Analysis of LoRaWAN 1.0 and 1.1 Protocols Security Mechanisms
Abstract
:1. Introduction
- (i)
- Provide a comprehensive overview of the two LoRaWAN architectures’ communication protocols with a focus on security aspects.
- (ii)
- Highlight security-related compatibility issues between the two LoRaWAN major versions, v1.0 and v1.1.
- (iii)
- Analyze the compatibility issues within the two architecture components by interchanging NS and ED versions (homogeneity and heterogeneity). Furthermore, we analyze how security session keys are generated and how integrity and confidentiality are guaranteed in LoRaWAN.
2. LoRaWAN
2.1. LoRaWAN-Alliance
2.2. LoRa Technology
2.3. LoRaWAN Protocol
- LoRaWAN version 1.0 (January 2015) [19]: The first approved version of LoRaWAN 1.0.
- LoRaWAN version 1.0.1 (February 2016) [20]: This minor revision clarified some points that were not clear in the previous version, added some frequency plans, and made some modifications to MAC commands.
- LoRaWAN version 1.0.2 (July 2016) [21]: This minor revision added more MAC commands, fixed some errors in the previous version, and moved the Section "Physical Layer" to a separate document.
- LoRaWAN version 1.1 (October 2017) [22]: This major revision presented a new architecture by adding a new server called Join Server (JS), provided many enhancements in the security mechanism, such as using two root keys instead of one to derive the session security keys, and adding many countermeasures to avoid some vulnerabilities reported in the previous versions.
- LoRaWAN version 1.0.3 (July 2018) [23]: This minor revision related to v1.0.2 reused the same specifications for the class B devices mentioned in LoRaWAN version 1.1, added some MAC commands for class A devices, and deprecated some others.
- LoRaWAN version 1.0.4 (October 2020) [24]: This minor revision related to v1.0.3 provided some clarification on matters such as FCnt usage and behaviors, ADR behavior, channel selection procedure during joining, and retransmission backoff. We noticed two major security-related changes in this release: DevNonce generation is incremental instead of random, and AppEUI and AppNonce were replaced with JoinEUI and JoinNonce.
2.4. LoRaWAN Limitations
2.5. LoRaWAN Architectures
2.5.1. LoRaWAN v1.0.x Architecture
2.5.2. LoRaWAN v1.1 Architecture
2.6. Basic Messages with LoRaWAN
2.6.1. Message Structures Used in LoRaWAN v1.0.x
- Join-request: This type of message is used each time an end-device (ED) wants to join the network server (NS) in order to open a new session with it. This message is sent by an ED after powering on or resetting, or when the terminal wants to change its security session keys.
- Join-accept: This type of message is a response to the join-request message. It is created and sent by JS if the ED has permission to join the network.
- Unconfirmed dataUp: this type of message is sent by an ED to an NS when the terminal decides to send data that do not require acknowledgment.
- Unconfirmed dataDown: this type of message is sent by an NS to an ED when the NS has data to send which does not require acknowledgment. It can only be sent during one of the two reception windows opened by an ED after an uplink communication.
- Confirmed dataUp: This type of message is distinguished from unconfirmed dataUP by the need for an acknowledgment from the receiver (NS).
- Confirmed dataDown: This type of message is distinguished from unconfirmed dataDown by the need for an acknowledgment from the receiver (ED).
2.6.2. Message Structure Used in LoRaWAN v1.1 Architecture
3. Related Works
4. LoRaWAN Compatibility Scenarios: Basic Security Concepts
4.1. First Scenario: ED v1.0 with NS v1.0
- Sixteen-byte wide security session keys (NwkSkey and AppSkey),
- Two or three-byte frame counters (FCntUp and FCntDown),
- A four-byte address (DevAddr) to identify the ED in the network.
4.1.1. Security Session Context Generation (OTA Activation)
4.1.2. Security Session Context Generation (ABP Activation)
4.1.3. Confidentiality of Messages
- a
- Defining a sequence of blocks /i = 1 k (k = ceil(len(FRMPayload)/16)) that mainly contains Dir (0 for dataUp or 1 for dataDown), DevAddr, a counter (FCntUp for dataUp or FCntDown for dataDown), and i. Each block has a size of 128 bits.
- b
- Calculating a stream of keys (a sequence S of blocks ) by encryption the sequence of blocks , already calculated above, using the AES algorithm.
