Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity
Abstract
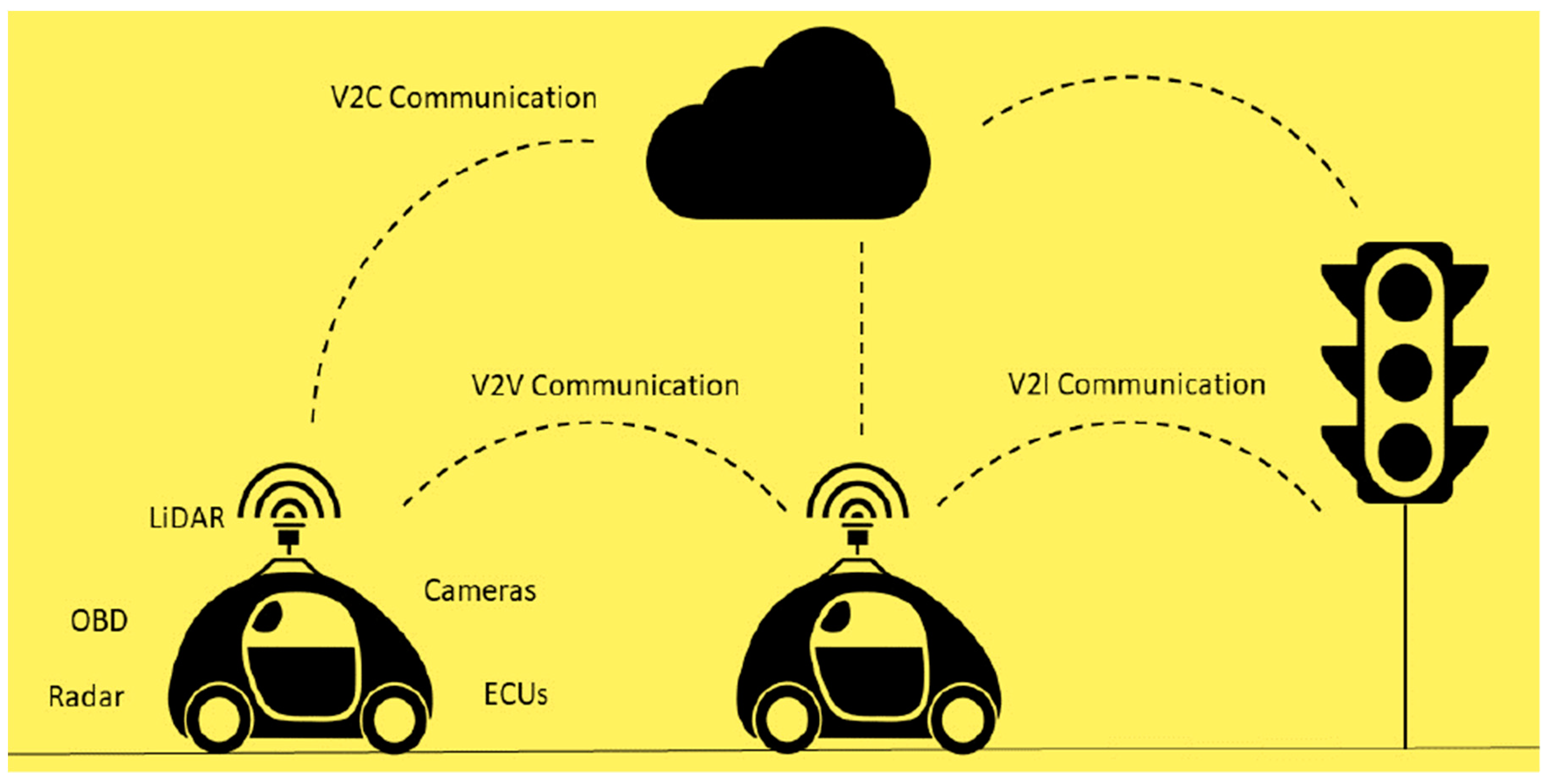
:1. Introduction
2. Related Works
3. Contribution
4. Materials and Methods
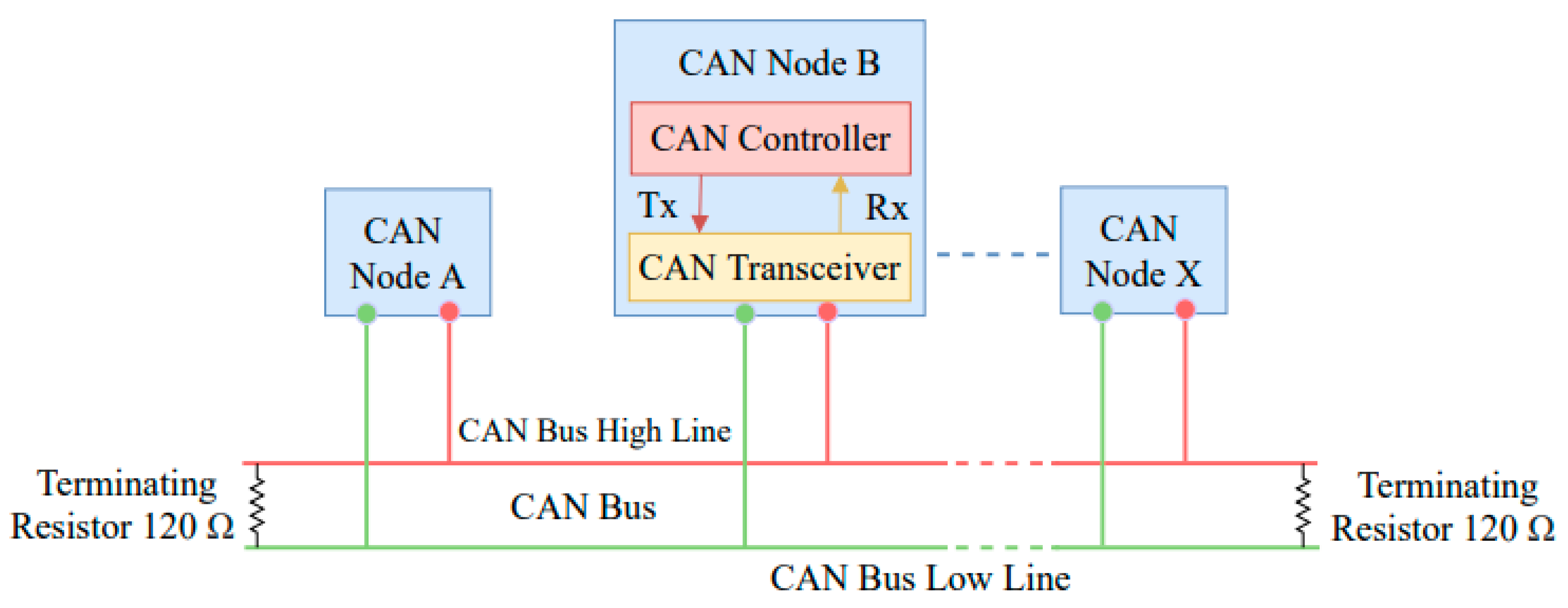
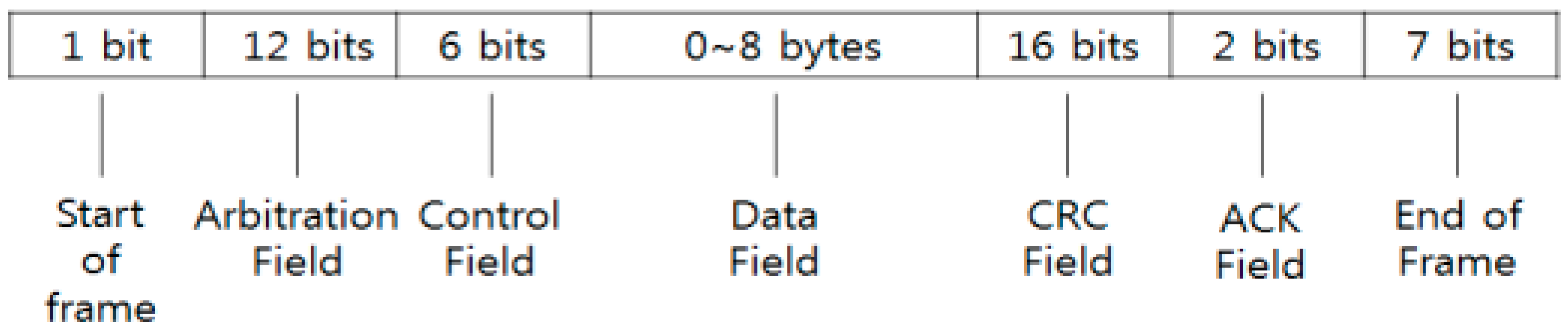
4.1. Dataset
4.2. Preprocessing
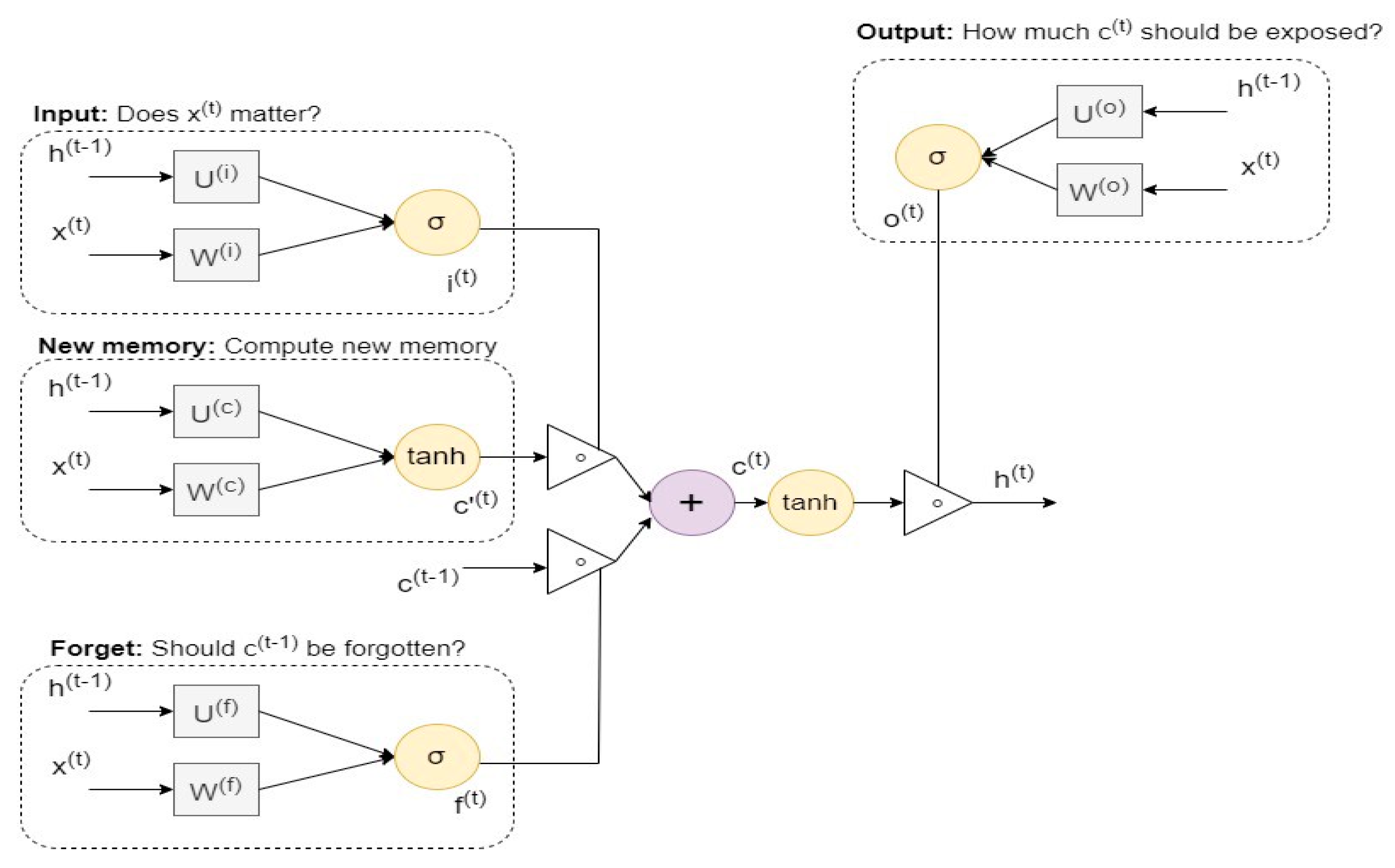
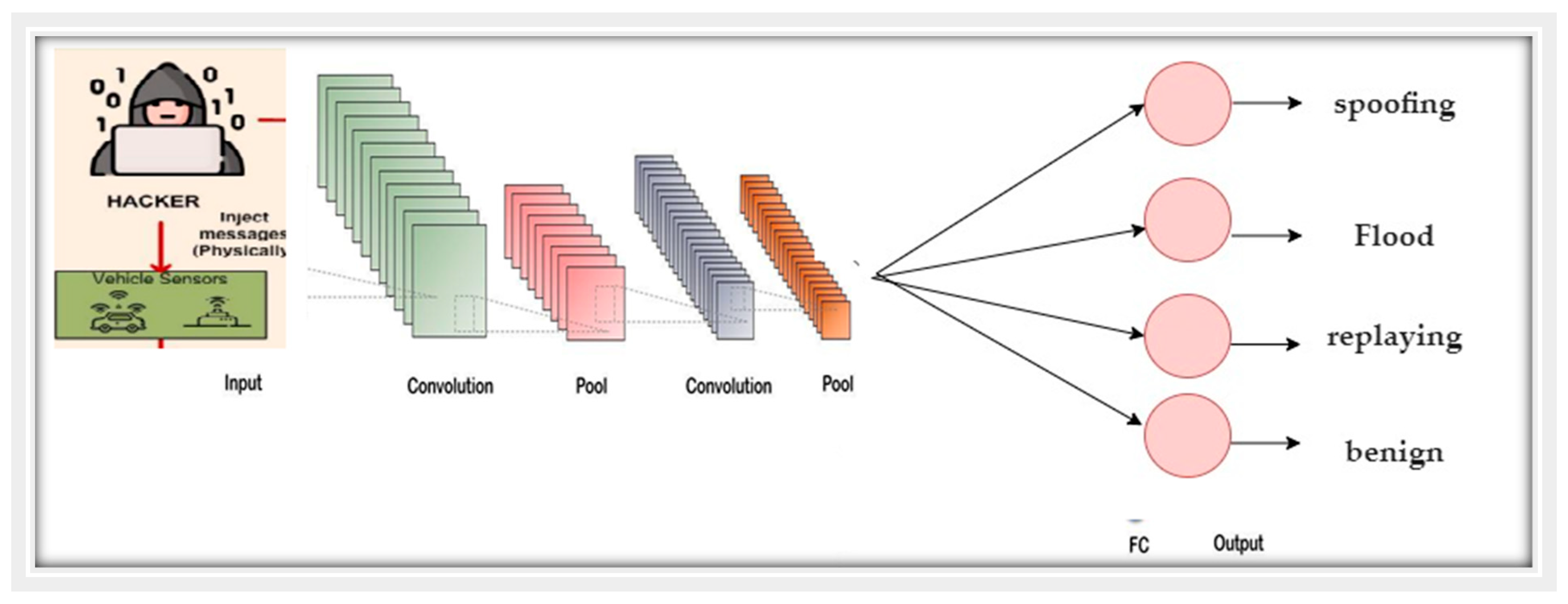
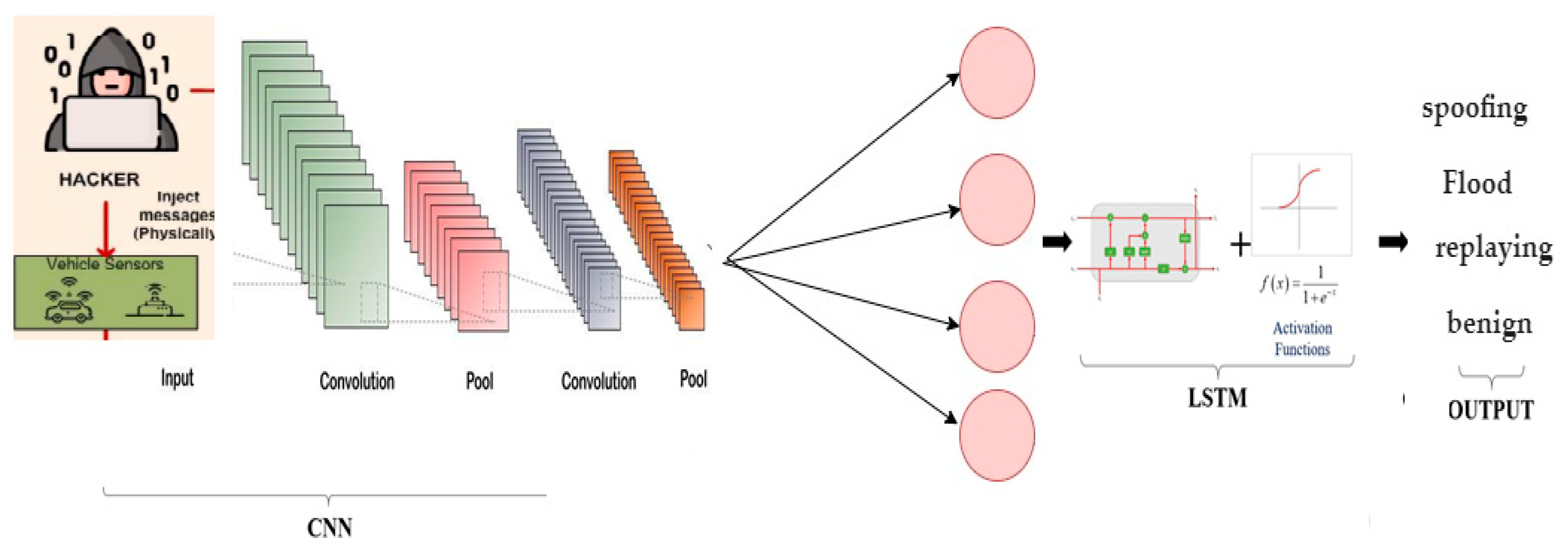
4.3. Proposed System of the Deep Learning Algorithm
| Algorithm 1. Algorithm of CNN-LSTM |
| Preprocessing data Class 4, input data 22222 Model = Sequential() model. Add(Conv1D(filters = 128, kernel_size = 1, strides = 1, padding = ‘same’, input shape = (train_data_st.shape [1], 1))) model. Add(Conv1D(filters = 128, kernel size = 1, strides = 1, padding = ‘same’)) model. Add(LSTM(64, activation = ‘relu’, return sequences = True)) model. Add(LSTM(64, return sequences = True)) model. Add(Flatten()) model.add(Dense(128, activation = ‘relu’)) model.add(Dense(256, activation = ‘relu’)) Build Model Input = Input(shape = (train_data_st.shape[1],1)) C = Conv1D(filters = 32, kernel_size = 1, strides = 1)(inp) C2 = Conv1D(filters = 32, kernel_size = 1, strides = 1, padding = ‘same’)(C) A1 = Activation(“relu”)(C11) C3 = Conv1D(filters = 32, kernel_size = 1, strides = 1, padding = ‘same’)(A11) S13 = Add()([C12, C]) A1 = Activation(“relu”)(S11) M11 = MaxPooling1D(pool_size = 1, strides = 2)(A12) C3 = Conv1D(filters = 32, kernel_size = 1, strides = 1, padding = ‘same’)(M11) A3 = Activation(“relu”)(C21) C4 = Conv1D(filters = 32, kernel_size = 1, strides = 1, padding = ‘same’)(A21) S4 = Add()([C22, M11]) A4 = Activation(“relu”)(S11) M4 = MaxPooling1D(pool_size = 1, strides = 2)(A22) C5 = Conv1D(filters = 32, kernel_size = 1, strides = 1, padding = ‘same’)(M21) A5 = Activation(“relu”)(C31) C6 = Conv1D(filters = 32, kernel_size = 1, strides = 1, padding = ‘same’)(A31) S5 = Add()([C32, M21]) A5 = Activation(“relu”)(S31) M31 = MaxPooling1D(pool_size = 1, strides = 2)(A32) F1 = Flatten()(M31) D1 = Dense(32)(F1) A66 = Activation(“relu”)(D1) D22 = Dense(32)(A66) D33 = Dense(labels.shape[1])(D22) A77 = Activation(“softmax”)(D33) model = Model(inputs = inp, outputs = A7) # opotimnaztion Paramters patience = 3, verbose = 1, factor = 0.5, lr = 0.00001 and optimizer = rms, epochs = 10 batch_size = 64 Forrms = keras.optimizers.rms = RMSprop(learning_rate = 0.001, rho = 0.9) history = model.fit(x_train_cnn,y_train, batch_size = batch_size, steps_per_epoch = x_train.shape[0]//batch_size, epochs = epochs, validation_data = (x_validate_cnn,y_validate), #validation_split = 0.10, callbacks = [learning_rate_reduction, checkpoint] |
4.4. Evaluation Metrics
5. Experiments
5.1. Splitting the Dataset
5.2. Environment Setup
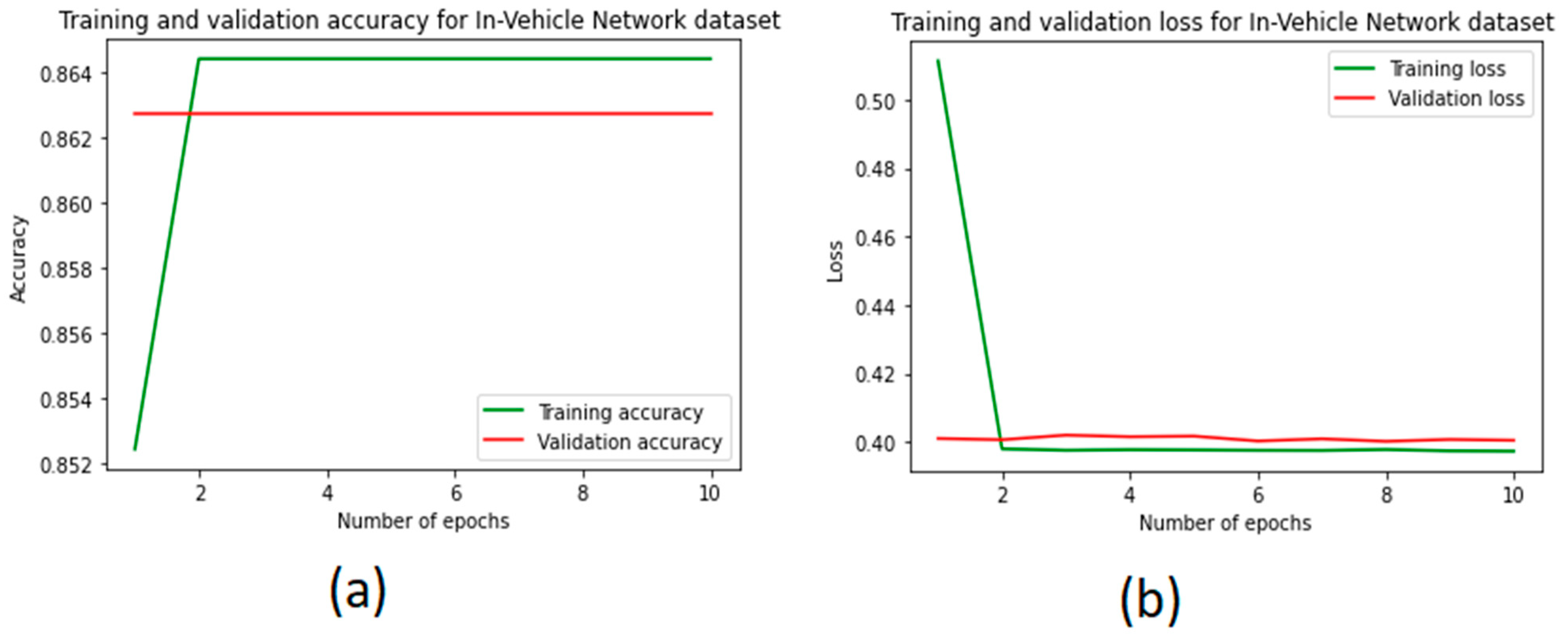
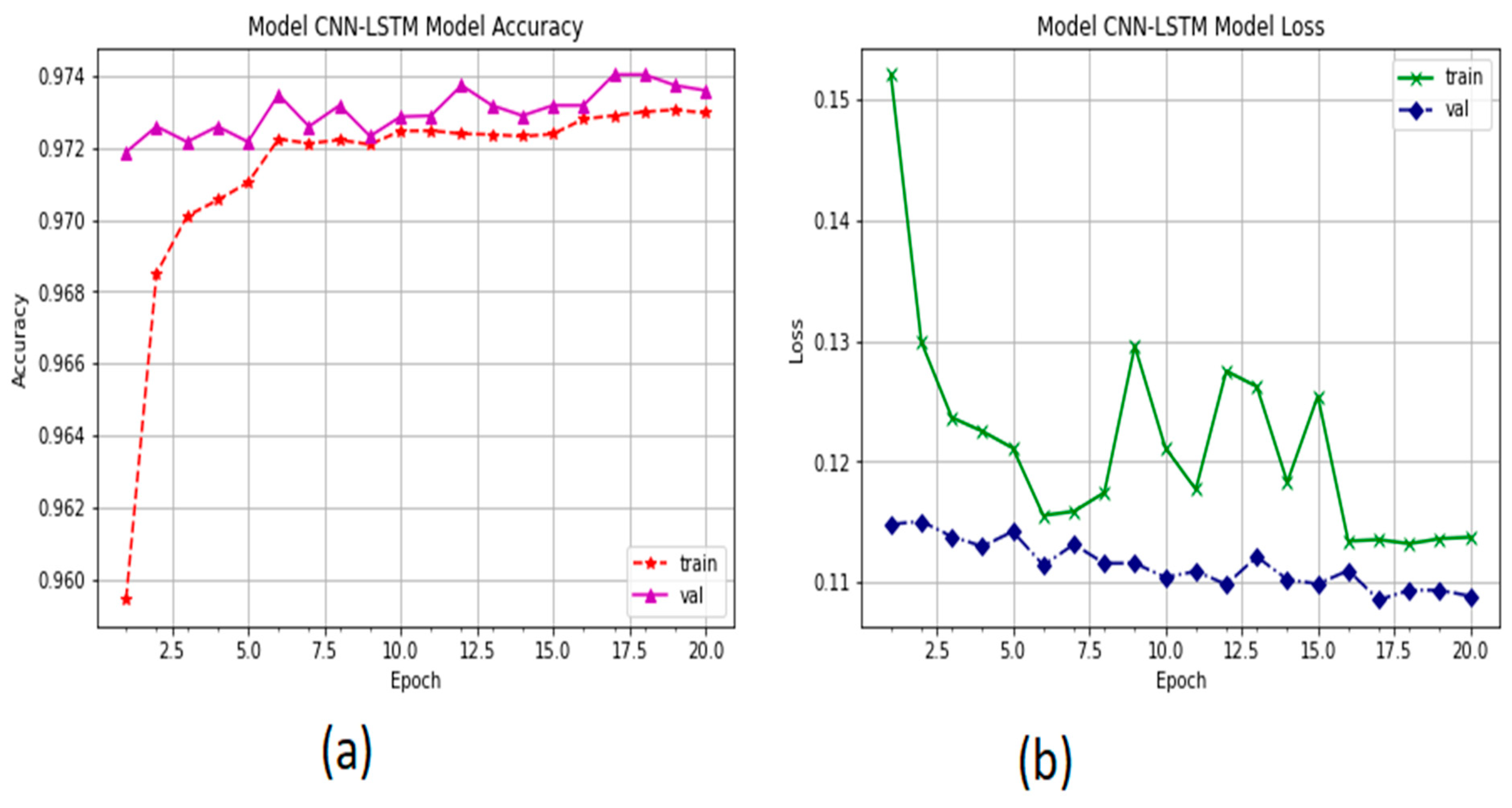
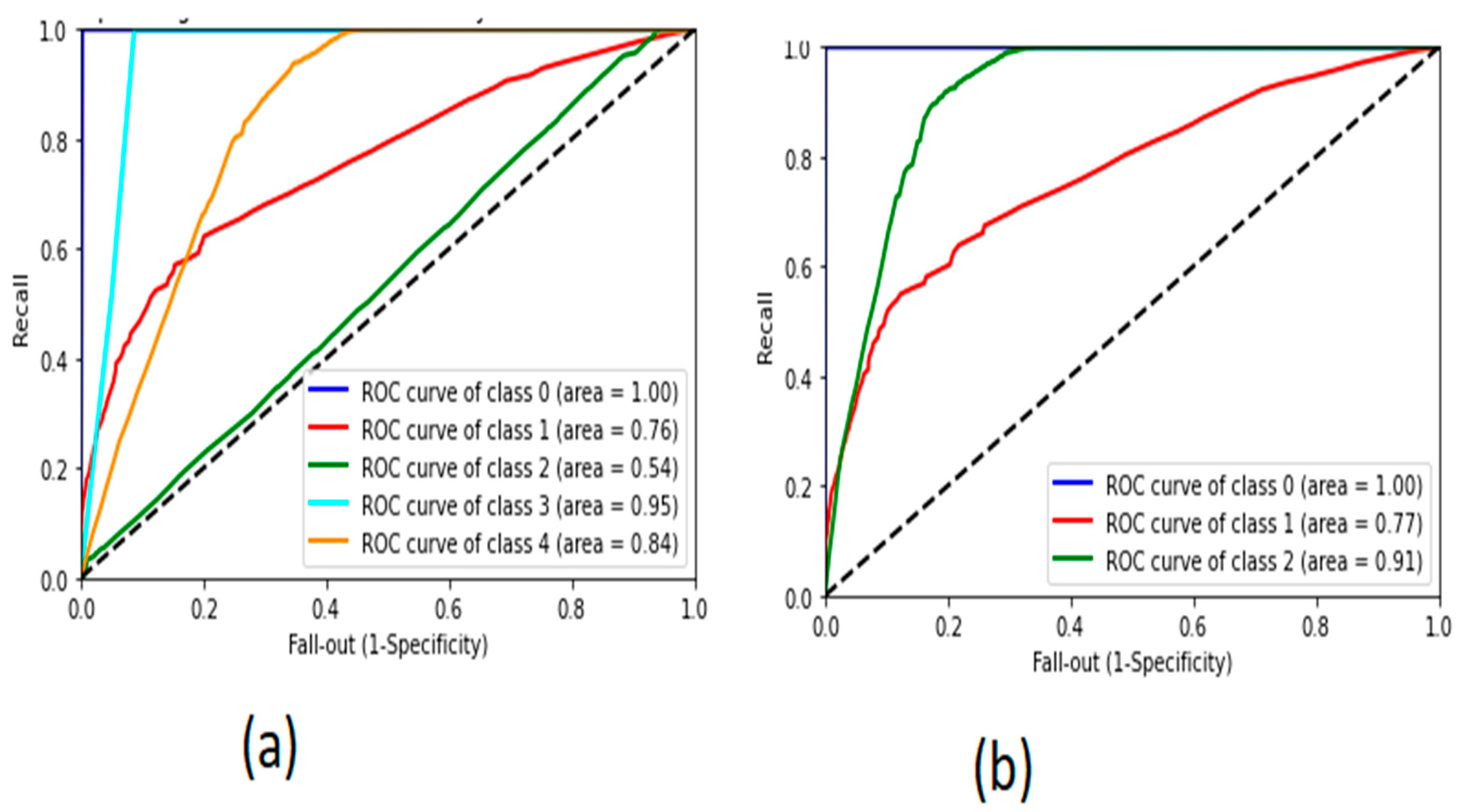
5.3. Results
6. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hartenstein, H.; Laberteaux, K.P. VANET: Vehicular Applications and Inter-Networking Technologies; John Wiley & Sons: Chichester, UK, 2009. [Google Scholar]
- Zeng, W.; Khalid, M.A.S.; Chowdhury, S. In-Vehicle Networks Outlook: Achievements and Challenges. IEEE Commun. Surv. Tutor. 2016, 18, 1552–1571. [Google Scholar] [CrossRef]
- Mehedi, S.T.; Anwar, A.; Rahman, Z.; Ahmed, K. Deep Transfer Learning Based Intrusion Detection System for Electric Vehicular Networks. Sensors 2021, 21, 4736. [Google Scholar] [CrossRef]
- Kiencke, U.; Dais, S.; Litschel, M. Automotive Serial Controller Area Network. SAE Trans. 1986, 95, 823–828. [Google Scholar]
- Vasudev, H.; Das, D.; Vasilakos, A.V. Secure message propagation protocols for IoVs communication components. Comput. Electr. Eng. 2020, 82, 106555. [Google Scholar] [CrossRef]
- Du, R.; Santi, P.; Xiao, M.; Vasilakos, A.V.; Fischione, C. The Sensable City: A Survey on the Deployment and Management for Smart City Monitoring. IEEE Commun. Surv. Tutor. 2019, 21, 1533–1560. [Google Scholar] [CrossRef]
- Barletta, V.; Caivano, D.; DiMauro, G.; Nannavecchia, A.; Scalera, M. Managing a Smart City Integrated Model through Smart Program Management. Appl. Sci. 2020, 10, 714. [Google Scholar] [CrossRef] [Green Version]
