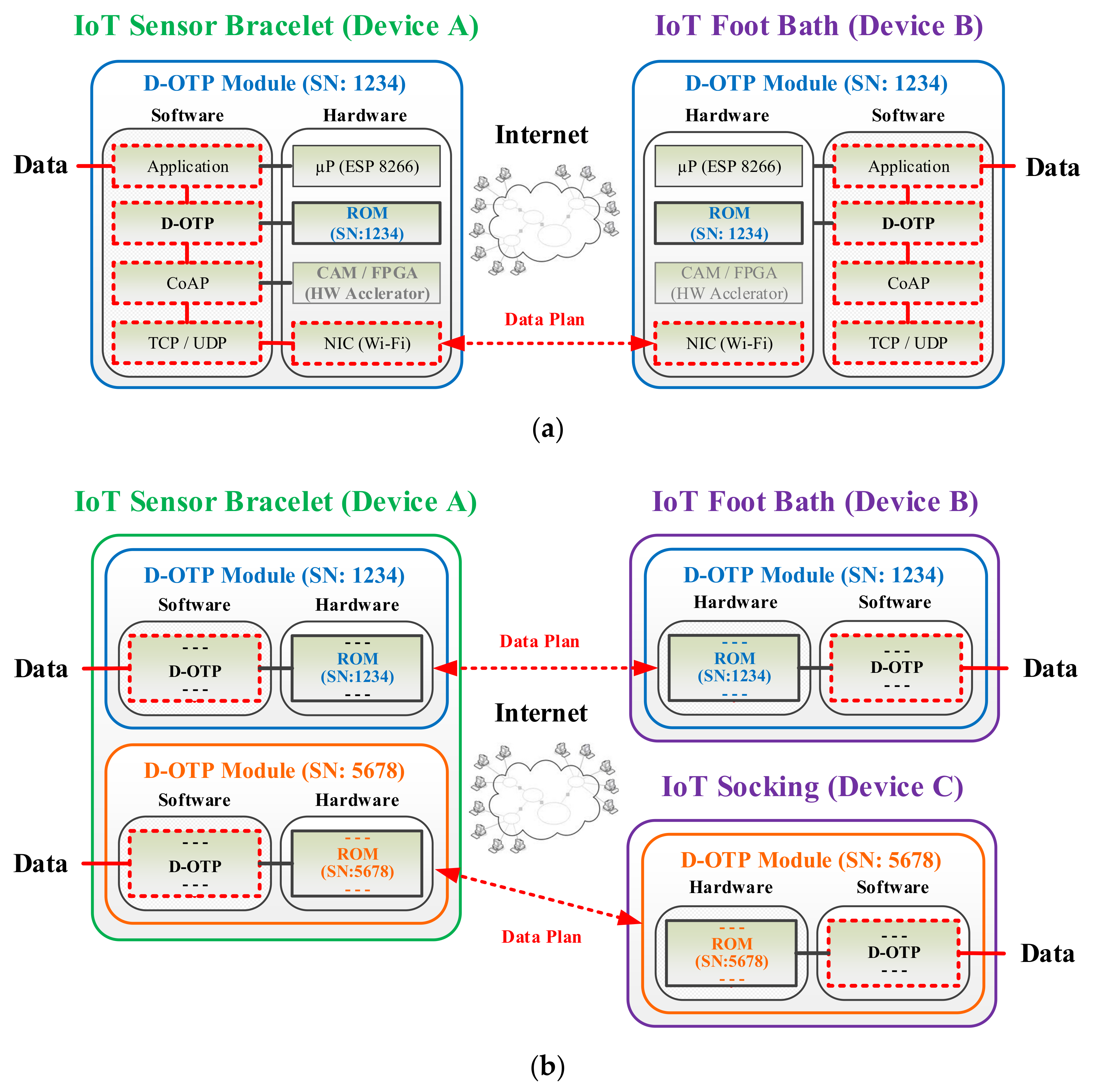
3.3. Applications of D-OTP
3.4. Implementation of CoAP
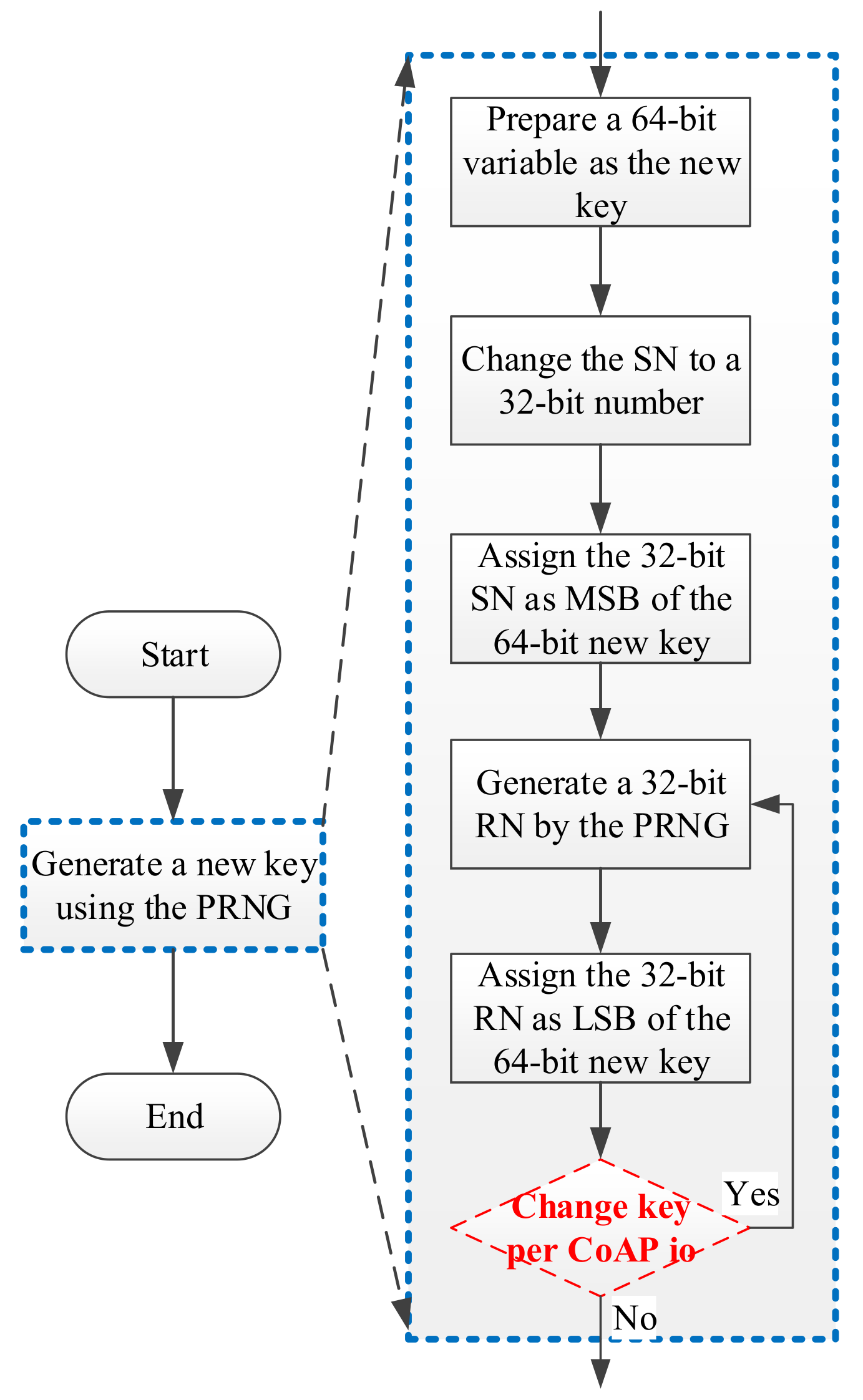
3.5. Implementation of PRNG
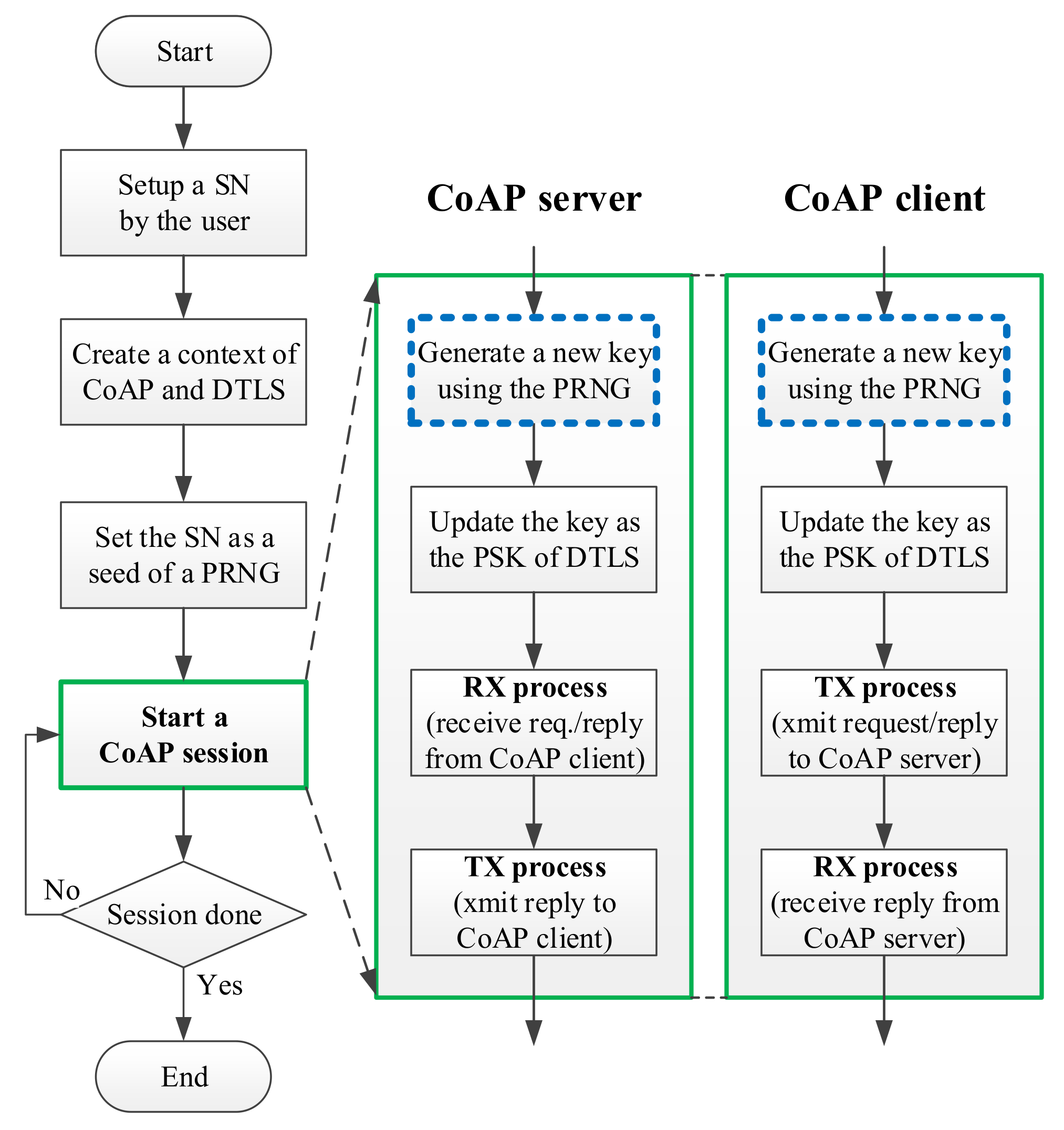
3.6. System Execution Flow