- S =
- = aes128_encrypt(K,) i = 1 k
- K = NwkSKey or AppSkey
- c
- The encryption or decryption is calculated by truncating (FRMPayload) XOR S to the first len(FRMPayload) bytes.
4.1.4. Integrity and Authenticity of Messages
- cmac = aes128_cmac(AppKey, X)
- MIC = cmac[0…3]
- Defining block which is mainly composed Dir (0: dataUp, 1: dataDown), DevAddr, FCntUp or FCntDown and len(X).
- cmac = aes128_cmac(NwkSKey, X)
- MIC = cmac[0…3]
4.2. Second Scenario: ED v1.1 with NS v1.1
4.2.1. LoRWAN Enhancements in v1.1
- fNS: only forward messages exchanged between ED and sNS or EDs and hNS.
- sNS: forwards messages between hNS and EDs directly or via fNS and sends MAC commands to EDs directly or via fNS
- hNS: forwards messages between EDs and the application server (AS) directly or via sNS or fNS, and sends MAC commands to ED directly or via sNS or fNS
- AppSKey: derived from AppKey and used for data encryption,
- NwkSEncKey: derived from NwkKey used for MAC command encryption,
- SNwkSIntKey: derived from NwkKey used by hNS or SNs for checking message integrity,
- FNwkSIntKey: derived from NwkKey used by hNS or FNs for checking message integrity.
4.2.2. Security Session Context Generation: OTA Activation
- A.
- Activation a new session for the first time
- B.
- Reactivation During an Ongoing Session
4.2.3. Security Session Context Generation (ABP Activation)
4.2.4. Confidentiality of Messages
- a
- A single block A (16 bytes wide) mainly contains Dir (Dir is 0x00 for uplink frames; otherwise 0x01), DevAddr, and a frame counter (FCntUp for dataUp, NFCntDwn for dataDown carrying MAC Commands, or AFCntDwn for dataDown carrying data application).
- b
- Calculating block S by encryption block A using the AES algorithm. The encryption key used is NwkSEncKey generated in the activation phase.
- c
- Encryption or decryption is calculated by truncating (FOpts) XOR S to the first “FOptsLen” bytes.
- a
- Defining a sequence of blocks /i = 1 ceil(len(FRMPayload)/16) mainly containing Dir, DevAddr, frame counter (FCntUp, NFCntDown, or AFCntDown), and i. Each block has a size of 16 bytes.
- b