- Baldassarre, M.T.; Barletta, V.S.; Caivano, D. Smart Program Management in a Smart City. In Proceedings of the 2018 AEIT International Annual Conference, Bari, Italy, 3–5 October 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Zhou, J.; Dong, X.; Cao, Z.; Vasilakos, A.V. Secure and Privacy Preserving Protocol for Cloud-Based Vehicular DTNs. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1299–1314. [Google Scholar] [CrossRef]
- Baldassarre, M.T.; Barletta, V.; Caivano, D.; Scalera, M. Integrating security and privacy in software development. Softw. Qual. J. 2020, 28, 987–1018. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and Privacy for Cloud-Based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Gope, P.; Kumar, N.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber–physical systems. Future Gener. Comput. Syst. 2020, 108, 1267–1286. [Google Scholar] [CrossRef]
- Sommer, F.; Duerrwang, J.; Kriesten, R. Survey and Classification of Automotive Security Attacks. Information 2019, 10, 148. [Google Scholar] [CrossRef] [Green Version]
- Caivano, D. Continuous Software Process Improvement through Statistical Process Control. In Proceedings of the Ninth European Conference on Software Maintenance and Reengineering, Manchester, UK, 21–23 March 2005; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2005; pp. 288–293. [Google Scholar]
- Baldassarre, M.T.; Barletta, V.S.; Caivano, D.; Raguseo, D.; Scalera, M. Teaching cybersecurity: The hack-space integrated model, CEUR Workshop Proceedings. In ITASEC, Proceedings of the Third Italian Conference on Cyber Security, Pisa, Italy, 13–15 February 2019; University of BariAldo Moro: Bari, Italy, 2019; Volume 2315. [Google Scholar]
- Lokman, S.F.; Othman, A.T.; Abu-Bakar, M.-H. Intrusion detection system for automotive Controller Area Network (CAN) bus system: A review. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 184. [Google Scholar] [CrossRef] [Green Version]