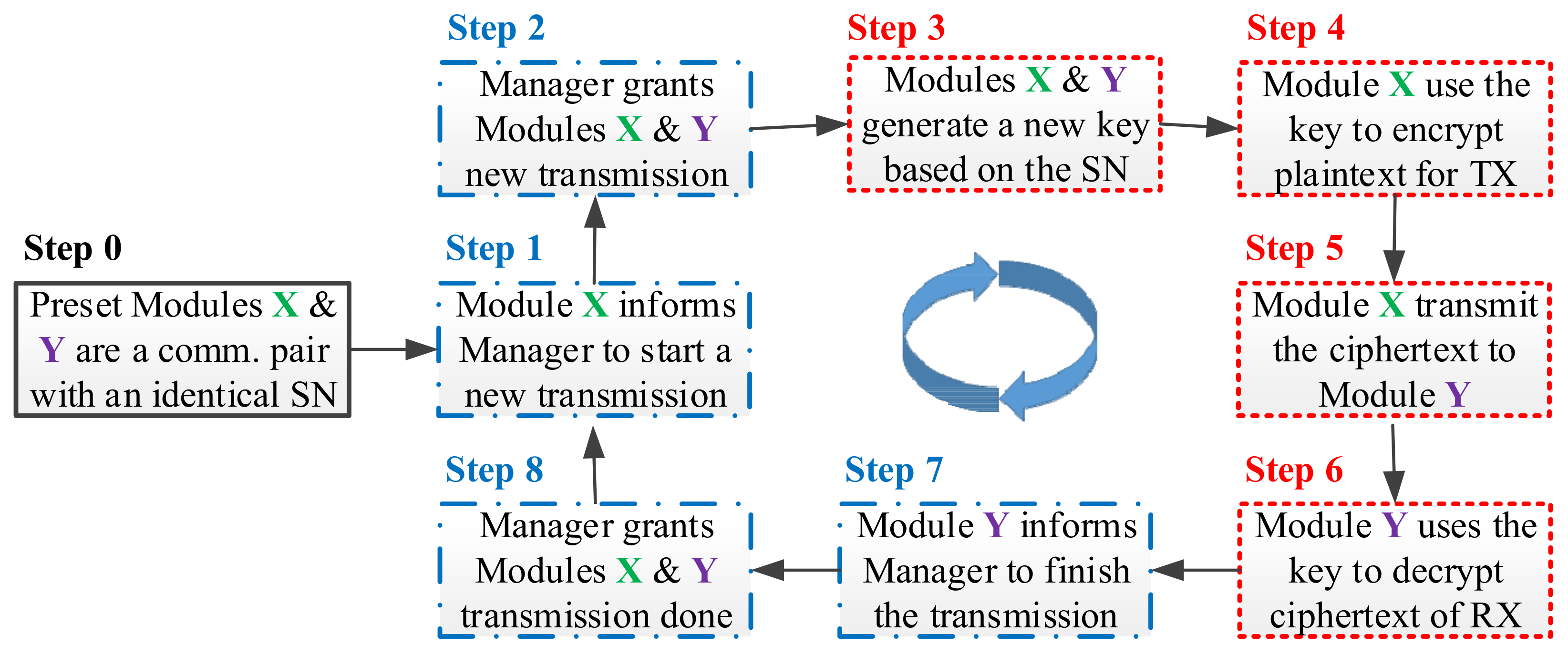
3.7. Key Update Flow
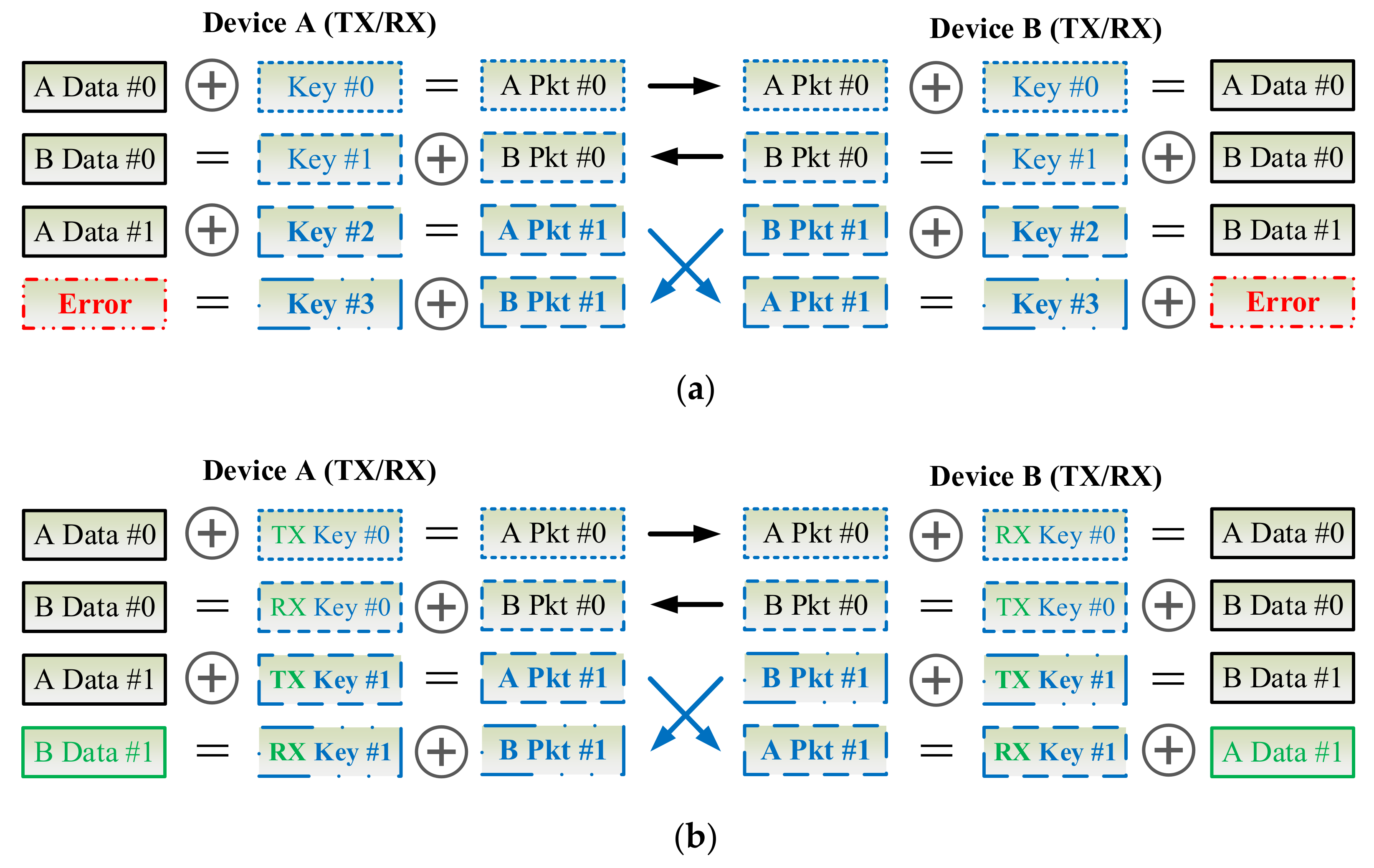
3.8. Key Synchronization Issue
4. Experimental Results
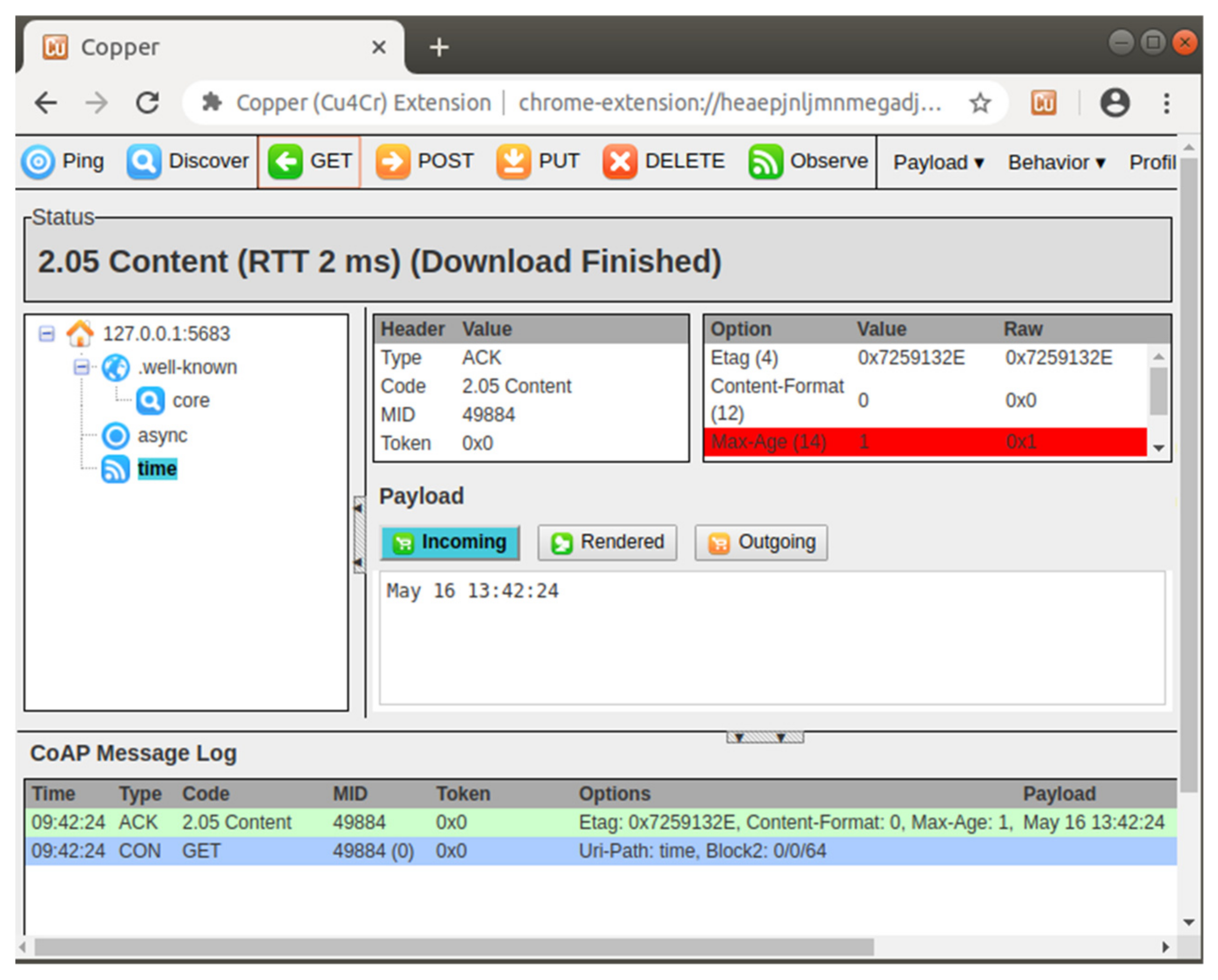
4.1. Executions of Libcoap
4.2. Automatic Key Update Mechanism