- Calculating a stream of keys (a sequence S of blocks ) by encryption a sequence of blocks using AES algorithm:
- S =
- = aes128_encrypt(K,) i = 1 k
- K = NwkSEncKey or AppSkey
- c
- Encryption or decryption is calculated by truncating (FRMPayload) XOR S to the first len(FRMPayload) bytes.
4.2.5. Integrity and Authenticity of Messages
- cmac = aes128_cmac(NwkKey, MHDR∣JoinEUI∣DevEUI∣DevNonce)
- MIC = cmac[0…3]
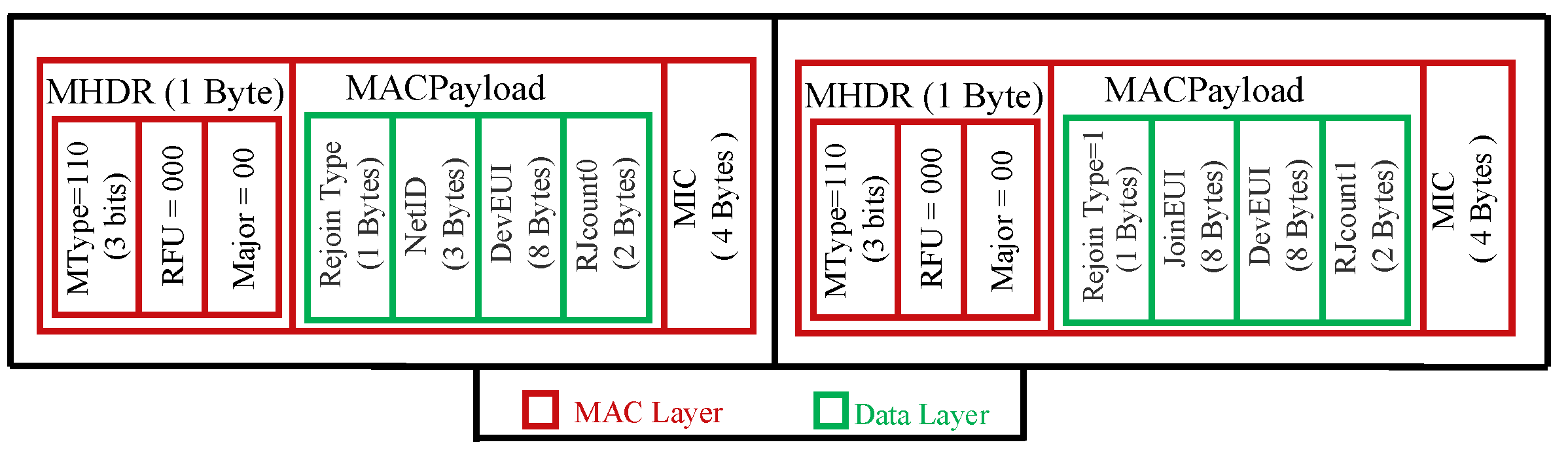
- cmac = aes128_cmac(SNwkSIntKey, MHDR∣Rejoin Type= 0 or 2∣NetID∣DevEUI∣RJCount0)
- MIC = cmac[0…3]
- cmac = aes128_cmac(JSIntKey, MHDR∣Rejoin Type = 1∣JoinEUI ∣DevEUI∣RJCount1)
- MIC = cmac[0…3]
- cmac=aes128_cmac(JSIntKey, JoinReqType∣JoinEUI∣DevNonce∣MHDR∣JoinNonce∣NetID∣DevAdd∣DLSettings∣RxDelay∣CFList)
- MIC=cmac[0…3]
- Defining block which is mainly composed of ConfFCnt, Dir, DevAddr, AFCntDown or NFCntDown, and len(msg).
- cmac = aes128_cmac(SNwkSIntKey, msg).
- MIC=cmac[0…3]
- Defining block , which is mainly composed of Dir, DevAddr, FCntUp, and len(msg).
- Defining block , which is mainly composed of ConfFCnt, TxDr (data rate for uplink transmission), TxCh (index of the channel used for transmission), Dir, DevAddr, FCntUp, and len(msg).
- cmacS = aes128_cmac(SNwkSIntKey, msg)
- cmacF = aes128_cmac(FNwkSIntKey, msg)
- MIC = cmacS[0…1]∣cmacF[0…1]
4.3. Third Scenario: ED v1.1 with NS v1.0
4.3.1. Message Structure
4.3.2. Security Session Context Generation (ABP Activation)
4.3.3. Security Session Context Generation (OTA Activation)
- FNwkSIntKey = aes128_encrypt(Nwkkey, 0x01∣AppNonce∣NetID∣DevNonce )
- SNwkSIntKey = NwkSEncKey = FNwkSIntKey
- AppSKey = aes128_encrypt(NwkKey, 0x02∣AppNonce∣NetID∣DevNonce )
4.3.4. Confidentiality of Messages
4.3.5. Integrity and Authenticity of Messages
- cmac = aes128_cmac(RootKey,X)
- MIC = cmac[0…3]
- on the NS side
- -
- Defining block which is mainly composed of Dir (0: uplink, 1: downlink), DevAddr, FCntUp or FCntDown, and len(X).
- -
- cmac = aes128_cmac(NwkSKey, X)
- -
- MIC = cmac[0…3]
- on the ED side
- -
- Defining block which is mainly composed of Dir (0: uplink, 1: downlink), DevAddr, FCntUp or FCntDown, and len(X).