- Carsten, P.; Andel, T.R.; Yampolskiy, M.; McDonald, J.T. In-Vehicle Networks. In Proceedings of the 10th Annual Cyber and Information Security Research Conference on-CISR ’15, London, UK, 6–8 April 2015; Association for Computing Machinery (ACM): New York, NY, USA; pp. 1–8. [Google Scholar]
- Gmiden, M.; Gmiden, M.H.; Trabelsi, H. An intrusion detection method for securing in-vehicle CAN bus. In Proceedings of the 2016 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA), Sousse, Tunisia, 19–21 December 2016; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2016; pp. 176–180. [Google Scholar]
- Young, C.; Zambreno, J.; Olufowobi, H.; Bloom, G. Survey of Automotive Controller Area Network Intrusion Detection Systems. IEEE Des. Test Comput. 2019, 36, 48–55. [Google Scholar] [CrossRef] [Green Version]
- Qu, X.; Yang, L.; Guo, K.; Ma, L.; Sun, M.; Ke, M.; Li, M. A Survey on the Development of Self-Organizing Maps for Unsupervised Intrusion Detection. Mob. Netw. Appl. 2019, 26, 808–829. [Google Scholar] [CrossRef]
- Yao, X.Q.; Tang, G.; Hu, X. Method for recognizing mechanical status of container crane motor based on SOM neural network. In IOP Conference Series: Materials Science and Engineering; IOP: London, UK, 2018; Volume 435, p. 12009. [Google Scholar]
- NCSL. Autonomous Vehicles|Self-Driving Vehicles Enacted Legislation; NCSL: Washington, DC, USA, 2019. [Google Scholar]
- Madrigal, A.C. Inside Waymo’s Secret World for Training Self-Driving Cars. In The Atlantic; Carnegie Mellon University: Pittsburgh, PA, USA, 23 August 2017. [Google Scholar]
- Dikmen, M.; Burns, C.M. Autonomous driving in the real world: Experiences with tesla autopilot and summon. In Proceedings of the 8th International Conference on Automotive User Interfaces and Interactive Vehicular Applications, New York, NY, USA, 24 October 2016; ACM: New York, NY, USA, 2016; pp. 225–228. [Google Scholar]
- Eustice, R. University of Michigan’s Work toward Autonomous Cars; Technical Report; University of Michigan: Ann Arbor, MI, USA, 2015. [Google Scholar]