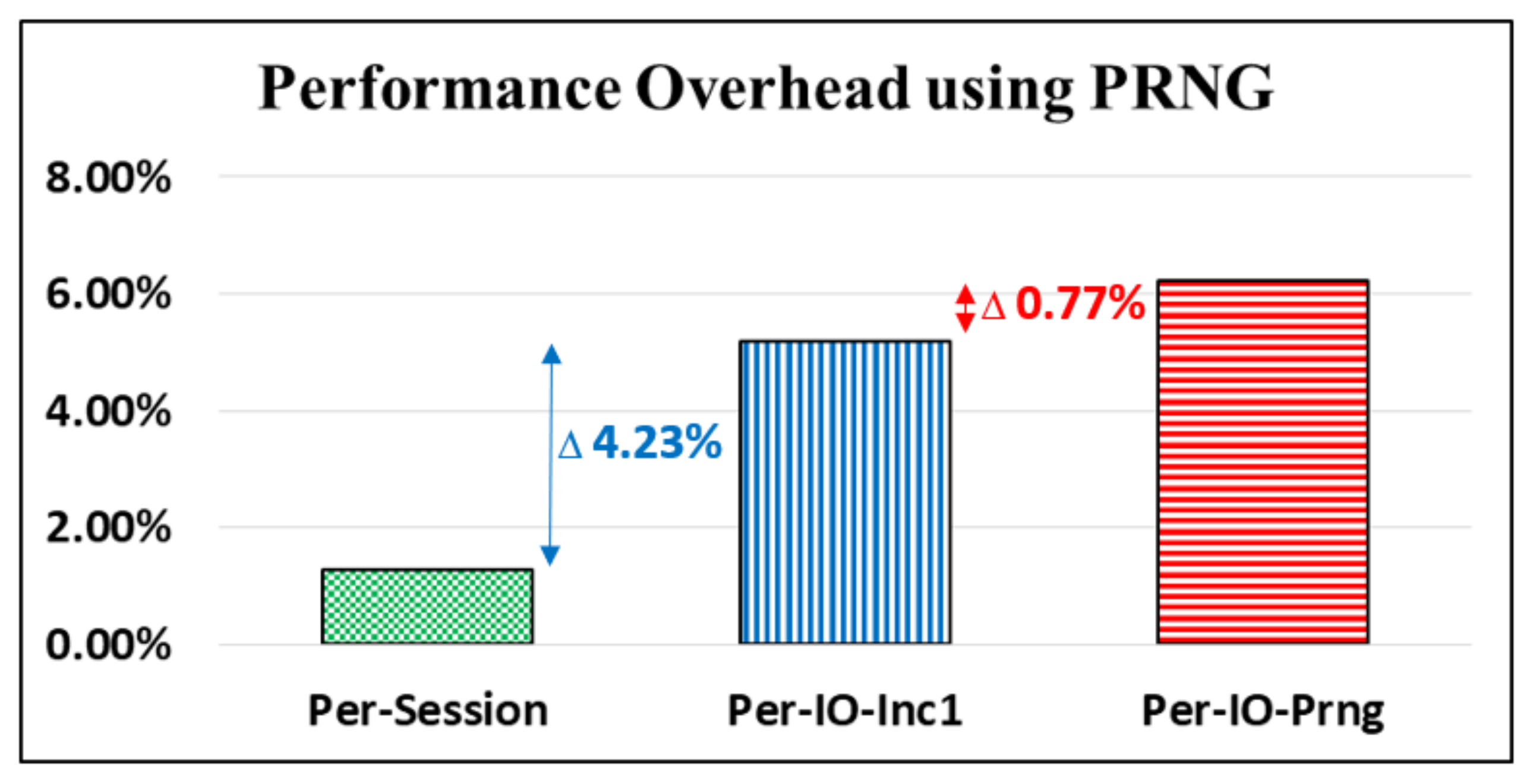
4.3. Performance Analyses for PRNG
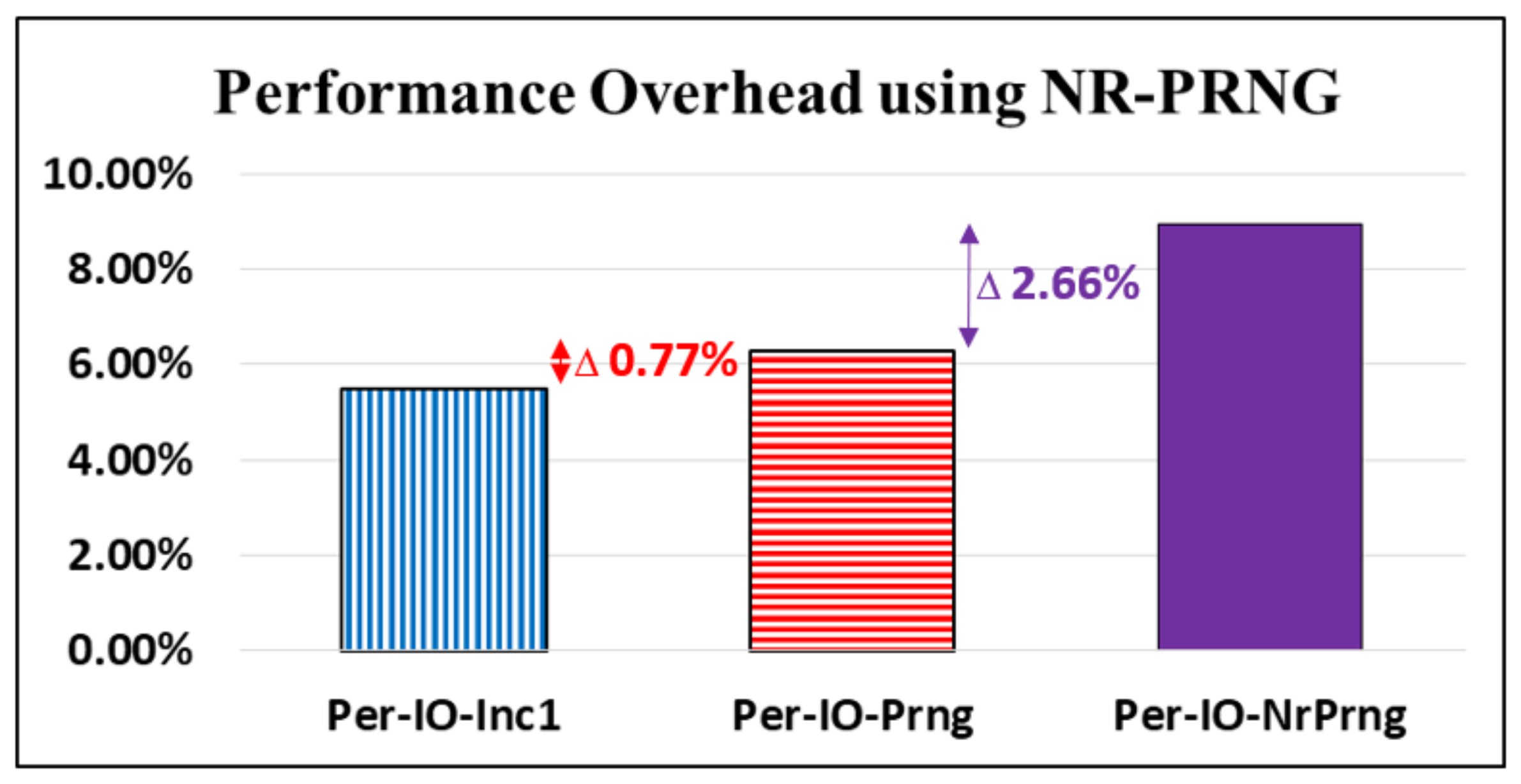
4.4. Performance Analyses for NR-PRNG
4.5. Performance Analyses for NR-PRNG in Mass Data Transfers