- -
- cmacF = aes128_cmac(FNwkSIntKey, X)
- -
- MIC = cmacF[0…3]
4.4. Fourth Scenario: ED v1.0 with NS v1.1
4.4.1. Message Structure
4.4.2. Security Session Context Generation (OTA Activation)
4.4.3. Security Session Context Generation (ABP Activation)
4.4.4. Confidentiality of Messages
4.4.5. Integrity and Authenticity of Messages
4.5. Synthesis
5. Current Research Directions in LoRaWAN
5.1. Network Scalability
5.2. Power Consumption
5.3. Security
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ABP | Activation By Personalization |
| ADR | Adaptive Data Rate |
| AES | Advanced Encryption Standard |
| AFCntDwn | Application Frame Counter Down |
| AppEUI | Application Extended Unique Identifier |
| AppKey | Application Key |
| AppSkey | Application Session Key |
| AS | Application Server |
| CRC | Cyclic Redundancy Check |
| CSS | Chirp Spread Spectrum |
| DevAddr | Device Address |
| DevEUI | Device Extended Unique Identifier |
| ED | End-Node |
| FCntDown | Frame Counter Down |
| FCntUP | Frame Counter UP |
| fNS | forward Network Server |
| FNwkSIntKey | Forwarding Network Session Integrity Key |
| GW | GateWay |
| hNS | home Network Server |
| IoT | Internet of Things |
| ISM band | Industrial, Scientific and Medical band |
| JoinEUI | Join Server Extended Unique Identifier |
| JS | Join Server |
| JSEncKey | Join Server Encryption Key |
| JSIntKey | join Server Integrity Key |
| LoRa | Long Range |
| LPWAN | Low Power Wide Area Network |
| MCU | Micro-Controller Unit |
| MAC | Media Access Control |
| MIC | Message Integrity Code |
| NS | Network Server |
| NFCntDwn | Network Frame Counter Down |
| NwkKey | Network Key |
| NwkSEncKey | Network Session Encryption Key |
| NwkSkey | Network Session Key |
| OTAA | Over-The-Air Activation |
| OTP | One Time Password |
| sNS | serving Network Server |
| SNwkSIntKey | Serving Network Session Integrity Key |
References
- Ericsson Mobility Report: IoT Connections Outlook. Available online: https://www.ericsson.com/en/reports-and-papers/mobility-report/dataforecasts/iot-connections-outlook (accessed on 15 August 2021).
- Akyildiz, I.; Kak, A.; Nie, S. 6G and Beyond: The Future of Wireless Communications Systems. IEEE Access 2020, 8, 133995–134030. [Google Scholar] [CrossRef]
- LoRaWAN Specifications. Available online: https://lora-alliance.org/about-lorawan/ (accessed on 10 August 2021).
- Lonzetta, A.M.; Cope, P.; Campbell, J.; Mohd, B.J.; Hayajneh, T. Security vulnerabilities in Bluetooth technology as used in IoT. J. Sens. Actuator Netw. 2018, 7, 28. [Google Scholar] [CrossRef] [Green Version]
- Raza, S.; Misra, P.; He, Z.; Voigt, T. Bluetooth smart: An enabling technology for the Internet of Things. In Proceedings of the 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Abu Dhabi, United Arab Emirates, 19–21 October 2015; pp. 155–162. [Google Scholar]
- Aggarwal, R.; Das, M. RFID security in the context of “internet of things”. In Proceedings of the First International Conference on Security of Internet of Things, Kerala, India, 17–19 August 2012; pp. 51–56. [Google Scholar]
- Khoo, B. RFID as an Enabler of the Internet of Things: Issues of Security and Privacy. In Proceedings of the 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, Dalian, China, 19–22 October 2011; pp. 709–712. [Google Scholar]
- Ramya, C.M.; Shanmugaraj, M.; Prabakaran, R. Study on ZigBee technology. In Proceedings of the 2011 3rd International Conference on Electronics Computer Technology, Kanyakumari, India, 8–10 April 2011; pp. 297–301. [Google Scholar]
- Sruthy, S.; George, S.N. WiFi enabled home security surveillance system using Raspberry Pi and IoT module. In Proceedings of the 2017 IEEE International Conference on Signal Processing, Informatics, Communication and Energy Systems (SPICES), Kollam, India, 8–10 August 2017; pp. 1–6. [Google Scholar]