- Fagnant, D.J.; Kockelman, K. Preparing a nation for autonomous vehicles: Intelligent connected vehicles: The industrial practices and impacts on automotive value-chains in China recommendations. Transp. Res. Part A Policy Pract. 2015, 77, 167–181. [Google Scholar] [CrossRef]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Chekoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Berkeley/Oakland, CA, USA, 16–19 May 2010. [Google Scholar]
- Checkoway, S.; Damon, M.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive experimental analyses of automotive attack surfaces. In Proceedings of the USENIX Security Symposium, San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Miller, C.; Valasek, C. A Survey of Remote Automotive Attack Surfaces; BlackHat: Las Vegas, NV, USA, 2014. [Google Scholar]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016. [Google Scholar]
- Song, H.M.; Woo, J.; Kim, H.K. In-vehicle network intrusion detection using deep convolutional neural network. Veh. Commun. 2020, 21, 100198. [Google Scholar] [CrossRef]
- Cover, T.M.; Hart, P. Nearest Neighbor Pattern Classification. IEEE Trans. Inf. Theory 1967, 13, 21–27. [Google Scholar] [CrossRef]
- Quinlan, J.R. Induction of Decision Trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Chen, X.; Jin, L.; Wang, X.; Guo, D. Network Intrusion Detection: Based on Deep Hierarchical Network and Original Flow Data. IEEE Access 2019, 7, 37004–37016. [Google Scholar] [CrossRef]
- Liang, L.; Ye, H.; Li, G.Y. Toward Intelligent Vehicular Networks: A Machine Learning Framework. IEEE Internet Things J. 2019, 6, 124–135. [Google Scholar] [CrossRef] [Green Version]
- Hoppe, T.; Kiltz, S.; Dittmann, J. Security threats to automotive CAN networks Practical examples and selected short-term countermeasures. Reliab. Eng. Syst. Saf. 2011, 96, 11–25. [Google Scholar] [CrossRef]
- Taylor, A.; Leblanc, S.; Japkowicz, N. Anomaly detection in automobile control network data with long short-term memory networks. In Proceedings of the IEEE International Conference on Data Science and Advanced Analytics (DSAA 2016), Montreal, QC, Canada, 17–19 October 2016; pp. 130–139. [Google Scholar]