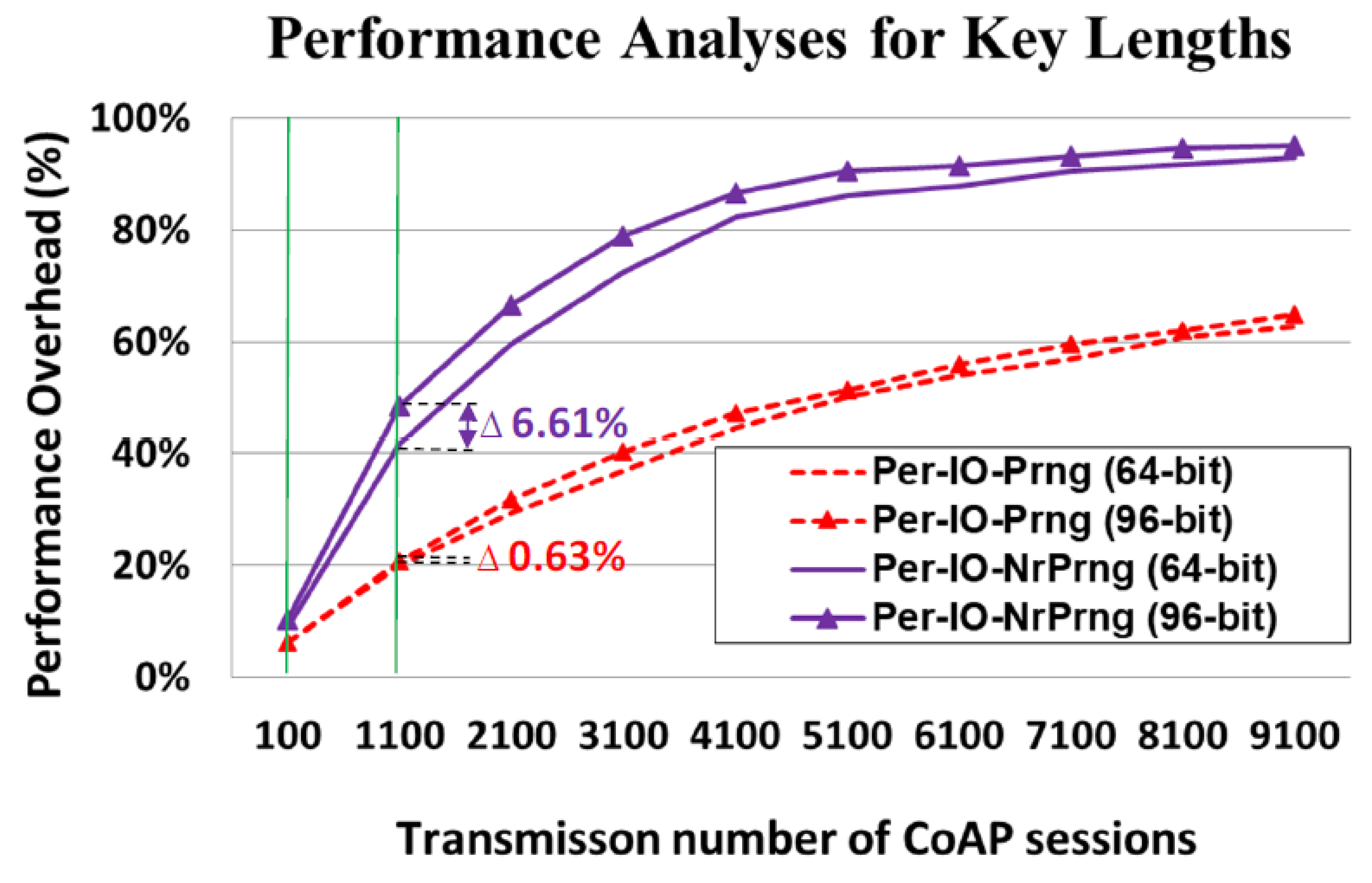
4.6. Performance Analyses for NR-PRNG with a Long Key
5. Discussion
- We propose a D-OTP mechanism that combines both OTP and one-time pad to achieve theoretically unbreakable security.
- To the best of our knowledge, D-OTP is the first implementation of the theoretically unbreakable security in a real IoT ecosystem.
- The proposed D-OTP mechanism can be implemented using the libcoap library, which is a popular and commonly used open-source CoAP.
- We demonstrated that the D-OTP mechanism can be a feasible solution that provides guaranteed unbreakable security when a limited number of transmissions are being made or when latency is not a concern in lightweight M2M communications.