- Nair, K.K.; Abu-Mahfouz, A.M.; Lefophane, S. Analysis of the narrow band internet of things (NB-IoT) technology. In Proceedings of the 2019 Conference on Information Communications Technology and Society (ICTAS), Durban, South Africa, 6–8 March 2019; pp. 1–6. [Google Scholar]
- Pitu, F.; Gaitan, N.C. Surveillance of SigFox technology integrated with environmental monitoring. In Proceedings of the 2020 International Conference on Development and Application Systems (DAS), Suceava, Romania, 21–23 May 2020; pp. 69–72. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Novel enhanced LoRaWAN framework for smart home remote control security. Wirel. Pers. Commun. 2020, 110, 2109–2130. [Google Scholar] [CrossRef]
- Eldefrawy, M.; Butun, I.; Pereira, N.; Gidlund, M. Formal security analysis of LoRaWAN. Comput. Netw. 2019, 148, 328–339. [Google Scholar] [CrossRef] [Green Version]
- Butun, I.; Pereira, N.; Gidlund, M. Security risk analysis of LoRaWAN and future directions. Future Internet 2019, 1, 3. [Google Scholar] [CrossRef] [Green Version]
- Seller, O.B.; Sornin, N. Low Power Long Range Transmitter. U.S. Patent No. 9,252,834, 2 February 2016. [Google Scholar]
- Sforza, F. Communications System. U.S. Patent No. 8,406,275, 26 March 2013. [Google Scholar]
- Augustin, A.; Yi, J.; Clausen, T.; Townsley, W.M. A study of LoRa: Long range & low power networks for the internet of things. Sensors 2016, 16, 1466. [Google Scholar]
- LoRa Alliance Technical Committee. RP002-1.0.3 LoRaWAN Regional Parameters; Tech. rep. Version: RP002-1.0.3; LoRa Alliance Technical Committee: Fremont, CA, USA, 2021. [Google Scholar]
- LoRa Alliance Technical Committee. LoRaWAN Specification; Tech. rep. Version 1.0; LoRa Alliance Technical Committee: Fremont, CA, USA, 2015. [Google Scholar]
- LoRa Alliance Technical Committee. LoRaWAN Specification; Tech. rep. Version 1.0.1; LoRa Alliance Technical Committee: Fremont, CA, USA, 2016. [Google Scholar]
- LoRa Alliance Technical Committee. LoRaWAN Specification; Tech. rep. Version 1.0.2; LoRa Alliance Technical Committee: Fremont, CA, USA, 2016. [Google Scholar]
- LoRa Alliance Technical Committee. LoRaWAN Specification; Tech. rep. Version 1.0.3; LoRa Alliance Technical Committee: Fremont, CA, USA, 2018. [Google Scholar]
- LoRa Alliance Technical Committee. LoRaWAN Specification; Tech. rep. Version 1.1; LoRa Alliance Technical Committee: Fremont, CA, USA, 2017. [Google Scholar]
- LoRa Alliance Technical Committee. LoRaWAN Specification; Tech. rep. Version 1.0.4; LoRa Alliance Technical Committee: Fremont, CA, USA, 2020. [Google Scholar]
- Noura, H.; Hatoum, T.; Salman, O.; Yaacoub, J.P.; Chehab, A. LoRaWAN security survey: Issues, threats and possible mitigation techniques. Internet Things 2020, 12, 100303. [Google Scholar] [CrossRef]
- Adelantado, F.; Vilajosana, X.; Tuset-Peiro, P.; Martinez, B.; Melia-Segui, J.; Watteyne, T. Understanding the limits of LoRaWAN. IEEE Commun. Mag. 2017, 55, 34–40. [Google Scholar] [CrossRef] [Green Version]
- Bankov, D.; Khorov, E.; Lyakhov, A. On the limits of LoRaWAN channel access. In Proceedings of the 2016 International Conference on Engineering and Telecommunication (EnT), Moscow, Russia, 29–30 November 2016; pp. 10–14. [Google Scholar]
- Le, D.T.; Dinh, T.D.; Kirichek, R.; Filin, E.; Shestakov, A. A Combined Attack Scenario to Exploit the Join Procedure of LoRaWAN. In Proceedings of the 2021 13th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Brno, Czech Republic, 25–27 October 2021; pp. 188–193. [Google Scholar]
- Zulian, S. Security Threat Analysis and Countermeasures for LoRaWAN Join Procedure. 2016. Available online: https://thesis.unipd.it/bitstream/20.500.12608/27531/1/zulian_simone_tesi.pdf (accessed on 3 June 2021).