- Wang, C.; Zhao, Z.; Gong, L.; Zhu, L.; Liu, Z.; Cheng, X. A Distributed Anomaly Detection System for In-Vehicle Network Using HTM. IEEE Access 2018, 6, 9091–9098. [Google Scholar] [CrossRef]
- Bezemskij, A.; Loukas, G.; Gan, D.; Anthony, R.J. Detecting Cyber-Physical Threats in an Autonomous Robotic Vehicle Using Bayesian Networks. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, 21–23 June 2017; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2017; pp. 98–103. [Google Scholar]
- Kang, M.-J.; Kang, J.-W. A Novel Intrusion Detection Method Using Deep Neural Network for In-Vehicle Network Security. In Proceedings of the 2016 IEEE 83rd Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2016; pp. 1–5. [Google Scholar]
- Kalash, M.; Rochan, M.; Mohammed, N.; Bruce, N.D.B.; Wang, Y.; Iqbal, F. Malware Classification with Deep Convolutional Neural Networks. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Lin, Z.; Shi, Y.; Xue, Z. IDSGAN: Generative Adversarial Networks for Attack Generation against Intrusion Detection. arXiv 2018, arXiv:1809.02077. [Google Scholar]
- Miller, C.; Valasek, C. Remote Exploitation of an Unaltered Passenger Vehicle. In Proceedings of the Black Hat USA 2015, Las Vegas, NV, USA, 1–6 August 2015; pp. 1–91. [Google Scholar]
- Miller, C. Lessons learned from hacking a car. IEEE Des. Test Comput. 2019, 36, 7–9. [Google Scholar] [CrossRef]
- Petit, J.; Shladover, S.E. Potential cyberattacks on automated vehicles. IEEE Trans. Intell. Transp. Syst. 2015, 16, 546–556. [Google Scholar] [CrossRef]
- He, Q.; Meng, X.; Qu, R. Survey on cyber security of CAV. In Cooperative Positioning and Service (CPGPS); IEEE: Harbin, China, 2017; pp. 351–354. [Google Scholar]
- Integrating Autonomous Vehicle Safety and Security. 2017. Available online: https://www.researchgate.net/publication/321323032_Integrating_Autonomous_Vehicle_Safety_and_Security (accessed on 10 March 2019).