- The nonrepeating key generation process may have critical performance challenges in mass data transfers, which may be a topic worth investigating in the future.
6. Conclusions
Supplementary Materials
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Acronym | Explanation |
|---|---|
| µP | Microprocessor |
| AES | Advanced Encryption Standard |
| ASCII | Information Interchange |
| AV | Audiovisual |
| BB84 | A quantum key distribution scheme by Bennett and Brassard in 1984 |
| CAM | Content-addressable memory |
| CoAP | Constrained Application Protocol |
| C-SGN | Cellular Serving Gateway Node |
| DES | Data Encryption Standard |
| DH | Diffie–Hellman |
| D-OTP | Double OTP |
| DTLS | Datagram TLS |
| eNB | Basestation of 4G-LTE |
| FPGA | Field-programmable gate array |
| gNB | Basestation of 5G |
| IDC | International Data Corporation |
| III | Institute for Information Industry |
| IoT | Internet of Things |
| IP | Internet Protocol |
| M2M | Machine-to-machine |
| NAS | Non-access stratum |
| NB-IoT | Narrowband Internet of Things |
| NIC | Network interface controller |
| NR-PRNG | Nonrepeating PRNG |
| OTP | One-time password |
| Per-IO | Update the key per CoAP io |
| Per-IO-Inc1 | Update the key per CoAP io by just increase of 1 |
| Per-IO-NrPrng | Update the key per CoAP io by nonrepeating PRNG |
| Per-IO-Prng | Update the key per CoAP io by PRNG |
| Per-Session | Update the key per CoAP session |
| PRNG | Pseudorandom number generator |
| PSK | Pre-shared key |
| QKD | Quantum key distribution |
| RC4 | Rivest Cipher 4 |
| RN | Random number |
| ROM | Read-only Memory |
| RPK | Raw public key |
| RSA | Rivest–Shamir–Adleman |
| RX | Receive |
| SN | Serial number |
| SSID | Service set identifier |
| SSL | Secure sockets layer |
| TCP | Transmission Control Protocol |
| TLS | Transport Layer Security |
| TX | Transmit |
| Ubuntu | An open source operating system on Linux |
| UDP | User Datagram Protocol |
| UE | User equipment |
| URI | Uniform Resource Identifier |
| Uu | Wireless interface specification of 4G-LTE |
| WPA | Wi-Fi Protected Access |
| XOR | Exclusive-OR |
References
- Turner, V.; MacGillivray, C. IDC FutureScape: Worldwide IoT 2018 Predictions; International Data Corporation: Needham, MA, USA, 2017. [Google Scholar]
- Biral, A.; Centenaro, M.; Zanellan, A.; Vangelista, L.; Zorzi, M. The Challenges of M2M Massive Access in Wireless Cellular Networks. Digit. Commun. Netw. 2016, 1, 1–19. [Google Scholar] [CrossRef]
- Adeel, A.; Ahmad, J.; Larijani, H.; Hussain, A. A Novel Real-Time, Lightweight Chaotic-Encryption Scheme for Next-Generation Audio-Visual Hearing Aids. Cogn. Comput. 2020, 12, 589–601. [Google Scholar] [CrossRef]
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (CoAP); RFC 7252; Internet Engineering Task Force: Wilmington, DE, USA, 2014. [Google Scholar]
- Libcoap, C-Implementation of CoAP. Available online: https://libcoap.net/ (accessed on 21 December 2021).
- OpenSSL, Cryptography and SSL/TLS Toolkit. Available online: https://www.openssl.org/ (accessed on 21 December 2021).
- Lamport, L. Password Authentication with Insecure Communication. Comm. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Tsai, W.C.; Tsai, T.H.; Xiao, G.H.; Wang, T.J.; Lian, Y.R.; Huang, S.H. An Automatic Key-update Mechanism for M2M Communication and IoT Security Enhancement. In Proceedings of the IEEE International Conference on Smart Internet of Things, Beijing, China, 14–16 August 2020; pp. 354–355. [Google Scholar]
- Bellovin, S.M. Frank Miller: Inventor of the One-Time Pad. Cryptologia 2011, 35, 203–222. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication Theory of Secrecy Systems. Bell Sys. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Malikovich, K.M.; Turakulovich, K.Z.; Tileubayevna, A.J. A Method of Efficient OTP Generation Using Pseudorandom Number Generators. In Proceedings of the International Conference on Information Science and Communications Technologies, Tashkent, Uzbekistan, 4–6 November 2019; pp. 1–4. [Google Scholar]
- Imamah, One Time Password (OTP) Based on Advanced Encrypted Standard (AES) and Linear Congruential Generator (LCG). In Proceedings of the Electrical Power, Electronics, Communications, Controls and Informatics Seminar, Batu, Indonesia, 9–11 October 2018; pp. 39–394.
- Wu, L.; Cai, H.J.; Li, H. SGX-UAM: A Secure Unified Access Management Scheme with One Time Passwords via Intel SGX. IEEE Access 2021, 9, 38029–38042. [Google Scholar] [CrossRef]
- Wi-Fi Alliance. Available online: https://www.wi-fi.org/ (accessed on 21 December 2021).
- Church of Wifi WPA-PSK Rainbow Tables, The Renderlab. Available online: https://www.renderlab.net/projects/WPA-tables/ (accessed on 21 December 2021).
- Diffie, W.; Hellman, M.E. New Directions in Cryptography. IEEE Trans. Inform. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef] [Green Version]
- Ronald, L.; Shamir, A.; Adleman Leonard, M. The Original RSA Patent as filed with the U.S. Patent Office by Rivest. U.S. Patent 4,405,829, 14 December 1977. [Google Scholar]
- Merkle, R.C. Publishing a New Idea. Available online: http://www.merkle.com/1974/ (accessed on 21 December 2021).