- Fan, C.I.; Zhuang, E.S.; Karati, A.; Su, C.H. A Multiple End-Devices Authentication Scheme for LoRaWAN. Electronics 2022, 11, 797. [Google Scholar] [CrossRef]
- Van Es, E.; Vranken, H.; Hommersom, A. Denial-of-service attacks on LoRaWAN. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–6. [Google Scholar]
- Na, S.; Hwang, D.; Shin, W.; Kim, K.H. Scenario and countermeasure for replay attack using join request messages in LoRaWAN. In Proceedings of the 2017 International Conference on Information Networking (ICOIN), Da Nang, Vietnam, 11–13 January 2017; pp. 718–720. [Google Scholar]
- Kim, J.; Song, J. A simple and efficient replay attack prevention scheme for LoRaWAN. In Proceedings of the 2017 the 7th International Conference on Communication and Network Security, Tokyo, Japan, 24–26 November 2017; pp. 32–36. [Google Scholar]
- Gebremichael, T.; Ledwaba, L.P.; Eldefrawy, M.H.; Hancke, G.P.; Pereira, N.; Gidlund, M.; Akerberg, J. Security and privacy in the industrial internet of things: Current standards and future challenges. IEEE Access 2020, 8, 152351–152366. [Google Scholar] [CrossRef]
- Sundaram, J.P.S.; Du, W.; Zhao, Z. A survey on lora networking: Research problems, current solutions, and open issues. IEEE Commun. Surv. Tutor. 2019, 22, 371–388. [Google Scholar] [CrossRef] [Green Version]
- Lalle, Y.; Fourati, L.C.; Fourati, M.; Barraca, J.P. A comparative study of lorawan, sigfox, and nb-iot for smart water grid. In Proceedings of the 2019 Global Information Infrastructure and Networking Symposium (GIIS), Paris, France, 18–20 December 2019; pp. 1–6. [Google Scholar]
- Lalle, Y.; Fourati, L.C.; Fourati, M.; Barraca, J.P. LoRaWAN Network Capacity Analysis for Smart Water Grid. In Proceedings of the 2020 12th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20–22 July 2020; pp. 1–6. [Google Scholar]
- Kuntke, F.; Romanenko, V.; Linsner, S.; Steinbrink, E.; Reuter, C. LoRaWAN security issues and mitigation options by the example of agricultural IoT scenarios. Trans. Emerg. Telecommun. Technol. 2022, e4452. [Google Scholar] [CrossRef]
- de Moraes, P.; da Conceição, A.F. A Systematic Review of Security in the LoRaWAN Network Protocol. arXiv 2021, arXiv:2105.00384. [Google Scholar]
- Hessel, F. LoRaWAN Security Analysis: An Experimental Evaluation of Attacks. Master’s Thesis, Technische Universität Darmstadt, Darmstadt, Germany, 2021. [Google Scholar]
- Claverie, T.; Esteves, J.L. A LoRaWAN Security Assessment Test Bench. In Proceedings of the GNU Radio Conference, Charlotte, NC, USA, 20–24 September 2021; Volume 2. [Google Scholar]
- 102 024-3 v4. 1.1; Telecommunications and Internet Protocol Harmonization over Networks (TIPHON) Release 4; Protocol Framework Definition; Methods and Protocols for Security; part 1: Threat Analysis. Technical Specification. European Telecommunications Standards Institute: Cedex, France, 2003.
- Butun, I.; Pereira, N.; Gidlund, M. Analysis of LoRaWAN v1.1 security. In Proceedings of the 4th ACM MobiHoc Workshop on Experiences with the Design and Implementation of Smart Objects, Los Angeles, CA, USA, 25 June 2018; pp. 1–6. [Google Scholar]
- Haxhibeqiri, J.; De Poorter, E.; Moerman, I.; Hoebeke, J. A survey of LoRaWAN for IoT: From technology to application. Sensors 2018, 18, 3995. [Google Scholar] [CrossRef] [Green Version]
- Yang, X.; Karampatzakis, E.; Doerr, C.; Kuipers, F. Security vulnerabilities in LoRaWAN. In Proceedings of the 2018 IEEE/ACM Third International Conference on Internet-of-Things Design and Implementation (IoTDI), Orlando, FL, USA, 17–20 April 2018; pp. 129–140. [Google Scholar]
- Jalowiczor, J.; Rozhon, J.; Voznak, M. Study of the Efficiency of Fog Computing in an Optimized LoRaWAN Cloud Architecture. Sensors 2021, 21, 3159. [Google Scholar] [CrossRef] [PubMed]
- Aljumah, A.; Ahanger, T.A. Fog computing and security issues: A review. In Proceedings of the 2018 7th International Conference on Computers Communications and Control (ICCCC), Oradea, Romania, 8–12 May 2018; pp. 237–239. [Google Scholar]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog computing for the internet of things: Security and privacy issues. IEEE Internet Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- IEEE Std. 802; IEEE Standard for Local and Metropolitan Area Networks—Part 15.4: Low-Rate Wireless Personal area Networks (LR-WPANS). IEEE: New York, NY, USA, 2011; pp. 4–2011.