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. Veh. Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- Alkahtani, H.; Aldhyani, T.H.H. Botnet Attack Detection by Using CNN-LSTM Model for Internet of Things Applications. Secur. Commun. Netw. 2021, 2021, 3806459. [Google Scholar] [CrossRef]
- Khan, M.A.; Karim, M.R.; Kim, Y. A Scalable and Hybrid Intrusion Detection System Based on the Convolutional-LSTM Network. Symmetry 2019, 11, 583. [Google Scholar] [CrossRef] [Green Version]
- Alkahtani, H.; Aldhyani, T.; Al-Yaari, M. Adaptive anomaly detection framework model objects in cyberspace. Appl. Bionics Biomech. 2020, 2020, 6660489. [Google Scholar] [CrossRef] [PubMed]
- Kim, J.; Kim, J.; Kim, H.; Shim, M.; Choi, E. CNN-Based Network Intrusion Detection against Denial-of-Service Attacks. Electronics 2020, 9, 916. [Google Scholar] [CrossRef]
- Zheng, Z.; Yatao, Y.; Niu, X. Wide & Deep Convolutional Neural Networks for Electricity-Theft Detection to Secure Smart Grids. IEEE Trans. Ind. Inform. 2017, 14, 1606–1615. [Google Scholar]
- Ullah, A.; Javaid, N.; Omaji, S. CNN and GRU based Deep Neural Network for Electricity Theft Detection to Secure Smart Grid. In Proceedings of the 2020 International Wireless Communications and Mobile Computing, Limassol, Cyprus, 15–19 June 2020. [Google Scholar]
- Yao, R.; Wang, N.; Liu, Z.; Chen, P.; Sheng, X. Intrusion Detection System in the Advanced Metering Infrastructure: A Cross-Layer Feature-Fusion CNN-LSTM-Based Approach. Sensors 2021, 21, 626. [Google Scholar] [CrossRef] [PubMed]
- Kang, M.J.; Kang, J.W. Intrusion Detection System Using Deep Neural Network for In-Vehicle Network Security. PLoS ONE 2016, 11, e0155781. [Google Scholar] [CrossRef] [PubMed]
- Loukas, G.; Vuong, T.; Heartfield, R.; Sakellari, G.; Yoon, Y.; Gan, D. Cloud-Based Cyber-Physical Intrusion Detection for Vehicles Using Deep Learning. IEEE Access 2017, 6, 3491–3508. [Google Scholar] [CrossRef]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based Intrusion Detection System for In-Vehicle Network. In Proceedings of the IEEE Access 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Zhu, K.; Chen, Z.; Peng, Y.; Zhang, L. Mobile Edge Assisted Literal Multi-Dimensional Anomaly Detection of In-Vehicle Network Using LSTM. IEEE Trans. Veh. Technol. 2019, 68, 4275–4284. [Google Scholar] [CrossRef]
- Avatefipour, O.; Al-Sumaiti, A.S.; El-Sherbeeny, A.M.; Awwad, E.M.; Elmeligy, M.A.; Mohamed, M.A.; Malik, H. An Intelligent Secured Framework for Cyberattack Detection in Electric Vehicles’ CAN Bus Using Machine Learning. IEEE Access 2019, 7, 127580–127592. [Google Scholar] [CrossRef]
- Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal. Smart Cities 2020, 3, 17–30. [Google Scholar] [CrossRef] [Green Version]




| Attacks | Description |
|---|---|
| Flood Attack | Sending flood messages from CAN to different ECU nodes. The attacks were injected every 0.3 ms. |
| Replaying Attack | The replaying attacks send a message to CAN, earlier sent by users that have injected CAN messages containing replaying attacks. The injections occurred every 0.5 ms. |
| Spoofing Attack (RPM/gear) | Injecting attacks to CAN messages related to RPM/gear information. They were injected every 1 ms. |
| Feature | |
|---|---|