- Sasaki, M. Quantum Key Distribution and Its Applications. IEEE Secur. Priv. 2018, 16, 42–48. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G. Quantum Cryptography: Public Key Distribution and Coin Tossing. In Proceedings of the IEEE International Conference of Computers, Systems, and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Zhang, H.G.; Ji, Z.X.; Wang, H.Z.; Wu, W.Q. Survey on quantum information security. China Comm. 2019, 16, 1–36. [Google Scholar] [CrossRef]
- Amer, O.; Garg, V.; Krawec, W.O. An Introduction to Practical Quantum Key Distribution. IEEE Aerosp. Electron. Syst. Mag. 2021, 36, 30–55. [Google Scholar] [CrossRef]
- Vadhan, S.P. Pseudorandomness. In Foundations and Trends in Theoretical Computer Science; Now Publishers: Norwell, MA, USA, 2012; Volume 7, pp. 1–336. [Google Scholar]
- Call for Stream Cipher Primitives, ECRYPT. Available online: https://www.ecrypt.eu.org/ (accessed on 21 December 2021).
- The eSTREAM Portfolio in 2012. Available online: https://www.ecrypt.eu.org/ecrypt2/documents/D.SYM.10-v1.pdf (accessed on 21 December 2021).
- Daemen, J.; Rijmen, V. AES Proposal: Rijndael. Available online: https://csrc.nist.gov/csrc/media/projects/cryptographic-standards-and-guidelines/documents/aes-development/rijndael-ammended.pdf (accessed on 21 December 2021).
- Daemen, J.; Rijmen, V. The Design of Rijndael: AES. In The Advanced Encryption Standard; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Coppersmith, D. The Data Encryption Standard (DES) and its Strength Against Attacks. IBM J. Res. Dev. 1994, 38, 243–250. [Google Scholar] [CrossRef]
- Barnes, R.; Thomson, M.; Pironti, A.; Langley, A. Deprecating Secure Sockets Layer Version 3.0; RFC 7568; Internet Engineering Task Force: Wilmington, DE, USA, 2015. [Google Scholar]
- 3GPP Standardization of NB-IOT Completed. Available online: http://www.3gpp.org/news-events/3gpp-news/1785-nb_iot_complete (accessed on 21 December 2021).
- NB-IoT Solution Provided by Institute for Information Industry. Available online: https://www.iii.org.tw/Files/FileManager/03-nbiot-190524FFINAL).pdf (accessed on 21 December 2021).
- Preshing, J. A Random Number Generator Which Outputs A Unique 32-Bit Integer Each Time It’s Called. Available online: https://github.com/preshing/RandomSequence (accessed on 21 December 2021).
- Lin, Y.T.; Huang, Y.H.; Hsiao, Y.H.; Cheng, Y.J.; Chang, J.S.; Wang, S.W.; Lin, F.P.; Wang, C.M. An Implementation of The Efficient Huge Amount of Pseudo-random Unique Numbers Generator and The Acceleration Analysis of Parallelization. In Proceedings of the International Conference on Data Science and Advanced Analytics, Shanghai, China, 30 October–1 November 2014; pp. 1237–1248. [Google Scholar]
- Fisher, R.A.; Yates, F. Statistical Tables for Biological, Agricultural and Medical Research; Oliver and Boyd: Edinburgh, UK, 1963. [Google Scholar]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Venegas-Andraca, S.E.; Elwahsh, H.; Piran, M.J.; Bashir, A.K.; Song, O.Y.; Mazurczyk, W. Providing End-to-End Security Using Quantum Walks in IoT Networks. IEEE Access 2020, 8, 92687–92696. [Google Scholar] [CrossRef]
- Health-Care IoT Devices Using D-OTP. Available online: https://youtu.be/HnX-qpJNHjw (accessed on 21 December 2021).
- Barker, E.; Kelsey, J. Recommendation for Random Number Generation Using Deterministic Random Bit Generators; NIST SP800-90A; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012. [Google Scholar]
- Bakiri, M.; Guyeux, C.; Franc, J.; Couchot, O.; Marangio, L.; Galatolo, S. A Hardware and Secure Pseudorandom Generator for Constrained Devices. IEEE Trans. Ind. Inform. 2018, 14, 3754–3765. [Google Scholar] [CrossRef]
- Kovatsch, M. Copper (Cu) CoAP User-Agent for Chrome. Available online: https://github.com/mkovatsc/Copper4Cr (accessed on 21 December 2021).
- M’Raihi, D.; Bellare, M.; Hoornaert, F.; Naccache, D.; Ranen, O. HOTP: An HMAC-Based One-Time Password Algorithm; RFC 4226; Internet Engineering Task Force: Wilmington, DE, USA, 2005. [Google Scholar]
- Mujahid, O.; Ullah, Z. High Speed Partial Pattern Classification System Using a CAM-Based LBP Histogram on FPGA. IEEE Embed. Syst. Lett. 2019, 12, 87–90. [Google Scholar] [CrossRef]






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tsai, W.-C.; Tsai, T.-H.; Wang, T.-J.; Chiang, M.-L. Automatic Key Update Mechanism for Lightweight M2M Communication and Enhancement of IoT Security: A Case Study of CoAP Using Libcoap Library. Sensors 2022, 22, 340. https://doi.org/10.3390/s22010340
Tsai W-C, Tsai T-H, Wang T-J, Chiang M-L. Automatic Key Update Mechanism for Lightweight M2M Communication and Enhancement of IoT Security: A Case Study of CoAP Using Libcoap Library. Sensors. 2022; 22(1):340. https://doi.org/10.3390/s22010340
Chicago/Turabian StyleTsai, Wen-Chung, Tzu-Hsuan Tsai, Te-Jen Wang, and Mao-Lun Chiang. 2022. "Automatic Key Update Mechanism for Lightweight M2M Communication and Enhancement of IoT Security: A Case Study of CoAP Using Libcoap Library" Sensors 22, no. 1: 340. https://doi.org/10.3390/s22010340