- Song, J.; Poovendran, R.; Lee, J.; Iwata, T. The Aes-cmac Algorithm. RFC 4493. June 2006. Available online: https://datatracker.ietf.org/doc/html/rfc4493 (accessed on 23 March 2022).
- Sornin, N.; Yegin, A. LoRaWAN Backend Interfaces 1.0 Specification. Lora Alliance Standard Specification. 2017. Available online: https://lora-alliance.org/wp-content/uploads/2020/11/lorawantm-backend-interfaces-v1.0.pdf (accessed on 23 March 2022).
- Jouhari, M.; Amhoud, E.M.; Saeed, N.; Alouini, M.S. A Survey on Scalable LoRaWAN for Massive IoT: Recent Advances, Potentials, and Challenges. arXiv 2022, arXiv:2202.11082. [Google Scholar]
- Almuhaya, M.A.; Jabbar, W.A.; Sulaiman, N.; Abdulmalek, S. A Survey on LoRaWAN Technology: Recent Trends, Opportunities, Simulation Tools and Future Directions. Electronics 2022, 11, 164. [Google Scholar] [CrossRef]
- Wu, Y.; He, Y.; Shi, L. Energy-saving measurement in LoRaWAN-based wireless sensor networks by using compressed sensing. IEEE Access 2020, 8, 49477–49486. [Google Scholar] [CrossRef]
- El Rachkidy, N.; Guitton, A.; Kaneko, M. Collision resolution protocol for delay and energy efficient LoRa networks. IEEE Trans. Green Commun. Netw. 2019, 3, 535–551. [Google Scholar] [CrossRef]
- Abdelfadeel, K.Q.; Zorbas, D.; Cionca, V.; Pesch, D. $ free $—Fine-grained scheduling for reliable and energy-efficient data collection in lorawan. IEEE Internet Things J. 2019, 7, 669–683. [Google Scholar] [CrossRef] [Green Version]
- Delgado, C.; Sanz, J.M.; Blondia, C.; Famaey, J. Batteryless LoRaWAN communications using energy harvesting: Modeling and characterization. IEEE Internet Things J. 2020, 8, 2694–2711. [Google Scholar] [CrossRef]










| Frequency Band | Common Name |
|---|---|
| 863–870 MHz | EU868 |
| 902–928 MHz | US915 |
| 779–787 MHz | CN779 |
| 433 MHz | EU433 |
| 915–928 MHZ | AU915 |
| 470–510 MHz | CN470 |
| 923 MHz | AS923 |
| 920–923 MHz | KR920 |
| 865–867 MHZ | IN865 |
| 864–870 MHZ | RU864 |
| Scenario 1 | Scenario 2 | |||
| Root Keys Lifetime Keys | AppKey - - | AppKey NwkKey JSEncKey (from NwkKey) JSIntKey (from NwkKey) | ||
| Identifiers | DevEUI - AppEUI | DevEUI JoinEUI AppEUI (storage on NS) | ||
| Nonce used for deriving security session | DevNonce (randomly) AppNonce (randomly) | DevNonce (Incremental) JoinNonce (Incremental) RJcount0 (Incremental) RJcount1(Incremenatl) | ||
| Session context -address of device -frame counters -security session keys | DevAddr FCntUp FCntDown AppSKey (from AppKey) NwkSKey (from AppKey) | DevAddr FCntUp NFCntDwn AFCntDwn AppSKey (from AppKey) NwkSEncKey (from NwkKey) SNwkSIntKey (from NwkKey) FNwkSIntKey (from NwkKey) | ||
| Exchanged messages | Ciphered by | Signed by | Ciphered by | Signed by |
| -Join-request -Rejoin-request type 0, 2 -Rejoin-request type 1 -Join-accept (reply to Join-request) -Join-accept (reply to Rejoin-request) -Data Up FRMPayload (MAC Commands) FRMPayload (Data) FOpts -Data Down FRMPayload (MAC Commands) FRMPayload (Data) FOpts | Plain Text Not used Not used AppKey Not used NwkSKey AppSkey Plain Text NwkSKey AppSkey Plain Text | AppKey Not used Not used AppKey Not used NwkSKey NwkSkey | Plain Text Plain Text Plain Text NwkKey JSEncKey NwkSEncKey AppSKey NwkSEncKey NwkSEncKey AppSkey NwkSEncKey | NwkKey SNwkSIntKey JSIntKey JSIntKey JSIntKey SNwkSIntKey + FNwkSIntKey SNwkSIntKey |