| Timestamp | recorded time (s) |
| CAN ID | identifier of CAN message in HEX (ex. 043f) |
| DLC | number of data bytes, from 0 to 8 |
| DATA [0~7] | data value (byte) |
| #Labels | Volume |
|---|---|
| Flood attack | 38,657 |
| Replaying attack | 13,294 |
| Spoofing attack | 2890 |
| Normal packets | 739,679 |
| Fuzzing | 22,527 |
| Parameters | Size of Values |
|---|---|
| Convolutions layer | 128 |
| Kernel size | 5 |
| Size of max pooling | 5 |
| Size of Drop out | 0.50 |
| Size of Fully connected | 256 |
| Name of Activation function | tanh |
| Optimizers function | RMSprop |
| Learning_rate | 0.001 |
| #Data | #Instance Values |
|---|---|
| Training | 490,526 |
| Testing | 240,258 |
| Validation | 70,076 |
| Hardware | Software |
|---|---|
| 8 GB RAM | Python |
| CPU I7 | Jupyter |
| Operating System: Windows |
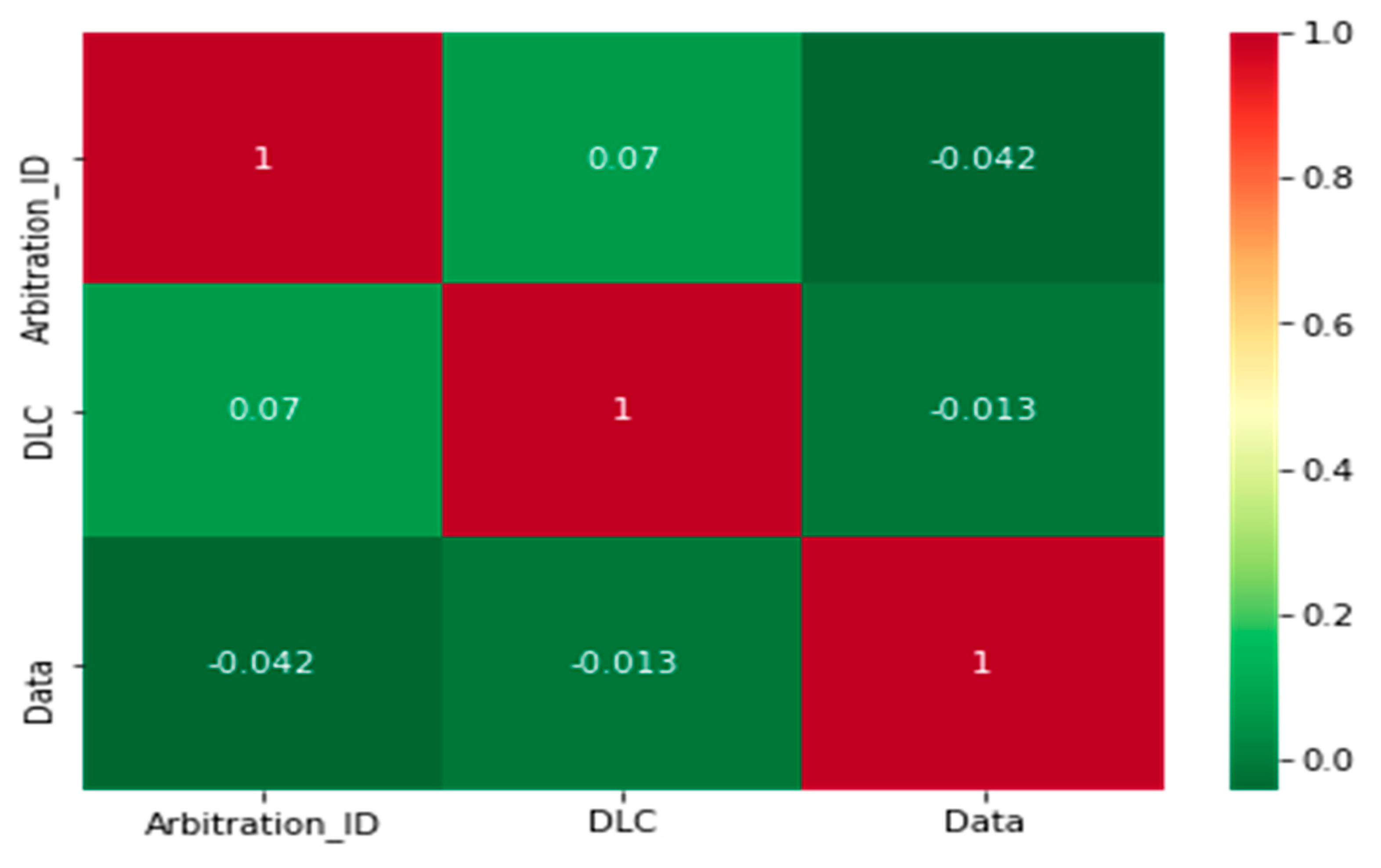
| Features | Mean | Standard Deviation | Minimum | Maximum |
|---|---|---|---|---|
| Arbitration ID | 1.80 | 1.67 | 0.00 | 8.00 |
| DLC | 7.50 | 1.188 | 2.00 | 8.00 |
| Data | 1.61 | 5.98 | 0.00 | 2.78 |
| Dataset | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| Normal | 0.86 | 100 | 93 |
| Attacks | 0.00 | 0.00 | 0.00 |
| Accuracy | 0.86 | ||
| Weighted average | 0.75 | 0.86 | 0.80 |
| Attacks | Precision % | Recall % | F1-Score % |
|---|---|---|---|
| Benign | 95 | 100 | 97 |
| Flood | 91 | 0.09 | 0.16 |
| Replaying | 0.0 | 0.0 | 0.0 |
| Spoofing | 0.0 | 0.0 | 0.0 |
| Fuzzy | 96 | 100 | 98 |
| Accuracy 95.44% | |||
| Weighted average | 93 | 95 | 93 |
| Loss 0.20 | |||
| Attacks | Precision % | Recall % | F1-Score % |
|---|---|---|---|
| Benign | 99 | 100 | 99 |
| Flood | 66 | 11 | 18 |
| Fuzzy | 97 | 100 | 99 |
| Accuracy | 97.30% | ||
| Weighted average | 97 | 97 | 96 |
| Loss 0.11 | |||
| Models | Labels | Precision (%) | Recall (%) | F1-Score (%) | Accuracy (%) |
|---|---|---|---|---|---|
| CNN | Two | 75 | 86 | 80 | 86 |
| CNN-LSTM | Six | 93 | 95 | 93 | 95.44 |
| CNN-LSTM | Three | 97 | 97 | 96 | 97.30 |
| Ref. | Models | Accuracy % | Attack Types |
|---|---|---|---|
| Ref. [56] | Deep learning model | 95% | Normal and attacks (Two classes) |
| Ref. [57] | Deep learning model | 85% | DoS, Command Injection, Malware attacks |
| Ref. [58] | Generative adversarial networks | 95% | DoS, Fuzzing, and Gear attacks |
| Ref. [59] | LSTM | 80% | Spoofing, Replay, and Flooding attacks |
| Ref. [60] | Machine learning | 90% | DoS, Fuzzing, Spoofing attacks |
| Ref. [61] | Neural network–LSTM | 90% | DoS, Fuzzing, Spoofing attacks |
| Proposed model | CNN-LSTM | 97% | DoS, Fuzzing, Spoofing, Replaying |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aldhyani, T.H.H.; Alkahtani, H. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors 2022, 22, 360. https://doi.org/10.3390/s22010360
Aldhyani THH, Alkahtani H. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors. 2022; 22(1):360. https://doi.org/10.3390/s22010360
Chicago/Turabian StyleAldhyani, Theyazn H. H., and Hasan Alkahtani. 2022. "Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity" Sensors 22, no. 1: 360. https://doi.org/10.3390/s22010360
APA StyleAldhyani, T. H. H., & Alkahtani, H. (2022). Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors, 22(1), 360. https://doi.org/10.3390/s22010360