| Scenario 3 | Scenario 4 | |||||||
| ED v1.1 Side | NS v1.0 Side | ED v1.0 Side | NS v1.1 Side | |||||
| Root Keys Lifetime Keys | NwkKey - | AppKey - | AppKey - | NwkKey - | ||||
| Identifiers | DevEUI JoinEUI | DevEUI AppEUI | DevEUI AppEUI | DevEUI JoinEUI (out-of-band mechanism) | ||||
| Nonce used for deriving security session | DevNonce (Incremental) JoinNonce(keep track) | DevNonce (keep track) appNonce(randomly) | DevNonce (randomly) AppNonce(No track) | DevNonce (Keep track) JoinNonce(Incremental) | ||||
| Session context -address of device -frame counters -security session keys | DevAddr FCntUp FCntDown AppSkey(from NwkKey) | DevAddr FCntUp FCntDown AppSKey(from AppKey) | DevAddr FCntUp FCntDown AppSKey(from AppKey) | DevAddr FCntUp FCntDown AppSKey(from NwkKey) | ||||
| FNwkSIntKey(from NwkKey) = SNwkSIntKey = NwkSEncKey | NwkSKey(from AppKey) | NwkSKey(from AppKey) | NwkSKey(from NwkKey) | |||||
| Exchanged messages | Ciphered by | Signed by | Ciphered by | Signed by | Ciphered by | Signed by | Ciphered by | Signed by |
| -Join-Request (JR) -ReJoin-Request(RJR) type 0, 2 -ReJoin-Request(RJR) type 1 -Join-accept (reply to JR) -Join-accept (reply to RJR) -Data Up FRMPayload (MAC Commands) FRMPayload (Data) FOpts -Data Down FRMPayload (MAC Commands) FRMPayload (Data) FOpts | Plain Text Not used Not used NwkKey Not used - NwkSEncKey AppSKey Plain Text - NwkSEncKey AppSkey Plain Text | NwkKey Not used Not used NwkKey Not used FNwkSIntKey SNwkSIntKey | Plain Text Not used Not used AppKey Not used - NwkSKey AppSKey Plain Text NwkSKey AppSkey PlainText | AppKey Not used Not used AppKey NwkSkey NwkSKey | Plain Text Not used Not used AppKey Not used - NwkSKey AppSKey Plain Text - NwkSKey AppSkey Plain Text | AppKey Not used Not used AppKey Not used NwkSKey NwkSKey | Plain text Not used Not used NwkKey Not used - NwkSEncKey AppSKey Plain Text - NwkSEncKey AppSkey Plain Text | NwkKey Not used Not used NwkKey Not used NwkSKey NwkSKey |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Loukil, S.; Fourati, L.C.; Nayyar, A.; Chee, K.-W.-A. Analysis of LoRaWAN 1.0 and 1.1 Protocols Security Mechanisms. Sensors 2022, 22, 3717. https://doi.org/10.3390/s22103717
Loukil S, Fourati LC, Nayyar A, Chee K-W-A. Analysis of LoRaWAN 1.0 and 1.1 Protocols Security Mechanisms. Sensors. 2022; 22(10):3717. https://doi.org/10.3390/s22103717
Chicago/Turabian StyleLoukil, Slim, Lamia Chaari Fourati, Anand Nayyar, and K.-W.-A. Chee. 2022. "Analysis of LoRaWAN 1.0 and 1.1 Protocols Security Mechanisms" Sensors 22, no. 10: 3717. https://doi.org/10.3390/s22103717
APA StyleLoukil, S., Fourati, L. C., Nayyar, A., & Chee, K.-W.-A. (2022). Analysis of LoRaWAN 1.0 and 1.1 Protocols Security Mechanisms. Sensors, 22(10), 3717. https://doi.org/10.3390/s22103717







